Lock
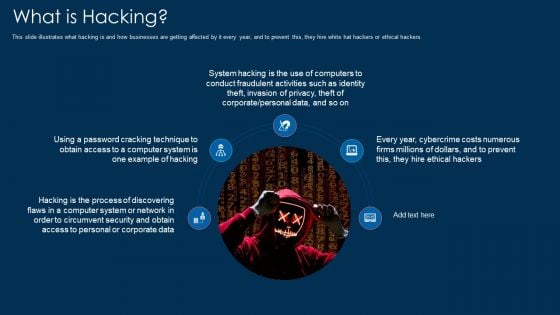
What Is Hacking Ppt Gallery Layouts PDF
Presenting what is hacking ppt gallery layouts pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like system, technique, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
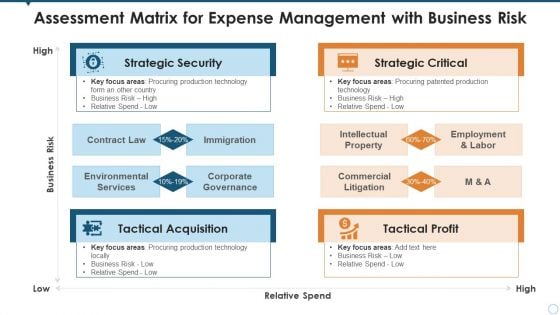
Assessment Matrix For Expense Management With Business Risk Mockup PDF
Showcasing this set of slides titled assessment matrix for expense management with business risk mockup pdf. The topics addressed in these templates are strategic security, strategic critical, tactical profit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
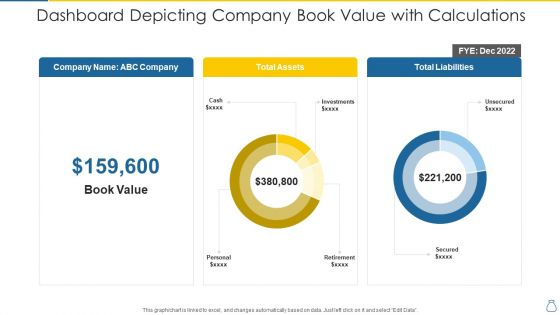
Dashboard Depicting Company Book Value With Calculations Microsoft PDF
Pitch your topic with ease and precision using this dashboard depicting company book value with calculations microsoft pdf. This layout presents information on cash, investments, personal, retirement, secured. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
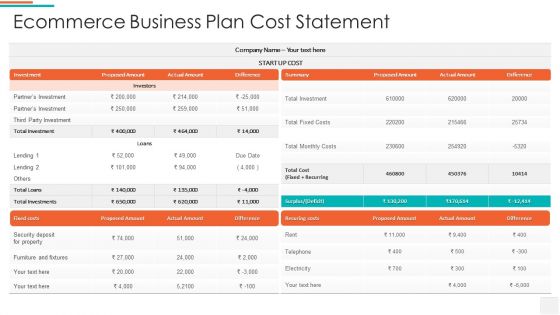
Ecommerce Business Plan Cost Statement Demonstration PDF
Pitch your topic with ease and precision using this ecommerce business plan cost statement demonstration pdf. This layout presents information on investments, security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents For Effective IT Risk Management Process Summary PDF
Deliver and pitch your topic in the best possible manner with this table of contents for effective it risk management process summary pdf. Use them to share invaluable insights on management, matrix, system, security, analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
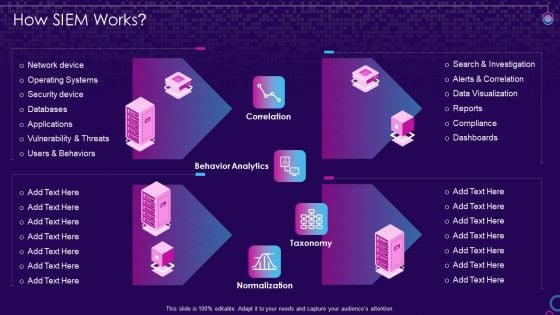
SIEM Services How SIEM Works Ppt Microsoft PDF
Deliver an awe inspiring pitch with this creative siem services how siem works ppt microsoft pdf bundle. Topics like network device, operating systems, security device, vulnerability and threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Application Programming Interface Management Architecture With Gateway And Resource Formats PDF
Showcasing this set of slides titled application programming interface management architecture with gateway and resource formats pdf. The topics addressed in these templates are demonstration, security, application. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
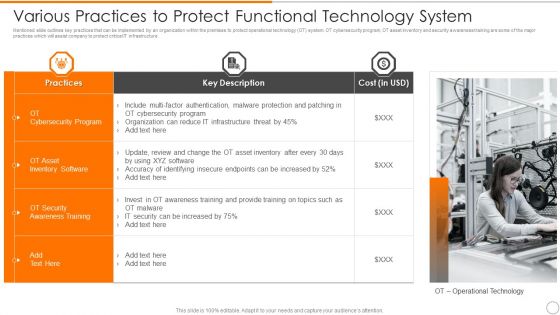
Various Practices To Protect Functional Technology System Information PDF
Showcasing this set of slides titled various practices to protect functional technology system information pdf. The topics addressed in these templates are inventory software, awareness training, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Motivators And Hygiene Factors For Human Capital Optimization Icons PDF
Pitch your topic with ease and precision using this motivators and hygiene factors for human capital optimization icons pdf. This layout presents information on growth, security, remuneration. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Software Application Architecture Roadmap Covering Features And User Experience Topics PDF
Pitch your topic with ease and precision using this software application architecture roadmap covering features and user experience topics pdf. This layout presents information on conversion tracking, security policy, search. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
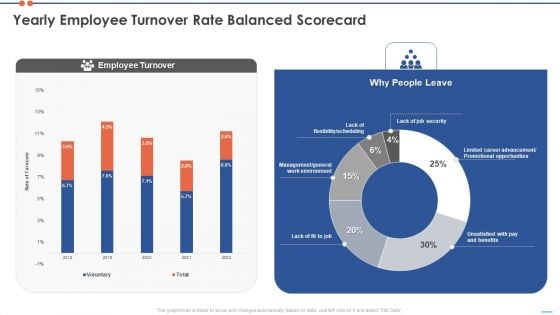
Staff Turnover Ratio BSC Yearly Employee Turnover Rate Balanced Scorecard Inspiration PDF
Deliver and pitch your topic in the best possible manner with this staff turnover ratio bsc yearly employee turnover rate balanced scorecard inspiration pdf. Use them to share invaluable insights on opportunities, job security, flexibility, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Digitized Record Book Technology Portrait PDF
Deliver an awe inspiring pitch with this creative table of contents for digitized record book technology portrait pdf bundle. Topics like security, technologies, implementation, system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
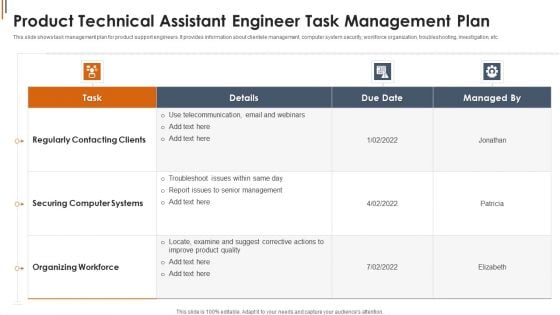
Product Technical Assistant Engineer Task Management Plan Background PDF
Showcasing this set of slides titled Product Technical Assistant Engineer Task Management Plan Background PDF. The topics addressed in these templates are Securing Computer Systems, Organizing Workforce, Telecommunication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
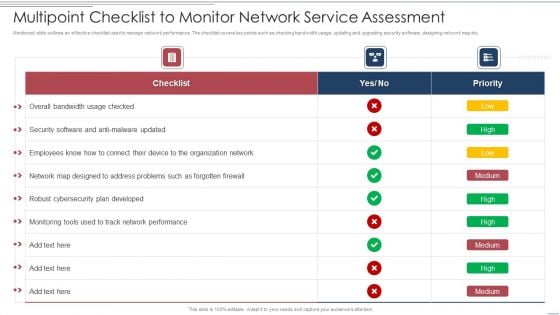
Multipoint Checklist To Monitor Network Service Assessment Structure PDF
Showcasing this set of slides titled Multipoint Checklist To Monitor Network Service Assessment Structure PDF. The topics addressed in these templates are Security, Developed, Organization Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
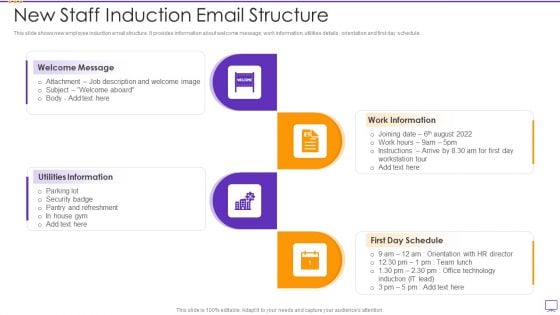
New Staff Induction Email Structure Inspiration PDF
Presenting New Staff Induction Email Structure Inspiration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Utilities Information, Work Information, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
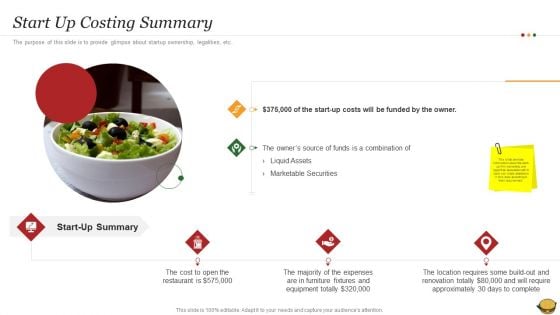
Hamburger Commerce Company Analysis Start Up Costing Summary Introduction PDF
The purpose of this slide is to provide glimpse about startup ownership, legalities, etc.Deliver an awe inspiring pitch with this creative Hamburger Commerce Company Analysis Start Up Costing Summary Introduction PDF bundle. Topics like Marketable Securities, Liquid Assets, Equipment Totally can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
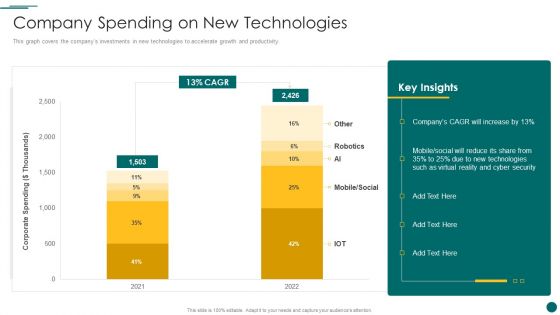
Organization Reinvention Company Spending On New Technologies Microsoft PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Reinvention Company Spending On New Technologies Microsoft PDF bundle. Topics like Social, Technologies, Cyber Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Andcryptography With Quantum Computing Ppt Pictures Backgrounds PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Andcryptography With Quantum Computing Ppt Pictures Backgrounds PDF. Use them to share invaluable insights on Cyber Security, Globally, Measurement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
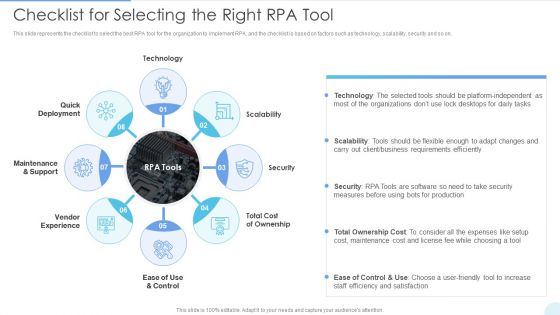
Checklist For Selecting The Right RPA Tool Brochure PDF
Presenting Checklist For Selecting The Right RPA Tool Brochure PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Technology, Scalability, Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
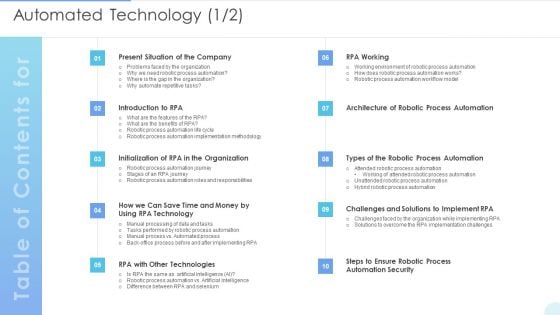
Table Of Contents Automated Technology Diagrams PDF
Deliver an awe inspiring pitch with this creative Table Of Contents Automated Technology Diagrams PDF bundle. Topics like Robotic Process Automation, Automation Security, Technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
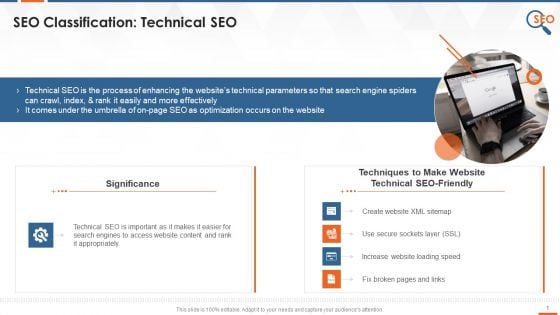
Significance Of Technical SEO And Techniques Training Ppt
This slide provides information regarding technical SEO along with its significance. It also provides information regarding multiple techniques to make a website technical SEO-friendly, such as creating a website XML sitemap, using a secure sockets layer SSL, increasing website loading speed, etc.

Real Estate Construction And Engineering Company Profile Table Of Contents Topics PDF
Deliver an awe inspiring pitch with this creative Real Estate Construction And Engineering Company Profile Table Of Contents Topics PDF bundle. Topics like Line Expansion, Security Consulting, Sourcing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
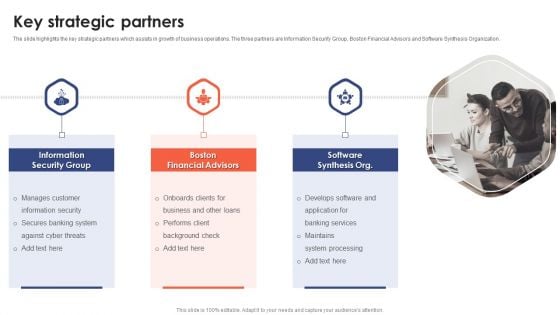
Banking Institution Company Profile Key Strategic Partners Structure PDF
Presenting Banking Institution Company Profile Key Strategic Partners Structure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Manages Customer, Information Security, Onboards Clients. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Important Certifications For IT Professionals Summary PDF
Presenting Table Of Contents Important Certifications For IT Professionals Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Certified Information, Security Professional. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents For IT Threats Response Playbook Clipart PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For IT Threats Response Playbook Clipart PDF. Use them to share invaluable insights on Security Incidents, Figures And Statistics, Ransom Payment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Investment Scheme Declaration For Short Term Capital Goals Icons PDF
Showcasing this set of slides titled Investment Scheme Declaration For Short Term Capital Goals Icons PDF. The topics addressed in these templates are Investment Characteristics, Cash Equivalent, Government Securities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
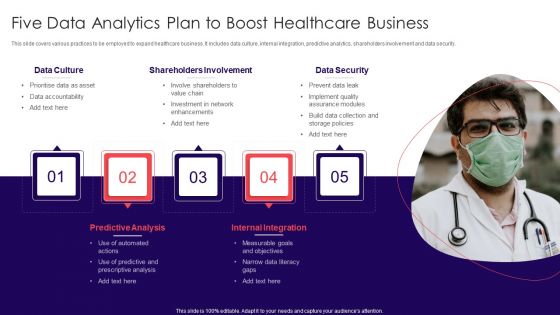
Five Data Analytics Plan To Boost Healthcare Business Formats PDF
Showcasing this set of slides titled Five Data Analytics Plan To Boost Healthcare Business Formats PDF. The topics addressed in these templates are Shareholders Involvement, Data Security, Data Culture. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
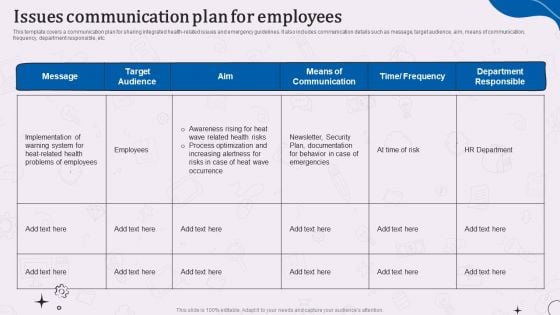
Types Of Corporate Communication Techniques Issues Communication Plan For Employees Microsoft PDF
Deliver and pitch your topic in the best possible manner with this Types Of Corporate Communication Techniques Issues Communication Plan For Employees Microsoft PDF. Use them to share invaluable insights on Implementation, Target Audience, Security Plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
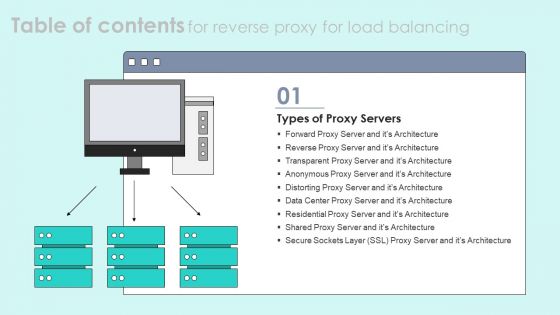
Table Of Contents For Reverse Proxy For Load Balancing Slide Sample PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Reverse Proxy For Load Balancing Slide Sample PDF bundle. Topics like Security Measure, Reverse Proxies Hide Existence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
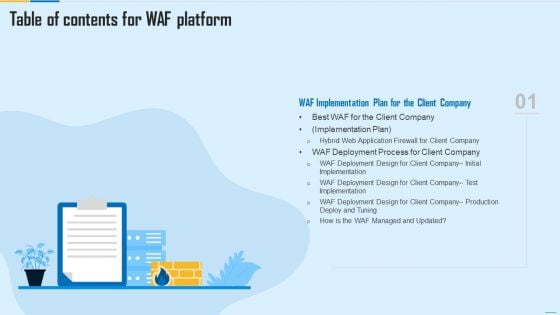
Table Of Contents For WAF Platform Plan Guidelines PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For WAF Platform Plan Guidelines PDF bundle. Topics like Web Application Firewall, Centralized Management System, Firewall Security Models can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Vendor Management To Handle Purchase Vendor Risk Management And Audit Checklist Clipart PDF
Deliver and pitch your topic in the best possible manner with this Vendor Management To Handle Purchase Vendor Risk Management And Audit Checklist Clipart PDF. Use them to share invaluable insights on Lawsuits Termination, Renewal Requirements, Proper Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Cyber Intelligent Computing System Infographics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Cyber Intelligent Computing System Infographics PDF bundle. Topics like Systems Development, Systems Implementation, Security Strategy Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
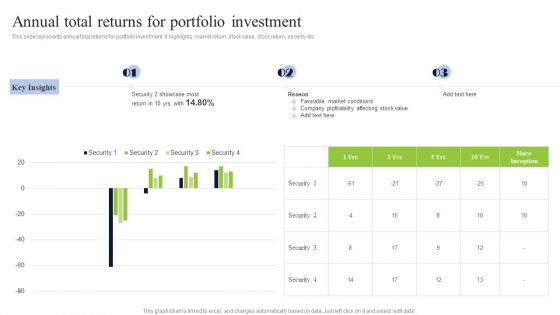
Diversified Profitable Portfolio Annual Total Returns For Portfolio Investment Graphics PDF
Deliver and pitch your topic in the best possible manner with this Diversified Profitable Portfolio Annual Total Returns For Portfolio Investment Graphics PDF. Use them to share invaluable insights on Security, Market Conditions, Company Profitability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Diversified Profitable Portfolio Conservative Allocation Portfolio Investment Management Summary PDF
Deliver an awe inspiring pitch with this creative Diversified Profitable Portfolio Conservative Allocation Portfolio Investment Management Summary PDF bundle. Topics like Investment, Low Risk, Securities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF
This slide explains the working of a reverse proxy server in two ways proxying for load balancing and proxy as a stand-in for a server which is further divided into three parts such as secure client to proxy, secure proxy to content server and secure client to proxy and secure proxy to content server. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Reverse Proxy Web Server How Does A Reverse Proxy Web Server Application Icons PDF.
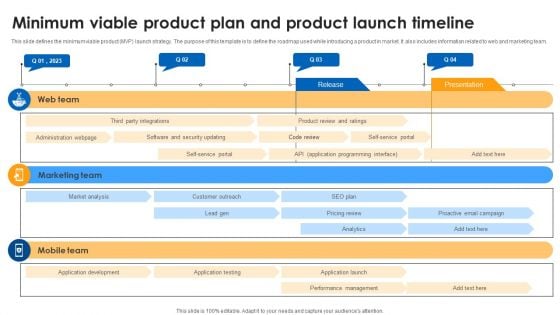
Minimum Viable Product Plan And Product Launch Timeline Diagrams PDF
Pitch your topic with ease and precision using this Minimum Viable Product Plan And Product Launch Timeline Diagrams PDF. This layout presents information on Administration Webpage, Security Updating, Customer Outreach. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Global Educative And Training Events For Skill Development Summary PDF
Showcasing this set of slides titled Global Educative And Training Events For Skill Development Summary PDF. The topics addressed in these templates are Leadership Program, Security Training, Melbourne Australia. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Data Processing Cloud Services Icon Infographics PDF
Pitch your topic with ease and precision using this Data Processing Cloud Services Icon Infographics PDF. This layout presents information on Security Compliance, Monitor Visibility, Authentication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icon For Software Architecture And Building Design Microsoft PDF
Presenting Icon For Software Architecture And Building Design Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon Software, Architecture Building Design, Communication Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
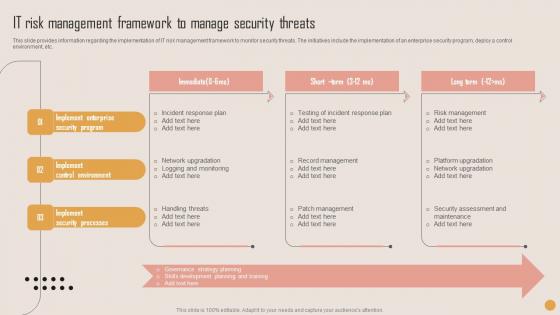
IT Risk Management Framework Playbook For Strategic Actions To Improve IT Performance Topics Pdf
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download IT Risk Management Framework Playbook For Strategic Actions To Improve IT Performance Topics Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the IT Risk Management Framework Playbook For Strategic Actions To Improve IT Performance Topics Pdf. This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc.

Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf
The purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties.
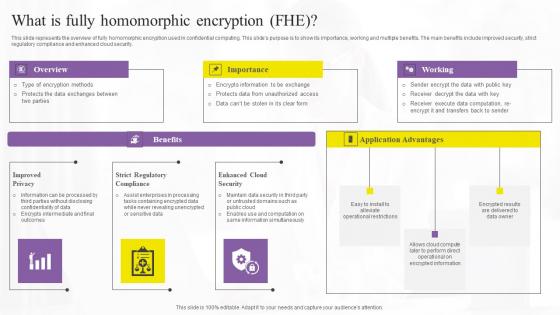
What Is Fully Homomorphic Encryption Confidential Computing Technologies Inspiration Pdf
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Whether you have daily or monthly meetings, a brilliant presentation is necessary. What Is Fully Homomorphic Encryption Confidential Computing Technologies Inspiration Pdf can be your best option for delivering a presentation. Represent everything in detail using What Is Fully Homomorphic Encryption Confidential Computing Technologies Inspiration Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security.
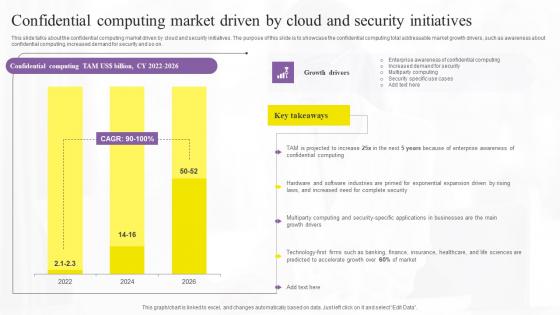
Confidential Computing Market Driven Confidential Computing Technologies Rules Pdf
This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. This modern and well-arranged Confidential Computing Market Driven Confidential Computing Technologies Rules Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on.
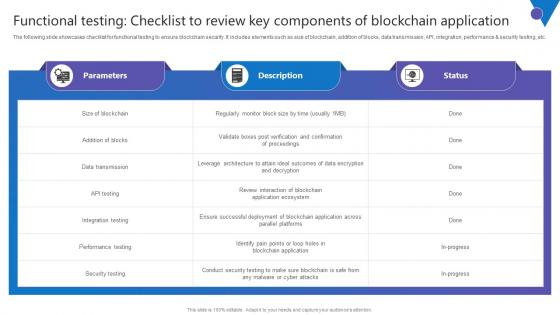
Functional Testing Checklist To Review Key Components Of Blockchain Application Topics Pdf
The following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Functional Testing Checklist To Review Key Components Of Blockchain Application Topics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Functional Testing Checklist To Review Key Components Of Blockchain Application Topics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc.
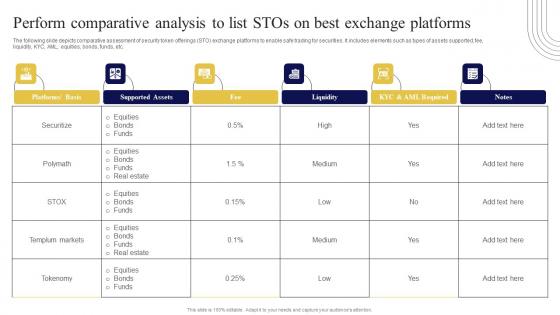
Perform Comparative Analysis To Exploring Investment Opportunities Topics Pdf
The following slide depicts comparative assessment of security token offerings STO exchange platforms to enable safe trading for securities. It includes elements such as types of assets supported, fee, liquidity, KYC, AML, equities, bonds, funds, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Perform Comparative Analysis To Exploring Investment Opportunities Topics Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Perform Comparative Analysis To Exploring Investment Opportunities Topics Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide depicts comparative assessment of security token offerings STO exchange platforms to enable safe trading for securities. It includes elements such as types of assets supported, fee, liquidity, KYC, AML, equities, bonds, funds, etc.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.

Zero Trust Model Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Find highly impressive Zero Trust Model Comparison Between Zero Trust Model SDP And VPN on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Model Comparison Between Zero Trust Model SDP And VPN for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.
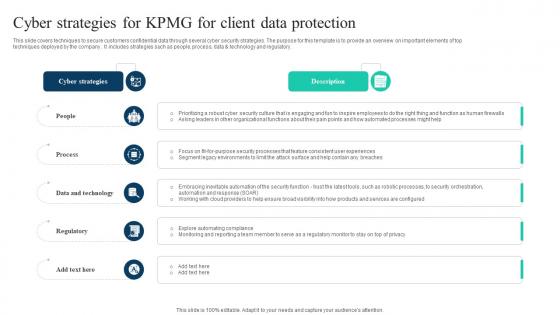
The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal The Ultimate Guide To KPMG Cyber Strategies For KPMG For Client Data Protection Strategy SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory.
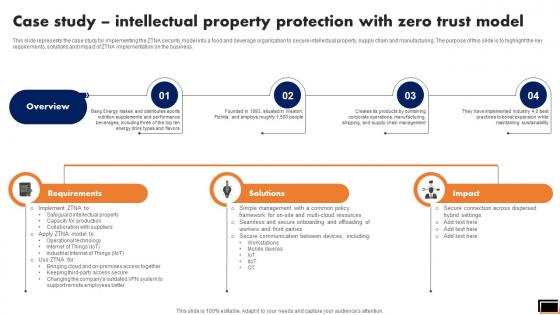
Case Study Intellectual Property Protection With Zero Trust Model Software Defined Perimeter SDP
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Want to ace your presentation in front of a live audience Our Case Study Intellectual Property Protection With Zero Trust Model Software Defined Perimeter SDP can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
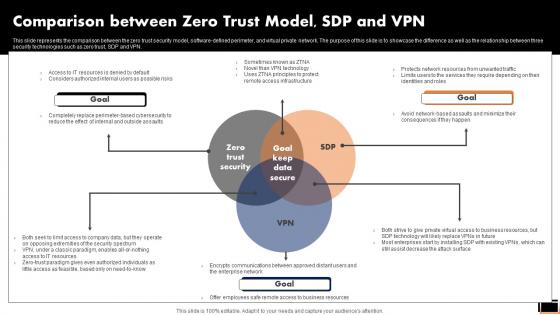
Comparison Between Zero Trust ModelSDP And Vpn Software Defined Perimeter SDP
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Present like a pro with Comparative Assessment Of Ztna Version 1 0 And 2 0 Software Defined Perimeter SDP. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.
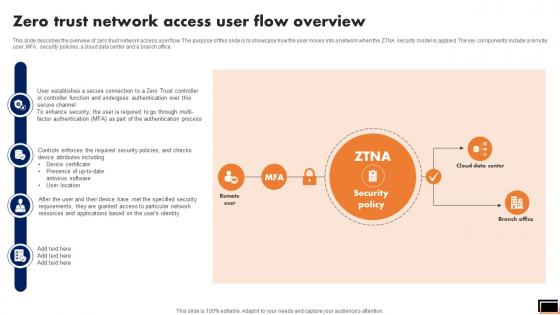
Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Network Access User Flow Overview Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
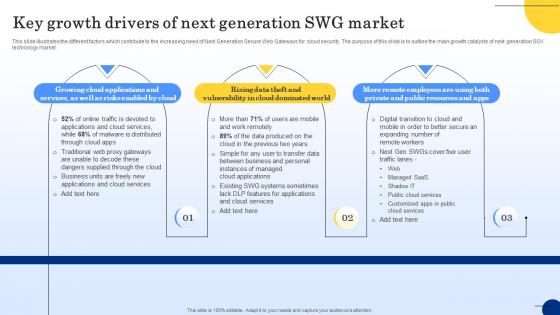
Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Explore a selection of the finest Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.
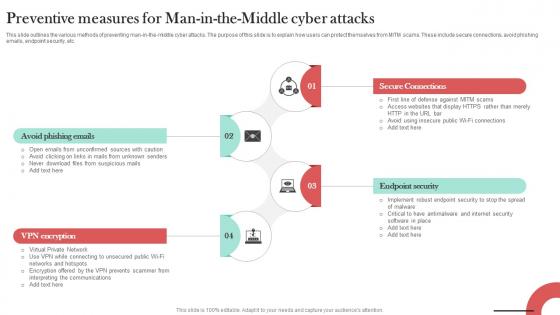
Preventive Measures For Man In The Middle Man In The Middle Phishing IT
This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Get a simple yet stunning designed Preventive Measures For Man In The Middle Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Preventive Measures For Man In The Middle Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc.
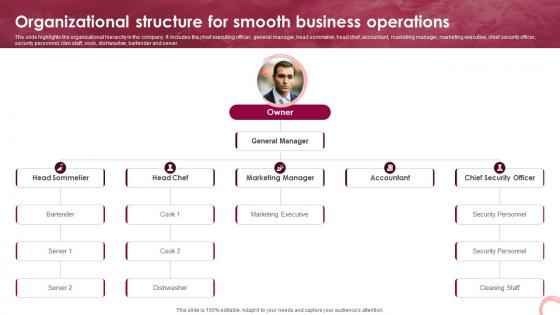
Wine Lounge Business Plan Organizational Structure For Smooth Business Operations BP SS V
The slide highlights the organizational hierarchy in the company. It includes the chief executing officer, general manager, head sommelier, head chef, accountant, marketing manager, marketing executive, chief security officer, security personnel, clen staff, cook, dishwasher, bartender and server. Are you searching for a Wine Lounge Business Plan Organizational Structure For Smooth Business Operations BP SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wine Lounge Business Plan Organizational Structure For Smooth Business Operations BP SS V from Slidegeeks today. The slide highlights the organizational hierarchy in the company. It includes the chief executing officer, general manager, head sommelier, head chef, accountant, marketing manager, marketing executive, chief security officer, security personnel, clen staff, cook, dishwasher, bartender and server.

Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN
This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN. Welcome to our selection of the Zero Trust Network Access Comparison Between Zero Trust Model SDP And VPN. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide represents the comparison between the zero trust security model, software-defined perimeter, and virtual private network. The purpose of this slide is to showcase the difference as well as the relationship between three security technologies such as zero trust, SDP and VPN.

Zero Trust Network Access Roadmap To Implement Zero Trust Network Access Model

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.


 Continue with Email
Continue with Email

 Home
Home


































