Information Security

Building Trust With IoT Security Automated Patch Management To Increase Overall Productivity IoT SS V
This slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies. It includes steps such as scan for missing patches, collect patches from vendors, deploy patches, and report results. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Automated Patch Management To Increase Overall Productivity IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies. It includes steps such as scan for missing patches, collect patches from vendors, deploy patches, and report results.

Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V
This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery. There are so many reasons you need a Building Trust With IoT Security Best Practices To Provision Devices And Systems IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines best practices of device and system provisioning that aim to effectively integrate devices into the IoT ecosystem. It includes allocate unique identifies, set up access control, and backup and recovery.
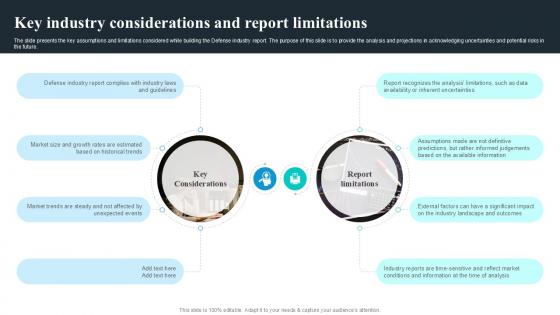
Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. The slide presents the key assumptions and limitations considered while building the Defense industry report. The purpose of this slide is to provide the analysis and projections in acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile.

Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. This Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Traditional Perimeter Based Network Security Overview And Limitations features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.
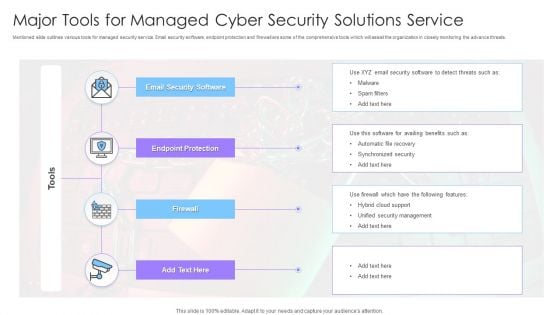
Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF
Mentioned slide outlines various tools for managed security service. Email security software, endpoint protection and firewall are some of the comprehensive tools which will assist the organization in closely monitoring the advance threats. Showcasing this set of slides titled Major Tools For Managed Cyber Security Solutions Service Ppt Infographics Graphics Tutorials PDF. The topics addressed in these templates are Endpoint Protection, Firewall, Email Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizational Network Security Awareness Staff Learning Communication Plan General Format Infographics PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning communication plan general format infographics pdf bundle. Topics like communication, security awareness, organizations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Portable Home Safety Systems Company Profile Security Company Strategic Partnerships Structure PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation. Deliver and pitch your topic in the best possible manner with this Portable Home Safety Systems Company Profile Security Company Strategic Partnerships Structure PDF. Use them to share invaluable insights on Services, Partnership Type, Year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Exit Strategy Voice Assistance Security Platform Investor Funding Presentation Structure Pdf
The slide provides most profitable feasible ways for investors to exit from their investment in the company. It consists of strategies like IPO Initial Public Offering and partnership exit. Welcome to our selection of the Exit Strategy Voice Assistance Security Platform Investor Funding Presentation Structure Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today The slide provides most profitable feasible ways for investors to exit from their investment in the company. It consists of strategies like IPO Initial Public Offering and partnership exit.
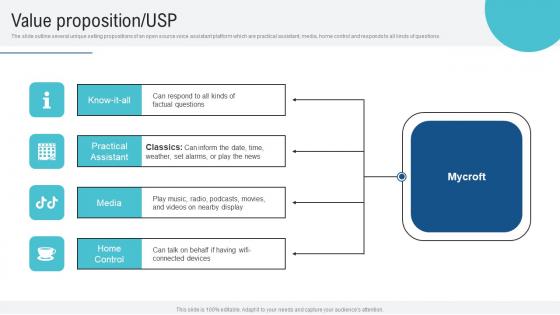
Value Proposition USP Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The slide outline several unique selling propositions of an open source voice assistant platform which are practical assistant, media, home control and responds to all kinds of questions. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Value Proposition USP Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The slide outline several unique selling propositions of an open source voice assistant platform which are practical assistant, media, home control and responds to all kinds of questions.

Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF
The following slide showcases the impact of software as a service SaaS security in developing business. It includes key elements such as scalability, security, customization, maintenance, availability, IT cost etc. Showcasing this set of slides titled Impact Saas Cloud Security Practices In Business Growth Ppt PowerPoint Presentation Gallery Elements PDF. The topics addressed in these templates are Scalability, Security, Customization, Maintenance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
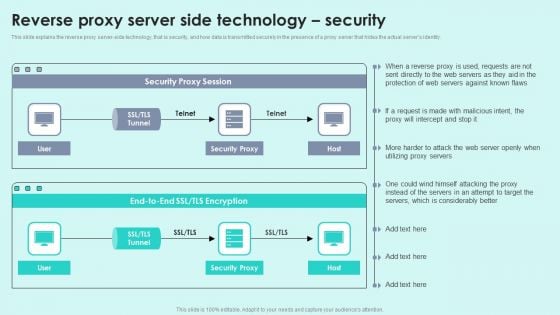
Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity.Deliver and pitch your topic in the best possible manner with this Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF. Use them to share invaluable insights on Security Proxy, Protection Servers, Considerably Better and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
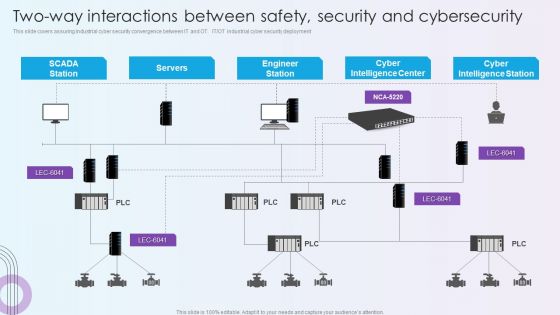
Digitalization Of Operative Enterprises Two Way Interactions Between Safety Security And Cybersecurity Themes PDF
This slide covers assuring industrial cyber security convergence between IT and OT. IT or OT industrial cyber security deployment. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises Two Way Interactions Between Safety Security And Cybersecurity Themes PDF. Use them to share invaluable insights on Cyber Intelligence Center, Cyber Intelligence Station, Engineer Station and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
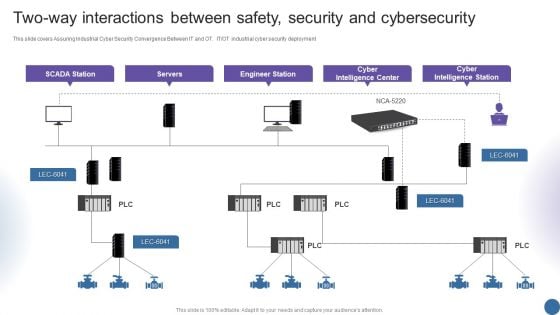
Two Way Interactions Between Safety Security And Cybersecurity Managing Organizational Transformation Summary PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT OT industrial cyber security deployment. Deliver an awe inspiring pitch with this creative Two Way Interactions Between Safety Security And Cybersecurity Managing Organizational Transformation Summary PDF bundle. Topics like Servers, Engineer Station, Intelligence Center can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
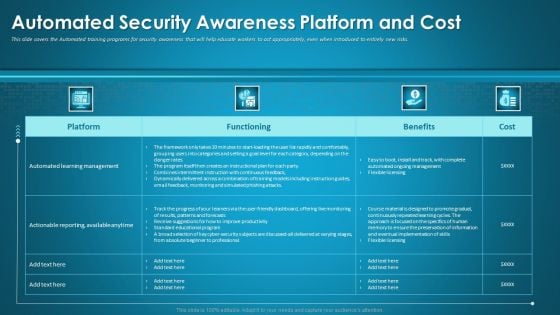
Organizational Network Staff Learning Automated Security Awareness Platform And Cost Introduction PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative organizational network staff learning automated security awareness platform and cost introduction pdf bundle. Topics like automated security awareness platform and cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
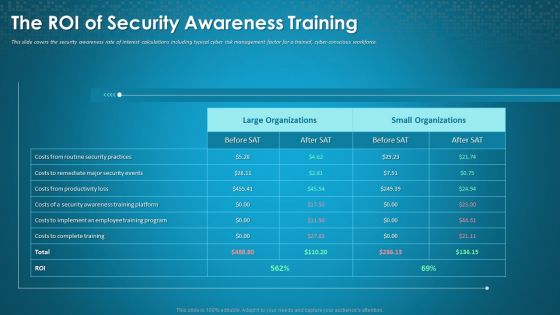
Organizational Network Staff Learning The ROI Of Security Awareness Training Designs PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this organizational network staff learning the roi of security awareness training designs pdf. Use them to share invaluable insights on employee training program, security awareness training platform, productivity loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF
This slide provide the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market etc.Persuade your audience using this Comparative Analysis Of Cloud And Traditional Computing It Security Diagrams PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Provided Parties, Initial Cost Investment, Comparatively Longer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
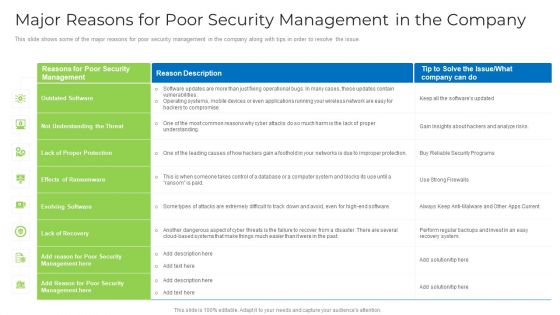
Major Reasons For Poor Security Management In The Company Download PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative major reasons for poor security management in the company download pdf bundle. Topics like applications, operating systems, network, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
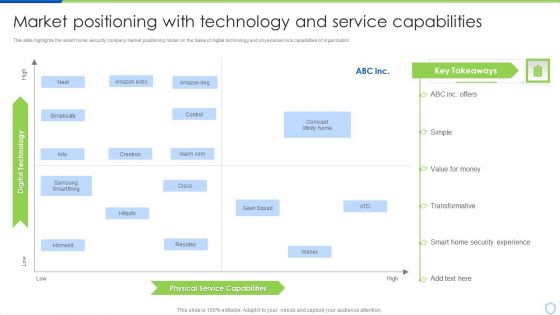
Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF bundle. Topics like Monitoring, Bluestone Security, Launched Integrated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF
This slide highlights security risks occurred in the company. The purpose of this template is to report the severity of security threats. It also includes action steps taken in prevention or resolution of security incidents along with risk categories. Showcasing this set of slides titled Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF. The topics addressed in these templates are Incidents, Category, Severity, Response Action Steps. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
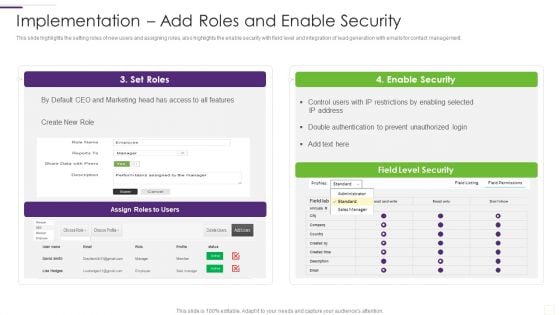
CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF bundle. Topics like Enable Security, Double Authentication, Prevent Unauthorized can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Kpis To Measure Phishing Scams And Attacks Topics PDF
Mentioned slide showcases 5 cyber security KPI which can be used by organization to measure phishing attacks. The KPIs mentioned in the slide are intrusion attempts, security incidents, mean time to detect MTTD, etc. Showcasing this set of slides titled cyber security kpis to measure phishing scams and attacks topics pdf. The topics addressed in these templates are cyber security kpis to measure phishing scams and attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf
Do you know about Slidesgeeks Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. Our Table Of Contents Exploring Investment Opportunities With Security Token Offerings Graphics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
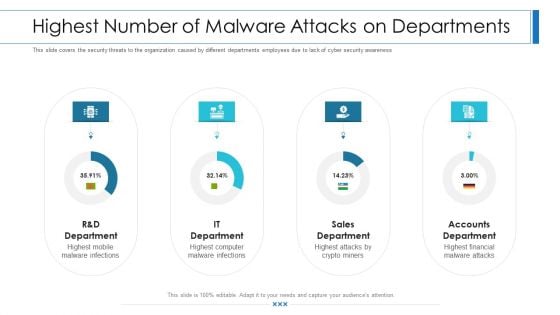
Workforce Security Realization Coaching Plan Highest Number Of Malware Attacks On Departments Professional PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan highest number of malware attacks on departments professional pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Checklist For Effectively Managing Asset Security Ppt Slides Example File PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative handling cyber threats digital era checklist for effectively managing asset security ppt slides example file pdf bundle. Topics like checklist for effectively managing asset security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
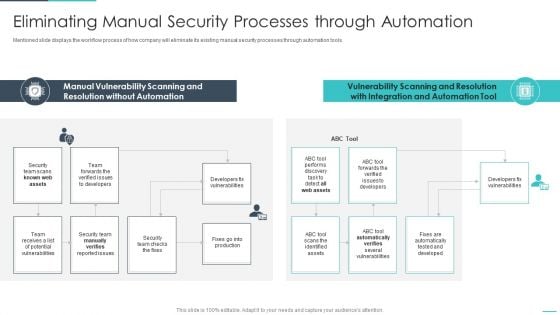
Handling Cyber Threats Digital Era Eliminating Manual Security Processes Ppt Show Influencers PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era eliminating manual security processes ppt show influencers pdf. Use them to share invaluable insights on eliminating manual security processes through automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
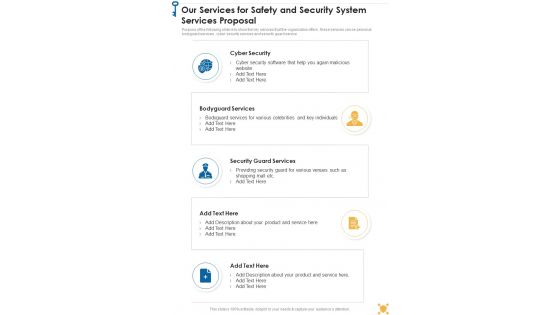
Our Services For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the key services that the organization offers , these services can be personal bodyguard services , cyber security services and security guard service. Presenting you an exemplary Our Services For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Services For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
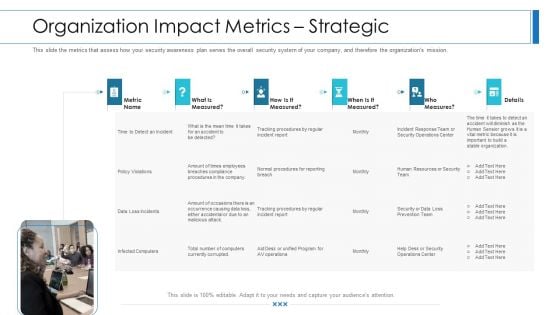
Workforce Security Realization Coaching Plan Organization Impact Metrics Strategic Infographics PDF
This slide the metrics that assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan organization impact metrics strategic infographics pdf. Use them to share invaluable insights on organization impact metrics strategicand impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
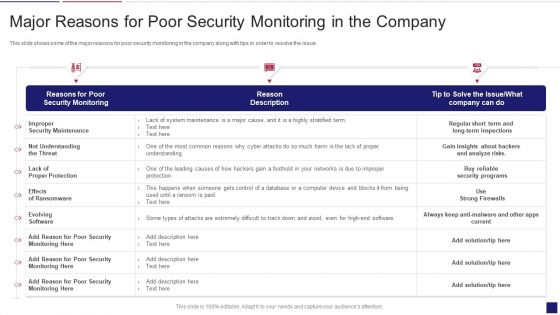
Continuous Development Evaluation Plan Eliminate Cyber Attacks Major Reasons For Poor Security Topics PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks major reasons for poor security topics pdf bundle. Topics like improper security maintenance, evolving software, effects of ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Artificial Intelligence Playbook Stage Five Security Breach Readiness Checklist Topics PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. Deliver an awe inspiring pitch with this creative artificial intelligence playbook stage five security breach readiness checklist topics pdf bundle. Topics like questions related, security breach readiness, each organizational procedure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
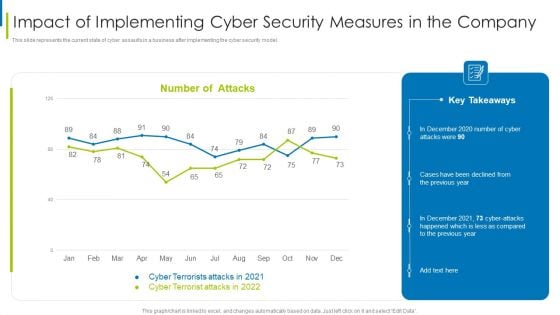
Cyber Terrorism Assault Impact Of Implementing Cyber Security Measures In The Company Professional PDF
This slide represents the current state of cyber assaults in a business after implementing the cyber security model.Deliver an awe inspiring pitch with this creative cyber terrorism assault impact of implementing cyber security measures in the company professional pdf bundle. Topics like impact of implementing cyber security measures in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
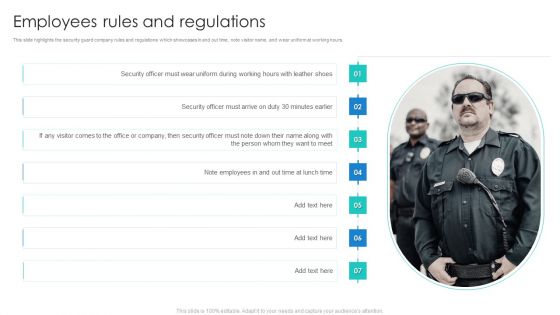
Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF bundle. Topics like Security, Employees Rules And Regulations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
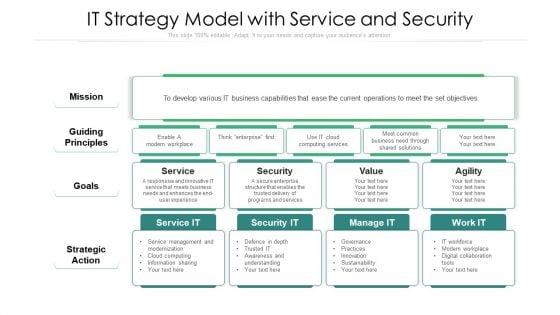
IT Strategy Model With Service And Security Ppt Professional Aids PDF
Showcasing this set of slides titled it strategy model with service and security ppt professional aids pdf. The topics addressed in these templates are strategic action, mission, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
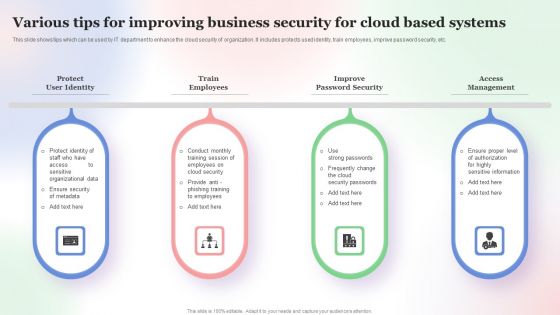
Various Tips For Improving Business Security For Cloud Based Systems Slides PDF
This slide shows tips which can be used by IT department to enhance the cloud security of organization. It includes protects used identity, train employees, improve password security, etc. Persuade your audience using this Various Tips For Improving Business Security For Cloud Based Systems Slides PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Various Tips For Improving, Business Security, Cloud Based Systems. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
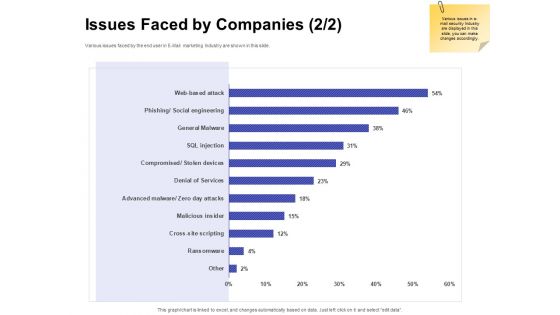
Global Cloud Based Email Security Market Issues Faced By Companies Services Portrait PDF
Presenting this set of slides with name global cloud based email security market issues faced by companies services portrait pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Our Services Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the key services that the organization offers , these services can be personal bodyguard services , cyber security services and security guard service. Presenting you an exemplary Our Services Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Services Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.
It Security With Lock On Computer Monitor Vector Icon Ppt PowerPoint Presentation Pictures Visual Aids PDF
Presenting it security with lock on computer monitor vector icon ppt powerpoint presentation pictures visual aids pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including it security with lock on computer monitor vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
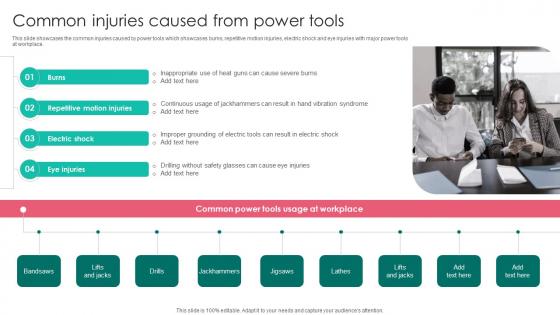
Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf
This slide showcases the common injuries caused by power tools which showcases burns, repetitive motion injuries, electric shock and eye injuries with major power tools at workplace. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Common Injuries Caused Power Workplace Safety Protocol And Security Practices Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the common injuries caused by power tools which showcases burns, repetitive motion injuries, electric shock and eye injuries with major power tools at workplace.
Vector Showing IT Security Under Threat Ppt PowerPoint Presentation Gallery Deck PDF
Showcasing this set of slides titled vector showing it security under threat ppt powerpoint presentation gallery deck pdf. The topics addressed in these templates are vector showing it security under threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF
Showcasing this set of slides titled Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF. The topics addressed in these templates are Cyber Security, Risk Management, Icon, IT Risk, Control Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
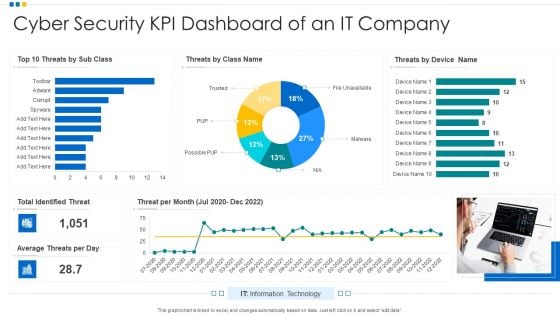
Cyber Security KPI Dashboard Of An IT Company Ppt Show Introduction PDF
Showcasing this set of slides titled Cyber Security KPI Dashboard Of An IT Company Ppt Show Introduction PDF. The topics addressed in these templates are Cyber Security, KPI Dashboard, Average Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
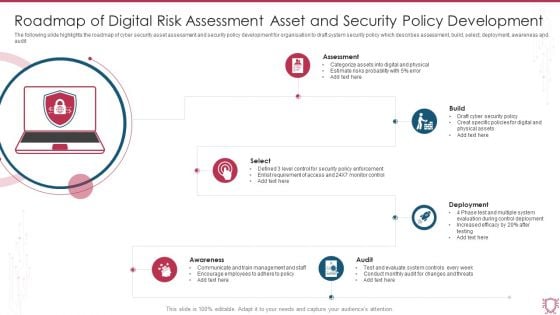
Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
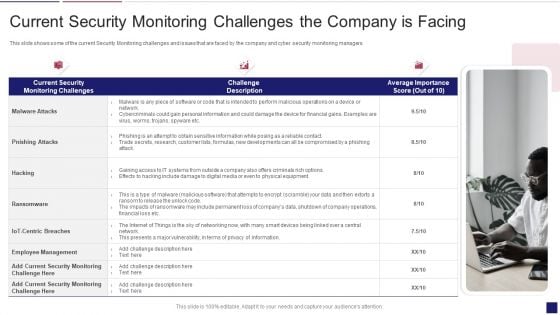
Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Infographics PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks current security monitoring infographics pdf bundle. Topics like monitoring, service, parameters can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
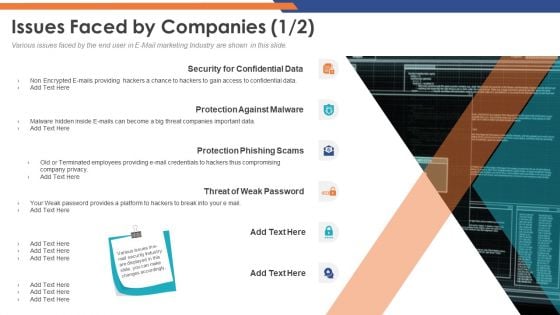
Email Security Market Research Report Issues Faced By Companies Professional PDF
Presenting this set of slides with name email security market research report issues faced by companies professional pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
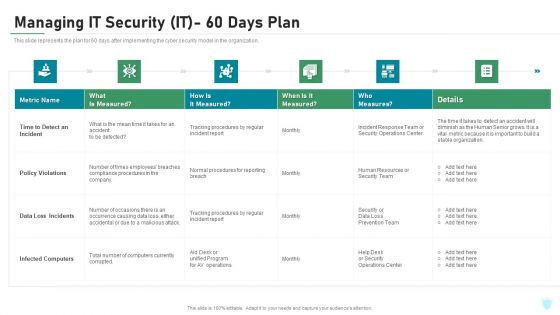
Managing IT Security IT 60 Days Plan Ppt Ideas Graphics PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative managing it security it 60 days plan ppt ideas graphics pdf bundle. Topics like policy violations, infected computers, data loss incidents, time to detect an incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
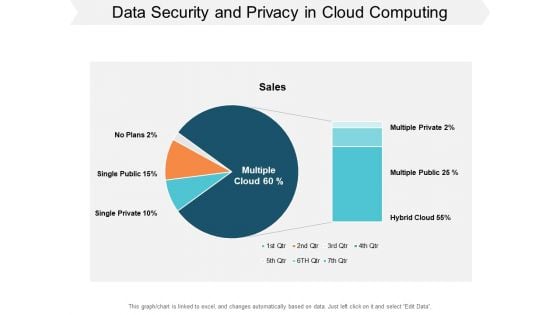
Data Security And Privacy In Cloud Computing Ppt PowerPoint Presentation Slides Graphic Tips
This is a data security and privacy in cloud computing ppt powerpoint presentation slides graphic tips. This is a two stage process. The stages in this process are cloud strategy, cloud planning, cloud management.
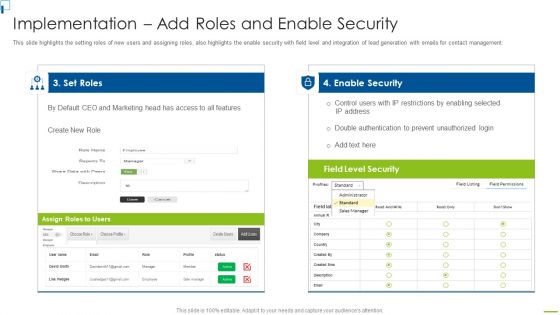
Designing And Deployment Implementation Add Roles And Enable Security Sample PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Deliver and pitch your topic in the best possible manner with this designing and deployment implementation add roles and enable security sample pdf. Use them to share invaluable insights on set roles, enable security, assign roles to users, field level security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security System Installation With Gear Wheel Vector Icon Ppt PowerPoint Presentation File Skills PDF
Presenting it security system installation with gear wheel vector icon ppt powerpoint presentation file skills pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including it security system installation with gear wheel vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twenty eight slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking. Our Internet Of Things Security Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cloud Data Storage Infrastructure And Security Ppt Powerpoint Presentation Model Show
This is a cloud data storage infrastructure and security ppt powerpoint presentation model show. This is a four stage process. The stages in this process are data management, data centre, storage system.
Digital Infrastructure Data Storage And Security Ppt Powerpoint Presentation Show Layout Ideas
This is a digital infrastructure data storage and security ppt powerpoint presentation show layout ideas. This is a six stage process. The stages in this process are data management, data centre, storage system.
Six Steps Of System Development Service Delivery And Data Security Ppt PowerPoint Presentation Icon Slide Download
This is a six steps of system development service delivery and data security ppt powerpoint presentation icon slide download. This is a six stage process. The stages in this process are risk management, risk factors, risk variable.

Threat Assessment For IT Network Security Ppt PowerPoint Presentation Gallery Example PDF
Presenting this set of slides with name threat assessment for it network security ppt powerpoint presentation gallery example pdf. This is a three stage process. The stages in this process are threat assessment for it network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
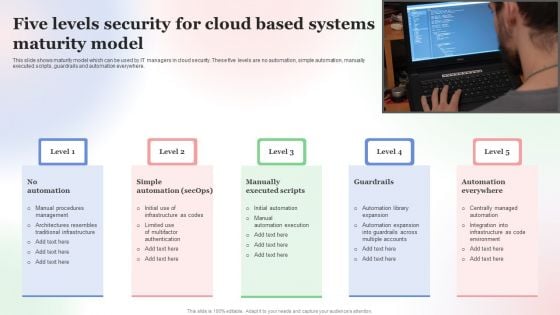
Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF
This slide shows maturity model which can be used by IT managers in cloud security. These five levels are no automation, simple automation, manually executed scripts, guardrails and automation everywhere. Presenting Five Levels Security For Cloud Based Systems Maturity Model Microsoft PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Five Levels Security, Cloud Based Systems, Maturity Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
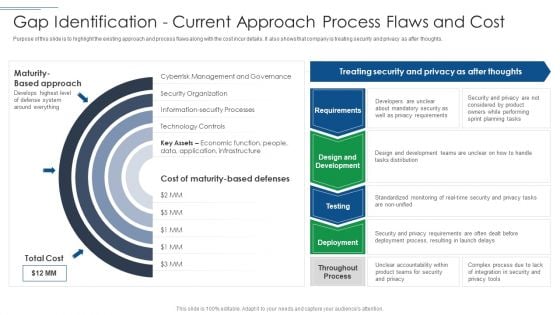
IT Security Risk Management Approach Introduction Gap Identification Current Approach Formats PDF
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Gap Identification Current Approach Formats PDF. Use them to share invaluable insights on Privacy Requirements, Mandatory Security, Planning Tasks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
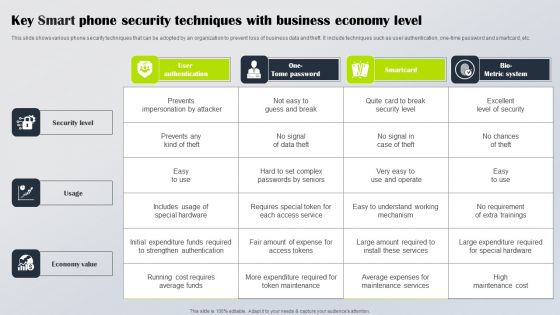
Key Smart Phone Security Techniques With Business Economy Level Brochure PDF
This slide shows various phone security techniques that can be adopted by an organization to prevent loss of business data and theft. It include techniques such as user authentication, one-time password and smartcard, etc. Showcasing this set of slides titled Key Smart Phone Security Techniques With Business Economy Level Brochure PDF. The topics addressed in these templates are Security Level, Usage, Economy Value. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Threat Scanning For IT Security Ppt PowerPoint Presentation Gallery Smartart PDF
Presenting this set of slides with name threat scanning for it security ppt powerpoint presentation gallery smartart pdf. This is a three stage process. The stages in this process are threat scanning for it security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Professional Showing Online Security System Model Ppt PowerPoint Presentation Model Graphic Tips PDF
Presenting this set of slides with name it professional showing online security system model ppt powerpoint presentation model graphic tips pdf. This is a one stage process. The stage in this process is it professional showing online security system model. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
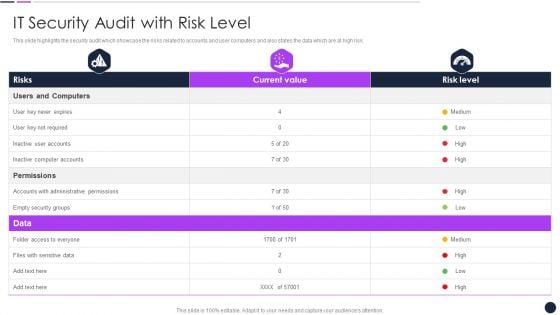
Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF
Deliver an awe inspiring pitch with this creative Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF bundle. Topics like Inactive Computer, Administrative Permissions, Security Groups can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
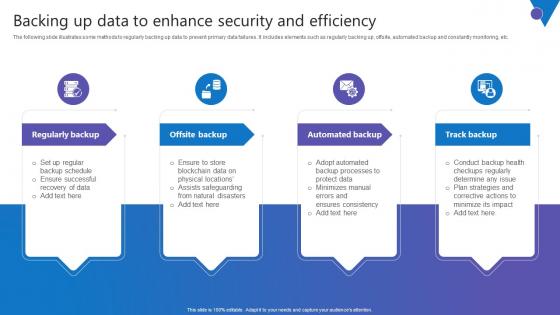
Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf
The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf. The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc.


 Continue with Email
Continue with Email

 Home
Home


































