Lock
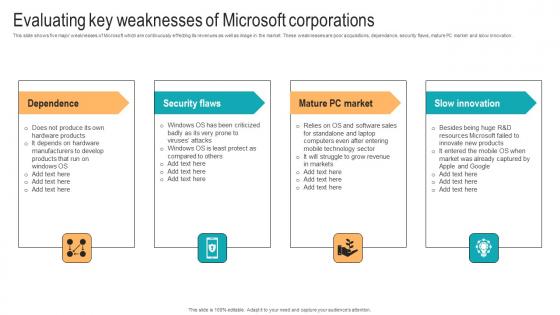
Evaluating Key Weaknesses Of Microsoft Strategic Advancements By Microsofts Microsoft Pdf
This slide shows five major weaknesses of Microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation. If you are looking for a format to display your unique thoughts, then the professionally designed Evaluating Key Weaknesses Of Microsoft Strategic Advancements By Microsofts Microsoft Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Evaluating Key Weaknesses Of Microsoft Strategic Advancements By Microsofts Microsoft Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide shows five major weaknesses of Microsoft which are continuously effecting its revenues as well as image in the market. These weaknesses are poor acquisitions, dependance, security flaws, mature PC market and slow innovation.

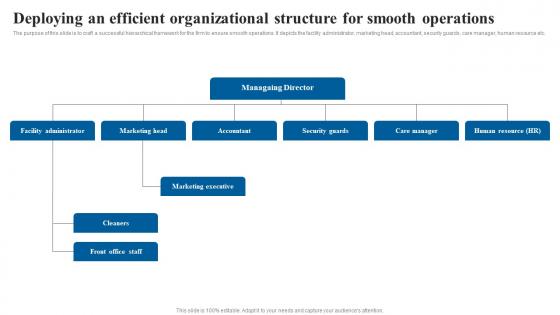
Deploying An Efficient Organizational Structure In Home Care Business Plan Brochure Pdf
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying An Efficient Organizational Structure In Home Care Business Plan Brochure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying An Efficient Organizational Structure In Home Care Business Plan Brochure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc.
Deploying An Efficient Organizational Elderly Care Business Plan Go To Market Strategy Background Pdf
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying An Efficient Organizational Elderly Care Business Plan Go To Market Strategy Background Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying An Efficient Organizational Elderly Care Business Plan Go To Market Strategy Background Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc.
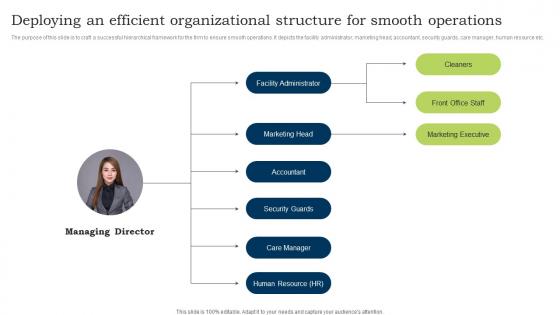
Go To Market Strategy Deploying An Efficient Organizational Structure For Smooth Clipart Pdf
The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Go To Market Strategy Deploying An Efficient Organizational Structure For Smooth Clipart Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Go To Market Strategy Deploying An Efficient Organizational Structure For Smooth Clipart Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. The purpose of this slide is to craft a successful hierarchical framework for the firm to ensure smooth operations. It depicts the facility administrator, marketing head, accountant, security guards, care manager, human resource etc.
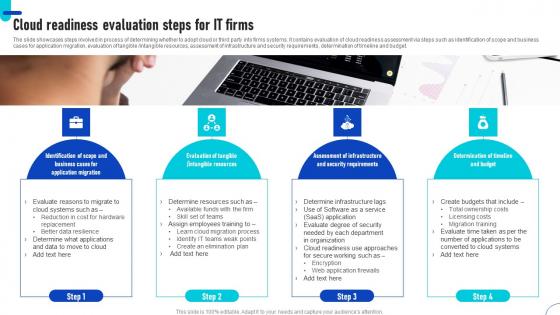
Cloud Readiness Evaluation Steps For IT Firms Ppt Outline Files Pdf
The slide showcases steps involved in process of determining whether to adopt cloud or third party into firms systems. It contains evaluation of cloud readiness assessment via steps such as identification of scope and business cases for application migration, evaluation of tangible intangible resources, assessment of infrastructure and security requirements, determination of timeline and budget. Pitch your topic with ease and precision using this Cloud Readiness Evaluation Steps For IT Firms Ppt Outline Files Pdf. This layout presents information on Determine Resources, Assign Employees Training, Determine Applications. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide showcases steps involved in process of determining whether to adopt cloud or third party into firms systems. It contains evaluation of cloud readiness assessment via steps such as identification of scope and business cases for application migration, evaluation of tangible intangible resources, assessment of infrastructure and security requirements, determination of timeline and budget.
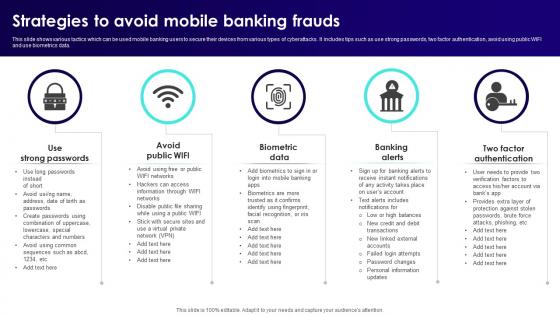
Wireless Banking To Improve Strategies To Avoid Mobile Banking Frauds Fin SS V
This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data. Welcome to our selection of the Wireless Banking To Improve Strategies To Avoid Mobile Banking Frauds Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide shows various tactics which can be used mobile banking users to secure their devices from various types of cyberattacks. It includes tips such as use strong passwords, two factor authentication, avoid using public WIFI and use biometrics data.

Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Are you searching for a Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V from Slidegeeks today. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.

Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V
This slide provides an overview of the blockchain technology used for remote monotiling. It also includes the benefits that are it allows device communication, enhance security and provides authorization access. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V today and make your presentation stand out from the rest This slide provides an overview of the blockchain technology used for remote monotiling. It also includes the benefits that are it allows device communication, enhance security and provides authorization access.
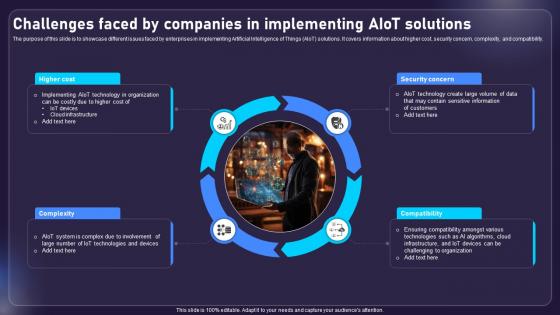
Challenges Faced By Companies In Implementing AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility. Find highly impressive Challenges Faced By Companies In Implementing AIOT Applications For Various Industries IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Challenges Faced By Companies In Implementing AIOT Applications For Various Industries IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility.
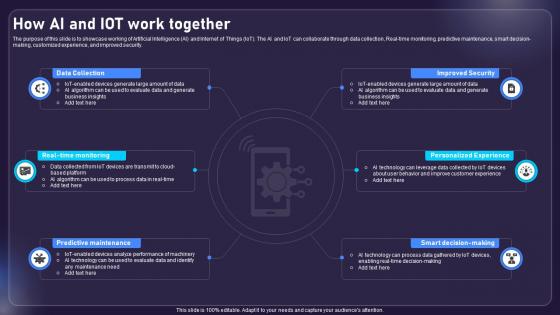
How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security. This How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security.
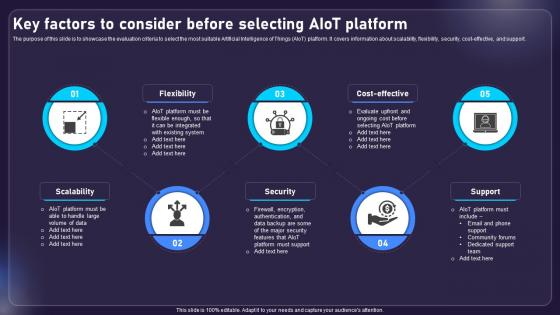
Key Factors To Consider Before Selecting AIOT Platform AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase the evaluation criteria to select the most suitable Artificial Intelligence of Things AIoT platform. It covers information about scalability, flexibility, security, cost-effective, and support. Are you searching for a Key Factors To Consider Before Selecting AIOT Platform AIOT Applications For Various Industries IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Factors To Consider Before Selecting AIOT Platform AIOT Applications For Various Industries IoT SS V from Slidegeeks today. The purpose of this slide is to showcase the evaluation criteria to select the most suitable Artificial Intelligence of Things AIoT platform. It covers information about scalability, flexibility, security, cost-effective, and support.

Overview And Key Benefits Of AIOT In Smart Homes AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase brief introduction to Artificial Intelligence of Things AIoT in smart homes. The slide covers information about major advantages and use cases of smart homes such as smart lighting, home security, and health and wellness. Want to ace your presentation in front of a live audience Our Overview And Key Benefits Of AIOT In Smart Homes AIOT Applications For Various Industries IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The purpose of this slide is to showcase brief introduction to Artificial Intelligence of Things AIoT in smart homes. The slide covers information about major advantages and use cases of smart homes such as smart lighting, home security, and health and wellness.
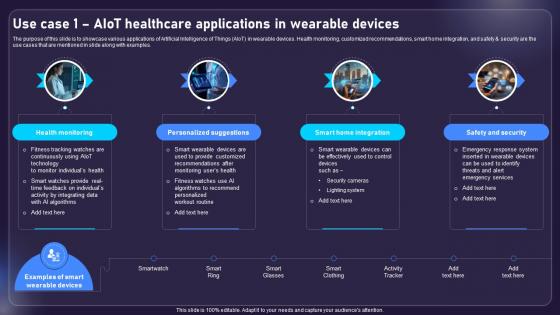
Use Case 1 AIOT Healthcare Applications In Wearable Devices AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase various applications of Artificial Intelligence of Things AIoT in wearable devices. Health monitoring, customized recommendations, smart home integration, and safety and security are the use cases that are mentioned in slide along with examples. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Use Case 1 AIOT Healthcare Applications In Wearable Devices AIOT Applications For Various Industries IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The purpose of this slide is to showcase various applications of Artificial Intelligence of Things AIoT in wearable devices. Health monitoring, customized recommendations, smart home integration, and safety and security are the use cases that are mentioned in slide along with examples.

Major Challenges Of IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V
Following slide showcases issues faced by educational institutions during implementation of intent of things IoT technologies. It includes challenges such as high cost infrastructure, security challenges and complexity. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Major Challenges Of IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Major Challenges Of IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V. Following slide showcases issues faced by educational institutions during implementation of intent of things IoT technologies. It includes challenges such as high cost infrastructure, security challenges and complexity.
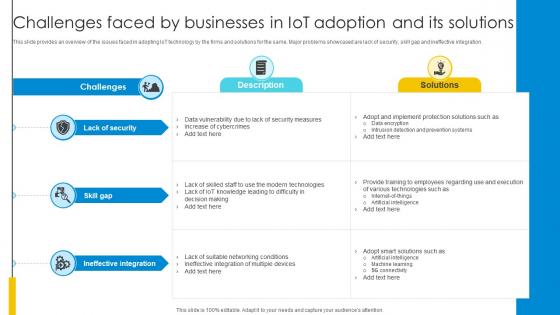
Challenges Faced By Businesses In IoT Adoption And Its Solutions Optimizing Inventory Management IoT SS V
This slide provides an overview of the issues faced in adopting IoT technology by the firms and solutions for the same. Major problems showcased are lack of security, skill gap and ineffective integration. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Challenges Faced By Businesses In IoT Adoption And Its Solutions Optimizing Inventory Management IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Challenges Faced By Businesses In IoT Adoption And Its Solutions Optimizing Inventory Management IoT SS V. This slide provides an overview of the issues faced in adopting IoT technology by the firms and solutions for the same. Major problems showcased are lack of security, skill gap and ineffective integration.
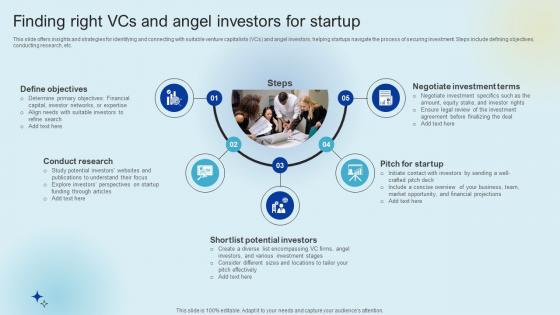
Finding Right VCS And Angel Investors For Startup Raising Venture Capital A Holistic Approach Fin SS V
This slide offers insights and strategies for identifying and connecting with suitable venture capitalists VCs and angel investors, helping startups navigate the process of securing investment. Steps include defining objectives, conducting research, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Finding Right VCS And Angel Investors For Startup Raising Venture Capital A Holistic Approach Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Finding Right VCS And Angel Investors For Startup Raising Venture Capital A Holistic Approach Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide offers insights and strategies for identifying and connecting with suitable venture capitalists VCs and angel investors, helping startups navigate the process of securing investment. Steps include defining objectives, conducting research, etc.

Terms And Clauses In Venture Capital Deal Investor Raising Venture Capital A Holistic Approach Fin SS V
This section discusses the provisions in venture capital deals that are designed to protect the interests and investments of venture capitalists, ensuring a level of security for their capital. The rights of investors include anti-dilution rights, preemptive rights, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Terms And Clauses In Venture Capital Deal Investor Raising Venture Capital A Holistic Approach Fin SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Terms And Clauses In Venture Capital Deal Investor Raising Venture Capital A Holistic Approach Fin SS V This section discusses the provisions in venture capital deals that are designed to protect the interests and investments of venture capitalists, ensuring a level of security for their capital. The rights of investors include anti-dilution rights, preemptive rights, etc.
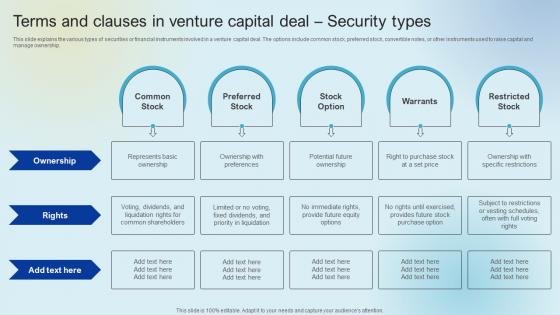
Terms And Clauses In Venture Raising Venture Capital A Holistic Approach Fin SS V
This slide explains the various types of securities or financial instruments involved in a venture capital deal. The options include common stock, preferred stock, convertible notes, or other instruments used to raise capital and manage ownership. This Terms And Clauses In Venture Raising Venture Capital A Holistic Approach Fin SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Terms And Clauses In Venture Raising Venture Capital A Holistic Approach Fin SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide explains the various types of securities or financial instruments involved in a venture capital deal. The options include common stock, preferred stock, convertible notes, or other instruments used to raise capital and manage ownership.

Investment Strategies Development To Strategic Wealth Management And Financial Fin SS V
This slide shows various strategies which can be used by wealth management personnels to invest clients money into various assets or securities. These strategies are passive investing, active investing, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Investment Strategies Development To Strategic Wealth Management And Financial Fin SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Investment Strategies Development To Strategic Wealth Management And Financial Fin SS V. This slide shows various strategies which can be used by wealth management personnels to invest clients money into various assets or securities. These strategies are passive investing, active investing, etc.

Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Model Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Get a simple yet stunning designed Zero Trust Model Benefits Of Zero Trust Network Access ZTNA. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Benefits Of Zero Trust Network Access ZTNA can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

Zero Trust Model Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Difference Between ZTNA And Software Defined Perimeter and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
Zero Trust Model On Ramp Option 2 Applications And Data
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks has constructed Zero Trust Model On Ramp Option 2 Applications And Data after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.

Zero Trust Model On Ramp Option 3 The Network
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Presenting this PowerPoint presentation, titled Zero Trust Model On Ramp Option 3 The Network, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Model On Ramp Option 3 The Network. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Model On Ramp Option 3 The Network that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Zero Trust Model Step 3 Assess The Environment
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Get a simple yet stunning designed Zero Trust Model Step 3 Assess The Environment. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Step 3 Assess The Environment can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.

Zero Trust Model Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Steps To Implement Zero Trust Network Access Model With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Zero Trust Model Timeline To Implement Zero Trust Network Access
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Model Timeline To Implement Zero Trust Network Access can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Model Timeline To Implement Zero Trust Network Access and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Zero Trust Model Zero Trust Network Access System Use Cases
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Model Zero Trust Network Access System Use Cases that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Model Zero Trust Network Access System Use Cases from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.

Cryptocurrencies Available On Kraken Complete Roadmap To Blockchain BCT SS V
This slide covers types of coins available for trading on Kraken crypto exchange platforms. It includes coins such as bitcoins, Ethereum, XRP, Cardano, Solana, Dogecoin, Polkadot, Polygon, TRON, etc along with ratings for Kraken based on trading, advanced trading features, security and storage, crypto wallets, staking, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Cryptocurrencies Available On Kraken Complete Roadmap To Blockchain BCT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cryptocurrencies Available On Kraken Complete Roadmap To Blockchain BCT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers types of coins available for trading on Kraken crypto exchange platforms. It includes coins such as bitcoins, Ethereum, XRP, Cardano, Solana, Dogecoin, Polkadot, Polygon, TRON, etc along with ratings for Kraken based on trading, advanced trading features, security and storage, crypto wallets, staking, etc.

Introduction To Cryptocurrency Exchange Platform Complete Roadmap To Blockchain BCT SS V
This slide covers brief summary of crypto exchanges platform highlighting its concept with key benefits. It includes benefits such as security and safety, liquidity and accessibility, flat support and payment options and regulatory compliance, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Introduction To Cryptocurrency Exchange Platform Complete Roadmap To Blockchain BCT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Introduction To Cryptocurrency Exchange Platform Complete Roadmap To Blockchain BCT SS V. This slide covers brief summary of crypto exchanges platform highlighting its concept with key benefits. It includes benefits such as security and safety, liquidity and accessibility, flat support and payment options and regulatory compliance, etc.
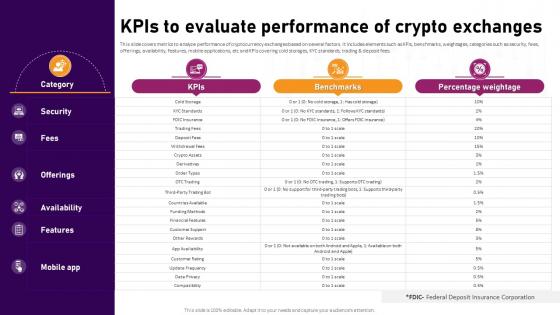
KPIs To Evaluate Performance Of Crypto Exchanges Complete Roadmap To Blockchain BCT SS V
This slide covers metrics to analyze performance of cryptocurrency exchanges based on several factors. It includes elements such as KPIs, benchmarks, weightages, categories such as security, fees, offerings, availability, features, mobile applications, etc and KPIs covering cold storages, KYC standards, trading and deposit fees. Do you know about Slidesgeeks KPIs To Evaluate Performance Of Crypto Exchanges Complete Roadmap To Blockchain BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide covers metrics to analyze performance of cryptocurrency exchanges based on several factors. It includes elements such as KPIs, benchmarks, weightages, categories such as security, fees, offerings, availability, features, mobile applications, etc and KPIs covering cold storages, KYC standards, trading and deposit fees.

Major Trading Challenges In Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V
This slide covers major issues identified while trading in cryptocurrency exchanges by users. It includes challenges such as lack of security or hacking risks, high trading fees, liquidity issues, etc with description and solutions to overcome the risks and problems. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Major Trading Challenges In Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide covers major issues identified while trading in cryptocurrency exchanges by users. It includes challenges such as lack of security or hacking risks, high trading fees, liquidity issues, etc with description and solutions to overcome the risks and problems.
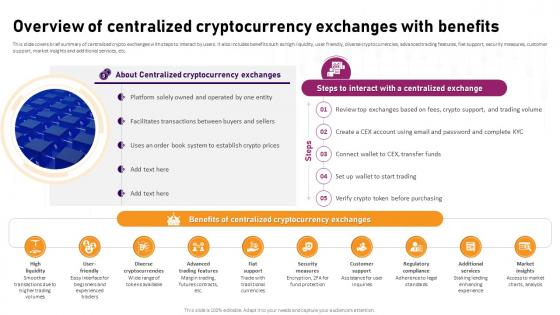
Overview Of Centralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V
This slide covers brief summary of centralized crypto exchanges with steps to interact by users. It also includes benefits such as high liquidity, user friendly, diverse cryptocurrencies, advanced trading features, fiat support, security measures, customer support, market insights and additional services, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview Of Centralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview Of Centralized Cryptocurrency Exchanges Complete Roadmap To Blockchain BCT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide covers brief summary of centralized crypto exchanges with steps to interact by users. It also includes benefits such as high liquidity, user friendly, diverse cryptocurrencies, advanced trading features, fiat support, security measures, customer support, market insights and additional services, etc.
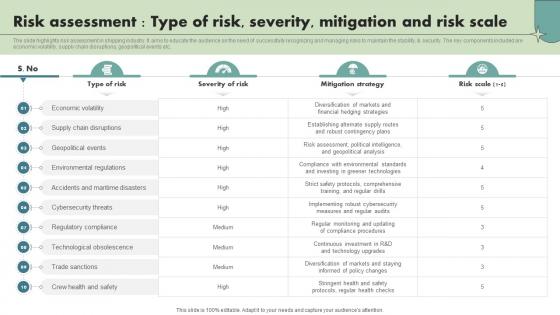
Risk Assessment Type Of Risk Severity Mitigation And Risk Scale Maritime Shipping Industry IR SS V
The slide highlights risk assessment in shipping industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability, and security. The key components included are economic volatility, supply chain disruptions, geopolitical events etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Risk Assessment Type Of Risk Severity Mitigation And Risk Scale Maritime Shipping Industry IR SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Risk Assessment Type Of Risk Severity Mitigation And Risk Scale Maritime Shipping Industry IR SS V. The slide highlights risk assessment in shipping industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability, and security. The key components included are economic volatility, supply chain disruptions, geopolitical events etc.

The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Take your projects to the next level with our ultimate collection of The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc.
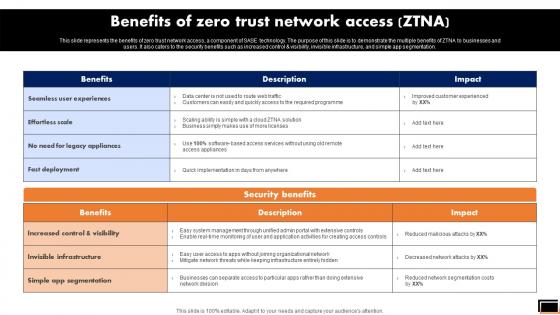
Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Access Ztna Software Defined Perimeter SDP for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.
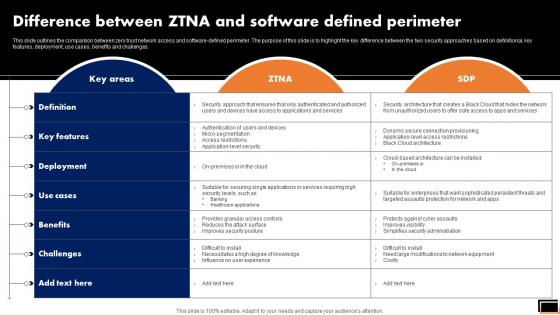
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
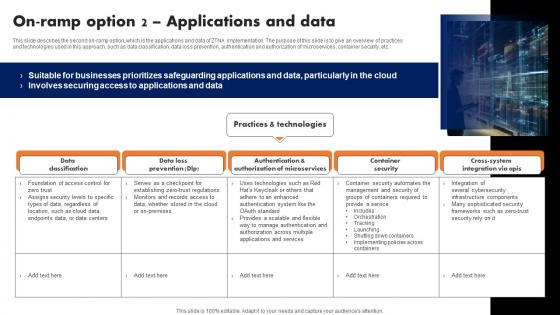
On Ramp Option 2 Applications And Data Software Defined Perimeter SDP
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. The On Ramp Option 2 Applications And Data Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.
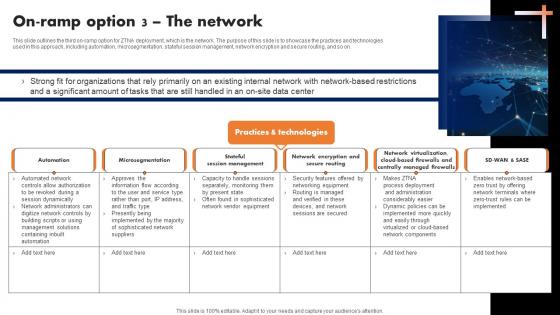
On Ramp Option 3 The Network Software Defined Perimeter SDP
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Software Defined Perimeter SDP from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc.
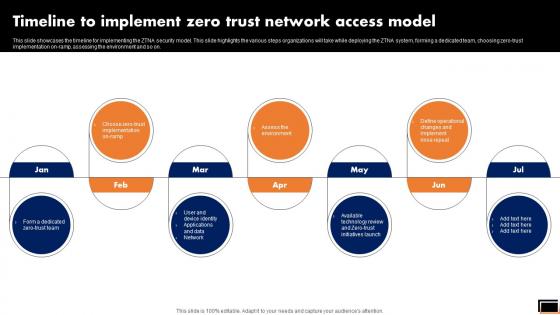
Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Zero Trust Network Access System Use Cases Software Defined Perimeter SDP
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Network Access System Use Cases Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access System Use Cases Software Defined Perimeter SDP from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.

Challenges And Considerations In Cloud Erp Integration Erp And Digital Transformation For Maximizing DT SS V
This slide addresses the key challenges faced while Integrating an ERP system with the cloud. It includes change management, security, access, permissions and productivity, optimum architectural and licensing models, and user onboarding and training.Slidegeeks is here to make your presentations a breeze with Challenges And Considerations In Cloud Erp Integration Erp And Digital Transformation For Maximizing DT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide addresses the key challenges faced while Integrating an ERP system with the cloud. It includes change management, security, access, permissions and productivity, optimum architectural and licensing models, and user onboarding and training.
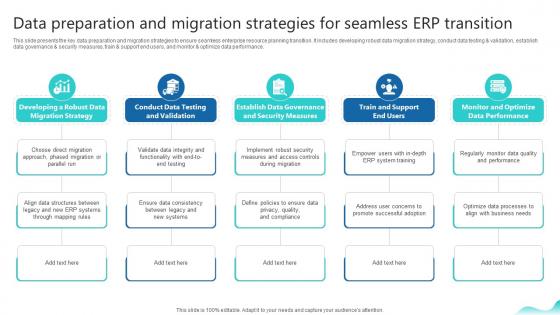
Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V
This slide presents the key data preparation and migration strategies to ensure seamless enterprise resource planning transition. It includes developing robust data migration strategy, conduct data testing and validation, establish data governance and security measures, train and support end users, and monitor and optimize data performance. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Data Preparation And Migration Strategies For Seamless Erp And Digital Transformation For Maximizing DT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide presents the key data preparation and migration strategies to ensure seamless enterprise resource planning transition. It includes developing robust data migration strategy, conduct data testing and validation, establish data governance and security measures, train and support end users, and monitor and optimize data performance.
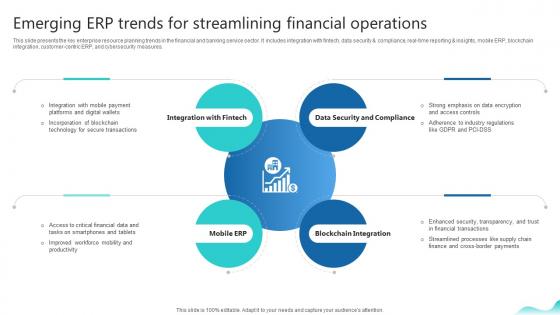
Emerging Erp Trends For Streamlining Financial Operations Erp And Digital Transformation For Maximizing DT SS V
This slide presents the key enterprise resource planning trends in the financial and banking service sector. It includes integration with fintech, data security and compliance, real-time reporting and insights, mobile ERP, blockchain integration, customer-centric ERP, and cybersecurity measures.Welcome to our selection of the Emerging Erp Trends For Streamlining Financial Operations Erp And Digital Transformation For Maximizing DT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide presents the key enterprise resource planning trends in the financial and banking service sector. It includes integration with fintech, data security and compliance, real-time reporting and insights, mobile ERP, blockchain integration, customer-centric ERP, and cybersecurity measures.

Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform
This slide outlines the various advantages of IoT platform utilization. The purpose of this slide is to showcase the key benefits of using IoT platforms which include scalability, security, cost saving, etc. Presenting this PowerPoint presentation, titled Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the various advantages of IoT platform utilization. The purpose of this slide is to showcase the key benefits of using IoT platforms which include scalability, security, cost saving, etc.
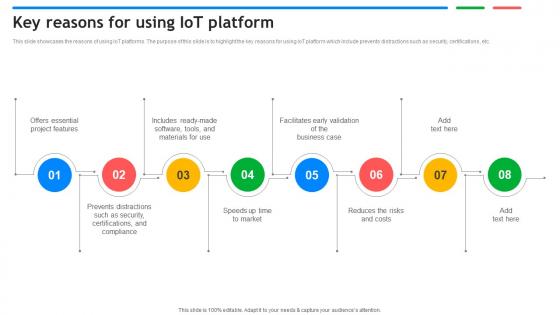
Key Reasons For Using IoT Platform Exploring Google Cloud IoT Platform
This slide showcases the reasons of using IoT platforms. The purpose of this slide is to highlight the key reasons for using IoT platform which include prevents distractions such as security, certifications, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Key Reasons For Using IoT Platform Exploring Google Cloud IoT Platform to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Key Reasons For Using IoT Platform Exploring Google Cloud IoT Platform This slide showcases the reasons of using IoT platforms. The purpose of this slide is to highlight the key reasons for using IoT platform which include prevents distractions such as security, certifications, etc.
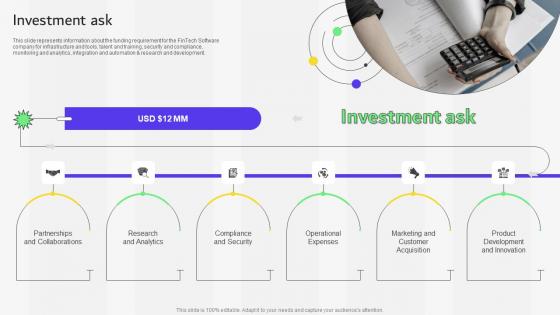
Investment Ask Financial Services Provider Investor Funding Elevator Pitch Deck
This slide represents information about the funding requirement for the FinTech Software company for infrastructure and tools, talent and training, security and compliance, monitoring and analytics, integration and automation and research and development. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Investment Ask Financial Services Provider Investor Funding Elevator Pitch Deck can be your best option for delivering a presentation. Represent everything in detail using Investment Ask Financial Services Provider Investor Funding Elevator Pitch Deck and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents information about the funding requirement for the FinTech Software company for infrastructure and tools, talent and training, security and compliance, monitoring and analytics, integration and automation and research and development.

Industry Wise Market Segmentation Of SWG Web Threat Protection System
This slide demonstrates the contribution of different industries in growth of Secure Web Gateway market. The purpose of this slide is to represent the industry wise market share of different sectors such as BFSI, IT and telecom, retail and e-Commerce, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Industry Wise Market Segmentation Of SWG Web Threat Protection System was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Industry Wise Market Segmentation Of SWG Web Threat Protection System This slide demonstrates the contribution of different industries in growth of Secure Web Gateway market. The purpose of this slide is to represent the industry wise market share of different sectors such as BFSI, IT and telecom, retail and e-Commerce, etc.
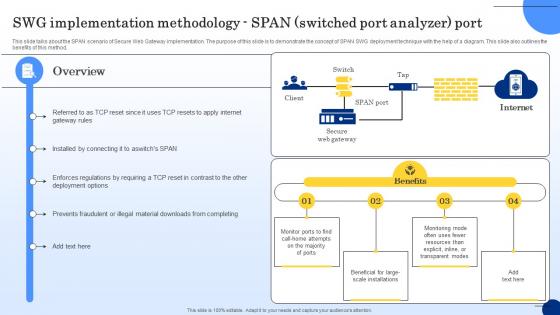
SWG Implementation Methodology Span Web Threat Protection System
This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than SWG Implementation Methodology Span Web Threat Protection System. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab SWG Implementation Methodology Span Web Threat Protection System today and make your presentation stand out from the rest This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
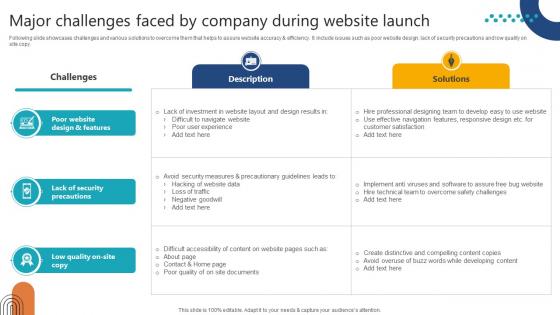
Complete Guide To Launch Major Challenges Faced By Company During Website
Following slide showcases challenges and various solutions to overcome them that helps to assure website accuracy and efficiency. It include issues such as poor website design, lack of security precautions and low quality on site copy. Explore a selection of the finest Complete Guide To Launch Major Challenges Faced By Company During Website here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Complete Guide To Launch Major Challenges Faced By Company During Website to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Following slide showcases challenges and various solutions to overcome them that helps to assure website accuracy and efficiency. It include issues such as poor website design, lack of security precautions and low quality on site copy.

Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V
This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc. Get a simple yet stunning designed Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc.
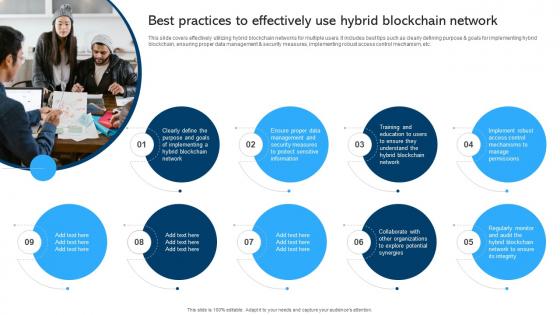
Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V
This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc. Welcome to our selection of the Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc.

Comprehensive Manual For Blockchain Use Cases Of Consortium Blockchain BCT SS V
This slide covers applications of consortium blockchain network platform. It includes use cases such as healthcare, finance, identity verification, real estate for securely storing data, facilitating trade financing, enabling identity verification, simplifying real estate transactions, etc. Do you know about Slidesgeeks Comprehensive Manual For Blockchain Use Cases Of Consortium Blockchain BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide covers applications of consortium blockchain network platform. It includes use cases such as healthcare, finance, identity verification, real estate for securely storing data, facilitating trade financing, enabling identity verification, simplifying real estate transactions, etc.

Resources And Training That Companies Man In The Middle Phishing IT
This slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if youve already been breached, be aware of the various phishing attacks, invest in security education, etc. Find highly impressive Resources And Training That Companies Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Resources And Training That Companies Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if youve already been breached, be aware of the various phishing attacks, invest in security education, etc.
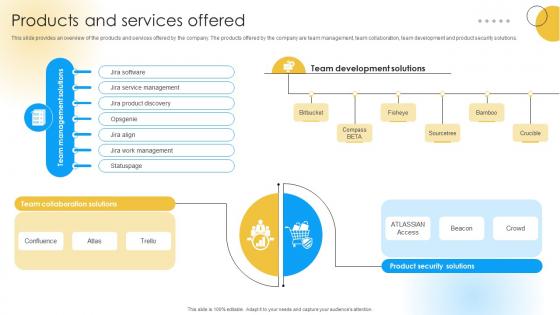
Products And Services Offered Software Development Company Funding Elevator Pitch Deck
This slide provides an overview of the products and services offered by the company. The products offered by the company are team management, team collaboration, team development and product security solutions. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Products And Services Offered Software Development Company Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Products And Services Offered Software Development Company Funding Elevator Pitch Deck. This slide provides an overview of the products and services offered by the company. The products offered by the company are team management, team collaboration, team development and product security solutions.

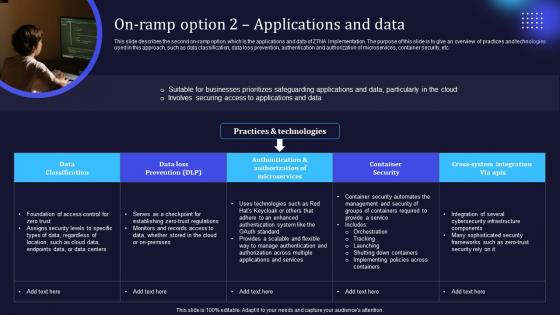
On Ramp Option 2 Applications And Data Zero Trust Network Access
This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc. Slidegeeks is here to make your presentations a breeze with On Ramp Option 2 Applications And Data Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the second on-ramp option, which is the applications and data of ZTNA implementation. The purpose of this slide is to give an overview of practices and technologies used in this approach, such as data classification, data loss prevention, authentication and authorization of microservices, container security, etc.


 Continue with Email
Continue with Email

 Home
Home


































