Insider Threat

Safety Breach Response Playbook Checklist To Ensure Asset Protection From Internal Designs PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Are you searching for a Safety Breach Response Playbook Checklist To Ensure Asset Protection From Internal Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Safety Breach Response Playbook Checklist To Ensure Asset Protection From Internal Designs PDF from Slidegeeks today.
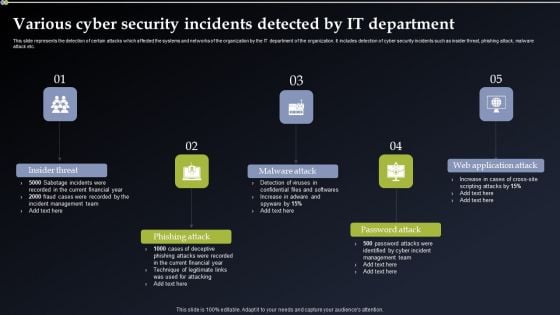
Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you searching for a Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF from Slidegeeks today.
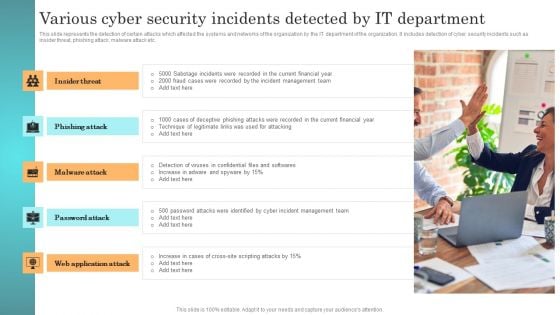
Incident Response Techniques Deployement Various Cyber Security Incidents Detected By IT Department Clipart PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Various Cyber Security Incidents Detected By IT Department Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Various Cyber Security Incidents Detected By IT Department Clipart PDF today and make your presentation stand out from the rest.
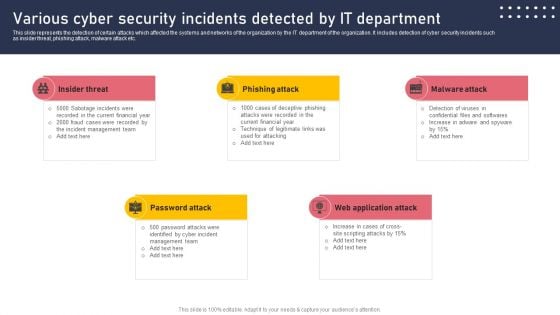
Various Cyber Security Incidents Detected By It Department Sample PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Various Cyber Security Incidents Detected By It Department Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
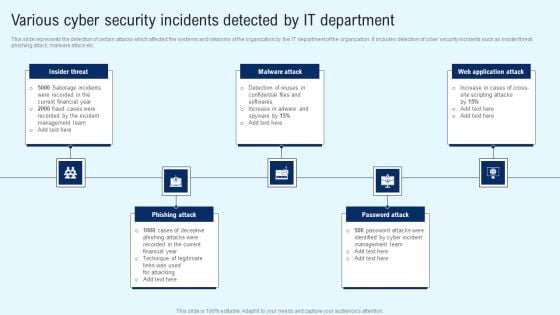
Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Zero Trust Network Access Architecture Overview Icons PDF
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Retrieve professionally designed Zero Trust Network Access Architecture Overview Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
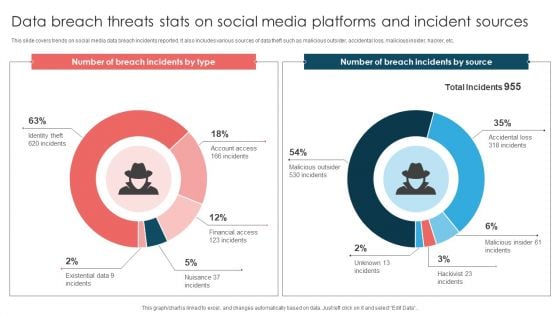
Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF
This slide covers trends on social media data breach incidents reported. It also includes various sources of data theft such as malicious outsider, accidental loss, malicious insider, hacker, etc. Pitch your topic with ease and precision using this Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF. This layout presents information on Number Breach, Total Incidents, Malicious Insider. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Risk Management For Organization Essential Assets Addressing Various Ways To Handle Icons PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting risk management for organization essential assets addressing various ways to handle icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
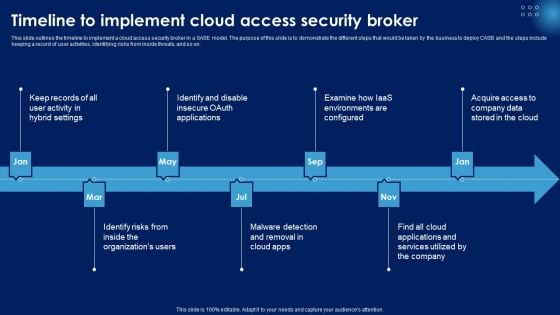
Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Styles PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Risk Management For Organization Essential Assets Ensuring Collaboration Among Various Slides PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting risk management for organization essential assets ensuring collaboration among various slides pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like procurement, finance, legal, public relations, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
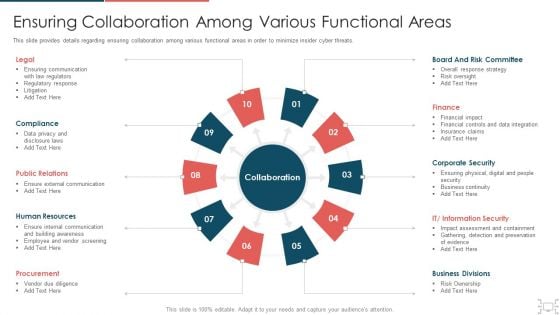
cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
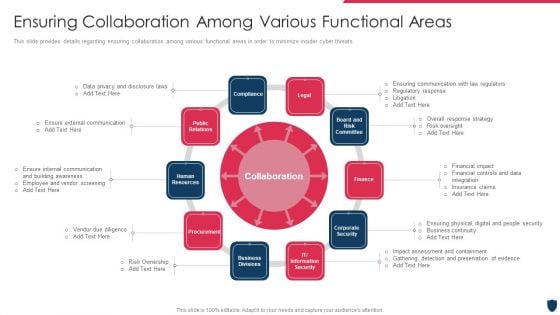
Cyber Safety Incident Management Ensuring Collaboration Among Various Functional Areas Themes PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber safety incident management ensuring collaboration among various functional areas themes pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like legal, finance, procurement, public relations, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
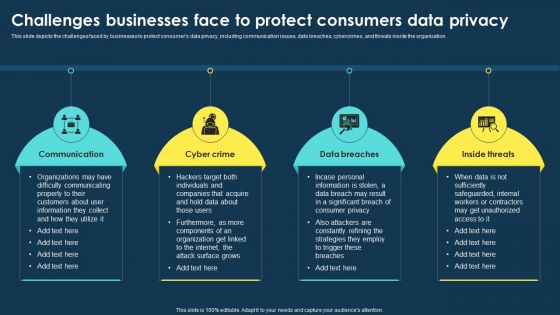
Integrating Data Privacy System Challenges Businesses Face To Protect Consumers Ppt Portfolio Influencers PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Integrating Data Privacy System Challenges Businesses Face To Protect Consumers Ppt Portfolio Influencers PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
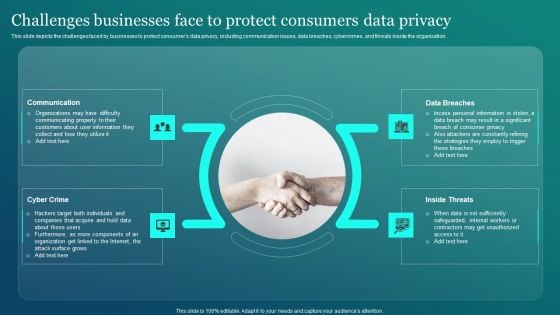
Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
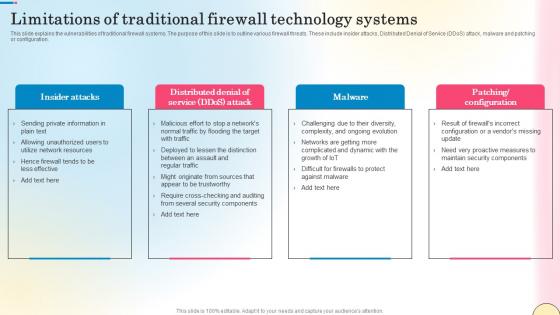
Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf
This slide explains the vulnerabilities of traditional firewall systems. The purpose of this slide is to outline various firewall threats. These include insider attacks, Distributed Denial of Service DDoS attack, malware and patching or configuration. Presenting this PowerPoint presentation, titled Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide explains the vulnerabilities of traditional firewall systems. The purpose of this slide is to outline various firewall threats. These include insider attacks, Distributed Denial of Service DDoS attack, malware and patching or configuration.
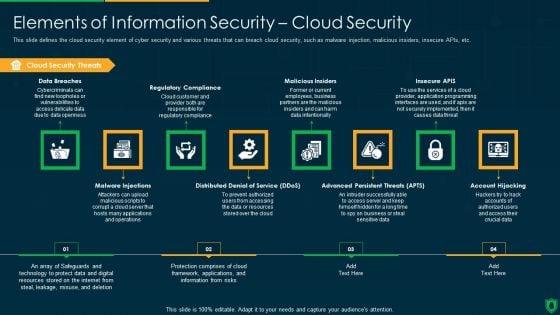
Info Security Elements Of Information Security Cloud Security Ppt PowerPoint Presentation Gallery Graphics Download PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting info security elements of information security cloud security ppt powerpoint presentation gallery graphics download pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like cloud security threats, regulatory compliance, malicious insiders, insecure apis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
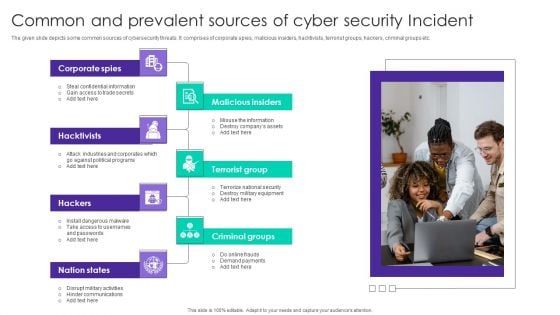
Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
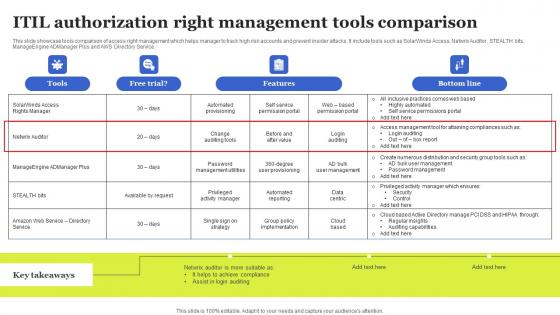
ITIL Authorization Right Management Tools Comparison Information Pdf
This slide showcase tools comparison of access right management which helps manager to track high risk accounts and prevent insider attacks. It include tools such as SolarWinds Access, Netwrix Auditor, STEALTH bits, ManageEngine ADManager Plus and AWS Directory Service. Showcasing this set of slides titled ITIL Authorization Right Management Tools Comparison Information Pdf The topics addressed in these templates are Features, ITIL Authorization, Right Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase tools comparison of access right management which helps manager to track high risk accounts and prevent insider attacks. It include tools such as SolarWinds Access, Netwrix Auditor, STEALTH bits, ManageEngine ADManager Plus and AWS Directory Service.

Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat.Present like a pro with Checklist To Ensure Asset Protection From Improving Cybersecurity With Incident Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
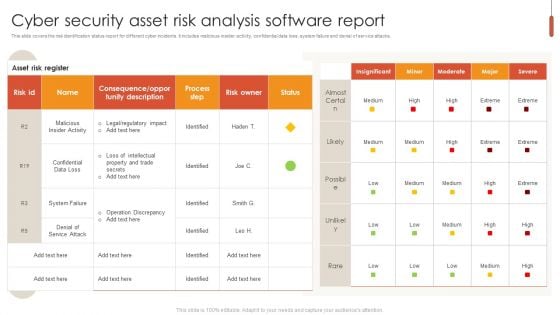
Cyber Security Asset Risk Analysis Software Report Pictures PDF
This slide covers the risk identification status report for different cyber incidents. It includes malicious insider activity, confidential data loss, system failure and denial of service attacks. Pitch your topic with ease and precision using this Cyber Security Asset Risk Analysis Software Report Pictures PDF. This layout presents information on Cyber Security Asset Risk, Analysis Software Report. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Operational Risk Event Sources And Causes Ppt PowerPoint Presentation Infographics Files PDF
This slide covers information about sources and causes of operational risk events. Events included are internal fraud, external fraud, employment practice and workshop safety and clients and business practices.Deliver and pitch your topic in the best possible manner with this operational risk event sources and causes ppt powerpoint presentation infographics files pdf. Use them to share invaluable insights on internal fraud, external fraud, insider trading, valuable information disclosure, employment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
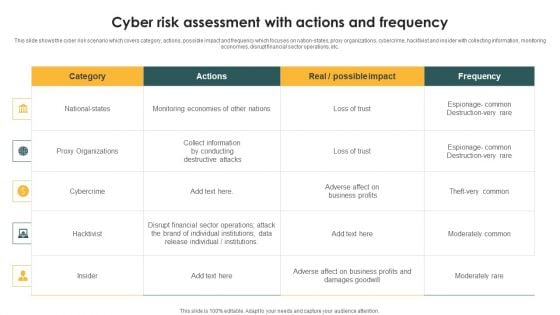
Cyber Risk Assessment With Actions And Frequency Ppt PowerPoint Presentation File Gridlines PDF
This slide shows the cyber risk scenario which covers category, actions, possible impact and frequency which focuses on nation-states, proxy organizations, cybercrime, hacktivist and insider with collecting information, monitoring economies, disrupt financial sector operations, etc. Pitch your topic with ease and precision using this Cyber Risk Assessment With Actions And Frequency Ppt PowerPoint Presentation File Gridlines PDF. This layout presents information on National states, Proxy Organizations, Cybercrime. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Risk Free Technology PowerPoint Templates And PowerPoint Backgrounds 0611
Microsoft PowerPoint Template and Background with a green satisfaction guaranteed symbol inside the center of a large gear Customise your Risk Free Technology PowerPoint Templates And PowerPoint Backgrounds 0611 as per your choice. Discover that they are amenable and adaptive.
Confused Mind PowerPoint Icon C
The labyrinth inside the head. Concept of problem fear lost solution idea etc. Our Confused Mind PowerPoint Icon C provide many a facility. They assist in the assimilation of your ideas.
Confused Mind PowerPoint Icon S
The labyrinth inside the head. Concept of problem fear lost solution idea etc. Champion your favourite cause with our Confused Mind PowerPoint Icon S. They give your argument added depth.

Stock Photo Black Electricity Plug In Socket PowerPoint Slide
Concept of problem solving is well displayed in this power point image slide. This image slide contains the graphic of black and white electricity plugs. Black plug is inside the socket which shows the right selection method of solution. Use this image for displaying problem solving technique in any presentations.
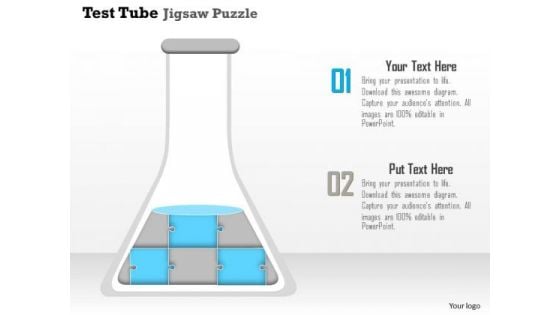
Business Diagram Test Tube Jigsaw Puzzle Conceptual Presentation Template
This power point template has been crafted with test tube graphic and puzzles inside it. This business slide contains the concept of experiment for problem solving. Add this diagram in your business presentations and display problem solving techniques. This image slide may also be used for science related topics.
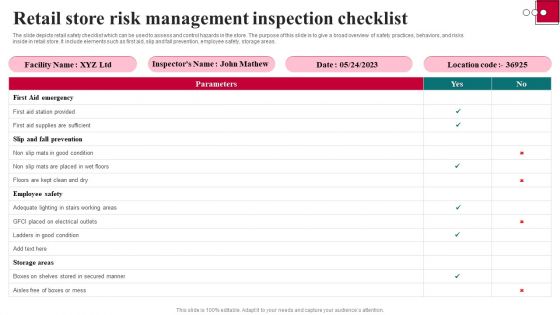
Retail Store Risk Management Inspection Checklist Brochure PDF
The slide depicts retail safety checklist which can be used to assess and control hazards in the store. The purpose of this slide is to give a broad overview of safety practices, behaviors, and risks inside in retail store. It include elements such as first aid, slip and fall prevention, employee safety, storage areas. Showcasing this set of slides titled Retail Store Risk Management Inspection Checklist Brochure PDF. The topics addressed in these templates are Retail Store Risk, Management Inspection Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
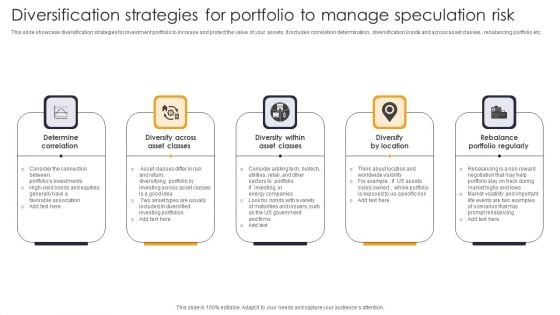
Diversification Strategies For Portfolio To Manage Speculation Risk Information PDF
This slide showcase diversification strategies for investment portfolio to increase and protect the value of your assets. It includes correlation determination , diversification inside and across asset classes , rebalancing portfolio etc. Persuade your audience using this Diversification Strategies For Portfolio To Manage Speculation Risk Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Diversify Across Asset Classes, Determine Correlation, Diversify By Location. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
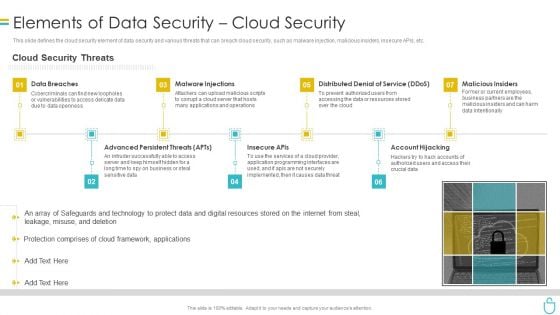
Information Security Elements Of Data Security Cloud Security Ppt Model Rules PDF
This slide defines the cloud security element of data security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting information security elements of data security cloud security ppt model rules pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data breaches, malware injections, distributed denial of service, malicious insiders, account hijacking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
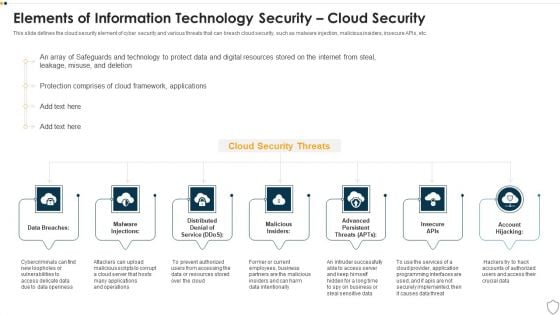
IT Security Elements Of Information Technology Security Cloud Security Ppt Outline Background Images PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a it security elements of information technology security cloud security ppt outline background images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data breaches, malware injections, malicious insiders, account hijacking, distributed denial of service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Elements Of Electronic Information Security Cloud Security Ppt Outline Background Designs PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a cybersecurity elements of electronic information security cloud security ppt outline background designs pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, information, risks, resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Elements Of IT Security IT Cloud Security Ppt Infographics Ideas PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting elements of it security it cloud security ppt infographics ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, service, vulnerabilities, implemented, digital resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Elements Of Computer Security Cloud Security Diagrams PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a desktop security management elements of computer security cloud security diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Elements Of Information Technology Security Cloud Security Ppt Icon Gridlines PDF
This slide defines the cloud security element of network security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a elements of information technology security cloud security ppt icon gridlines pdf show pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like elements of information technology security cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
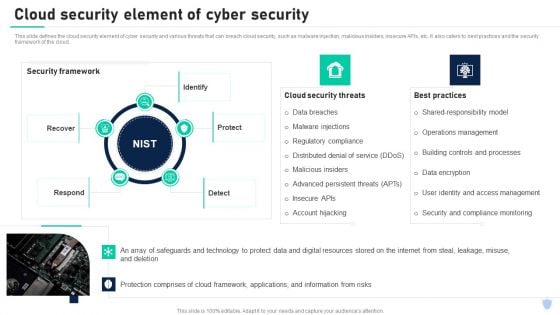
Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. It also caters to best practices and the security framework of the cloud. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Ppt Blue Diamond Linear Action 7 Phase Diagram PowerPoint Templates
PPT blue diamond linear action 7 phase diagram PowerPoint Templates-Use this Diamond based Operation Chart Diagram to explore seven stages of a Linear Process. This chart visualize the process steps, reoccurrences and components or of your company structure or product features.-PPT blue diamond linear action 7 phase diagram PowerPoint Templates-Abstract, Action, Artwork, Beam, Blue, Concept, Conceptual, Contemporary, Core, Cyberspace, Data, Depth, Dimension, Dynamic, Field, Form, Geometric, Glow, Glowing, Graphic, Hi-Tech, Idea, Illumination, Inner, Inside, Linear, Lines Cure your organization's problems with our Ppt Blue Diamond Linear Action 7 Phase Diagram PowerPoint Templates. You will come out on top.
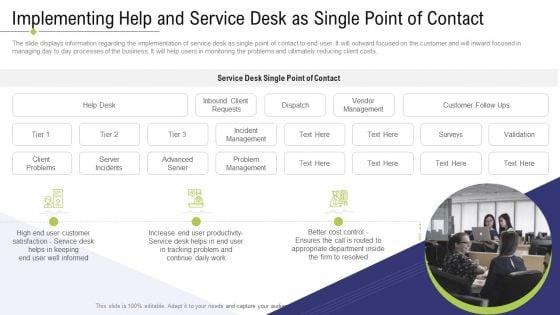
Technology Facility Maintenance And Provider Implementing Help And Service Desk As Single Point Of Contact Template PDF
The slide displays information regarding the implementation of service desk as single point of contact to end user. It will outward focused on the customer and will inward focused in managing day to day processes of the business. It will help users in monitoring the problems and ultimately reducing client costs. Presenting technology facility maintenance and provider implementing help and service desk as single point of contact template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like problem management, service desk, appropriate department inside, better cost control, service desk single point of contact. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Business People 3d Men Colorful Gear Process Interconnected PowerPoint Templates
We present our business people 3d men colorful gear process interconnected PowerPoint templates.Download our People PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Use our Process and Flows PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Download our Shapes PowerPoint Templates because You can Hit the nail on the head with our PowerPoint Templates and Slides. Embed your ideas in the minds of your audience. Use our Business PowerPoint Templates because you can Set pulses racing with our PowerPoint Templates and Slides. They will raise the expectations of your team. Download our Future PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script.Use these PowerPoint slides for presentations relating to 3d, accuracy, anatomy, brain, colored,concentration, concept, creativity, cyborg,engineering, equipment, expertise, face,gear, head, human, idea, imagination,incentive, innovation, inside, inspiration,intelligence, machine, mechanical,memories, men, mental, motivation,order, organization, part, people, person,problem, process, profile, shape, sign,skull, solution, technology, think, turning. The prominent colors used in the PowerPoint template are Blue light, Red, Yellow. The feedback we get is that our business people 3d men colorful gear process interconnected PowerPoint templates provide great value for your money. Be assured of finding the best projection to highlight your words. Professionals tell us our anatomy PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. PowerPoint presentation experts tell us our business people 3d men colorful gear process interconnected PowerPoint templates have awesome images to get your point across. People tell us our cyborg PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Presenters tell us our business people 3d men colorful gear process interconnected PowerPoint templates will make you look like a winner. Professionals tell us our brain PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. Experience craftsmanship with our Business People 3d Men Colorful Gear Process Interconnected PowerPoint Templates. They are designed by excellent artisans.


 Continue with Email
Continue with Email

 Home
Home


































