Lock
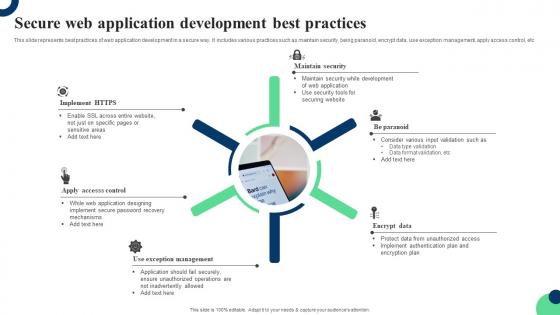
Secure Web Application Development Best Practices Ppt Inspiration Outline Pdf
This slide represents best practices of web application development in a secure way. It includes various practices such as maintain security, being paranoid, encrypt data, use exception management, apply access control, etc. Showcasing this set of slides titled Secure Web Application Development Best Practices Ppt Inspiration Outline Pdf. The topics addressed in these templates are Being Paranoid, Encrypt Data, Use Exception Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents best practices of web application development in a secure way. It includes various practices such as maintain security, being paranoid, encrypt data, use exception management, apply access control, etc.
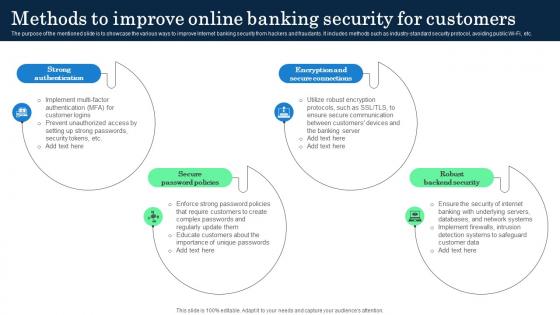
Methods To Improve Online Banking Security Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Do you know about Slidesgeeks Methods To Improve Online Banking Security Incorporating Banking Operational Growth These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc.

Main Goals Of Application Level Encryption Application Security Testing
This slide showcases the objectives of application-level encryption in application security which include data protection, increased security, etc. Retrieve professionally designed Main Goals Of Application Level Encryption Application Security Testing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases the objectives of application-level encryption in application security which include data protection, increased security, etc.

Overview Of Platform Tokenization In Data Security PPT Sample
This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc. Find a pre-designed and impeccable Overview Of Platform Tokenization In Data Security PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the introduction of first type tokenization in data security. The purpose of this slide is to highlight the overview of platform tokenization and how they gain security, transactional capacity, etc.
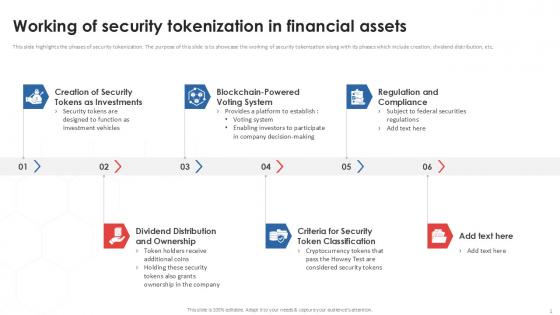
Working Of Security Tokenization In Financial Assets PPT Powerpoint
This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Find a pre-designed and impeccable Working Of Security Tokenization In Financial Assets PPT Powerpoint. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc.
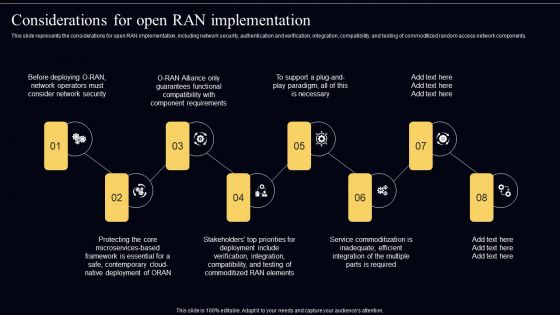
Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Boost your pitch with our creative Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc. Take your projects to the next level with our ultimate collection of Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc.
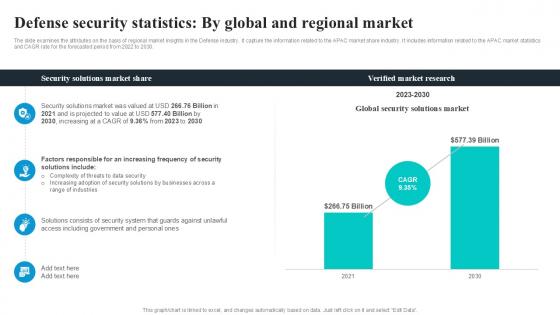
Defense Security Statistics By Global Security Industry PPT Sample IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates.Defense Security Statistics By Global Security Industry PPT Sample IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030.

Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example
This slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics. Want to ace your presentation in front of a live audience Our Before Vs After Implementing Tokenization In Data Security Securing Your Data Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide showcases the comparative analysis of the before versus after tokenization. The purpose of this slide is to showcase the different performance metrics and how tokenization has improved these metrics.

Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation
This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Data Security Benefits Of Adopting Tokenization Securing Your Data Ppt Presentation and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the cons of tokenization. The purpose of this slide is to showcase the advantages of tokenization such as utilizing less resources, decreases risk, stimulates innovation, etc.

Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. The Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc.
Employee Incentives Icon For Healthcare And Financial Security Designs Pdf
Showcasing this set of slides titled Employee Incentives Icon For Healthcare And Financial Security Designs Pdf The topics addressed in these templates are Employee Incentives, Icon For Healthcare, Financial Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Employee Incentives Icon For Healthcare And Financial Security Designs Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Internet Of Things Security Icon For Home Safety Background Pdf
Pitch your topic with ease and precision using this Internet Of Things Security Icon For Home Safety Background Pdf This layout presents information on Internet Of Things Security, Icon For Home Safety It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Internet Of Things Security Icon For Home Safety Background Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Internet Of Things Security Icon For Software Management Template Pdf
Showcasing this set of slides titled Internet Of Things Security Icon For Software Management Template Pdf The topics addressed in these templates are Internet Of Things Security, Icon For Software, Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Internet Of Things Security Icon For Software Management Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf
Pitch your topic with ease and precision using this Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Distributed Ledger Security Protocol List Icon Structure Pdf
Pitch your topic with ease and precision using this Distributed Ledger Security Protocol List Icon Structure Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Distributed Ledger Security Protocol List Icon Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf
Showcasing this set of slides titled Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf The topics addressed in these templates are Ecommerce Payment Security, Distributed Ledger, Technology Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Secured Childcare Market Strategic Assessment Icon Topics Pdf
Pitch your topic with ease and precision using this Secured Childcare Market Strategic Assessment Icon Topics Pdf This layout presents information on Secured Childcare, Market Strategic, Assessment Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Secured Childcare Market Strategic Assessment Icon Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf This layout presents information on Cyber Security Breach, Icon Corrupting Devices Files It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf
Showcasing this set of slides titled Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf The topics addressed in these templates are Cyber Security Breach, Icon Sending Malicious Emails All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
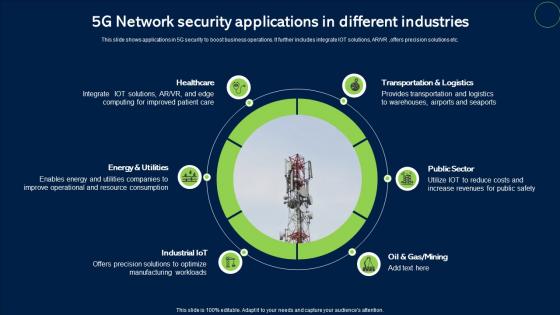
5G Network Security Applications In Different Industries Infographics Pdf
This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc. Showcasing this set of slides titled 5G Network Security Applications In Different Industries Infographics Pdf. The topics addressed in these templates are Healthcare, Public Sector, Transportation And Logistics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows applications in 5G security to boost business operations. It further includes integrate IOT solutions, ARVR ,offers precision solutions etc.
5G Network Security Icon For Device Safety Sample Pdf
Pitch your topic with ease and precision using this 5G Network Security Icon For Device Safety Sample Pdf. This layout presents information on 5G Network Security, Device Safety. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our 5G Network Security Icon For Device Safety Sample Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Security Challenges And Solutions In Banking Industry Download Pdf
This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.Showcasing this set of slides titled Internet Security Challenges And Solutions In Banking Industry Download Pdf The topics addressed in these templates are Installing Intergraded, Introducing Firewall, Learning Algorisms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security challenges in digital banking and tactics to mitigate data risk. It include challenges like malware, spoofing, phishing, third part service.
Security System In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security System In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security System that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security System In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Wireless In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Wireless In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Wireless that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Wireless In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Application Security Program In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Application Security Program In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Application Security Program that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Application Security Program In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Wifi Systems Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Wifi Systems Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Wifi Systems Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Wifi Systems Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Computer Personal Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Computer Personal Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Personal Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Computer Personal Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
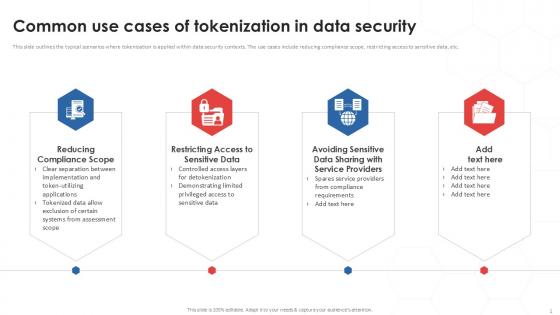
Common Use Cases Of Tokenization In Data Security PPT Template
This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc. Find a pre-designed and impeccable Common Use Cases Of Tokenization In Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the typical scenarios where tokenization is applied within data security contexts. The use cases include reducing compliance scope, restricting access to sensitive data, etc.
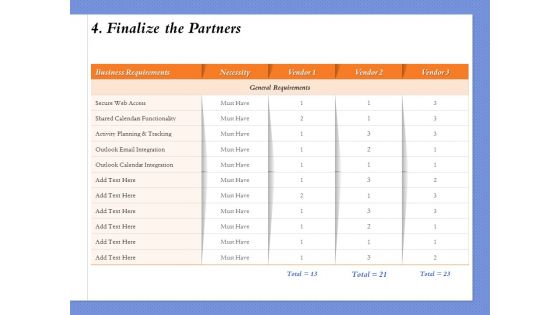
Selecting The Right Channel Strategy 4 Finalize The Partners Ppt PowerPoint Presentation Model Graphic Tips PDF
Presenting this set of slides with name selecting the right channel strategy 4 finalize the partners ppt powerpoint presentation model graphic tips pdf. The topics discussed in these slides are business requirements, necessity, vendor, secure web access, activity planning and tracking. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
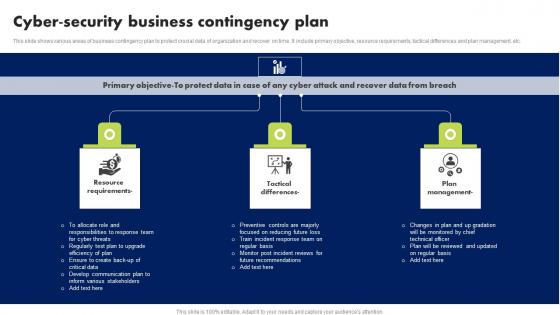
Cyber Security Business Contingency Plan Brochure Pdf
This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc. Showcasing this set of slides titled Cyber Security Business Contingency Plan Brochure Pdf. The topics addressed in these templates are Resource Requirements, Tactical Differences, Plan Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc.

Main Data Security Tokenization Techniques PPT Powerpoint
This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc. Boost your pitch with our creative Main Data Security Tokenization Techniques PPT Powerpoint. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the various categories of tokenization. The purpose of this slide is to showcase the types of tokenization such as platform, utility, governance, non-fungible, etc.
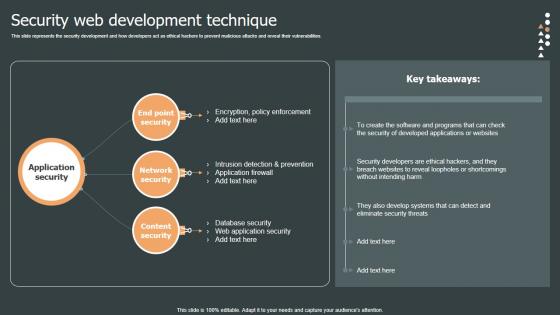
Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today. This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.
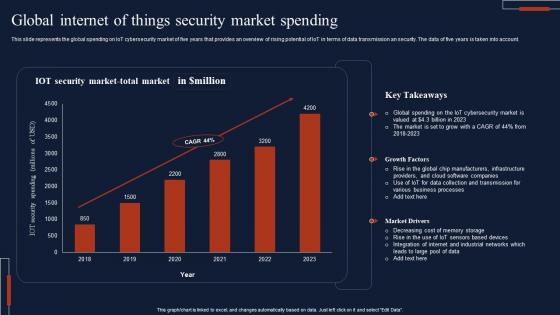
Global Internet Of Things Security Market Spending Download Pdf
This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account. Pitch your topic with ease and precision using this Global Internet Of Things Security Market Spending Download Pdf This layout presents information on IOT Security, Market Total, Key Takeaways It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account.
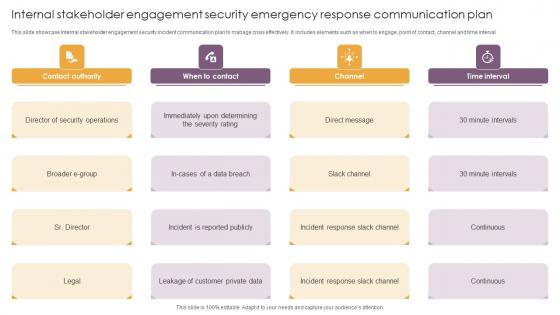
Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf
This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval Showcasing this set of slides titled Internal Stakeholder Engagement Security Emergency Response Communication Plan Introduction Pdf The topics addressed in these templates are Contact Authority, Time Interval, Director Of Security Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase Internal stakeholder engagement security incident communication plan to manage crisis effectively. It includes elements such as when to engage, point of contact, channel and time interval
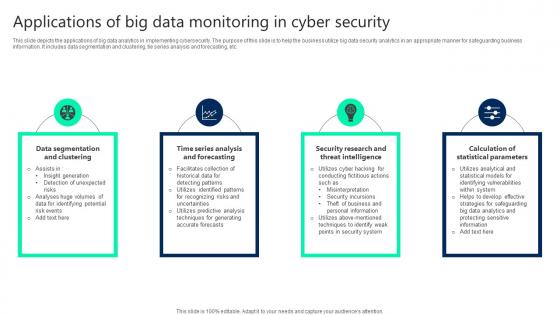
Applications Of Big Data Monitoring In Cyber Security Themes pdf
This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc. Pitch your topic with ease and precision using this Applications Of Big Data Monitoring In Cyber Security Themes pdf. This layout presents information on Data Segmentation, Security Research, Threat Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc.
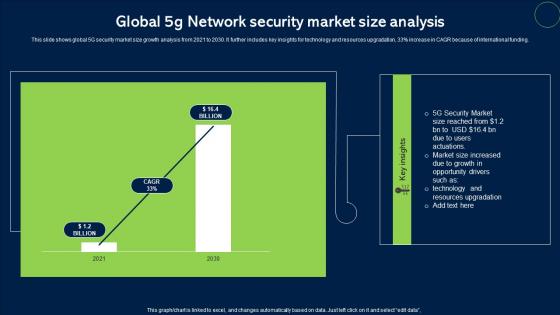
Global 5G Network Security Market Size Analysis Topics Pdf
This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding. Pitch your topic with ease and precision using this Global 5G Network Security Market Size Analysis Topics Pdf. This layout presents information on Network Security, Market Size. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding.
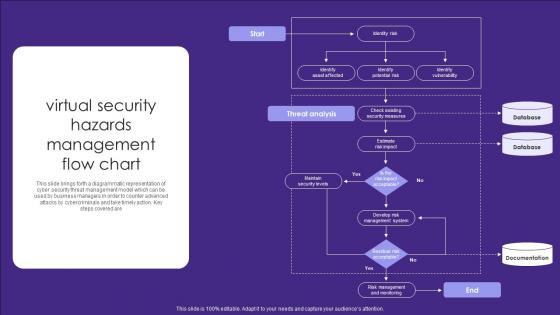
Virtual Security Hazards Management Flow Chart Infographics Pdf
This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Showcasing this set of slides titled Virtual Security Hazards Management Flow Chart Infographics Pdf. The topics addressed in these templates are Security Measures, Database, Documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are
Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard
This slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc. Get a simple yet stunning designed Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Web Access Control Solution Secure Web Gateway Performance Tracking Dashboard can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web isolations, etc.
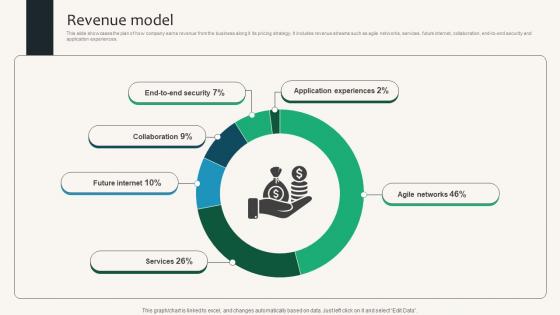
Revenue Model Security Service Provider Business Model BMC SS V
This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences. Find highly impressive Revenue Model Security Service Provider Business Model BMC SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Revenue Model Security Service Provider Business Model BMC SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences.

Compound Annual Growth Rate CAGR Of Application Security Testing
This slide depicts the market growth of application security by software tools such as white-box testing, black-box testing, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Compound Annual Growth Rate CAGR Of Application Security Testing template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Compound Annual Growth Rate CAGR Of Application Security Testing that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide depicts the market growth of application security by software tools such as white-box testing, black-box testing, etc.
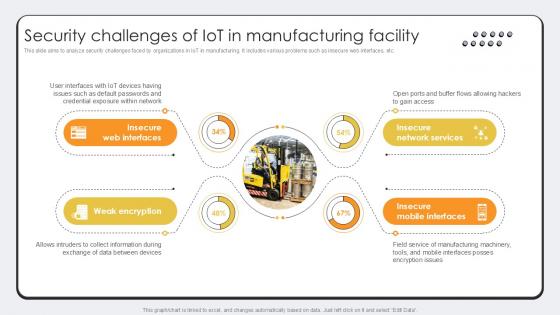
Security Challenges Of IoT In Revolutionizing Production IoT Ppt Example
This slide aims to analyze security challenges faced by organizations in IoT in manufacturing. It includes various problems such as insecure web interfaces, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Security Challenges Of IoT In Revolutionizing Production IoT Ppt Example to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Security Challenges Of IoT In Revolutionizing Production IoT Ppt Example. This slide aims to analyze security challenges faced by organizations in IoT in manufacturing. It includes various problems such as insecure web interfaces, etc.
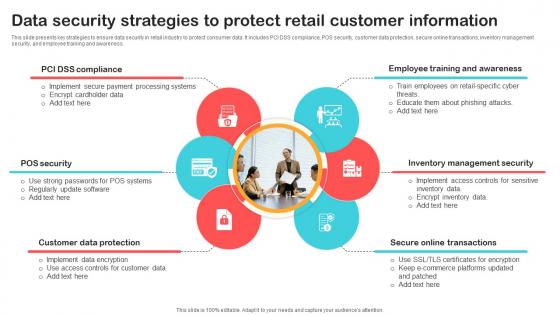
Data Security Strategies To Protect Retail Customer Optimizing Retail Operations With Digital DT SS V
This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Security Strategies To Protect Retail Customer Optimizing Retail Operations With Digital DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness.
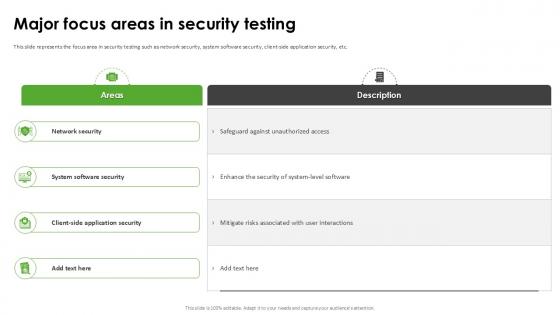
Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example
This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Focus Areas In Security Testing Harnessing The World Of Ethical Ppt Example to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc.
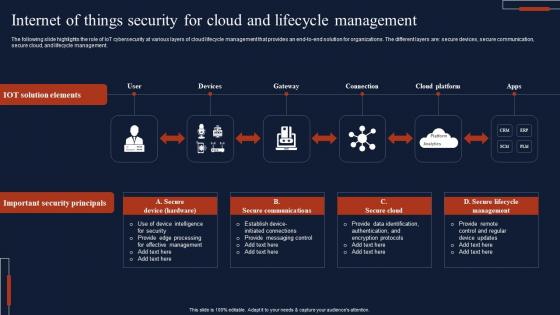
Internet Of Things Security For Cloud And Lifecycle Management Slides Pdf
The following slide highlights the role of IoT cybersecurity at various layers of cloud lifecycle management that provides an end-to-end solution for organizations. The different layers are secure devices, secure communication, secure cloud, and lifecycle management. Showcasing this set of slides titled Internet Of Things Security For Cloud And Lifecycle Management Slides Pdf The topics addressed in these templates are Important Security Principals, Secure Communications All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights the role of IoT cybersecurity at various layers of cloud lifecycle management that provides an end-to-end solution for organizations. The different layers are secure devices, secure communication, secure cloud, and lifecycle management.
Icons Slide For Data Security In Cloud Computing Ppt Presentation
Download our innovative and attention grabbing Icons Slide For Data Security In Cloud Computing Ppt Presentation template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Data Security In Cloud Computing Ppt Presentation are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
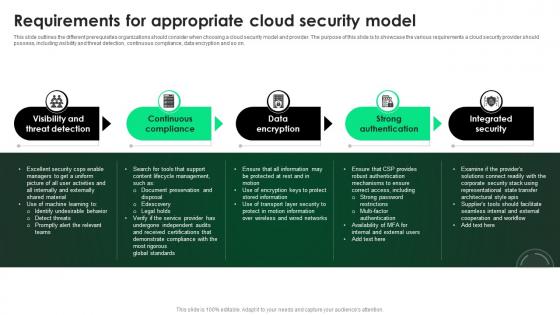
CASB 2 0 IT Requirements For Appropriate Cloud Security Model
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Find highly impressive CASB 2 0 IT Requirements For Appropriate Cloud Security Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CASB 2 0 IT Requirements For Appropriate Cloud Security Model for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on.

Devsecops Development Security And Operations Role Of Devsecops Ppt Template
This slide discusses the working process of development, security and operations in DevSecOps. The purpose of this slide is to highlight the process followed by DevSecOps for providing, monitoring and managing security at each level of the software system. Find highly impressive Devsecops Development Security And Operations Role Of Devsecops Ppt Template on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Devsecops Development Security And Operations Role Of Devsecops Ppt Template for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide discusses the working process of development, security and operations in DevSecOps. The purpose of this slide is to highlight the process followed by DevSecOps for providing, monitoring and managing security at each level of the software system.

Building Trust With IoT Security Case Study 2 Improving Connected Home Security With Aws IoT SS V
This slide exhibits case study showcasing how AWS solutions helps consumer product company in enhancing connected home products security. It includes elements such as business goals, challenges, IoT solutions, and results. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Building Trust With IoT Security Case Study 2 Improving Connected Home Security With Aws IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Building Trust With IoT Security Case Study 2 Improving Connected Home Security With Aws IoT SS V today and make your presentation stand out from the rest This slide exhibits case study showcasing how AWS solutions helps consumer product company in enhancing connected home products security. It includes elements such as business goals, challenges, IoT solutions, and results.
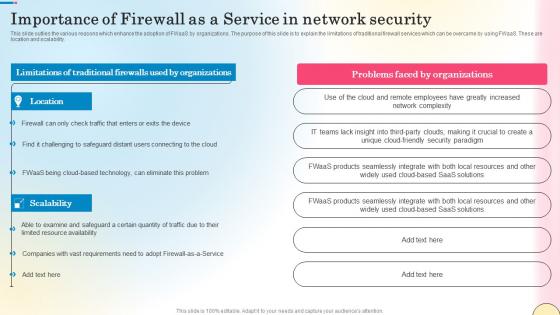
Importance Of Firewall As A Service In Network Security Network Security Designs Pdf
This slide outlies the various reasons which enhance the adoption of FWaaS by organizations. The purpose of this slide is to explain the limitations of traditional firewall services which can be overcame by using FWaaS. These are location and scalability. The Importance Of Firewall As A Service In Network Security Network Security Designs Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlies the various reasons which enhance the adoption of FWaaS by organizations. The purpose of this slide is to explain the limitations of traditional firewall services which can be overcame by using FWaaS. These are location and scalability.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.
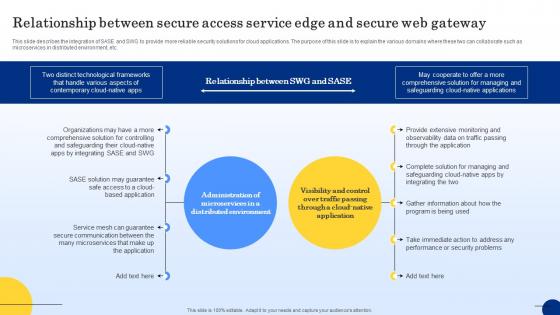
Relationship Between Secure Access Service Edge Web Threat Protection System
This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Presenting this PowerPoint presentation, titled Relationship Between Secure Access Service Edge Web Threat Protection System, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Relationship Between Secure Access Service Edge Web Threat Protection System. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Relationship Between Secure Access Service Edge Web Threat Protection System that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc.
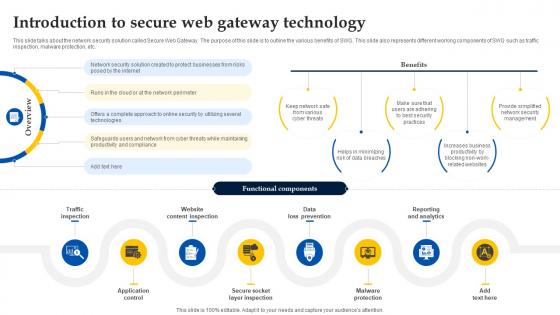
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
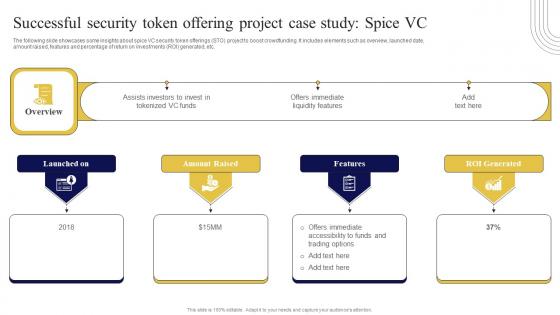
Successful Security Token Offering Project Exploring Investment Opportunities Professional Pdf
The following slide showcases some insights about spice VC security token offerings STO project to boost crowdfunding. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc. Take your projects to the next level with our ultimate collection of Successful Security Token Offering Project Exploring Investment Opportunities Professional Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The following slide showcases some insights about spice VC security token offerings STO project to boost crowdfunding. It includes elements such as overview, launched date, amount raised, features and percentage of return on investments ROI generated, etc.
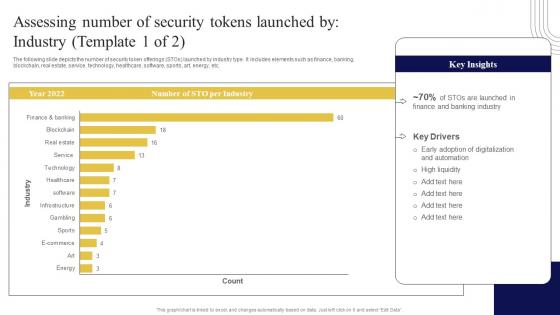
Assessing Number Of Security Tokens Exploring Investment Opportunities Introduction Pdf
The following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Want to ace your presentation in front of a live audience Our Assessing Number Of Security Tokens Exploring Investment Opportunities Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc.
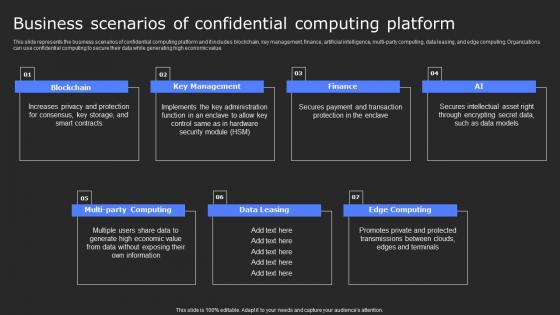
Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. There are so many reasons you need a Business Scenarios Of Confidential Computing Secure Computing Framework Information Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value.
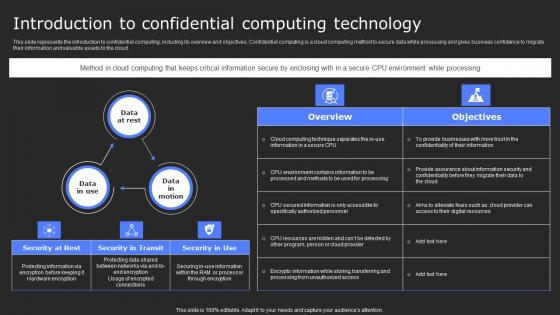
Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf
This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Boost your pitch with our creative Introduction To Confidential Computing Technology Secure Computing Framework Elements Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud.

About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Slidegeeks is here to make your presentations a breeze with About Cryptography Overview Cloud Data Security Using Cryptography Designs Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc.
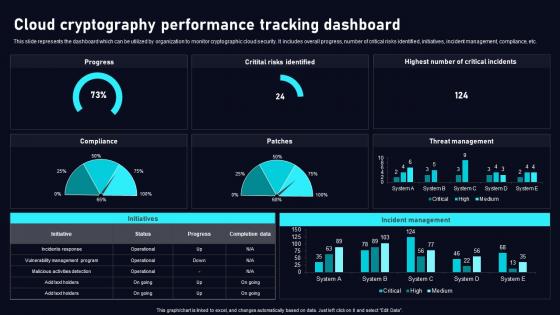
Cloud Cryptography Performance Cloud Data Security Using Cryptography Sample Pdf
This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Cryptography Performance Cloud Data Security Using Cryptography Sample Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc.


 Continue with Email
Continue with Email

 Home
Home


































