Lock

Asset Protection Privacy Ppt PowerPoint Presentation Pictures Visual Aids Cpb
This is a asset protection privacy ppt powerpoint presentation pictures visual aids cpb. This is a five stage process. The stages in this process are asset protection privacy.

What Are Benefits Of Using Data Security In Cloud Computing Ppt Template
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit What Are Benefits Of Using Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.
Customer Privacy Policy Ppt PowerPoint Presentation Show Introduction Cpb
This is a customer privacy policy ppt powerpoint presentation show introduction cpb. This is a four stage process. The stages in this process are customer privacy policy, business, management, marketing.
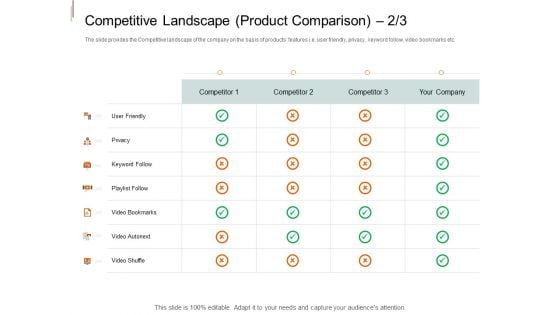
Equity Crowd Investing Competitive Landscape Product Comparison Privacy Guidelines PDF
The slide provides the Competitive landscape of the company on the basis of products features i.e. user friendly, privacy, keyword follow, video bookmarks etc. Deliver and pitch your topic in the best possible manner with this equity crowd investing competitive landscape product comparison privacy guidelines pdf. Use them to share invaluable insights on competitive landscape, product comparison, competitor, privacy, Privacy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cloud Computing Protection And Privacy Icon Designs PDF
Presenting Cloud Computing Protection And Privacy Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Privacy Icon, Cloud Computing Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Online Data Protection And Privacy Icon Structure PDF
Presenting Online Data Protection And Privacy Icon Structure PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Privacy Icon, Online Data Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Customer Data Profiling Solutions And Privacy Management Icon Rules PDF
Presenting Customer Data Profiling Solutions And Privacy Management Icon Rules PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Customer Data Profiling, Solutions And Privacy, Management Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
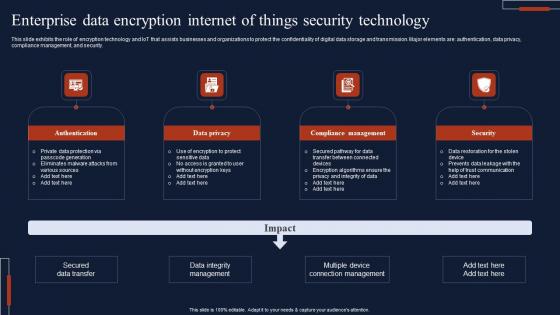
Enterprise Data Encryption Internet Of Things Security Technology Summary Pdf
This slide exhibits the role of encryption technology and IoT that assists businesses and organizations to protect the confidentiality of digital data storage and transmission. Major elements are authentication, data privacy, compliance management, and security. Showcasing this set of slides titled Enterprise Data Encryption Internet Of Things Security Technology Summary Pdf The topics addressed in these templates are Authentication, Data Privacy, Compliance Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide exhibits the role of encryption technology and IoT that assists businesses and organizations to protect the confidentiality of digital data storage and transmission. Major elements are authentication, data privacy, compliance management, and security.
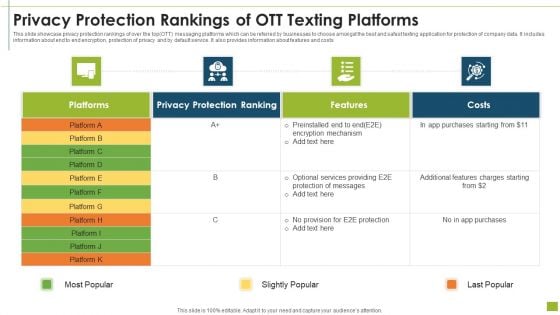
Privacy Protection Rankings Of OTT Texting Platforms Template PDF
This slide showcase privacy protection rankings of over the top OTT messaging platforms which can be referred by businesses to choose amongst the best and safest texting application for protection of company data. It includes information about end to end encryption, protection of privacy and by default service. It also provides information about features and costs Showcasing this set of slides titled privacy protection rankings of ott texting platforms template pdf The topics addressed in these templates are optional services providing, encryption mechanism, purchases starting All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Data Protection Privacy Ppt PowerPoint Presentation Portfolio Templates Cpb Pdf
Presenting this set of slides with name data protection privacy ppt powerpoint presentation portfolio templates cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like data protection privacy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Privacy Risks Ppt PowerPoint Presentation Topics Cpb Pdf
Presenting this set of slides with name privacy risks ppt powerpoint presentation topics cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like privacy risks to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Consumer Online Privacy Ppt PowerPoint Presentation Styles Guide Cpb Pdf
Presenting this set of slides with name consumer online privacy ppt powerpoint presentation styles guide cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like consumer online privacy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Communication Privacy Management Ppt PowerPoint Presentation Gallery Background Cpb Pdf
Presenting this set of slides with name communication privacy management ppt powerpoint presentation gallery background cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like communication privacy management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Privacy Protection Ppt PowerPoint Presentation Professional Graphics Template Cpb Pdf
Presenting this set of slides with name privacy protection ppt powerpoint presentation professional graphics template cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like privacy protection to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Social Media User Protection And Privacy Icon Summary PDF
Persuade your audience using this Social Media User Protection And Privacy Icon Summary PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Privacy Icon, Social Media User Protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
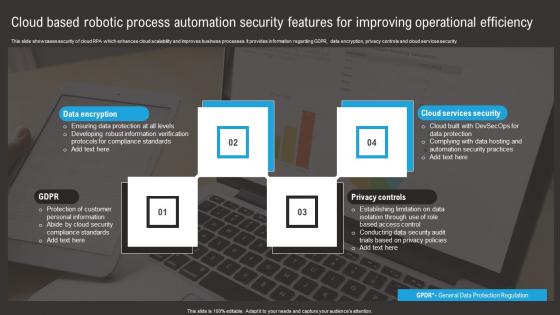
Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf
This slide showcases security of cloud RPA which enhances cloud scalability and improves business processes. It provides information regarding GDPR, data encryption, privacy controls and cloud services security. Pitch your topic with ease and precision using this Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf. This layout presents information on Data Encryption, Privacy Controls, Cloud Services Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases security of cloud RPA which enhances cloud scalability and improves business processes. It provides information regarding GDPR, data encryption, privacy controls and cloud services security.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information Privacy IT Track Record Of Our Company Guidelines PDF
This slide highlights our past track record as a data privacy provider company and outlines that we promise 100 parcent client satisfaction. Presenting information privacy it track record of our company guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like track record of our company. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
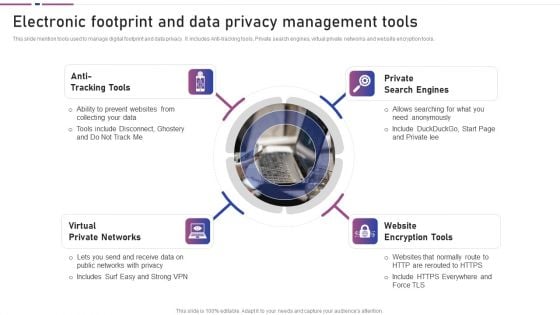
Electronic Footprint And Data Privacy Management Tools Professional PDF
This slide mention tools used to manage digital footprint and data privacy. It includes Anti-tracking tools, Private search engines, virtual private networks and website encryption tools. Presenting Electronic Footprint And Data Privacy Management Tools Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Virtual Private Networks, Website Encryption Tools, Private Search Engines. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Privacy Risk Management Matrix With Mitigation Plan Demonstration PDF
This slide shows risk evaluation and mitigation matrix for privacy management which contains risk value low, medium and high and acceptance criteria action. This can enable IT managers in ensuring proper flow of operations so that minimal or no private data is lost or leaked into public. Persuade your audience using this Privacy Risk Management Matrix With Mitigation Plan Demonstration PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Information, Plan, Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icons Slide For Information Privacy It Demonstration PDF
Help your business to create an attention-grabbing presentation using our icons slide for information privacy it demonstration pdf set of slides. The slide contains innovative icons that can be flexibly edited. Choose this ZZZZZZZ template to create a satisfactory experience for your customers. Go ahead and click the download button.
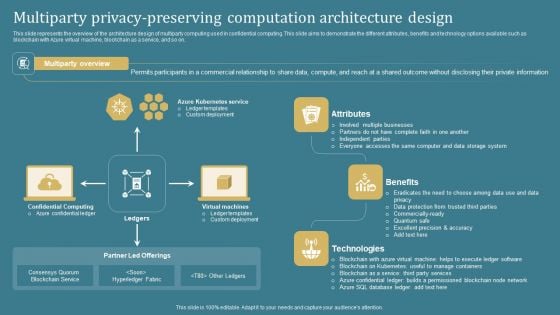
Confidential Computing System Technology Multiparty Privacy Preserving Computation Demonstration PDF
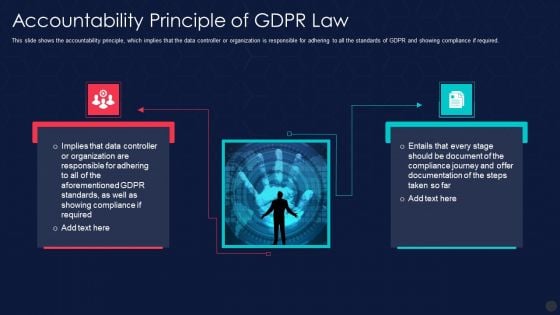
Information Privacy IT Accountability Principle Of Gdpr Law Structure PDF
This slide shows the accountability principle, which implies that the data controller or organization is responsible for adhering to all the standards of GDPR and showing compliance if required. Deliver an awe inspiring pitch with this creative information privacy it accountability principle of gdpr law structure pdf bundle. Topics like accountability principle of gdpr law can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
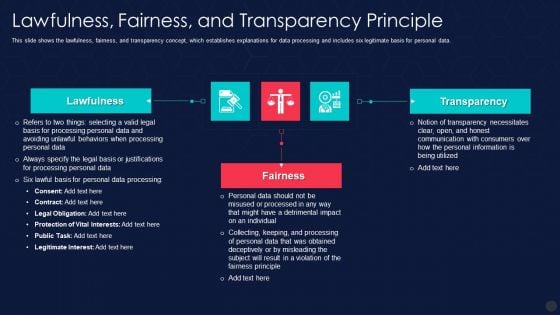
Information Privacy IT Lawfulness Fairness And Transparency Principle Structure PDF
This slide shows the lawfulness, fairness, and transparency concept, which establishes explanations for data processing and includes six legitimate basis for personal data. Deliver an awe inspiring pitch with this creative information privacy it lawfulness fairness and transparency principle structure pdf bundle. Topics like lawfulness, fairness, and transparency principle can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Playbook For Achieving Privacy And Performance In Digital Marketing Template
Create winning presentations effortlessly with our Playbook For Achieving Privacy And Performance In Digital Marketing Template. Designed to impress, each template is 100 percent editable, visually-stunning, and easy-to-use. Our team of researchers has meticulously crafted the right content for each template, so you do not have to worry about anything. Just select the perfect template for your project, personalize it, and deliver a memorable presentation that leaves a lasting impact.
Information Privacy IT Seven Principles Of Gdpr Law Icons PDF
This slide represents the seven principles of GDPR law, including lawfulness and transparency, purpose limitation, data minimization, accuracy, storage limitation, integrity and confidentiality, accountability. Presenting information privacy it seven principles of gdpr law icons pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like seven principles of gdpr law. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
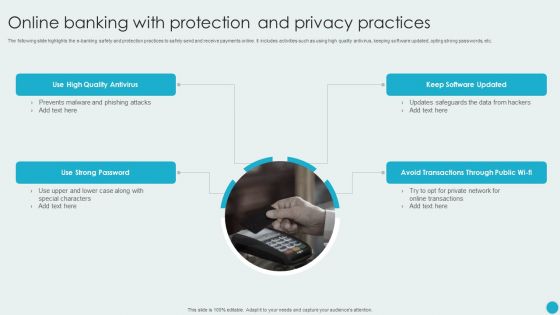
Online Banking With Protection And Privacy Practices Structure PDF
The following slide highlights the e-banking safety and protection practices to safely send and receive payments online. It includes activities such as using high quality antivirus, keeping software updated, opting strong passwords, etc. Persuade your audience using this Online Banking With Protection And Privacy Practices Structure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Use High Quality Antivirus, Use Strong Password, Keep Software Updated. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
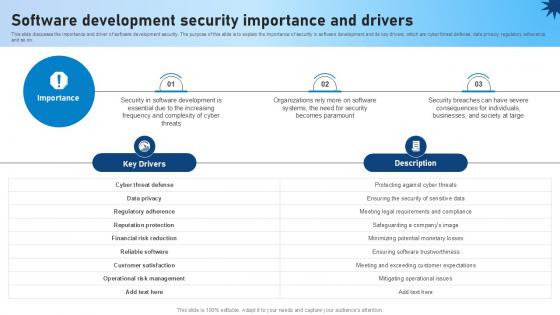
Software Development Security Importance And Drivers Role Of Devsecops Ppt Slide
This slide discusses the importance and driver of software development security. The purpose of this slide is to explain the importance of security in software development and its key drivers, which are cyber threat defense, data privacy, regulatory adherence, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Software Development Security Importance And Drivers Role Of Devsecops Ppt Slide a try. Our experts have put a lot of knowledge and effort into creating this impeccable Software Development Security Importance And Drivers Role Of Devsecops Ppt Slide You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide discusses the importance and driver of software development security. The purpose of this slide is to explain the importance of security in software development and its key drivers, which are cyber threat defense, data privacy, regulatory adherence, and so on.

Protection And Privacy Ppt PowerPoint Presentation Complete With Slides
Share a great deal of information on the topic by deploying this Protection And Privacy Ppt PowerPoint Presentation Complete With Slides. Support your ideas and thought process with this prefabricated set. It includes a set of ninteen slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.

Security Technology Stack Powerpoint Ppt Template Bundles
You will save yourself your energy and hours of time when you choose to use this impactful PowerPoint Deck. This Security Technology Stack Powerpoint Ppt Template Bundles has been tailor-made to your business needs which ensures that you will always be prepared for that next meeting. Worry can not touch you when you present in your area of expertise using this PPT Template Bundle. With a modern design and easy to follow structure, this PowerPoint Presentation has Encryption Tools, API Security, Cloud Technology, Network Security, Zero Trust-slides, which ensures that you can cover you need to without much work. Create your next presentation using this PPT Theme to deliver a memorable performance. Enhance your cybersecurity expertise with our Security Technology Stack PowerPoint presentation. Explore the intricacies of cybersecurity tech stacks through practical examples and insights to safeguard your digital assets. The presentation covers various tech stacks such as web development and Microsoft technology. Learn how to build a robust security technology stack to protect your organization from emerging threats and vulnerabilities. Designed for IT professionals, developers, or business leaders, this PPT provides tools and strategies to create a resilient defense system.
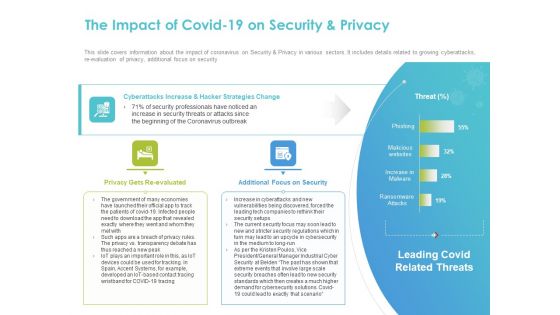
COVID 19 Mitigating Impact On High Tech Industry The Impact Of COVID 19 On Security And Privacy Demonstration PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry the impact of covid 19 on security and privacy demonstration pdf. The topics discussed in these slides are privacy gets re evaluated, additional focus security, leading covid related threats, coronavirus outbreak, security threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Business Daigram Internet Symbol For Privacy Concept Presentation Templets
This business slide contains email symbol with puzzle pattern. Our above given diagram with graphics of email can be used illustrate the communication and technology concepts. Download this diagram slide to make professional presentations.

Information Privacy IT Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the sixty five slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
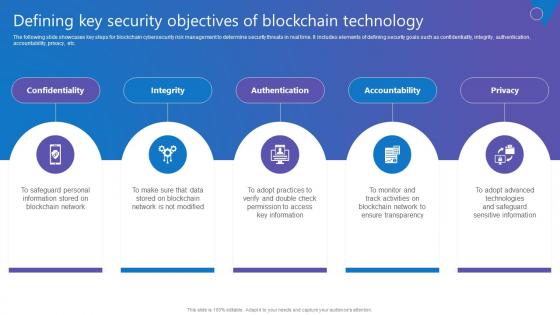
Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf
The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Want to ace your presentation in front of a live audience Our Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc.
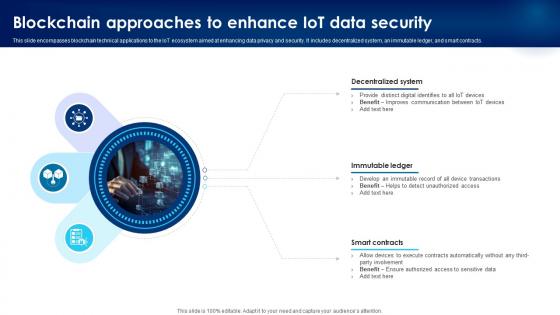
Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V
This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Building Trust With IoT Security Blockchain Approaches To Enhance IoT Data Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide encompasses blockchain technical applications to the IoT ecosystem aimed at enhancing data privacy and security. It includes decentralized system, an immutable ledger, and smart contracts.

Security Access Control Iris Scanning System Ppt PowerPoint Presentation Show Gridlines
This is a security access control iris scanning system ppt powerpoint presentation show gridlines. This is a two stage process. The stages in this process are access rights, access management, business.
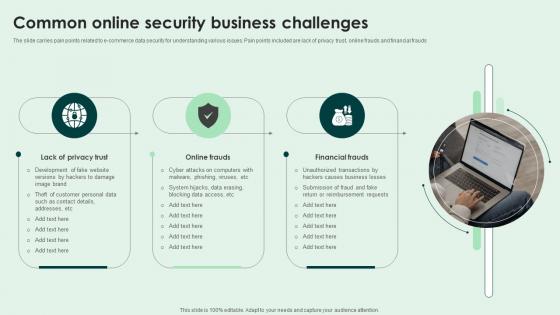
Common Online Security Business Challenges Guidelines Pdf
Showcasing this set of slides titled Common Online Security Business Challenges Guidelines Pdf. The topics addressed in these templates are Lack Of Privacy Trust, Online Frauds, Financial Frauds. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Common Online Security Business Challenges Guidelines Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
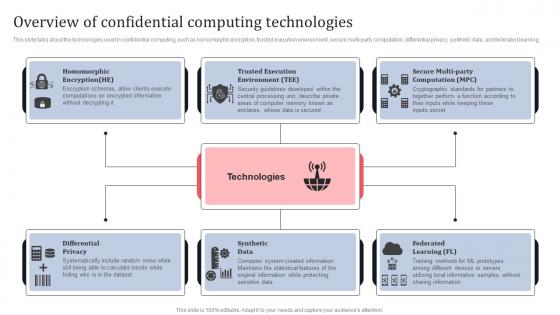
Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Get a simple yet stunning designed Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview Of Confidential Computing Technologies Secure Multi Party Designs Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
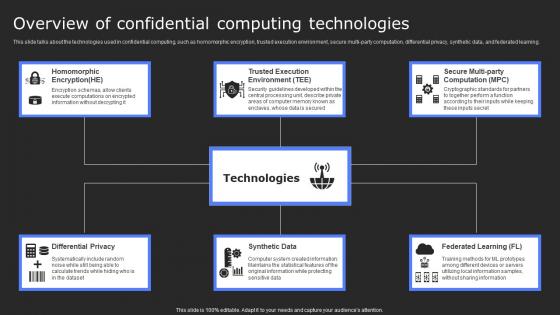
Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Present like a pro with Overview Of Confidential Computing Technologies Secure Computing Framework Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
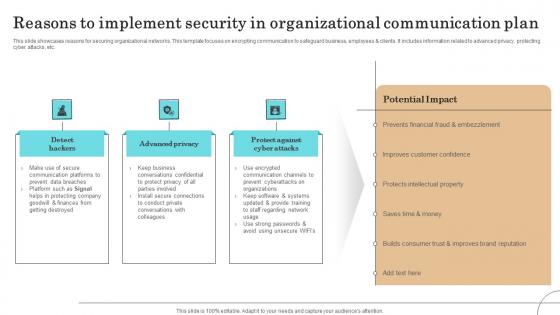
Reasons To Implement Security In Organizational Communication Plan Sample Pdf
This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.Showcasing this set of slides titled Reasons To Implement Security In Organizational Communication Plan Sample Pdf The topics addressed in these templates are Communication Platforms, Protecting Company, Improves Customer Confidence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.
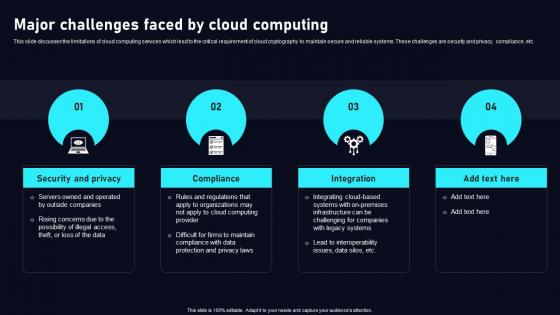
Major Challenges Faced By Cloud Data Security Using Cryptography Inspiration Pdf
This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc. QThere are so many reasons you need a Major Challenges Faced By Cloud Data Security Using Cryptography Inspiration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc.
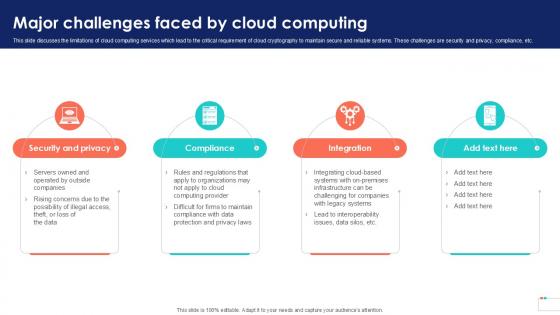
Major Challenges Faced By Data Security In Cloud Computing Ppt Sample
This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc. Do you know about Slidesgeeks Major Challenges Faced By Data Security In Cloud Computing Ppt Sample These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc.
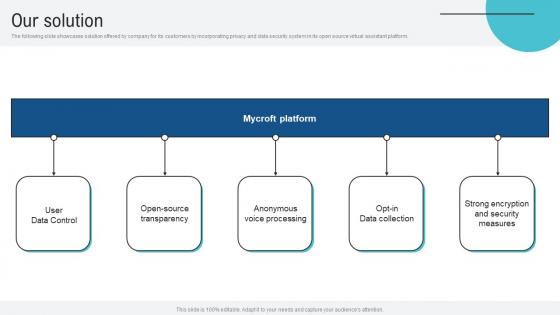
Our Solution Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf
The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform. This Our Solution Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform.
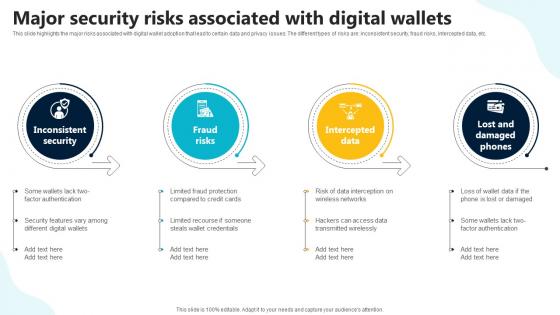
Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V
This slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc. Boost your pitch with our creative Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc.
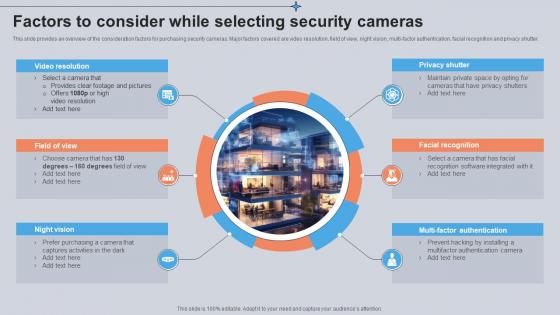
Factors To Consider While Selecting Security Cameras Utilizing Smart Appliances IoT SS V
This slide provides an overview of the consideration factors for purchasing security cameras. Major factors covered are video resolution, field of view, night vision, multi-factor authentication, facial recognition and privacy shutter. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Factors To Consider While Selecting Security Cameras Utilizing Smart Appliances IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide provides an overview of the consideration factors for purchasing security cameras. Major factors covered are video resolution, field of view, night vision, multi-factor authentication, facial recognition and privacy shutter.
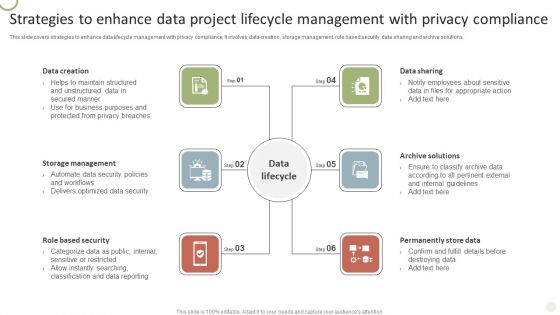
Strategies To Enhance Data Project Lifecycle Management With Privacy Compliance Guidelines PDF
This slide covers strategies to enhance data lifecycle management with privacy compliance. It involves data creation, storage management, role based security, data sharing and archive solutions.Persuade your audience using this Strategies To Enhance Data Project Lifecycle Management With Privacy Compliance Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Secured Manner, Business Purposes, Protected Privacy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
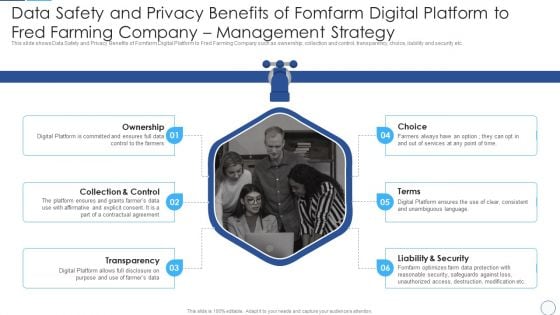
Data Safety And Privacy Benefits Of Fomfarm Digital Platform To Fred Farming Designs PDF
This slide shows Data Safety and Privacy Benefits of Fomfarm Digital Platform to Fred Farming Company such as ownership, collection and control, transparency, choice, liability and security etc. This is a Data Safety And Privacy Benefits Of Fomfarm Digital Platform To Fred Farming Designs PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Transparency, Collection Control, Liability Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
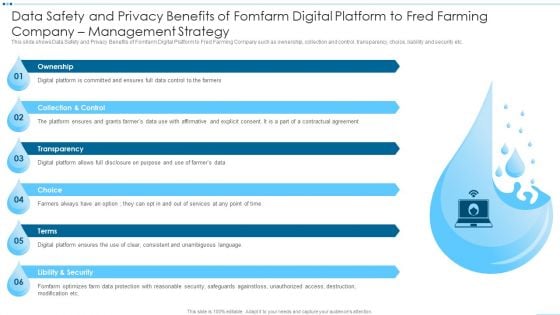
Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF
This slide shows Data Safety and Privacy Benefits of Fomfarm Digital Platform to Fred Farming Company such as ownership, collection and control, transparency, choice, liability and security etc. Deliver an awe inspiring pitch with this creative Digital Media Channels Data Safety And Privacy Benefits Of Fomfarm Digital Platform Demonstration PDF bundle. Topics like Ownership, Collection And Control, Transparency, Choice can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V
This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface.
Define Access Control Measures For Employees IT Security IT Ppt Professional Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a define access control measures for employees it security it ppt professional icon pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, access data, networks, responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Security Define Access Control Measures For Employees Ppt Professional Design Templates PDF
This slide represents how it is essential to minimize the rights access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information technology security define access control measures for employees ppt professional design templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like staff duties, organization, roles, access, permissions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
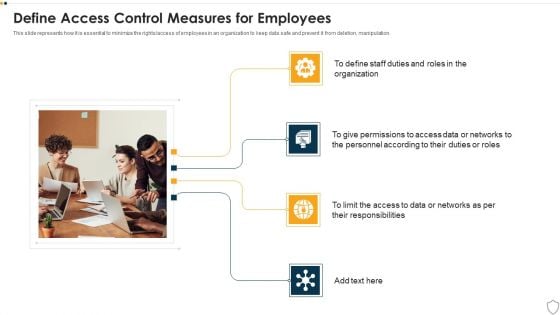
IT Security Define Access Control Measures For Employees Ppt Styles Good PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Presenting it security define access control measures for employees ppt styles good pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like organization, responsibilities, access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Info Security Define Access Control Measures For Employees Ppt PowerPoint Presentation Gallery Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Presenting info security define access control measures for employees ppt powerpoint presentation gallery icon pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like access data, personnel according, duties or roles, organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Security Define Access Control Measures For Employees Ppt Icon Pictures PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information security define access control measures for employees ppt icon pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Desktop Security Management Define Access Control Measures For Employees Icons PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a desktop security management define access control measures for employees icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
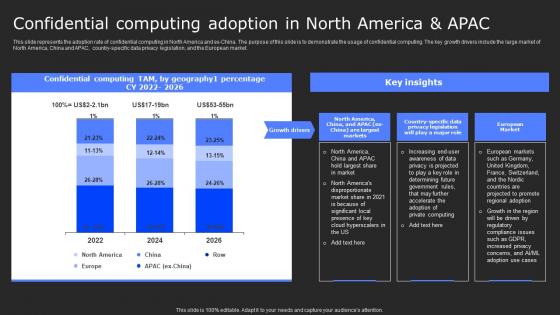
Confidential Computing Adoption In North Secure Computing Framework Template Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In North Secure Computing Framework Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In North Secure Computing Framework Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market.
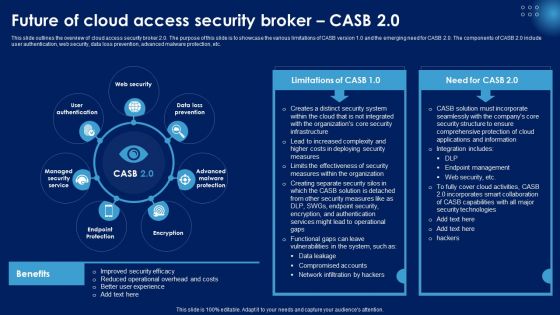
Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Explore a selection of the finest Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Future Of Cloud Access Security Broker CASB 2 0 Ppt PowerPoint Presentation File Outline PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
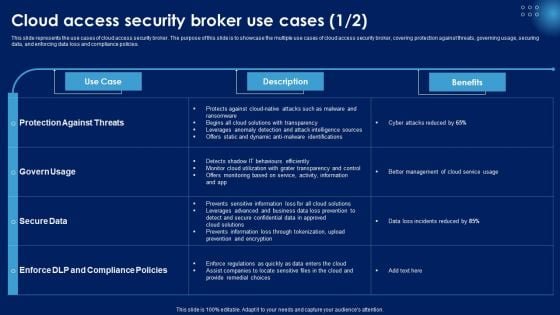
Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
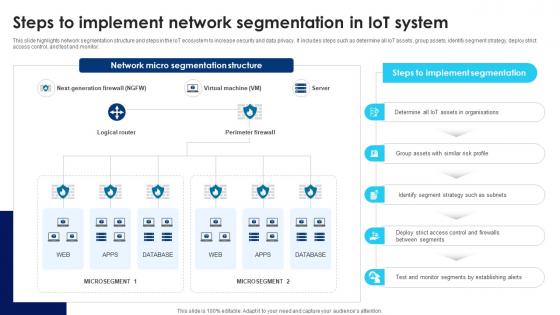
Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V
This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor.


 Continue with Email
Continue with Email

 Home
Home


































