Information Security

30 60 90 Days Plan To Implement Tokenization Securing Your Data Ppt Example
This slide depicts the 30 60 90 days plan for implementing tokenization. The plan includes the activities and goals such as assessment, planning, selecting tokenization solutions, etc. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Tokenization Securing Your Data Ppt Example The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide depicts the 30 60 90 days plan for implementing tokenization. The plan includes the activities and goals such as assessment, planning, selecting tokenization solutions, etc.
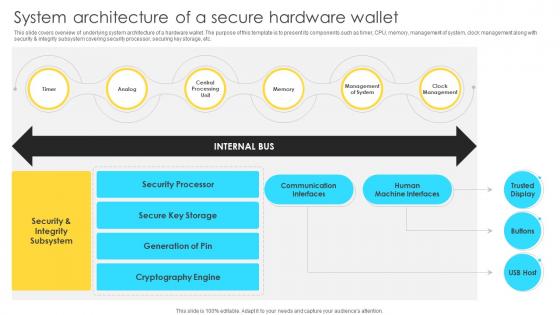
Mastering Blockchain Wallets System Architecture Of A Secure Hardware Wallet BCT SS V
This slide covers overview of underlying system architecture of a hardware wallet. The purpose of this template is to present its components such as timer, CPU, memory, management of system, clock management along with security and integrity subsystem covering security processor, securing key storage, etc. Welcome to our selection of the Mastering Blockchain Wallets System Architecture Of A Secure Hardware Wallet BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers overview of underlying system architecture of a hardware wallet. The purpose of this template is to present its components such as timer, CPU, memory, management of system, clock management along with security and integrity subsystem covering security processor, securing key storage, etc.

Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Get a simple yet stunning designed Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comparison Between ZTNA And Secure Access Service Edge Zero Trust Network Access can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
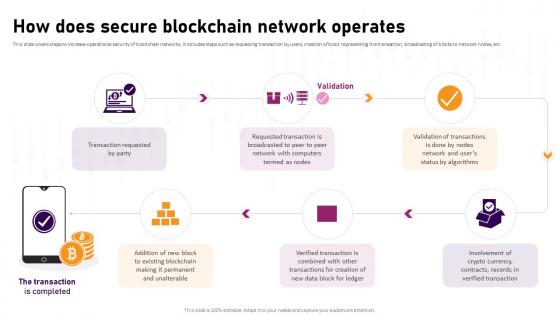
How Does Secure Blockchain Network Operates Complete Roadmap To Blockchain BCT SS V
This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc. Retrieve professionally designed How Does Secure Blockchain Network Operates Complete Roadmap To Blockchain BCT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide covers steps to increase operational security of blockchain networks. It includes steps such as requesting transaction by users, creation of block representing the transaction, broadcasting of blocks to network nodes, etc.

Reasons Behind Need For Secure Web Gateway Web Threat Protection System
This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc. Slidegeeks has constructed Reasons Behind Need For Secure Web Gateway Web Threat Protection System after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc.
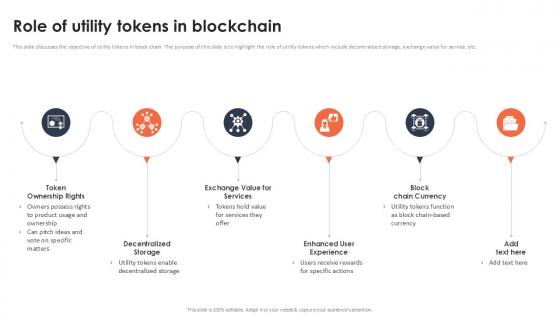
Role Of Utility Tokens In Blockchain Securing Your Data Ppt Presentation
This slide discusses the objective of utility tokens in block chain. The purpose of this slide is to highlight the role of utility tokens which include decentralized storage, exchange value for service, etc. Create an editable Role Of Utility Tokens In Blockchain Securing Your Data Ppt Presentation that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Role Of Utility Tokens In Blockchain Securing Your Data Ppt Presentation is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide discusses the objective of utility tokens in block chain. The purpose of this slide is to highlight the role of utility tokens which include decentralized storage, exchange value for service, etc.

Global Market Analysis Of Secure Web Gateway Web Threat Protection System
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. If you are looking for a format to display your unique thoughts, then the professionally designed Global Market Analysis Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Market Analysis Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.

For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf
Are you searching for a For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf from Slidegeeks today. Our For Secure Multi Party Computation SMPC Table Of Contents Diagrams Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
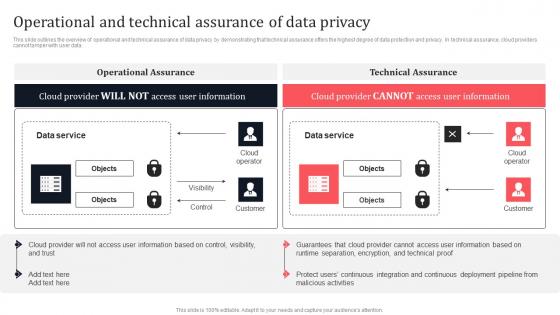
Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. There are so many reasons you need a Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.

Comparison Between Secure Web Gateway And Firewalls Web Access Control Solution
This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Web Access Control Solution Comparison Between Secure Web Gateway And Firewalls and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Web Access Control Solution Comparison Between Secure Web Gateway And Firewalls and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
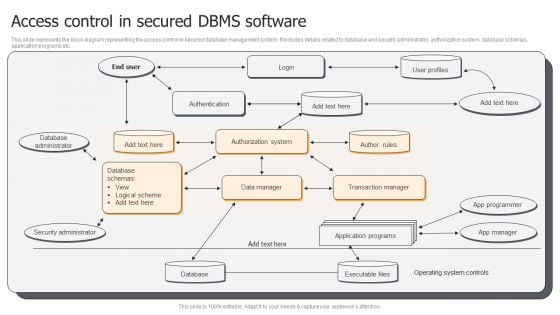
Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF
This slide represents the block diagram representing the access control in secured database management system. It includes details related to database and security administrator, authorization system, database schemas, application programs etc. Presenting Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Database Administrator, Security Administrator, Database, Application Programs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
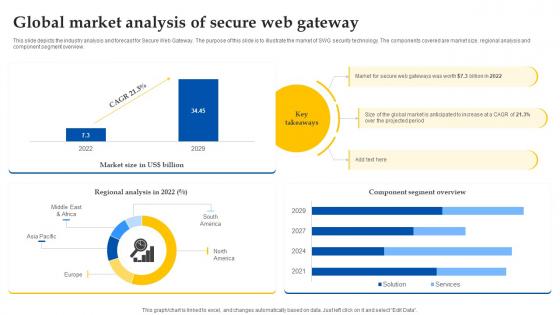
Web Access Control Solution Global Market Analysis Of Secure Web Gateway
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. This Web Access Control Solution Global Market Analysis Of Secure Web Gateway is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Web Access Control Solution Global Market Analysis Of Secure Web Gateway features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.
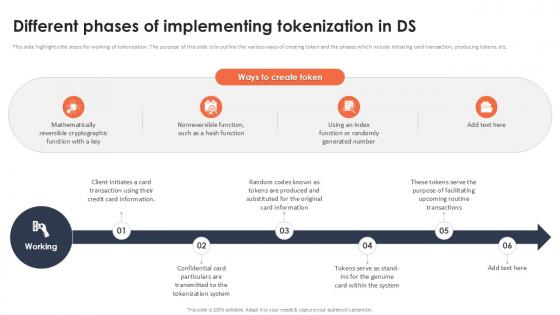
Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation
This slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc.
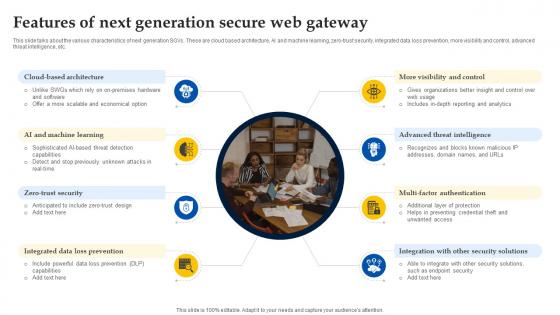
Web Access Control Solution Features Of Next Generation Secure Web Gateway
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Access Control Solution Features Of Next Generation Secure Web Gateway to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc.

Is Blockchain Technology Secure Involving Cryptographic Ledger To Enhance Structure PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Is Blockchain Technology Secure Involving Cryptographic Ledger To Enhance Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Is Blockchain Technology Secure Involving Cryptographic Ledger To Enhance Structure PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
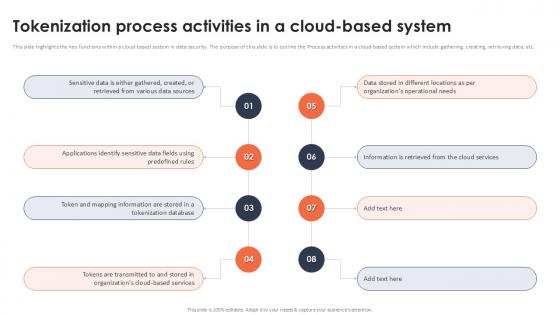
Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint
This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Tokenization Process Activities In A Cloud Based System Securing Your Data Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the key functions within a cloud-based system in data security. The purpose of this slide is to outline the Process activities in a cloud-based system which include gathering, creating, retrieving data, etc.
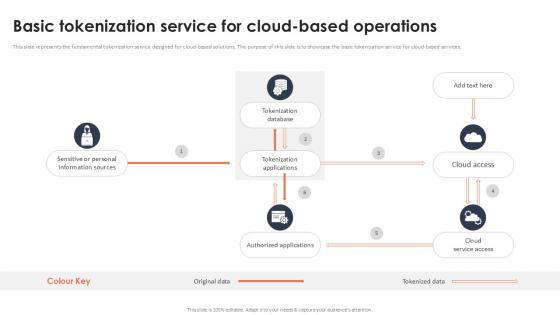
Basic Tokenization Service For Cloud Based Operations Securing Your Data Ppt Presentation
This slide represents the fundamental tokenization service designed for cloud-based solutions. The purpose of this slide is to showcase the basic tokenization service for cloud-based services. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Basic Tokenization Service For Cloud Based Operations Securing Your Data Ppt Presentation for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the fundamental tokenization service designed for cloud-based solutions. The purpose of this slide is to showcase the basic tokenization service for cloud-based services.
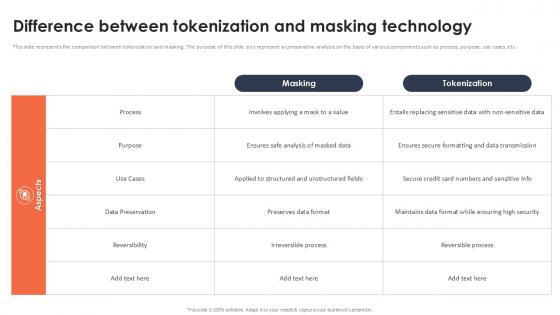
Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint
This slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc.

Introduction To Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. This modern and well-arranged Introduction To Next Generation Secure Web Gateway Web Threat Protection System provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.

Importance Of Secure Ecommerce Evaluation And Deployment Of Enhanced Portrait Pdf
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. Welcome to our selection of the Importance Of Secure Ecommerce Evaluation And Deployment Of Enhanced Portrait Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today. This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc.

Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V
This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Best Practices To Secure And Use Paper Wallets BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers tips to increase security of paper wallets for using it effectively. The purpose of this template is to provide recommendations such as using reputable tools or websites, encrypting private keys with strong passphrase, creating multiple copies of paper wallets, testing and verifying paper wallet, etc.
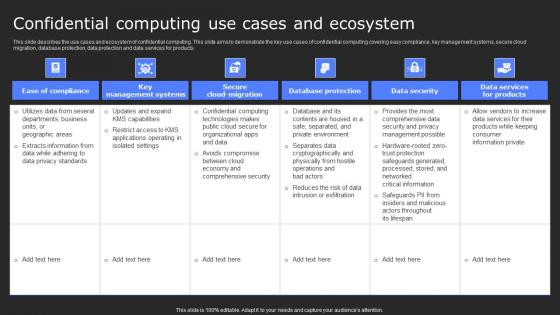
Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. The Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
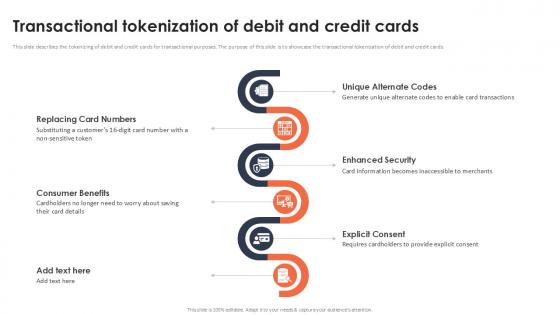
Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide
This slide describes the tokenizing of debit and credit cards for transactional purposes. The purpose of this slide is to showcase the transactional tokenization of debit and credit cards. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide describes the tokenizing of debit and credit cards for transactional purposes. The purpose of this slide is to showcase the transactional tokenization of debit and credit cards.
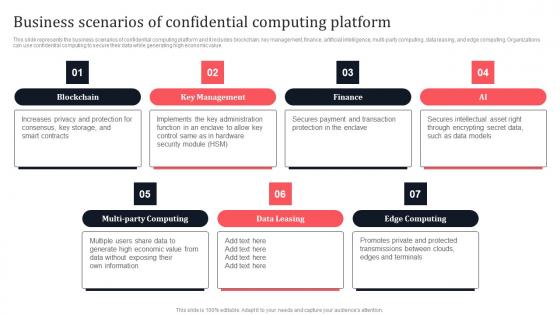
Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Boost your pitch with our creative Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
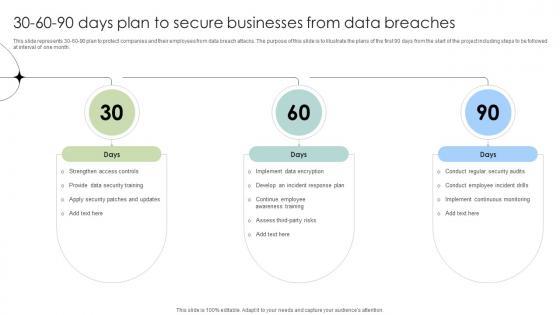
30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breaches Data Fortification Strengthening Defenses. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.
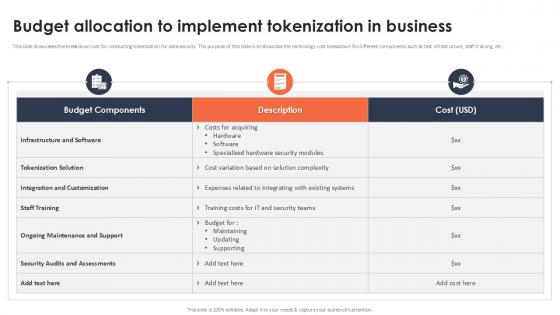
Budget Allocation To Implement Tokenization In Business Securing Your Data Ppt Example
This slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Budget Allocation To Implement Tokenization In Business Securing Your Data Ppt Example a try. Our experts have put a lot of knowledge and effort into creating this impeccable Budget Allocation To Implement Tokenization In Business Securing Your Data Ppt Example You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc.

Web Access Control Solution Key Benefits Of Using Secure Web Gateway
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Slidegeeks has constructed Web Access Control Solution Key Benefits Of Using Secure Web Gateway after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc.
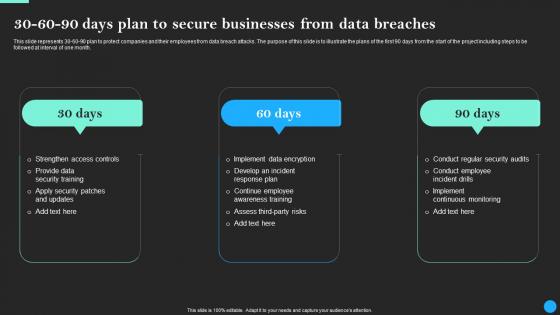
30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf
This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Businesses From Data Breach Prevention Portrait Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.

Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf
Find highly impressive Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. Our Table Of Contents For Secure Multi Party Computation SMPC Elements Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
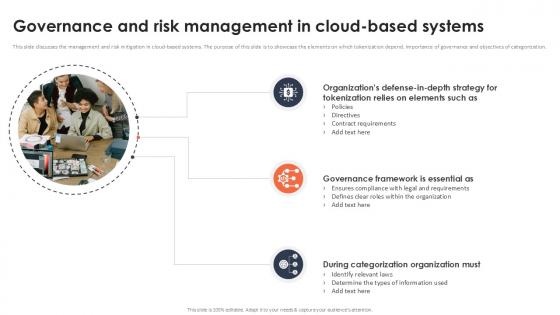
Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. This modern and well-arranged Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization.
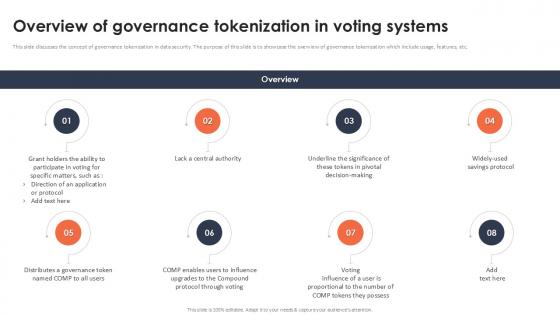
Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint
This slide discusses the concept of governance tokenization in data security. The purpose of this slide is to showcase the overview of governance tokenization which include usage, features, etc. Presenting this PowerPoint presentation, titled Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Overview Of Governance Tokenization In Voting Systems Securing Your Data Ppt Powerpoint that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide discusses the concept of governance tokenization in data security. The purpose of this slide is to showcase the overview of governance tokenization which include usage, features, etc.

Key Benefits Of Using Secure Web Gateway Web Threat Protection System
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Welcome to our selection of the Key Benefits Of Using Secure Web Gateway Web Threat Protection System. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc.
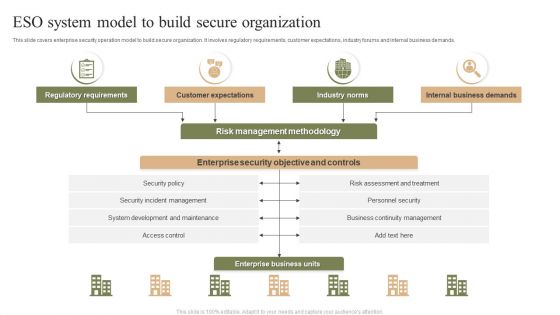
ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF
This slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Showcasing this set of slides titled ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF. The topics addressed in these templates are Customer Expectations, Industry Norms, Internal Business Demands. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
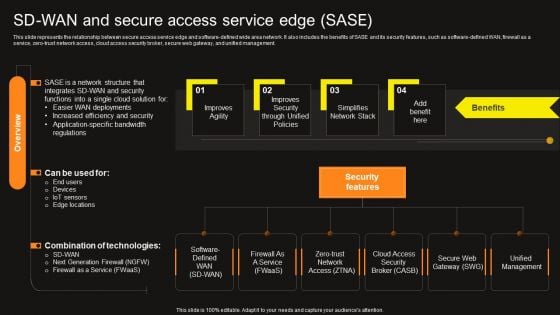
Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF
This slide represents the relationship between secure access service edge and software-defined wide area network. It also includes the benefits of SASE and its security features, such as software-defined WAN, firewall as a service, zero-trust network access, cloud access security broker, secure web gateway, and unified management. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Virtual WAN Architecture Sd Wan And Secure Access Service Edge Sase Formats PDF today and make your presentation stand out from the rest.
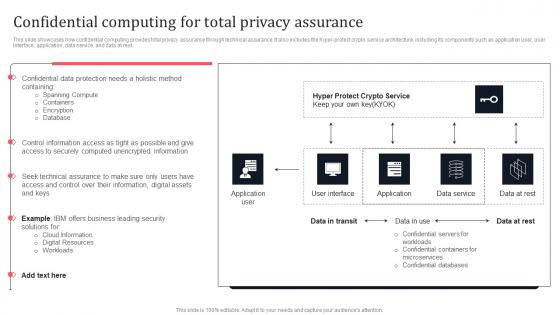
Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
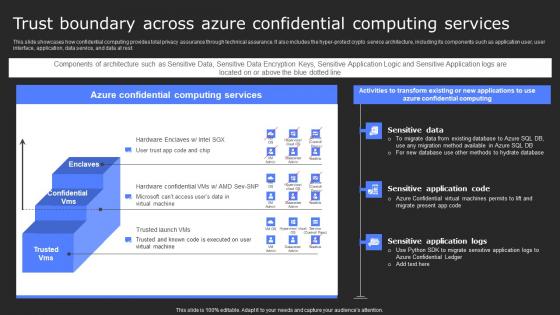
Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.

Features Of Next Generation Secure Web Gateway Web Threat Protection System
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Find highly impressive Features Of Next Generation Secure Web Gateway Web Threat Protection System on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of Next Generation Secure Web Gateway Web Threat Protection System for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc.
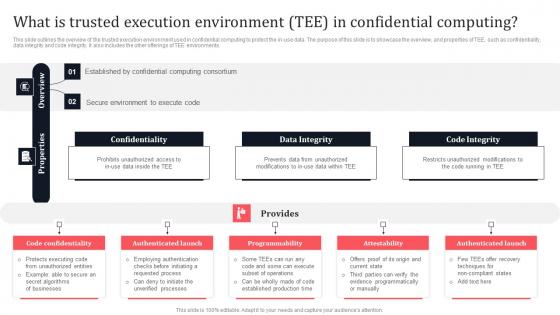
What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.
Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF
This slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Get a simple yet stunning designed Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
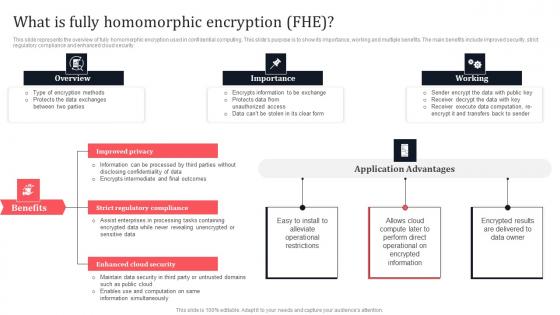
What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Make sure to capture your audiences attention in your business displays with our gratis customizable What Is Fully Homomorphic Encryption FHE Secure Multi Party Graphics Pdf These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.
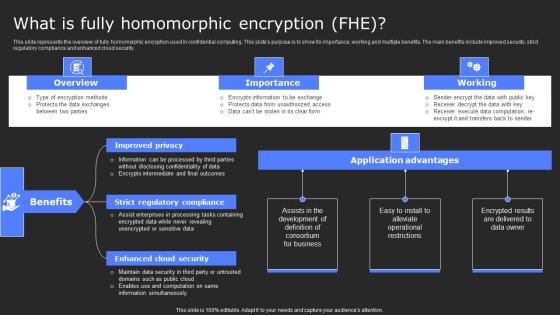
What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. What Is Fully Homomorphic Encryption Fhe Secure Computing Framework Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.
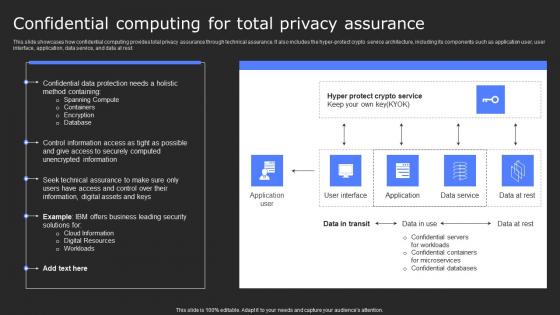
Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.

Tokenization Case Study Comforte Fashion Retailer Securing Your Data Ppt Example
This slide represents the tokenization case study at comforte fashion retailer. The purpose of this slide is to give an overview of the retailer, including the challenges they face and the solutions provided by tokenization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Tokenization Case Study Comforte Fashion Retailer Securing Your Data Ppt Example will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the tokenization case study at comforte fashion retailer. The purpose of this slide is to give an overview of the retailer, including the challenges they face and the solutions provided by tokenization.
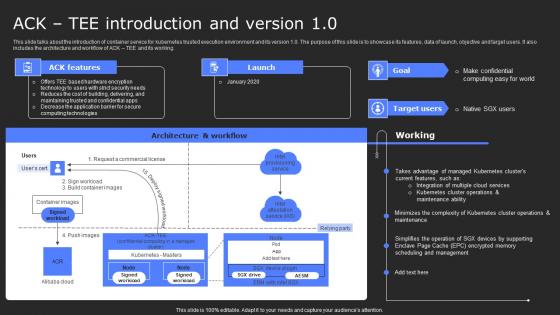
ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf
This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Find a pre-designed and impeccable ACK Tee Introduction And Version 10 Secure Computing Framework Slides Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide talks about the introduction of container service for kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.
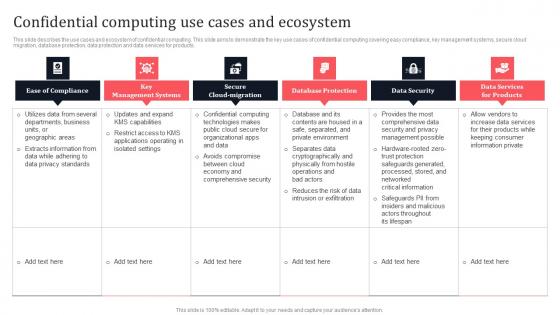
Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Explore a selection of the finest Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.

IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Present like a pro with What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments.

Web Access Control Solution Before Vs After Implementing Secure Web Gateway
This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Web Access Control Solution Before Vs After Implementing Secure Web Gateway. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Web Access Control Solution Before Vs After Implementing Secure Web Gateway today and make your presentation stand out from the rest This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc.
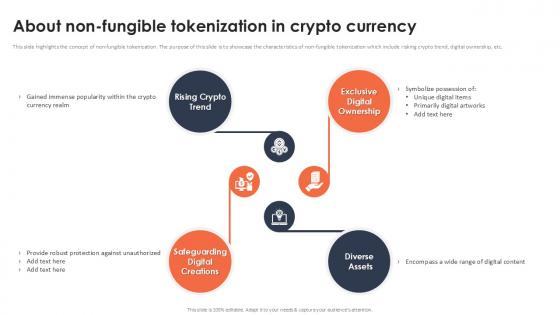
About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide
This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc. Boost your pitch with our creative About Non Fungible Tokenization In Crypto Currency Securing Your Data Ppt Slide Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the concept of non-fungible tokenization. The purpose of this slide is to showcase the characteristics of non-fungible tokenization which include risking crypto trend, digital ownership, etc.

Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint
This slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint from Slidegeeks and deliver a wonderful presentation. This slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc.

Evolution Of Tokenization From Ancient Times To Modern Era Securing Your Data Ppt Powerpoint
This slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Evolution Of Tokenization From Ancient Times To Modern Era Securing Your Data Ppt Powerpoint These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the history of tokenization. The purpose of this slide is to showcase the years of evolution such as 1970s digital tokenization, data compliance in 2001, etc.
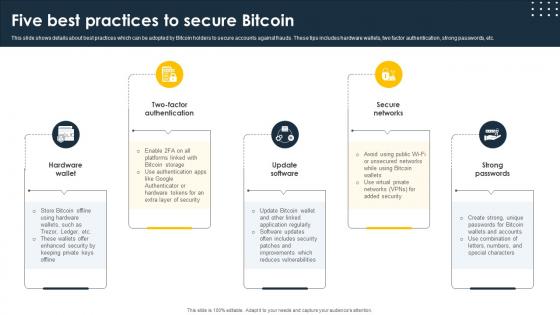
Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V
This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Complete Beginners Guide Five Best Practices To Secure Bitcoin Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc.
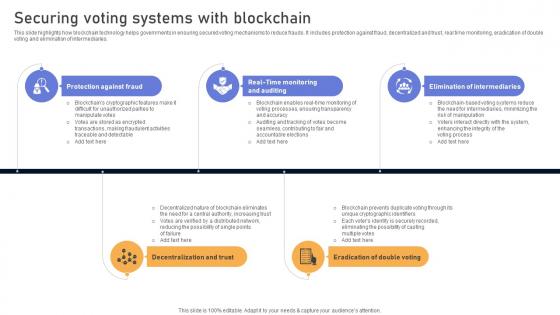
Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. Get a simple yet stunning designed Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries.

Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web Access Control Solution Best Practices For Secure Web Gateway Implementation
This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Web Access Control Solution Best Practices For Secure Web Gateway Implementation can be your best option for delivering a presentation. Represent everything in detail using Web Access Control Solution Best Practices For Secure Web Gateway Implementation and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines various measures to be taken to maintain and enhance the functionality of Secure Web Gateway. The purpose of this slide is to demonstrate best practices for SWG. These are perform a risk assessment, deploy safe setups, monitor and analyse traffic, etc.

Five Best Practices To Secure Everything About Bitcoin PPT Template Fin SS V
This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Five Best Practices To Secure Everything About Bitcoin PPT Template Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide shows details about best practices which can be adopted by Bitcoin holders to secure accounts against frauds. These tips includes hardware wallets, two factor authentication, strong passwords, etc.

Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.
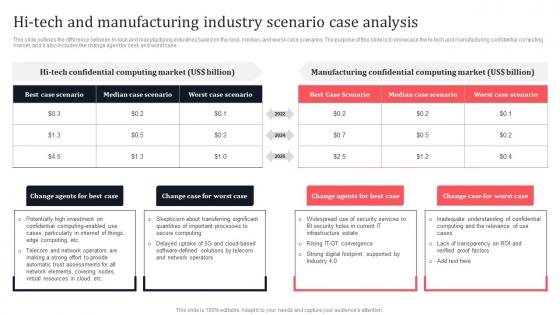
Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Presenting this PowerPoint presentation, titled Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Hi Tech And Manufacturing Industry Scenario Case Analysis Secure Multi Party Graphics Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.
Smart Phone Data Transfer Via Secured Network Image Ppt Show Graphics PDF
Presenting smart phone data transfer via secured network image ppt show graphics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including smart phone data safety application with protection shield. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
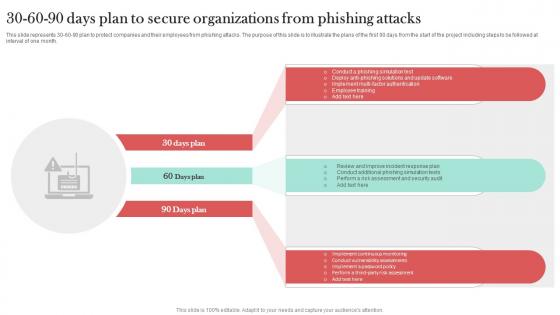
30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT
This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month.


 Continue with Email
Continue with Email

 Home
Home


































