Information Security
Benefit Of Block Chain Technology For Securing Confidential Data Icon Topics PDF
Presenting Benefit Of Block Chain Technology For Securing Confidential Data Icon Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Benefit Of Block Chain, Technology For Securing, Confidential Data Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
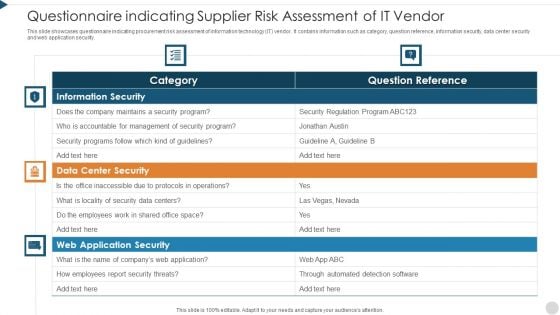
Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
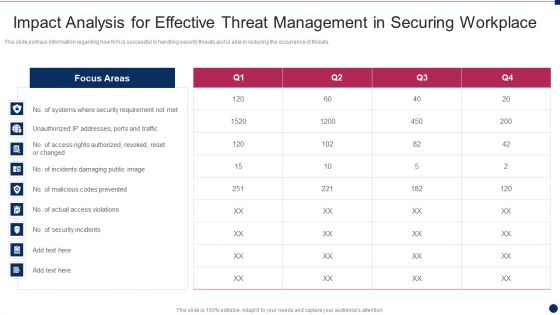
Threat Management At Workplace Impact Analysis For Effective Threat Management In Securing Structure PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative threat management at workplace impact analysis for effective threat management in securing structure pdf bundle. Topics like security incidents, incidents damaging public image, actual access violations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
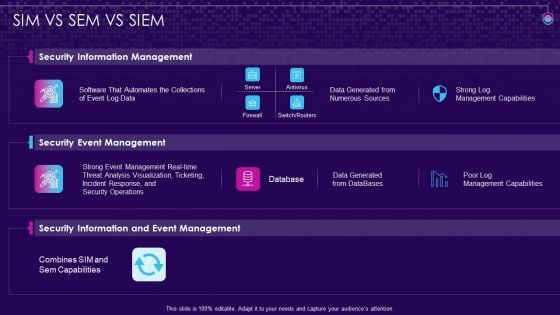
SIM VS SEM VS SIEM SIEM Services Ppt Show Slides PDF
Deliver and pitch your topic in the best possible manner with this sim vs sem vs siem siem services ppt show slides pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
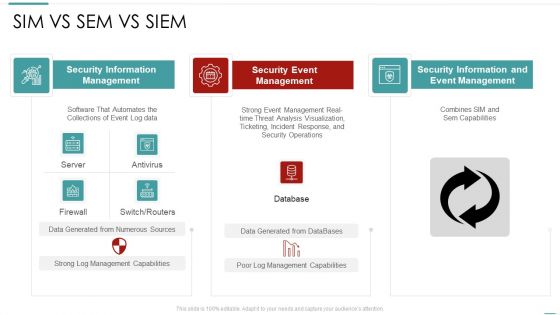
Risk Recognition Automation Sim Vs Sem Vs Siem Ppt Professional Background Designs PDF
Deliver and pitch your topic in the best possible manner with this risk recognition automation sim vs sem vs siem ppt professional background designs pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Secure Password Management Best Password Application In Powerpoint And Google Slides Cpb
Introducing our well-designed Secure Password Management Best Password Application In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Secure Password Management Best Password Application. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Secure Password Management Best Password Application In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
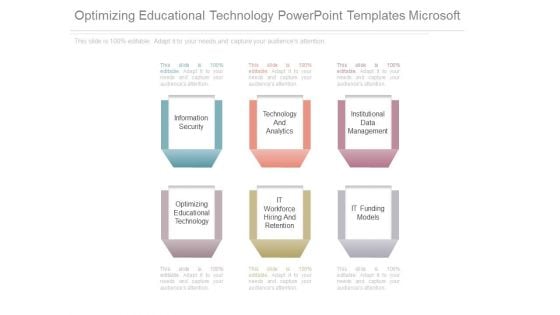
Optimizing Educational Technology Powerpoint Templates Microsoft
This is a optimizing educational technology powerpoint templates microsoft. This is a six stage process. The stages in this process are information security, technology and analytics, institutional data management, optimizing educational technology, it workforce hiring and retention, it funding models.
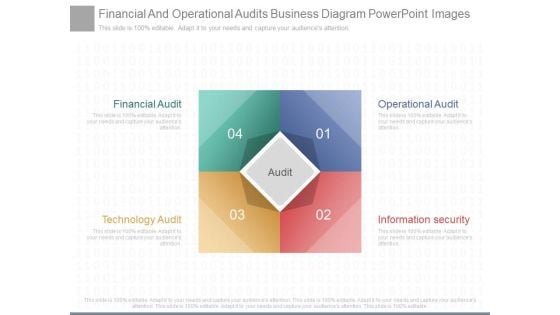
Financial And Operational Audits Business Diagram Powerpoint Images
This is a financial and operational audits business diagram powerpoint images. This is a four stage process. The stages in this process are financial audit, technology audit, operational audit, information security, audit.
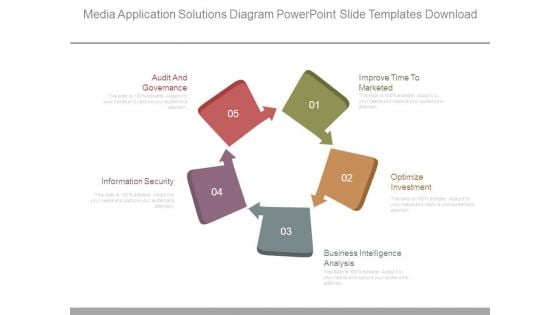
Media Application Solutions Diagram Powerpoint Slide Templates Download
This is a media application solutions diagram powerpoint slide templates download. This is a five stage process. The stages in this process are audit and governance, information security, improve time to marketed, optimize investment, business intelligence analysis.

Administration Assessment Example Sample Ppt Files
This is a administration assessment example sample ppt files. This is a six stage process. The stages in this process are aims and objective, implementation, feasibility, consultancy, solutions, audit and testing, information security.
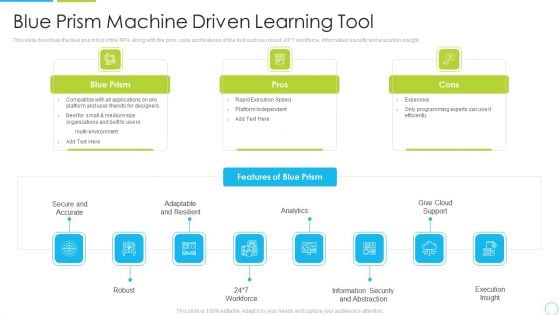
Blue Prism Machine Driven Learning Tool Ppt Show Structure PDF
This slide describes the blue prism tool of the RPA along with the pros, cons and features of the tool such as robust, 24 7 workforce, information security and execution insight. This is a blue prism machine driven learning tool ppt show structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secure, analytics, information, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
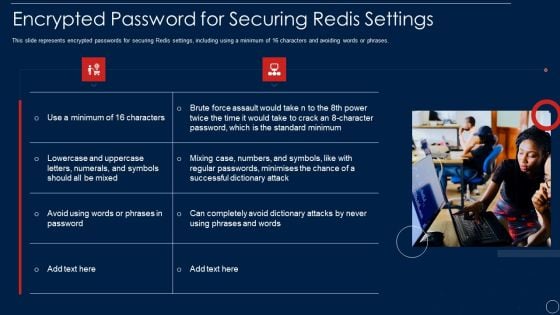
Redis Cache Data Structure IT Encrypted Password For Securing Redis Settings Formats PDF
This slide represents encrypted passwords for securing Redis settings, including using a minimum of 16 characters and avoiding words or phrases. This is a redis cache data structure it encrypted password for securing redis settings formats pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypted password for securing redis settings. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
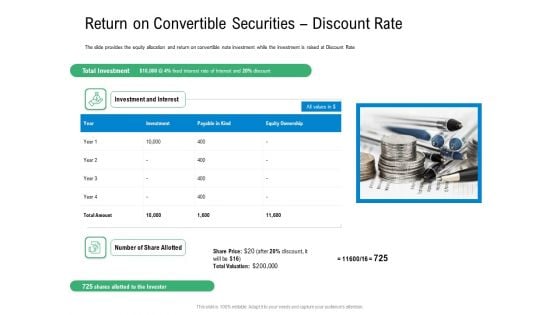
Convertible Preferred Stock Funding Pitch Deck Return On Convertible Securities Discount Rate Portrait PDF
The slide provides the equity allocation and return on convertible note investment while the investment is raised at Discount Rate. This is a convertible preferred stock funding pitch deck return on convertible securities discount rate portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like return on convertible securities discount rate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Secure Email Technology PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Technology PowerPoint Templates because Your audience will believe you are the cats whiskers. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Present our Communication PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download and present our Signs PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Illustration of envelope and email sign protect with padloc, security, communication, technology, business, signs. The prominent colors used in the PowerPoint template are Red, Gray, Yellow. Deal a decisive blow with our Secure Email Technology PowerPoint Templates Ppt Backgrounds For Slides 0413. Get clearlyahead in a critical event.
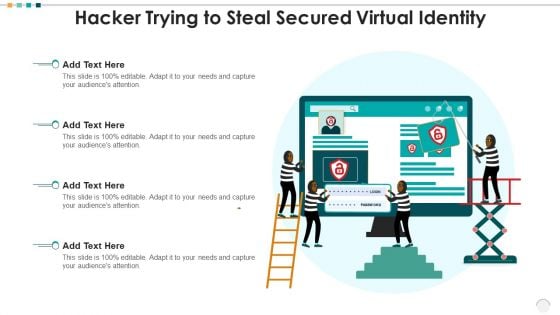
Hacker Trying To Steal Secured Virtual Identity Sample PDF
Persuade your audience using this hacker trying to steal secured virtual identity sample pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including hacker trying to steal secured virtual identity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
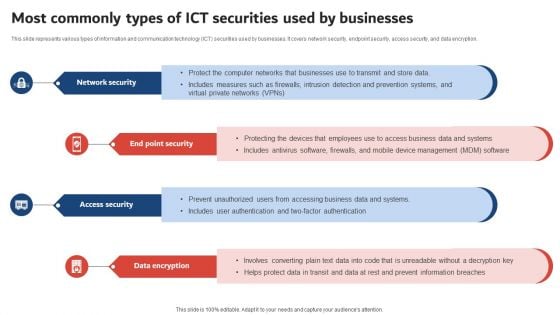
Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF
This slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Secure Your Money PowerPoint Templates Ppt Backgrounds For Slides 0413
Our Secure Your Money PowerPoint Templates PPT Backgrounds For Slides 0413 allow you to do it with ease. Just like picking the low hanging fruit. Boil the ocean with your thoughts. Our Secure Your Money PowerPoint Templates PPT Backgrounds For Slides 0413 will help create waves. Communicate goals with our Secure Your Money PowerPoint Templates Ppt Backgrounds For Slides 0413. Download without worries with our money back guaranteee.

Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a lock padlock intersecting it List your core competencies with our Secure Internet Browser Computer PowerPoint Templates And PowerPoint Backgrounds 0811. They will make you look good.

Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with transparent internet browser with a lock padlock intersecting it Our Secure Internet Browser Computer PowerPoint Themes And PowerPoint Slides 0811 have amazing characteristics. They educate and entertain on your command.
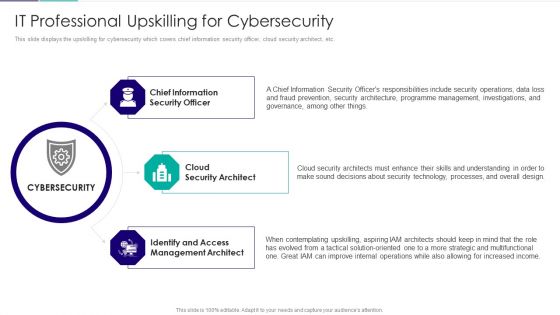
Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc.Presenting Role Of Technical Competence In Organizational It Professional Upskilling Inspiration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Chief Information Security, Cloud Security Architect, Identify And Access Management Architect In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
SIEM Sim Vs Sem Vs SIEM Ppt Icon Format Ideas PDF
This is a siem sim vs sem vs siem ppt icon format ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information management, security event management, security information and event management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
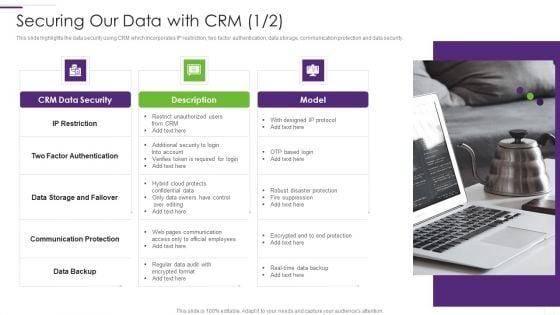
CRM Implementation Strategy Securing Our Data With CRM Summary PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security.This is a CRM Implementation Strategy Securing Our Data With CRM Summary PDF template with various stages. Focus and dispense information on One stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Factor Authentication, Communication Protection, Restrict Unauthorized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
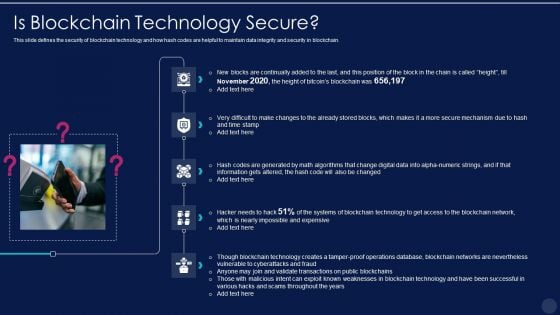
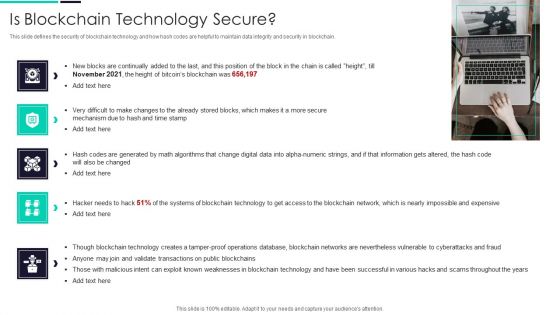
Blockchain Technology Framework IT Is Blockchain Technology Secure Demonstration PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a blockchain technology framework it is blockchain technology secure demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like expensive, systems, blockchain network, operations database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a Blockchain And DLT Framework Is Blockchain Technology Secure Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Time Stamp, Blockchain Technology, Weaknesses. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
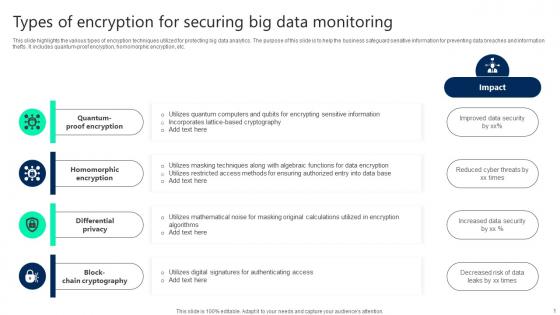
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc.

Role IT Team Digital Transformation It Professional Upskilling For Cybersecurity Introduction PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a role it team digital transformation it professional upskilling for cybersecurity introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information, security, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
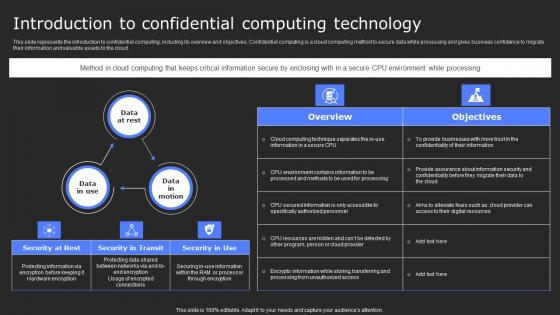
Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
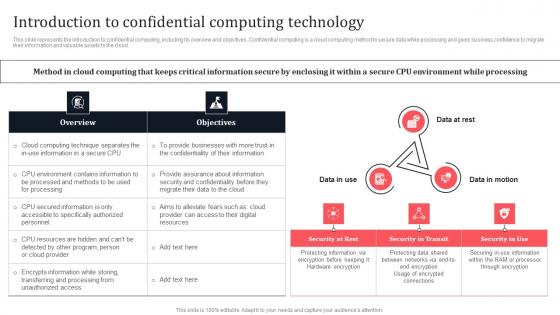
Introduction To Confidential Computing Technology Secure Multi Party Download Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Do you know about Slidesgeeks Introduction To Confidential Computing Technology Secure Multi Party Download Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.
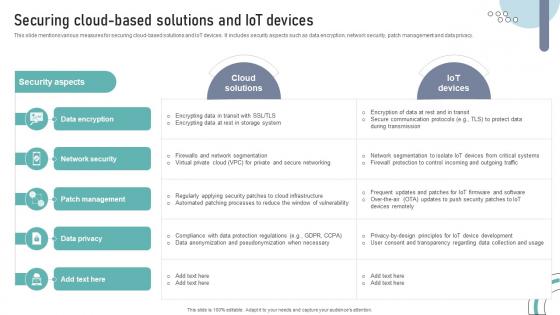
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy.
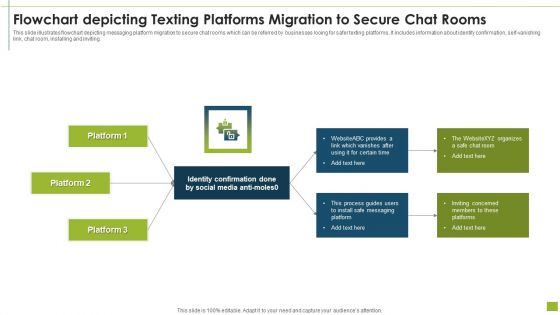
Flowchart Depicting Texting Platforms Migration To Secure Chat Rooms Inspiration PDF
This slide illustrates flowchart depicting messaging platform migration to secure chat rooms which can be referred by businesses looing for safer texting platforms. It includes information about identity confirmation, self-vanishing link, chat room, installing and inviting.Pitch your topic with ease and precision using this flowchart depicting texting platforms migration to secure chat rooms inspiration pdf This layout presents information on identity confirmation, process guides, install safe messaging It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
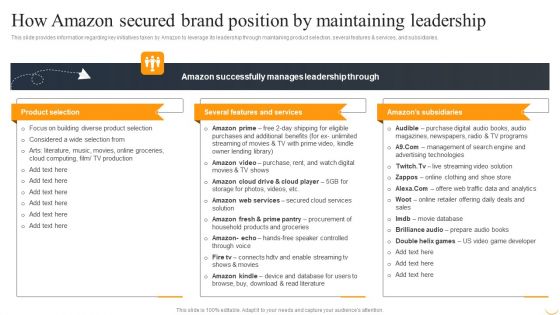
How Amazon Secured Brand Position By Maintaining Leadership Designs PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Get a simple yet stunning designed How Amazon Secured Brand Position By Maintaining Leadership Designs PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Amazon Secured Brand Position By Maintaining Leadership Designs PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. This Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc.
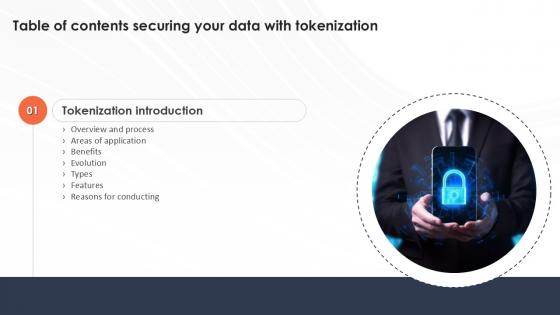
Securing Your Data With Tokenization Table Of Contents Ppt Sample
Want to ace your presentation in front of a live audience Our Securing Your Data With Tokenization Table Of Contents Ppt Sample can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. Our Securing Your Data With Tokenization Table Of Contents Ppt Sample are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
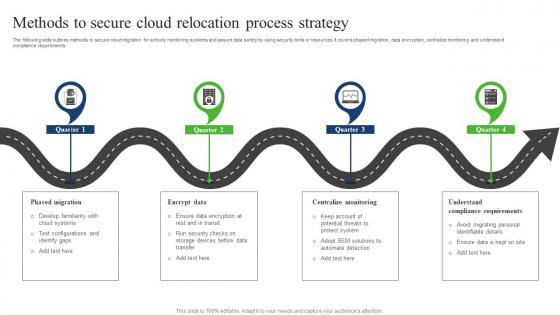
Methods To Secure Cloud Relocation Process Strategy Sample Pdf
The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements. Showcasing this set of slides titled Methods To Secure Cloud Relocation Process Strategy Sample Pdf. The topics addressed in these templates are Centralize Monitoring, Understand Compliance Requirements, Phased Migration, Encrypt Data . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide outlines methods to secure cloud migration for actively monitoring systems and assure data safety by using security tools or resources. It covers phased migration, data encryption, centralize monitoring and understand compliance requirements.
Icons Slide For Securing Your Data With Tokenization Ppt Slide
Download our innovative and attention grabbing Icons Slide For Securing Your Data With Tokenization Ppt Slide template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Securing Your Data With Tokenization Ppt Slide are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
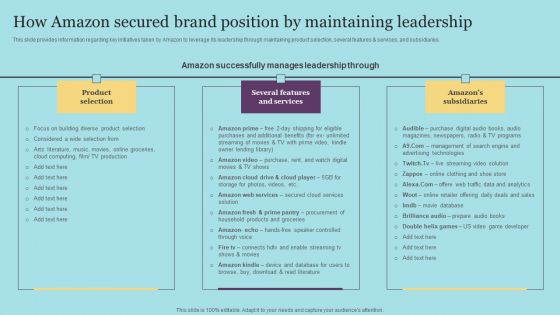
How Amazon Secured Brand Position By Maintaining Leadership Download PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. This modern and well-arranged How Amazon Secured Brand Position By Maintaining Leadership Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
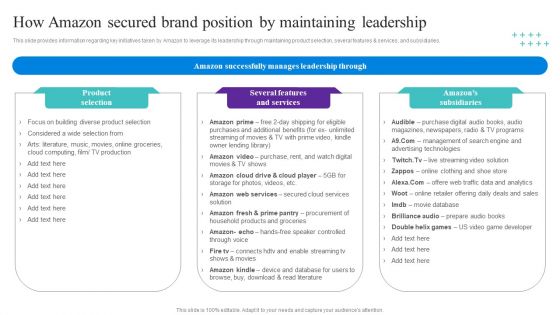
How Amazon Secured Brand Position By Maintaining Leadership Topics PDF
Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf
Showcasing this set of slides titled Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf. The topics addressed in these templates are Encryption Techniques, IconSecuring, Big Data Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Encryption Techniques Icon For Securing Big Data Monitoring Mockup pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Securing Your Data with Tokenization Powerpoint Presentation Slides PPT Example
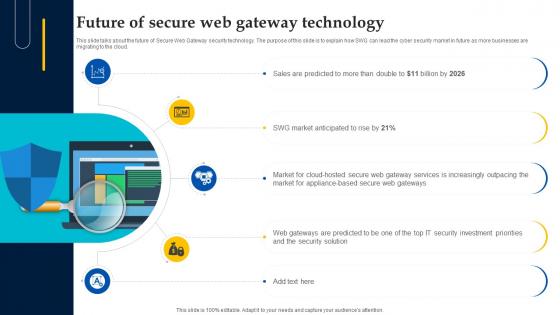
Web Access Control Solution Future Of Secure Web Gateway Technology
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. This modern and well-arranged Web Access Control Solution Future Of Secure Web Gateway Technology provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.

Secure Web Gateway Architecture And Working Web Threat Protection System
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. This Secure Web Gateway Architecture And Working Web Threat Protection System from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.
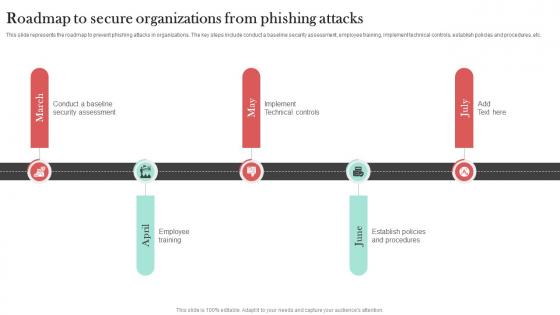
Roadmap To Secure Organizations Man In The Middle Phishing IT
This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roadmap To Secure Organizations Man In The Middle Phishing IT and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.
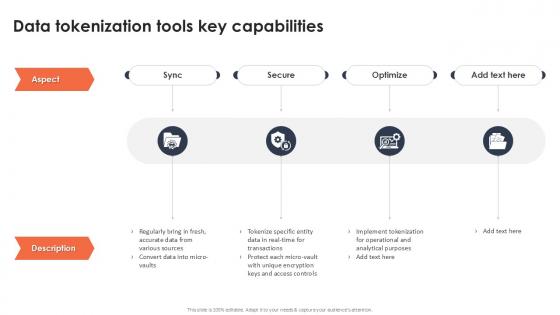
Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint
If you are looking for a format to display your unique thoughts, then the professionally designed Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Our Data Tokenization Tools Key Capabilities Securing Your Data Ppt Powerpoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
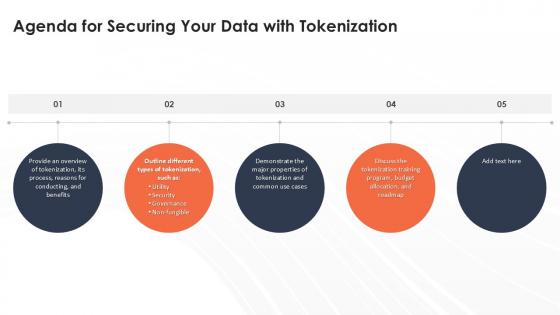
Agenda For Securing Your Data With Tokenization Ppt Template
Create an editable Agenda For Securing Your Data With Tokenization Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Securing Your Data With Tokenization Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Our Agenda For Securing Your Data With Tokenization Ppt Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
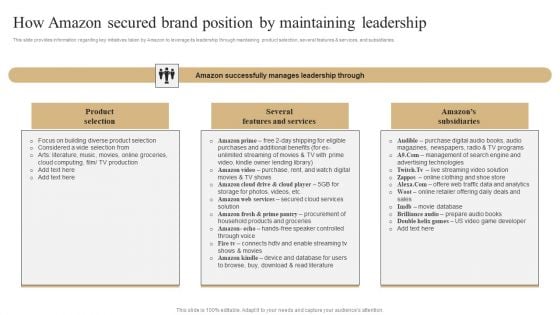
How Amazon Secured Brand Position By Maintaining Leadership Slides PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. If you are looking for a format to display your unique thoughts, then the professionally designed How Amazon Secured Brand Position By Maintaining Leadership Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download How Amazon Secured Brand Position By Maintaining Leadership Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
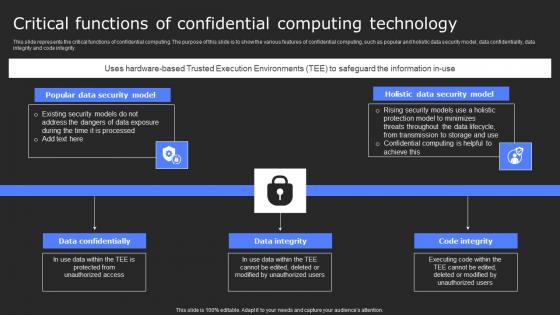
Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf
This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Are you searching for a Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Critical Functions Of Confidential Computing Secure Computing Framework Microsoft Pdf from Slidegeeks today. This slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity.
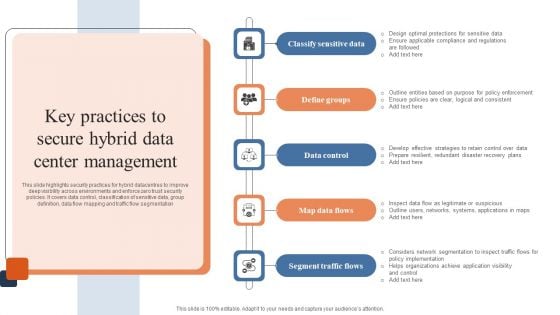
Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Deliver an awe inspiring pitch with this creative Cryptocurrency Ledger Is Blockchain Technology Secure Slides PDF bundle. Topics like Digital Data, Blockchain Networks, Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
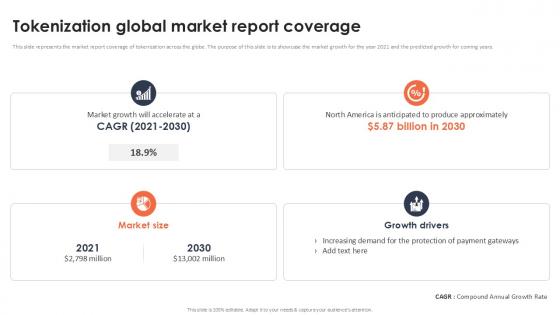
Tokenization Global Market Report Coverage Securing Your Data Ppt Slide
This slide represents the market report coverage of tokenization across the globe. The purpose of this slide is to showcase the market growth for the year 2021 and the predicted growth for coming years. Present like a pro with Tokenization Global Market Report Coverage Securing Your Data Ppt Slide Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the market report coverage of tokenization across the globe. The purpose of this slide is to showcase the market growth for the year 2021 and the predicted growth for coming years.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
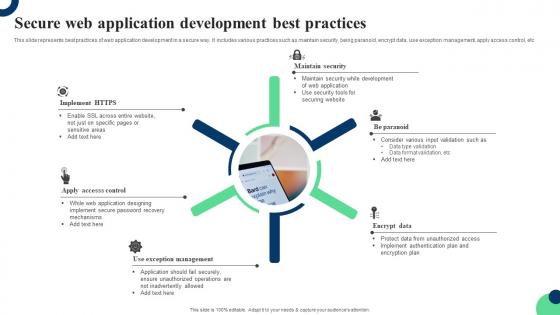
Secure Web Application Development Best Practices Ppt Inspiration Outline Pdf
This slide represents best practices of web application development in a secure way. It includes various practices such as maintain security, being paranoid, encrypt data, use exception management, apply access control, etc. Showcasing this set of slides titled Secure Web Application Development Best Practices Ppt Inspiration Outline Pdf. The topics addressed in these templates are Being Paranoid, Encrypt Data, Use Exception Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents best practices of web application development in a secure way. It includes various practices such as maintain security, being paranoid, encrypt data, use exception management, apply access control, etc.

Secure Computing Framework Table Of Contents Inspiration Pdf
Boost your pitch with our creative Secure Computing Framework Table Of Contents Inspiration Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Secure Computing Framework Table Of Contents Inspiration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
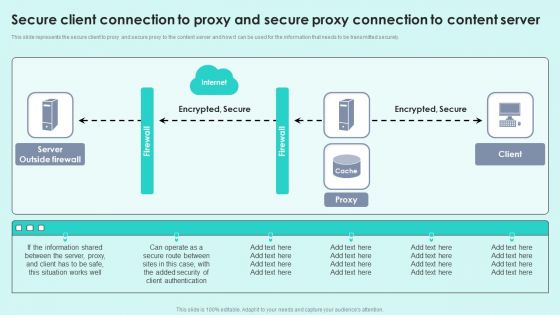
Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely.Deliver and pitch your topic in the best possible manner with this Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF. Use them to share invaluable insights on Server Outside, Between Server, Situation Works and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
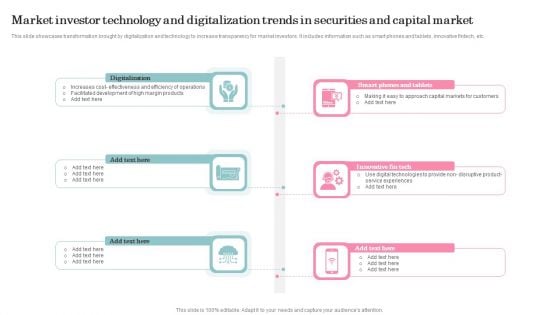
Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF
This slide showcases transformation brought by digitalization and technology to increase transparency for market investors. It includes information such as smart phones and tablets, innovative fintech, etc. Presenting Market Investor Technology And Digitalization Trends In Securities And Capital Market Structure PDF to dispense important information. This template comprises Six stages. It also presents valuable insights into the topics including Digitalization, Innovative Fin Tech. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
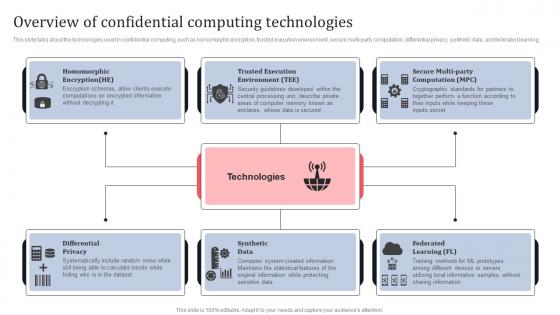
Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Get a simple yet stunning designed Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
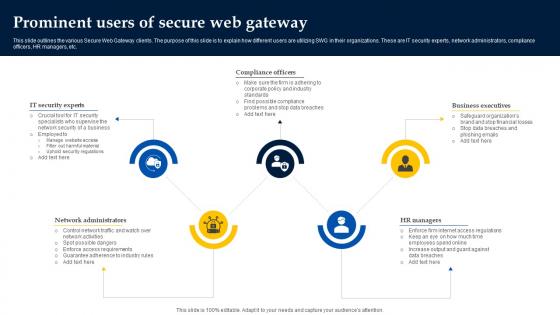
Web Access Control Solution Prominent Users Of Secure Web Gateway
Do you know about Slidesgeeks Web Access Control Solution Prominent Users Of Secure Web Gateway These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.

DLT Technology Is Blockchain Technology Secure Pictures PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download DLT Technology Is Blockchain Technology Secure Pictures PDF from Slidegeeks and deliver a wonderful presentation.


 Continue with Email
Continue with Email

 Home
Home


































