Lock Icon
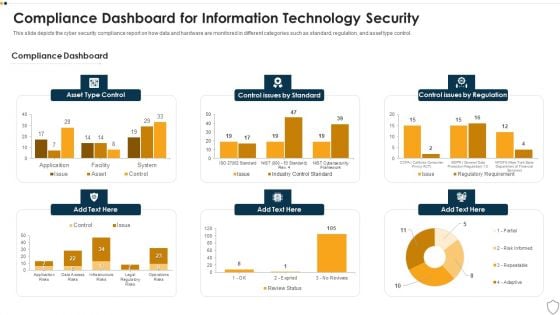
IT Security Compliance Dashboard For Information Technology Security Ppt Slides Brochure PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative it security compliance dashboard for information technology security ppt slides brochure pdf bundle. Topics like asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Requirement Of Information Technology Security In Different Sectors Ppt File Display PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative it security requirement of information technology security in different sectors ppt file display pdf bundle. Topics like business transactions, organizations, financial, process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
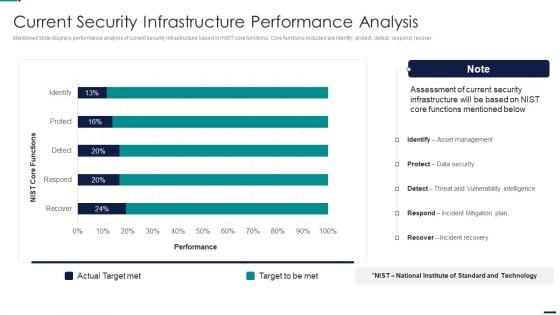
Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF. Use them to share invaluable insights on Identify, Protect, Detect, Respond, Recover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
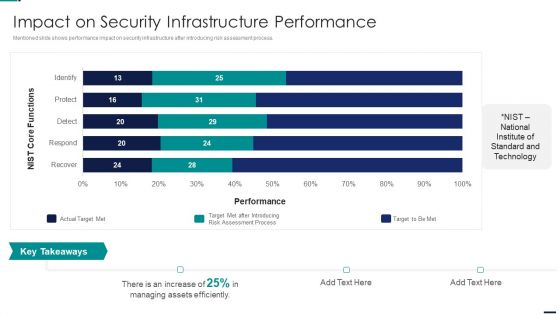
Risk Management Model For Data Security Impact On Security Infrastructure Performance Elements PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Impact On Security Infrastructure Performance Elements PDF. Use them to share invaluable insights on Identify, Protect, Detect, Respond, Recover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
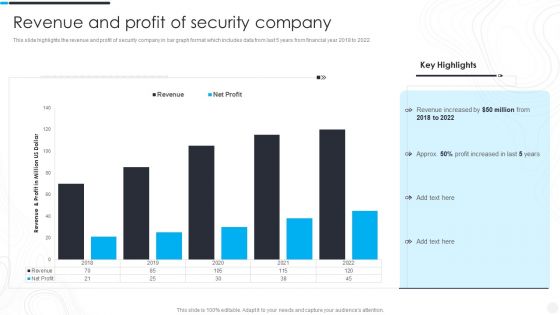
Security Camera System Company Profile Revenue And Profit Of Security Company Clipart PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Revenue And Profit Of Security Company Clipart PDF. Use them to share invaluable insights on Revenue Increased, Profit Increased, Key Highlights and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
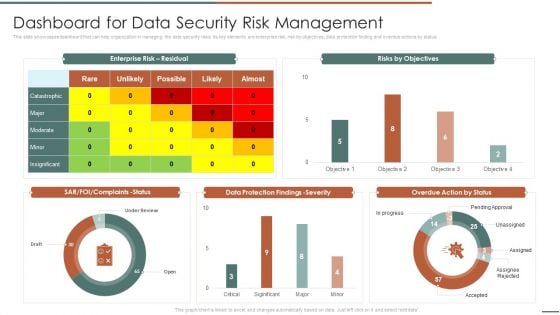
Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF bundle. Topics like Complaints Status, Protection Findings, Overdue Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
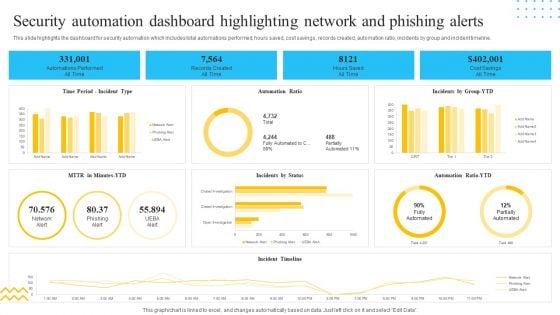
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF bundle. Topics like Records Created, All Time, Hours Saved, Cost Savings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
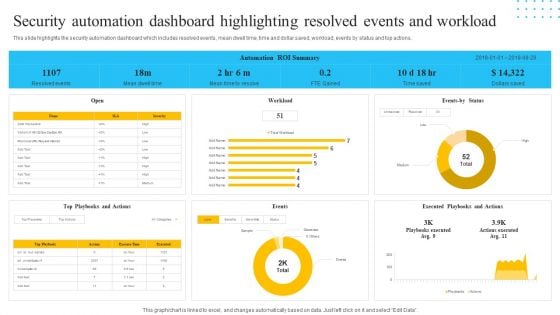
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF bundle. Topics like Events Status, Workload, Events, Open can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
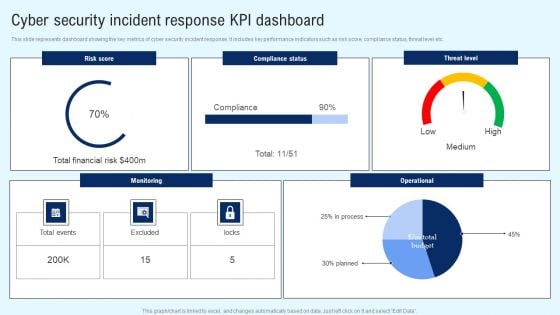
Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
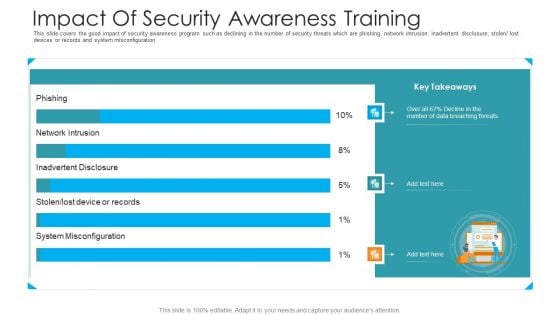
Impact Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Infographics PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe inspiring pitch with this creative impact of security awareness training hacking prevention awareness training for it security infographics pdf bundle. Topics like system misconfiguration, network intrusion breakdown, phishing breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
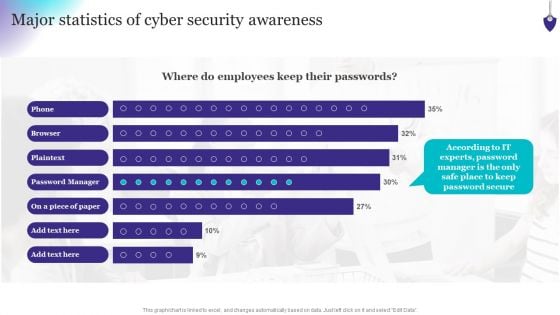
Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Welcome to our selection of the Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
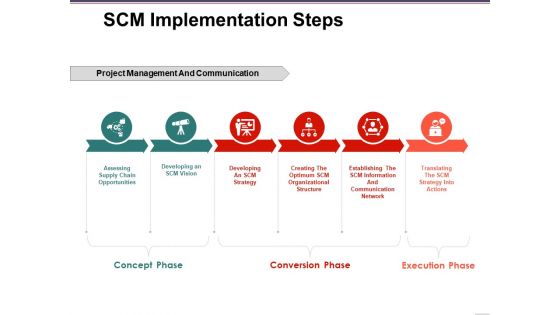
Scm Implementation Steps Ppt PowerPoint Presentation Infographic Template Example Topics
This is a scm implementation steps ppt powerpoint presentation infographic template example topics. This is a six stage process. The stages in this process are developing an scm vision, developing an scm strategy, translating the scm strategy into actions, assessing supply chain opportunities, concept phase.

Alert Traffic Cones PowerPoint Slides And Ppt Diagram Templates
Alert Traffic Cones PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT! Approve plans with our Alert Traffic Cones PowerPoint Slides And Ppt Diagram Templates. You will come out on top.

Road Directions PowerPoint Slides And Ppt Diagram Templates
Road Directions PowerPoint Slides And PPT Diagram Templates These high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Coach subordinates with our Road Directions PowerPoint Slides And Ppt Diagram Templates. Download without worries with our money back guaranteee.
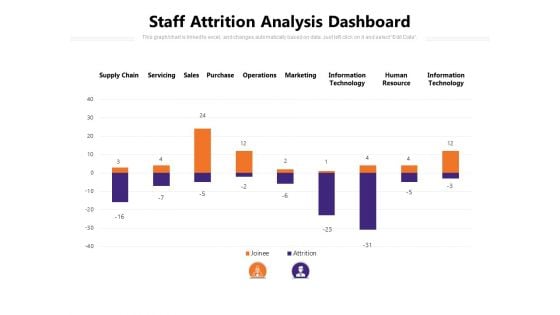
Staff Attrition Analysis Dashboard Ppt PowerPoint Presentation Inspiration Show PDF
Presenting this set of slides with name staff attrition analysis dashboard ppt powerpoint presentation inspiration show pdf. The topics discussed in these slides are supply chain, servicing, sales, purchase, operations, marketing, information technology, human resource, information technology. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
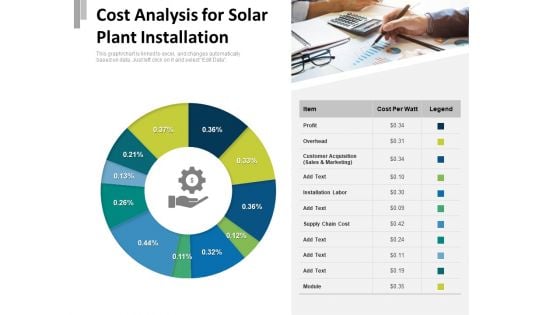
Cost Analysis For Solar Plant Installation Ppt PowerPoint Presentation Ideas Smartart PDF
Presenting this set of slides with name cost analysis for solar plant installation ppt powerpoint presentation ideas smartart pdf. The topics discussed in these slides are profit, supply chain cost, overhead, installation labor, customer acquisition, sales and marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
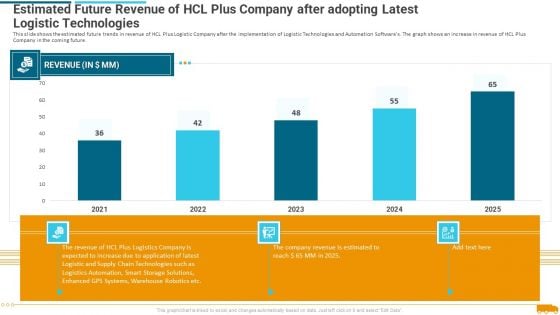
Estimated Future Revenue Of Hcl Plus Company After Adopting Latest Logistic Technologies Rules PDF
Deliver an awe inspiring pitch with this creative estimated future revenue of hcl plus company after adopting latest logistic technologies rules pdf bundle. Topics like warehouse, application, supply chain, revenue, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
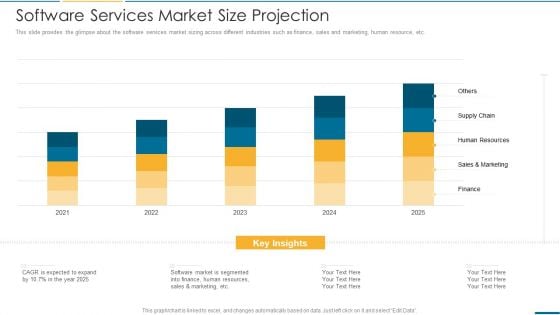
Computer Operating System Services Investment Fundraising Software Services Market Size Projection Clipart PDF
Deliver an awe inspiring pitch with this creative computer operating system services investment fundraising software services market size projection clipart pdf bundle. Topics like human resources, sales and marketing, supply chain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
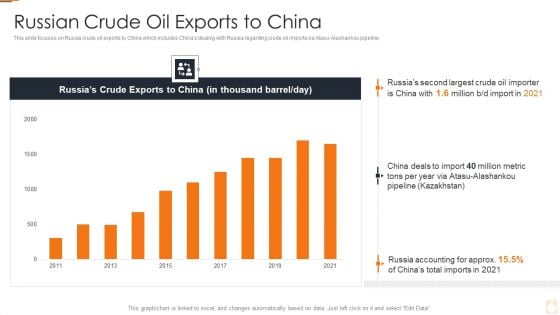
Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF
Deliver an awe inspiring pitch with this creative Ukraine Russia Conflict Effect On Petroleum Industry Russian Crude Oil Exports To China Information PDF bundle. Topics like Higher Energy Prices, Trade And Supply Chains, Increase In Cyber Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Dashboard For Threat Tracking In Data Security Summary PDF
Deliver an awe inspiring pitch with this creative information security dashboard for threat tracking in data security summary pdf bundle. Topics like monthly threat status, current risk status, threats based on role, threats by owners, risk by threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
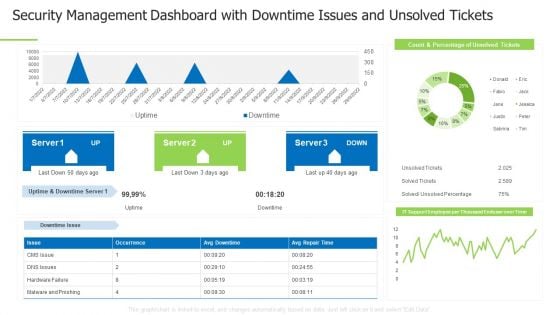
Techniques And Strategies To Reduce Security Management Risks Security Management Dashboard Information PDF
Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks security management dashboard information pdf bundle. Topics like logical access control, physical access control, access control categories can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
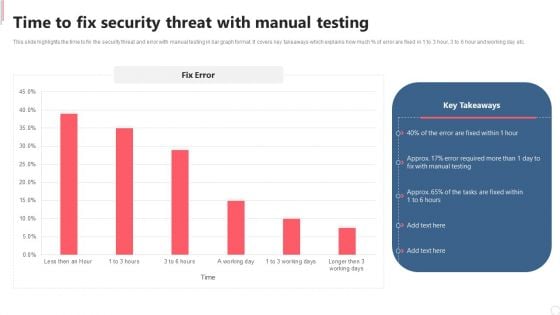
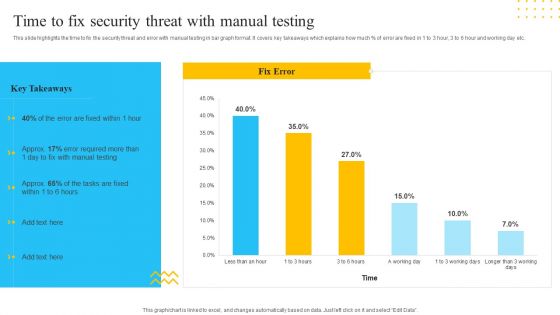
Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. This Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Security Automation Systems Guide Time To Fix Security Threat With Manual Testing Topics PDF
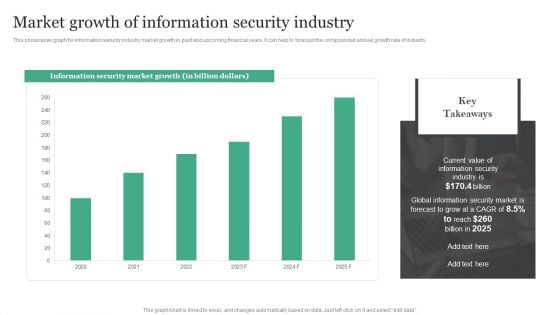
Market Growth Of Information Security Industry Information Security Risk Administration Rules PDF
This showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. This Market Growth Of Information Security Industry Information Security Risk Administration Rules PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Market Growth Of Information Security Industry Information Security Risk Administration Rules PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
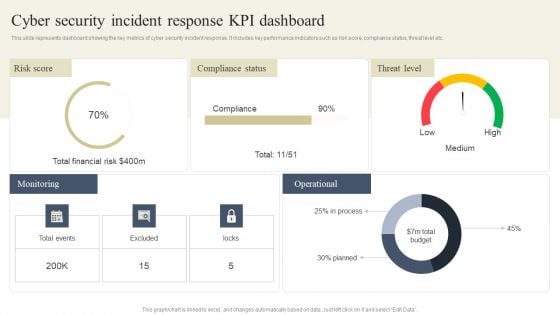
CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
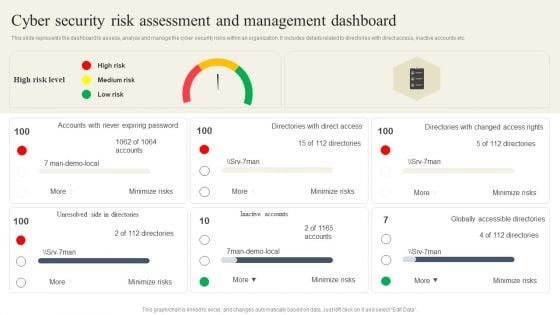
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. This CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Get a simple yet stunning designed Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Hand Putting Money In Saving Future PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with hand putting money into saving pig finance theme Our Hand Putting Money In Saving Future PowerPoint Templates And PowerPoint Backgrounds 0311 are all encompassing. They cover each and every angle.

IT Security How Is Automation Used In Information Technology Security Ppt Diagram Lists PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting it security how is automation used in information technology security ppt diagram lists pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.
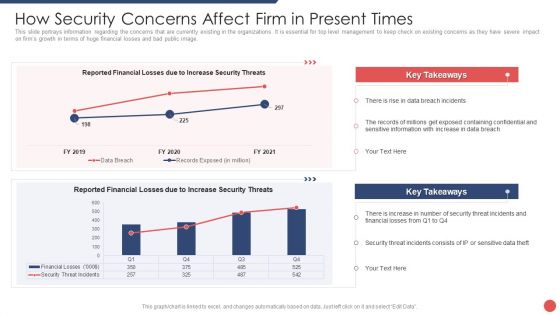
Security Functioning Centre How Security Concerns Affect Firm In Present Times Ideas PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver and pitch your topic in the best possible manner with this security functioning centre how security concerns affect firm in present times ideas pdf. Use them to share invaluable insights on financial, security threat, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Desktop Security Management Dashboard For Threat Tracking In Computer Security Guidelines PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative desktop security management dashboard for threat tracking in computer security guidelines pdf bundle. Topics like threats by owners, risk by threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
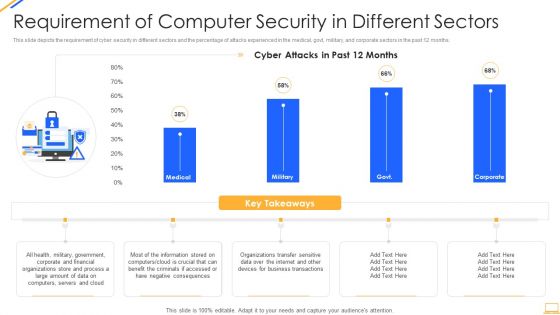
Desktop Security Management Requirement Of Computer Security In Different Sectors Sample PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this desktop security management requirement of computer security in different sectors sample pdf. Use them to share invaluable insights on information, organizations, financial, servers, internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Dashboard For Threat Tracking In Information Technology Security Ppt Inspiration Gallery PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative it security dashboard for threat tracking in information technology security ppt inspiration gallery pdf bundle. Topics like current risk status, threat report, risk by threats, threats based on role, threats by owners can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Compliance Dashboard Of Information Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative info security compliance dashboard of information security ppt powerpoint presentation file graphics download pdf bundle. Topics like compliance dashboard, asset type control, control issues by standard, control issues by regulation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Info Security Dashboard For Threat Tracking In Information Security Ppt PowerPoint Presentation File Example Introduction PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative info security dashboard for threat tracking in information security ppt powerpoint presentation file example introduction pdf bundle. Topics like threats by owners, risk by threats, threat report, monthly threat status, current risk status, threats based on role can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
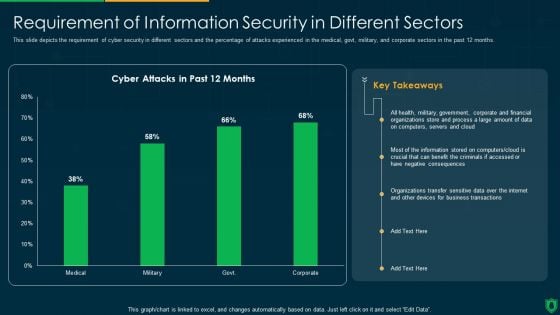
Info Security Requirement Of Information Security In Different Sectors Ppt PowerPoint Presentation File Grid PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative info security requirement of information security in different sectors ppt powerpoint presentation file grid pdf bundle. Topics like cyber attacks, past 12 months, organizations transfer, sensitive data over internet can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
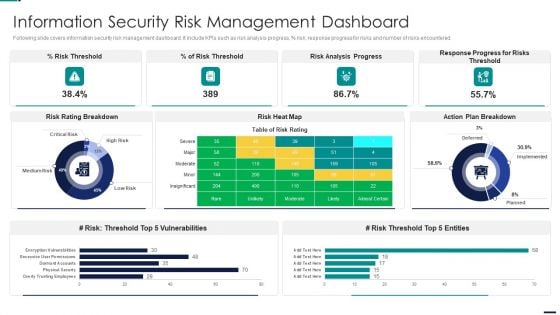
Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF bundle. Topics like Risk Threshold, Risk Analysis Progress, Response Progress For Risks Threshold, Action Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
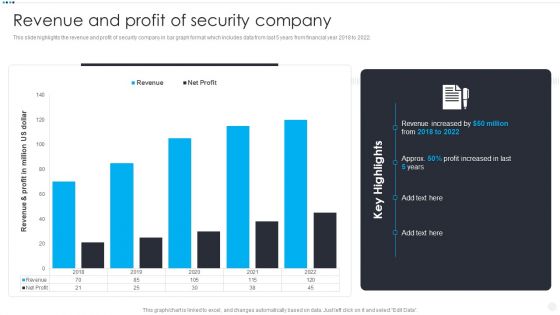
Smart Home Security Solutions Company Profile Revenue And Profit Of Security Company Elements PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Revenue And Profit Of Security Company Elements PDF. Use them to share invaluable insights on Revenue And Profit, Million US Dollar, Revenue Increased Profit and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
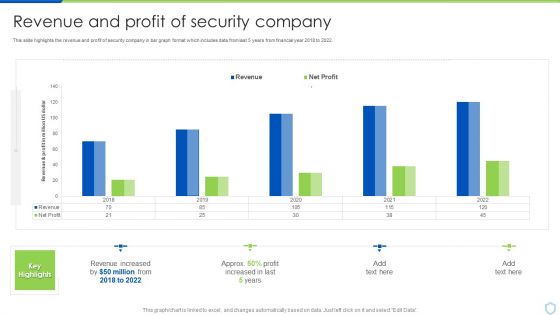
Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF. Use them to share invaluable insights on Revenue Increased, Increased In Last, Key Highlights and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
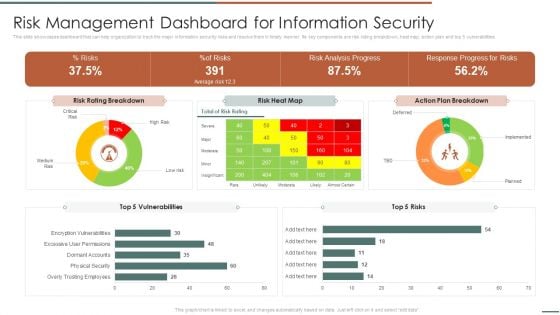
Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF. Use them to share invaluable insights on Rating Breakdown, Vulnerabilities, Response Progress and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF. Use them to share invaluable insights on Manual Testing, Fix Error, 3 Working Days and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizing Security Awareness How To Overcome The Security Awareness Training Brochure PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Organizing Security Awareness How To Overcome The Security Awareness Training Brochure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Organizing Security Awareness Measuring The Impact Of Security Awareness Training Background PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Organizing Security Awareness Measuring The Impact Of Security Awareness Training Background PDF from Slidegeeks and deliver a wonderful presentation.
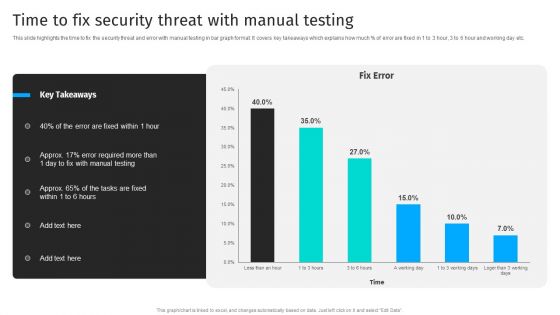
Security Automation To Analyze And Mitigate Cyberthreats Time To Fix Security Threat Ideas PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc.The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Security Automation To Analyze And Mitigate Cyberthreats Time To Fix Security Threat Ideas PDF from Slidegeeks and deliver a wonderful presentation.
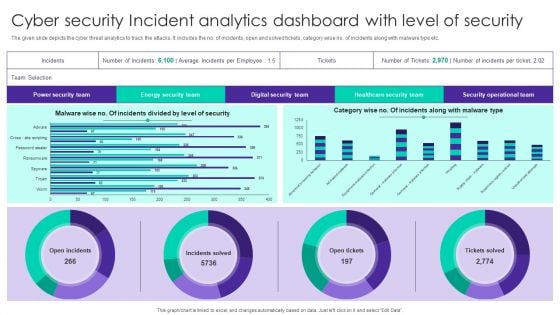
Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF
The given slide depicts the cyber threat analytics to track the attacks. It includes the no. of incidents, open and solved tickets, category wise no. of incidents along with malware type etc. Pitch your topic with ease and precision using this Cyber Security Incident Analytics Dashboard With Level Of Security Ppt Ideas Graphics Tutorials PDF. This layout presents information on Power Security Team, Open Incidents, Incidents Solved, Open Tickets. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Organizational Assets Security Management Strategy Ensuring Effective Intellectual Property Security Structure PDF
This slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Present like a pro with Organizational Assets Security Management Strategy Ensuring Effective Intellectual Property Security Structure PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
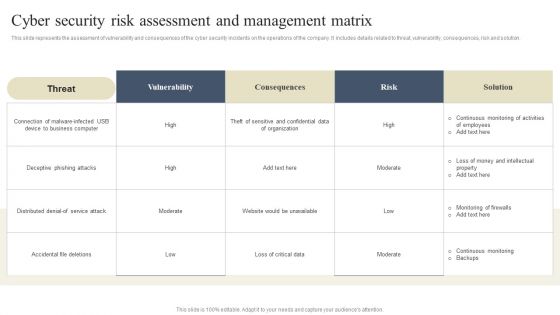
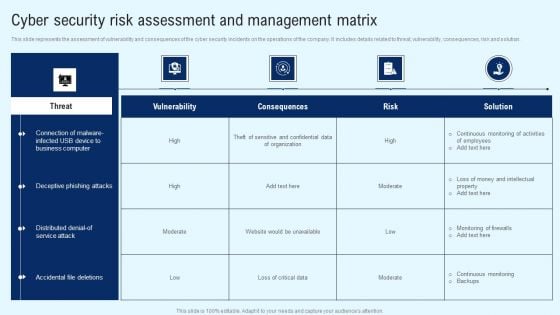
CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
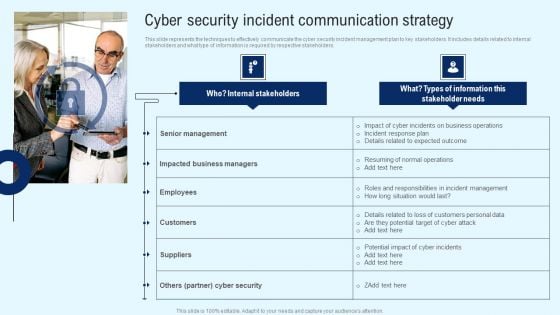
Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Explore a selection of the finest CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
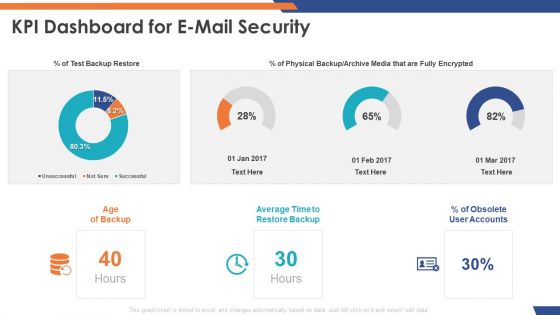
Email Security Market Research Report KPI Dashboard For E Mail Security Graphics PDF
Presenting this set of slides with name email security market research report kpi dashboard for e mail security graphics pdf. The topics discussed in these slides are test backup restore, physical backup or archive media that are fully encrypted, obsolete user accounts, average time to restore backup. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
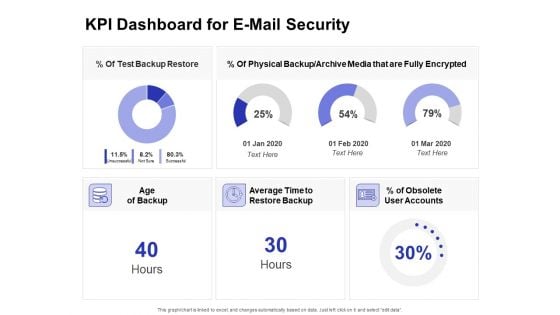
Global Cloud Based Email Security Market KPI Dashboard For E Mail Security Ideas PDF
Presenting this set of slides with name global cloud based email security market kpi dashboard for e mail security ideas pdf. The topics discussed in these slides are test backup restore, physical backup or archive media that are fully encrypted, obsolete user accounts, average time to restore backup. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
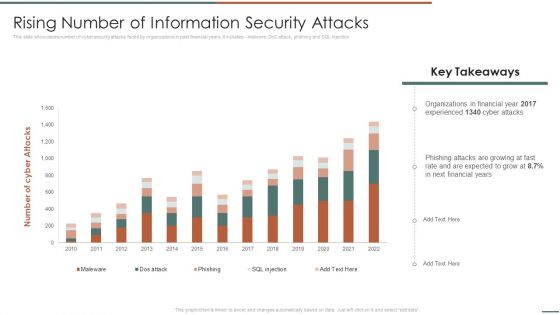
Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF. Use them to share invaluable insights on Organizations In Financial, Experienced, Phishing Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
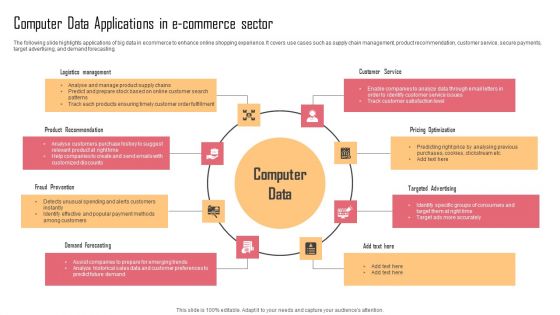
Computer Data Applications In E Commerce Sector Information PDF
The following slide highlights applications of big data in ecommerce to enhance online shopping experience. It covers use cases such as supply chain management, product recommendation, customer service, secure payments, target advertising, and demand forecasting. Presenting Computer Data Applications In E Commerce Sector Information PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Logistics Management, Customer Service, Pricing Optimization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
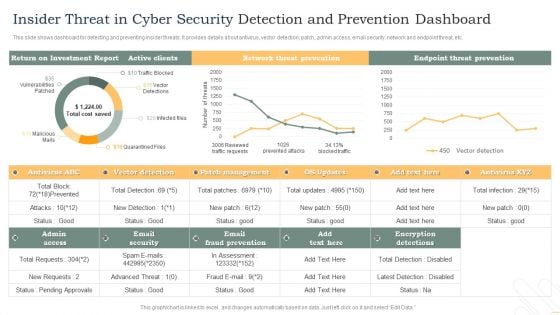
Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF
This slide shows dashboard for detecting and preventing insider threats. It provides details about antivirus, vector detection, patch, admin access, email security, network and endpoint threat, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF. This layout presents information on Active Clients, Network Threat Prevention, Endpoint Threat Prevention. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
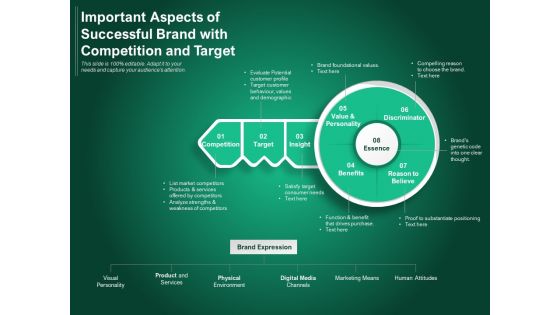
Important Aspects Of Successful Brand With Competition And Target Ppt PowerPoint Presentation Gallery Themes PDF
Presenting this set of slides with name important aspects of successful brand with competition and target ppt powerpoint presentation gallery themes pdf. This is a seven stage process. The stages in this process are visual personality, digital media, marketing means. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
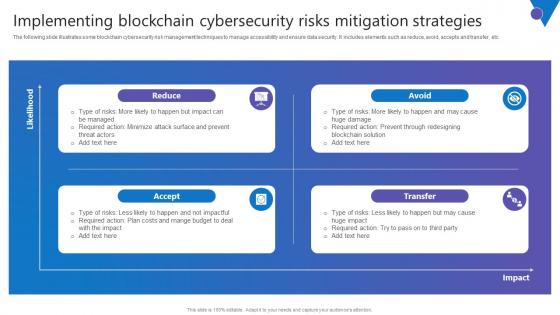
Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Implementing Blockchain Comprehensive Guide To Blockchain Digital Security Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc.

Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This modern and well-arranged Organizing Security Awareness KPI Dashboard To Monitor Cyber Security Performance Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
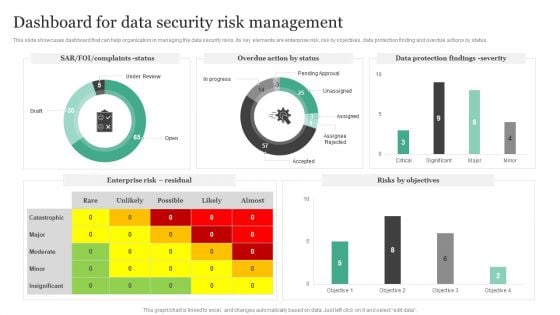
Dashboard For Data Security Risk Management Information Security Risk Administration Formats PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Dashboard For Data Security Risk Management Information Security Risk Administration Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
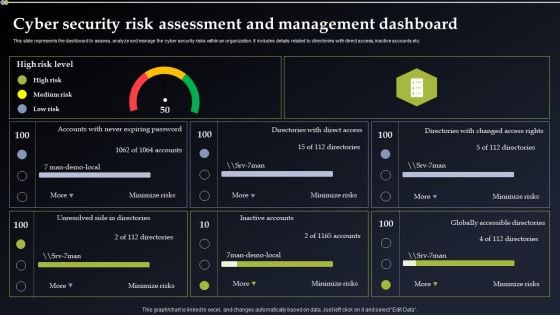
Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

 Home
Home