Information Security
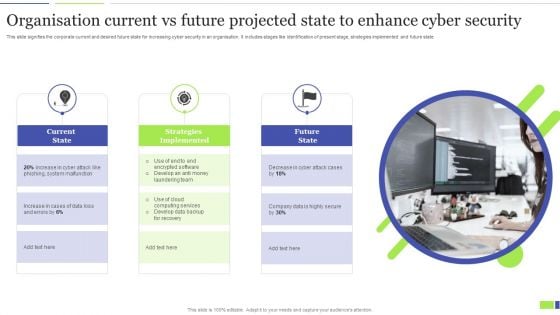
Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF
This slide signifies the corporate current and desired future state for increasing cyber security in an organisation. It includes stages like identification of present stage, strategies implemented and future state. Presenting Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Current State, Strategies Implemented, Future State. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
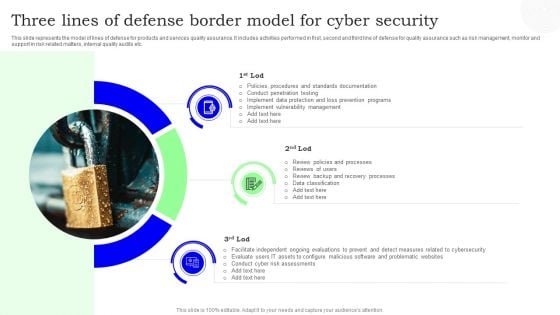
Three Lines Of Defense Border Model For Cyber Security Designs PDF
This slide represents the model of lines of defense for products and services quality assurance. It includes activities performed in first, second and third line of defense for quality assurance such as risk management, monitor and support in risk related matters, internal quality audits etc. Presenting Three Lines Of Defense Border Model For Cyber Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Security, Three Lines, Border Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Project Security Administration IT Determine Project Safety Management Team Structure Sample PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a project security administration it determine project safety management team structure sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like public affair advisor, security manager, legal advisor, medical advisor, crisis management advisor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
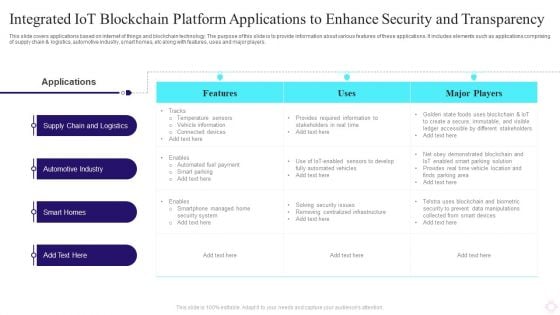
Integrated IOT Blockchain Platform Applications To Enhance Security And Transparency Portrait PDF
This slide covers applications based on internet of things and blockchain technology. The purpose of this slide is to provide information about various features of these applications. It includes elements such as applications comprising of supply chain and logistics, automotive industry, smart homes, etc along with features, uses and major players. Pitch your topic with ease and precision using this Integrated IOT Blockchain Platform Applications To Enhance Security And Transparency Portrait PDF. This layout presents information on Automotive Industry, Smart Homes, Applications. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Various Strategies To Ensure Food Safety Food Security Excellence Ppt Icon Slide PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety food security excellence ppt icon slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF
This slide shows comparison of software available for detecting insider threat. It provides information about tools, features, user reviews, detection rate, free trial and pricing. Pitch your topic with ease and precision using this Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF. This layout presents information on User Reviews, Detection Rate, Free Trial. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Laptop Deals Cyber Security Awareness In Powerpoint And Google Slides Cpb
Introducing our well-designed Laptop Deals Cyber Security Awareness In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Laptop Deals Cyber Security Awareness. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Laptop Deals Cyber Security Awareness In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Google Pixel Enterprise Security System In Powerpoint And Google Slides Cpb
Introducing our well-designed Google Pixel Enterprise Security System In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Google Pixel Enterprise Security System. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Google Pixel Enterprise Security System In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
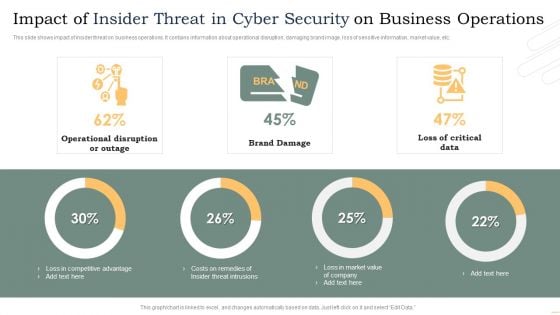
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
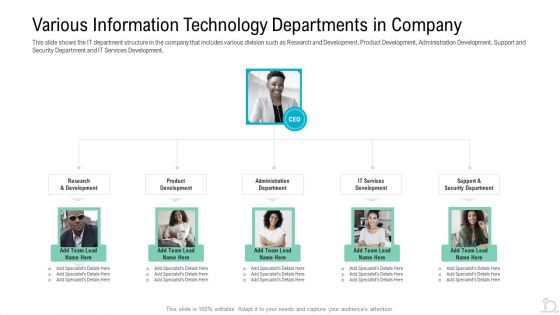
Various Information Technology Departments In Company Formats PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development. This is a various information technology departments in company formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like product development, research and development, support and security department. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
3 Stage Plan Cyber Security Plan For Data Protection Ppt Icon Picture PDF
This slide signifies the three stage cyber security program to improve data protection. It covers information about steps like prevention, response and remediation. Persuade your audience using this 3 Stage Plan Cyber Security Plan For Data Protection Ppt Icon Picture PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prevention, Response, Remediation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Implementing Cybersecurity Awareness Program To Prevent Attacks Overview Of Cyber Security Awareness Course Microsoft PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Key Objectives Of People Centric Work Culture Security System Infographics PDF
The following slide highlights the main reasons to develop human centric security system for better security features. It mainly includes activities such as establishing secure perimeter, comprehending cause behind user actions, optimizing remote security operations etc. Presenting Key Objectives Of People Centric Work Culture Security System Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Establish Secure Perimeter, Acknowledges Potential Threats, Employee Roles. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
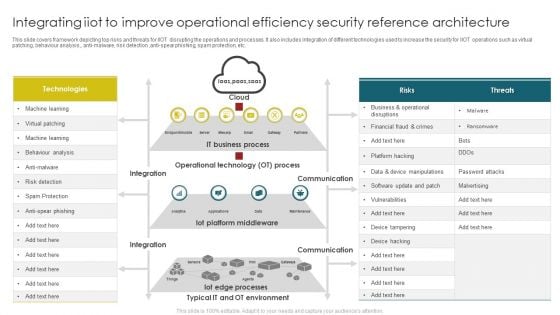
Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF
This slide covers framework depicting top risks and threats for IIOT disrupting the operations and processes. It also includes integration of different technologies used to increase the security for IIOT operations such as virtual patching, behaviour analysis, anti malware, risk detection, anti spear phishing, spam protection, etc. Pitch your topic with ease and precision using this Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF. This layout presents information on Operational Technology, IT Business Process, Iot Platform Middleware . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Supply Chain Management Iot Security Lock For Safe Fleet Management Download PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Iot Security Lock For Safe Fleet Management Download PDF. Use them to share invaluable insights on Key Applications, Potential Impact, Multiple Positioning Methods and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
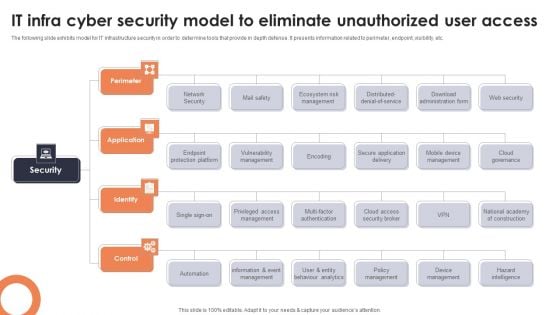
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
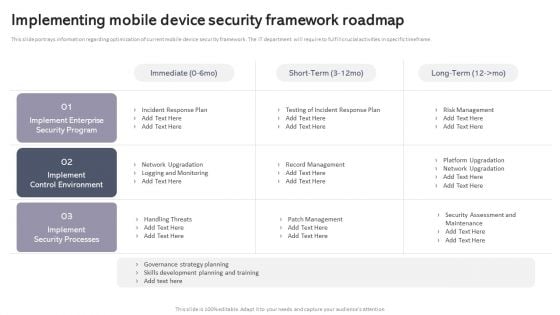
Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Explore a selection of the finest Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Workplace Portable Device Monitoring And Administration Implementing Mobile Device Security Framework Roadmap Mockup PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

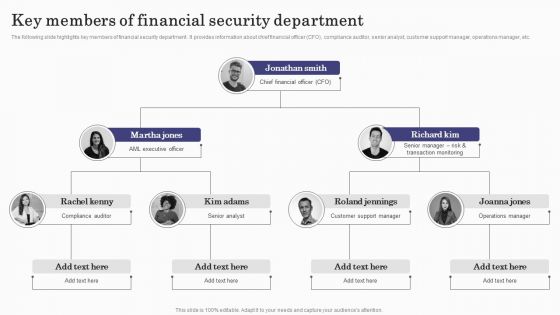
Integrating AML And Transaction Key Members Of Financial Security Department Slides PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This Integrating AML And Transaction Key Members Of Financial Security Department Slides PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. TheIntegrating AML And Transaction Key Members Of Financial Security Department Slides PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF
The following slide showcases various approaches to AI infrastructure which bodes well for future of organizations association. It presents information related to regulatory framework, expert consultations, etc. Presenting Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Regulatory Framework, Protect AI Related Data, Involve Cybersecurity Experts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
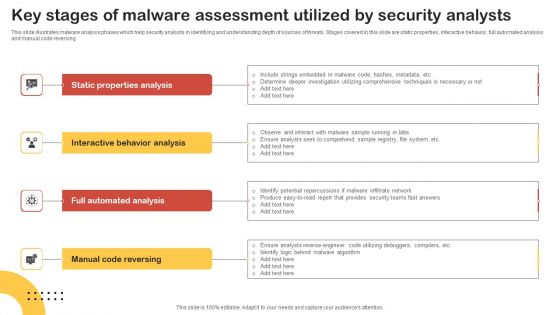
Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF
This slide illustrates malware analysis phases which help security analysts in identifying and understanding depth of sources of threats. Stages covered in this slide are static properties, interactive behavior, full automated analysis and manual code reversing. Presenting Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Static Properties Analysis, Interactive Behavior Analysis, Full Automated Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
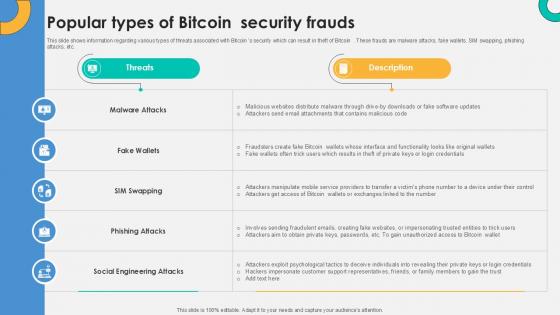
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc.

Agenda For Information Technology Threat Mitigation Methods Background PDF
This is a Agenda For Information Technology Threat Mitigation Methods Background PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enterprise, Organization, Management Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
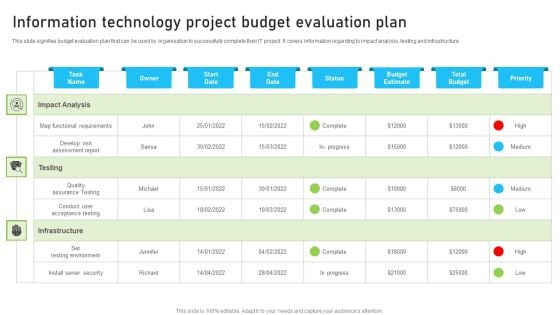
Information Technology Project Budget Evaluation Plan Pictures PDF
This slide signifies the project key performance indicator dashboard to evaluate financial budget evaluation. It covers information regarding to allocated and used budget. Pitch your topic with ease and precision using this Information Technology Project Budget Evaluation Plan Pictures PDF. This layout presents information on Develop Risk Assessment Report, Environment, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Deploying Banking Transaction Key Members Of Financial Security Department Guidelines PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This modern and well-arranged Deploying Banking Transaction Key Members Of Financial Security Department Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
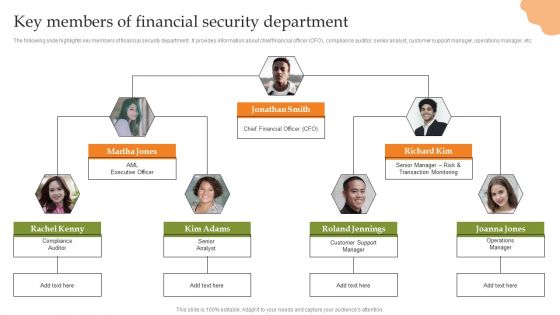
Creating Transaction Monitoring Key Members Of Financial Security Department Summary PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This modern and well-arranged Creating Transaction Monitoring Key Members Of Financial Security Department Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you know about Slidesgeeks Implementing Cybersecurity Awareness Program To Prevent Attacks Pricing Plan Of Security Awareness Packages Template PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Retrieve professionally designed Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Welcome to our selection of the Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
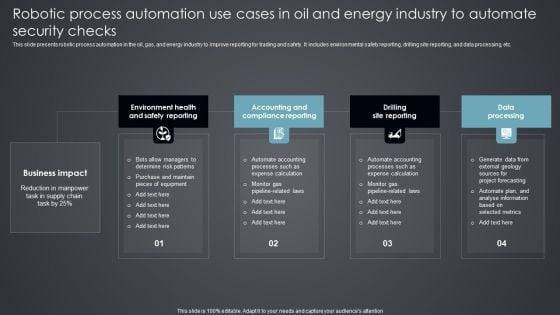
Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF
This slide presents robotic process automation in the oil, gas, and energy industry to improve reporting for trading and safety. It includes environmental safety reporting, drilling site reporting, and data processing, etc. Presenting Robotic Process Automation Use Cases In Oil And Energy Industry To Automate Security Checks Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Environment Health, Accounting Compliance Reporting, Drilling Site Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
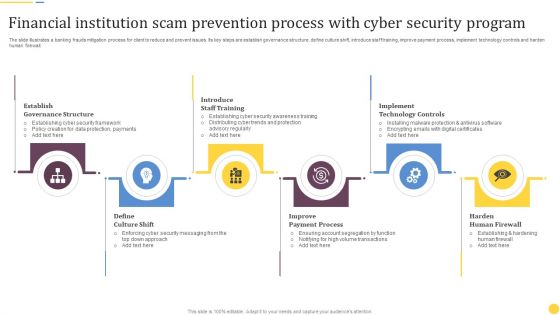
Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Best Paid Password Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Best Paid Password Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Best Paid Password Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Best Paid Password Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
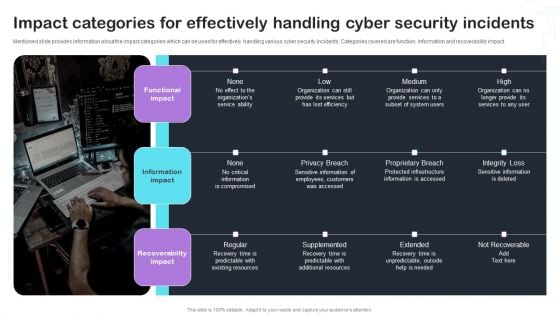
Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. This Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

IT Services Business Profile Information Technology Services Summary PDF
The slide showcases range of information technology services offered by company for customers. It depicts managed services, intelligent business services, digital experience, solution engineering, innovation services and technology and security advisory. Presenting IT Services Business Profile Information Technology Services Summary PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Managed Services, Intelligent Business, Digital Experience. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
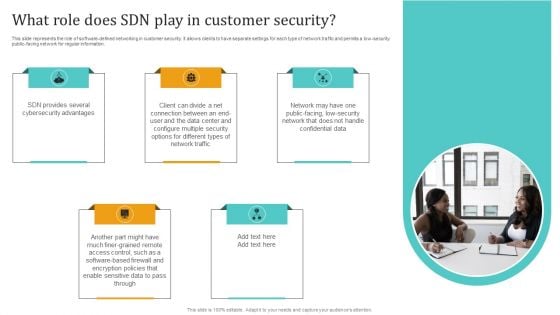
Empowering Network Agility Through SDN What Role Does SDN Play In Customer Security Professional PDF
This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information. This Empowering Network Agility Through SDN What Role Does SDN Play In Customer Security Professional PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
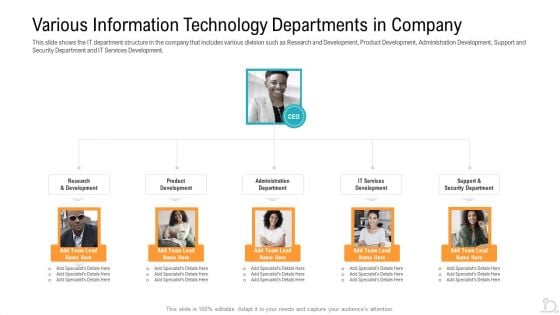
Various Information Technology Departments In Company Designs PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development.Presenting various information technology departments in company designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like various information technology departments in company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Protection And Privacy Roadmap Sample PDF
The following slide showcases IT security and privacy roadmap to protect digital information from severe threats. It includes elements such as assess, build, select, deploy, train and test. Persuade your audience using this Information Technology Protection And Privacy Roadmap Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Deploy, Build, Select, Train. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Solutions Business Profile Our Management Team Introduction PDF
This slide shows the key people involved in management team which includes chief executive officer, executive assistant, chief financial officer, senior developer, security risk manager and chief technology officer.Presenting Information Technology Solutions Business Profile Our Management Team Introduction PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Executive Officer, Executive Assistant, Financial Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Implementing Safety Administration Initiative For Risk Mitigation Way To Overcome Security Demonstration PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. This is a implementing safety administration initiative for risk mitigation way to overcome security demonstration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like goals, information, risk, analysis, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. The Managing E Commerce Business Accounting Pci Certification For Increasing Security Of Online Transactions Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
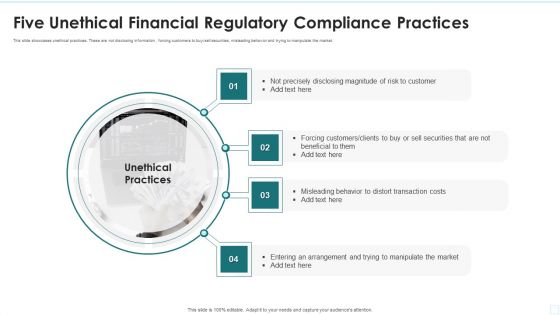
Five Unethical Financial Regulatory Compliance Practices Information PDF
This slide showcases unethical practices. These are not disclosing information , forcing customers to buy sell securities, misleading behavior and trying to manipulate the market.Presenting Five Unethical Financial Regulatory Compliance Practices Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Precisely Disclosing, Forcing Customers, Misleading Behavior This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
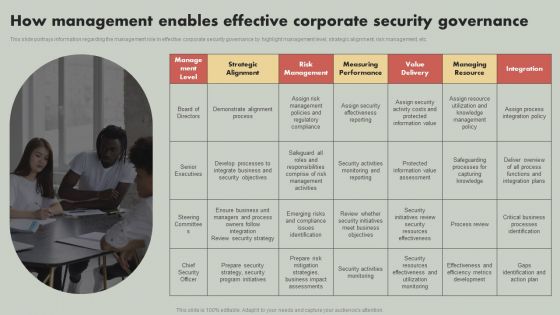
IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Get a simple yet stunning designed IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
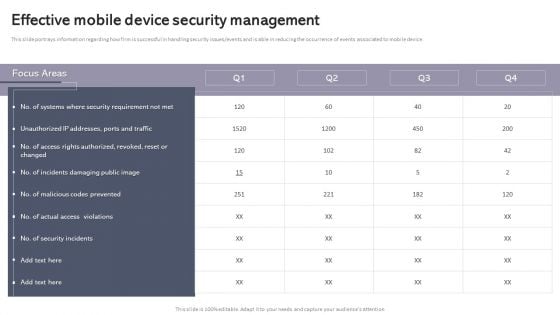
Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. This Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Workplace Portable Device Monitoring And Administration Effective Mobile Device Security Management Pictures PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
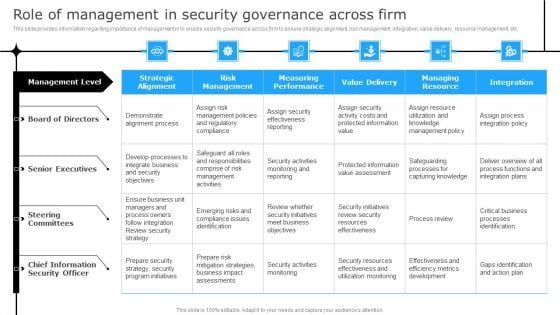
Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Get a simple yet stunning designed Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
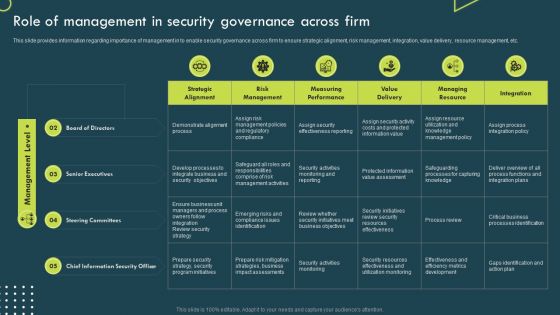
Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Strategic Corporate Planning To Attain Role Of Management In Security Governance Across Firm Guidelines PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.
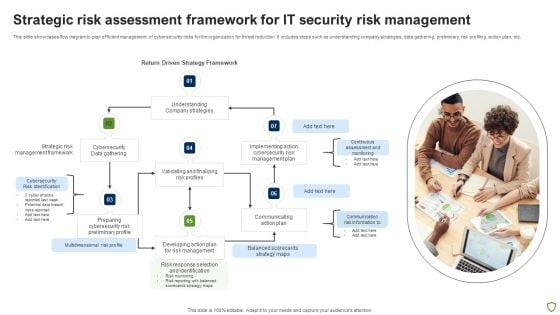
Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF
This slide showcases flow diagram to plan efficient management of cybersecurity risks for the organization for threat reduction. It includes steps such as understanding company strategies, data gathering, preliminary risk profiling, action plan, etc. Presenting Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Strategic Risk, Cybersecurity, Management Framework, Data Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF
This slide depicts payment card industry PCI certification for increasing security of online transactions. It provides information about authorization, 2 way authentication, one time password OTP, repository, cyber attacks, compliance, data breach, etc. Slidegeeks has constructed PCI Certification For Increasing Security Of Online Transactions Financial Management Strategies Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
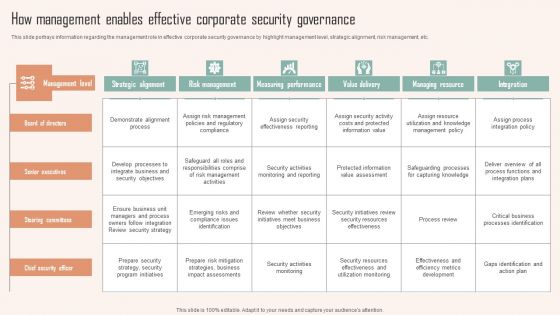
How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Present like a pro with Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Security Management Plan Steps In Detail System Maintenance And Monitoring Summary PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. Presenting security management plan steps in detail system maintenance and monitoring summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like types of system maintenance, installation costs, types of system monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF
The following slide highlights multistep process of digitization of security systems. The company can detect security breach after following steps such as investigating the steps of IT analyst, determining responsive action, eradication and closing the ticked. Presenting Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Studies Data Science In Business Sector Download PDF
This slide represents the data science application in business and its benefits, such as gaining customer insights, increased security, streamlining manufacturing, and predicting future market trends. This is a Information Studies Data Science In Business Sector Download PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Inform Internal Finances, Streamline Manufacturing, Increase Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
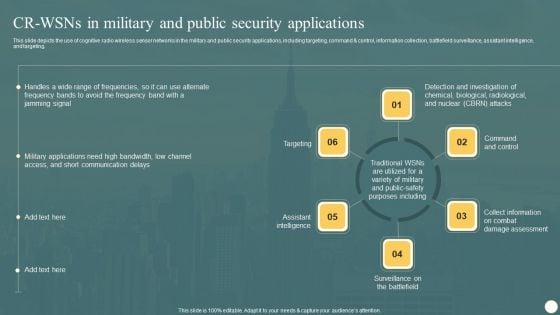
Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Presenting this PowerPoint presentation, titled Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Statement Of Work And Contract For Security Camera Services One Pager Sample Example Document
This slide depicts the terms and conditions of the proposal contract covering details about the client name, address, and company information. Presenting you an exemplary Statement Of Work And Contract For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Statement Of Work And Contract For Security Camera Services One Pager Sample Example Document brilliant piece now.
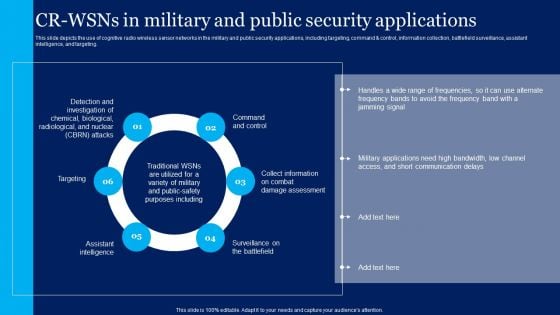
Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Explore a selection of the finest Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Operational Outlook Of Security Awareness Training Software Ppt Icon Slideshow PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Organizing Security Awareness In House Training Schedule We Will Implement Background PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and iot-based attack. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Organizing Security Awareness In House Training Schedule We Will Implement Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Organizing Security Awareness In House Training Schedule We Will Implement Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.


 Continue with Email
Continue with Email

 Home
Home


































