Internet Security
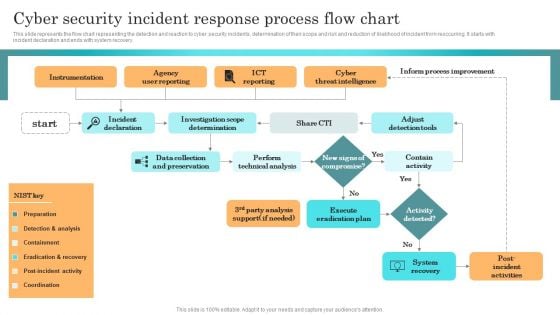
Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF from Slidegeeks and deliver a wonderful presentation.
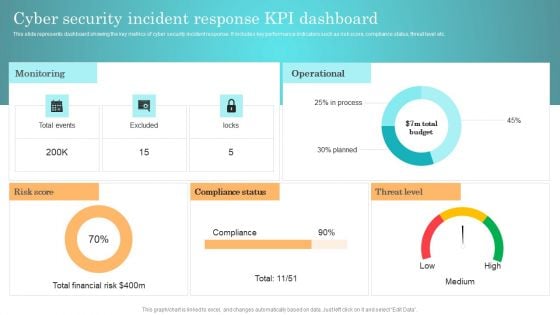
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF
The following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Want to ace your presentation in front of a live audience Our Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF
This slide signifies the strategic plan timeline to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor Persuade your audience using this Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Analyse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
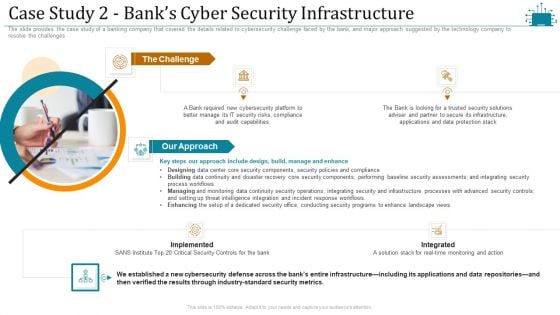
Cloud Intelligence Framework For Application Consumption Case Study 2 Banks Cyber Security Infrastructure Microsoft PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges. This is a cloud intelligence framework for application consumption case study 2 banks cyber security infrastructure microsoft pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process workflows, industry standard security metrics, implemented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
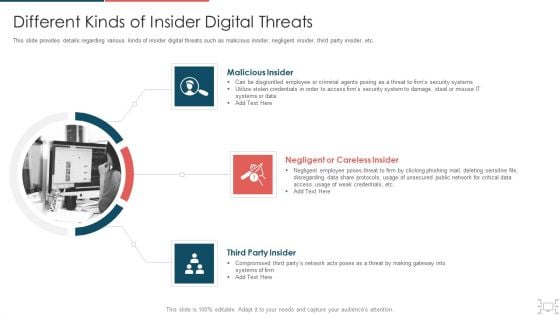
Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
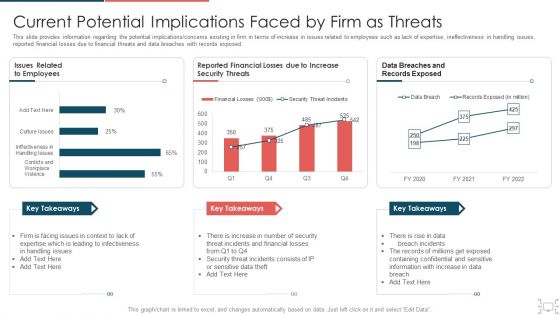
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
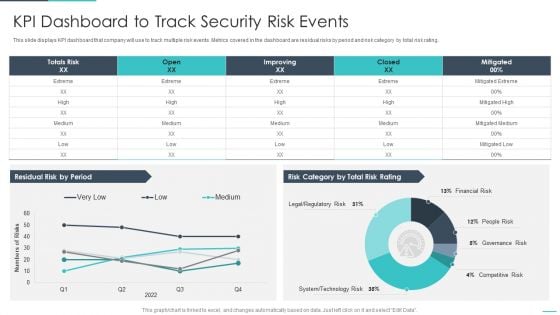
Handling Cyber Threats Digital Era KPI Dashboard To Track Security Risk Events Ppt Inspiration PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era kpi dashboard to track security risk events ppt inspiration pdf. Use them to share invaluable insights on kpi dashboard to track security risk events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
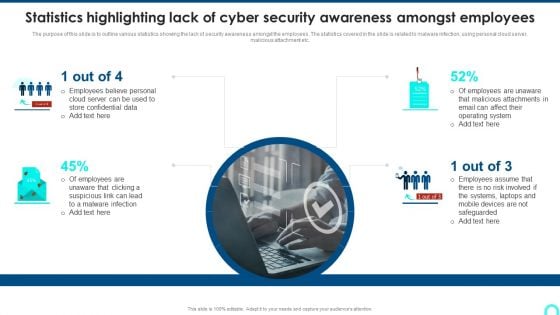
Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc.Presenting Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Employees Believe, Store Confidential, Malicious Attachments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
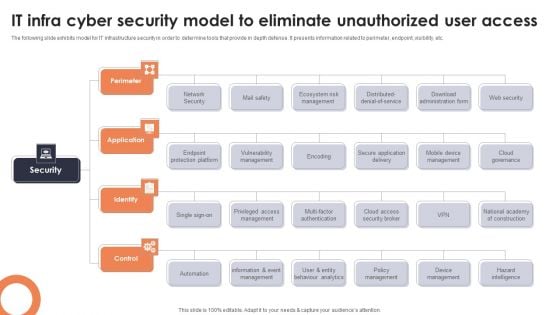
IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF
The following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defense. It presents information related to perimeter, endpoint, visibility, etc. Presenting IT Infra Cyber Security Model To Eliminate Unauthorized User Access Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Perimeter, Application, Identify. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Digital Transformation Security Risk Ppt PowerPoint Presentation Slides Graphics Example Cpb Pdf
Presenting this set of slides with name digital transformation security risk ppt powerpoint presentation slides graphics example cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like digital transformation security risk to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Deploying SDN System What Role Does SDN Play In Customer Security Structure PDF.
Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security For Your Organization Amount Spent On Cyber Fraud Settlements Ppt File Elements PDF
Presenting this set of slides with name cyber security for your organization amount spent on cyber fraud settlements ppt file elements pdf. This is a ONE stage process. The stages in this process are settlements, amount, average per settlement. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Incident Reporting By Different Cyber Departments Ppt Professional Topics PDF
Presenting this set of slides with name cyber security for your organization incident reporting by different cyber departments ppt professional topics pdf. This is a one stage process. The stages in this process are number incidents, person involved incident, average cost per incident, department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Categorization Of Cyber Risks Ppt Model Designs Download PDF
Presenting this set of slides with name strategies to mitigate cyber security risks categorization of cyber risks ppt model designs download pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Dashboard Cyber Risk Management Ppt Professional Display PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard cyber risk management ppt professional display pdf. The topics discussed in these slides are risks threshold top 5 vulnerabilities, risk rating breakdown, action plan breakdown, risk heat map. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Incident Reporting By Different Cyber Departments Summary PDF
Presenting this set of slides with name strategies to mitigate cyber security risks incident reporting by different cyber departments summary pdf. This is a one stage process. The stages in this process are number incidents, person involved incident, average cost per incident, department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
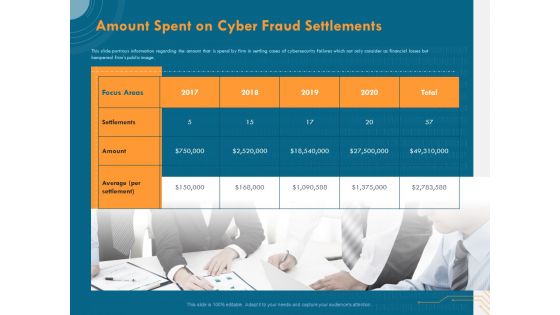
Cyber Security Implementation Framework Amount Spent On Cyber Fraud Settlements Ppt PowerPoint Presentation Summary Introduction PDF
Presenting this set of slides with name cyber security implementation framework amount spent on cyber fraud settlements ppt powerpoint presentation summary introduction pdf. This is a one stage process. The stages in this process are focus areas, settlements, amount, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
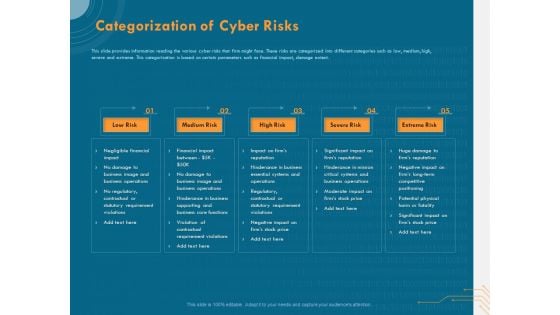
Cyber Security Implementation Framework Categorization Of Cyber Risks Ppt PowerPoint Presentation Portfolio Sample PDF
Presenting this set of slides with name cyber security implementation framework categorization of cyber risks ppt powerpoint presentation portfolio sample pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Dashboard Cyber Risk Management Ppt Outline Structure PDF
Presenting this set of slides with name cyber security implementation framework dashboard cyber risk management ppt outline structure pdf. The topics discussed in these slides are risk rating breakdown, risk analysis progress, average risk threshold, response progress for risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
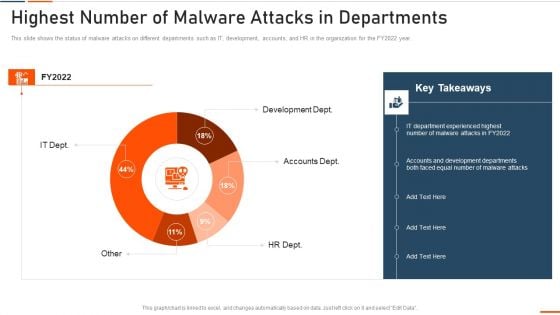
Information Technology Security Highest Number Of Malware Attacks In Departments Ppt Styles Slide Portrait PDF
This slide depicts the impact of network security training on an organization. It also shows how trained employees can reduce network attacks in the organization. Deliver and pitch your topic in the best possible manner with this information technology security highest number of malware attacks in departments ppt styles slide portrait pdf. Use them to share invaluable insights on phishing, network, intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF
This slide provides information about enabling online brand protection by tracking incidents per seller, incident per platform and infringements per country. Presenting this PowerPoint presentation, titled Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Dsl Is A Best Security Option PowerPoint Templates Ppt Backgrounds For Slides 0713
Give them a dose of your ability. It will go down well with our DSL Is A Best Security Option PowerPoint Templates PPT Backgrounds For Slides. Connect the dots with our People PowerPoint Templates. Watch the whole picture clearly emerge. Dot your thoughts with our Globe PowerPoint Templates. Give your demeanour that Propah look. Make the play with our Dsl Is A Best Security Option PowerPoint Templates Ppt Backgrounds For Slides 0713. Achieve the goals you have set.

Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF
This slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. This is a Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Mitigate Ddos Attacks, Prevent Customer Data Breach, Block Malicious Bot Abuse. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.
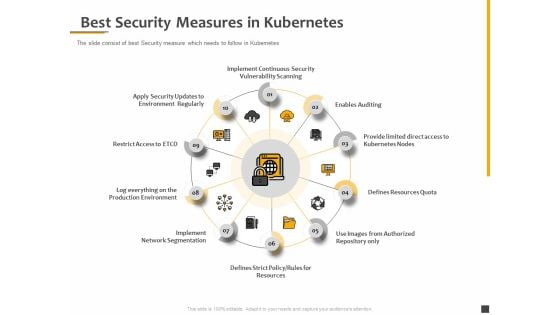
Understanding The Kubernetes Components Through Diagram Best Security Measures In Kubernetes Themes PDF
Presenting this set of slides with name understanding the kubernetes components through diagram best security measures in kubernetes themes pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Development Company Pitch Deck Problems Faced By Companies Security Introduction PDF
This is a it development company pitch deck problems faced by companies security introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poor network security, backup issues, software concerns, qualified experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
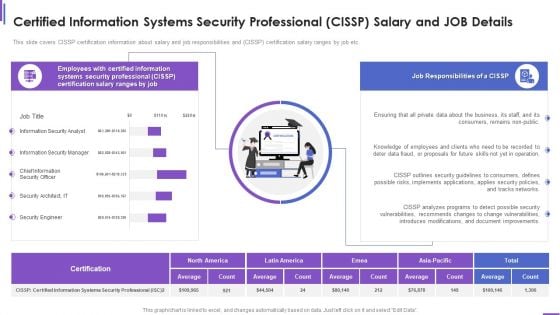
Certified Information Systems Security Professional Cissp Salary And Job Details Brochure PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver and pitch your topic in the best possible manner with this certified information systems security professional cissp salary and job details brochure pdf. Use them to share invaluable insights on consumers, security, document, networks, implements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
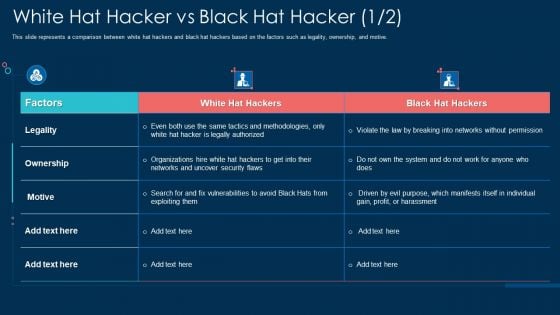
White Hat Hacker Vs Black Hat Hacker Security Ppt File Example PDF
This slide represents a comparison between white hat hackers and black hat hackers based on the factors such as legality, ownership, and motive. Deliver and pitch your topic in the best possible manner with this white hat hacker vs black hat hacker security ppt file example pdf. Use them to share invaluable insights on ownership, networks, organizations, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
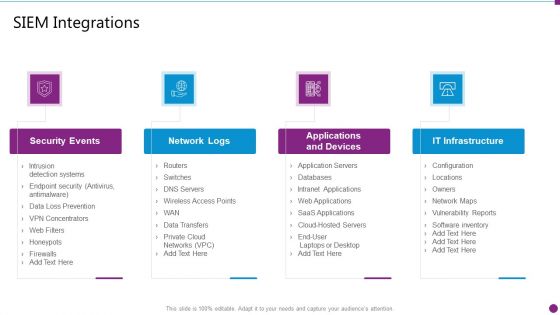
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Integrations Ideas PDF
This is a security information and event management strategies for financial audit and compliance siem integrations ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
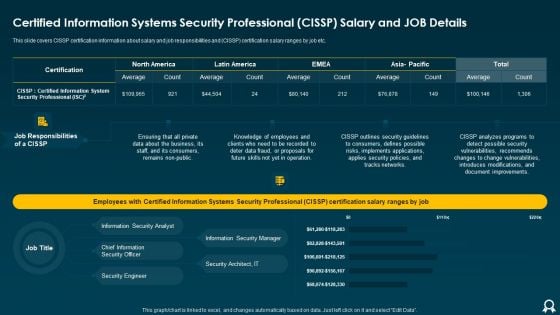
Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF bundle. Topics like Average, Tracks Networks, Applies Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
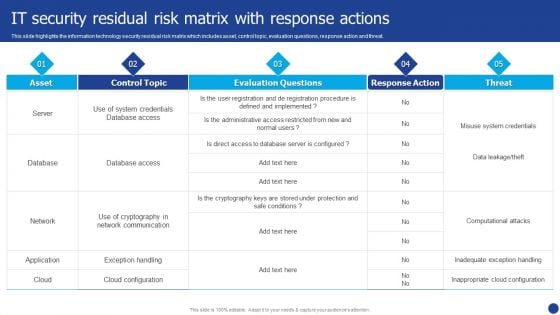
Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Online And Onsite Training Schedule For Employee Elements PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative cyber security risk management plan online and onsite training schedule for employee elements pdf bundle. Topics like position, software name, course type, training mode, duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Intelligence With Data Governance And Security Ppt PowerPoint Presentation Infographics Example PDF
Pitch your topic with ease and precision using this business intelligence with data governance and security ppt powerpoint presentation infographics example pdf. This layout presents information on data governance, data discovery, data quality management, connected clouds, security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
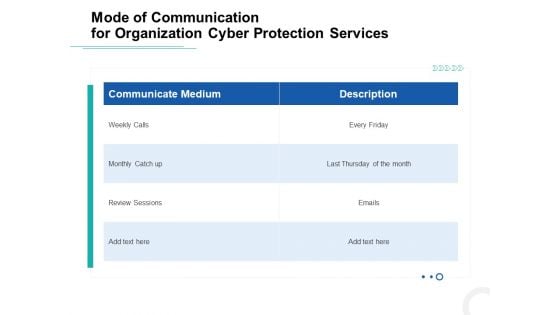
Develop Corporate Cyber Security Risk Mitigation Plan Mode Communication Organization Protection Services Introduction PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan mode communication organization protection services introduction pdf bundle. Topics like communicate medium, weekly calls, monthly catch up, review sessions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
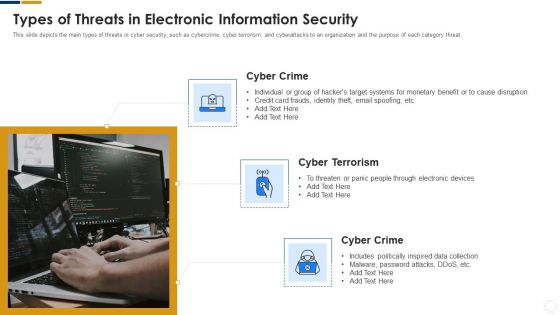
Cybersecurity Types Of Threats In Electronic Information Security Ppt Examples PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a cybersecurity types of threats in electronic information security ppt examples pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber crime. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Network Access Role Of ZTNA To Improve Business Operations And Security will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
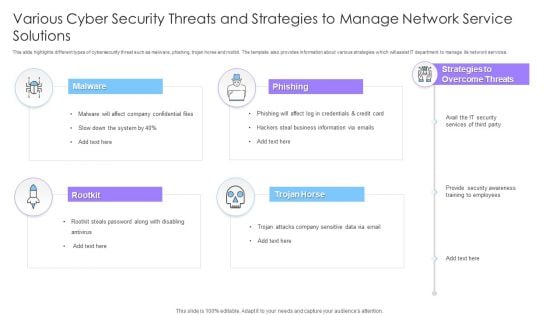
Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
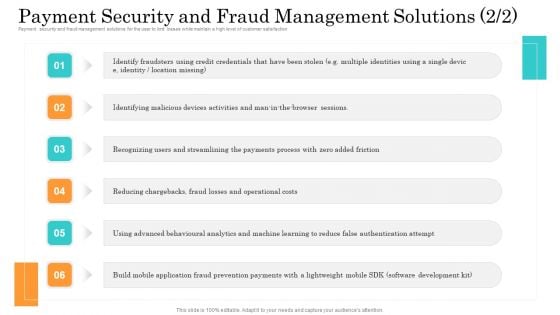
Online Payment Service Payment Security And Fraud Management Solutions Portrait PDF
Payment security and fraud management solutions for the user to limit losses while maintain a high level of customer satisfaction. Presenting online payment service payment security and fraud management solutions portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like operational costs, behavioural analytics, mobile application. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
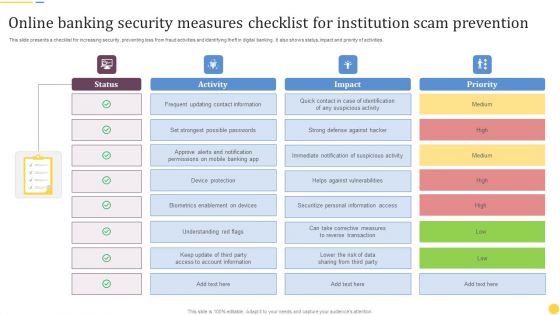
Online Banking Security Measures Checklist For Institution Scam Prevention Formats PDF
This slide presents a checklist for increasing security, preventing loss from fraud activities and identifying theft in digital banking. It also shows status, impact and priority of activities. Pitch your topic with ease and precision using this Online Banking Security Measures Checklist For Institution Scam Prevention Formats PDF. This layout presents information on Frequent Updating, Contact Information, Device Protection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
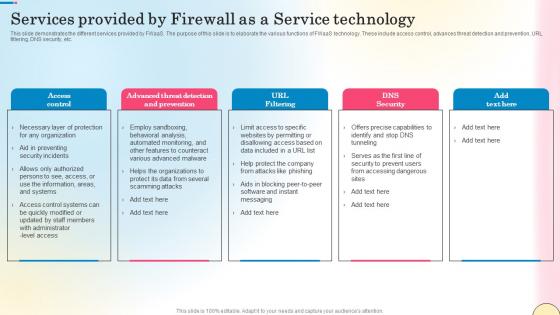
Services Provided By Firewall As A Service Technology Network Security Infographics Pdf
This slide demonstrates the different services provided by FWaaS. The purpose of this slide is to elaborate the various functions of FWaaS technology. These include access control, advances threat detection and prevention, URL filtering, DNS security, etc. There are so many reasons you need a Services Provided By Firewall As A Service Technology Network Security Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide demonstrates the different services provided by FWaaS. The purpose of this slide is to elaborate the various functions of FWaaS technology. These include access control, advances threat detection and prevention, URL filtering, DNS security, etc.
Online Settlement Revolution Payment Security And Fraud Management Solutions Browser Icons PDF
Payment security and fraud management solutions for the user to limit losses while maintain a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions browser icons pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like costs, process, analytics, development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Mitigate Cyber Security Risks Determining Firm Current Capabilities Ppt Inspiration Smartart PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining firm current capabilities ppt inspiration smartart pdf. The topics discussed in these slides are identify, protect, detect, response, recovery, key enablers, minimum standard, evolving strength. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Determining Firm Current Capabilities Ppt Outline Shapes PDF
Presenting this set of slides with name cyber security implementation framework determining firm current capabilities ppt outline shapes pdf. The topics discussed in these slides are identify, protect, detect, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Process Steps With Icons Ppt PowerPoint Presentation Summary Slide
Presenting this set of slides with name cyber security process steps with icons ppt powerpoint presentation summary slide. This is a four stage process. The stages in this process are assess, evaluate, build, execute. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Stages Circular Process Business Cyber Security Ppt PowerPoint Presentation Icon Tips
Presenting this set of slides with name five stages circular process business cyber security ppt powerpoint presentation icon tips. This is a five stage process. The stages in this process are technology, strategy, steps approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Testing Process With Icons Ppt PowerPoint Presentation Infographic Template Demonstration
Presenting this set of slides with name cyber security testing process with icons ppt powerpoint presentation infographic template demonstration. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
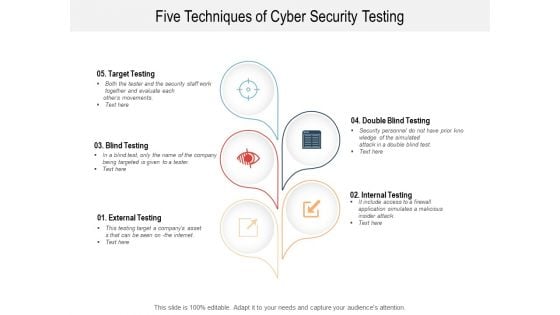
Five Techniques Of Cyber Security Testing Ppt PowerPoint Presentation Layouts Model
Presenting this set of slides with name five techniques of cyber security testing ppt powerpoint presentation layouts model. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name cyber security for your organization ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are risk management, business, analysis, goal, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Backup Maintenance Recovery Budget Planning Ppt Inspiration Slide Portrait PDF
Presenting this set of slides with name cyber security for your organization backup maintenance recovery budget planning ppt inspiration slide portrait pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, travel shipping costs, labor contractor costs, testing costs, supply costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Critical Business Functions Recovery Priorities Ppt Inspiration Slide PDF
Presenting this set of slides with name cyber security for your organization critical business functions recovery priorities ppt inspiration slide pdf. This is a one stage process. The stages in this process are priorities, maximum allowable downtime, department. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Essential Contingency Plan Strategies Ppt Layouts Vector PDF
Presenting this set of slides with name cyber security for your organization essential contingency plan strategies ppt layouts vector pdf. This is a one stage process. The stages in this process are contingency considerations, contingency solutions, server, vendor information, critical components, technologies integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Our Mission Ppt Infographics Model PDF
Presenting this set of slides with name cyber security for your organization our mission ppt infographics model pdf. This is a one stage process. The stages in this process are vision, mission, goal. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Our Team Ppt Ideas Infographic Template PDF
Presenting this set of slides with name cyber security for your organization our team ppt ideas infographic template pdf. This is a four stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
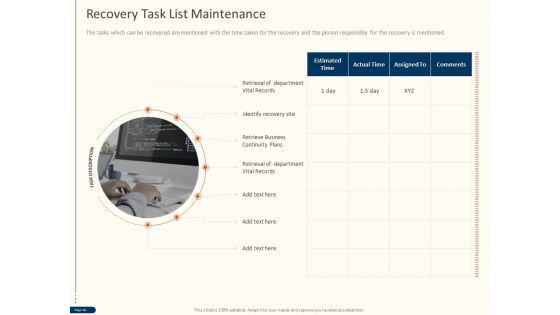
Cyber Security For Your Organization Recovery Task List Maintenance Ppt Layouts Designs Download PDF
Presenting this set of slides with name cyber security for your organization recovery task list maintenance ppt layouts designs download pdf. This is a one stage process. The stages in this process are estimated time, actual time, assigned, comments. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































