Line Graph

Key Steps Involved In Agile Software Development Technological Innovation Playbook Structure Pdf
This slide provides information regarding major steps of agile software development lifecycle in terms of essential elements involved such as concept, inception, iteration and construction, etc. It include project selection, initiation, production deployment, release support and removal of production, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Key Steps Involved In Agile Software Development Technological Innovation Playbook Structure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Key Steps Involved In Agile Software Development Technological Innovation Playbook Structure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provides information regarding major steps of agile software development lifecycle in terms of essential elements involved such as concept, inception, iteration and construction, etc. It include project selection, initiation, production deployment, release support and removal of production, etc.
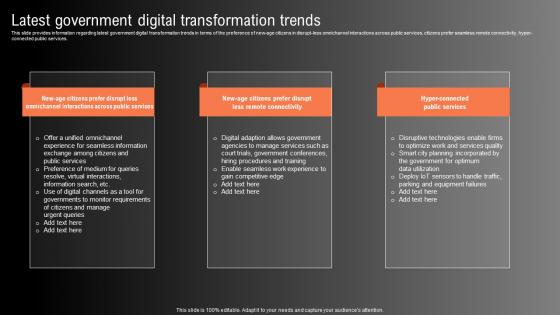
Latest Government Digital Transformation Trends Technological Innovation Playbook Formats Pdf
This slide provides information regarding latest government digital transformation trends in terms of the preference of new age citizens in disrupt less omnichannel interactions across public services, citizens prefer seamless remote connectivity, hyper connected public services. Get a simple yet stunning designed Latest Government Digital Transformation Trends Technological Innovation Playbook Formats Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Latest Government Digital Transformation Trends Technological Innovation Playbook Formats Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides information regarding latest government digital transformation trends in terms of the preference of new age citizens in disrupt less omnichannel interactions across public services, citizens prefer seamless remote connectivity, hyper connected public services.
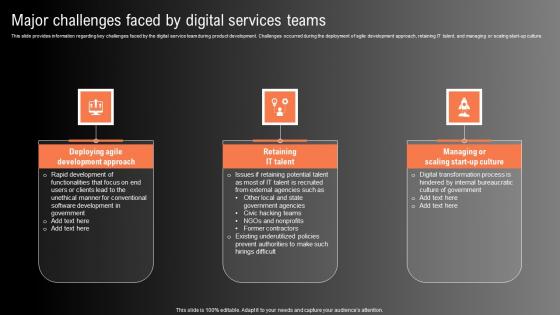
Major Challenges Faced By Digital Services Teams Technological Innovation Playbook Background Pdf
This slide provides information regarding key challenges faced by the digital service team during product development. Challenges occurred during the deployment of agile development approach, retaining IT talent, and managing or scaling start up culture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Major Challenges Faced By Digital Services Teams Technological Innovation Playbook Background Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides information regarding key challenges faced by the digital service team during product development. Challenges occurred during the deployment of agile development approach, retaining IT talent, and managing or scaling start up culture.

Major Principles Associated With Agile Software Technological Innovation Playbook Introduction Pdf
This slide provides information regarding key principles of Agile software management in terms of focus on customer satisfaction with consistent delivery of high quality software, optimizing amount of work done, offer consistent focus on technical excellence enable agility enhancement to design, etc. Slidegeeks is here to make your presentations a breeze with Major Principles Associated With Agile Software Technological Innovation Playbook Introduction Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide provides information regarding key principles of Agile software management in terms of focus on customer satisfaction with consistent delivery of high quality software, optimizing amount of work done, offer consistent focus on technical excellence enable agility enhancement to design, etc.
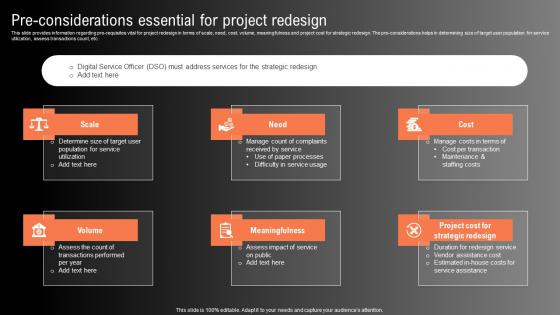
Pre Considerations Essential For Project Redesign Technological Innovation Playbook Summary Pdf
This slide provides information regarding pre requisites vital for project redesign in terms of scale, need, cost, volume, meaningfulness and project cost for strategic redesign. The pre considerations helps in determining size of target user population for service utilization, assess transactions count, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Pre Considerations Essential For Project Redesign Technological Innovation Playbook Summary Pdf from Slidegeeks and deliver a wonderful presentation. This slide provides information regarding pre requisites vital for project redesign in terms of scale, need, cost, volume, meaningfulness and project cost for strategic redesign. The pre considerations helps in determining size of target user population for service utilization, assess transactions count, etc.
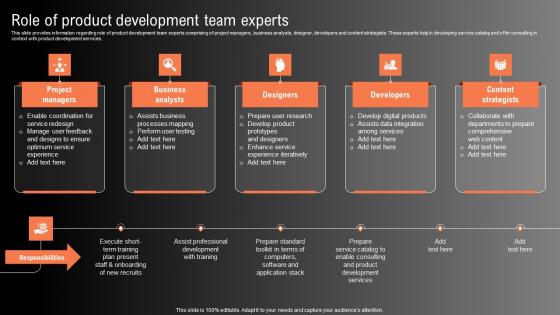
Role Of Product Development Team Experts Technological Innovation Playbook Sample Pdf
This slide provides information regarding role of product development team experts comprising of project managers, business analysts, designer, developers and content strategists. These experts help in developing service catalog and offer consulting in context with product development services. Slidegeeks has constructed Role Of Product Development Team Experts Technological Innovation Playbook Sample Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates. This slide provides information regarding role of product development team experts comprising of project managers, business analysts, designer, developers and content strategists. These experts help in developing service catalog and offer consulting in context with product development services.
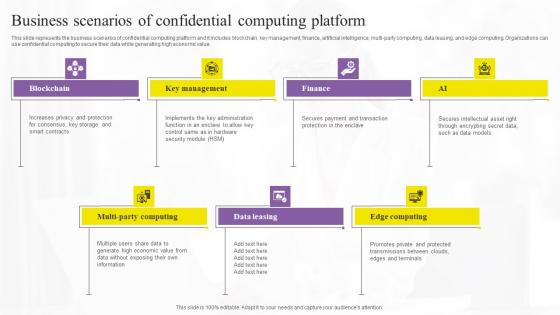
Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Confidential Computing Technologies Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
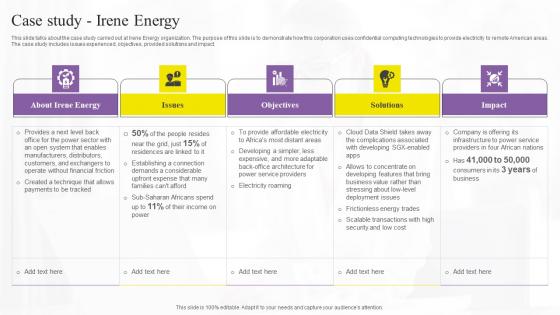
Case Study Irene Energy Confidential Computing Technologies Download Pdf
This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Irene Energy Confidential Computing Technologies Download Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Irene Energy Confidential Computing Technologies Download Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact.
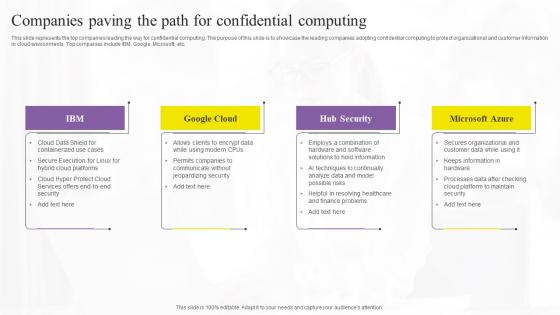
Companies Paving The Path For Confidential Computing Technologies Demonstration Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Present like a pro with Companies Paving The Path For Confidential Computing Technologies Demonstration Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc.
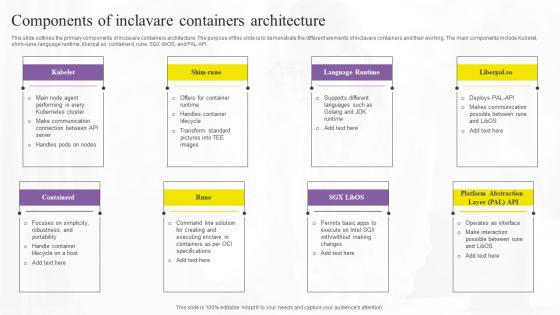
Components Of Inclavare Containers Confidential Computing Technologies Diagrams Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Slidegeeks is here to make your presentations a breeze with Components Of Inclavare Containers Confidential Computing Technologies Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
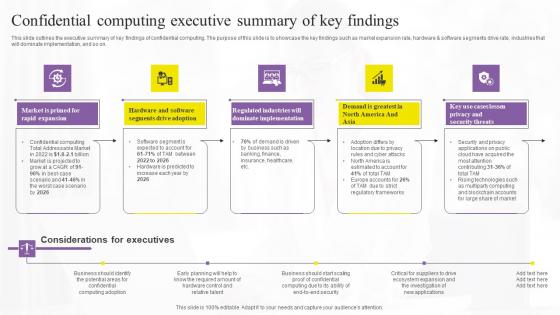
Confidential Computing Executive Confidential Computing Technologies Guidelines Pdf
This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Executive Confidential Computing Technologies Guidelines Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the executive summary of key findings of confidential computing. The purpose of this slide is to showcase the key findings such as market expansion rate, hardware and software segments drive rate, industries that will dominate implementation, and so on.

Confidential Computing For Total Confidential Computing Technologies Background Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing For Total Confidential Computing Technologies Background Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing For Total Confidential Computing Technologies Background Pdf This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
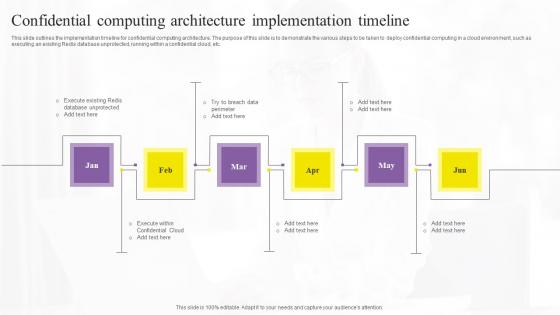
Confidential Computing Technologies Confidential Computing Architecture Topics Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Explore a selection of the finest Confidential Computing Technologies Confidential Computing Architecture Topics Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Technologies Confidential Computing Architecture Topics Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.

Confidential Computing Technologies Confidential Computing Consortium Demonstration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Confidential Computing Technologies Confidential Computing Consortium Demonstration Pdf from Slidegeeks and deliver a wonderful presentation. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
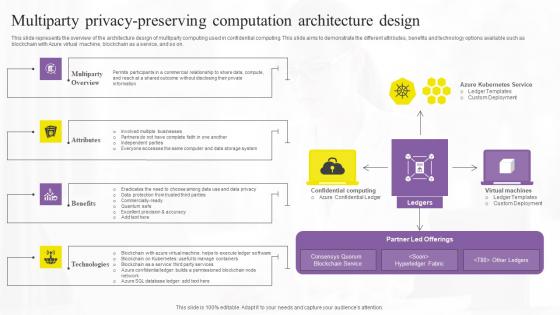
Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Multiparty Privacy Preserving Confidential Computing Technologies Rules Pdf. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on.
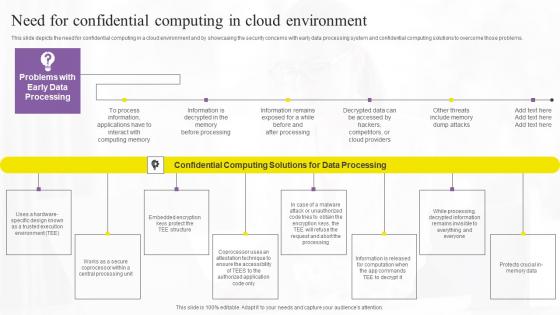
Need For Confidential Computing In Confidential Computing Technologies Structure Pdf
This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. This Need For Confidential Computing In Confidential Computing Technologies Structure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems.
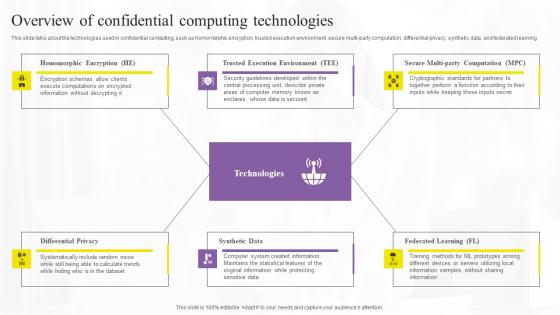
Overview Of Confidential Computing Technologies Elements Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. The Overview Of Confidential Computing Technologies Elements Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
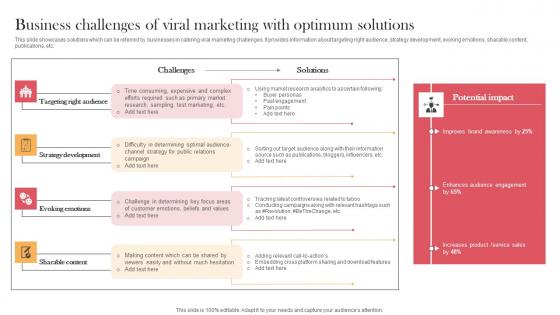
Business Challenges Of Viral Marketing With Optimum Designing Approaches Rules Pdf
This slide showcases solutions which can be referred by businesses in catering viral marketing challenges. It provides information about targeting right audience, strategy development, evoking emotions, sharable content, publications, etc. Get a simple yet stunning designed Business Challenges Of Viral Marketing With Optimum Designing Approaches Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Business Challenges Of Viral Marketing With Optimum Designing Approaches Rules Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases solutions which can be referred by businesses in catering viral marketing challenges. It provides information about targeting right audience, strategy development, evoking emotions, sharable content, publications, etc.

How To Create Buzz Marketing Campaigns Designing Approaches Demonstration Pdf
This slide showcases steps to initiate buzz promotion campaigns. It provides information about know audience, tease campaign beforehand, give customers reasons to engage, video marketing campaign, optimal influencers, monitor and learn. If you are looking for a format to display your unique thoughts, then the professionally designed How To Create Buzz Marketing Campaigns Designing Approaches Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download How To Create Buzz Marketing Campaigns Designing Approaches Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases steps to initiate buzz promotion campaigns. It provides information about know audience, tease campaign beforehand, give customers reasons to engage, video marketing campaign, optimal influencers, monitor and learn.

Marketer Techniques To Improve Word Of Designing Approaches Topics Pdf
The following slide showcases marketing techniques to improve WOM campaigns. It provides details about customer service, community management, page reviews, communicate, products, services, etc. This Marketer Techniques To Improve Word Of Designing Approaches Topics Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Marketer Techniques To Improve Word Of Designing Approaches Topics Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide showcases marketing techniques to improve WOM campaigns. It provides details about customer service, community management, page reviews, communicate, products, services, etc.

Viral Marketing Strategies Buzz Online Guerilla And Wom Designing Approaches Topics Pdf
This slide showcases overview major viral marketing strategies namely buzz, online, guerilla and word of mouth. It provides details about campaign, product service marketing, social media platforms, videos, search engine, etc. Want to ace your presentation in front of a live audience Our Viral Marketing Strategies Buzz Online Guerilla And Wom Designing Approaches Topics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases overview major viral marketing strategies namely buzz, online, guerilla and word of mouth. It provides details about campaign, product service marketing, social media platforms, videos, search engine, etc.

Viral Marketing Strategies To Share Social Media Campaigns Designing Approaches Microsoft Pdf
This slide showcases strategies which marketers can refer who want to reach bigger audience through viral marketing. It provides details about visuals, creative campaigns, emotional appeals, timely sharing, target audience, etc. There are so many reasons you need a Viral Marketing Strategies To Share Social Media Campaigns Designing Approaches Microsoft Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide showcases strategies which marketers can refer who want to reach bigger audience through viral marketing. It provides details about visuals, creative campaigns, emotional appeals, timely sharing, target audience, etc.
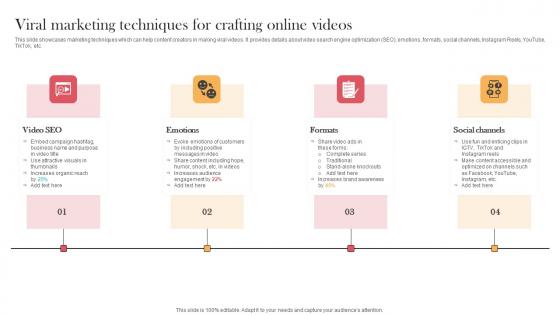
Viral Marketing Techniques For Crafting Online Videos Designing Approaches Professional Pdf
This slide showcases marketing techniques which can help content creators in making viral videos. It provides details about video search engine optimization SEO, emotions, formats, social channels, Instagram Reels, YouTube, TikTok, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Viral Marketing Techniques For Crafting Online Videos Designing Approaches Professional Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Viral Marketing Techniques For Crafting Online Videos Designing Approaches Professional Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases marketing techniques which can help content creators in making viral videos. It provides details about video search engine optimization SEO, emotions, formats, social channels, Instagram Reels, YouTube, TikTok, etc.
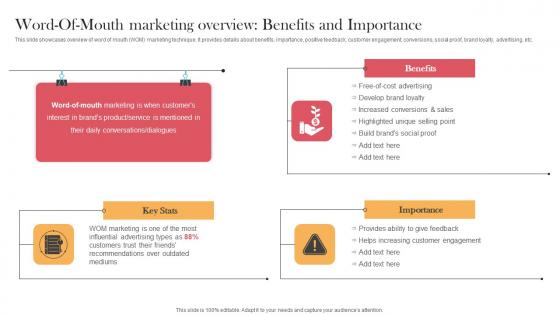
Word Of Mouth Marketing Overview Benefits And Importance Designing Approaches Structure Pdf
This slide showcases overview of word of mouth WOM marketing technique. It provides details about benefits, importance, positive feedback, customer engagement, conversions, social proof, brand loyalty, advertising, etc. Present like a pro with Word Of Mouth Marketing Overview Benefits And Importance Designing Approaches Structure Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases overview of word of mouth WOM marketing technique. It provides details about benefits, importance, positive feedback, customer engagement, conversions, social proof, brand loyalty, advertising, etc.
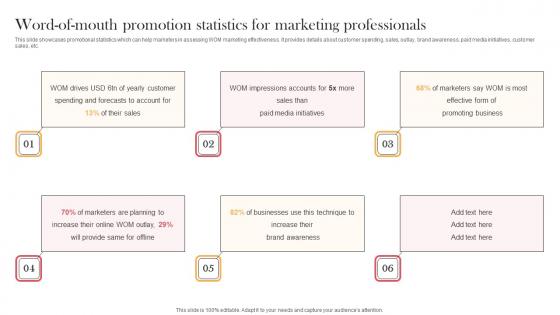
Word Of Mouth Promotion Statistics For Marketing Professionals Designing Approaches Demonstration Pdf
This slide showcases promotional statistics which can help marketers in assessing WOM marketing effectiveness. It provides details about customer spending, sales, outlay, brand awareness, paid media initiatives, customer sales, etc. Slidegeeks is here to make your presentations a breeze with Word Of Mouth Promotion Statistics For Marketing Professionals Designing Approaches Demonstration Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide showcases promotional statistics which can help marketers in assessing WOM marketing effectiveness. It provides details about customer spending, sales, outlay, brand awareness, paid media initiatives, customer sales, etc.
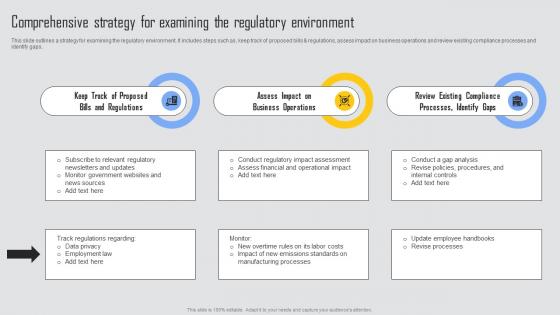
Comprehensive Strategy Managing Risks And Establishing Trust Through Efficient Themes Pdf
This slide outlines a strategy for examining the regulatory environment. It includes steps such as, keep track of proposed bills and regulations, assess impact on business operations and review existing compliance processes and identify gaps. Welcome to our selection of the Comprehensive Strategy Managing Risks And Establishing Trust Through Efficient Themes Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today This slide outlines a strategy for examining the regulatory environment. It includes steps such as, keep track of proposed bills and regulations, assess impact on business operations and review existing compliance processes and identify gaps.
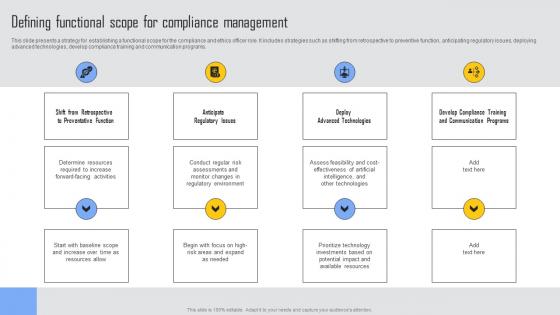
Defining Functional Scope Managing Risks And Establishing Trust Through Efficient Slides Pdf
This slide presents a strategy for establishing a functional scope for the compliance and ethics officer role. It includes strategies such as shifting from retrospective to preventive function, anticipating regulatory issues, deploying advanced technologies, develop compliance training and communication programs. Presenting this PowerPoint presentation, titled Defining Functional Scope Managing Risks And Establishing Trust Through Efficient Slides Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Defining Functional Scope Managing Risks And Establishing Trust Through Efficient Slides Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Defining Functional Scope Managing Risks And Establishing Trust Through Efficient Slides Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide presents a strategy for establishing a functional scope for the compliance and ethics officer role. It includes strategies such as shifting from retrospective to preventive function, anticipating regulatory issues, deploying advanced technologies, develop compliance training and communication programs.

Ensuring Uninterrupted Process Managing Risks And Establishing Trust Through Efficient Information Pdf
This slide presents strategies to effectively administer operational process risks. It includes implement risk accountability, champion ORM from the top, conduct timely risk assessments, quantify and prioritize risks and implements. Create an editable Ensuring Uninterrupted Process Managing Risks And Establishing Trust Through Efficient Information Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Ensuring Uninterrupted Process Managing Risks And Establishing Trust Through Efficient Information Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide presents strategies to effectively administer operational process risks. It includes implement risk accountability, champion ORM from the top, conduct timely risk assessments, quantify and prioritize risks and implements.
Establishing A Sustainability Program Managing Risks And Establishing Trust Through Efficient Icons Pdf
This slide provides and overview of sustainability program to promote environmentally responsible practices throughout the organization. It includes goal, strategies and impact. Want to ace your presentation in front of a live audience Our Establishing A Sustainability Program Managing Risks And Establishing Trust Through Efficient Icons Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide provides and overview of sustainability program to promote environmentally responsible practices throughout the organization. It includes goal, strategies and impact.
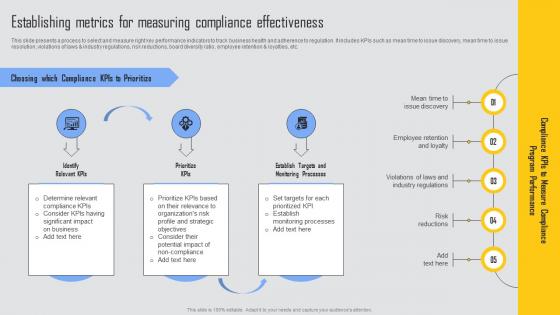
Establishing Metrics Measuring Managing Risks And Establishing Trust Through Efficient Ideas Pdf
This slide presents a process to select and measure right key performance indicators to track business health and adherence to regulation. It includes KPIs such as mean time to issue discovery, mean time to issue resolution, violations of laws and industry regulations, risk reductions, board diversity ratio, employee retention and loyalties, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Establishing Metrics Measuring Managing Risks And Establishing Trust Through Efficient Ideas Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Establishing Metrics Measuring Managing Risks And Establishing Trust Through Efficient Ideas Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide presents a process to select and measure right key performance indicators to track business health and adherence to regulation. It includes KPIs such as mean time to issue discovery, mean time to issue resolution, violations of laws and industry regulations, risk reductions, board diversity ratio, employee retention and loyalties, etc.

Establishing Policies And Procedures Managing Risks And Establishing Trust Through Efficient Ideas Pdf
This slide presents policies and procedures for regulatory compliance implementation of which help business improve their business compliance. It include anti bribery and corruption policy, data protection policy, whistleblower policy, compliance monitoring and reporting procedure. Get a simple yet stunning designed Establishing Policies And Procedures Managing Risks And Establishing Trust Through Efficient Ideas Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Establishing Policies And Procedures Managing Risks And Establishing Trust Through Efficient Ideas Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide presents policies and procedures for regulatory compliance implementation of which help business improve their business compliance. It include anti bribery and corruption policy, data protection policy, whistleblower policy, compliance monitoring and reporting procedure.
Expected Outcomes Of Successful Managing Risks And Establishing Trust Through Efficient Icons Pdf
This slide highlights performance statistics relating to the successful implementation of compliance strategy. It includes data highlighting the increase in trust and confidence, a reduction in penalties, an increase in cost savings, a reduction in compliance incidents, and an improvement in employee behavior. Slidegeeks is here to make your presentations a breeze with Expected Outcomes Of Successful Managing Risks And Establishing Trust Through Efficient Icons Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights performance statistics relating to the successful implementation of compliance strategy. It includes data highlighting the increase in trust and confidence, a reduction in penalties, an increase in cost savings, a reduction in compliance incidents, and an improvement in employee behavior.

Introducing Data Compliance Managing Risks And Establishing Trust Through Efficient Rules Pdf
This slide provides an overview of data compliance and its importance in business. It includes benefits such as easier business process automation, increased trust and credibility, improved data management, protected and enhanced enterprise reputation. Make sure to capture your audiences attention in your business displays with our gratis customizable Introducing Data Compliance Managing Risks And Establishing Trust Through Efficient Rules Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide provides an overview of data compliance and its importance in business. It includes benefits such as easier business process automation, increased trust and credibility, improved data management, protected and enhanced enterprise reputation.
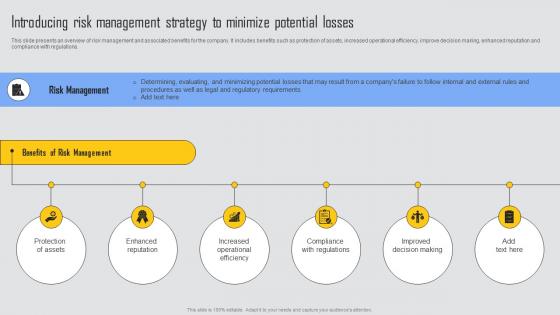
Introducing Risk Management Managing Risks And Establishing Trust Through Efficient Infographics Pdf
This slide presents an overview of risk management and associated benefits for the company. It includes benefits such as protection of assets, increased operational efficiency, improve decision making, enhanced reputation and compliance with regulations. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introducing Risk Management Managing Risks And Establishing Trust Through Efficient Infographics Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introducing Risk Management Managing Risks And Establishing Trust Through Efficient Infographics Pdf This slide presents an overview of risk management and associated benefits for the company. It includes benefits such as protection of assets, increased operational efficiency, improve decision making, enhanced reputation and compliance with regulations.

Introduction To Process Risk Managing Risks And Establishing Trust Through Efficient Brochure Pdf
This slide presents an overview of process risk and why organizations must adhere to process risk compliance. It also includes types of process risks such as poor quality assurance, improper machinery maintenance, reporting and accounting errors. This modern and well arranged Introduction To Process Risk Managing Risks And Establishing Trust Through Efficient Brochure Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide presents an overview of process risk and why organizations must adhere to process risk compliance. It also includes types of process risks such as poor quality assurance, improper machinery maintenance, reporting and accounting errors.

Key Components Of Corporate Managing Risks And Establishing Trust Through Efficient Slides Pdf
This slide presents the key components of compliance strategy to ensure effective development and implementation of compliance in the company. It includes components such as , compliance risk assessment, development of compliance policies and procedures, training and education, monitoring and reporting and continuous improvement. This Key Components Of Corporate Managing Risks And Establishing Trust Through Efficient Slides Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Key Components Of Corporate Managing Risks And Establishing Trust Through Efficient Slides Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide presents the key components of compliance strategy to ensure effective development and implementation of compliance in the company. It includes components such as , compliance risk assessment, development of compliance policies and procedures, training and education, monitoring and reporting and continuous improvement.

Steps To Ensure Compliance Managing Risks And Establishing Trust Through Efficient Microsoft Pdf
This slide presents steps to ensure regulatory compliance and develop a successful compliance program. It includes steps such as identify regulatory requirements, designate responsible person or team, evaluate current compliance status, create a compliance plan, implement compliance plan, provide training, monitor compliance and update compliance plan. There are so many reasons you need a Steps To Ensure Compliance Managing Risks And Establishing Trust Through Efficient Microsoft Pdf, The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide presents steps to ensure regulatory compliance and develop a successful compliance program. It includes steps such as identify regulatory requirements, designate responsible person or team, evaluate current compliance status, create a compliance plan, implement compliance plan, provide training, monitor compliance and update compliance plan.

Strategies For Integrating Quality Managing Risks And Establishing Trust Through Efficient Graphics Pdf
This slide presents an overview of quality risk compliance. It also includes information about strategies to optimize quality such as supplier management, internal audits, quality control processes and quality management system. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Strategies For Integrating Quality Managing Risks And Establishing Trust Through Efficient Graphics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Strategies For Integrating Quality Managing Risks And Establishing Trust Through Efficient Graphics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide presents an overview of quality risk compliance. It also includes information about strategies to optimize quality such as supplier management, internal audits, quality control processes and quality management system.
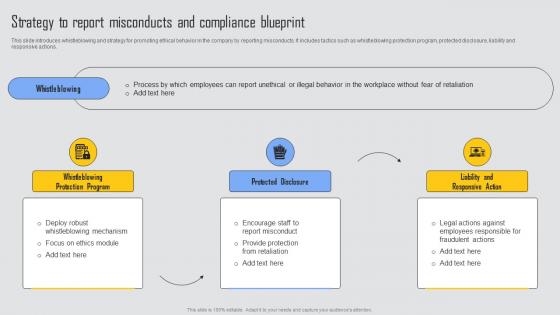
Strategy To Report Misconducts Managing Risks And Establishing Trust Through Efficient Diagrams Pdf
This slide introduces whistleblowing and strategy for promoting ethical behavior in the company by reporting misconducts. It includes tactics such as whistleblowing protection program, protected disclosure, liability and responsive actions. Get a simple yet stunning designed Strategy To Report Misconducts Managing Risks And Establishing Trust Through Efficient Diagrams Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Strategy To Report Misconducts Managing Risks And Establishing Trust Through Efficient Diagrams Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide introduces whistleblowing and strategy for promoting ethical behavior in the company by reporting misconducts. It includes tactics such as whistleblowing protection program, protected disclosure, liability and responsive actions.

Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Retrieve professionally designed Adopt Two Factor Authentication Comprehensive Guide To Blockchain Digital Security Ideas Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc.
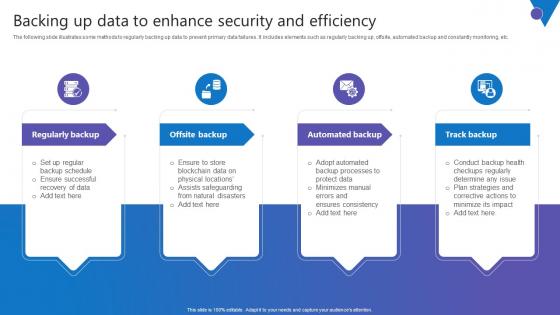
Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf
The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Backing Up Data To Enhance Comprehensive Guide To Blockchain Digital Security Download Pdf. The following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc.
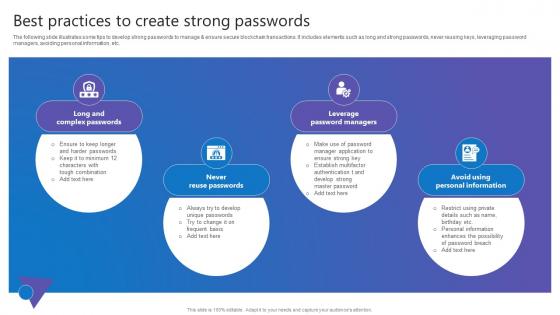
Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf
The following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc. This Best Practices To Create Comprehensive Guide To Blockchain Digital Security Clipart Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide illustrates some tips to develop strong passwords to manage and ensure secure blockchain transactions. It includes elements such as long and strong passwords, never reusing keys, leveraging password managers, avoiding personal information, etc.
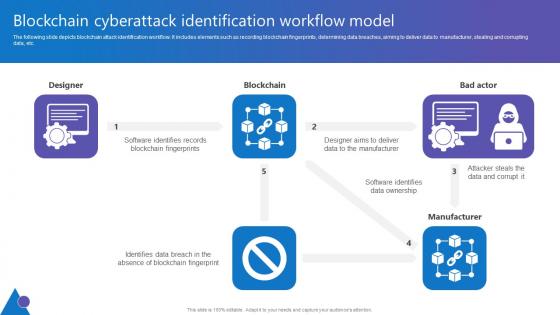
Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf
The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Take your projects to the next level with our ultimate collection of Blockchain Cyberattack Identification Comprehensive Guide To Blockchain Digital Security Microsoft Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc.
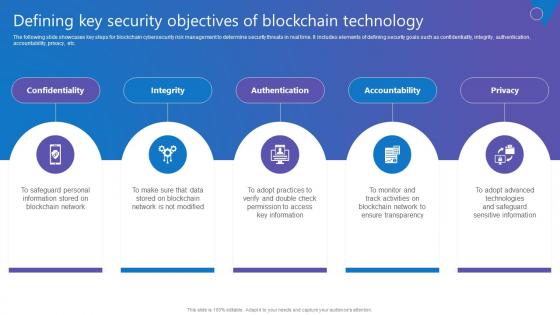
Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf
The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Want to ace your presentation in front of a live audience Our Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc.
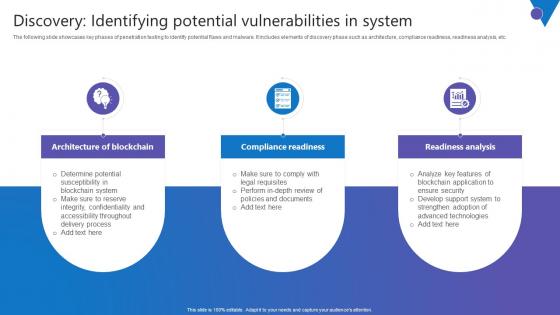
Discovery Identifying Potential Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc. There are so many reasons you need a Discovery Identifying Potential Comprehensive Guide To Blockchain Digital Security Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. The following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc.

How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Get a simple yet stunning designed How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit How Does Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc.
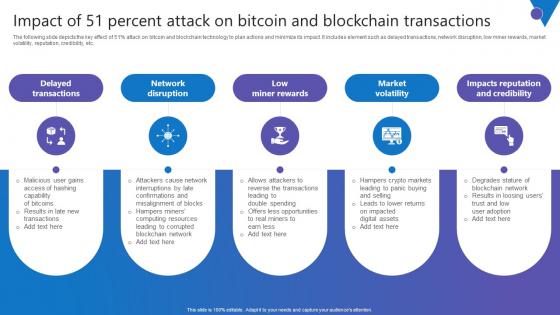
Impact Of 51 Percent Attack Comprehensive Guide To Blockchain Digital Security Infographics Pdf
The following slide depicts the key effect of 51percent attack on bitcoin and blockchain technology to plan actions and minimize its impact. It includes element such as delayed transactions, network disruption, low miner rewards, market volatility, reputation, credibility, etc. Present like a pro with Impact Of 51 Percent Attack Comprehensive Guide To Blockchain Digital Security Infographics Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide depicts the key effect of 51percent attack on bitcoin and blockchain technology to plan actions and minimize its impact. It includes element such as delayed transactions, network disruption, low miner rewards, market volatility, reputation, credibility, etc.
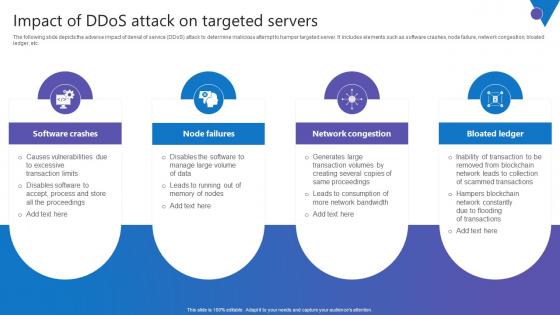
Impact Of DDoS Attack Comprehensive Guide To Blockchain Digital Security Sample Pdf
The following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc. Slidegeeks is here to make your presentations a breeze with Impact Of DDoS Attack Comprehensive Guide To Blockchain Digital Security Sample Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide depicts the adverse impact of denial of service DDoS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc.
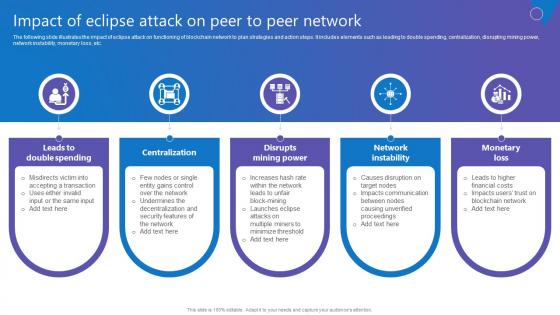
Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf today and make your presentation stand out from the rest The following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc.
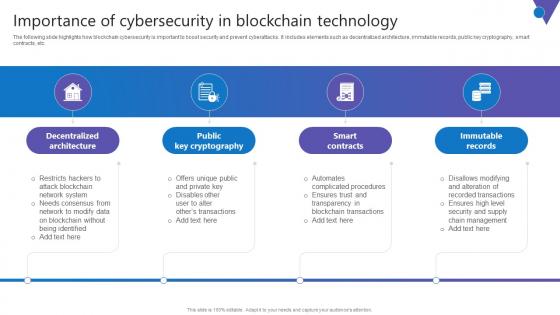
Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Find highly impressive Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc.

Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf
The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Statistics Associated Comprehensive Guide To Blockchain Digital Security Topics Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide depicts key facts related with blockchain frauds to ensure secure transactions. It includes elements such as hacking of decentralized finance, stolen funds, fraudulent schemes, cryptocurrency scams, etc.

Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc. This Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Methods To Identify Crypto Comprehensive Guide To Blockchain Digital Security Template Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide illustrates various methods to determine blockchain phishing attack and safeguard confidential information. It includes elements such as copycatting, spellings, ambiguous links, using public email ID, disordered content etc.
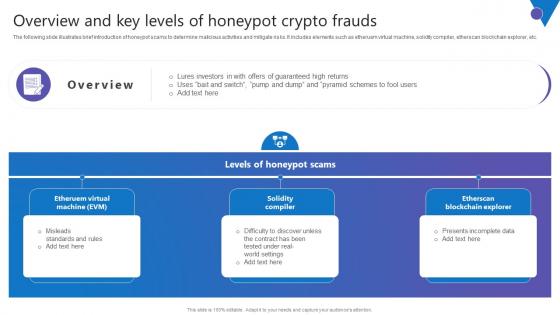
Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf
The following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as etheruem virtual machine, solidity compiler, etherscan blockchain explorer, etc. Welcome to our selection of the Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today The following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as etheruem virtual machine, solidity compiler, etherscan blockchain explorer, etc.
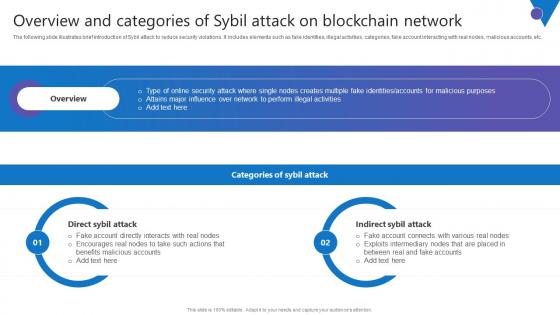
Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf
The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Are you searching for a Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf from Slidegeeks today. The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc.
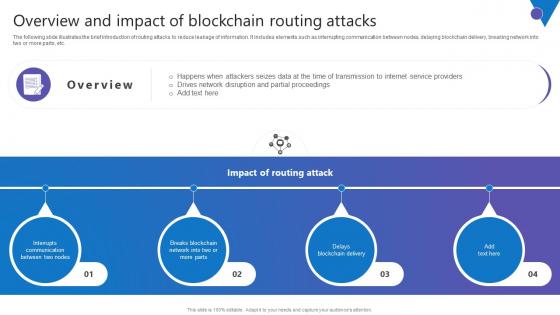
Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf
The following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc. Retrieve professionally designed Overview Impact Blockchain Comprehensive Guide To Blockchain Digital Security Pictures Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide illustrates the brief introduction of routing attacks to reduce leakage of information. It includes elements such as interrupting communication between nodes, delaying blockchain delivery, breaking network into two or more parts, etc.
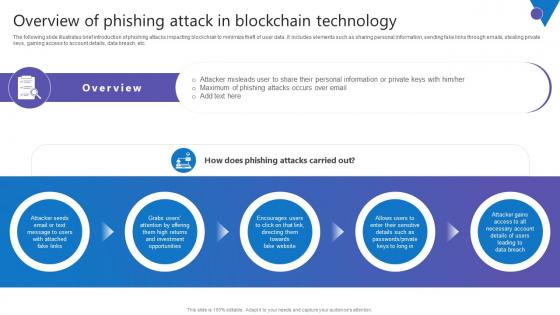
Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Presenting this PowerPoint presentation, titled Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Overview Of Phishing Attack Comprehensive Guide To Blockchain Digital Security Summary Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide illustrates brief introduction of phishing attacks impacting blockchian to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc.
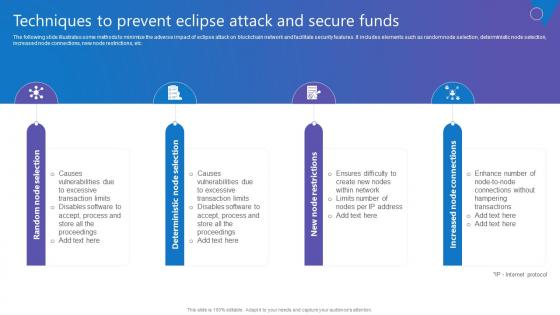
Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf
The following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Create an editable Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc.
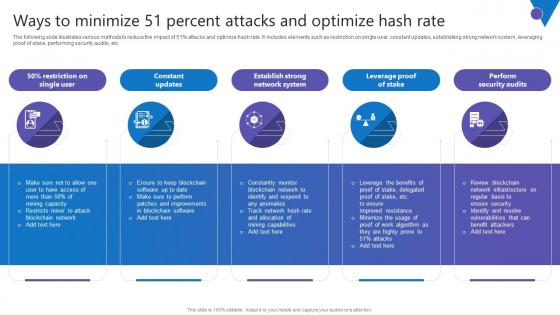
Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Present like a pro with Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc.
Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf
The following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Slidegeeks is here to make your presentations a breeze with Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc.
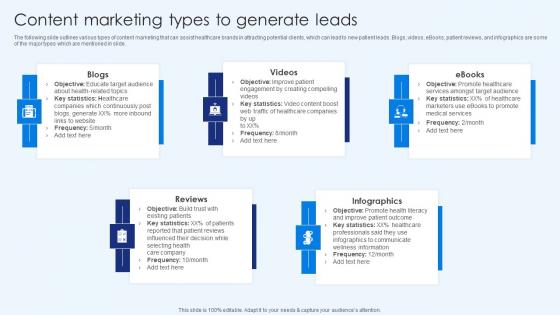
Content Marketing Types To Generate Leads Healthcare Promotion Background Pdf
The following slide outlines various types of content marketing that can assist healthcare brands in attracting potential clients, which can lead to new patient leads. Blogs, videos, eBooks, patient reviews, and infographics are some of the major types which are mentioned in slide. Get a simple yet stunning designed Determining Marketing Goals For Healthcare Company Healthcare Promotion Topics Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Determining Marketing Goals For Healthcare Company Healthcare Promotion Topics Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide outlines various types of content marketing that can assist healthcare brands in attracting potential clients, which can lead to new patient leads. Blogs, videos, eBooks, patient reviews, and infographics are some of the major types which are mentioned in slide.


 Continue with Email
Continue with Email

 Home
Home


































