Lock Icon
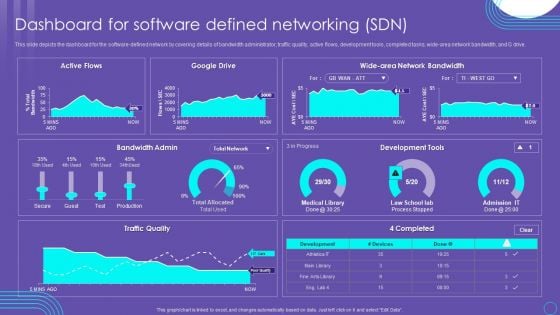
SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF
This slide depicts the dashboard for the software defined network by covering details of bandwidth administrator, traffic quality, active flows, development tools, completed tasks, wide area network bandwidth, and G drive. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
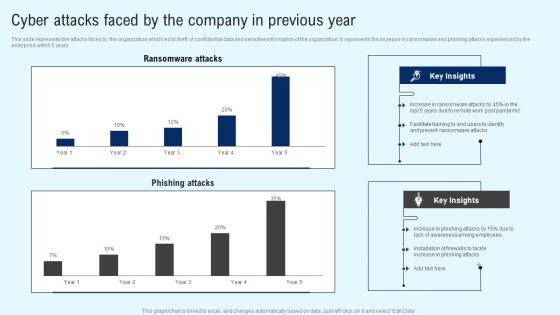
Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

IT Security Risk Management Process For Organization Template PDF
This slide displays flow diagram to illustrate cybersecurity risk management process to ensure continuous monitoring. It includes components such as threats, vulnerabilities, impacts, intelligence, etc. Showcasing this set of slides titled IT Security Risk Management Process For Organization Template PDF. The topics addressed in these templates are Organization, Cyber Intelligence, Continuous Monitoring, Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
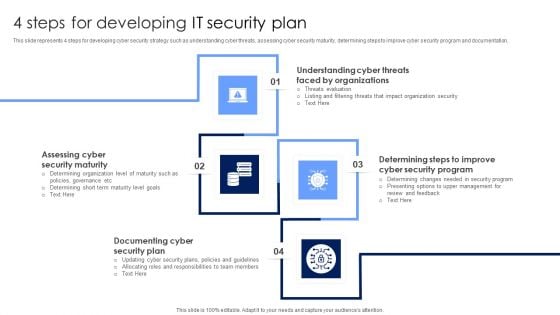
4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
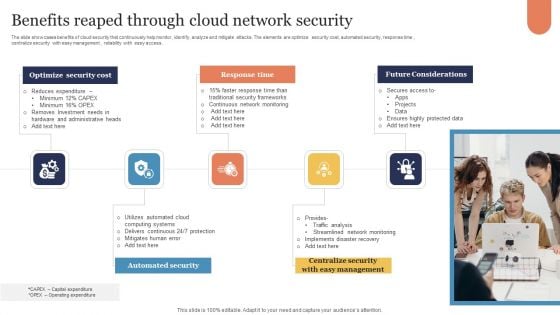
Benefits Reaped Through Cloud Network Security Sample PDF
The slide showcases benefits of cloud security that continuously help monitor, identify, analyze and mitigate attacks. The elements are optimize security cost, automated security, response time , centralize security with easy management , reliability with easy access . Presenting Benefits Reaped Through Cloud Network Security Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Optimize Security Cost, Response Time, Future Considerations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
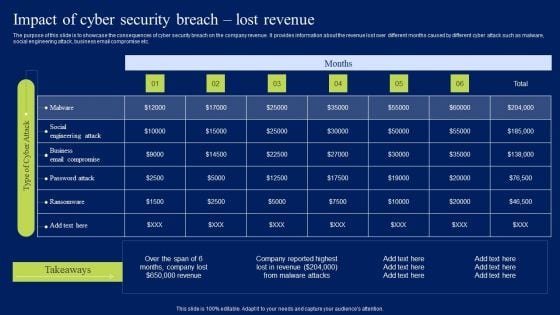
Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. If you are looking for a format to display your unique thoughts, then the professionally designed Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Impact Of Cyber Security Breach Lost Revenue Ppt Templates PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
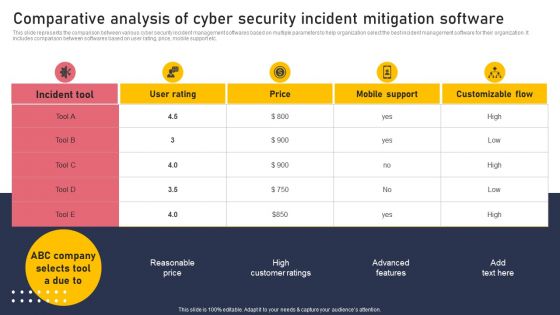
Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

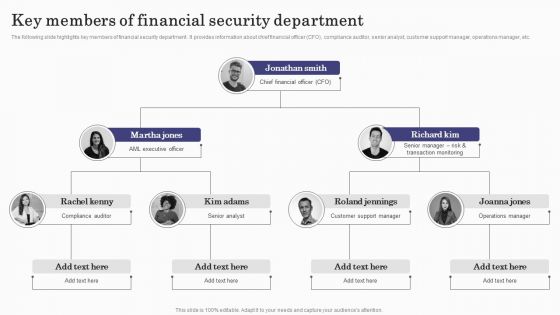
Integrating AML And Transaction Key Members Of Financial Security Department Slides PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This Integrating AML And Transaction Key Members Of Financial Security Department Slides PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. TheIntegrating AML And Transaction Key Members Of Financial Security Department Slides PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
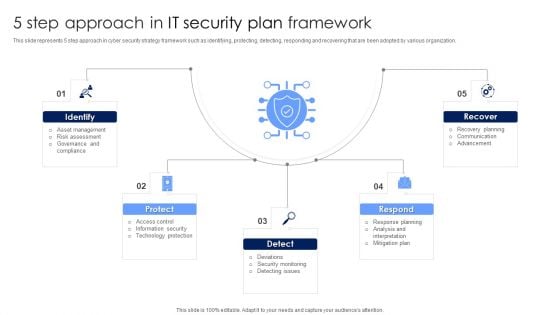
5 Step Approach In IT Security Plan Framework Designs PDF
This slide represents 5 step approach in cyber security strategy framework such as identifying, protecting, detecting, responding and recovering that are been adopted by various organization. Presenting 5 Step Approach In IT Security Plan Framework Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
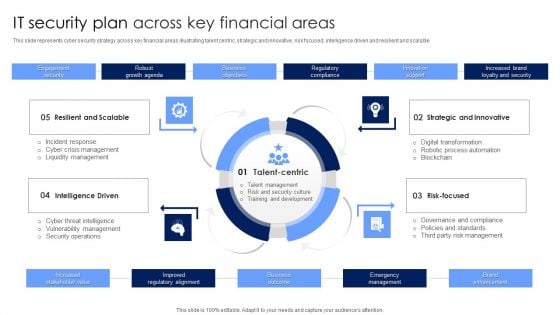
IT Security Plan Across Key Financial Areas Portrait PDF
This slide represents cyber security strategy across key financial areas illustrating talent centric, strategic and innovative, risk focused, intelligence driven and resilient and scalable. Presenting IT Security Plan Across Key Financial Areas Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strategic And Innovative, Risk Focused, Intelligence Driven. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
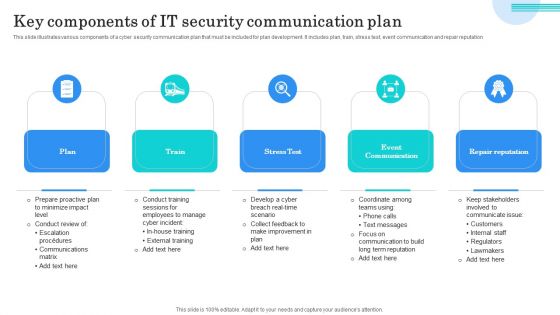
Key Components Of IT Security Communication Plan Mockup PDF
This slide illustrates various components of a cyber security communication plan that must be included for plan development. It includes plan, train, stress test, event communication and repair reputation. Presenting Key Components Of IT Security Communication Plan Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Plan, Train, Stress Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
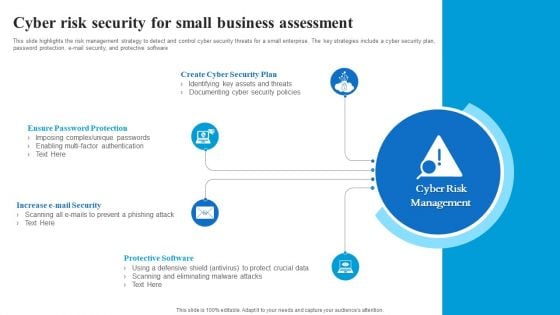
Cyber Risk Security For Small Business Assessment Brochure PDF
This slide highlights the risk management strategy to detect and control cyber security threats for a small enterprise. The key strategies include a cyber security plan, password protection, e-mail security, and protective software. Presenting Cyber Risk Security For Small Business Assessment Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Create Cyber Security Plan, Ensure Password Protection, Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Essential Measures For Business Cyber Security Assessment Plan Rules PDF
This slide demonstrates the safety measures in a business security plan that helps in decreasing the frequency of security threats data hacks, information breaches etc. The measures include handy backups, multi layer security, protective software, and employee training. Presenting Essential Measures For Business Cyber Security Assessment Plan Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
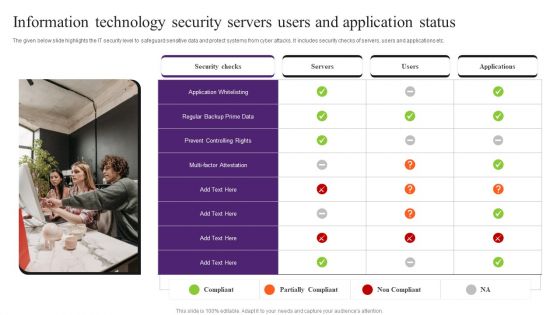
Information Technology Security Servers Users And Application Status Pictures PDF
The given below slide highlights the IT security level to safeguard sensitive data and protect systems from cyber attacks. It includes security checks of servers, users and applications etc. Presenting Information Technology Security Servers Users And Application Status Pictures PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Application Whitelisting, Security Checks, Information Technology Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
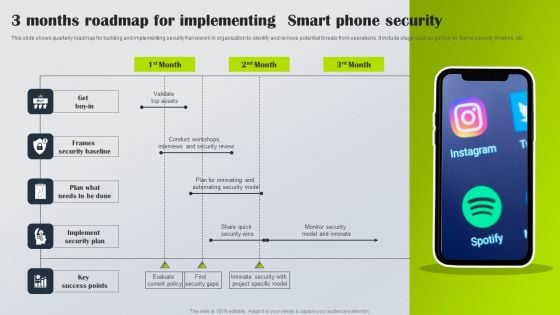
3 Months Roadmap For Implementing Smart Phone Security Information PDF
This slide shows quarterly roadmap for building and implementing security framework in organization to identify and remove potential threats from operations. It include stage such as get buy-in, frame security timeline, etc. Presenting 3 Months Roadmap For Implementing Smart Phone Security Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Get Buy In, Frames Security Baseline, Implement Security Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
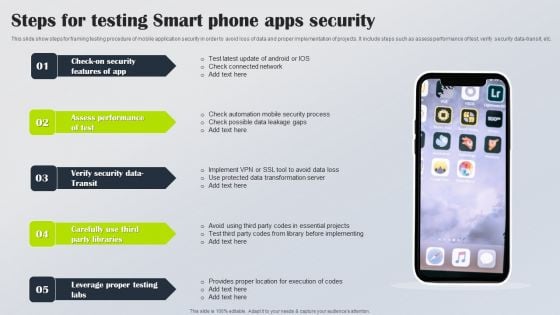
Steps For Testing Smart Phone Apps Security Inspiration PDF
This slide show steps for framing testing procedure of mobile application security in order to avoid loss of data and proper implementation of projects. It include steps such as assess performance of test, verify security data transit, etc. Presenting Steps For Testing Smart Phone Apps Security Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Check Security Features App, Assess Performance Test, Verify Security Data Transit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Based Computing Analysis Strategies For Every Phase Of The Cloud Journey Clipart PDF
This slide covers the strategies to overcome network complexities and increase reliability, enhanced user experience, increasing efficiency and high security. Do you know about Slidesgeeks Cloud Based Computing Analysis Strategies For Every Phase Of The Cloud Journey Clipart PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
Business Intelligence Architecture Diagram And Spoke Strategic Ppt PowerPoint Templates
We present our business intelligence architecture diagram and spoke strategic ppt PowerPoint templates.Use our Circle Charts PowerPoint Templates because It will Give impetus to the hopes of your colleagues. Our PowerPoint Templates and Slides will aid you in winning their trust. Download our Arrows PowerPoint Templates because You can Zap them with our PowerPoint Templates and Slides. See them reel under the impact. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. Download our Flow Charts PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate. Use our Ring Charts PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink.Use these PowerPoint slides for presentations relating to Abstract, access, arrow, background, bright, business, chart, circle, color, concept, connection, corporate, creative, cycle, design, different, graphic, group, illustration, part, piece, process, shape, solution,, strategy, template, text, usable, vector. The prominent colors used in the PowerPoint template are Black, Gray, White. Browse through our collection. Our Business Intelligence Architecture Diagram And Spoke Strategic Ppt PowerPoint Templates offer you the widest possible range of options.
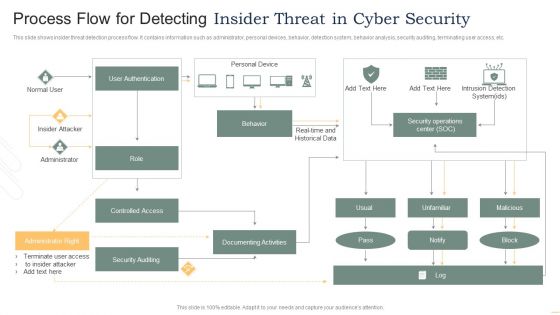
Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Attacks Faced By Organization Mockup PDF
This slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. If you are looking for a format to display your unique thoughts, then the professionally designed Information Security Attacks Faced By Organization Mockup PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Security Attacks Faced By Organization Mockup PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
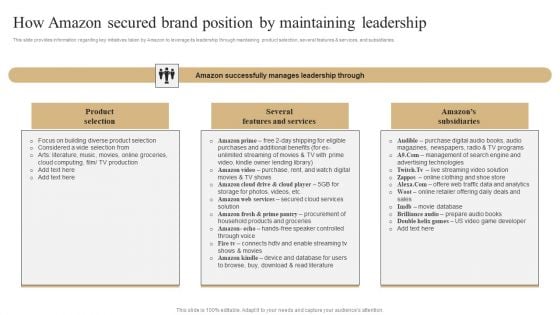
How Amazon Secured Brand Position By Maintaining Leadership Slides PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. If you are looking for a format to display your unique thoughts, then the professionally designed How Amazon Secured Brand Position By Maintaining Leadership Slides PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download How Amazon Secured Brand Position By Maintaining Leadership Slides PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

The Digital Project Managers Deployment Of Cloud Project Management Model
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. If you are looking for a format to display your unique thoughts, then the professionally designed The Digital Project Managers Deployment Of Cloud Project Management Model is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download The Digital Project Managers Deployment Of Cloud Project Management Model and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc.

Security In 5G Technology Architecture 5G Network Structure Pictures PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Retrieve professionally designed Security In 5G Technology Architecture 5G Network Structure Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You Do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
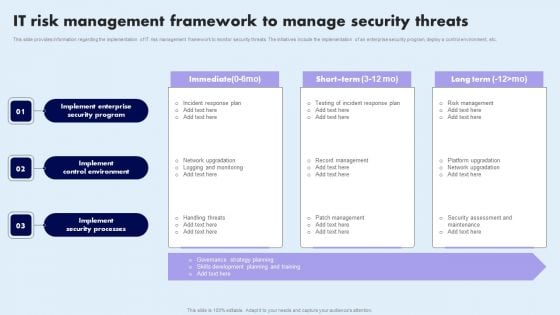
IT Risk Management Framework To Manage Security Threats Summary PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Retrieve professionally designed IT Risk Management Framework To Manage Security Threats Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Project Security Administration IT Determine Project Safety Management Team Structure Sample PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a project security administration it determine project safety management team structure sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like public affair advisor, security manager, legal advisor, medical advisor, crisis management advisor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
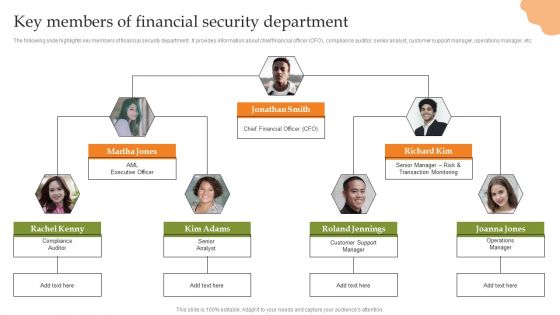
Deploying Banking Transaction Key Members Of Financial Security Department Guidelines PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This modern and well-arranged Deploying Banking Transaction Key Members Of Financial Security Department Guidelines PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Creating Transaction Monitoring Key Members Of Financial Security Department Summary PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This modern and well-arranged Creating Transaction Monitoring Key Members Of Financial Security Department Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
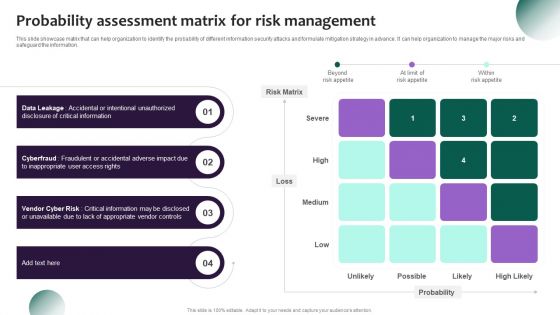
Information Systems Security And Risk Management Plan Probability Assessment Matrix For Risk Management Portrait PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Information Systems Security And Risk Management Plan Probability Assessment Matrix For Risk Management Portrait PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Welcome to our selection of the Deploying AML Transaction Monitoring Key Members Of Financial Security Department Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
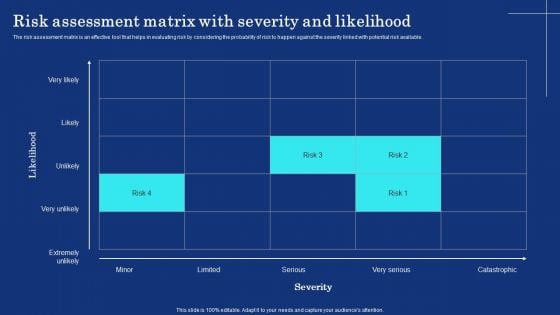
Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Organizational Assets Security Management Strategy Risk Assessment Matrix With Severity And Likelihood Brochure PDF.
3d Complicating Arrows Stages Description Pro Forma Business Plan PowerPoint Slides
We present our 3d complicating arrows stages description pro forma business plan PowerPoint Slides.Use our Symbol PowerPoint Templates because this an appropriate template to get your ideas across to your target audience. Use our Flow charts PowerPoint Templates because chain reactions are the element of teamwork which add value to your efforts. Present our Arrows PowerPoint Templates because different personalities, different abilities but formidable together. Use our Puzzles or Jigsaws PowerPoint Templates because with the help of our Slides you can Illustrate your plans on using the many social media modes available to inform soceity at large of the benefits of your product. Download and present our Business PowerPoint Templates because the fruits of your labour are beginning to show.Enlighten them on the great plans you have for their enjoyment.Use these PowerPoint slides for presentations relating to 3d, Puzzle, Process, Arrow, Arrows, Block, Business, Chart, Design, Development, Diagram, Direction, Element, Flow, Flowchart, Graph, Linear, Management, Organization, Process, Program, Section, Sign, Solution, Symbol. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Professionals tell us our 3d complicating arrows stages description pro forma business plan PowerPoint Slides are Magnificent. We assure you our Arrow PowerPoint templates and PPT Slides are second to none. People tell us our 3d complicating arrows stages description pro forma business plan PowerPoint Slides are readymade to fit into any presentation structure. Customers tell us our Process PowerPoint templates and PPT Slides are Upbeat. Use our 3d complicating arrows stages description pro forma business plan PowerPoint Slides are second to none. We assure you our Chart PowerPoint templates and PPT Slides are Colorful. Feed in some energy with our 3d Complicating Arrows Stages Description Pro Forma Business Plan PowerPoint Slides. Your thoughts will drum up a catchy beat.
Series Of Illustration Displayed In Sequence Online Business Plans PowerPoint Slides
We present our series of illustration displayed in sequence online business plans PowerPoint Slides.Download and present our Flow charts PowerPoint Templates because you can Show them the way, be Captain of the ship and lead them to new shores. Present our Arrows PowerPoint Templates because this slide imprint them on the minds of your audience via our slides. Download and present our Process and flows PowerPoint Templates because this will helps you to explore the minutest detail of each concept and follow the trail to its conclusion. Download and present our Shapes PowerPoint Templates because this business powerpoint template helps expound on the logic of your detailed thought process to take your company forward. Present our Business PowerPoint Templates because like the famed William Tell, they put aside all emotions and concentrate on the target.Use these PowerPoint slides for presentations relating to action, attach, box, business, center, chain, chart, color, communication concept, connection, cube, cycle, data, diagram, flow, globe, horizontal, idea illustration, information, interaction, jigsaw, join, link, pieces, process, puzzle, relation relationship, shape, success. The prominent colors used in the PowerPoint template are Blue, Gray, White. People tell us our series of illustration displayed in sequence online business plans PowerPoint Slides are Nice. People tell us our chart PowerPoint templates and PPT Slides are Chic. Presenters tell us our series of illustration displayed in sequence online business plans PowerPoint Slides are Precious. Customers tell us our center PowerPoint templates and PPT Slides are Bold. Customers tell us our series of illustration displayed in sequence online business plans PowerPoint Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. The feedback we get is that our communication PowerPoint templates and PPT Slides will help you be quick off the draw. Just enter your specific text and see your points hit home.
Series Of Illustration Displayed In Sequence Sample Business Plan Outline PowerPoint Slides
We present our series of illustration displayed in sequence sample business plan outline PowerPoint Slides.Present our Flow charts PowerPoint Templates because strengthen your relationship with your present customers and likely future ones as the occasion has an intrinsic business potential. Present our Arrows PowerPoint Templates because clarity of thought has been the key to your growth. Download our Process and flows PowerPoint Templates because getting it done may not be enough. Download and present our Shapes PowerPoint Templates because this shows ideas to get the different elements of your Business to mesh and coalesce into a focused team driven by a common goal to achieve the common aim with Excellence. Present our Business PowerPoint Templates because this layout helps you to bring some important aspects of your business process to the notice of all concerned. Streamline the flow of information across the board.Use these PowerPoint slides for presentations relating to action, attach, box, business, center, chain, chart, color, communication concept, connection, cube, cycle, data, diagram, flow, globe, horizontal, idea illustration, information, interaction, jigsaw, join, link, pieces, process, puzzle, relation relationship, shape, success. The prominent colors used in the PowerPoint template are Green, Gray, White. People tell us our series of illustration displayed in sequence sample business plan outline PowerPoint Slides are Ritzy. People tell us our color PowerPoint templates and PPT Slides will save the presenter time. Presenters tell us our series of illustration displayed in sequence sample business plan outline PowerPoint Slides are Romantic. Customers tell us our chart PowerPoint templates and PPT Slides are Nifty. Customers tell us our series of illustration displayed in sequence sample business plan outline PowerPoint Slides are Wonderful. The feedback we get is that our business PowerPoint templates and PPT Slides are Beautiful. Fly in the face of conservative approaches. Our Series Of Illustration Displayed In Sequence Sample Business Plan Outline PowerPoint Slides encourage bold actions.
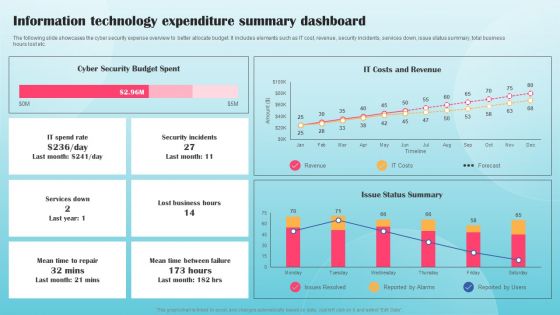
Information Technology Expenditure Summary Dashboard Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. This Information Technology Expenditure Summary Dashboard Ppt PowerPoint Presentation Diagram Graph Charts PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
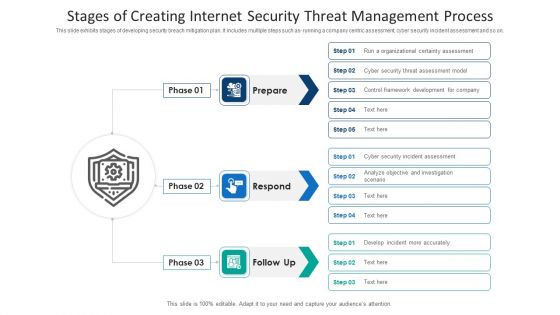
Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
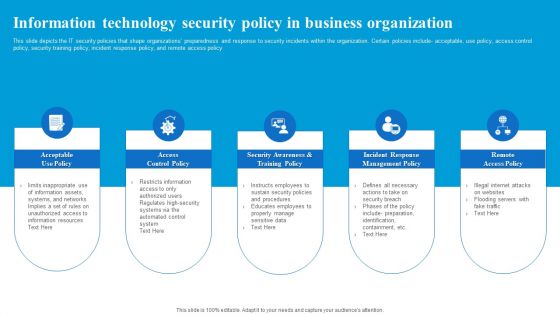
Information Technology Security Policy In Business Organization Download PDF
This slide depicts the IT security policies that shape organizations preparedness and response to security incidents within the organization. Certain policies include acceptable, use policy, access control policy, security training policy, incident response policy, and remote access policy. Presenting Information Technology Security Policy In Business Organization Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Access Control Policy, Acceptable Use Policy, Remote Access Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
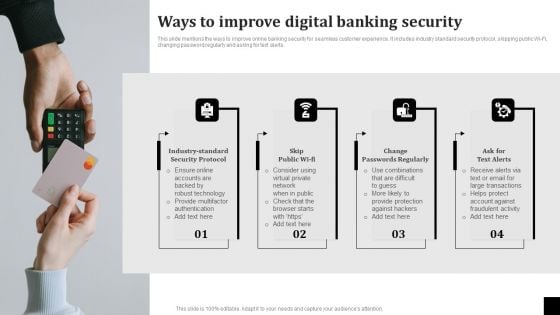
Ways To Improve Digital Banking Security Elements PDF
This slide mentions the ways to improve online banking security for seamless customer experience. It includes industry standard security protocol, skipping public Wi-Fi, changing password regularly and asking for text alerts. Presenting Ways To Improve Digital Banking Security Elements PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Industry Standard Security Protocol, Skip Public Wifi, Change Passwords Regularly. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
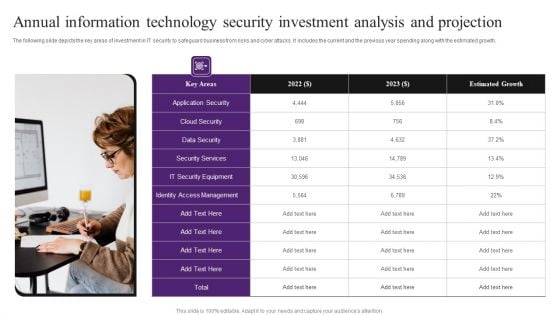
Annual Information Technology Security Investment Analysis And Projection Portrait PDF
The following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Presenting Annual Information Technology Security Investment Analysis And Projection Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cloud Security, Security Services, Identity Access Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Operations Team Roles And Responsibilities Infographics PDF
This slide exhibits key roles on the SecOps team with their roles and responsibilities that manage cybersecurity threats and attacks. It includes a security investigator, advanced security analyst, SOC manager, and security manager. Presenting Security Operations Team Roles And Responsibilities Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Skills Required, Determine, Develop Mitigation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone Security Tools For Preventing Threats Topics PDF
This slide shows latest security tools for managing phone security model. The purpose of this slide is to highlight various tools names with description for selecting most suitable tool. It include tools such as data loss prevention, identify and access management, etc. Presenting Smart Phone Security Tools For Preventing Threats Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Loss Prevention, Identity Access Management, Security Event Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Software Testing Methodologies To Improve Data Security Graphics PDF
This slides signifies the application testing practises to increase data security. It covers information about steps like build secure environment, create team, simulate end user, adopt shifting left testing methodology and focus on regression testing. Presenting Software Testing Methodologies To Improve Data Security Graphics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Build Secure Testing Environment, Simulate End User Environment, Focus Regression Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
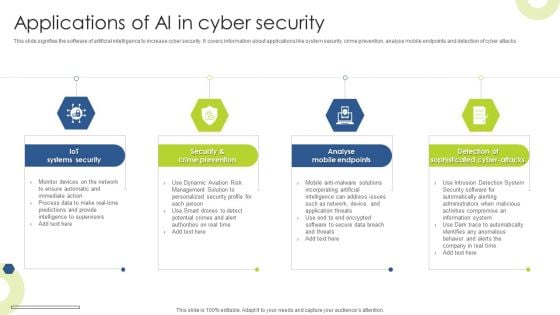
Applications Of AI In Cyber Security Infographics PDF
This slide signifies the software of artificial intelligence to increase cyber security. It covers information about applications like system security, crime prevention, analyse mobile endpoints and detection of cyber attacks Presenting Applications Of AI In Cyber Security Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Iot Systems Security, Crime Prevention, Analyse Mobile Endpoints. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
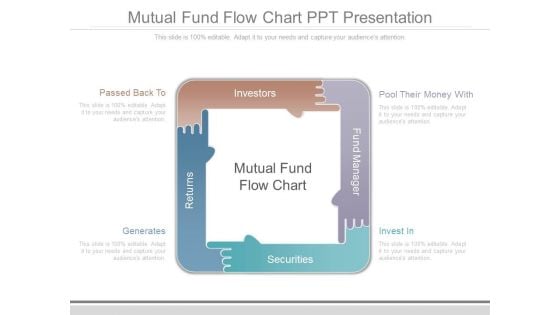
Mutual Fund Flow Chart Ppt Presentation
This is a mutual fund flow chart ppt presentation. This is a four stage process. The stages in this process are passed back to, generates, pool their money with, invest in, returns, securities, fund manager, investors.

Deployment Of Cloud Project Management Model Integrating Cloud Computing To Enhance Projects Effectiveness Themes PDF
This slide showcases deployment of cloud project management model. It provides information about public, private, hybrid, setup, data security, data control, privacy, scalability, integration, etc. Slidegeeks is here to make your presentations a breeze with Deployment Of Cloud Project Management Model Integrating Cloud Computing To Enhance Projects Effectiveness Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Financing Catalogue For Security Underwriting Agreement Key Competitors Of The Company Slides PDF
The slide provides the key players in the industry by companys size Top or Large companies, mid market companies, small or boutique companies etc. It has also mentioned the companys major competitors, This is a financing catalogue for security underwriting agreement key competitors of the company slides pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like top or large investment banks, mid market investment banks, boutique investment banks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Determine Threat Management Team Structure Topics PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a corporate security and risk management determine threat management team structure topics pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Formulating Money Laundering Key Members Of Financial Security Department Structure PDF
This Formulating Money Laundering Key Members Of Financial Security Department Structure PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
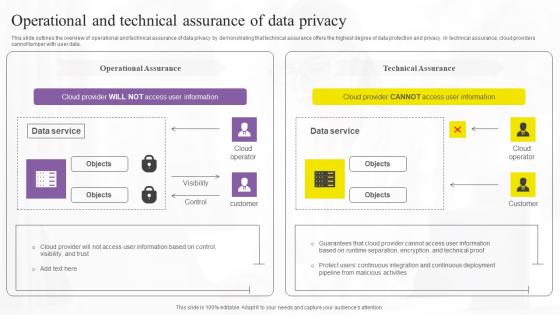
Operational And Technical Assurance Confidential Computing Technologies Inspiration Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Do you know about Slidesgeeks Operational And Technical Assurance Confidential Computing Technologies Inspiration Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data.
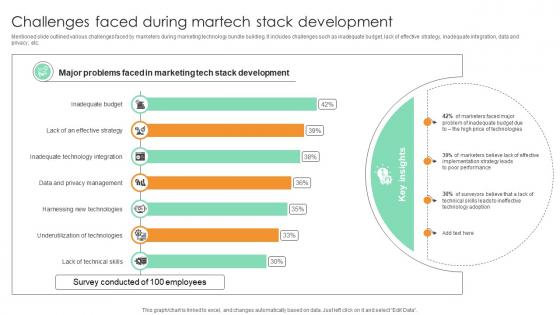
Challenges Faced During Martech Stack Development Comprehensive Guide For Marketing Technology
Mentioned slide outlined various challenges faced by marketers during marketing technology bundle building. It includes challenges such as inadequate budget, lack of effective strategy, inadequate integration, data and privacy, etc.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Challenges Faced During Martech Stack Development Comprehensive Guide For Marketing Technology. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Challenges Faced During Martech Stack Development Comprehensive Guide For Marketing Technology today and make your presentation stand out from the rest Mentioned slide outlined various challenges faced by marketers during marketing technology bundle building. It includes challenges such as inadequate budget, lack of effective strategy, inadequate integration, data and privacy, etc.
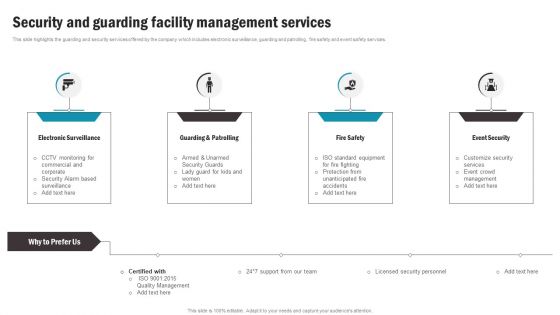
Security And Guarding Facility Management Services Information PDF
This slide highlights the guarding and security services offered by the company which includes electronic surveillance, guarding and patrolling, fire safety and event safety services. Retrieve professionally designed Security And Guarding Facility Management Services Information PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Managing Cyber Security In Manufacturing 60 Days Plan Information PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Retrieve professionally designed Managing Cyber Security In Manufacturing 60 Days Plan Information PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Logical World Business PowerPoint Templates Steps Plan Pdf
We present our logical world business powerpoint templates steps plan pdf.Present our Communication PowerPoint Templates because you are going along well but your foresight shows that it may need a slight change in plans or direction. Use our Boxes PowerPoint Templates because the Venn graphic comprising interlinking circles geometrically demonstate how various functions operating independantly, to a large extent, are essentially interdependant. Present our Business PowerPoint Templates because it helps you to project your enthusiasm and single mindedness to your colleagues. Present our Flow charts PowerPoint Templates because you can Inform your team of the various means they have to achieve them. Download and present our Arrows PowerPoint Templates because you can blaze a brilliant trail from point to point.Use these PowerPoint slides for presentations relating to Abstract, Action, Attach, Box, Business, Center, Chain, Chart, Color, Communication, Concept, Connection, Cube, Cycle, Data, Diagram, Flow, Globe, Horizontal, Idea, Illustration, Information, Interaction, Jigsaw, Join, Link, Pieces, Process, Puzzle, Relation, Relationship, Shape, Success. The prominent colors used in the PowerPoint template are Green, Gray, Black. Presenters tell us our logical world business powerpoint templates steps plan pdf are Dazzling. Use our Color PowerPoint templates and PPT Slides are Lush. You can be sure our logical world business powerpoint templates steps plan pdf are the best it can get when it comes to presenting. Professionals tell us our Box PowerPoint templates and PPT Slides are Wonderful. Presenters tell us our logical world business powerpoint templates steps plan pdf are Nifty. PowerPoint presentation experts tell us our Box PowerPoint templates and PPT Slides are Endearing. Conquer fatigue with our Logical World Business PowerPoint Templates Steps Plan Pdf. They are like a deep breath.
Series Of Illustration Displayed In Sequence Model Business Plan PowerPoint Templates
We present our series of illustration displayed in sequence model business plan PowerPoint templates.Use our Flow charts PowerPoint Templates because it helps you to inform your team of your innovative ideas. Download our Arrows PowerPoint Templates because you can blaze a brilliant trail from point to point. Download our Process and flows PowerPoint Templates because in this Slide Various threads are joining up and being stitched together providing necessary strength Now you have to take the last leap. Download and present our Shapes PowerPoint Templates because there is a very good saying that prevention is better than cure, either way you have a store of knowledge for sure. Download and present our Business PowerPoint Templates because you are ready to flap your wings and launch off. All poised are you to touch the sky with glory.Use these PowerPoint slides for presentations relating to action, attach, box, business, center, chain, chart, color, communication concept, connection, cube, cycle, data, diagram, flow, globe, horizontal, idea illustration, information, interaction, jigsaw, join, link, pieces, process, puzzle, relation relationship, shape, success. The prominent colors used in the PowerPoint template are Orange, Yellow, Gray. People tell us our series of illustration displayed in sequence model business plan PowerPoint templates are topically designed to provide an attractive backdrop to any subject. People tell us our color PowerPoint templates and PPT Slides are Graceful. Presenters tell us our series of illustration displayed in sequence model business plan PowerPoint templates are Majestic. Customers tell us our center PowerPoint templates and PPT Slides are Upbeat. Customers tell us our series of illustration displayed in sequence model business plan PowerPoint templates are Majestic. The feedback we get is that our box PowerPoint templates and PPT Slides are Radiant. Advocate your case with our Series Of Illustration Displayed In Sequence Model Business Plan PowerPoint Templates. They will deliver a strong defense.
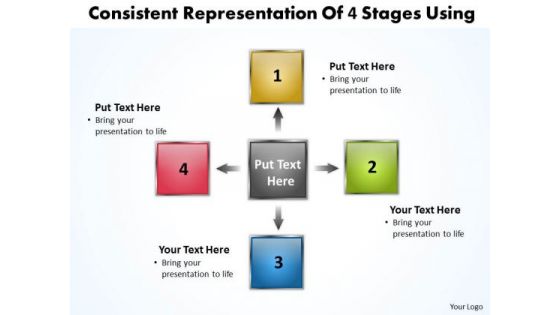
Consistent Representation Of 4 Stages Using Circular Flow Process PowerPoint Slides
We present our consistent representation of 4 stages using Circular Flow Process PowerPoint Slides.Present our Boxes PowerPoint Templates because activities which in themselves have many inherent business oppurtunities. Present our Business PowerPoint Templates because you are ready to flap your wings and launch off. All poised are you to touch the sky with glory. Present our Arrows PowerPoint Templates because you can Employ the right colours for your brilliant ideas. Use our Shapes PowerPoint Templates because the basic stages are in place, you need to build upon them with our PowerPoint templates. Use our Flow Charts PowerPoint Templates because it shows how one can contribute to the overall feeling of well-being.Use these PowerPoint slides for presentations relating to 3d, abstract, algorithm, arrow, background, blank, block, box, business, chain, chart, circle, colorful, concept, connect, connection, corporate, design, diagram, empty, flow, flowchart, graph, graphic, hierarchy, illustration, information, isolated, management, network, organisation, organization, organize, plan, procedure, process, program, scalable, shape, sign, solution, structure, symbol, teamwork, technology,. The prominent colors used in the PowerPoint template are Green, Blue, Red. Presenters tell us our consistent representation of 4 stages using Circular Flow Process PowerPoint Slides are Luxuriant. You can be sure our arrow PowerPoint templates and PPT Slides are Appealing. Professionals tell us our consistent representation of 4 stages using Circular Flow Process PowerPoint Slides are Multicolored. People tell us our background PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. People tell us our consistent representation of 4 stages using Circular Flow Process PowerPoint Slides are Elegant. Professionals tell us our blank PowerPoint templates and PPT Slides are Bright. Brace yourself with our Consistent Representation Of 4 Stages Using Circular Flow Process PowerPoint Slides. Cater for any adversity that can emerge.
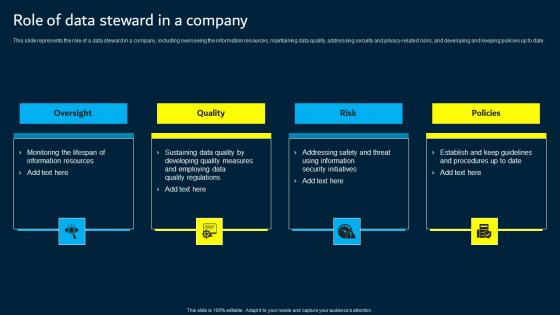
Role Of Data Steward In A Company Data Custodianship Brochure Pdf
This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date. Retrieve professionally designed Role Of Data Steward In A Company Data Custodianship Brochure Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the role of a data steward in a company, including overseeing the information resources, maintaining data quality, addressing security and privacy related risks, and developing and keeping policies up to date.
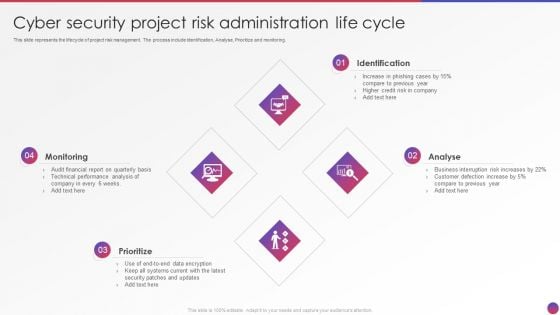
Cyber Security Project Risk Administration Life Cycle Summary PDF
This slide represents the lifecycle of project risk management. The process include Identification, Analyse, Prioritize and monitoring. Presenting Cyber Security Project Risk Administration Life Cycle Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Monitoring, Identification, Analyse, Prioritize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Risk Assessment Framework Demonstration PDF
The following slide highlights the structure to identify best practices to fix risk tolerances. It constitutes of activities such as identify, protect, detect, respond and recover. Presenting Information Technology Security Risk Assessment Framework Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
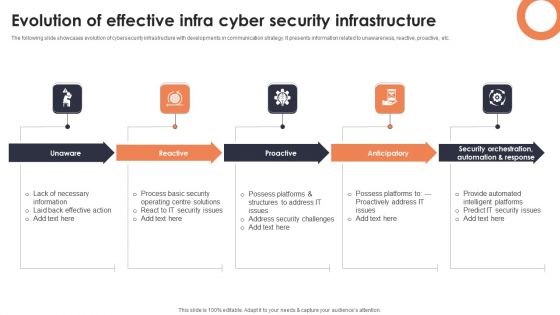
Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF
The following slide showcases evolution of cybersecurity infrastructure with developments in communication strategy. It presents information related to unawareness, reactive, proactive, etc. Presenting Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Unaware, Reactive, Proactive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
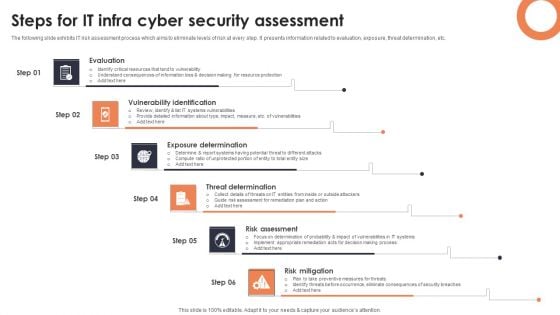
Steps For IT Infra Cyber Security Assessment Background PDF
The following slide exhibits IT risk assessment process which aims to eliminate levels of risk at every step. It presents information related to evaluation, exposure, threat determination, etc. Presenting Steps For IT Infra Cyber Security Assessment Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Evaluation, Vulnerability Identification, Exposure Determination. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
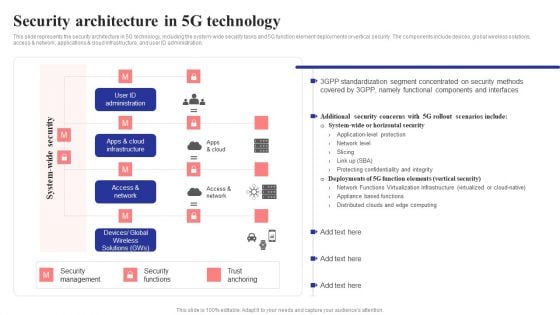
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
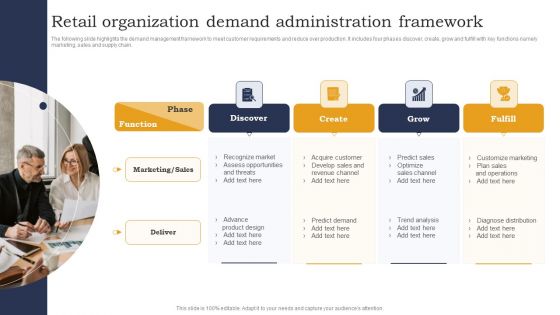
Retail Organization Demand Administration Framework Download PDF
The following slide highlights the demand management framework to meet customer requirements and reduce over production. It includes four phases discover, create, grow and fulfill with key functions namely marketing, sales and supply chain. Showcasing this set of slides titled Retail Organization Demand Administration Framework Download PDF. The topics addressed in these templates are Recognize Market, Assess Opportunities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
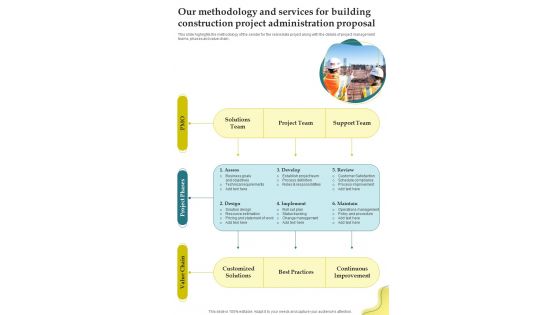
Our Methodology And Services For Building Construction Project Administration Proposal One Pager Sample Example Document
This slide highlights the methodology of the sender for the real estate project along with the details of project management teams, phases and value chain. Presenting you an exemplary Our Methodology And Services For Building Construction Project Administration Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Methodology And Services For Building Construction Project Administration Proposal One Pager Sample Example Document brilliant piece now.

Our Methodology And Services For Project Development Planning Template One Pager Sample Example Document
This slide highlights the methodology of the sender for the real estate project along with the details of project management teams, phases and value chain . Presenting you an exemplary Our Methodology And Services For Project Development Planning Template One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Methodology And Services For Project Development Planning Template One Pager Sample Example Document brilliant piece now.

Our Methodology Services Strategic Project Plan Administration Proposal One Pager Sample Example Document
This slide highlights the methodology of the sender for the real estate project along with the details of project management teams, phases and value chain. Presenting you an exemplary Our Methodology Services Strategic Project Plan Administration Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Methodology Services Strategic Project Plan Administration Proposal One Pager Sample Example Document brilliant piece now.

DAD Framework Disciplined Agile Delivery Phases And Goals Ppt Model Professional PDF
This slide covers delivery phases like Inception, Construction, Transition and ongoing. Each of these phases are described by specific goals. Some goals, such as Grow Team Members and Address Risk, are applicable throughout the entire lifecycle. Deliver and pitch your topic in the best possible manner with this DAD framework disciplined agile delivery phases and goals ppt model professional pdf. Use them to share invaluable insights on develop test strategy, grow team members, produce a potentially consumable solution, secure funding, goals and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
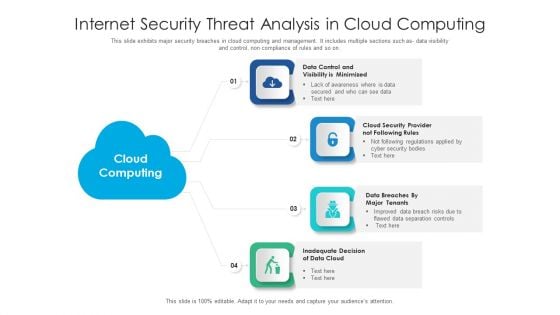
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
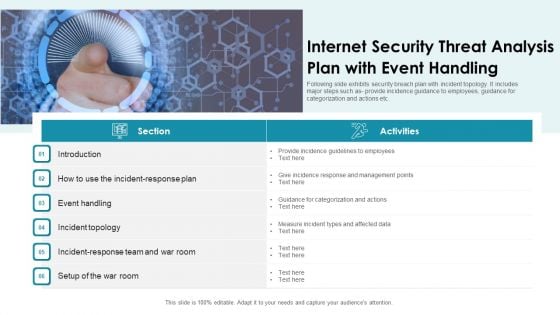
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
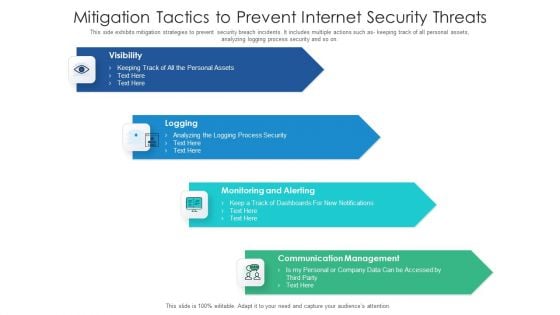
Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
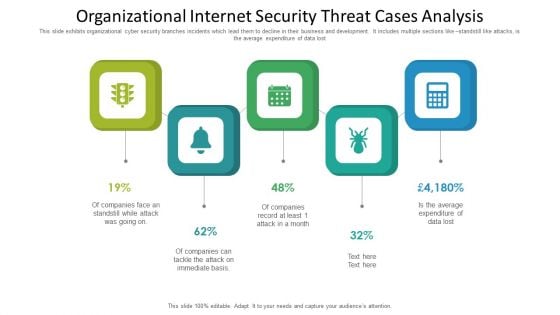
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
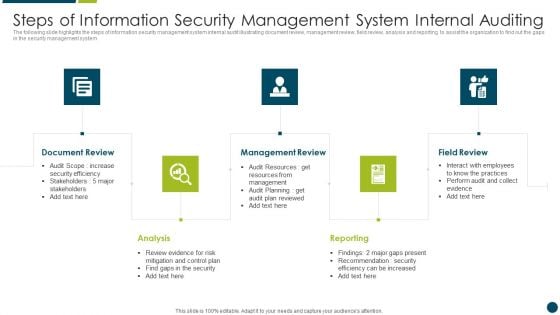
Steps Of Information Security Management System Internal Auditing Structure PDF
The following slide highlights the steps of information security management system internal audit illustrating document review, management review, field review, analysis and reporting to assist the organization to find out the gaps in the security management system Presenting Steps Of Information Security Management System Internal Auditing Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Management Review, Reporting, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully

Five Key Consideration For Hotel Protection And Security Infographics PDF
This slide highlights five strategies to ensure safety and security in hotels. It involves strategies such as installation of proper lighting, CCTV security cameras, fire alarms, emergency power and manual.Presenting Five Key Consideration For Hotel Protection And Security Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Emergency Power, Emergency Manual, Proper Lighting This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Six Practices For IT Security Management Program Microsoft PDF
This slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency.Presenting Six Practices For IT Security Management Program Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Analysis Prioritization, Consolidation Procedure, Strategic Initiatives This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
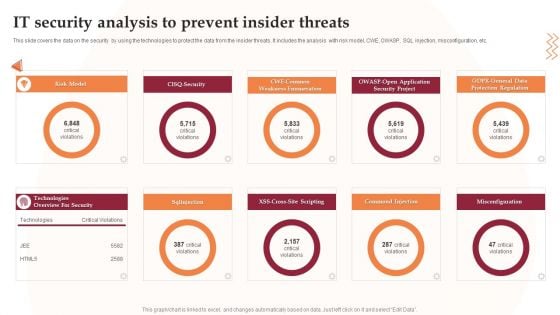
IT Security Analysis To Prevent Insider Threats Infographics PDF
This slide covers the data on the security by using the technologies to protect the data from the insider threats. It includes the analysis with risk model, CWE, OWASP, SQL injection, misconfiguration, etc. Presenting IT Security Analysis To Prevent Insider Threats Infographics PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Project, Application, Risk Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
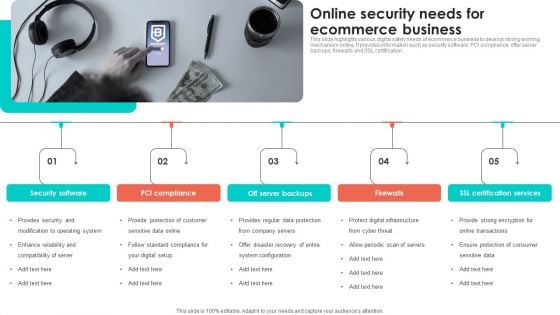
Online Security Needs For Ecommerce Business Professional PDF
This slide highlights various digital safety needs of ecommerce business to develop strong working mechanism online. It provides information such as security software, PCI compliance, offer server backups, firewalls and SSL certification. Presenting Online Security Needs For Ecommerce Business Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including PCI Compliance, Off Server Backups, Security Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
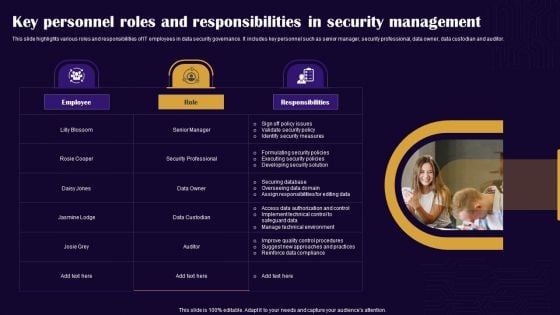
Key Personnel Roles And Responsibilities In Security Management Slides PDF
This slide highlights various roles and responsibilities of IT employees in data security governance. It includes key personnel such as senior manager, security professional, data owner, data custodian and auditor. Presenting Key Personnel Roles And Responsibilities In Security Management Slides PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Employee, Role, Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
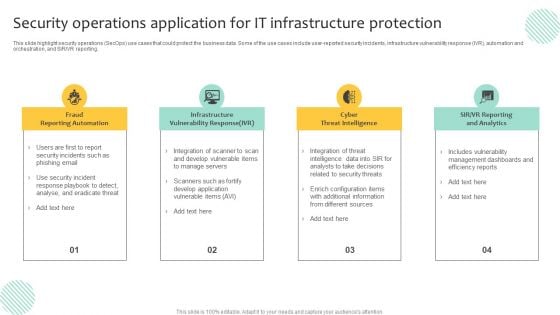
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
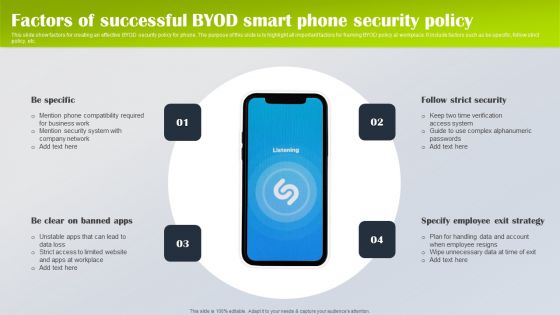
Factors Of Successful Byod Smart Phone Security Policy Designs PDF
This slide show factors for creating an effective BYOD security policy for phone. The purpose of this slide is to highlight all important factors for framing BYOD policy at workplace. It include factors such as be specific, follow strict policy, etc. Presenting Factors Of Successful Byod Smart Phone Security Policy Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Be Specific, Specify Employee Exit Strategy, Follow Strict Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
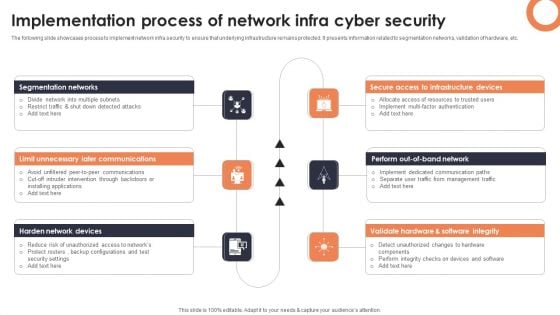
Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
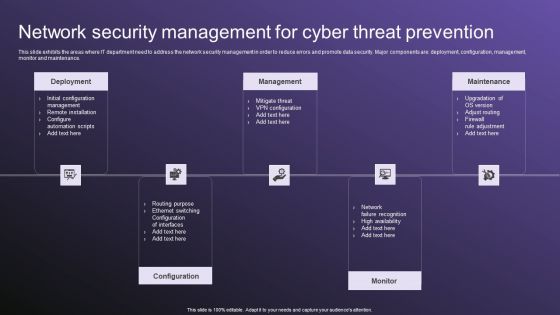
Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
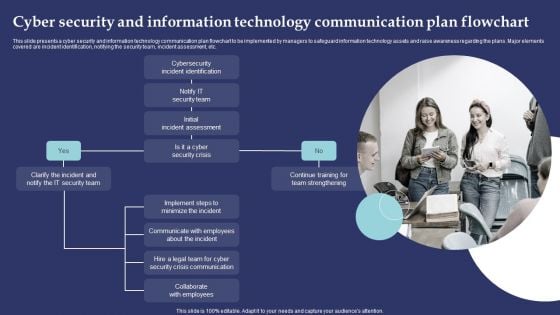
Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF
This slide presents a cyber security and information technology communication plan flowchart to be implemented by managers to safeguard information technology assets and raise awareness regarding the plans. Major elements covered are incident identification, notifying the security team, incident assessment, etc. Presenting Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cybersecurity Incident Identification, Initial Incident Assessment, Continue Training Team Strengthening. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
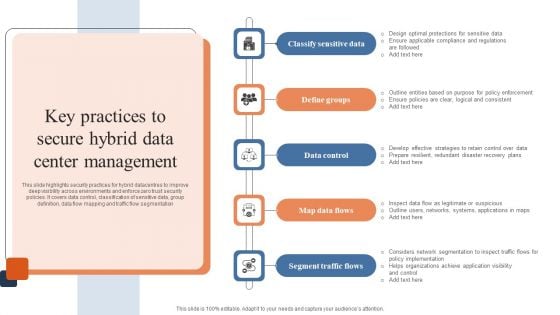
Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
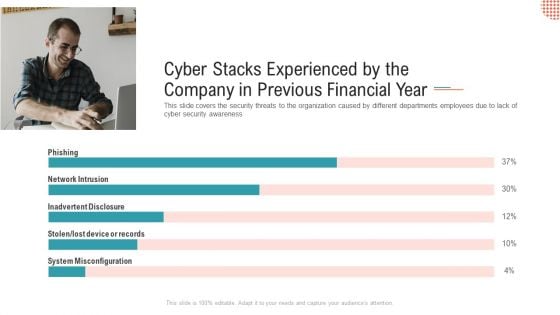
Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Show Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver and pitch your topic in the best possible manner with this cyber stacks experienced by the company in previous financial year ppt show themes pdf. Use them to share invaluable insights on network intrusion, inadvertent disclosure, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
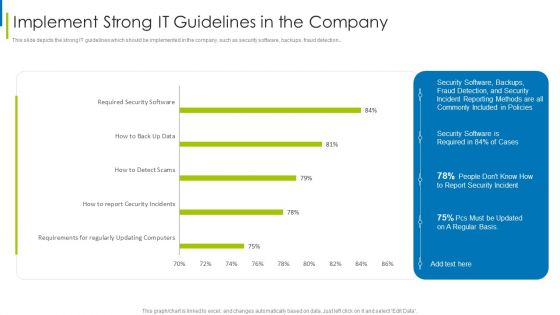
Cyber Terrorism Assault Implement Strong IT Guidelines In The Company Themes PDF
This slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault implement strong it guidelines in the company themes pdf Use them to share invaluable insights on requirements regularly, updating computers, required security software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Bar Graph To Secure Data PowerPoint Templates Ppt Backgrounds For Slides 0713
Get the doers into action. Activate them with our Bar Graph To Secure Data PowerPoint Templates PPT Backgrounds For Slides. Put your money on our Pie Charts PowerPoint Templates. Your ideas will rake in the dollars. Put in a dollop of our Arrows PowerPoint Templates. Give your thoughts a distinctive flavour. Our Bar Graph To Secure Data PowerPoint Templates Ppt Backgrounds For Slides 0713 assist execution. They channel the action in the desired direction.
Sequential Description Using Circular Arrows Workflow Management PowerPoint Slides
We present our sequential description using circular arrows workflow management PowerPoint Slides.Use our Arrows PowerPoint Templates because,You can Start with the fundamental basic activities and slowly but surely hone them down to the top of the pyramid, the ultimate goal. Use our Circle Charts PowerPoint Templates because,Our cleverly selected background hues are guaranteed to achieve this aim. Use our Shapes PowerPoint Templates because,This diagram depicts the essence of this chain reaction like sequence of events. Use our Design PowerPoint Templates because,watching them will strengthen your companys sinews. Use our Process and Flows PowerPoint Templates because,our creative template will lay down your views.Use these PowerPoint slides for presentations relating to 3d, Abstract, Around, Arrows, Blue, Border, Business, Center, Circle, Circular, Concept, Connections, Copy, Curve, Cycle, Directions, Distribution, Illustration, Management, Middle, Objects, Pieces, Plan, Pointing, Process, Recycle, Rounded, Shadows, Space, System. The prominent colors used in the PowerPoint template are Blue, Gray, Black. People tell us our sequential description using circular arrows workflow management PowerPoint Slides are Second to none. PowerPoint presentation experts tell us our Blue PowerPoint templates and PPT Slides are Second to none. PowerPoint presentation experts tell us our sequential description using circular arrows workflow management PowerPoint Slides are Festive. Professionals tell us our Arrows PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Professionals tell us our sequential description using circular arrows workflow management PowerPoint Slides will get their audience's attention. People tell us our Business PowerPoint templates and PPT Slides are Energetic. Consumer connect with our Sequential Description Using Circular Arrows Workflow Management PowerPoint Slides. Enhance customer connectivity of your thoughts.

2012 And 2013 Concept On Grey Key PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our 2012 And 2013 Concept On Grey Key PowerPoint Templates PPT Backgrounds For Slides 1212.Use our Business PowerPoint Templates because you too have got the framework of your companys growth in place. Use our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download and present our Success PowerPoint Templates because the choices you make today will determine the future growth of your enterprise. Download our Services PowerPoint Templates because these slides are the triggers of our growth. Use our New year PowerPoint Templates because its New Year time.Use these PowerPoint slides for presentations relating to Key Isolated gray concept , business, marketing, new year, services, success. The prominent colors used in the PowerPoint template are Yellow, Orange, Gray. Professionals tell us our 2012 And 2013 Concept On Grey Key PowerPoint Templates PPT Backgrounds For Slides 1212 will help you be quick off the draw. Just enter your specific text and see your points hit home. We assure you our business PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our 2012 And 2013 Concept On Grey Key PowerPoint Templates PPT Backgrounds For Slides 1212 are Ritzy. Presenters tell us our business PowerPoint templates and PPT Slides are Radiant. The feedback we get is that our 2012 And 2013 Concept On Grey Key PowerPoint Templates PPT Backgrounds For Slides 1212 are Detailed. You can be sure our marketing PowerPoint templates and PPT Slides are Swanky. Get your ideas buzzing with our 2012 And 2013 Concept On Grey Key PowerPoint Templates Ppt Backgrounds For Slides 1212. They will be flying all around.
Business Entity Diagram 3d Men Social Group Of Friends Cooperation Concept PowerPoint Slides
We present our business entity diagram 3d men social group of friends cooperation concept PowerPoint Slides.Use our People PowerPoint Templates because It will get your audience in sync. Download and present our Leadership PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will let you Leave a lasting impression to your audiences. They possess an inherent longstanding recall factor. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Use these PowerPoint slides for presentations relating to 3d, business, cgi, chain, circle, color, colorful, community, company, concept, connection, cooperation, corporate, diversity, equality, friends, friendship, global, group, help, humanity, illustration, link, love, meeting, men, network, partner, partnership, peace, people, person, population, relation, relationship, render, social, society, standing, success, support, team, teamwork, together, unite, unity, white, world. The prominent colors used in the PowerPoint template are Orange, Green , Blue. Professionals tell us our business entity diagram 3d men social group of friends cooperation concept PowerPoint Slides will save the presenter time. The feedback we get is that our cgi PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our business entity diagram 3d men social group of friends cooperation concept PowerPoint Slides are readymade to fit into any presentation structure. You can be sure our community PowerPoint templates and PPT Slides effectively help you save your valuable time. People tell us our business entity diagram 3d men social group of friends cooperation concept PowerPoint Slides effectively help you save your valuable time. You can be sure our chain PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Attain success with our Business Entity Diagram 3d Men Social Group Of Friends Cooperation Concept PowerPoint Slides. You will come out on top.
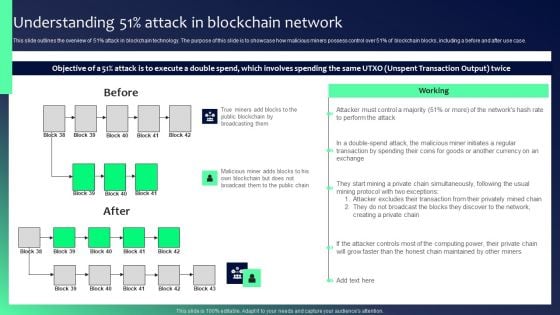
Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF
This slide outlines the overview of 51 percent attack in blockchain technology. The purpose of this slide is to showcase how malicious miners possess control over 51 percent of blockchain blocks, including a before and after use case. Retrieve professionally designed Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
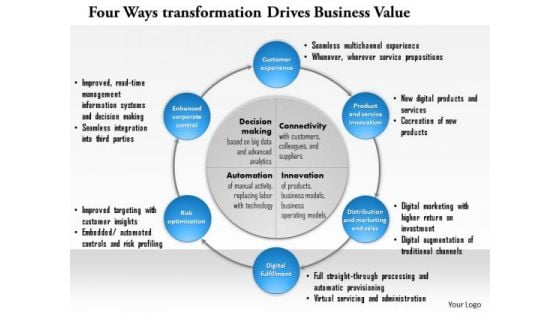
Business Framework Four Ways Digital Transformation Drives Business Value PowerPoint Presentation 1
This image slide displays four ways digital transformation drives business value. This image has been designed with graphic of circular diagram with decision making, connectivity, automation and innovation attributes. This image slide may be used in business and marketing presentations. Use this image slide to depict value chain in your presentations. This image slide will enhance the quality of your presentations.
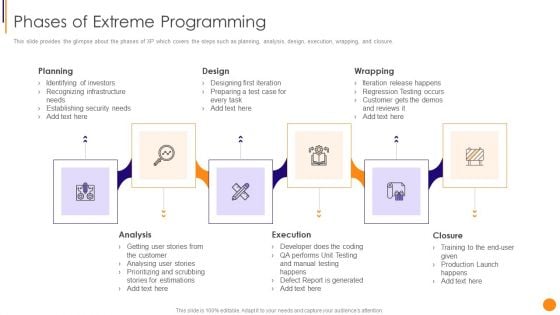
Scrum Crystal And Extreme Programming Procedure Phases Of Extreme Programming Graphics PDF
This slide provides the glimpse about the phases of XP which covers the steps such as planning, analysis, design, execution, wrapping, and closure. This is a scrum crystal and extreme programming procedure phases of extreme programming graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, infrastructure, recognizing, investors, security, prioritizing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
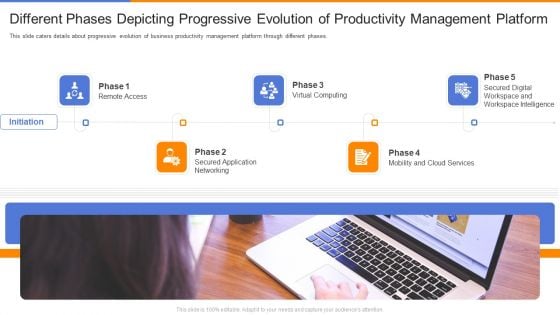
Organizational Productivity Administration Software Different Phases Depicting Progressive Evolution Microsoft PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. Presenting organizational productivity administration software different phases depicting progressive evolution microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secured application networking, virtual computing, mobility and cloud services, remote access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
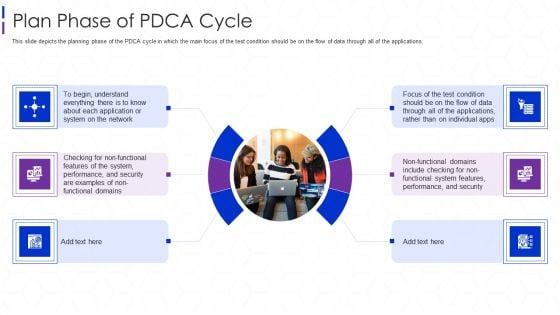
Software Interoperability Examination IT Plan Phase Of PDCA Cycle Clipart PDF
This slide depicts the planning phase of the PDCA cycle in which the main focus of the test condition should be on the flow of data through all of the applications. This is a software interoperability examination it plan phase of pdca cycle clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, system, security, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
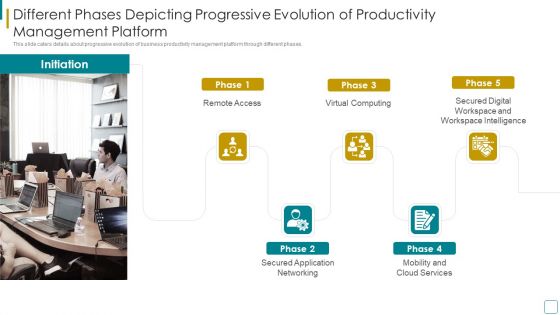
Strategic Business Efficiency Administration Tool Investor Financing Elevator Pitch Deck Different Phases Depicting Graphics PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. This is a strategic business efficiency administration tool investor financing elevator pitch deck different phases depicting graphics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like remote access, virtual computing, secured application networking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Application Development Life Cycle Phase 2 Designing The Product Architecture Template PDF
This slide depicts the designing of the product architecture phase of SDLC, including the factors documented in the DDS sheet such as risk assessment, product resilience, design flexibility, cost, etc. Presenting application development life cycle phase 2 designing the product architecture template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like overview and importance of secure sdlc. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
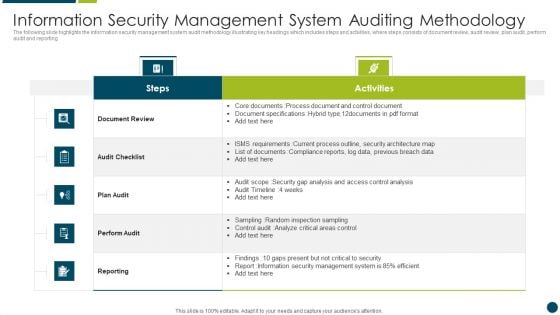
Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

3 Techniques To Manage Hotel Protection And Security Sample PDF
This slide highlights three techniques to manage hotel safety and security. It involves elements such as access control system, cameras in different locations and video verification system.Presenting 3 Techniques To Manage Hotel Protection And Security Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Access Control System, Cameras In Different Locations, Verification System This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
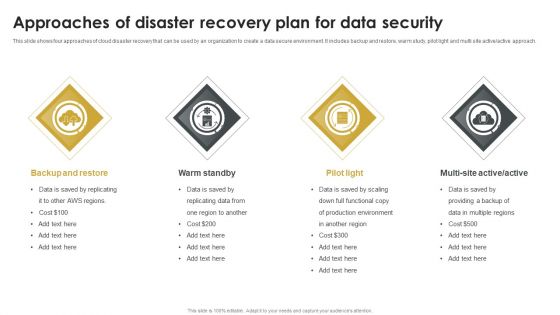
Approaches Of Disaster Recovery Plan For Data Security Topics PDF
This slide shows four approaches of cloud disaster recovery that can be used by an organization to create a data secure environment. It includes backup and restore, warm study, pilot light and multi site active or active approach. Presenting Approaches Of Disaster Recovery Plan For Data Security Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Warm Standby, Backup And Restore, Pilot Light. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Safety And Security Threat Report With Action Plan Mockup PDF
This slide shows report which can be used by an organization to prepare server security threat report. It includes date, time, description, action plan and remarks related to incident. Presenting Safety And Security Threat Report With Action Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Action Plan, Remarks, Diagnostic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
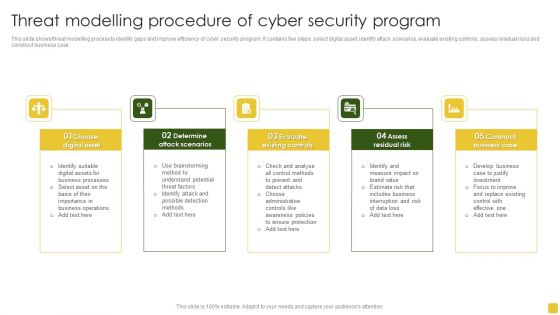
Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Data Breach And Trend Analysis Professional PDF
The following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting Information Technology Security Data Breach And Trend Analysis Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Breach, Average Cost, Determine. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
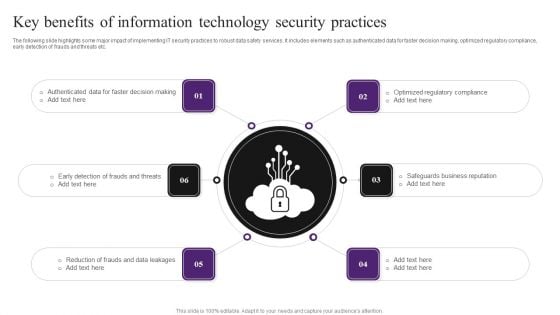
Key Benefits Of Information Technology Security Practices Summary PDF
The following slide highlights some major impact of implementing IT security practices to robust data safety services. It includes elements such as authenticated data for faster decision making, optimized regulatory compliance, early detection of frauds and threats etc. Presenting Key Benefits Of Information Technology Security Practices Summary PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Leakages, Reduction Of Frauds, Safeguards Business Reputation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
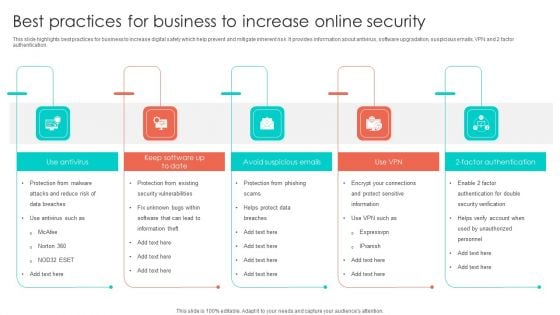
Best Practices For Business To Increase Online Security Introduction PDF
This slide highlights best practices for business to increase digital safety which help prevent and mitigate inherent risk. It provides information about antivirus, software upgradation, suspicious emails, VPN and 2 factor authentication. Presenting Best Practices For Business To Increase Online Security Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Vulnerabilities, Factor Authentication, Avoid Suspicious Emails. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
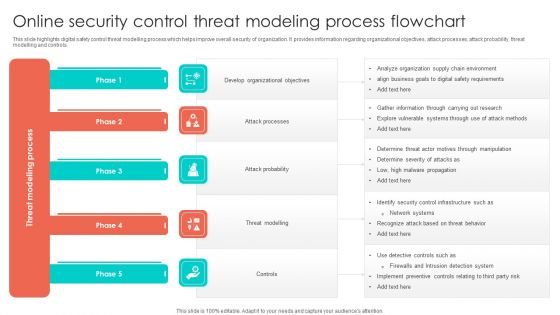
Online Security Control Threat Modeling Process Flowchart Structure PDF
This slide highlights digital safety control threat modelling process which helps improve overall security of organization. It provides information regarding organizational objectives, attack processes, attack probability, threat modelling and controls. Presenting Online Security Control Threat Modeling Process Flowchart Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Develop Organizational Objectives, Attack Probability, Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
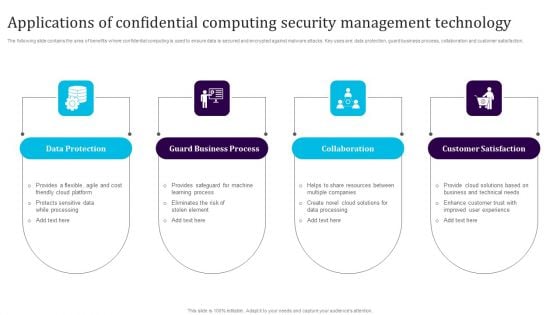
Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
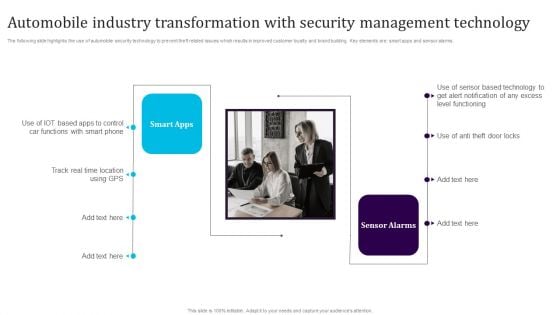
Automobile Industry Transformation With Security Management Technology Microsoft PDF
The following slide highlights the use of automobile security technology to prevent theft related issues which results in improved customer loyalty and brand building. Key elements are smart apps and sensor alarms. Presenting Automobile Industry Transformation With Security Management Technology Microsoft PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Smart Apps, Sensor Alarms. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Banking Security Management Technology Trends Introduction PDF
The following slide provides the integration of security technology with banking which helps to provide improved and enhanced customer experience. Key components are login protection, artificial intelligence and cloud computing. Presenting Digital Banking Security Management Technology Trends Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Login Protection, Ai, Cloud Computing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
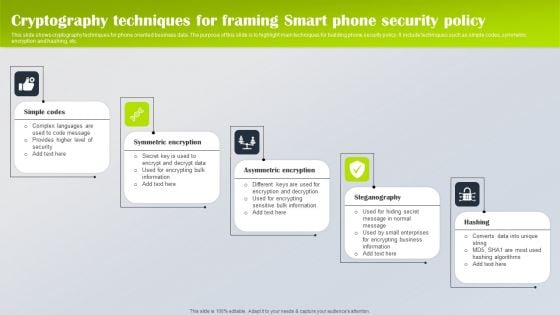
Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF
This slide shows cryptography techniques for phone oriented business data. The purpose of this slide is to highlight main techniques for building phone security policy. It include techniques such as simple codes, symmetric encryption and hashing, etc. Presenting Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Simple Codes, Symmetric Encryption, Asymmetric Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone Device Security Best Practices Structure PDF
This slide shows key practices for protecting business data of mobile. The purpose of this slide is to highlight latest practices that can be used for securing mobile data. It include practices such as enable user authentication, update OS system, etc. Presenting Smart Phone Device Security Best Practices Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Enable User Authentication, Avoid Using Public Wi Fi, Follow BYOD Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Network Security Threats And Solutions Infographics PDF
The slide showcases threats occurred due to data flowing between cloud service providers and organizations with their solutions. It includes lack of cloud security architecture and tactics, account hijacking , weak control plane , inadequate of identity, credentials, etc. Presenting Cloud Network Security Threats And Solutions Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats, Description, Solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
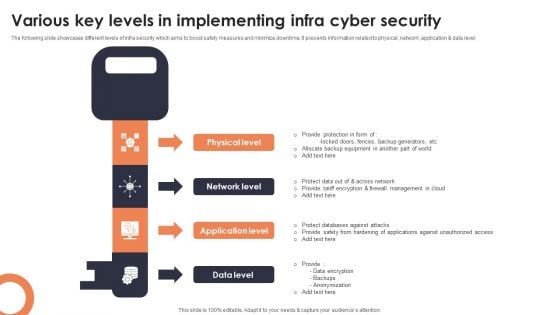
Various Key Levels In Implementing Infra Cyber Security Mockup PDF
The following slide showcases different levels of infra security which aims to boost safety measures and minimize downtime. It presents information related to physical, network, application and data level. Presenting Various Key Levels In Implementing Infra Cyber Security Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Physical Level, Network Level, Application Level. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
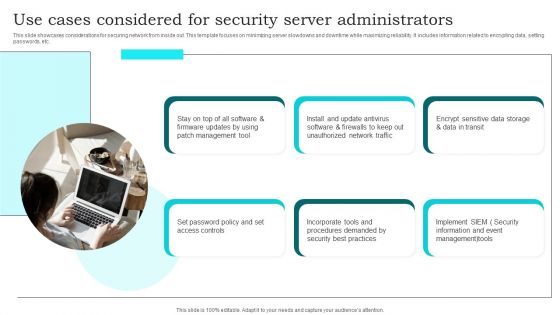
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
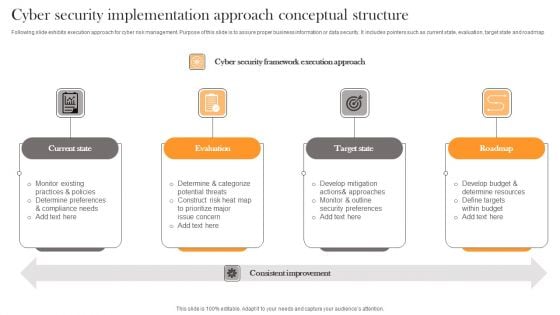
Cyber Security Implementation Approach Conceptual Structure Professional PDF
Following slide exhibits execution approach for cyber risk management. Purpose of this slide is to assure proper business information or data security. It includes pointers such as current state, evaluation, target state and roadmap. Presenting Cyber Security Implementation Approach Conceptual Structure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State, Evaluation, Target State . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
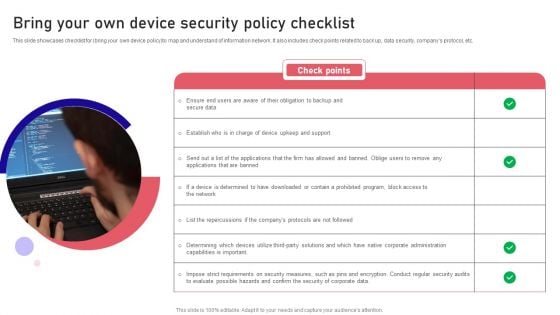
Bring Your Own Device Security Policy Checklist Graphics PDF
This slide showcases checklist for bring your own device policy to map and understand of information network. It also includes check points related to back up, data security, companys protocol, etc. Presenting Bring Your Own Device Security Policy Checklist Graphics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Check Points, Checklist, Device. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
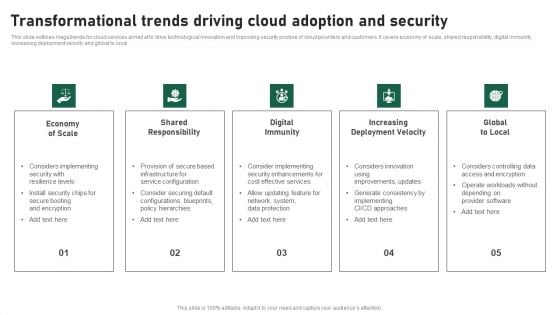
Transformational Trends Driving Cloud Adoption And Security Clipart PDF
This slide outlines mega trends for cloud services aimed at to drive technological innovation and improving security posture of cloud providers and customers. It covers economy of scale, shared responsibility, digital immunity, increasing deployment velocity and global to local. Presenting Transformational Trends Driving Cloud Adoption And Security Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Economy Of Scale, Shared Responsibility, Digital Immunity, Increasing Deployment Velocity, Global To Local. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
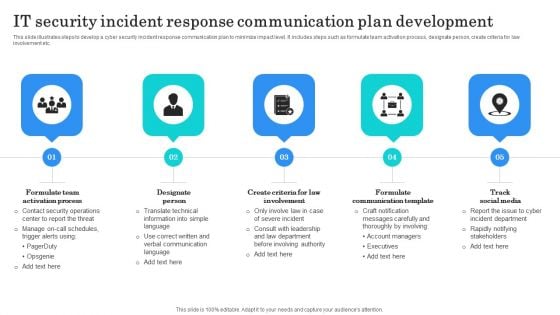
IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
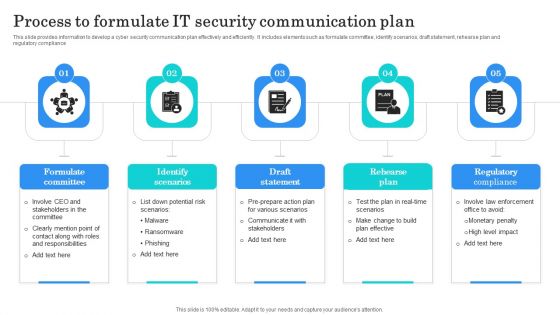
Process To Formulate IT Security Communication Plan Clipart PDF
This slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Presenting Process To Formulate IT Security Communication Plan Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Committee, Identify Scenarios, Draft Statement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home