It Security Roadmap
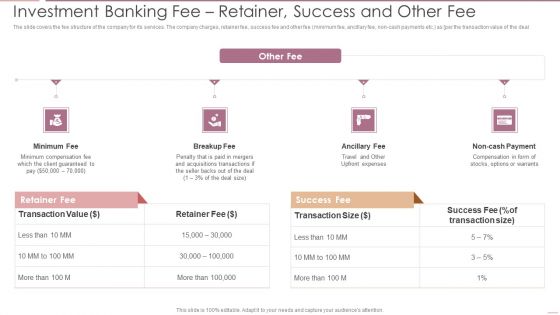
Investment Banking Security Underwriting Pitchbook Investment Banking Feer Retainer Success Demonstration PDF
The slide covers the fee structure of the company for its services. The company charges, retainer fee, success fee and other fee minimum fee, ancillary fee, non cash payments etc. as per the transaction value of the deal.This is a Investment Banking Security Underwriting Pitchbook Investment Banking Feer Retainer Success Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Minimum Compensation, Acquisitions Transactions, Compensation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How Is Automation Used In Cybersecurity IT Security IT Ppt Topics PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. This is a how is automation used in cybersecurity it security it ppt topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat detection, threat response, human augmentation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement Share Allocation Process Clipart PDF
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. Presenting financing catalogue for security underwriting agreement share allocation process clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like in case undersubscription, in case of oversubscription. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
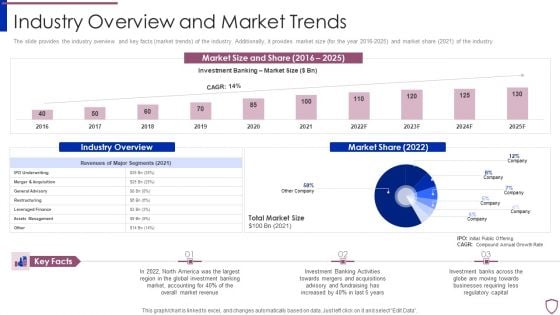
Financing Catalogue For Security Underwriting Agreement Industry Overview And Market Trends Introduction PDF
The slide provides the industry overview and key facts market trends of the industry. Additionally, it provides market size for the year 2016-2025 and market share 2021 of the industry. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement industry overview and market trends introduction pdf bundle. Topics like assets management, leveraged finance, restructuring, general advisory, merger and acquisition can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
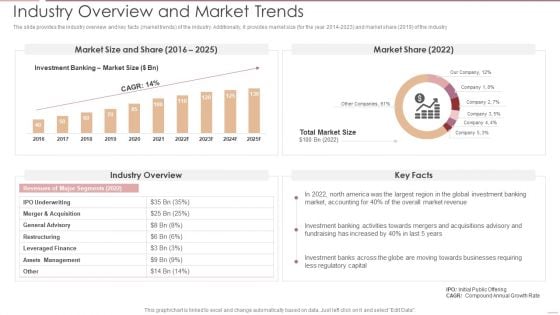
Investment Banking Security Underwriting Pitchbook Industry Overview And Market Trends Ideas PDF
The slide provides the industry overview and key facts market trends of the industry. Additionally, it provides market size for the year 2014 to 202 and market share 2019 of the industry.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Industry Overview And Market Trends Ideas PDF Use them to share invaluable insights on Assets Management, Leveraged Finance, Restructuring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Evaluating Financial Practices In Firm Graphics PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. This is a corporate security and risk management evaluating financial practices in firm graphics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluating financial practices in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
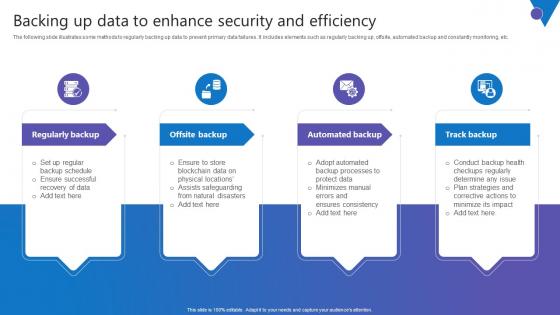
Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf
The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf. The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc.
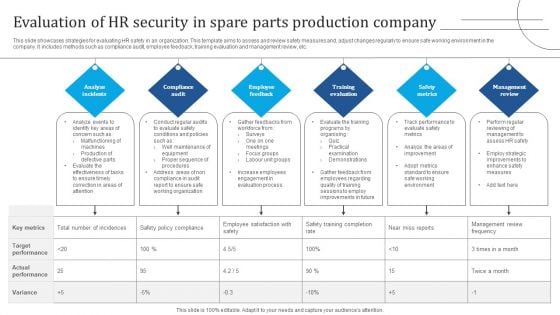
Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF
This slide showcases strategies for evaluating HR safety in an organization. This template aims to assess and review safety measures and, adjust changes regularly to ensure safe working environment in the company. It includes methods such as compliance audit, employee feedback, training evaluation and management review, etc. Presenting Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Analyze Incidents, Compliance Audit, Employee Feedback. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
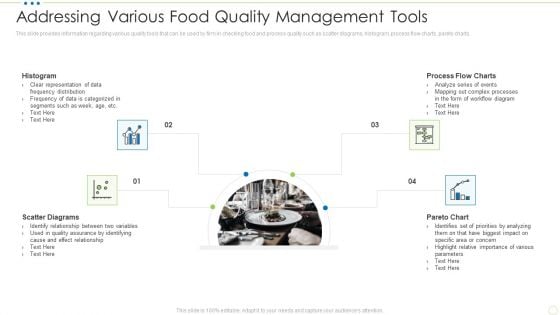
Addressing Various Food Quality Management Tools Food Security Excellence Ppt Inspiration Example PDF
This slide provides information regarding various quality tools that can be used by firm in checking food and process quality such as scatter diagrams, histogram, process flow charts, pareto charts. This is a addressing various food quality management tools food security excellence ppt inspiration example pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like scatter diagrams, histogram, process flow charts, pareto chart. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
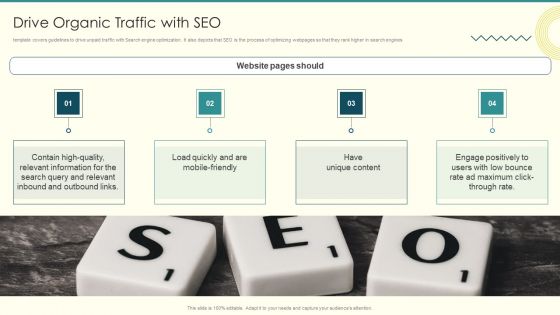
Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF
template covers guidelines to drive unpaid traffic with Search engine optimization. It also depicts that SEO is the process of optimizing webpages so that they rank higher in search engines.Presenting Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Relevant Information, Inbound Outbound, Engage Positively. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
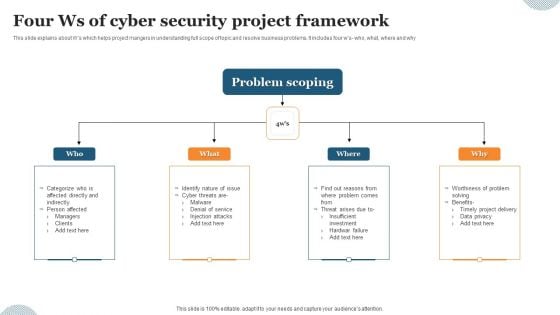
Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF
This slide explains about Ws which helps project mangers in understanding full scope of topic and resolve business problems. It includes four ws- who, what, where and why. Presenting Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Problem Scoping, Denial Service, Injection Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
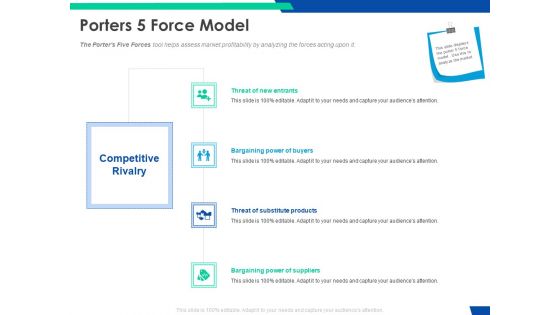
Cloud Based Email Security Market Report Porters 5 Force Model Ppt Inspiration Sample PDF
The Porters Five Forces tool helps assess market profitability by analyzing the forces acting upon it. This is a cloud based email security market report porters 5 force model ppt inspiration sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat of new entrants, bargaining power of buyers, threat of substitute products, bargaining power of suppliers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
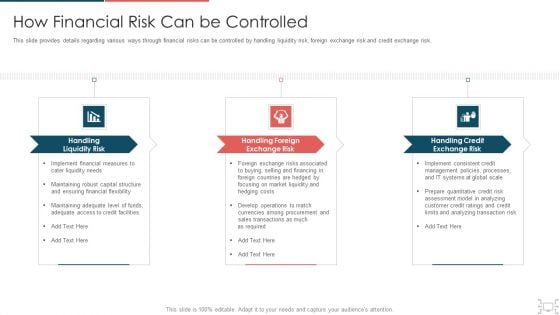
cyber security administration in organization how financial risk can be controlled inspiration pdf
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. This is a cyber security administration in organization how financial risk can be controlled inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like handling, liquidity, financial, flexibility, structure . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
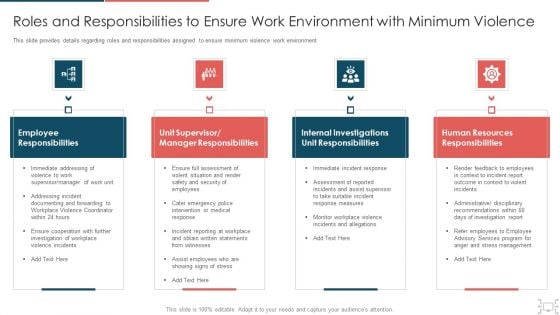
cyber security administration in organization roles and responsibilities to ensure work environment slides pdf
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a cyber security administration in organization roles and responsibilities to ensure work environment slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsibilities, manager, assessment, manager. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
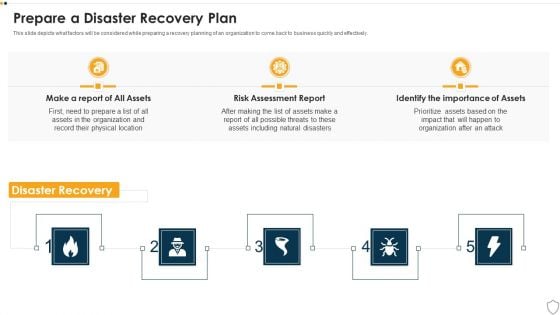
IT Security Prepare A Disaster Recovery Plan Ppt Show Templates PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a it security prepare a disaster recovery plan ppt show templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a report of all assets, risk assessment report, identify the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF
This template covers first step for LinkedIn marketing such as update company profile and position the company account according to the target audience. This is a Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Profiles Position, Target Audience, Account According. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF
This template covers content creation tactics in account based marketing such as launching multi touch campaigns, use of marketing automated tools etc.This is a Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Campaign Launch, Campaign Workflow, Ensure Prospects. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF
This template covers search engine optimization guidelines for images. It also depicts that Alt Attributes must be added at backend of the images to assists search engine crawlers in indexing. This is a Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Descriptions, Search Engine, Assisting Indexing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF
This template depicts that Facebook Ads needs three parts to run such as a campaign, ad set, and ad. All these parts are called campaign structure and help run ads the way the company wants and reach the right prospects.his is a Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Powerful Consisting, Features Campaigns, Define Creative. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
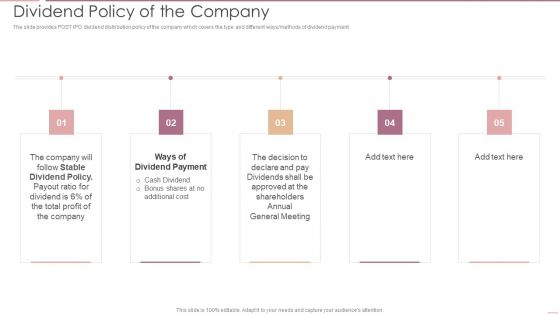
Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF
The slide provides POST IPO dividend distribution policy of the company which covers the type and different ways methods of dividend payment.Presenting Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Stable Dividend, Dividend Payment, General Meeting In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF
This template covers account based marketing strategy such as create content that provide value to the customers. It also depicts that Different types of target accounts require additional content focuses.Presenting Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Competitors Customers, Strategic Importance, Different. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
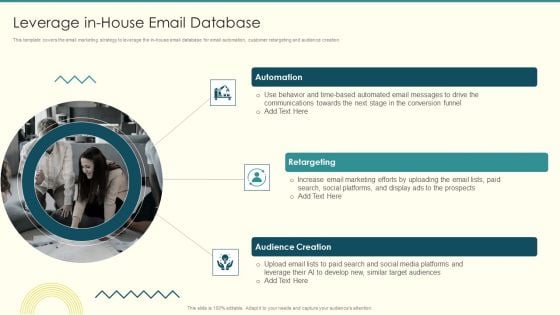
Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF
This template covers the email marketing strategy to leverage the in house email database for email automation, customer retargeting and audience creation. Presenting Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Communications Towards, Automated Messages, Social Platforms. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
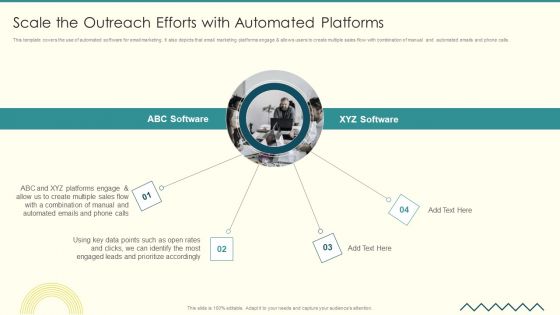
Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF
This template covers the use of automated software for email marketing. It also depicts that email marketing platforms engage allows users to create multiple sales flow with combination of manual and automated emails and phone calls.Presenting Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Combination Manual, Leads Prioritize, Identify Most. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
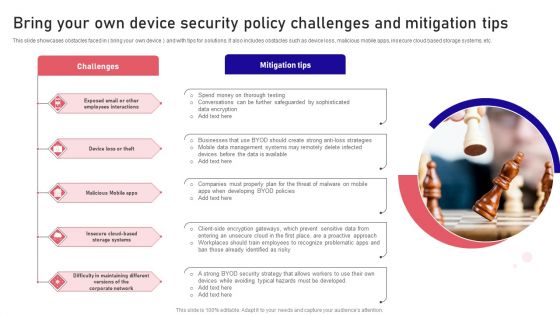
Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF
This slide showcases obstacles faced in bring your own device and with tips for solutions. It also includes obstacles such as device loss, malicious mobile apps, insecure cloud based storage systems, etc. Presenting Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Challenges, Mitigation Tips, Malicious Mobile. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
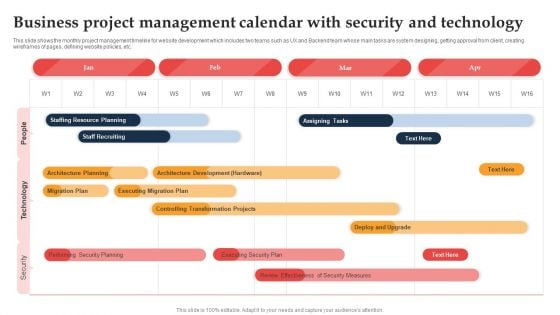
Business Project Management Calendar With Security And Technology Ppt Outline Clipart PDF
This slide shows the monthly project management timeline for website development which includes two teams such as UX and Backend team whose main tasks are system designing, getting approval from client, creating wireframes of pages, defining website policies, etc. Showcasing this set of slides titled Business Project Management Calendar With Security And Technology Ppt Outline Clipart PDF. The topics addressed in these templates are Staffing Resource Planning, Staff Recruiting, Architecture Planning. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF
This slide covers key elements of cybersecurity awareness training program. It involves elements such as make message relevant, use real world examples, common language, present small messages and use continued reinforcement. Presenting Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Make Message Relevant, Use Examples, Use Common Language. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Get a simple yet stunning designed How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc.

Cyber Security Administration In Organization Various Types Of Workplace Violence And Threats Inspiration PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber security administration in organization various types of workplace violence and threats inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical, threatening, behavior, stalking, harassment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
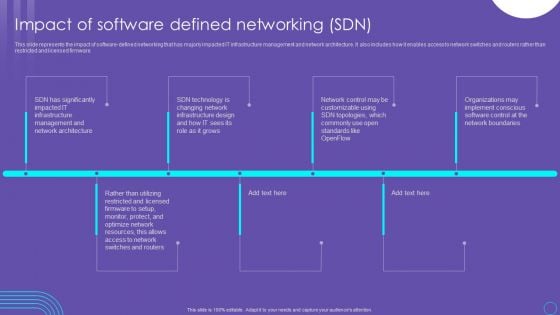
SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF
This slide represents the impact of software defined networking that has majorly impacted IT infrastructure management and network architecture. It also includes how it enables access to network switches and routers rather than restricted and licensed firmware. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download SDN Security Architecture Impact Of Software Defined Networking SDN Guidelines PDF from Slidegeeks and deliver a wonderful presentation.
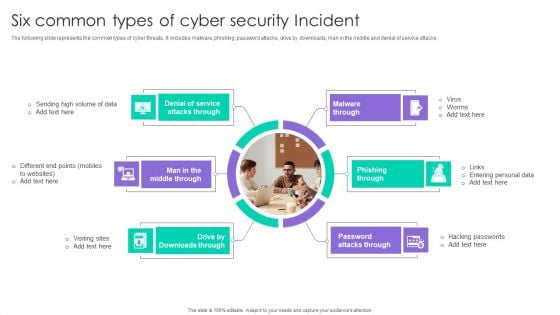
Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF
The following slide represents the common types of cyber threats. It includes malware, phishing, password attacks, drive by downloads, man in the middle and denial of service attacks. Persuade your audience using this Six Common Types Of Cyber Security Incident Ppt Slides Graphics Tutorials PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Malware Through, Phishing Through, Password Attacks Through. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Use this Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Increasing Information Security Awareness In Company Using Various Techniques Complete Deck
Use this Increasing Information Security Awareness In Company Using Various Techniques Complete Deck to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in fifteen slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
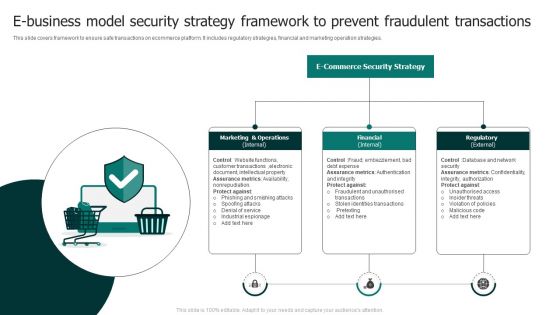
E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF
This slide covers framework to ensure safe transactions on ecommerce platform. It includes regulatory strategies, financial and marketing operation strategies. Persuade your audience using this E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Transactions, Assurance Metrics, Document Intellectual. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
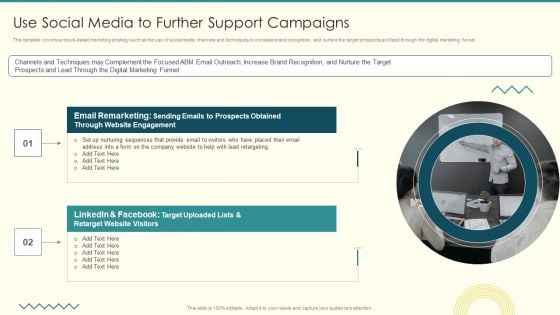
Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF
This template covers account-based marketing strategy such as the use of social media channels and techniques to increase brand recognition, and nurture the target prospects and lead through the digital marketing funnel.This is a Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Prospects Obtained, Nurturing Sequences, Channels Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT Addressing Frequent Communication For Project Quality Management Icons PDF
This slide provides information regarding meetings that held in order to keep consistent quality entire project. These meetings are held on quarterly, annual basis. Presenting project security administration it addressing frequent communication for project quality management icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like executive, leaders, coordinators, initiation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
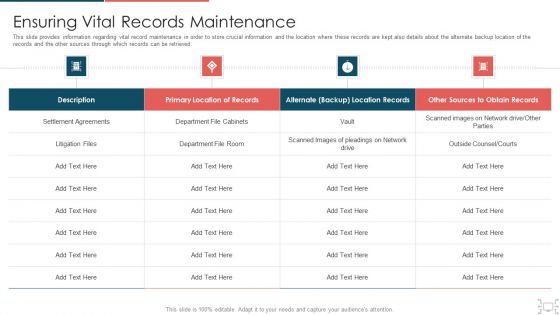
Cyber Security Administration In Organization Ensuring Vital Records Maintenance Topics PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization ensuring vital records maintenance topics pdf. Use them to share invaluable insights on ensuring vital records maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Ensuring Vital Records Maintenance Summary PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver an awe inspiring pitch with this creative corporate security and risk management ensuring vital records maintenance summary pdf bundle. Topics like ensuring vital records maintenance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
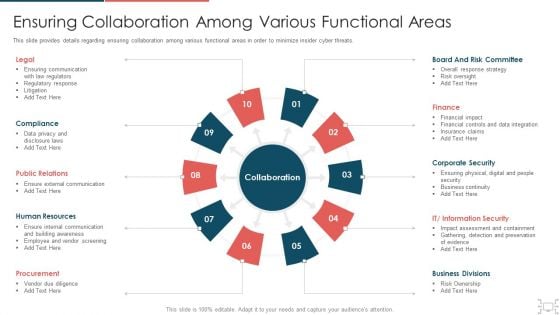
cyber security administration in organization ensuring collaboration among various functional areas brochure pdf
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting cyber security administration in organization ensuring collaboration among various functional areas brochure pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like communication, compliance, relations, resources, procurement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides
Use this Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.
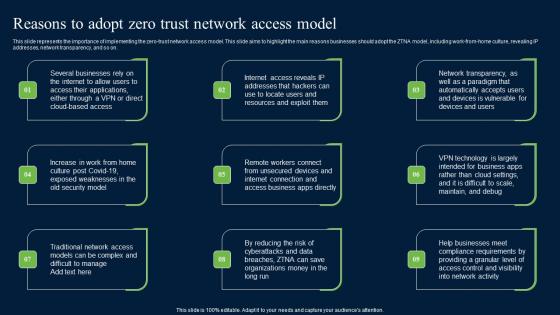
Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Reasons To Adopt Zero Trust Network Access Model Zero Trust Network Security Brochure Pdf. This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on.
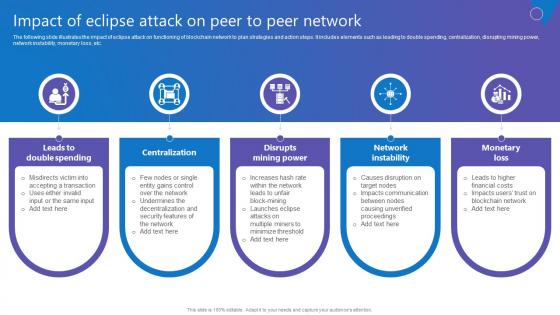
Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf today and make your presentation stand out from the rest The following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc.

Financial Security Concept Padlock And Dollars PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Financial Security Concept Padlock And Dollars PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Future PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Use our Finance PowerPoint Templates because Our PowerPoint Templates and Slides will provide you the cutting edge. Slice through the doubts in the minds of your listeners. Download and present our Money PowerPoint Templates because You can Hit the nail on the head with our PowerPoint Templates and Slides. Embed your ideas in the minds of your audience. Present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will let your words and thoughts hit bullseye everytime. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are endowed to endure. Ideas conveyed through them will pass the test of time.Use these PowerPoint slides for presentations relating to dollar currency notes with lock and chain, future, money, chains, finance, shapes. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Make your presentations glow like the sun with our Financial Security Concept Padlock And Dollars PowerPoint Templates Ppt Backgrounds For Slides 0313. You will be at the top of your game.

Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.
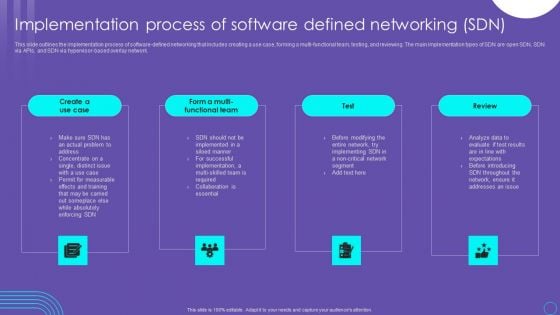
SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF
This slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. The SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
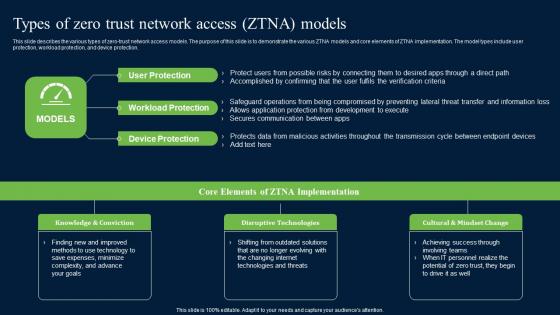
Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Boost your pitch with our creative Types Of Zero Trust Network Access ZTNA Models Zero Trust Network Security Clipart Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection.

Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112
We present our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because,You too have got the framework of your companys growth in place. Use our Success PowerPoint Templates because, You can Transmit this concern to your staff using our helpful slides. Use our Puzzles or jigsaws PowerPoint Templates because,We all know that alphabetical order is a time honoured concept. Use our Shapes PowerPoint Templates because,you can put it up there for all to see. Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Key chain tied with puzzle piece, business, success, puzzles or jigsaws, shapes, marketing. The prominent colors used in the PowerPoint template are Yellow, Black, Red Engineer growth with our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112. Download without worries with our money back guaranteee.
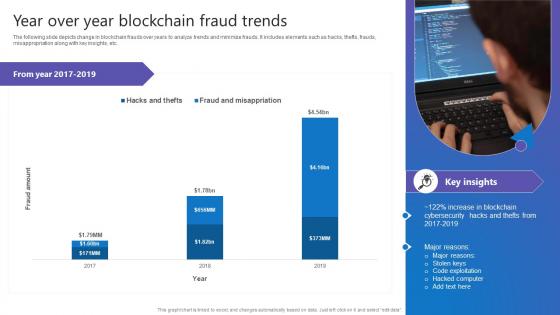
Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf
The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf can be your best option for delivering a presentation. Represent everything in detail using Year Over Year Blockchain Fraud Comprehensive Guide To Blockchain Digital Security Background Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc.

Overview And Working Process Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. The Overview And Working Process Comprehensive Guide To Blockchain Digital Security Template Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc.
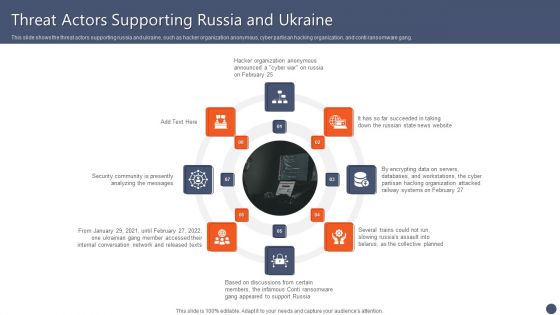
Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF
This slide shows the threat actors supporting russia and ukraine, such as hacker organization anonymous, cyber partisan hacking organization, and conti ransomware gang. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Series Of Cyber Security Attacks Against Ukraine 2022 Threat Actors Supporting Russia And Ukraine Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Disciplinary Action Against Workplace Safety Protocol And Security Practices Themes Pdf
The following slide highlights the disciplinary action against employees for not complying the rules and safety guidelines which includes oral warning, written notice, suspension and discharge Make sure to capture your audiences attention in your business displays with our gratis customizable Disciplinary Action Against Workplace Safety Protocol And Security Practices Themes Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The following slide highlights the disciplinary action against employees for not complying the rules and safety guidelines which includes oral warning, written notice, suspension and discharge
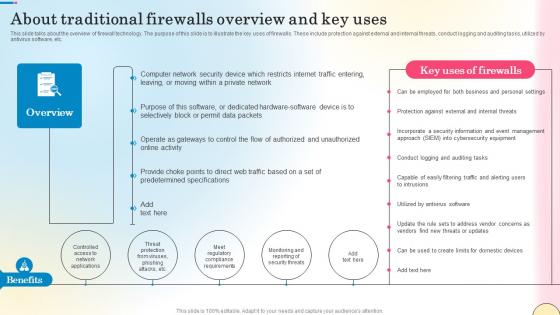
About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf
This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc. Boost your pitch with our creative About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc.
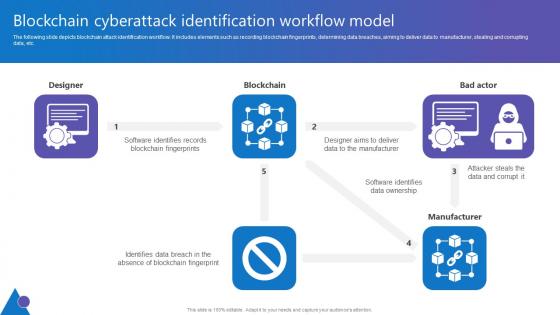
Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf
The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Take your projects to the next level with our ultimate collection of Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc.
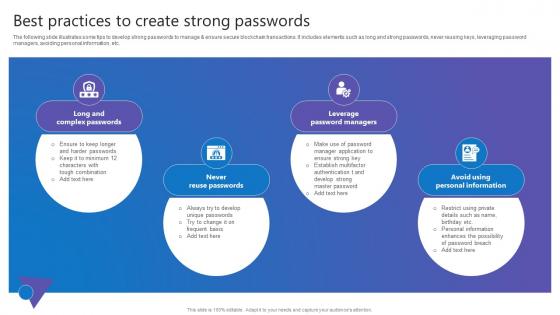
Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc. This Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc.
Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf
The following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Slidegeeks is here to make your presentations a breeze with Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc.
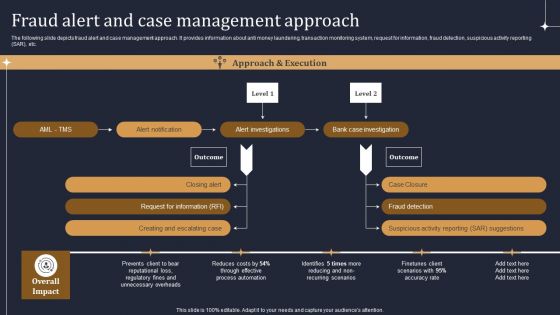
KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF
The following slide depicts fraud alert and case management approach. It provides information about anti money laundering, transaction monitoring system, request for information, fraud detection, suspicious activity reporting SAR, etc. The KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
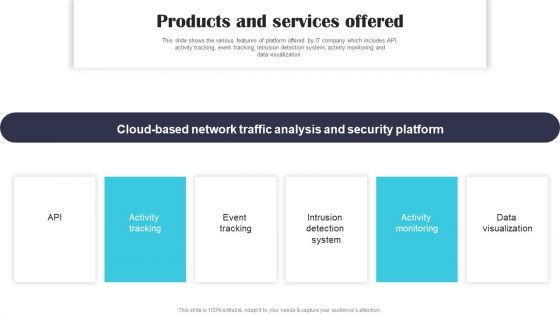
Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF
This slide shows the various features of platform offered by IT company which includes API, activity tracking, event tracking, intrusion detection system, activity monitoring and data visualization. This modern and well arranged Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.


 Continue with Email
Continue with Email

 Home
Home


































