List

How To Create Cost Effective Highlighting Various Categories Of Videos Strategy SS V
The following slide outlines multiple types of videos which can be posted on Facebook such as user-generated, informational, tutorial, and behind the scene. These kinds of videos can assist marketers in improving reach, conversions, and strengthening emotional relationship with customers. The How To Create Cost Effective Highlighting Various Categories Of Videos Strategy SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The following slide outlines multiple types of videos which can be posted on Facebook such as user-generated, informational, tutorial, and behind the scene. These kinds of videos can assist marketers in improving reach, conversions, and strengthening emotional relationship with customers.

How To Create Cost Effective Projected Cost Of Running Ads On Facebook Strategy SS V
The following slide outlines projected expenses which company incur while running paid advertising campaign on Facebook. Information covered in this slide is related to cost-per-click CPC, click-through rate CTR, cost-per-thousand CPM, cost-per-like CPL, cost-per-download, and cost-per-action CPA. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give How To Create Cost Effective Projected Cost Of Running Ads On Facebook Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable How To Create Cost Effective Projected Cost Of Running Ads On Facebook Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide outlines projected expenses which company incur while running paid advertising campaign on Facebook. Information covered in this slide is related to cost-per-click CPC, click-through rate CTR, cost-per-thousand CPM, cost-per-like CPL, cost-per-download, and cost-per-action CPA.

How To Create Cost Effective Strategies To Optimize Facebook Ads On Mobile Strategy SS V
The following slide outlines multiple techniques to streamline Facebook mobile advertisement. Tailor headlines, trim video, crop images, and carousel ads are the major techniques that can assist companies in reaching wider audience and improve user experience. Slidegeeks is here to make your presentations a breeze with How To Create Cost Effective Strategies To Optimize Facebook Ads On Mobile Strategy SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide outlines multiple techniques to streamline Facebook mobile advertisement. Tailor headlines, trim video, crop images, and carousel ads are the major techniques that can assist companies in reaching wider audience and improve user experience.
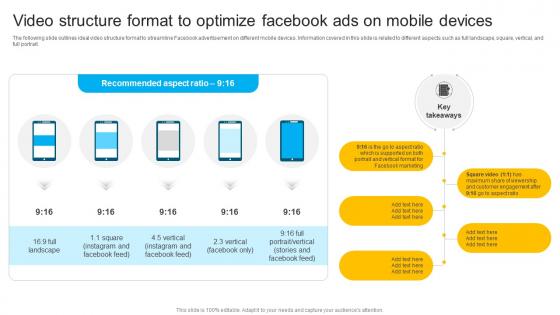
How To Create Cost Effective Video Structure Format To Optimize Facebook Strategy SS V
The following slide outlines ideal video structure format to streamline Facebook advertisement on different mobile devices. Information covered in this slide is related to different aspects such as full landscape, square, vertical, and full portrait. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How To Create Cost Effective Video Structure Format To Optimize Facebook Strategy SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide outlines ideal video structure format to streamline Facebook advertisement on different mobile devices. Information covered in this slide is related to different aspects such as full landscape, square, vertical, and full portrait.

Zero Trust Model Checklist To Build Zero Trust Network Access
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Checklist To Build Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Model Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Difference Between ZTNA And Software Defined Perimeter and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
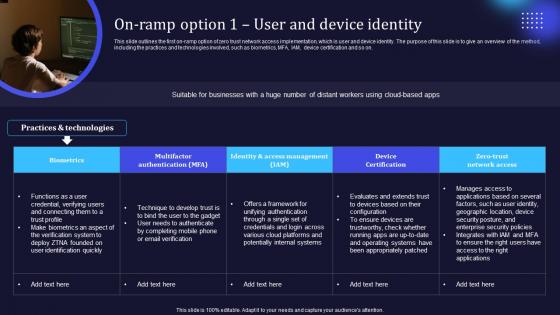
Zero Trust Model On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Retrieve professionally designed Zero Trust Model On Ramp Option 1 User And Device Identity to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

Zero Trust Model On Ramp Option 3 The Network
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Presenting this PowerPoint presentation, titled Zero Trust Model On Ramp Option 3 The Network, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Model On Ramp Option 3 The Network. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Model On Ramp Option 3 The Network that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Zero Trust Model Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Get a simple yet stunning designed Zero Trust Model Step 3 Assess The Environment. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Step 3 Assess The Environment can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
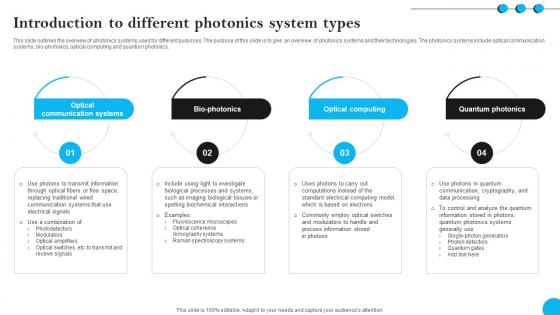
Fibers IT Introduction To Different Photonics System Types
This slide outlines the overview of photonics systems used for different purposes. The purpose of this slide is to give an overview of photonics systems and their technologies. The photonics systems include optical communication systems, bio-photonics, optical computing and quantum photonics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fibers IT Introduction To Different Photonics System Types to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the overview of photonics systems used for different purposes. The purpose of this slide is to give an overview of photonics systems and their technologies. The photonics systems include optical communication systems, bio-photonics, optical computing and quantum photonics.
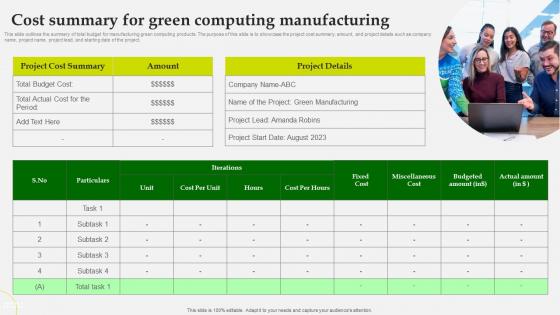
Green Computing Cost Summary For Green Computing Manufacturing
This slide outlines the summary of total budget for manufacturing green computing products. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Get a simple yet stunning designed Green Computing Cost Summary For Green Computing Manufacturing It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Green Computing Cost Summary For Green Computing Manufacturing can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the summary of total budget for manufacturing green computing products. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.

Green Computing Green Manufacturing Overview Materials And Suppliers
This slide outlines the overview of green manufacturing, including materials and suppliers. The purpose of this slide is to introduce green manufacturing, toxic chemicals used in average computers, materials used by manufacturers to build eco-friendly computer parts and companies with the eco-conscious production process. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Green Computing Green Manufacturing Overview Materials And Suppliers was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Green Computing Green Manufacturing Overview Materials And Suppliers This slide outlines the overview of green manufacturing, including materials and suppliers. The purpose of this slide is to introduce green manufacturing, toxic chemicals used in average computers, materials used by manufacturers to build eco-friendly computer parts and companies with the eco-conscious production process.
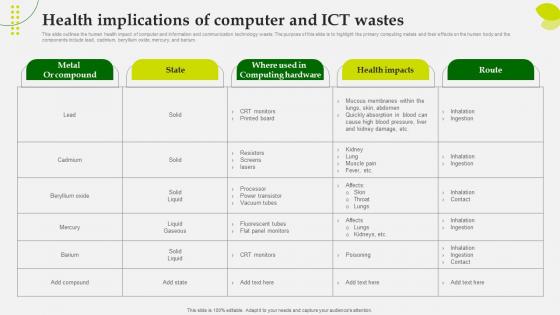
Green Computing Health Implications Of Computer And Ict Wastes
This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium. This Green Computing Health Implications Of Computer And Ict Wastes is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Green Computing Health Implications Of Computer And Ict Wastes features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium.
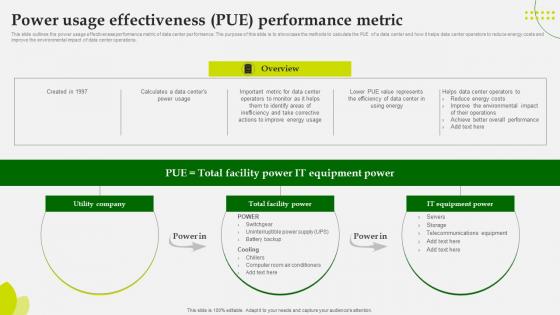
Green Computing Power Usage Effectiveness Pue Performance Metric
This slide outlines the power usage effectiveness performance metric of data center performance. The purpose of this slide is to showcase the methods to calculate the PUE of a data center and how it helps data center operators to reduce energy costs and improve the environmental impact of data center operations. Create an editable Green Computing Power Usage Effectiveness Pue Performance Metric that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Green Computing Power Usage Effectiveness Pue Performance Metric is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide outlines the power usage effectiveness performance metric of data center performance. The purpose of this slide is to showcase the methods to calculate the PUE of a data center and how it helps data center operators to reduce energy costs and improve the environmental impact of data center operations.

Sustainable Green Computing Design Overview And Features
This slide outlines the overview of green design in green computing and its various aspects of it. The purpose of this slide is to give an overview of green design and its features, including product longevity, size, modularity, end-of-life, and packaging. Retrieve professionally designed Sustainable Green Computing Design Overview And Features to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the overview of green design in green computing and its various aspects of it. The purpose of this slide is to give an overview of green design and its features, including product longevity, size, modularity, end-of-life, and packaging.

Sustainable Health Implications Of Computer And ICT Wastes
This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium. Take your projects to the next level with our ultimate collection of Sustainable Health Implications Of Computer And ICT Wastes. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium.
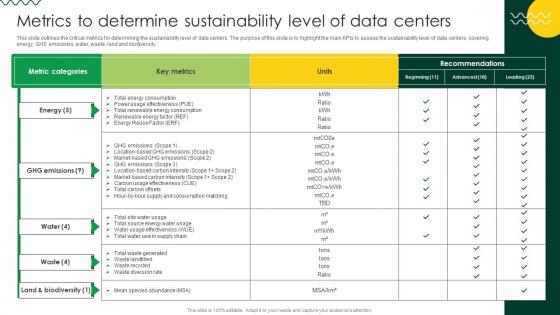
Sustainable Metrics To Determine Sustainability Level Of Data Centers
This slide outlines the critical metrics for determining the sustainability level of data centers. The purpose of this slide is to highlight the main KPIs to assess the sustainability level of data centers, covering energy, GHS emissions, water, waste, land and biodiversity. Get a simple yet stunning designed Sustainable Metrics To Determine Sustainability Level Of Data Centers. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Sustainable Metrics To Determine Sustainability Level Of Data Centers can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the critical metrics for determining the sustainability level of data centers. The purpose of this slide is to highlight the main KPIs to assess the sustainability level of data centers, covering energy, GHS emissions, water, waste, land and biodiversity.

Sustainable Strategies To Migrate Towards Sustainable Green Cloud Computing
This slide outlines the five methods to migrate toward sustainable green cloud computing in an organization. The purpose of this slide is to showcase the various strategies for migrating towards sustainable green cloud computing, including nano data centers, IaaS for effective infrastructure utilization, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Sustainable Strategies To Migrate Towards Sustainable Green Cloud Computing was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Sustainable Strategies To Migrate Towards Sustainable Green Cloud Computing This slide outlines the five methods to migrate toward sustainable green cloud computing in an organization. The purpose of this slide is to showcase the various strategies for migrating towards sustainable green cloud computing, including nano data centers, IaaS for effective infrastructure utilization, etc.

Sustainable Types Of Green Data Centers Energy Efficient
This slide outlines the overview of energy efficient types of green data centers. The purpose of this slide is to showcase the different energy efficiency methods, including cooling systems, green cloud technology and community heating and cooling. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Sustainable Types Of Green Data Centers Energy Efficient. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Sustainable Types Of Green Data Centers Energy Efficient today and make your presentation stand out from the rest This slide outlines the overview of energy efficient types of green data centers. The purpose of this slide is to showcase the different energy efficiency methods, including cooling systems, green cloud technology and community heating and cooling.
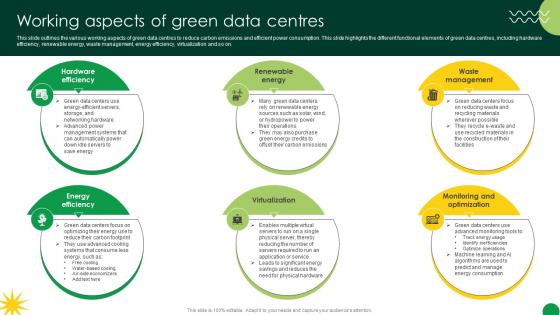
Sustainable Working Aspects Of Green Data Centres
This slide outlines the various working aspects of green data centres to reduce carbon emissions and efficient power consumption. This slide highlights the different functional elements of green data centres, including hardware efficiency, renewable energy, waste management, energy efficiency, virtualization and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Sustainable Working Aspects Of Green Data Centres template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Sustainable Working Aspects Of Green Data Centres that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the various working aspects of green data centres to reduce carbon emissions and efficient power consumption. This slide highlights the different functional elements of green data centres, including hardware efficiency, renewable energy, waste management, energy efficiency, virtualization and so on.
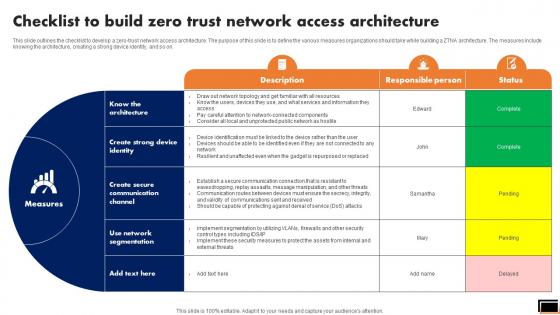
Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Want to ace your presentation in front of a live audience Our Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
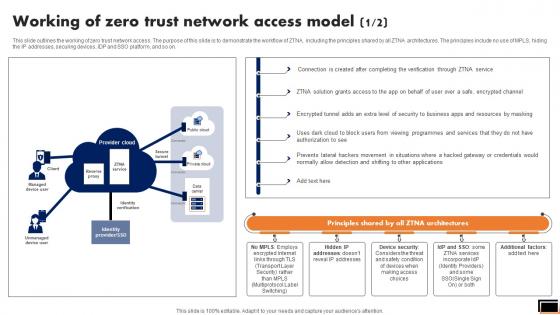
Working Of Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Zero Trust Network Access Model Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Business Development Team Set Up Live Chat Feature On Website SA SS V
The following slide outlines step by step guide to integrate live chat on website, including steps such as select right CRM platform, integrate and customise, create agent profiles, set service hours, and integrate channels and connect CRM. Do you know about Slidesgeeks Business Development Team Set Up Live Chat Feature On Website SA SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The following slide outlines step by step guide to integrate live chat on website, including steps such as select right CRM platform, integrate and customise, create agent profiles, set service hours, and integrate channels and connect CRM.

Case Study 1 Wembley Park Adopted Evac Waste Management IOT Applications In Smart Waste IoT SS V
This slide outlines a case study of how Wembley Park transformed waste collection by utilizing an effective smart waste management system. It includes elements such as overview, project name, collaboration partner, challenges, and solutions implemented. Get a simple yet stunning designed Case Study 1 Wembley Park Adopted Evac Waste Management IOT Applications In Smart Waste IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Case Study 1 Wembley Park Adopted Evac Waste Management IOT Applications In Smart Waste IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines a case study of how Wembley Park transformed waste collection by utilizing an effective smart waste management system. It includes elements such as overview, project name, collaboration partner, challenges, and solutions implemented.
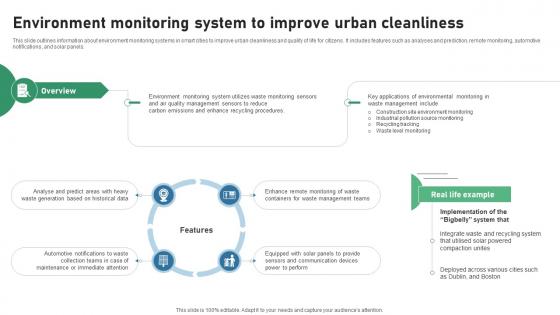
Environment Monitoring System To Improve Urban Cleanliness IOT Applications In Smart Waste IoT SS V
This slide outlines information about environment monitoring systems in smart cities to improve urban cleanliness and quality of life for citizens. It includes features such as analyses and prediction, remote monitoring, automotive notifications, and solar panels. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Environment Monitoring System To Improve Urban Cleanliness IOT Applications In Smart Waste IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Environment Monitoring System To Improve Urban Cleanliness IOT Applications In Smart Waste IoT SS V today and make your presentation stand out from the rest This slide outlines information about environment monitoring systems in smart cities to improve urban cleanliness and quality of life for citizens. It includes features such as analyses and prediction, remote monitoring, automotive notifications, and solar panels.
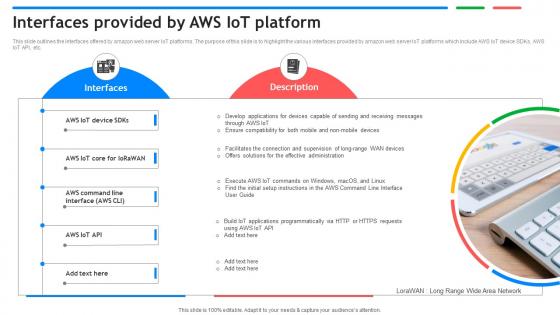
Interfaces Provided By Aws IoT Platform Exploring Google Cloud IoT Platform
This slide outlines the interfaces offered by amazon web server IoT platforms. The purpose of this slide is to highlight the various interfaces provided by amazon web server IoT platforms which include AWS IoT device SDKs, AWS IoT API, etc. This modern and well arranged Interfaces Provided By Aws IoT Platform Exploring Google Cloud IoT Platform provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide outlines the interfaces offered by amazon web server IoT platforms. The purpose of this slide is to highlight the various interfaces provided by amazon web server IoT platforms which include AWS IoT device SDKs, AWS IoT API, etc.

Key Benefits For Samsung Artik Customers Exploring Google Cloud IoT Platform
This slide outlines the various advantages for customers of Samsung ARTIK. The purpose of this slide is to highlight the key benefits for Samsung ARTIK customers which include quicker pace, amplified speed of application, etc. Retrieve professionally designed Key Benefits For Samsung Artik Customers Exploring Google Cloud IoT Platform to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various advantages for customers of Samsung ARTIK. The purpose of this slide is to highlight the key benefits for Samsung ARTIK customers which include quicker pace, amplified speed of application, etc.

Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform
This slide outlines the various advantages of IoT platform utilization. The purpose of this slide is to showcase the key benefits of using IoT platforms which include scalability, security, cost saving, etc. Presenting this PowerPoint presentation, titled Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the various advantages of IoT platform utilization. The purpose of this slide is to showcase the key benefits of using IoT platforms which include scalability, security, cost saving, etc.

Audience And Influencer Analysis Of Social Media Analytics Cracking The Code Of Social Media
This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc. Create an editable Audience And Influencer Analysis Of Social Media Analytics Cracking The Code Of Social Media that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Audience And Influencer Analysis Of Social Media Analytics Cracking The Code Of Social Media is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc.

Current Trends Enhancing Performance Of Secure Web Gateway Web Threat Protection System
This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc. Slidegeeks is here to make your presentations a breeze with Current Trends Enhancing Performance Of Secure Web Gateway Web Threat Protection System With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the recent developments for Secure Web Gateway. The purpose of this slide is to briefly explain the top current SWG trends. These include cloud based SWG, advanced threat protection, user behavior analytics, Secure Access Service Edge, etc.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
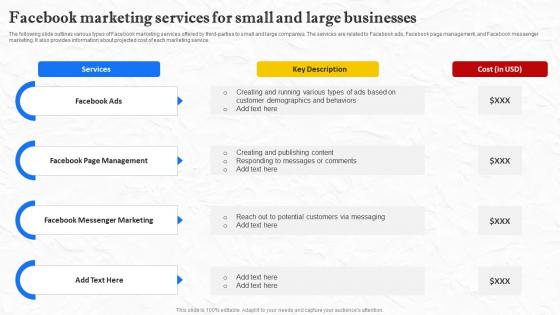
A41 Facebook Marketing Services For Small And Large Businesses Strategy SS V
The following slide outlines various types of Facebook marketing services offered by third-parties to small and large companies. The services are related to Facebook ads, Facebook page management, and Facebook messenger marketing. It also provides information about projected cost of each marketing service. Create an editable A41 Facebook Marketing Services For Small And Large Businesses Strategy SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. A41 Facebook Marketing Services For Small And Large Businesses Strategy SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide outlines various types of Facebook marketing services offered by third-parties to small and large companies. The services are related to Facebook ads, Facebook page management, and Facebook messenger marketing. It also provides information about projected cost of each marketing service.
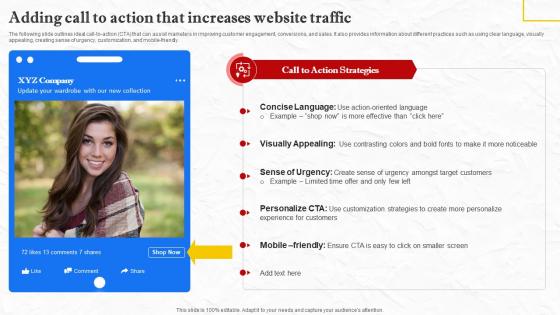
Facebook Marketing Techniques Adding Call To Action That Increases Website Strategy SS V
The following slide outlines ideal call-to-action CTA that can assist marketers in improving customer engagement, conversions, and sales. It also provides information about different practices such as using clear language, visually appealing, creating sense of urgency, customization, and mobile-friendly. Get a simple yet stunning designed Facebook Marketing Techniques Adding Call To Action That Increases Website Strategy SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Facebook Marketing Techniques Adding Call To Action That Increases Website Strategy SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide outlines ideal call-to-action CTA that can assist marketers in improving customer engagement, conversions, and sales. It also provides information about different practices such as using clear language, visually appealing, creating sense of urgency, customization, and mobile-friendly.
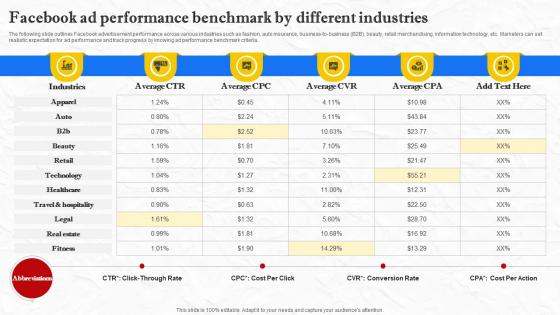
Facebook Marketing Techniques Facebook Ad Performance Benchmark Strategy SS V
The following slide outlines Facebook advertisement performance across various industries such as fashion, auto insurance, business-to-business B2B , beauty, retail merchandising, information technology, etc. Marketers can set realistic expectation for ad performance and track progress by knowing ad performance benchmark criteria. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Facebook Marketing Techniques Facebook Ad Performance Benchmark Strategy SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Facebook Marketing Techniques Facebook Ad Performance Benchmark Strategy SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide outlines Facebook advertisement performance across various industries such as fashion, auto insurance, business-to-business B2B , beauty, retail merchandising, information technology, etc. Marketers can set realistic expectation for ad performance and track progress by knowing ad performance benchmark criteria.

Facebook Marketing Techniques Factors Determine Cost Of Facebook Strategy SS V
The following slide outlines various factors that determines cost of running ads on Facebook platform such as audience targeting, ad format, ad placement, ad frequency. By carefully considering these factors, advertisers can optimize their ad campaigns and achieve marketing objectives. This modern and well-arranged Facebook Marketing Techniques Factors Determine Cost Of Facebook Strategy SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The following slide outlines various factors that determines cost of running ads on Facebook platform such as audience targeting, ad format, ad placement, ad frequency. By carefully considering these factors, advertisers can optimize their ad campaigns and achieve marketing objectives.

Facebook Marketing Techniques Fictional Representation Of Buyer Persona Strategy SS V
The following slide outlines semi-fictional representation of customer persona for Facebook marketing that can assist companies in creating targeted content. Information covered in this slide is related to buyer objectives, pain points, buying triggers, lifestyle, social media, content preferences, hashtags, etc. This Facebook Marketing Techniques Fictional Representation Of Buyer Persona Strategy SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Facebook Marketing Techniques Fictional Representation Of Buyer Persona Strategy SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide outlines semi-fictional representation of customer persona for Facebook marketing that can assist companies in creating targeted content. Information covered in this slide is related to buyer objectives, pain points, buying triggers, lifestyle, social media, content preferences, hashtags, etc.
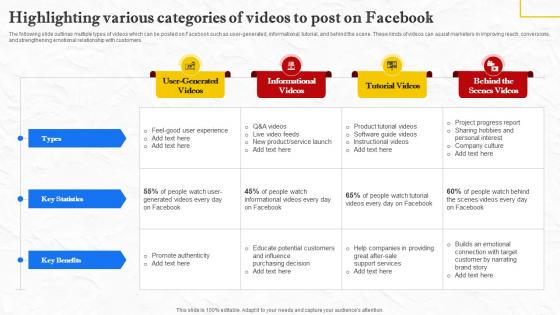
Facebook Marketing Techniques Highlighting Various Categories Of Videos To Post Strategy SS V
The following slide outlines multiple types of videos which can be posted on Facebook such as user-generated, informational, tutorial, and behind the scene. These kinds of videos can assist marketers in improving reach, conversions, and strengthening emotional relationship with customers. The Facebook Marketing Techniques Highlighting Various Categories Of Videos To Post Strategy SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The following slide outlines multiple types of videos which can be posted on Facebook such as user-generated, informational, tutorial, and behind the scene. These kinds of videos can assist marketers in improving reach, conversions, and strengthening emotional relationship with customers.
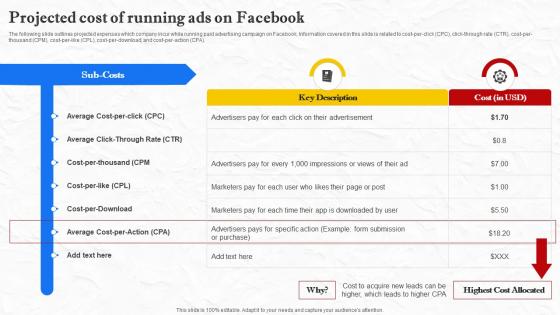
Facebook Marketing Techniques Projected Cost Of Running Ads On Facebook Strategy SS V
The following slide outlines projected expenses which company incur while running paid advertising campaign on Facebook. Information covered in this slide is related to cost-per-click CPC , click-through rate CTR , cost-per-thousand CPM , cost-per-like CPL , cost-per-download, and cost-per-action CPA . Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Facebook Marketing Techniques Projected Cost Of Running Ads On Facebook Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Facebook Marketing Techniques Projected Cost Of Running Ads On Facebook Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide outlines projected expenses which company incur while running paid advertising campaign on Facebook. Information covered in this slide is related to cost-per-click CPC , click-through rate CTR , cost-per-thousand CPM , cost-per-like CPL , cost-per-download, and cost-per-action CPA .

Facebook Marketing Techniques Strategies To Optimize Facebook Ads On Mobile Strategy SS V
The following slide outlines multiple techniques to streamline Facebook mobile advertisement. Tailor headlines, trim video, crop images, and carousel ads are the major techniques that can assist companies in reaching wider audience and improve user experience. Slidegeeks is here to make your presentations a breeze with Facebook Marketing Techniques Strategies To Optimize Facebook Ads On Mobile Strategy SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide outlines multiple techniques to streamline Facebook mobile advertisement. Tailor headlines, trim video, crop images, and carousel ads are the major techniques that can assist companies in reaching wider audience and improve user experience.

Facebook Marketing Techniques User Generated Content Example To Increase Customer Strategy SS V
The following slide outlines ideal user generated content which can be used by companies to build engagement, trust and community around brand. It covers information about practices such as asking for feedback, sharing customer success stories, collaborating with social media influencers, and hosting live events. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Facebook Marketing Techniques User Generated Content Example To Increase Customer Strategy SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide outlines ideal user generated content which can be used by companies to build engagement, trust and community around brand. It covers information about practices such as asking for feedback, sharing customer success stories, collaborating with social media influencers, and hosting live events.
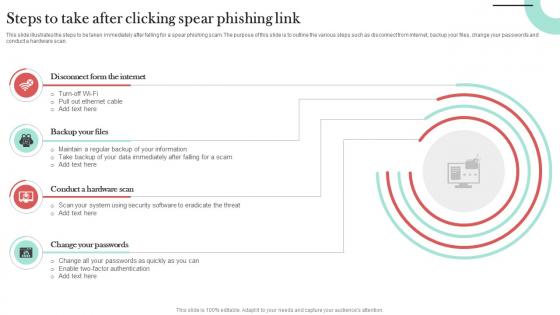
Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT
This slide illustrates the steps to be taken immediately after falling for a spear phishing scam. The purpose of this slide is to outline the various steps such as disconnect from internet, backup your files, change your passwords and conduct a hardware scan. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide illustrates the steps to be taken immediately after falling for a spear phishing scam. The purpose of this slide is to outline the various steps such as disconnect from internet, backup your files, change your passwords and conduct a hardware scan.

On Ramp Option 3 The Network Zero Trust Network Access
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than On Ramp Option 3 The Network Zero Trust Network Access. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab On Ramp Option 3 The Network Zero Trust Network Access today and make your presentation stand out from the rest This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Zero Trust Network Access Future And Emerging Trends In ZTNA Model
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Future And Emerging Trends In ZTNA Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Future And Emerging Trends In ZTNA Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Future And Emerging Trends In ZTNA Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.

Zero Trust Network Access Main Pillars Of Zero Network Trust Access
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Do you know about Slidesgeeks Zero Trust Network Access Main Pillars Of Zero Network Trust Access These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation.

Zero Trust Network Access On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Boost your pitch with our creative Zero Trust Network Access On Ramp Option 1 User And Device Identity. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
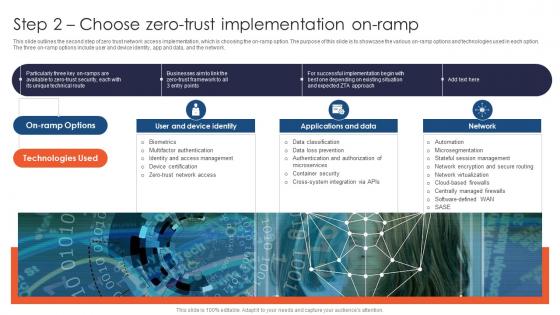
Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Find highly impressive Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.

CASB 2 0 IT CASB Deployment With Optional Components Pricing
This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CASB 2 0 IT CASB Deployment With Optional Components Pricing. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CASB 2 0 IT CASB Deployment With Optional Components Pricing today and make your presentation stand out from the rest This slide outlines the pricing of CASB deployment with optional or add-on components. The purpose of this slide is to showcase the pricing of additional components in CASB deployment, including data security subscription, support, threat protection subscription, data retention, and so on.
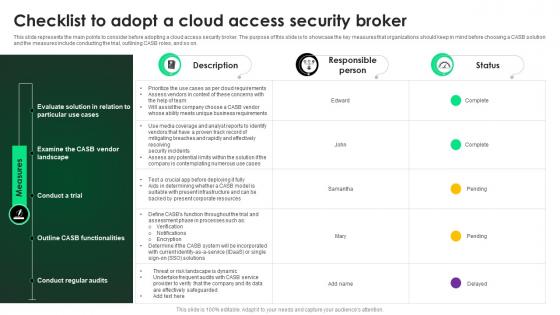
CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers. This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on.

CASB 2 0 IT Cloud Access Security Broker Architectural Components
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. This modern and well-arranged CASB 2 0 IT Cloud Access Security Broker Architectural Components provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on.
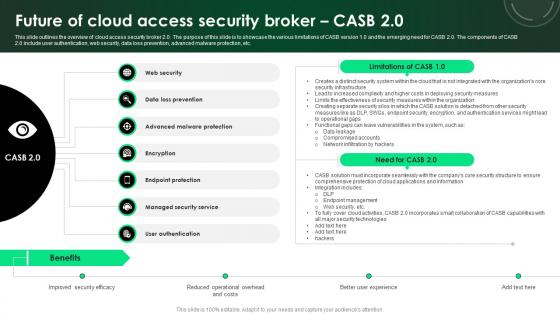
CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0 for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc.

CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment
This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc. Slidegeeks is here to make your presentations a breeze with CASB 2 0 IT Pros And Cons Of API Scanning CASB Deployment With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the advantages and disadvantages of the API scanning cloud access security broker deployment model. This slide aims to highlight the pros and cons of the API scanning deployment model and the benefits include no impact on user experience, taking only a few hours to configure, etc.
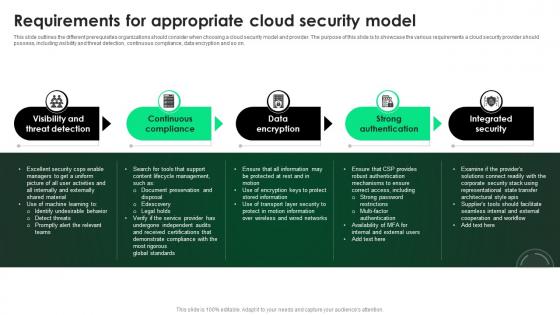
CASB 2 0 IT Requirements For Appropriate Cloud Security Model
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Find highly impressive CASB 2 0 IT Requirements For Appropriate Cloud Security Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CASB 2 0 IT Requirements For Appropriate Cloud Security Model for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on.

CASB 2 0 IT Shadow It Management Lifecycle Overview
This slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download CASB 2 0 IT Shadow It Management Lifecycle Overview and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring.

CASB 2 0 IT Steps To Deploy Cloud Access Security Broker
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Steps To Deploy Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Steps To Deploy Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model.

CASB 2 0 IT Why CASB Is Important For Businesses
This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management. This CASB 2 0 IT Why CASB Is Important For Businesses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Why CASB Is Important For Businesses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the importance of CASB for different organizations. The purpose of this slide is to showcase the various reasons for businesses to invest in the cloud access security broker model, including increased cloud adoption, better security, compliance, and cost-effective and centralized management.

About Hot Crypto Wallets Overview And Types Cryptocurrency Management With Blockchain
This slide discusses the key takeaways to keep in mind regarding Hot Wallets. This slide outlines that hot wallets which are connected to the internet and very easy to access are beginner-friendly and enable the storing, receiving, and sending of tokens.Create an editable About Hot Crypto Wallets Overview And Types Cryptocurrency Management With Blockchain that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Hot Crypto Wallets Overview And Types Cryptocurrency Management With Blockchain is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide discusses the key takeaways to keep in mind regarding Hot Wallets. This slide outlines that hot wallets which are connected to the internet and very easy to access are beginner-friendly and enable the storing, receiving, and sending of tokens.
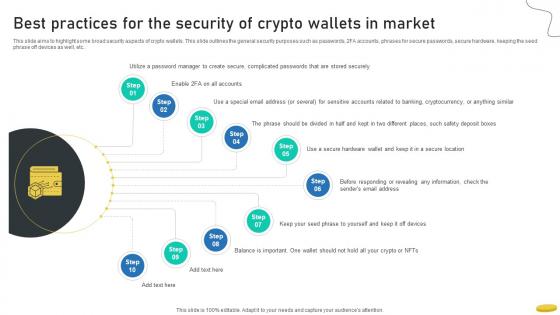
Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain
This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For The Security Of Crypto Wallets In Market Cryptocurrency Management With Blockchain today and make your presentation stand out from the rest This slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc.
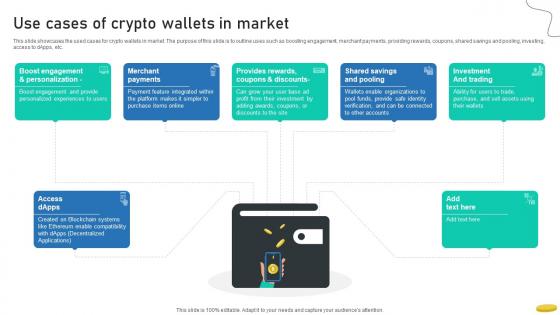
Use Cases Of Crypto Wallets In Market Cryptocurrency Management With Blockchain
This slide showcases the used cases for crypto wallets in market. The purpose of this slide is to outline uses such as boosting engagement, merchant payments, providing rewards, coupons, shared savings and pooling, investing, access to dApps, etc.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Use Cases Of Crypto Wallets In Market Cryptocurrency Management With Blockchain was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Use Cases Of Crypto Wallets In Market Cryptocurrency Management With Blockchain. This slide showcases the used cases for crypto wallets in market. The purpose of this slide is to outline uses such as boosting engagement, merchant payments, providing rewards, coupons, shared savings and pooling, investing, access to dApps, etc.


 Continue with Email
Continue with Email

 Home
Home


































