Internet Security
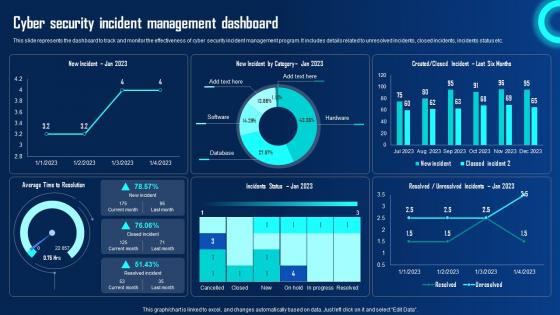
Cyber Security Incident Management Dashboard Ppt Powerpoint Presentation File Ideas Pdf
This slide represents the dashboard to track and monitor the effectiveness of cyber security incident management program. It includes details related to unresolved incidents, closed incidents, incidents status etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Security Incident Management Dashboard Ppt Powerpoint Presentation File Ideas Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Security Incident Management Dashboard Ppt Powerpoint Presentation File Ideas Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the dashboard to track and monitor the effectiveness of cyber security incident management program. It includes details related to unresolved incidents, closed incidents, incidents status etc.

Cybersecurity Key Elements Of Electronic Information Security Ppt Styles Smartart PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a cybersecurity key elements of electronic information security ppt styles smartart pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, operational security, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
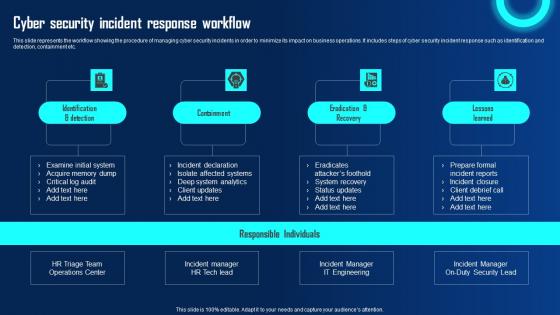
Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf
This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc. This Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Response Workflow Ppt Powerpoint Presentation File Diagrams Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the workflow showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It includes steps of cyber security incident response such as identification and detection, containment etc.
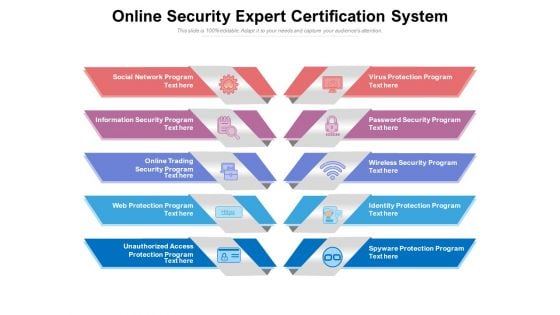
Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
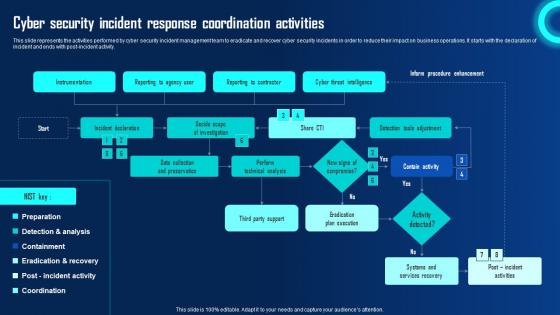
Cyber Security Incident Response Coordination Activities Ppt Powerpoint Presentation File Portfolio Pdf
This slide represents the activities performed by cyber security incident management team to eradicate and recover cyber security incidents in order to reduce their impact on business operations. It starts with the declaration of incident and ends with post incident activity. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Incident Response Coordination Activities Ppt Powerpoint Presentation File Portfolio Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the activities performed by cyber security incident management team to eradicate and recover cyber security incidents in order to reduce their impact on business operations. It starts with the declaration of incident and ends with post incident activity.

Cyber Security Crisis Management Action Plan Timeline Ppt Powerpoint Presentation File Example File Pdf
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. If you are looking for a format to display your unique thoughts, then the professionally designed Cyber Security Crisis Management Action Plan Timeline Ppt Powerpoint Presentation File Example File Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cyber Security Crisis Management Action Plan Timeline Ppt Powerpoint Presentation File Example File Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery.
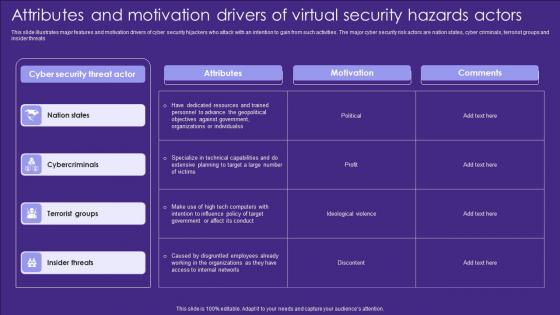
Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf
This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats Showcasing this set of slides titled Attributes And Motivation Drivers Of Virtual Security Hazards Actors Designs Pdf. The topics addressed in these templates are Attributes, Motivation, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats
Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf
This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc. The Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc.
Best Paid Password Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Best Paid Password Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Best Paid Password Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Best Paid Password Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides
Incorporate this Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides to make your business idea and proposal stand out. This will also ensure that your proposal,in seventeen slides of this complete deck,is well organized and professional. You can also add variables like market opportunity,value proposition,innovative solutions,and more for any business concern or issue that you might be facing. Download this design now. The 100 percent customizable nature of the template adds to the beauty of the entire concept of the off the shelf presentation concept that we have mastered. Our Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
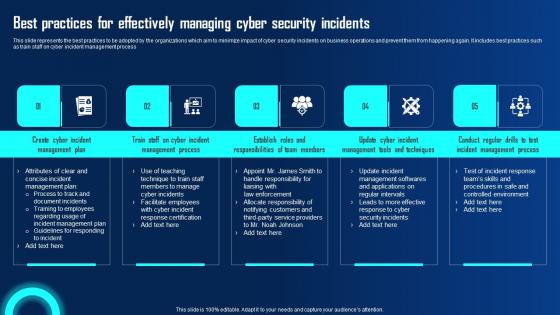
Best Practices For Effectively Managing Cyber Security Ppt Powerpoint Presentation File Model Pdf
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as train staff on cyber incident management process If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Best Practices For Effectively Managing Cyber Security Ppt Powerpoint Presentation File Model Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as train staff on cyber incident management process
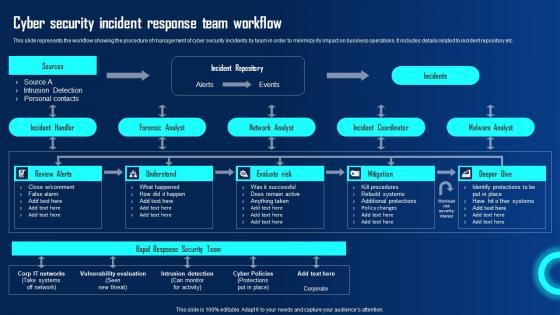
Cyber Security Incident Response Team Workflow Ppt Powerpoint Presentation File Deck Pdf
This slide represents the workflow showing the procedure of management of cyber security incidents by team in order to minimize its impact on business operations. It includes details related to incident repository etc. This modern and well arranged Cyber Security Incident Response Team Workflow Ppt Powerpoint Presentation File Deck Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the workflow showing the procedure of management of cyber security incidents by team in order to minimize its impact on business operations. It includes details related to incident repository etc.
Cyber Security Risk Register Template In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Security Risk Register Template In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Security Risk Register Template. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cyber Security Risk Register Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Laptop Deals Cyber Security Awareness In Powerpoint And Google Slides Cpb
Introducing our well-designed Laptop Deals Cyber Security Awareness In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Laptop Deals Cyber Security Awareness. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Laptop Deals Cyber Security Awareness In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf
This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc. Find highly impressive Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Barriers To Cyber Security Incident Management Ppt Powerpoint Presentation File Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the challenges faced by enterprises in managing cyber attacks to minimize its impact on business operations. It includes barriers related to people, technology, process etc.

Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck
Take advantage of this well-researched and professionally-designed Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the twenty one-slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below. Our Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
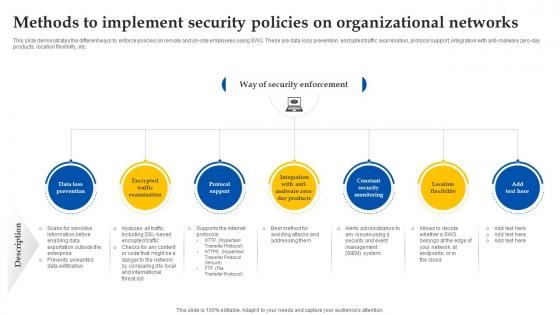
Web Access Control Solution Methods To Implement Security Policies On Organizational Networks
This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Take your projects to the next level with our ultimate collection of Web Access Control Solution Methods To Implement Security Policies On Organizational Networks. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc.
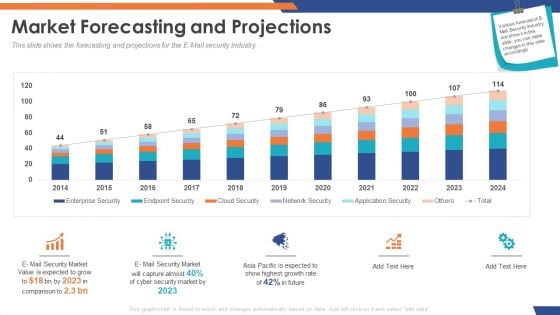
Email Security Market Research Report Market Forecasting And Projections Infographics PDF
Presenting this set of slides with name email security market research report market forecasting and projections infographics pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
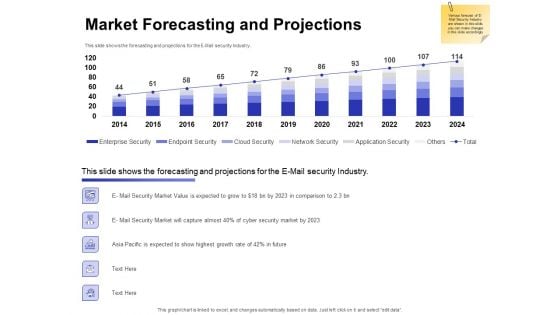
Global Cloud Based Email Security Market Market Forecasting And Projections Professional PDF
Presenting this set of slides with name global cloud based email security market market forecasting and projections professional pdf. The topics discussed in these slides are network security, cloud security, endpoint security, enterprise security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Zero Trust Network Access Traditional Security Models Vs Zero Trust Network Access
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Welcome to our selection of the Zero Trust Network Access Traditional Security Models Vs Zero Trust Network Access. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.

Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf
This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector. Explore a selection of the finest Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Emerging Cyber Security Incident Management Trends 2023 Ppt Powerpoint Presentation File Files Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the emerging trends in cyber attacks faced by the enterprises. It includes details related to cyber attacks experienced by enterprises, top global fraud types and volume of cyber security incidents by sector.
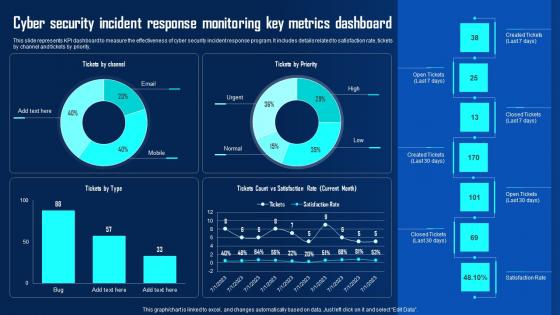
Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority.

Risks Associated With Neglecting Security In Devops Role Of Devsecops Ppt Slide
This slide showcases the various challenges associated with DevOps for neglecting security. The purpose of this slide is to explain the risks related to security these include elevated exposure to cyber threats, compliance and legal concerns, and so on. Want to ace your presentation in front of a live audience Our Risks Associated With Neglecting Security In Devops Role Of Devsecops Ppt Slide can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the various challenges associated with DevOps for neglecting security. The purpose of this slide is to explain the risks related to security these include elevated exposure to cyber threats, compliance and legal concerns, and so on.
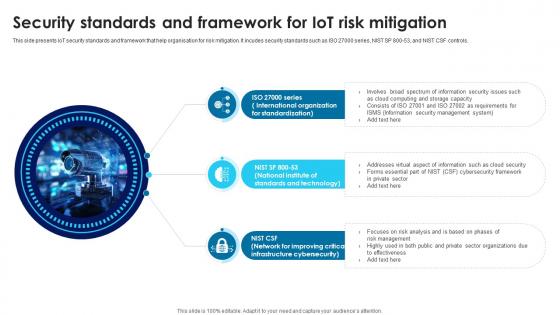
Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V
This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls. Present like a pro with Building Trust With IoT Security Standards And Framework For IoT Risk Mitigation IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800-53, and NIST CSF controls.
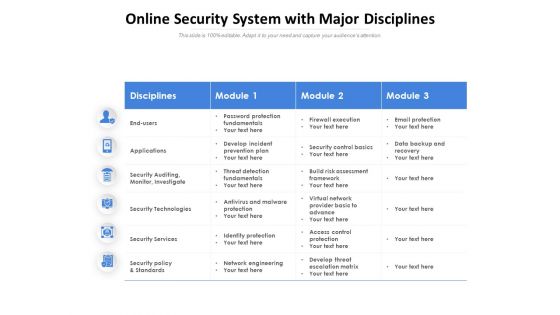
Online Security System With Major Disciplines Ppt PowerPoint Presentation Ideas Inspiration PDF
Presenting this set of slides with name online security system with major disciplines ppt powerpoint presentation ideas inspiration pdf. The topics discussed in these slides are disciplines, module, applications, security auditing, monitor, investigate, security technologies, security services, security policy and standards. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
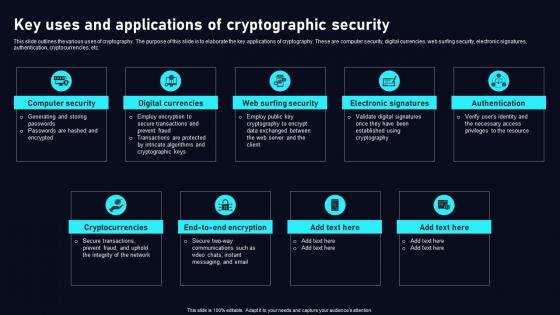
Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Want to ace your presentation in front of a live audience Our Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc.
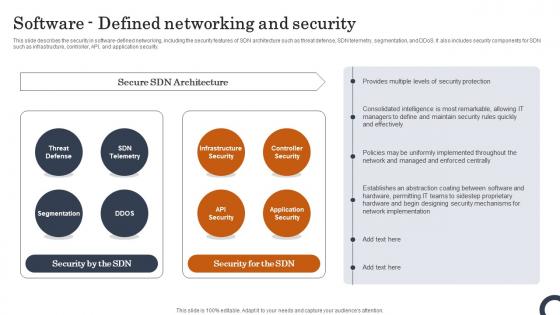
Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Do you know about Slidesgeeks Software Defined Networking And Security Evolution Of SDN Controllers Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security.

Web Consulting Business Different Security Threats To Be Managed By Web
Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs. This modern and well-arranged Web Consulting Business Different Security Threats To Be Managed By Web provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs.

Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V
This slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity. It includes devices such as smart cameras, RFID tags, Smart GPS systems, and smart home devices, smart meters. Find highly impressive Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Building Trust With IoT Security Concerns And Solutions For Interconnected Devices IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide exhibits security solution to safeguard interconnected devices against security attacks in order to enhance overall productivity. It includes devices such as smart cameras, RFID tags, Smart GPS systems, and smart home devices, smart meters.
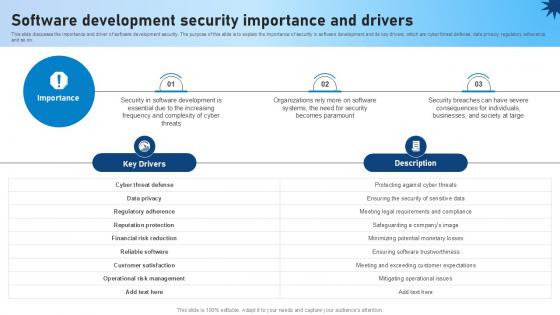
Software Development Security Importance And Drivers Role Of Devsecops Ppt Slide
This slide discusses the importance and driver of software development security. The purpose of this slide is to explain the importance of security in software development and its key drivers, which are cyber threat defense, data privacy, regulatory adherence, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Software Development Security Importance And Drivers Role Of Devsecops Ppt Slide a try. Our experts have put a lot of knowledge and effort into creating this impeccable Software Development Security Importance And Drivers Role Of Devsecops Ppt Slide You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide discusses the importance and driver of software development security. The purpose of this slide is to explain the importance of security in software development and its key drivers, which are cyber threat defense, data privacy, regulatory adherence, and so on.
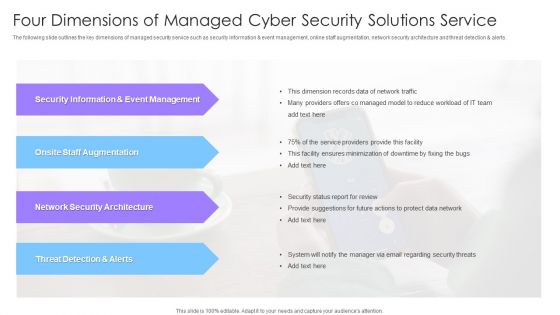
Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF
The following slide outlines the key dimensions of managed security service such as security information and event management, online staff augmentation, network security architecture and threat detection and alerts. Pitch your topic with ease and precision using this Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF. This layout presents information on Security Information, Event Management, Staff Augmentation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
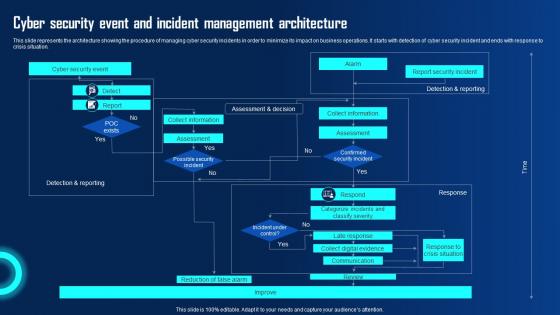
Cyber Security Event And Incident Management Ppt Powerpoint Presentation Diagram Graph Charts Pdf
This slide represents the architecture showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Security Event And Incident Management Ppt Powerpoint Presentation Diagram Graph Charts Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the architecture showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation.
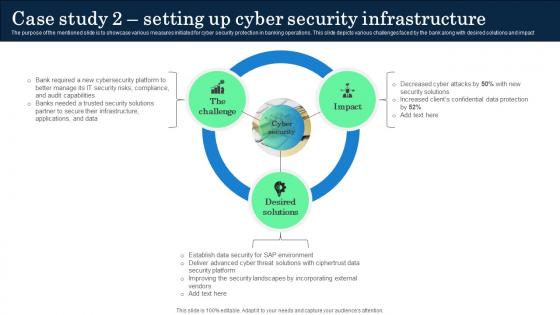
Case Study 2 Setting Up Cyber Security Infrastructure Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact. Present like a pro with Case Study 2 Setting Up Cyber Security Infrastructure Incorporating Banking Operational Growth. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The purpose of the mentioned slide is to showcase various measures initiated for cyber security protection in banking operations. This slide depicts various challenges faced by the bank along with desired solutions and impact

IT Protection Cyber Security Cyber Threat Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name it protection cyber security cyber threat ppt powerpoint presentation complete deck. The topics discussed in these slides are network protection, cyber security, cyber threat, laptop protected, security breach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Website Security Management Strategic Plan Step By Step Guide Slides PDF
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Website Security Management Strategic Plan Step By Step Guide Slides PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Website Security Management Strategic Plan Step By Step Guide Slides PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc.

Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication.

Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Take your projects to the next level with our ultimate collection of Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc.
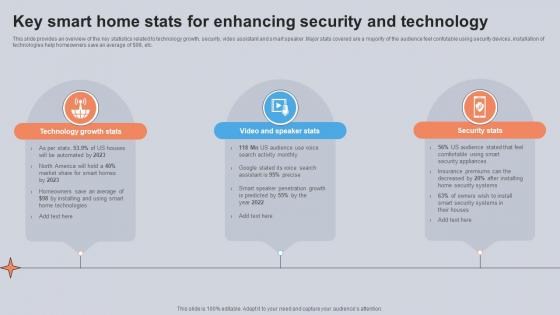
Key Smart Home Stats For Enhancing Security And Technology Utilizing Smart Appliances IoT SS V
This slide provides an overview of the key statistics related to technology growth, security, video assistant and smart speaker. Major stats covered are a majority of the audience feel confutable using security devices, installation of technologies help homeowners save an average of dollar 98, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Smart Home Stats For Enhancing Security And Technology Utilizing Smart Appliances IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide provides an overview of the key statistics related to technology growth, security, video assistant and smart speaker. Major stats covered are a majority of the audience feel confutable using security devices, installation of technologies help homeowners save an average of dollar 98, etc.

Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V
This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc. Retrieve professionally designed Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc.
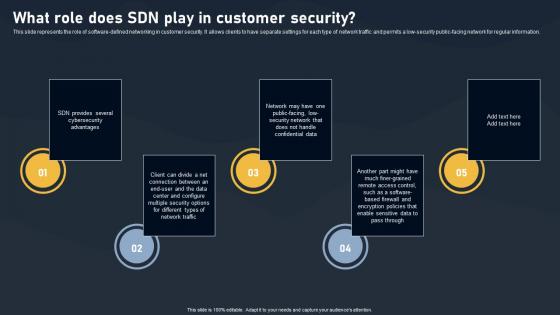
What Role Does SDN Play In Customer Security SDN Building Blocks Topics Pdf
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information.This modern and well-arranged What Role Does SDN Play In Customer Security SDN Building Blocks Topics Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information.
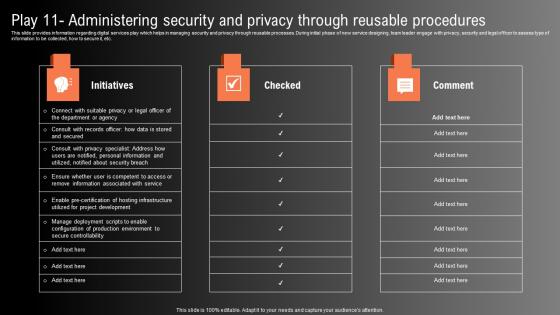
Play 11 Administering Security And Privacy Technological Innovation Playbook Portrait Pdf
This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. This Play 11 Administering Security And Privacy Technological Innovation Playbook Portrait Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Play 11 Administering Security And Privacy Technological Innovation Playbook Portrait Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc.
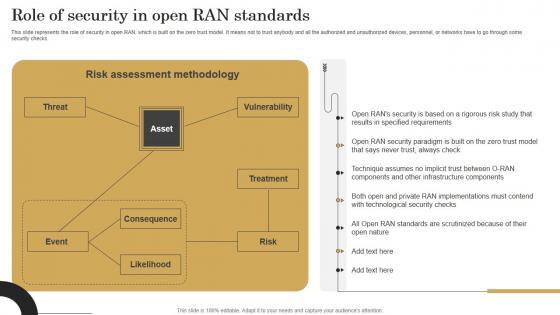
Role Of Security In Open Ran Standards Revolutionizing Mobile Networks Ideas PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Role Of Security In Open Ran Standards Revolutionizing Mobile Networks Ideas PDF from Slidegeeks and deliver a wonderful presentation. This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks.
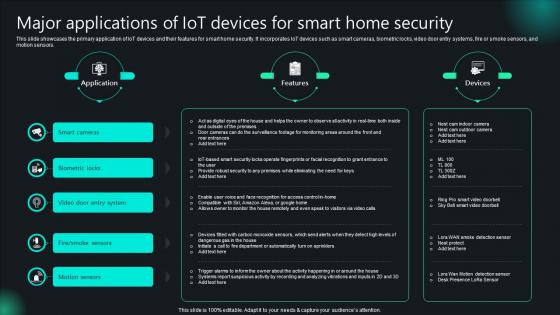
Major Applications Of IoT Devices For Smart Home Security Unlocking Potential IoTs Application IoT SS V
This slide showcases the primary application of IoT devices and their features for smart home security. It incorporates IoT devices such as smart cameras, biometric locks, video door entry systems, fire or smoke sensors, and motion sensors. There are so many reasons you need a Major Applications Of IoT Devices For Smart Home Security Unlocking Potential IoTs Application IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases the primary application of IoT devices and their features for smart home security. It incorporates IoT devices such as smart cameras, biometric locks, video door entry systems, fire or smoke sensors, and motion sensors.

Comprehensive Guide For Website Different Security Threats To Be Managed By Web
Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs. Are you searching for a Comprehensive Guide For Website Different Security Threats To Be Managed By Web that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Comprehensive Guide For Website Different Security Threats To Be Managed By Web from Slidegeeks today. Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs.
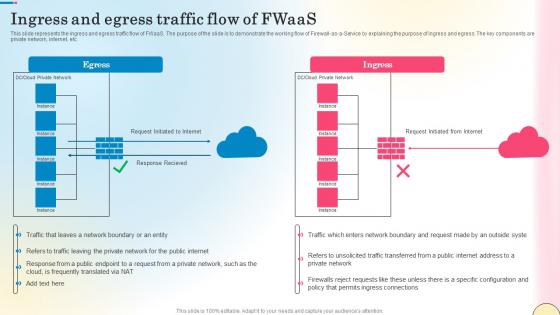
Ingress And Egress Traffic Flow Of Fwaas Network Security Elements Pdf
This slide represents the ingress and egress traffic flow of FWaaS. The purpose of the slide is to demonstrate the working flow of Firewall-as-a-Service by explaining the purpose of ingress and egress. The key components are private network, internet, etc. Are you searching for a Ingress And Egress Traffic Flow Of Fwaas Network Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Ingress And Egress Traffic Flow Of Fwaas Network Security Elements Pdf from Slidegeeks today. This slide represents the ingress and egress traffic flow of FWaaS. The purpose of the slide is to demonstrate the working flow of Firewall-as-a-Service by explaining the purpose of ingress and egress. The key components are private network, internet, etc.
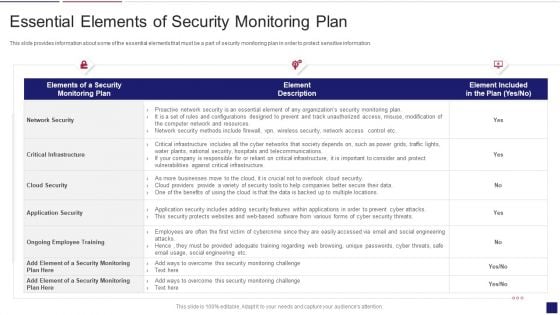
Continuous Development Evaluation Plan Eliminate Cyber Attacks Essential Elements Of Security Monitoring Elements PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks essential elements of security monitoring elements pdf bundle. Topics like network security, critical infrastructure, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
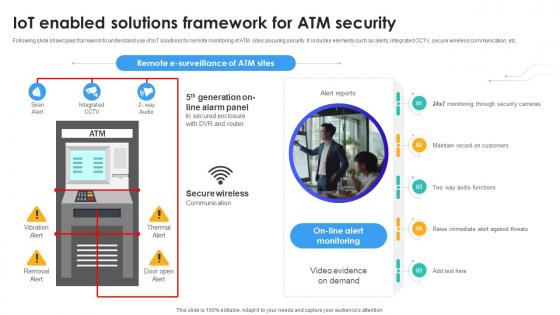
IoT Enabled Solutions Framework For Atm Security IoT In Banking For Digital Future IoT SS V
Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit IoT Enabled Solutions Framework For Atm Security IoT In Banking For Digital Future IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates Following slide showcases framework to understand use of IoT solutions for remote monitoring of ATM sites assuring security. It includes elements such as alerts, integrated CCTV, secure wireless communication, etc.
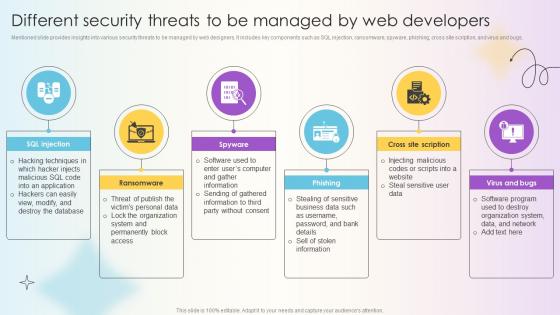
Managing Technical And Non Different Security Threats To Be Managed By Web Developers
Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Managing Technical And Non Different Security Threats To Be Managed By Web Developers to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. Mentioned slide provides insights into various security threats to be managed by web designers. It includes key components such as SQL injection, ransomware, spyware, phishing, cross site scription, and virus and bugs.

Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V
This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Get a simple yet stunning designed Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Beginners Guide To Checklist To Ensure Security Of Bitcoin Wallets Fin SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks.
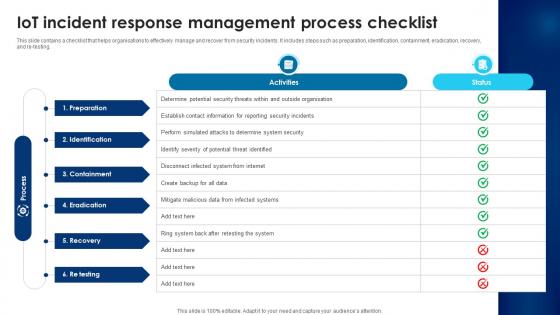
Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V
This slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re-testing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Building Trust With IoT Security IoT Incident Response Management Process Checklist IoT SS V. This slide contains a checklist that helps organisations to effectively manage and recover from security incidents. It includes steps such as preparation, identification, containment, eradication, recovery, and re-testing.
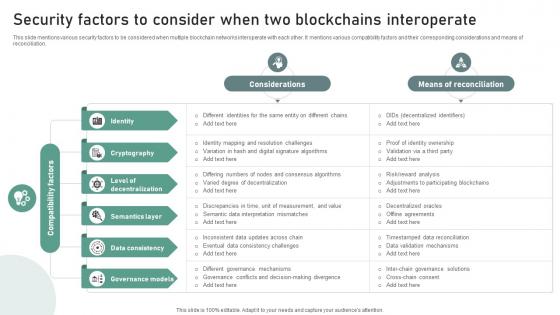
Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V
This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Create an editable Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Bridging Blockchains A Deep Security Factors To Consider When Two Blockchains BCT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation.
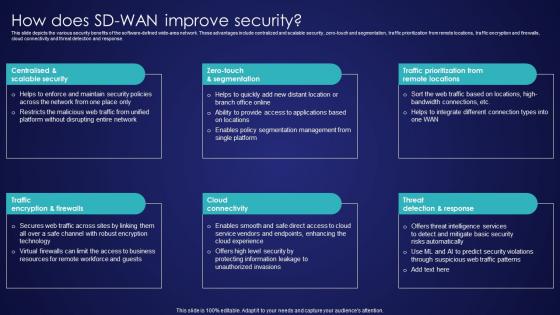
How Does SD Wan Improve Security Wide Area Network Services Structure Pdf
This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than How Does SD Wan Improve Security Wide Area Network Services Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab How Does SD Wan Improve Security Wide Area Network Services Structure Pdf today and make your presentation stand out from the rest. This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response.

Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Traditional Security Models Vs Zero Trust Network Access Software Defined Perimeter SDP and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling.
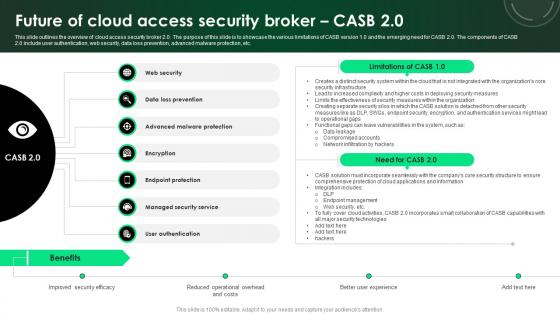
CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0 for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc.
Icons Slide For Network Security Using Firewall As A Service Clipart Pdf
Introducing our well designed Icons Slide For Network Security Using Firewall As A Service Clipart Pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience. Our Icons Slide For Network Security Using Firewall As A Service Clipart Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Get a simple yet stunning designed CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Overview Of Cloud Access Security Broker Architecture can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc.
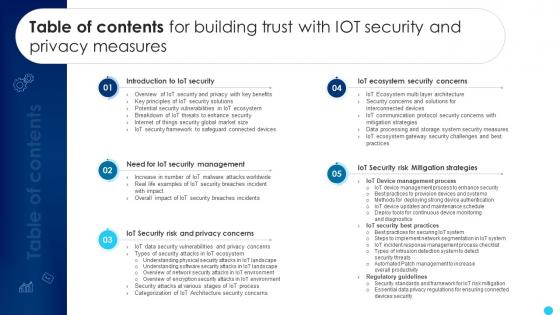
Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Our Table Of Contents For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Agenda For Building Trust With IoT Security And Privacy Measures IoT SS V
Find a pre-designed and impeccable Agenda For Building Trust With IoT Security And Privacy Measures IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda For Building Trust With IoT Security And Privacy Measures IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
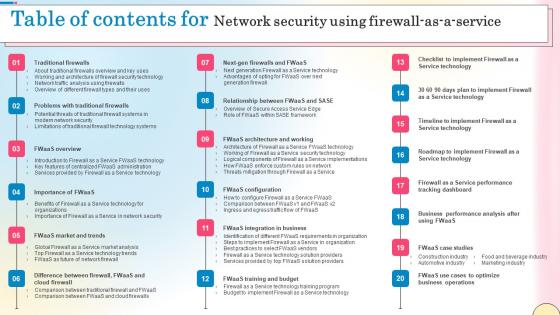
Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our Table Of Contents For Network Security Using Firewall As A Service Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
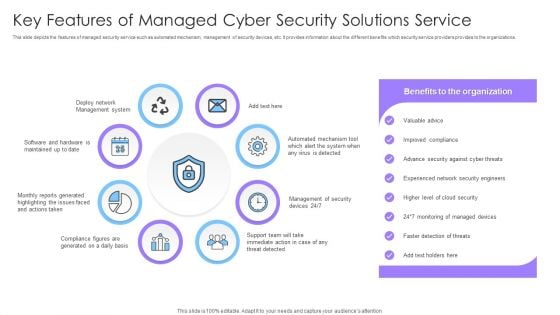
Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF
This slide depicts the features of managed security service such as automated mechanism, management of security devices, etc. It provides information about the different benefits which security service providers provides to the organizations. Presenting Key Features Of Managed Cyber Security Solutions Service Ppt Pictures Layouts PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Deploy Network, Management System, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


 Continue with Email
Continue with Email

 Home
Home


































