Iot Security
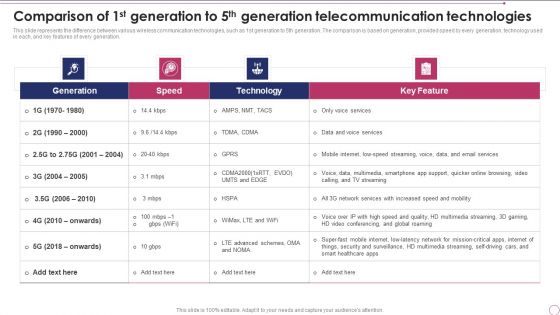
Comparison Of 1St Generation To 5Th Generation Telecommunication Technologies Template PDF
This slide represents the difference between various wireless communication technologies, such as 1st generation to 5th generation. The comparison is based on generation, provided speed by every generation, technology used in each, and key features of every generation. Deliver and pitch your topic in the best possible manner with this Comparison Of 1St Generation To 5Th Generation Telecommunication Technologies Template PDF. Use them to share invaluable insights on Technology, Network Services, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
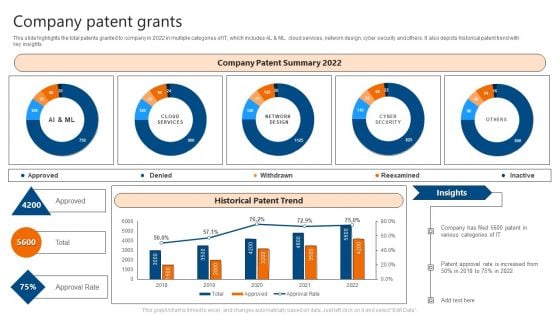
Company Patent Grants IT Software Development Company Profile Introduction PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver and pitch your topic in the best possible manner with this Company Patent Grants IT Software Development Company Profile Introduction PDF. Use them to share invaluable insights on Company Patent Summary, Historical Patent Trend and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Initiatives To Produce Effective Concept For Logistic Firm Risks Involved In Technology Formats PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high and Key Strategies or Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this initiatives to produce effective concept for logistic firm risks involved in technology formats pdf. Use them to share invaluable insights on connectivity risk, cyber security risk, inventory management risk, technology risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
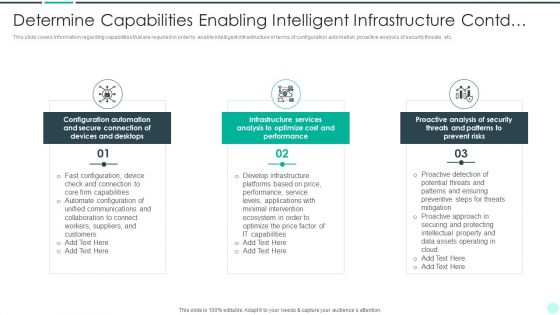
Executing Advance Data Analytics At Workspace Determine Capabilities Enabling Sample PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. Presenting executing advance data analytics at workspace determine capabilities enabling sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like capabilities, connection, communications, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
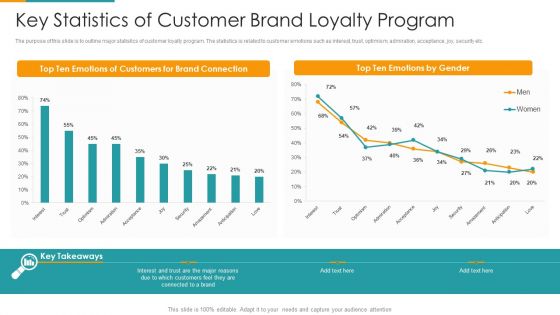
Key Statistics Of Customer Brand Loyalty Program Ppt PowerPoint Presentation File Background Image PDF
The purpose of this slide is to outline major statistics of customer loyalty program. The statistics is related to customer emotions such as interest, trust, optimism, admiration, acceptance, joy, security etc. Showcasing this set of slides titled key statistics of customer brand loyalty program ppt powerpoint presentation file background image pdf. The topics addressed in these templates are top ten emotions, customers for brand connection, top ten emotions by gender. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
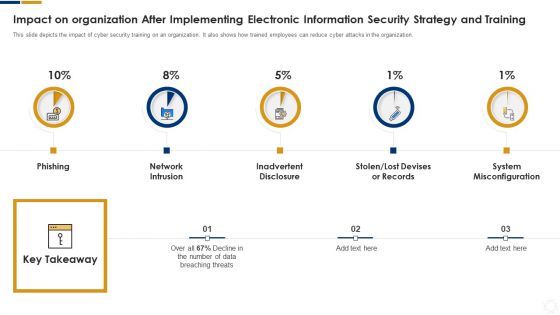
Cybersecurity Impact On Organization After Implementing Ppt Summary Influencers PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Presenting cybersecurity impact on organization after implementing ppt summary influencers pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network intrusion, inadvertent disclosure, system misconfiguration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Recognition Automation Need For Siem Software In Your Company Ppt Styles Gridlines PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management This is a risk recognition automation need for siem software in your company ppt styles gridlines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
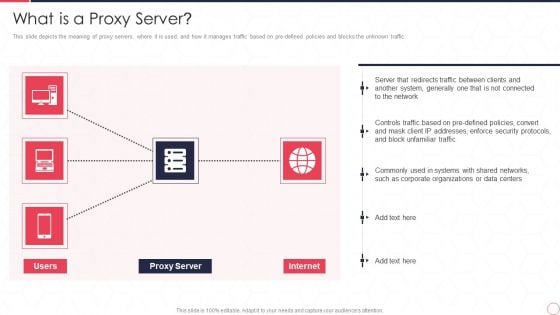
Reverse Proxy Server IT What Is A Proxy Server Ppt Infographics Infographics PDF
This slide depicts the meaning of proxy servers, where it is used, and how it manages traffic based on pre-defined policies and blocks the unknown traffic. This is a reverse proxy server it what is a proxy server ppt infographics infographics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, unfamiliar traffic, enforce security protocols, controls traffic based. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
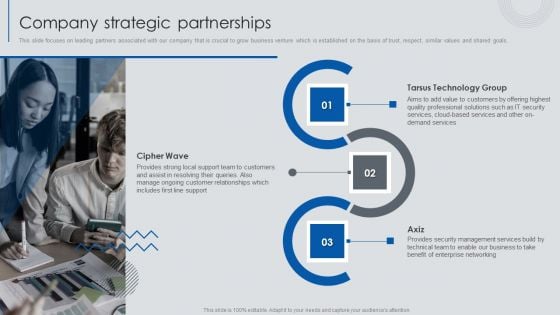
Information Technology Solutions Business Profile Company Strategic Partnerships Structure PDF
This slide focuses on leading partners associated with our company that is crucial to grow business venture which is established on the basis of trust, respect, similar values and shared goals.This is a Information Technology Solutions Business Profile Company Strategic Partnerships Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Quality Professional, Security Management, Enterprise Networking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

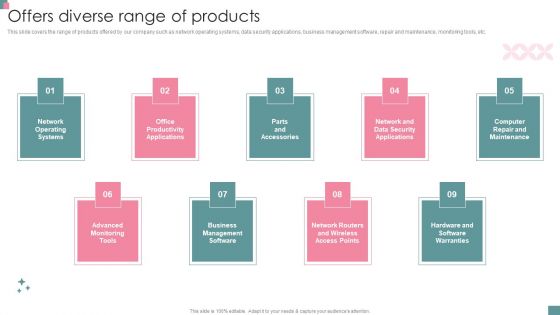
Information Technology Solutions Business Profile Offers Diverse Range Of Products Themes PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a Information Technology Solutions Business Profile Offers Diverse Range Of Products Themes PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operating Systems, Productivity Applications, Parts Accessories. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Small Business Venture Company Profile Offers Diverse Range Of Products Clipart PDF
This slide covers the range of products offered by our company such as network operating systems, data security applications, business management software, repair and maintenance, monitoring tools, etc.This is a Small Business Venture Company Profile Offers Diverse Range Of Products Clipart PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Operating Systems, Advanced Monitoring, Management Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
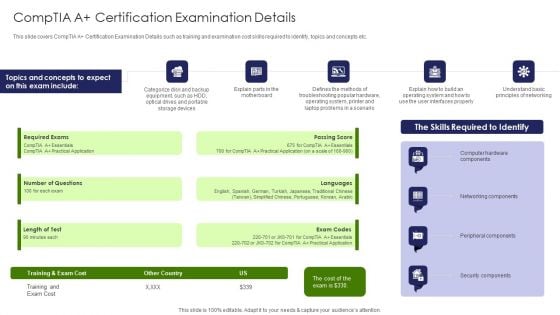
IT Professional Data Certification Program Comptia A Certification Examination Details Ideas PDF
This slide covers CompTIA A Certification Examination Details such as training and examination cost skills required to identify, topics and concepts etc. This is a IT Professional Data Certification Program Comptia A Certification Examination Details Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Networking Components, Security Components, Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Difference Between ZTNA And Software Defined Perimeter Diagrams PDF
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Make sure to capture your audiences attention in your business displays with our gratis customizable Difference Between ZTNA And Software Defined Perimeter Diagrams PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.
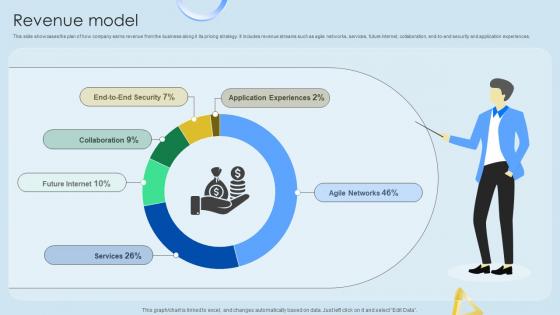
Revenue Model Cloud Networking Service Provider Business Model BMC SS V
This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences. Find highly impressive Revenue Model Cloud Networking Service Provider Business Model BMC SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Revenue Model Cloud Networking Service Provider Business Model BMC SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
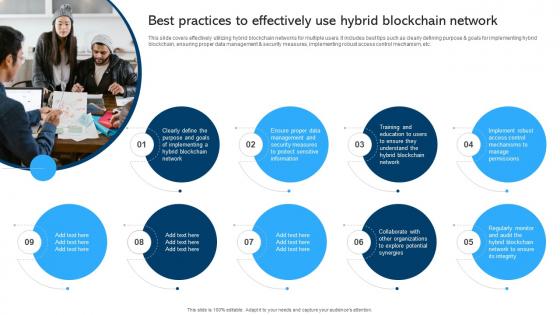
Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V
This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc. Welcome to our selection of the Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.
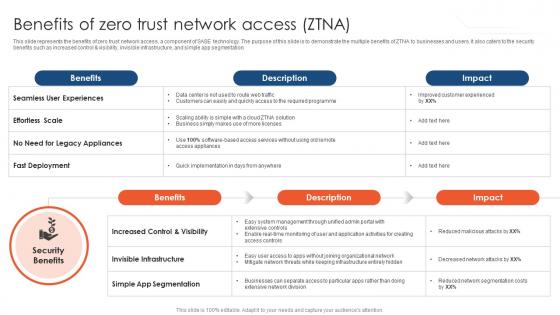
Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Benefits Of Zero Trust Network Access ZTNA that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Zero Trust Model Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Steps To Implement Zero Trust Network Access Model With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc.

Zero Trust Model Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Get a simple yet stunning designed Zero Trust Model Benefits Of Zero Trust Network Access ZTNA. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Benefits Of Zero Trust Network Access ZTNA can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
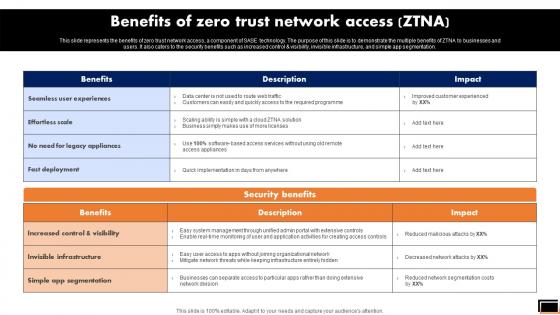
Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
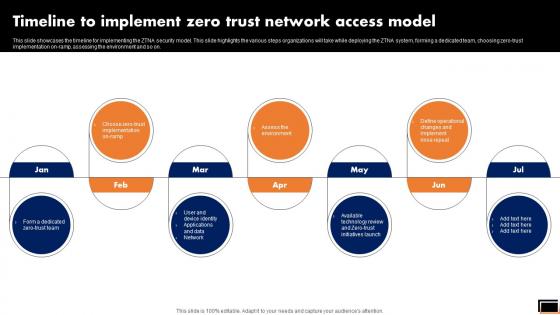
Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
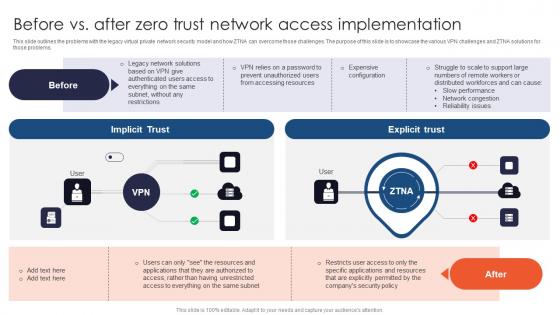
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Healthcare Information Technology Healthcare Information Tech Enhance Medical Facilities Professional Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Healthcare Information Technology Healthcare Information Tech Enhance Medical Facilities Professional Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
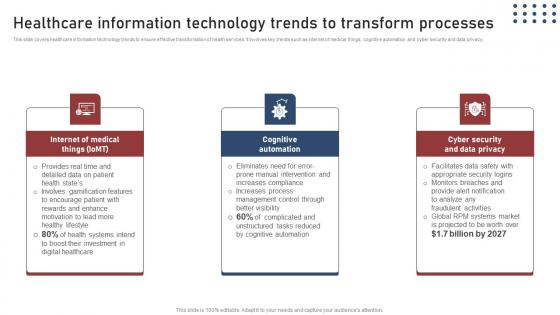
Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.

Improving Customer Satisfaction Essential Personnel Required For Digital Transformation
The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists. This Improving Customer Satisfaction Essential Personnel Required For Digital Transformation is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Improving Customer Satisfaction Essential Personnel Required For Digital Transformation features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists.
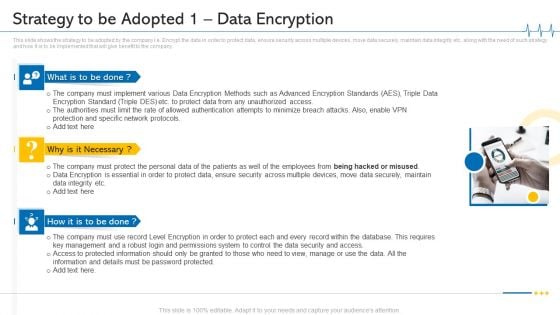
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 1 Data Encryption Microsoft PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting minimize cloud risks medical care business case competition strategy to be adopted 1 data encryption microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protection And Specific Network Protocols, Protect Data, Permissions System, Key Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
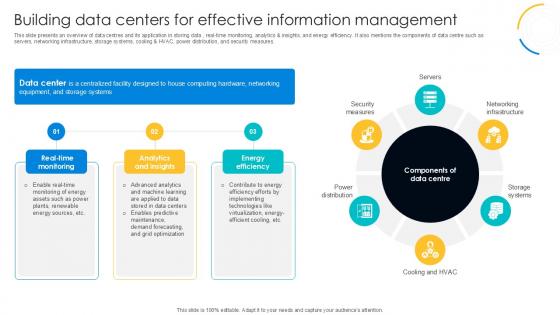
Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V
This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures. If you are looking for a format to display your unique thoughts, then the professionally designed Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures.

Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF
This slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Laptop With Key Chain Business PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Laptop With Key Chain Business PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Internet PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Present our Computer PowerPoint Templates because You can Stir your ideas in the cauldron of our PowerPoint Templates and Slides. Cast a magic spell on your audience. Download our Finance PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download our Money PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Download our Communication PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to Laptop security keychain, internet, computer, security, finance, communication. The prominent colors used in the PowerPoint template are Black, Yellow, Gray. Many factors can create a distraction. Our Laptop With Key Chain Business PowerPoint Templates Ppt Backgrounds For Slides 0213 will not let them fall for it.

Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V
This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc. Get a simple yet stunning designed Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc.
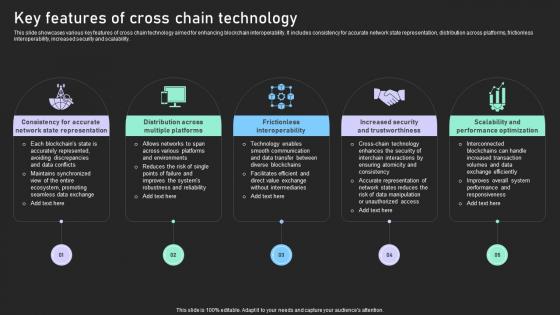
Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.
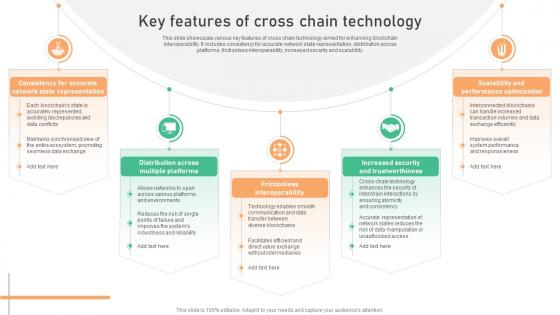
Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Are you searching for a Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V from Slidegeeks today. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.

Zero Trust Model Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Difference Between ZTNA And Software Defined Perimeter and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
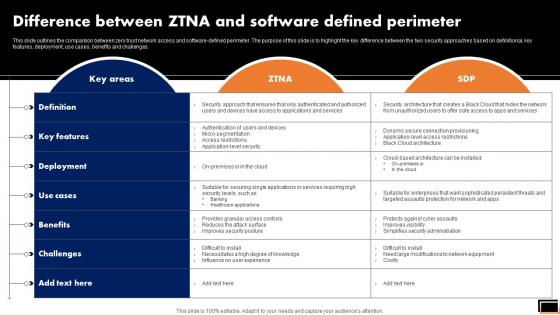
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
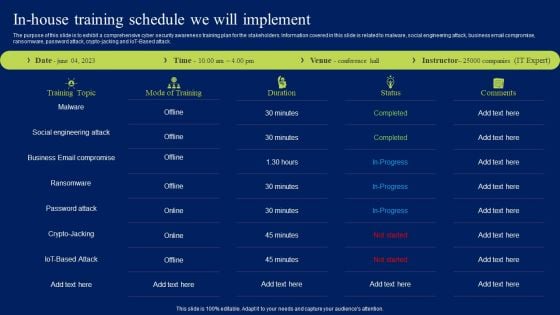
In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112
Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112-Use our Security PowerPoint Templates because, Present your views using our innovative slides and be assured of leaving a lasting impression. Use our Arrows PowerPoint Templates because; Help them develop their thoughts along the way. Use our Business PowerPoint Templates because; emphasize the process of your business/corporate growth. Use our Computer PowerPoint Templates because, Clarity of thought has been the key to your growth. Use our Internet PowerPoint Templates because; transmit this concern to your staff using our helpful slides.-Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-Upload download folder icon, Computer, Arrows, Symbol, Internet, Business Environmental awareness is the call to answer. Our Upload Download Folder Internet PowerPoint Templates And PowerPoint Themes 1112 will fit the bill.
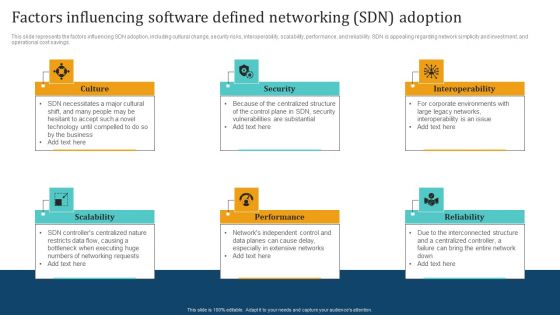
Empowering Network Agility Through SDN Factors Influencing Software Defined Networking SDN Adoption Slides PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Empowering Network Agility Through SDN Factors Influencing Software Defined Networking SDN Adoption Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Empowering Network Agility Through SDN Factors Influencing Software Defined Networking SDN Adoption Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
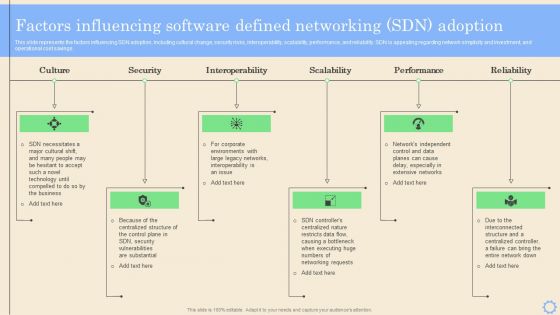
Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Software Defined Networking Development Strategies Factors Influencing Software Defined Networking Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

IT Policies And Procedures Internet Usage Policy Password Guidelines Microsoft PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. Explore a selection of the finest IT Policies And Procedures Internet Usage Policy Password Guidelines Microsoft PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our IT Policies And Procedures Internet Usage Policy Password Guidelines Microsoft PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. This Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
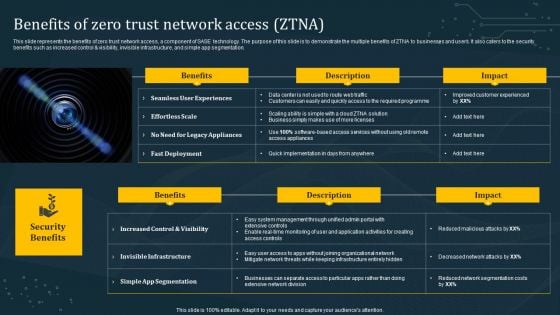
Benefits Of Zero Trust Network Access ZTNA Download PDF
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Present like a pro with Benefits Of Zero Trust Network Access ZTNA Download PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Zero Trust Network Access Architectural Models Diagrams PDF
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Are you searching for a Zero Trust Network Access Architectural Models Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Architectural Models Diagrams PDF from Slidegeeks today.
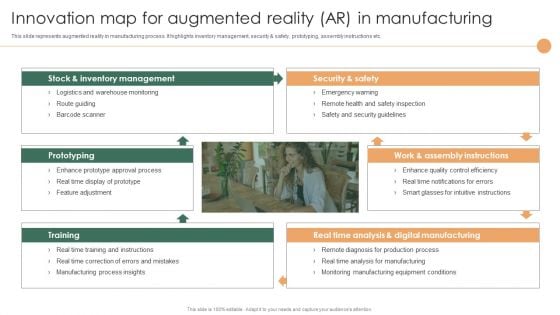
Smart Manufacturing Deployment Improve Production Procedures Innovation Map For Augmented Reality Summary PDF
This slide represents augmented reality in manufacturing process. It highlights inventory management, security safety, prototyping, assembly instructions etc.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Smart Manufacturing Deployment Improve Production Procedures Innovation Map For Augmented Reality Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Smart Manufacturing Deployment Improve Production Procedures Innovation Map For Augmented Reality Summary PDF.

Roadmap To Implement Zero Trust Network Access Model Structure PDF
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Want to ace your presentation in front of a live audience Our Roadmap To Implement Zero Trust Network Access Model Structure PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Zero Trust Network Access Implementation Challenges Rules PDF
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Implementation Challenges Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Implementation Challenges Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Implementation Challenges Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
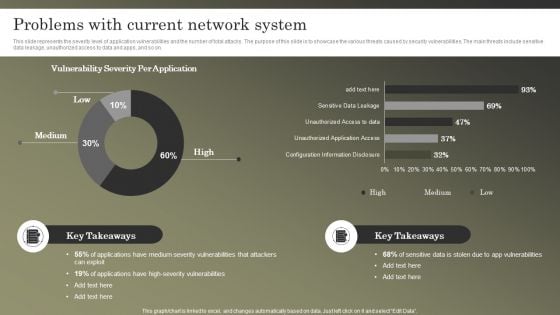
Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
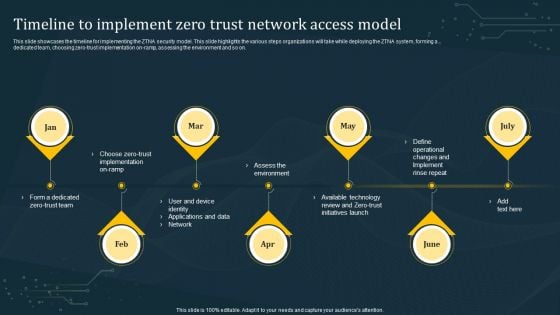
Timeline To Implement Zero Trust Network Access Model Rules PDF
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline To Implement Zero Trust Network Access Model Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline To Implement Zero Trust Network Access Model Rules PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
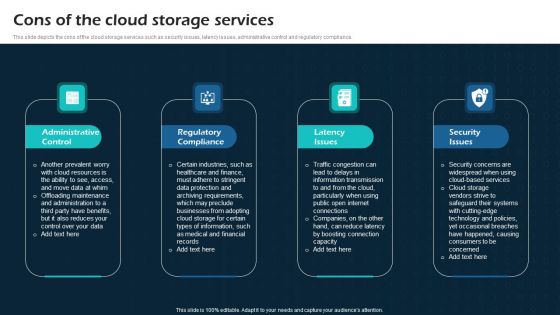
Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF
This slide depicts the cons of the cloud storage services such as security issues, latency issues, administrative control and regulatory compliance. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cons Of The Cloud Storage Services Virtual Cloud Network IT Ppt Show Good PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Incorporating HIS To Enhance Healthcare Services Healthcare Information Technology Trends To Transform Processes Professional PDF
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Incorporating HIS To Enhance Healthcare Services Healthcare Information Technology Trends To Transform Processes Professional PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Incorporating HIS To Enhance Healthcare Services Healthcare Information Technology Trends To Transform Processes Professional PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Factors Influencing Software Defined Networking SDN Adoption Ppt Portfolio Pictures PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged Factors Influencing Software Defined Networking SDN Adoption Ppt Portfolio Pictures PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
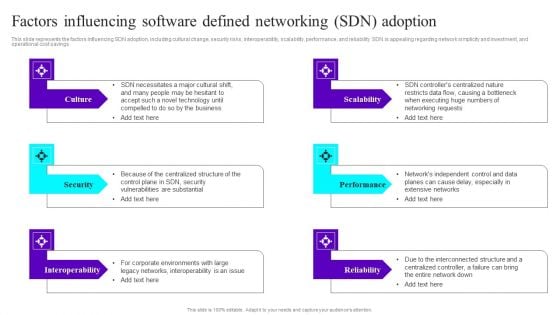
Factors Influencing Software Defined Networking SDN Adoption Ppt Summary Grid PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged Factors Influencing Software Defined Networking SDN Adoption Ppt Summary Grid PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
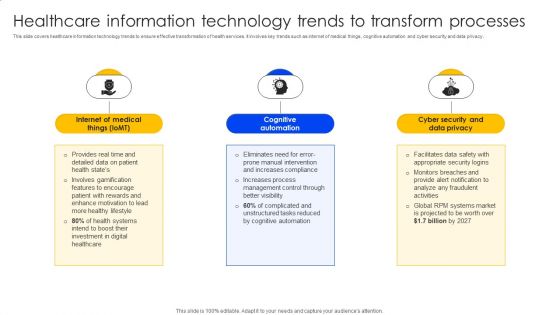
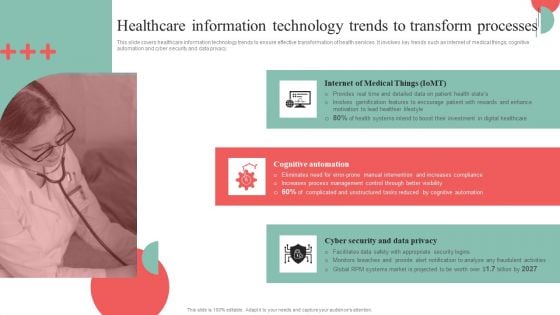
Healthcare Information Technology Trends To Transform Processes Formats PDF
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. This Healthcare Information Technology Trends To Transform Processes Formats PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
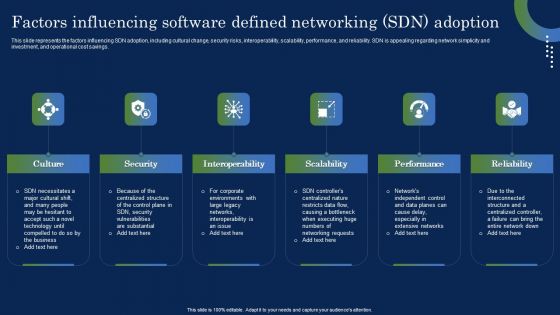
Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying SDN System Factors Influencing Software Defined Networking SDN Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.


 Continue with Email
Continue with Email

 Home
Home


































