Lock Icon
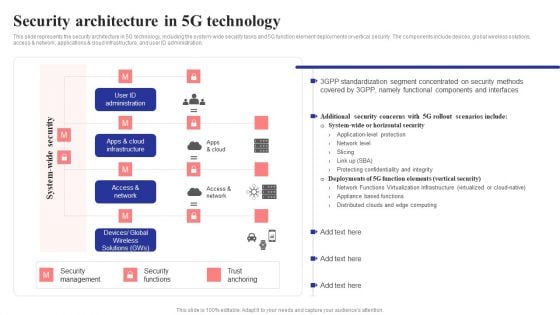
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
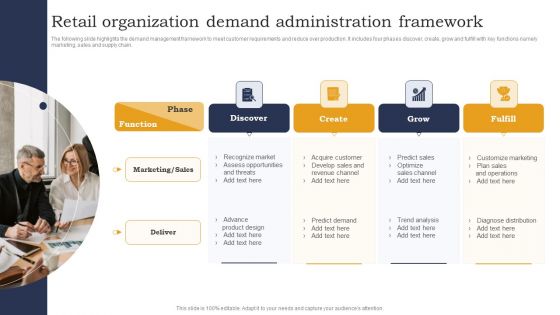
Retail Organization Demand Administration Framework Download PDF
The following slide highlights the demand management framework to meet customer requirements and reduce over production. It includes four phases discover, create, grow and fulfill with key functions namely marketing, sales and supply chain. Showcasing this set of slides titled Retail Organization Demand Administration Framework Download PDF. The topics addressed in these templates are Recognize Market, Assess Opportunities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
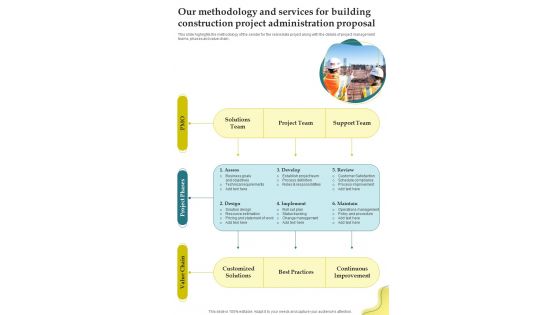
Our Methodology And Services For Building Construction Project Administration Proposal One Pager Sample Example Document
This slide highlights the methodology of the sender for the real estate project along with the details of project management teams, phases and value chain. Presenting you an exemplary Our Methodology And Services For Building Construction Project Administration Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Methodology And Services For Building Construction Project Administration Proposal One Pager Sample Example Document brilliant piece now.

Our Methodology And Services For Project Development Planning Template One Pager Sample Example Document
This slide highlights the methodology of the sender for the real estate project along with the details of project management teams, phases and value chain . Presenting you an exemplary Our Methodology And Services For Project Development Planning Template One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Methodology And Services For Project Development Planning Template One Pager Sample Example Document brilliant piece now.

Our Methodology Services Strategic Project Plan Administration Proposal One Pager Sample Example Document
This slide highlights the methodology of the sender for the real estate project along with the details of project management teams, phases and value chain. Presenting you an exemplary Our Methodology Services Strategic Project Plan Administration Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Methodology Services Strategic Project Plan Administration Proposal One Pager Sample Example Document brilliant piece now.

DAD Framework Disciplined Agile Delivery Phases And Goals Ppt Model Professional PDF
This slide covers delivery phases like Inception, Construction, Transition and ongoing. Each of these phases are described by specific goals. Some goals, such as Grow Team Members and Address Risk, are applicable throughout the entire lifecycle. Deliver and pitch your topic in the best possible manner with this DAD framework disciplined agile delivery phases and goals ppt model professional pdf. Use them to share invaluable insights on develop test strategy, grow team members, produce a potentially consumable solution, secure funding, goals and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
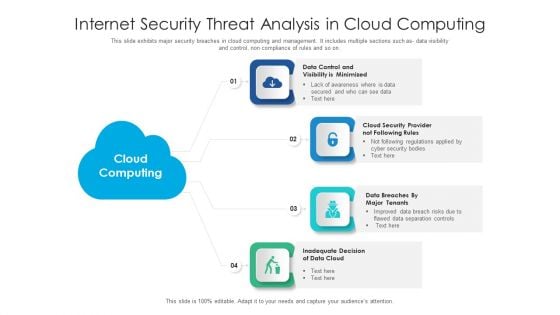
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
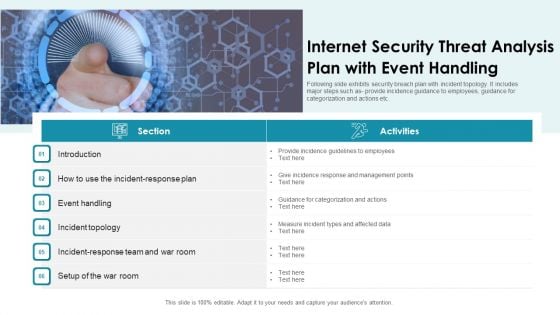
Internet Security Threat Analysis Plan With Event Handling Summary PDF
Following slide exhibits security breach plan with incident topology. It includes major steps such as- provide incidence guidance to employees, guidance for categorization and actions etc. Presenting internet security threat analysis plan with event handling summary pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including internet security threat analysis plan with event handling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
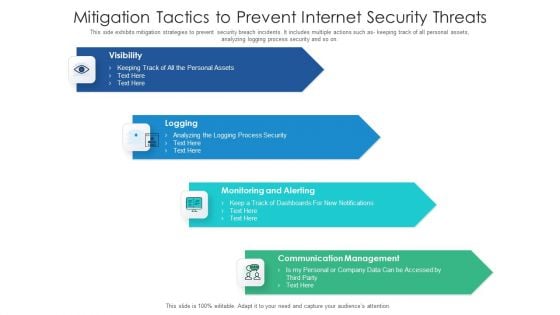
Mitigation Tactics To Prevent Internet Security Threats Formats PDF
This side exhibits mitigation strategies to prevent security breach incidents. It includes multiple actions such as keeping track of all personal assets, analyzing logging process security and so on. Presenting mitigation tactics to prevent internet security threats formats pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including communication management, monitoring and alerting, logging, visibility. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
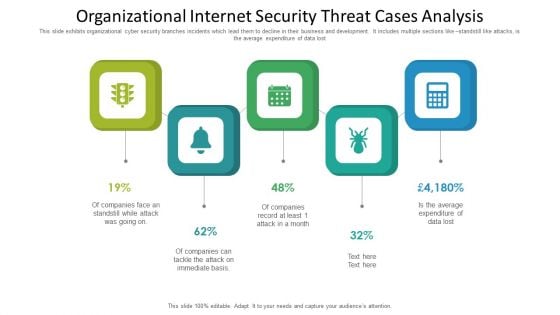
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
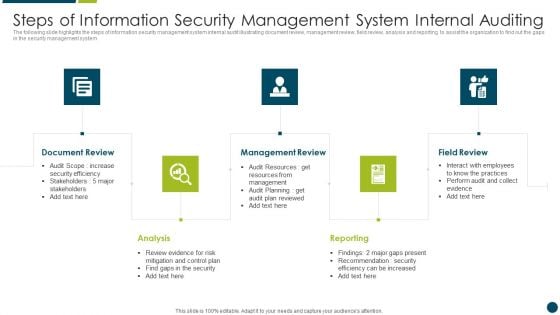
Steps Of Information Security Management System Internal Auditing Structure PDF
The following slide highlights the steps of information security management system internal audit illustrating document review, management review, field review, analysis and reporting to assist the organization to find out the gaps in the security management system Presenting Steps Of Information Security Management System Internal Auditing Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Management Review, Reporting, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully

Five Key Consideration For Hotel Protection And Security Infographics PDF
This slide highlights five strategies to ensure safety and security in hotels. It involves strategies such as installation of proper lighting, CCTV security cameras, fire alarms, emergency power and manual.Presenting Five Key Consideration For Hotel Protection And Security Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Emergency Power, Emergency Manual, Proper Lighting This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Six Practices For IT Security Management Program Microsoft PDF
This slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency.Presenting Six Practices For IT Security Management Program Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Analysis Prioritization, Consolidation Procedure, Strategic Initiatives This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
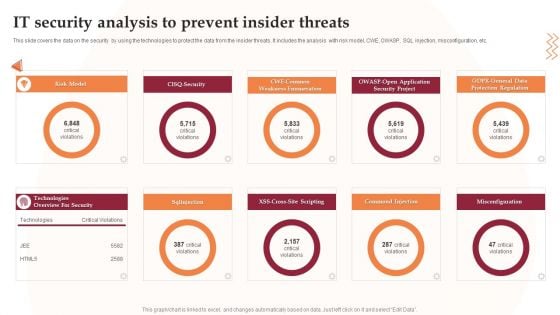
IT Security Analysis To Prevent Insider Threats Infographics PDF
This slide covers the data on the security by using the technologies to protect the data from the insider threats. It includes the analysis with risk model, CWE, OWASP, SQL injection, misconfiguration, etc. Presenting IT Security Analysis To Prevent Insider Threats Infographics PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Project, Application, Risk Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
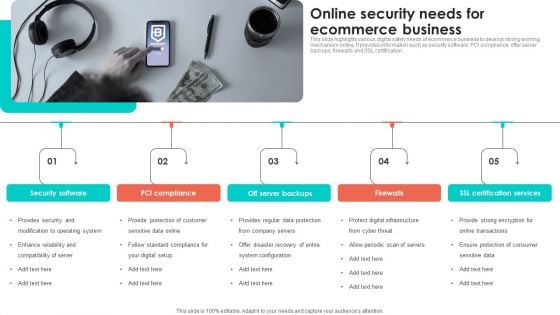
Online Security Needs For Ecommerce Business Professional PDF
This slide highlights various digital safety needs of ecommerce business to develop strong working mechanism online. It provides information such as security software, PCI compliance, offer server backups, firewalls and SSL certification. Presenting Online Security Needs For Ecommerce Business Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including PCI Compliance, Off Server Backups, Security Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
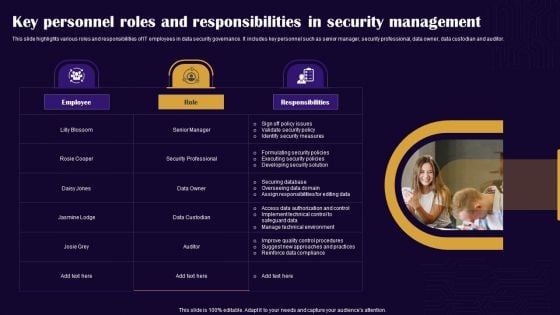
Key Personnel Roles And Responsibilities In Security Management Slides PDF
This slide highlights various roles and responsibilities of IT employees in data security governance. It includes key personnel such as senior manager, security professional, data owner, data custodian and auditor. Presenting Key Personnel Roles And Responsibilities In Security Management Slides PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Employee, Role, Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
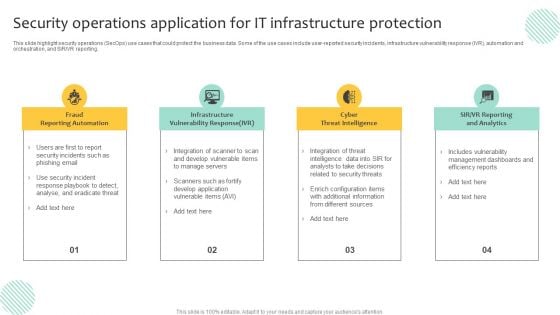
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
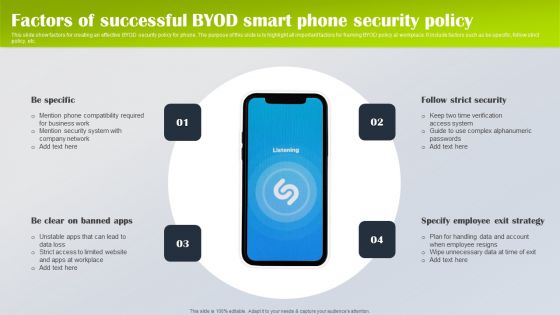
Factors Of Successful Byod Smart Phone Security Policy Designs PDF
This slide show factors for creating an effective BYOD security policy for phone. The purpose of this slide is to highlight all important factors for framing BYOD policy at workplace. It include factors such as be specific, follow strict policy, etc. Presenting Factors Of Successful Byod Smart Phone Security Policy Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Be Specific, Specify Employee Exit Strategy, Follow Strict Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
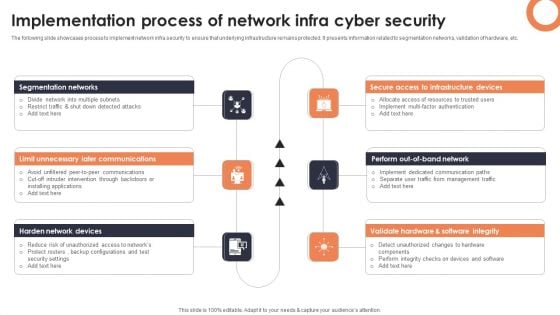
Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
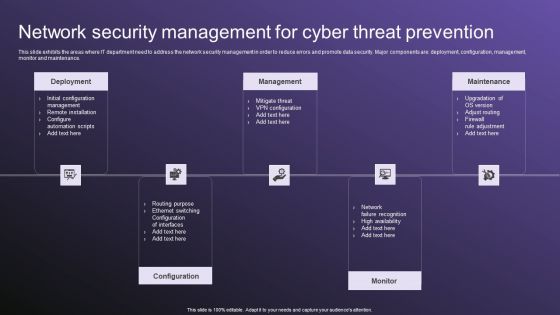
Network Security Management For Cyber Threat Prevention Demonstration PDF
This slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting Network Security Management For Cyber Threat Prevention Demonstration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Deployment, Management, Configuration. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
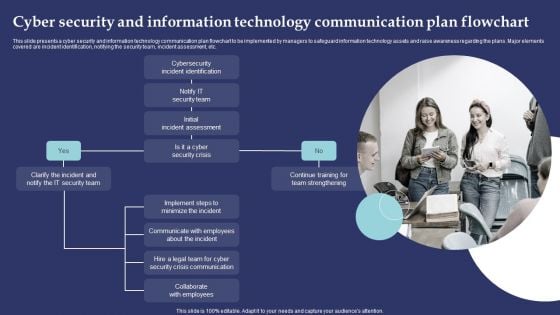
Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF
This slide presents a cyber security and information technology communication plan flowchart to be implemented by managers to safeguard information technology assets and raise awareness regarding the plans. Major elements covered are incident identification, notifying the security team, incident assessment, etc. Presenting Cyber Security And Information Technology Communication Plan Flowchart Guidelines PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cybersecurity Incident Identification, Initial Incident Assessment, Continue Training Team Strengthening. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
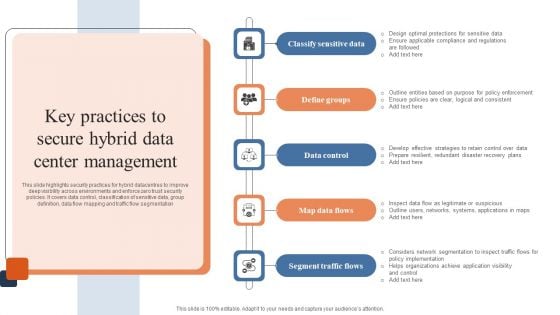
Key Practices To Secure Hybrid Data Center Management Ideas PDF
This slide highlights security practices for hybrid datacentres to improve deep visibility across environments and enforce zero trust security policies. It covers data control, classification of sensitive data, group definition, data flow mapping and traffic flow segmentation. Presenting Key Practices To Secure Hybrid Data Center Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Classify Sensitive Data, Define Groups, Data Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
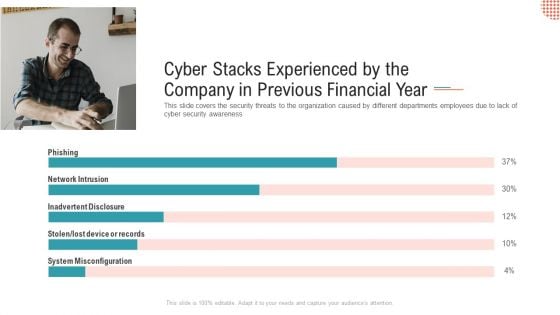
Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Show Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver and pitch your topic in the best possible manner with this cyber stacks experienced by the company in previous financial year ppt show themes pdf. Use them to share invaluable insights on network intrusion, inadvertent disclosure, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
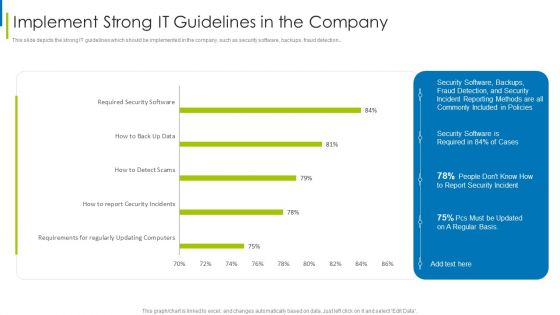
Cyber Terrorism Assault Implement Strong IT Guidelines In The Company Themes PDF
This slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault implement strong it guidelines in the company themes pdf Use them to share invaluable insights on requirements regularly, updating computers, required security software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Bar Graph To Secure Data PowerPoint Templates Ppt Backgrounds For Slides 0713
Get the doers into action. Activate them with our Bar Graph To Secure Data PowerPoint Templates PPT Backgrounds For Slides. Put your money on our Pie Charts PowerPoint Templates. Your ideas will rake in the dollars. Put in a dollop of our Arrows PowerPoint Templates. Give your thoughts a distinctive flavour. Our Bar Graph To Secure Data PowerPoint Templates Ppt Backgrounds For Slides 0713 assist execution. They channel the action in the desired direction.
Sequential Description Using Circular Arrows Workflow Management PowerPoint Slides
We present our sequential description using circular arrows workflow management PowerPoint Slides.Use our Arrows PowerPoint Templates because,You can Start with the fundamental basic activities and slowly but surely hone them down to the top of the pyramid, the ultimate goal. Use our Circle Charts PowerPoint Templates because,Our cleverly selected background hues are guaranteed to achieve this aim. Use our Shapes PowerPoint Templates because,This diagram depicts the essence of this chain reaction like sequence of events. Use our Design PowerPoint Templates because,watching them will strengthen your companys sinews. Use our Process and Flows PowerPoint Templates because,our creative template will lay down your views.Use these PowerPoint slides for presentations relating to 3d, Abstract, Around, Arrows, Blue, Border, Business, Center, Circle, Circular, Concept, Connections, Copy, Curve, Cycle, Directions, Distribution, Illustration, Management, Middle, Objects, Pieces, Plan, Pointing, Process, Recycle, Rounded, Shadows, Space, System. The prominent colors used in the PowerPoint template are Blue, Gray, Black. People tell us our sequential description using circular arrows workflow management PowerPoint Slides are Second to none. PowerPoint presentation experts tell us our Blue PowerPoint templates and PPT Slides are Second to none. PowerPoint presentation experts tell us our sequential description using circular arrows workflow management PowerPoint Slides are Festive. Professionals tell us our Arrows PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. Professionals tell us our sequential description using circular arrows workflow management PowerPoint Slides will get their audience's attention. People tell us our Business PowerPoint templates and PPT Slides are Energetic. Consumer connect with our Sequential Description Using Circular Arrows Workflow Management PowerPoint Slides. Enhance customer connectivity of your thoughts.

2012 And 2013 Concept On Grey Key PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our 2012 And 2013 Concept On Grey Key PowerPoint Templates PPT Backgrounds For Slides 1212.Use our Business PowerPoint Templates because you too have got the framework of your companys growth in place. Use our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download and present our Success PowerPoint Templates because the choices you make today will determine the future growth of your enterprise. Download our Services PowerPoint Templates because these slides are the triggers of our growth. Use our New year PowerPoint Templates because its New Year time.Use these PowerPoint slides for presentations relating to Key Isolated gray concept , business, marketing, new year, services, success. The prominent colors used in the PowerPoint template are Yellow, Orange, Gray. Professionals tell us our 2012 And 2013 Concept On Grey Key PowerPoint Templates PPT Backgrounds For Slides 1212 will help you be quick off the draw. Just enter your specific text and see your points hit home. We assure you our business PowerPoint templates and PPT Slides help you meet deadlines which are an element of today's workplace. Just browse and pick the slides that appeal to your intuitive senses. PowerPoint presentation experts tell us our 2012 And 2013 Concept On Grey Key PowerPoint Templates PPT Backgrounds For Slides 1212 are Ritzy. Presenters tell us our business PowerPoint templates and PPT Slides are Radiant. The feedback we get is that our 2012 And 2013 Concept On Grey Key PowerPoint Templates PPT Backgrounds For Slides 1212 are Detailed. You can be sure our marketing PowerPoint templates and PPT Slides are Swanky. Get your ideas buzzing with our 2012 And 2013 Concept On Grey Key PowerPoint Templates Ppt Backgrounds For Slides 1212. They will be flying all around.
Business Entity Diagram 3d Men Social Group Of Friends Cooperation Concept PowerPoint Slides
We present our business entity diagram 3d men social group of friends cooperation concept PowerPoint Slides.Use our People PowerPoint Templates because It will get your audience in sync. Download and present our Leadership PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Download our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will let you Leave a lasting impression to your audiences. They possess an inherent longstanding recall factor. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. Use these PowerPoint slides for presentations relating to 3d, business, cgi, chain, circle, color, colorful, community, company, concept, connection, cooperation, corporate, diversity, equality, friends, friendship, global, group, help, humanity, illustration, link, love, meeting, men, network, partner, partnership, peace, people, person, population, relation, relationship, render, social, society, standing, success, support, team, teamwork, together, unite, unity, white, world. The prominent colors used in the PowerPoint template are Orange, Green , Blue. Professionals tell us our business entity diagram 3d men social group of friends cooperation concept PowerPoint Slides will save the presenter time. The feedback we get is that our cgi PowerPoint templates and PPT Slides provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our business entity diagram 3d men social group of friends cooperation concept PowerPoint Slides are readymade to fit into any presentation structure. You can be sure our community PowerPoint templates and PPT Slides effectively help you save your valuable time. People tell us our business entity diagram 3d men social group of friends cooperation concept PowerPoint Slides effectively help you save your valuable time. You can be sure our chain PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Attain success with our Business Entity Diagram 3d Men Social Group Of Friends Cooperation Concept PowerPoint Slides. You will come out on top.
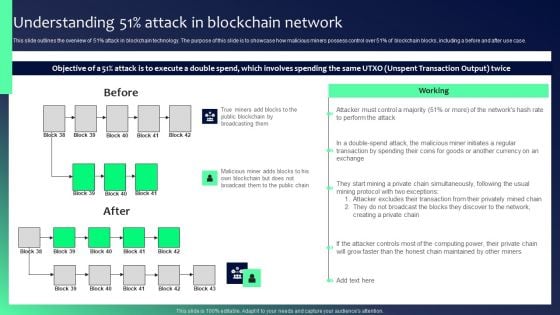
Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF
This slide outlines the overview of 51 percent attack in blockchain technology. The purpose of this slide is to showcase how malicious miners possess control over 51 percent of blockchain blocks, including a before and after use case. Retrieve professionally designed Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
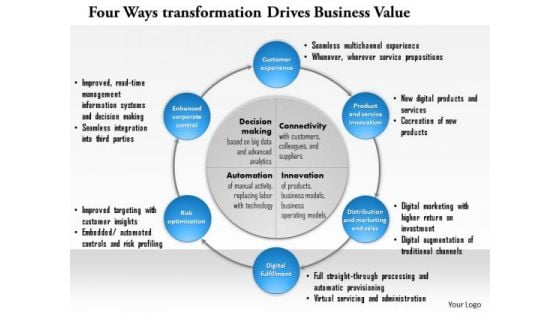
Business Framework Four Ways Digital Transformation Drives Business Value PowerPoint Presentation 1
This image slide displays four ways digital transformation drives business value. This image has been designed with graphic of circular diagram with decision making, connectivity, automation and innovation attributes. This image slide may be used in business and marketing presentations. Use this image slide to depict value chain in your presentations. This image slide will enhance the quality of your presentations.
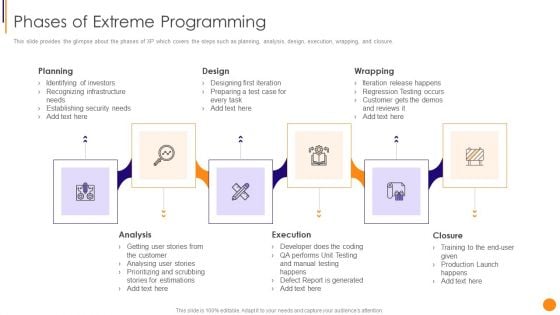
Scrum Crystal And Extreme Programming Procedure Phases Of Extreme Programming Graphics PDF
This slide provides the glimpse about the phases of XP which covers the steps such as planning, analysis, design, execution, wrapping, and closure. This is a scrum crystal and extreme programming procedure phases of extreme programming graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, infrastructure, recognizing, investors, security, prioritizing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
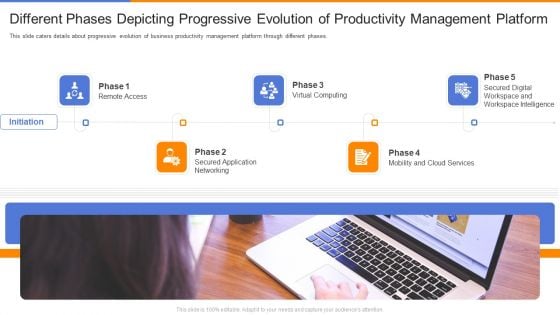
Organizational Productivity Administration Software Different Phases Depicting Progressive Evolution Microsoft PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. Presenting organizational productivity administration software different phases depicting progressive evolution microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like secured application networking, virtual computing, mobility and cloud services, remote access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
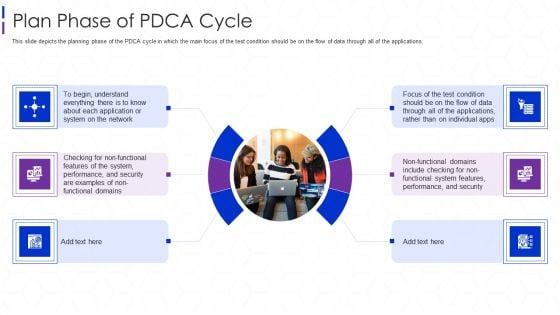
Software Interoperability Examination IT Plan Phase Of PDCA Cycle Clipart PDF
This slide depicts the planning phase of the PDCA cycle in which the main focus of the test condition should be on the flow of data through all of the applications. This is a software interoperability examination it plan phase of pdca cycle clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, system, security, performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
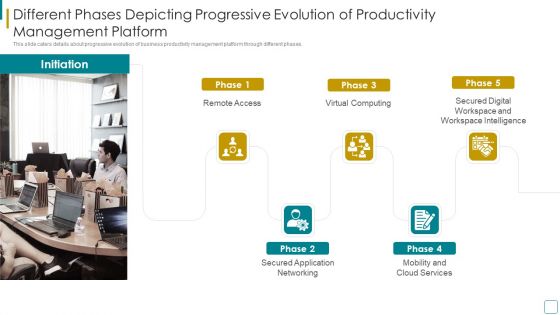
Strategic Business Efficiency Administration Tool Investor Financing Elevator Pitch Deck Different Phases Depicting Graphics PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. This is a strategic business efficiency administration tool investor financing elevator pitch deck different phases depicting graphics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like remote access, virtual computing, secured application networking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Application Development Life Cycle Phase 2 Designing The Product Architecture Template PDF
This slide depicts the designing of the product architecture phase of SDLC, including the factors documented in the DDS sheet such as risk assessment, product resilience, design flexibility, cost, etc. Presenting application development life cycle phase 2 designing the product architecture template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like overview and importance of secure sdlc. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
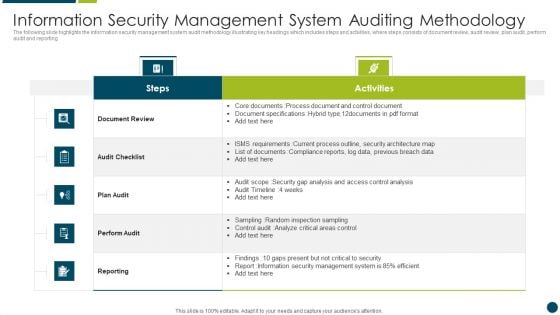
Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

3 Techniques To Manage Hotel Protection And Security Sample PDF
This slide highlights three techniques to manage hotel safety and security. It involves elements such as access control system, cameras in different locations and video verification system.Presenting 3 Techniques To Manage Hotel Protection And Security Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Access Control System, Cameras In Different Locations, Verification System This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
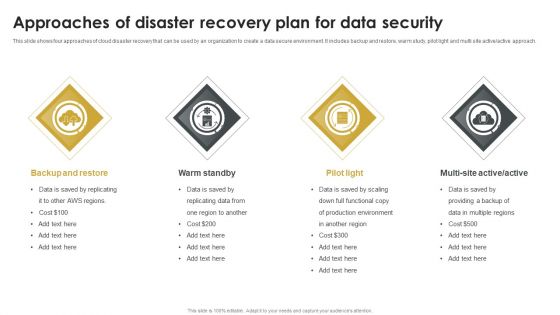
Approaches Of Disaster Recovery Plan For Data Security Topics PDF
This slide shows four approaches of cloud disaster recovery that can be used by an organization to create a data secure environment. It includes backup and restore, warm study, pilot light and multi site active or active approach. Presenting Approaches Of Disaster Recovery Plan For Data Security Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Warm Standby, Backup And Restore, Pilot Light. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Safety And Security Threat Report With Action Plan Mockup PDF
This slide shows report which can be used by an organization to prepare server security threat report. It includes date, time, description, action plan and remarks related to incident. Presenting Safety And Security Threat Report With Action Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Action Plan, Remarks, Diagnostic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
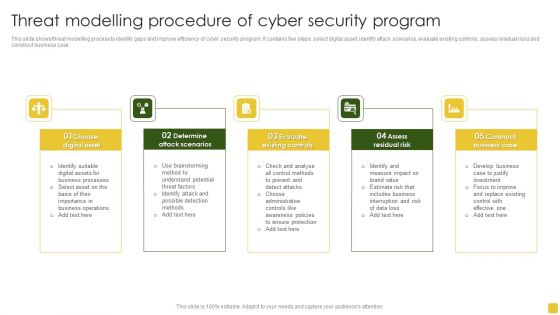
Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Security Data Breach And Trend Analysis Professional PDF
The following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting Information Technology Security Data Breach And Trend Analysis Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Breach, Average Cost, Determine. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
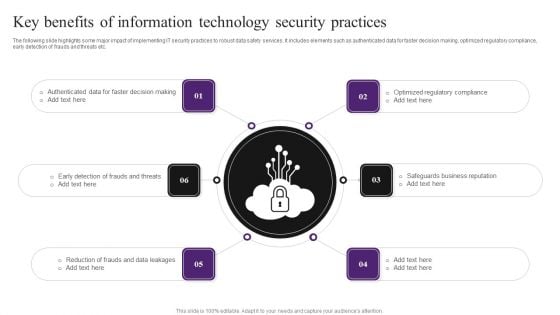
Key Benefits Of Information Technology Security Practices Summary PDF
The following slide highlights some major impact of implementing IT security practices to robust data safety services. It includes elements such as authenticated data for faster decision making, optimized regulatory compliance, early detection of frauds and threats etc. Presenting Key Benefits Of Information Technology Security Practices Summary PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Leakages, Reduction Of Frauds, Safeguards Business Reputation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
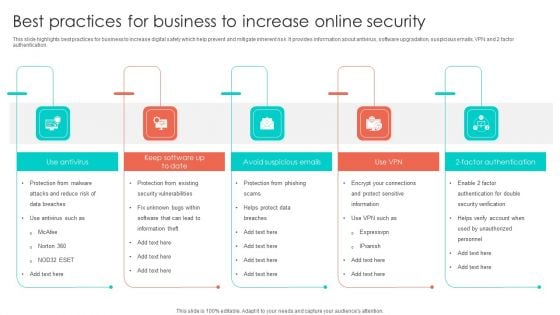
Best Practices For Business To Increase Online Security Introduction PDF
This slide highlights best practices for business to increase digital safety which help prevent and mitigate inherent risk. It provides information about antivirus, software upgradation, suspicious emails, VPN and 2 factor authentication. Presenting Best Practices For Business To Increase Online Security Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Vulnerabilities, Factor Authentication, Avoid Suspicious Emails. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
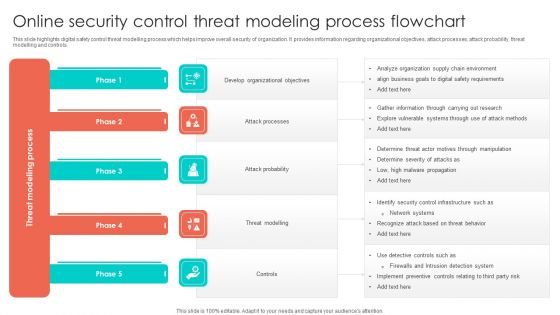
Online Security Control Threat Modeling Process Flowchart Structure PDF
This slide highlights digital safety control threat modelling process which helps improve overall security of organization. It provides information regarding organizational objectives, attack processes, attack probability, threat modelling and controls. Presenting Online Security Control Threat Modeling Process Flowchart Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Develop Organizational Objectives, Attack Probability, Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
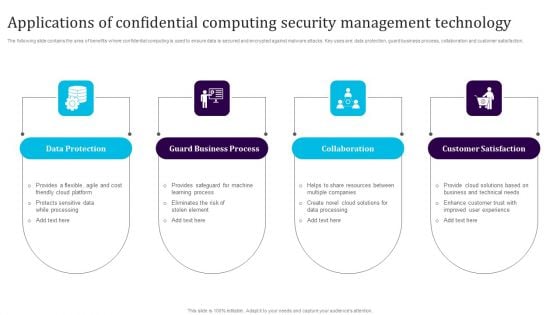
Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
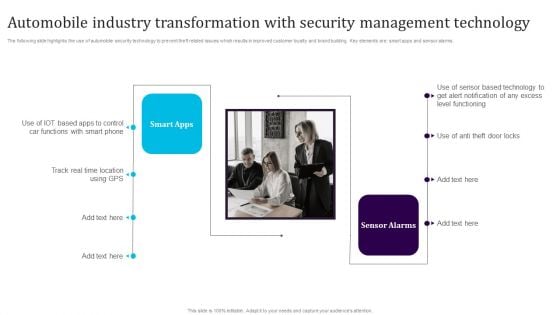
Automobile Industry Transformation With Security Management Technology Microsoft PDF
The following slide highlights the use of automobile security technology to prevent theft related issues which results in improved customer loyalty and brand building. Key elements are smart apps and sensor alarms. Presenting Automobile Industry Transformation With Security Management Technology Microsoft PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Smart Apps, Sensor Alarms. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Digital Banking Security Management Technology Trends Introduction PDF
The following slide provides the integration of security technology with banking which helps to provide improved and enhanced customer experience. Key components are login protection, artificial intelligence and cloud computing. Presenting Digital Banking Security Management Technology Trends Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Login Protection, Ai, Cloud Computing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
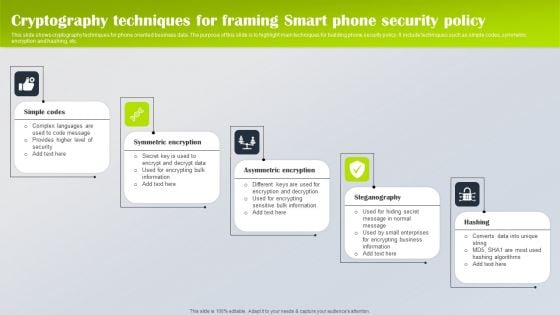
Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF
This slide shows cryptography techniques for phone oriented business data. The purpose of this slide is to highlight main techniques for building phone security policy. It include techniques such as simple codes, symmetric encryption and hashing, etc. Presenting Cryptography Techniques For Framing Smart Phone Security Policy Portrait PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Simple Codes, Symmetric Encryption, Asymmetric Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Phone Device Security Best Practices Structure PDF
This slide shows key practices for protecting business data of mobile. The purpose of this slide is to highlight latest practices that can be used for securing mobile data. It include practices such as enable user authentication, update OS system, etc. Presenting Smart Phone Device Security Best Practices Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Enable User Authentication, Avoid Using Public Wi Fi, Follow BYOD Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Network Security Threats And Solutions Infographics PDF
The slide showcases threats occurred due to data flowing between cloud service providers and organizations with their solutions. It includes lack of cloud security architecture and tactics, account hijacking , weak control plane , inadequate of identity, credentials, etc. Presenting Cloud Network Security Threats And Solutions Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats, Description, Solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
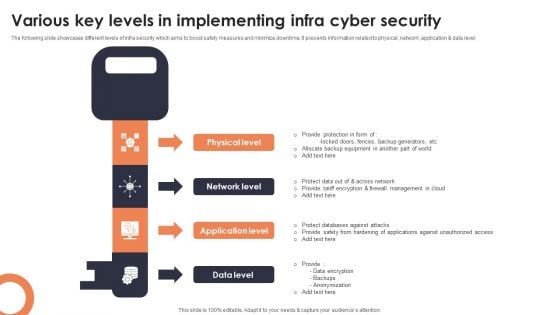
Various Key Levels In Implementing Infra Cyber Security Mockup PDF
The following slide showcases different levels of infra security which aims to boost safety measures and minimize downtime. It presents information related to physical, network, application and data level. Presenting Various Key Levels In Implementing Infra Cyber Security Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Physical Level, Network Level, Application Level. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
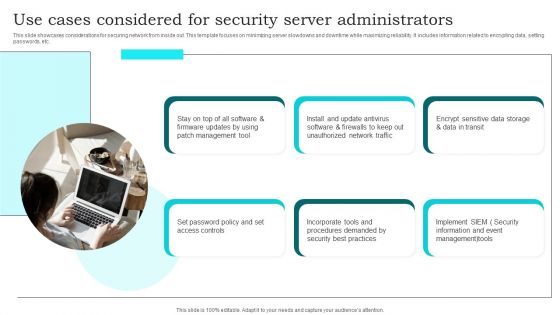
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
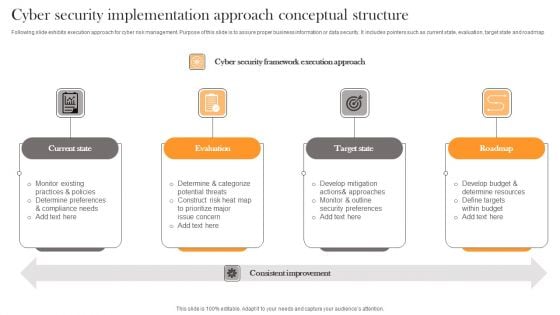
Cyber Security Implementation Approach Conceptual Structure Professional PDF
Following slide exhibits execution approach for cyber risk management. Purpose of this slide is to assure proper business information or data security. It includes pointers such as current state, evaluation, target state and roadmap. Presenting Cyber Security Implementation Approach Conceptual Structure Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State, Evaluation, Target State . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
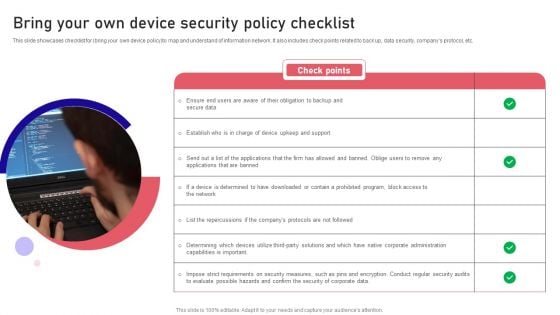
Bring Your Own Device Security Policy Checklist Graphics PDF
This slide showcases checklist for bring your own device policy to map and understand of information network. It also includes check points related to back up, data security, companys protocol, etc. Presenting Bring Your Own Device Security Policy Checklist Graphics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Check Points, Checklist, Device. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
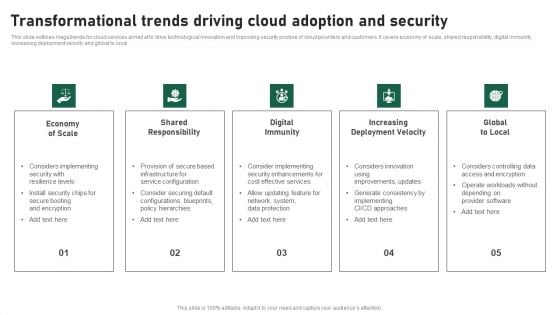
Transformational Trends Driving Cloud Adoption And Security Clipart PDF
This slide outlines mega trends for cloud services aimed at to drive technological innovation and improving security posture of cloud providers and customers. It covers economy of scale, shared responsibility, digital immunity, increasing deployment velocity and global to local. Presenting Transformational Trends Driving Cloud Adoption And Security Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Economy Of Scale, Shared Responsibility, Digital Immunity, Increasing Deployment Velocity, Global To Local. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
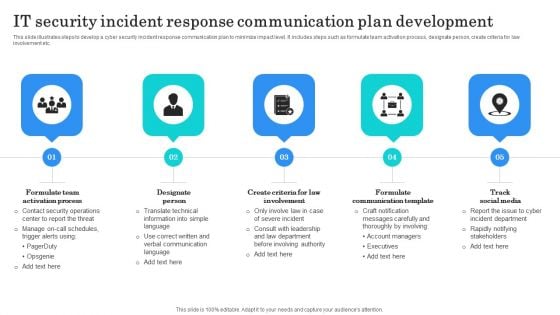
IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
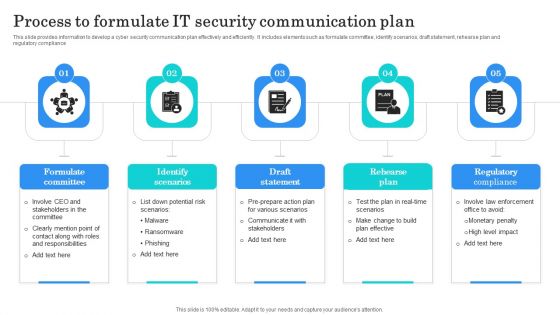
Process To Formulate IT Security Communication Plan Clipart PDF
This slide provides information to develop a cyber security communication plan effectively and efficiently. It includes elements such as formulate committee, identify scenarios, draft statement, rehearse plan and regulatory compliance. Presenting Process To Formulate IT Security Communication Plan Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Committee, Identify Scenarios, Draft Statement. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home