Internet Security
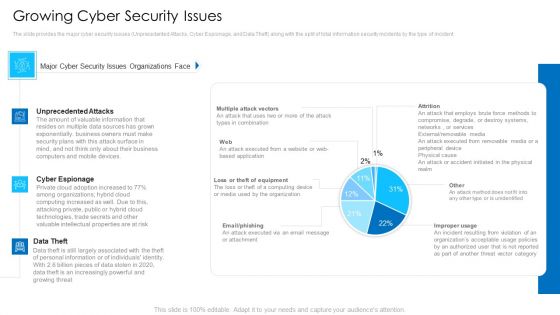
Growing Cyber Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative growing cyber security issues mockup pdf bundle. Topics like unprecedented attacks, cyber espionage, data theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Checklist Access Control Rules PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Presenting Cloud Security Checklist Access Control Rules PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Systems, Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information IT Security Communication Plan Guidelines PDF
This slide showcases an information cyber security communication plan to effectively communicate cyber incident and action plan. It includes cyber incidents such as virus, spyware, firewall hacking and phishing. Showcasing this set of slides titled Information IT Security Communication Plan Guidelines PDF. The topics addressed in these templates are Run Microsoft Defender Offline, Install Antivirus, Block Traffic Default. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
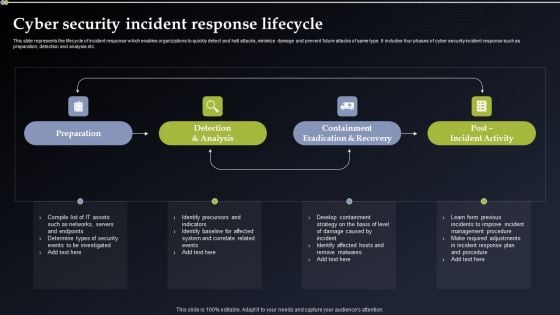
Cyber Security Incident Response Lifecycle Diagrams PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Incident Response Lifecycle Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
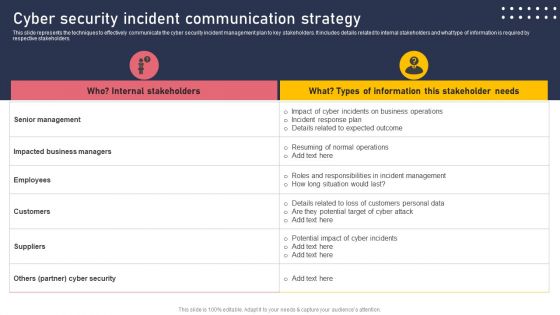
Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
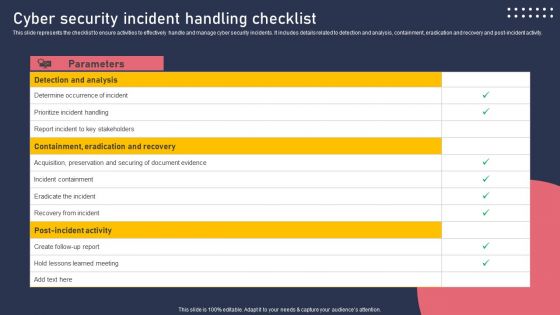
Cyber Security Incident Handling Checklist Information PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Welcome to our selection of the Cyber Security Incident Handling Checklist Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Cyber Security Half Yearly Strategic Timeline Icons
Presenting our innovatively structured cyber security half yearly strategic timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
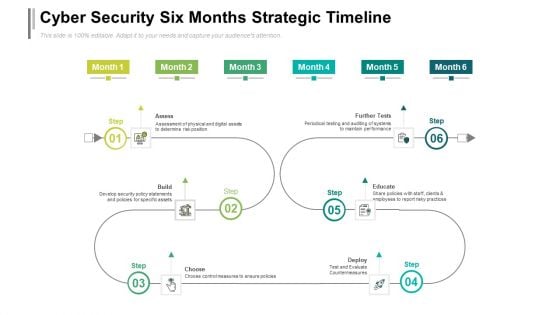
Cyber Security Six Months Strategic Timeline Designs
Introducing our cyber security six months strategic timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
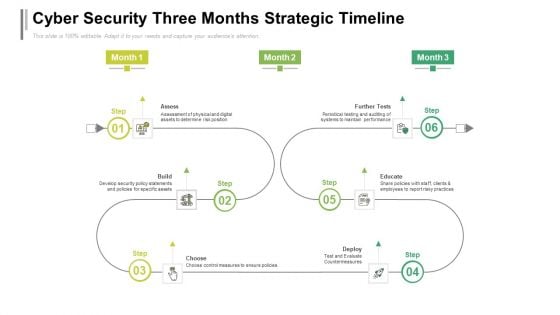
Cyber Security Three Months Strategic Timeline Sample
Presenting our jaw dropping cyber security three months strategic timeline sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
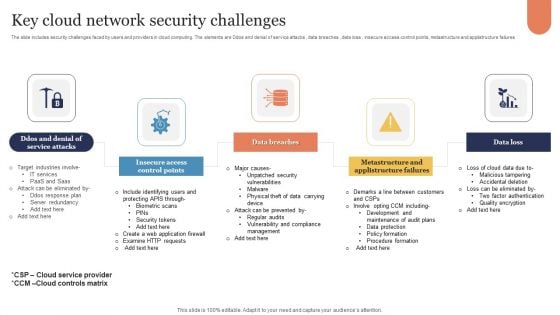
Key Cloud Network Security Challenges Sample PDF
The slide includes security challenges faced by users and providers in cloud computing. The elements are Ddos and denial of service attacks , data breaches , data loss , insecure access control points, metastructure and applistructure failures Persuade your audience using this Key Cloud Network Security Challenges Sample PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Insecure Access Control Points, Data Breaches, Data Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
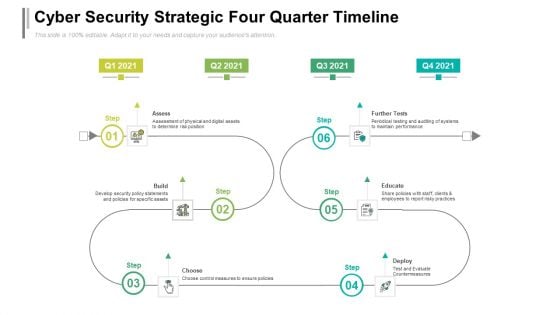
Cyber Security Strategic Four Quarter Timeline Formats
Presenting the cyber security strategic four quarter timeline formats. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
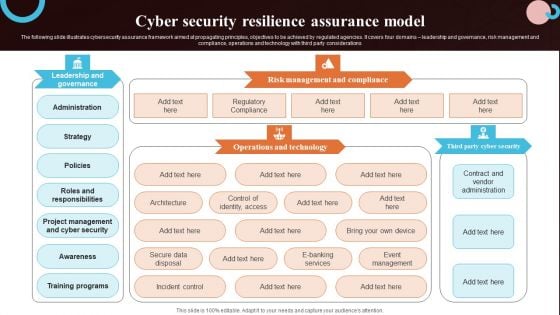
Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.
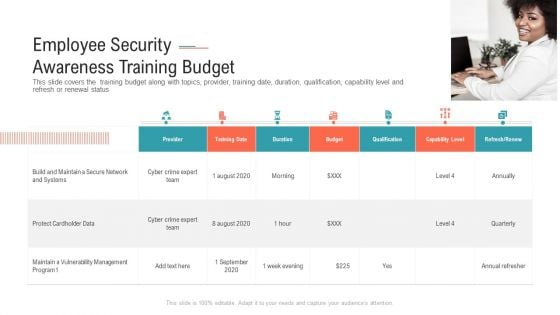
Employee Security Awareness Training Budget Sample PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status Presenting employee security awareness training budget sample pdf. to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like build and maintain a secure network and systems, protect cardholder data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Web Internet Safety PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Web Internet Safety PowerPoint Templates PPT Backgrounds For Slides 1212.Use our Business PowerPoint Templates because the fruits of your labour are beginning to show.Enlighten them on the great plans you have for their enjoyment. Present our Security PowerPoint Templates because it gives you really bright ideas. Download our Success PowerPoint Templates because your quest has taken you well onto the path of success. Download and present our Technology PowerPoint Templates because you can Present your views on the methods using our self-explanatory templates. Present our Internet PowerPoint Templates because the colour coding of our templates are specifically designed to highlight you points.Use these PowerPoint slides for presentations relating to Web safety, security, business, success, technology, internet. The prominent colors used in the PowerPoint template are Red, White, Blue. Customers tell us our Web Internet Safety PowerPoint Templates PPT Backgrounds For Slides 1212 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Presenters tell us our success PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Use our Web Internet Safety PowerPoint Templates PPT Backgrounds For Slides 1212 are Beautiful. PowerPoint presentation experts tell us our PowerPoint templates and PPT Slides are Handsome. Customers tell us our Web Internet Safety PowerPoint Templates PPT Backgrounds For Slides 1212 will help them to explain complicated concepts. Presenters tell us our security PowerPoint templates and PPT Slides are Exuberant. Bravely continue with your endeavour. Our Web Internet Safety PowerPoint Templates Ppt Backgrounds For Slides 1212 will keep the fight in you going.

Smart Home Security Solutions Company Profile Our Expertise Sample PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Our Expertise Sample PDF bundle. Topics like Integrated Control Devices, Internet Protocol Based, RFID Based Physical, Wireless Based Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Technology Domain Layout Powerpoint Slide Ideas
This is a internet technology domain layout powerpoint slide ideas. This is a fourteen stage process. The stages in this process are product management, security, erp, crm, wcdma, it infrastructure, rdbms, system software, embedded technology, technical trainer, semiconductor, application software, web technology, mainframe.

Internet Marketing Qualifications Diagram Powerpoint Slides
This is a internet marketing qualifications diagram powerpoint slides. This is a three stage process. The stages in this process are innovative, authentic internet marketing, authenticity, valuable information.
Internet Planning Diagram Powerpoint Slide Background Image
This is a internet planning diagram powerpoint slide background image. This is a eight stage process. The stages in this process are website, marketing, networking, server, blogs, blogging, seo, internet.

Internet Layouts Diagram Layout Ppt Inspiration
This is a internet layouts diagram layout ppt inspiration. This is a five stage process. The stages in this process are illustration, infographic, merchandise, ui design, print collateral.
Innovative Internet Ideas Diagram Ppt Images Gallery
This is a innovative internet ideas diagram ppt images gallery. This is a six stage process. The stages in this process are infrastructure, valuable, authenticity, operating, infrastructure, training.
Internet Marketing Media Sample Template Ppt Icon
This is a internet marketing media sample template ppt icon. This is a six stage process. The stages in this process are planning, social media, apps, site design, network, email.

Internet Marketing Best Practices Slides PDF
The following slide highlights best practices of digital advertising to recognize target audience, create relevant content etc. It includes components such as choose right audience, track performance, test and optimize and be authentic. Presenting Internet Marketing Best Practices Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Choose Right Audience, Track Performance, Test Optimize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Functioning Centre Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fifty six slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.
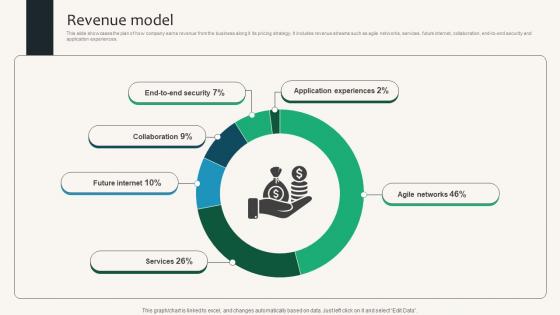
Revenue Model Security Service Provider Business Model BMC SS V
This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences. Find highly impressive Revenue Model Security Service Provider Business Model BMC SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Revenue Model Security Service Provider Business Model BMC SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences.
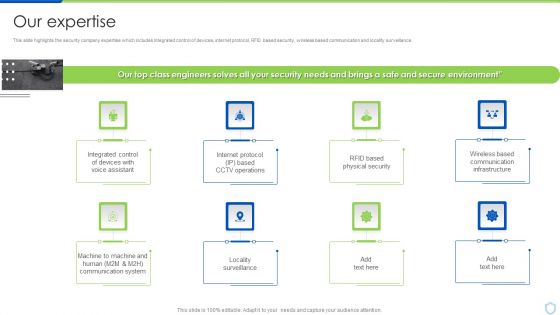
Security And Surveillance Company Profile Our Expertise Professional PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. Presenting Security And Surveillance Company Profile Our Expertise Professional PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Secure Environment, Communication Infrastructure, Physical Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
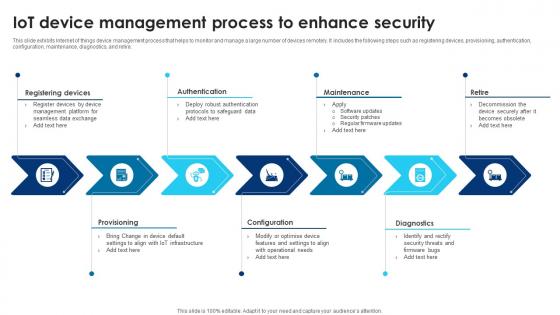
Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V
This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire. Are you searching for a Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Building Trust With IoT Security IoT Device Management Process To Enhance Security IoT SS V from Slidegeeks today. This slide exhibits Internet of things device management process that helps to monitor and manage a large number of devices remotely. It includes the following steps such as registering devices, provisioning, authentication, configuration, maintenance, diagnostics, and retire.

Electronic Voting System Voting System Standards Security Template PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection.Presenting Electronic Voting System Voting System Standards Security Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Manipulated Tampered, Ensuring Security, Security Include. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
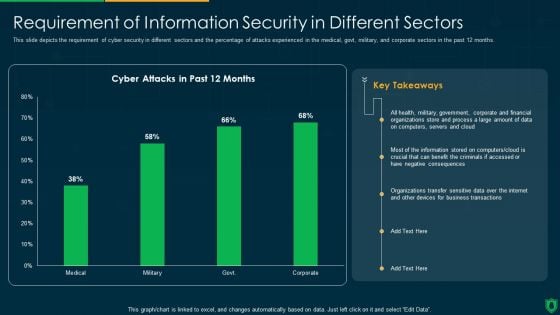
Info Security Requirement Of Information Security In Different Sectors Ppt PowerPoint Presentation File Grid PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative info security requirement of information security in different sectors ppt powerpoint presentation file grid pdf bundle. Topics like cyber attacks, past 12 months, organizations transfer, sensitive data over internet can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
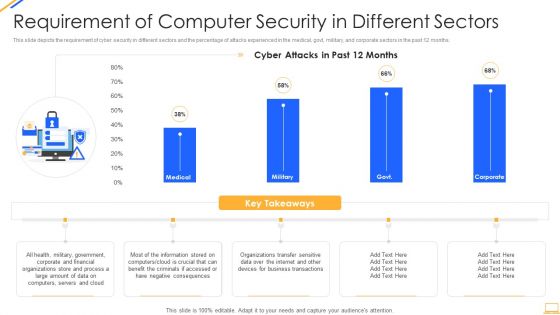
Desktop Security Management Requirement Of Computer Security In Different Sectors Sample PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this desktop security management requirement of computer security in different sectors sample pdf. Use them to share invaluable insights on information, organizations, financial, servers, internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
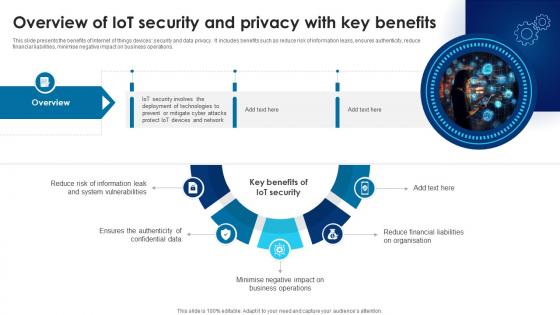
Building Trust With IoT Security Overview Of IoT Security And Privacy With Key Benefits IoT SS V
This slide presents the benefits of Internet of things devices security and data privacy. It includes benefits such as reduce risk of information leaks, ensures authenticity, reduce financial liabilities, minimise negative impact on business operations. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Overview Of IoT Security And Privacy With Key Benefits IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide presents the benefits of Internet of things devices security and data privacy. It includes benefits such as reduce risk of information leaks, ensures authenticity, reduce financial liabilities, minimise negative impact on business operations.
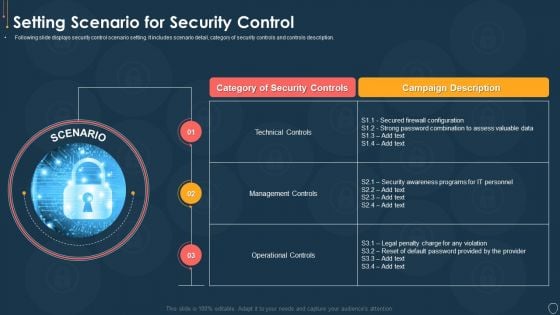
Cyber Security Risk Management Plan Setting Scenario For Security Control Microsoft PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. This is a cyber security risk management plan setting scenario for security control microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like category of security controls, campaign description, technical controls, management controls, operational controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF
The purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. Find highly impressive Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Organizing Security Awareness How Much Employees Are Aware Of Cyber Security Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
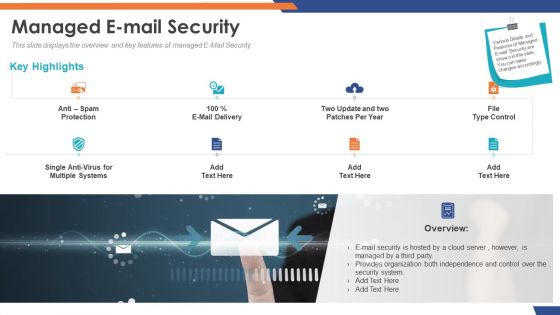
Email Security Market Research Report Managed E Mail Security Introduction PDF
Presenting this set of slides with name email security market research report managed e mail security introduction pdf. This is a two stage process. The stages in this process are e mail security is hosted by a cloud server, however is managed by a third party, provides organization both independence and control over the security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
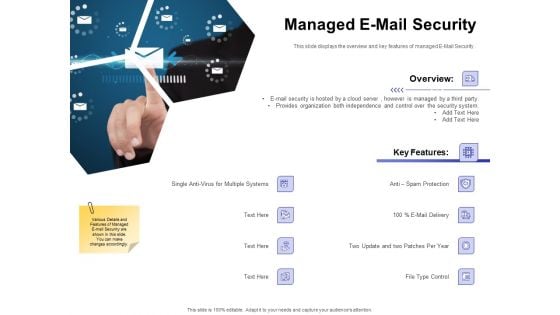
Global Cloud Based Email Security Market Managed E Mail Security Rules PDF
Presenting this set of slides with name global cloud based email security market managed e mail security rules pdf. This is a two stage process. The stages in this process are e mail security is hosted by a cloud server, however is managed by a third party, provides organization both independence and control over the security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
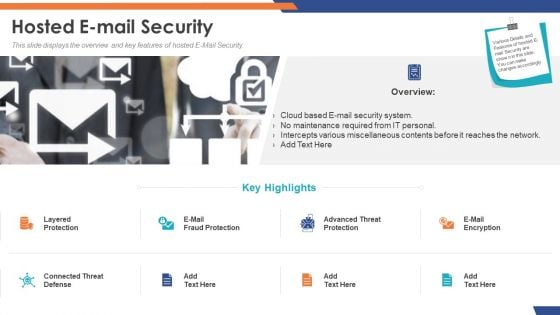
Email Security Market Research Report Hosted E Mail Security Formats PDF
Presenting this set of slides with name email security market research report hosted e mail security formats pdf. This is a two stage process. The stages in this process are cloud based e mail security system, no maintenance required from it personal, intercepts various miscellaneous contents before it reaches the network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Internet Browser Travel PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with a metallic lock dial inside window of internet browser Get an added advantage with our Internet Browser Travel PowerPoint Templates And PowerPoint Backgrounds 0211. Your thoughts will leap off the blocks.

Internet Browser Travel PowerPoint Themes And PowerPoint Slides 0211
Microsoft PowerPoint Theme and Slide with a metallic lock dial inside window of internet browser The corporate world can be fiercely competitive. Battle it out with our Internet Browser Travel PowerPoint Themes And PowerPoint Slides 0211.

Broken Link Internet PowerPoint Templates And PowerPoint Backgrounds 0411
Microsoft PowerPoint Template and Background with broken chain internet link and connection concept Start driving performance improvement with our Broken Link Internet PowerPoint Templates And PowerPoint Backgrounds 0411. They will make you look good.
Keyboard Symbol With Key Security PowerPoint Templates And PowerPoint Themes 0912
Keyboard Symbol With Key Security PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with computer keyboard with two security keys -Computer keyboard with two security keys, technology computer, internet, security, success Win trust with our Keyboard Symbol With Key Security PowerPoint Templates And PowerPoint Themes 0912. You will come out on top.

Data Recovery Internet PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with lifesaver floating in a binary data sea Conceive plans with our Data Recovery Internet PowerPoint Templates And PowerPoint Backgrounds 0511. Download without worries with our money back guaranteee.

Internet Dangers Computer PowerPoint Templates And PowerPoint Backgrounds 0611
Microsoft PowerPoint Template and Background with render of a skull and crossbones of binary digits Erroneous beliefs can be a bane. Be correct and accurate with our Internet Dangers Computer PowerPoint Templates And PowerPoint Backgrounds 0611.

Data Recovery Internet PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with lifesaver floating in a binary data sea Acquire a feel for it all with our Data Recovery Internet PowerPoint Themes And PowerPoint Slides 0511. They put you in your comfort zone.

Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V
This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Categorization Of IoT Architecture Security Concerns IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide consists of security concerns in each IoT architecture layer that helps to deploy a more secure security framework. It includes various security concerns such as insecure web interface, insufficient data authentication, insecure network services, etc.
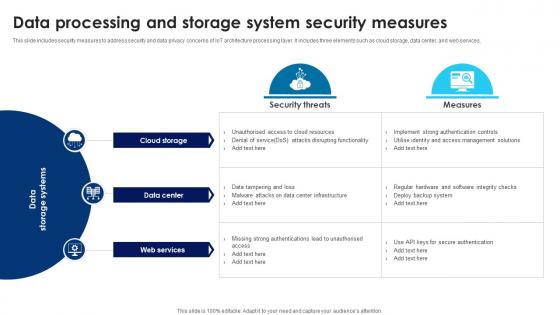
Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V
This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services.

Overview Of Secure Access Service Edge Network Security Download Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Boost your pitch with our creative Overview Of Secure Access Service Edge Network Security Download Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Overview Of Secure Access Service Edge Network Security Download Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
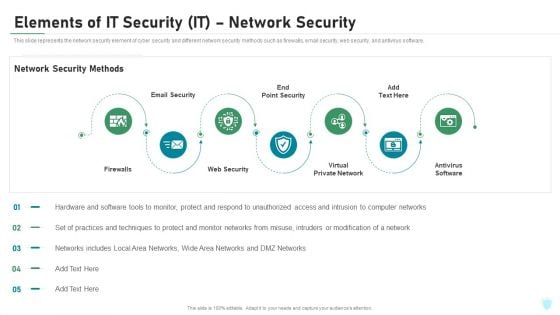
Elements Of IT Security IT Network Security Ppt Pictures Ideas PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a elements of it security it network security ppt pictures ideas pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like firewalls, email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
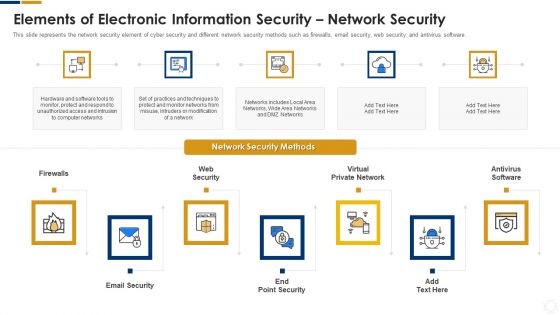
Cybersecurity Elements Of Electronic Information Security Network Security Ppt Ideas Skills PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a cybersecurity elements of electronic information security network security ppt ideas skills pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Yellow Computer Folder With-key Internet PowerPoint Templates And PowerPoint Themes 1112
We present our Yellow Computer Folder With-Key Internet PowerPoint Templates And PowerPoint Themes 1112.Use our Computer PowerPoint Templates because, Different people with differing ideas and priorities perform together to score. Use our Internet PowerPoint Templates because, Our template will help pinpoint their viability. Use our Communication PowerPoint Templates because, Use our creative template to lay down your views. Use our Security PowerPoint Templates because, Gears Interconnected:- The Gear Train is a basic element of living and daily business. Use our Symbol PowerPoint Templates because,Use our templates for your colleagues knowledge to feed.Use these PowerPoint slides for presentations relating to Yellow computer folder with key Internet Security Computer Symbol Communication. The prominent colors used in the PowerPoint template are Yellow, White, Brown No end is too far for our Yellow Computer Folder With-key Internet PowerPoint Templates And PowerPoint Themes 1112. They ensure your thoughts always arrive.
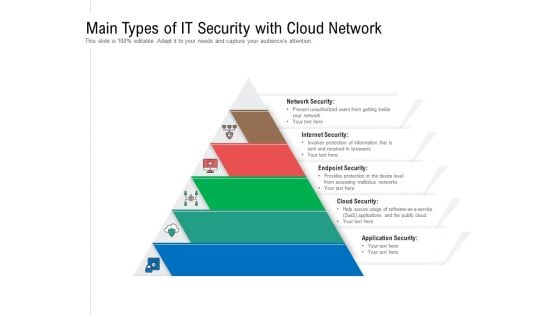
Main Types Of IT Security With Cloud Network Ppt PowerPoint Presentation Gallery Design Ideas PDF
Persuade your audience using this main types of it security with cloud network ppt powerpoint presentation gallery design ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including network security, internet security, endpoint security, cloud security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF
Showcasing this set of slides titled Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF. The topics addressed in these templates are Endpoint Security, Network Security, Messaging Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
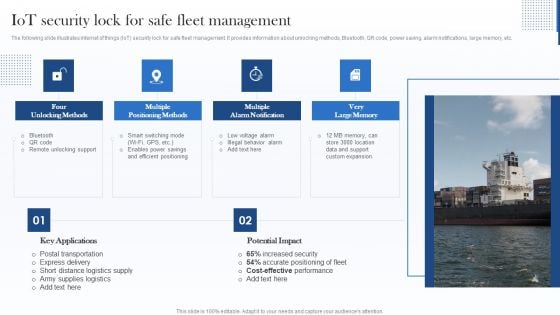
Iot Security Lock For Safe Fleet Management Sample PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
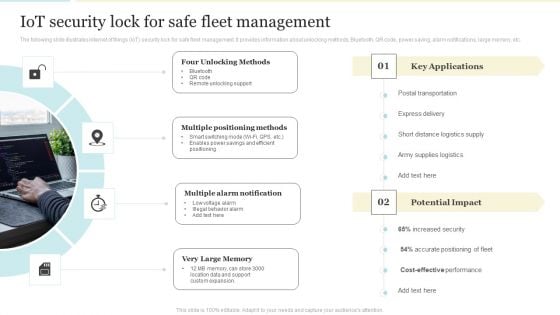
Iot Security Lock For Safe Fleet Management Mockup PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Mockup PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
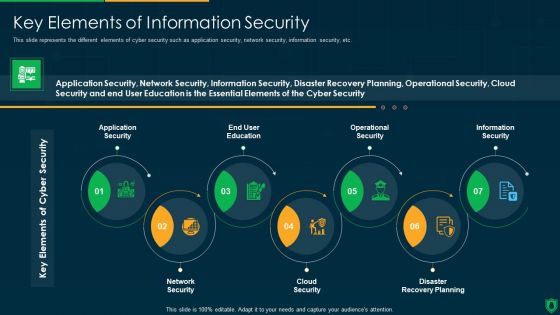
Info Security Key Elements Of Information Security Ppt PowerPoint Presentation Gallery Slide Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. Presenting info security key elements of information security ppt powerpoint presentation gallery slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like application security, end user education, operational security, information security, network security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
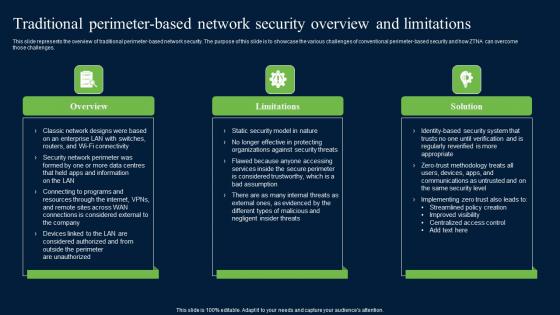
Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Find highly impressive Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Traditional Perimeter Based Network Security Zero Trust Network Security Structure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges.

Strategies To Mitigate Cyber Security Risks Cyber Security Governance Ppt Styles Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cyber security governance ppt styles model pdf. This is a one stage process. The stages in this process are senior management, steering committee and executive management, ciso steering committee, business strategy, risk management, information, security strategy, security action plan, policies, standards organisation, objectives security requirements, security programs, implementation, security objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
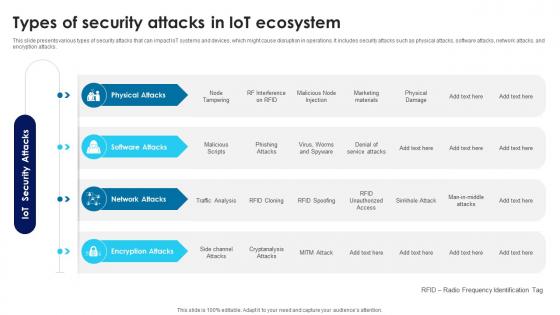
Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V
This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks.

Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V
This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V from Slidegeeks and deliver a wonderful presentation. This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc.
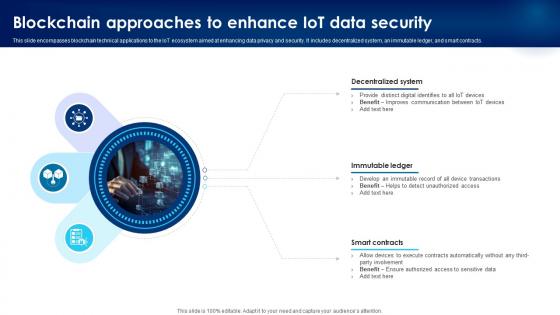
Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V
This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts.


 Continue with Email
Continue with Email

 Home
Home


































