Layered Security

Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF
This slide covers key elements of cybersecurity awareness training program. It involves elements such as make message relevant, use real world examples, common language, present small messages and use continued reinforcement. Presenting Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Make Message Relevant, Use Examples, Use Common Language. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF
This slide covers quarterly cybersecurity awareness training program plan. It involves activities such as cybersecurity knowledge and survey, compliance training, phishing simulation etc. Pitch your topic with ease and precision using this Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF. This layout presents information on Key Message, Core Awareness Activities, Responsible Person, Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
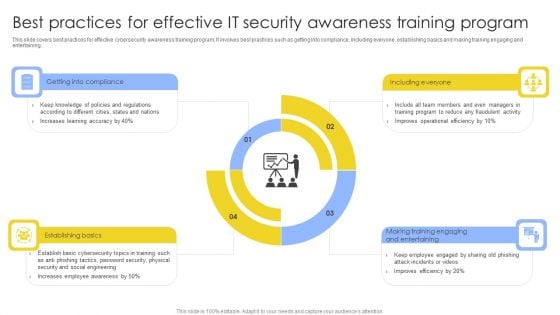
Best Practices For Effective IT Security Awareness Training Program Background PDF
This slide covers best practices for effective cybersecurity awareness training program. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting Best Practices For Effective IT Security Awareness Training Program Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Getting Into Compliance, Including Everyone, Establishing Basics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
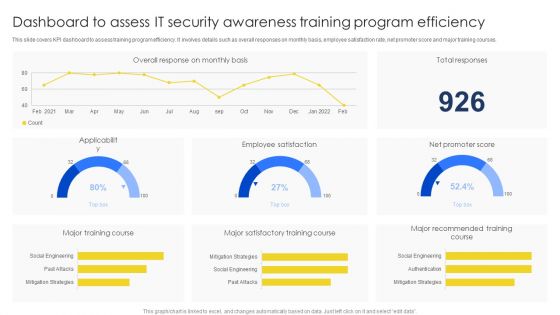
Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF
This slide covers KPI dashboard to assess training program efficiency. It involves details such as overall responses on monthly basis, employee satisfaction rate, net promoter score and major training courses. Pitch your topic with ease and precision using this Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF. This layout presents information on Major Training Course, Major Satisfactory, Training Course. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
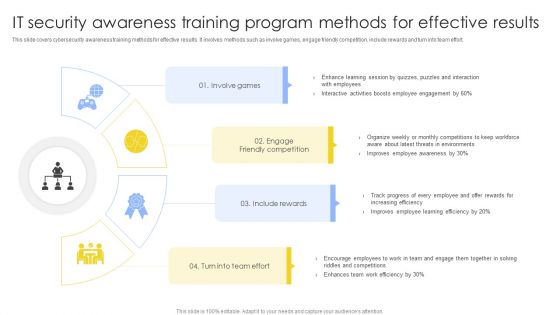
IT Security Awareness Training Program Methods For Effective Results Summary PDF
This slide covers cybersecurity awareness training methods for effective results. It involves methods such as involve games, engage friendly competition, include rewards and turn into team effort. Presenting IT Security Awareness Training Program Methods For Effective Results Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Involve Games, Engage Friendly Competition, Include Rewards. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
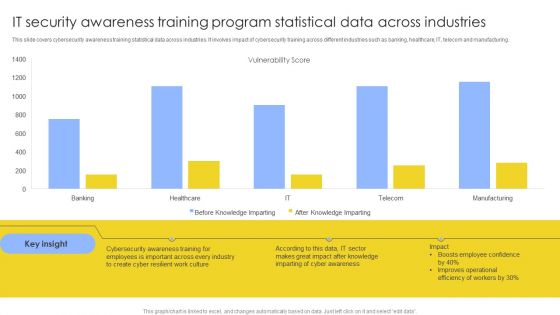
IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF
This slide covers cybersecurity awareness training statistical data across industries. It involves impact of cybersecurity training across different industries such as banking, healthcare, IT, telecom and manufacturing. Showcasing this set of slides titled IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF. The topics addressed in these templates are Vulnerability Score, Cyber Awareness, Improves Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
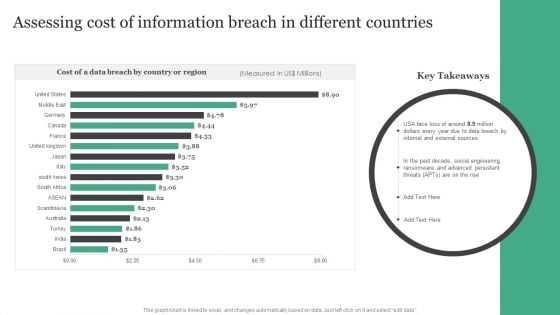
Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF
Retrieve professionally designed Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
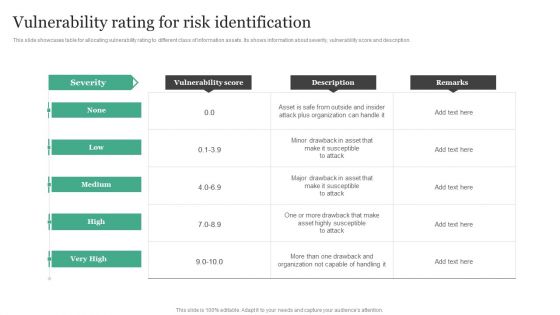
Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF
Retrieve professionally designed Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
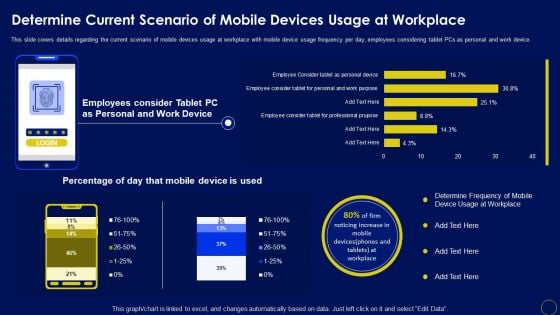
Determine Current Scenario Of Mobile Devices Usage At Workplace Business Mobile Device Security Structure PDF
This slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, employees considering tablet PCs as personal and work device. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Determine Current Scenario Of Mobile Devices Usage At Workplace Business Mobile Device Security Structure PDF from Slidegeeks and deliver a wonderful presentation.
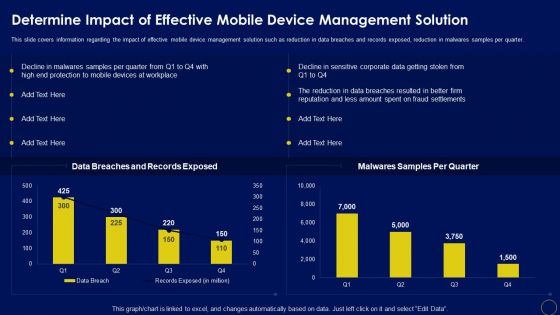
Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. The Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF
Retrieve professionally designed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF
This slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Presenting Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Probe, Initial Attack, Expanded Attack, Data Lift. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
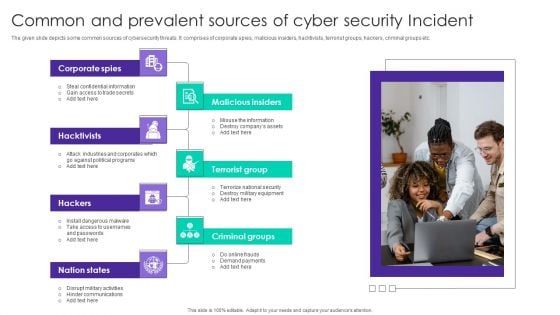
Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Do you know about Slidesgeeks Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Information Systems Security And Risk Management Plan Swot Analysis Topics PDF
Retrieve professionally designed Information Systems Security And Risk Management Plan Swot Analysis Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
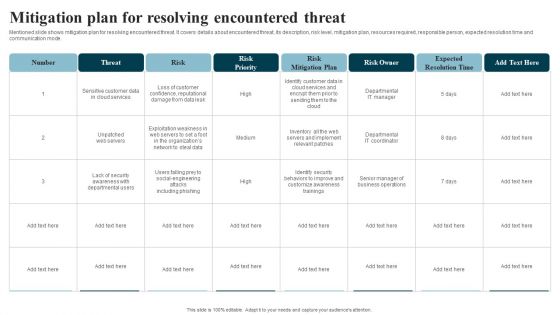
Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF
Do you know about Slidesgeeks Table Of Contents For Developing IT Security Strategy To Prevent Data Assets Guidelines PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
Hexagonal Unidirectional Shape For Process Flow Ppt Security Business Plan PowerPoint Templates
We present our hexagonal unidirectional shape for process flow ppt security business plan PowerPoint templates.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Present our Puzzles or Jigsaws PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Present our Hexagon PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly. Download our Leadership PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape.Use these PowerPoint slides for presentations relating to hexagon, honeycomb, 3d, abstract, background, vector, shelf, design, decoration, layout, achievement, business, blank, concept, sign, success, presentation, cube, bright, symbol, template, commercial, graphic, clean, element, marketing, technology, development, shape, modern, creative, illustration, decorative, up, frame, science, cover, trendy, banner, art, style, space. The prominent colors used in the PowerPoint template are Blue light, Gray, White. Exhibit high fibre with our Hexagonal Unidirectional Shape For Process Flow Ppt Security Business Plan PowerPoint Templates. They display your fearless character.
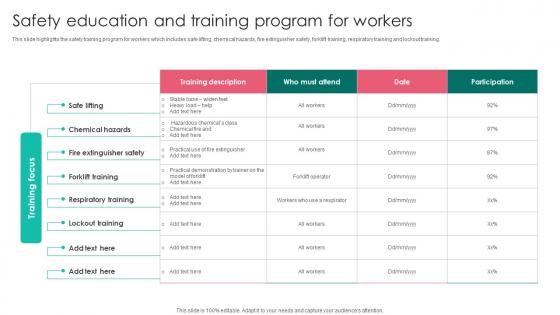
Safety Education And Training Program Workplace Safety Protocol And Security Practices Clipart Pdf
This slide highlights the safety training program for workers which includes safe lifting, chemical hazards, fire extinguisher safety, forklift training, respiratory training and lockout training. Do you know about Slidesgeeks Safety Education And Training Program Workplace Safety Protocol And Security Practices Clipart Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide highlights the safety training program for workers which includes safe lifting, chemical hazards, fire extinguisher safety, forklift training, respiratory training and lockout training.

Cyber Security Awareness Checklist To Ensure IT Asset Protection Structure PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Awareness Checklist To Ensure IT Asset Protection Structure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
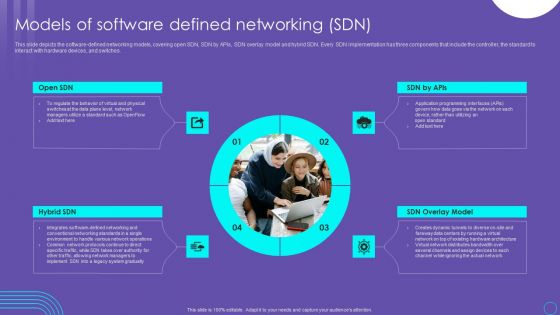
SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF
This slide depicts the software defined networking models, covering open SDN, SDN by APIs, SDN overlay model and hybrid SDN. Every SDN implementation has three components that include the controller, the standard to interact with hardware devices, and switches. Do you know about Slidesgeeks SDN Security Architecture Models Of Software Defined Networking SDN Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
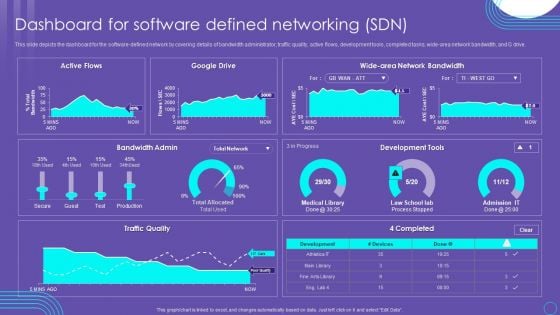
SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF
This slide depicts the dashboard for the software defined network by covering details of bandwidth administrator, traffic quality, active flows, development tools, completed tasks, wide area network bandwidth, and G drive. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF
This slide represents the importance of virtualization in software defined networking and how they complement one another. It also includes how SDN helps simplify the process of controlling data packet routing via a central server. Retrieve professionally designed SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
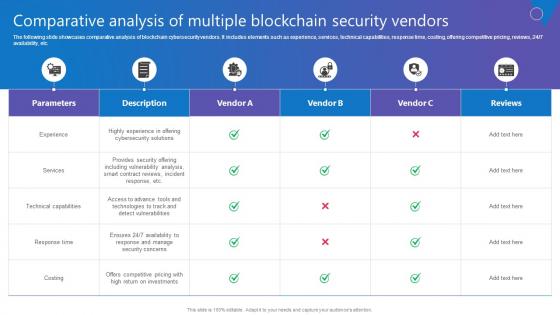
Comparative Analysis Multiple Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc. Do you know about Slidesgeeks Comparative Analysis Multiple Comprehensive Guide To Blockchain Digital Security Introduction Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 24 7 availability, etc.
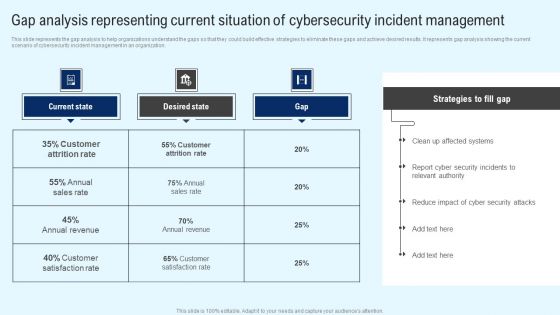
Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Retrieve professionally designed Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
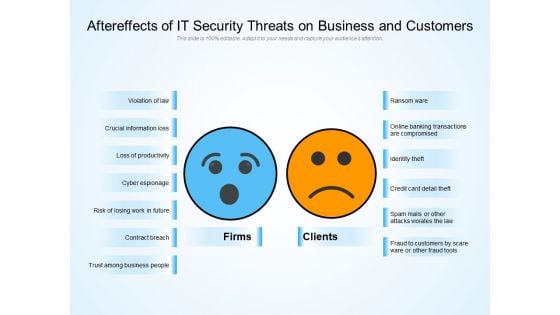
Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF
The purpose of this slide is to showcase the dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Present like a pro with Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
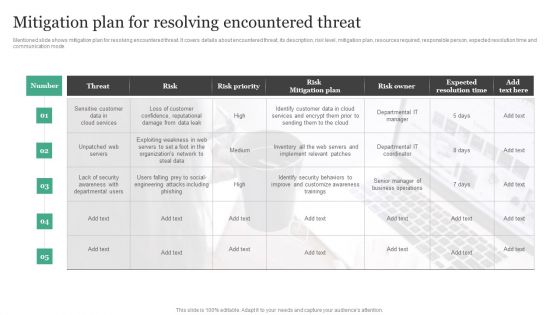
Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Slidegeeks has constructed Mitigation Plan For Resolving Encountered Threat Information Security Risk Administration Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
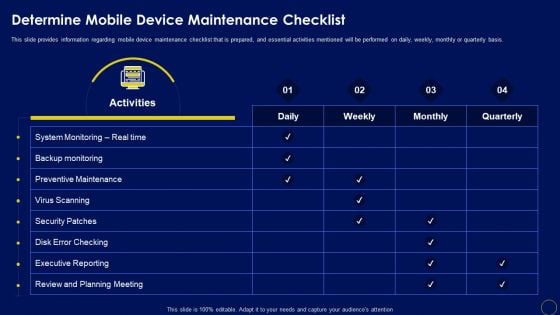
Determine Mobile Device Maintenance Checklist Business Mobile Device Security Management Professional PDF
This slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Retrieve professionally designed Determine Mobile Device Maintenance Checklist Business Mobile Device Security Management Professional PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
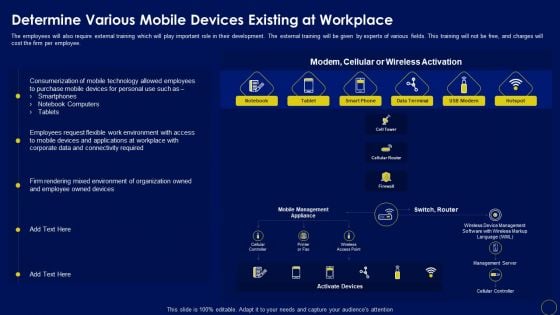
Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Do you know about Slidesgeeks Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
Tracking Mobile Device Activities At Workplace Business Mobile Device Security Management Icons PDF
This slide covers information regarding the tracking mobile device activities at workplace with details about MDM managed mobile summary, MDM users, vulnerabilities and severity summary. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Tracking Mobile Device Activities At Workplace Business Mobile Device Security Management Icons PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
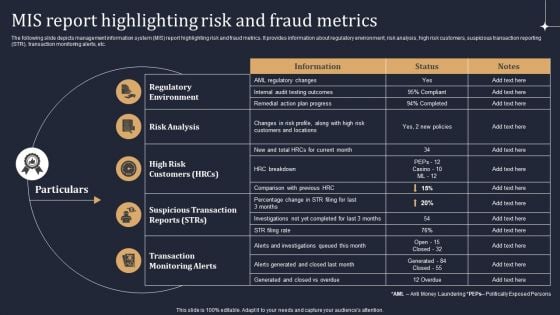
KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF
The following slide depicts management information system MIS report highlighting risk and fraud metrics. It provides information about regulatory environment, risk analysis, high risk customers, suspicious transaction reporting STR, transaction monitoring alerts, etc. Retrieve professionally designed KYC Transaction Monitoring System Business Security Mis Report Highlighting Risk And Fraud Metrics Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
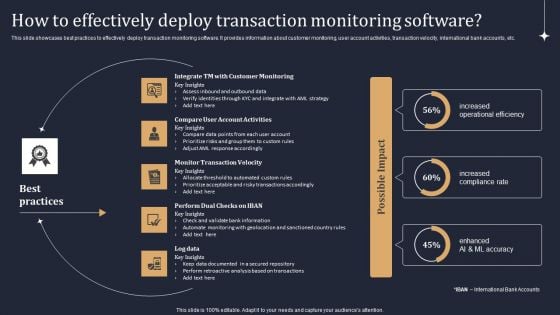
KYC Transaction Monitoring System Business Security How To Effectively Deploy Transaction Brochure PDF
This slide showcases best practices to effectively deploy transaction monitoring software. It provides information about customer monitoring, user account activities, transaction velocity, international bank accounts, etc. Do you know about Slidesgeeks KYC Transaction Monitoring System Business Security How To Effectively Deploy Transaction Brochure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
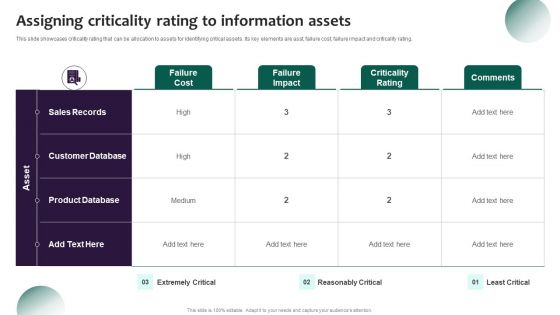
Information Systems Security And Risk Management Plan Assigning Criticality Rating To Information Assets Ideas PDF
This slide showcases criticality rating that can be allocation to assets for identifying critical assets. Its key elements are asst, failure cost, failure impact and criticality rating. Do you know about Slidesgeeks Information Systems Security And Risk Management Plan Assigning Criticality Rating To Information Assets Ideas PDFThese are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Retrieve professionally designed Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc.
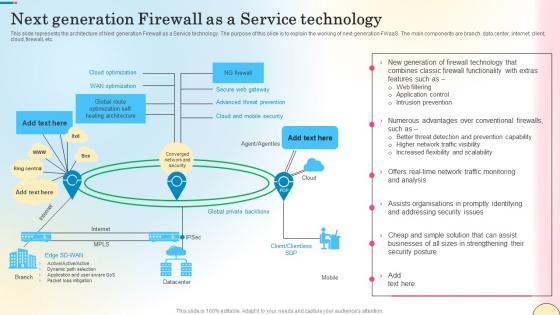
Next Generation Firewall As A Service Technology Network Security Mockup Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Do you know about Slidesgeeks Next Generation Firewall As A Service Technology Network Security Mockup Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc.
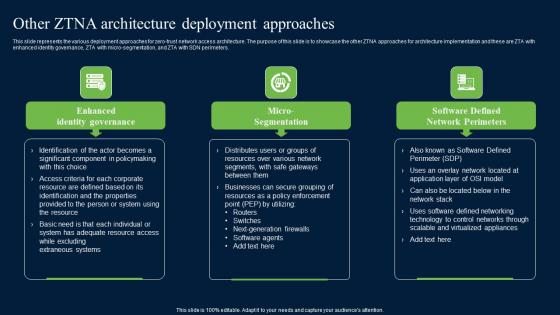
Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.
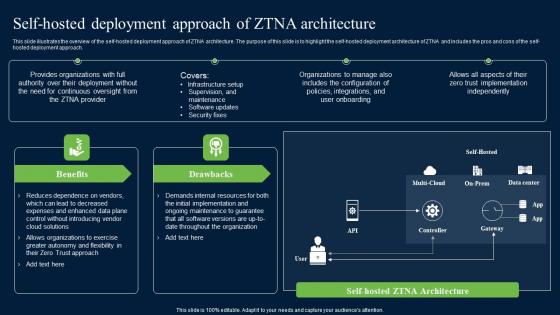
Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Network Security Graphics Pdf
This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Do you know about Slidesgeeks Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Network Security Graphics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.
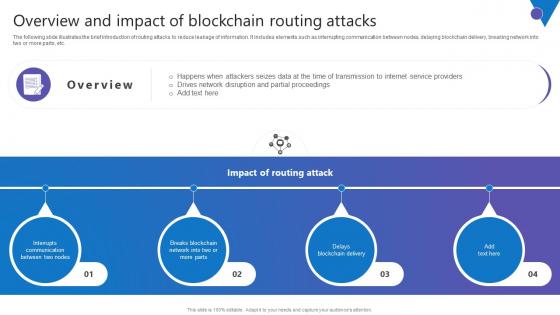
Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf
The following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc. Retrieve professionally designed Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc.
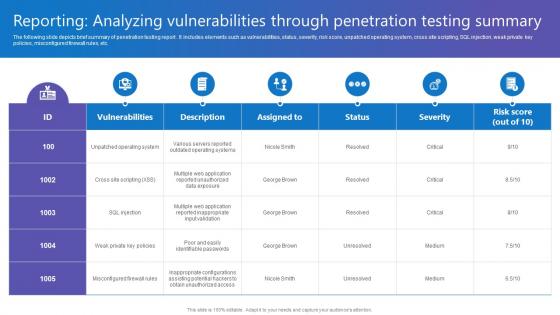
Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf
The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc. Do you know about Slidesgeeks Reporting Analyzing Vulnerabilities Comprehensive Guide To Blockchain Digital Security Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide depicts brief summary of penetration testing report . It includes elements such as vulnerabilities, status, severity, risk score, unpatched operating system, cross site scripting, SQL injection, weak private key policies, misconfigured firewall rules, etc.

Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf
This slide describes the overview of SD-WAN architectural layers, including orchestration and analytics, virtual service delivery, and secure cloud network. The purpose of this slide is to highlight the main features and functions of SD-WAN layers. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf This slide describes the overview of SD-WAN architectural layers, including orchestration and analytics, virtual service delivery, and secure cloud network. The purpose of this slide is to highlight the main features and functions of SD-WAN layers.

Security Information And Event Management Strategies For Financial Audit And Compliance SIM Vs SEM Vs SIEM Sample PDF
Presenting security information and event management strategies for financial audit and compliance sim vs sem vs siem sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
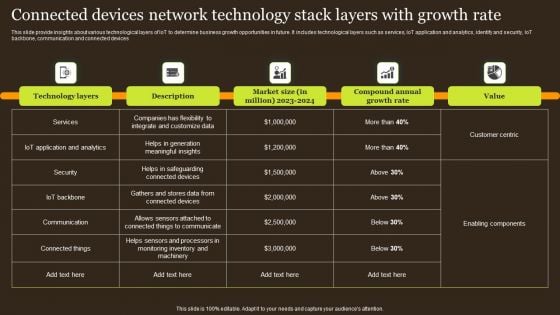
Connected Devices Network Technology Stack Layers With Growth Rate Rules PDF
This slide provide insights about various technological layers of IoT to determine business growth opportunities in future. It includes technological layers such as services, IoT application and analytics, identify and security, IoT backbone, communication and connected devices. Showcasing this set of slides titled Connected Devices Network Technology Stack Layers With Growth Rate Rules PDF. The topics addressed in these templates are Technology Layers, Description, Market Size. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
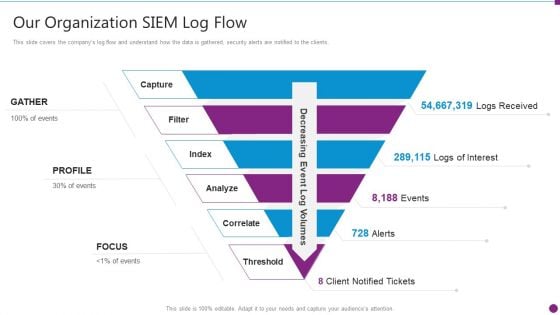
Security Information And Event Management Strategies For Financial Audit And Compliance Our Organization SIEM Log Flow Designs PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. This is a security information and event management strategies for financial audit and compliance our organization siem log flow designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our organization siem log flow. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
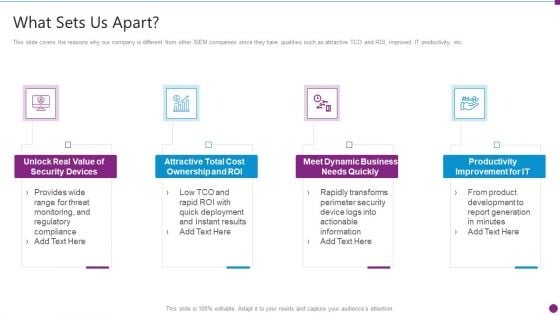
Security Information And Event Management Strategies For Financial Audit And Compliance What Sets Us Apart Pictures PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting security information and event management strategies for financial audit and compliance what sets us apart pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like cost ownership and roi, security devices, dynamic business, productivity improvement for it. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
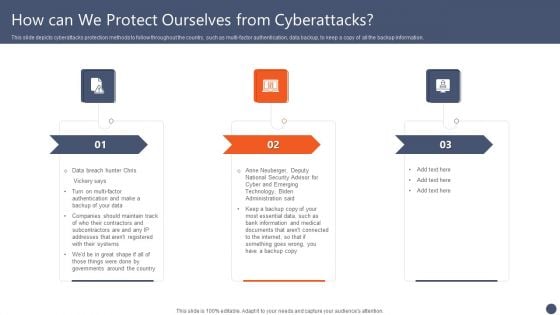
Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF
This slide depicts the hacking groups such as the anonymous hacker group, conti ransomware gang, threat actors in belarus launching cyber proxy war over ukraine attacks by russia. Find highly impressive Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Security Information And Event Management Strategies For Financial Audit And Compliance Need For SIEM Software Download PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting security information and event management strategies for financial audit and compliance need for siem software download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Virtual WAN Architecture Overview Of Software Defined Wan Architecture Layers Icons PDF
This slide describes the overview of SD-WAN architectural layers, including orchestration and analytics, virtual service delivery, and secure cloud network. The purpose of this slide is to highlight the main features and functions of SD-WAN layers. Get a simple yet stunning designed Virtual WAN Architecture Overview Of Software Defined Wan Architecture Layers Icons PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Virtual WAN Architecture Overview Of Software Defined Wan Architecture Layers Icons PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
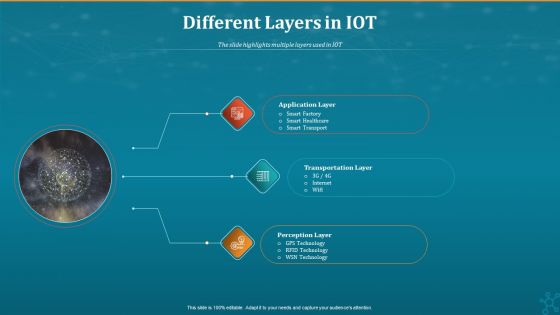
Machine To Machine Communication Different Layers In IOT Sample PDF
The slide highlights multiple layers used in IOT.This is a machine to machine communication end end iot security inspiration pdf. template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application layer, transportation layer, perception layer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
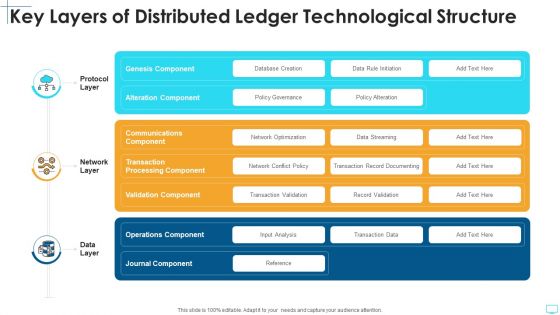
Key Layers Of Distributed Ledger Technological Structure Brochure PDF
Persuade your audience using this key layers of distributed ledger technological structure brochure pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including protocol layer, network layer, data layer . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
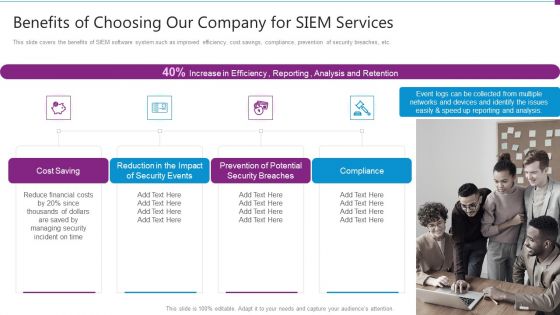
Security Information And Event Management Strategies For Financial Audit And Compliance Benefits Of Choosing Our Company Topics PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a security information and event management strategies for financial audit and compliance benefits of choosing our company topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, security breaches, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Key Security Controls To Be Addressed In The Program Ppt Infographics Samples PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Presenting handling cyber threats digital era key security controls to be addressed in the program ppt infographics samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prevents attacks, limits extent of attacks, data recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
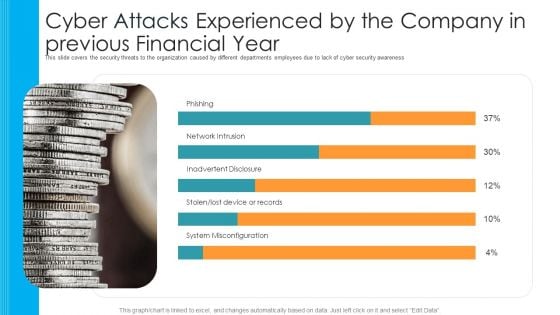
Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
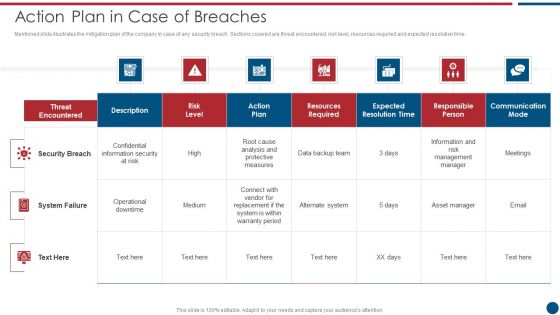
Risk Based Procedures To IT Security Action Plan In Case Of Breaches Ppt PowerPoint Presentation File Model PDF
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Action Plan In Case Of Breaches Ppt PowerPoint Presentation File Model PDF bundle. Topics like Threat Encountered, Communication Mode, Security Breach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
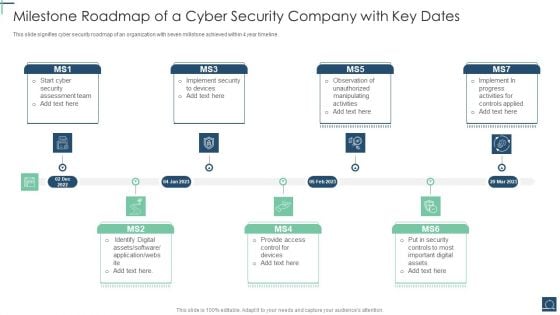
Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
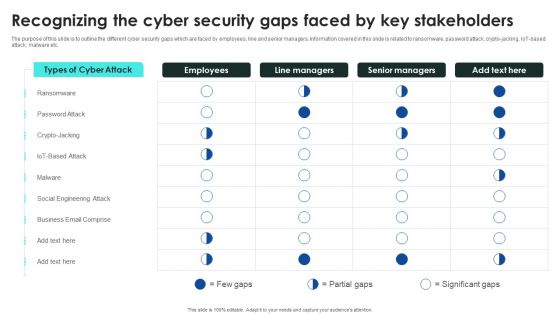
Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
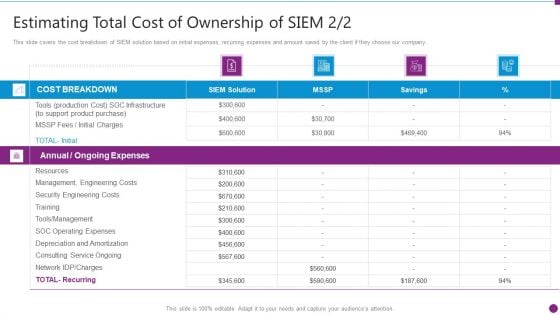
Estimating Total Cost Of Security Information And Event Management Strategies For Financial Audit And Compliance Formats PDF
This slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Deliver an awe inspiring pitch with this creative estimating total cost of security information and event management strategies for financial audit and compliance formats pdf bundle. Topics like cost breakdown, ongoing expenses, resources, security engineering costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































