Microbes
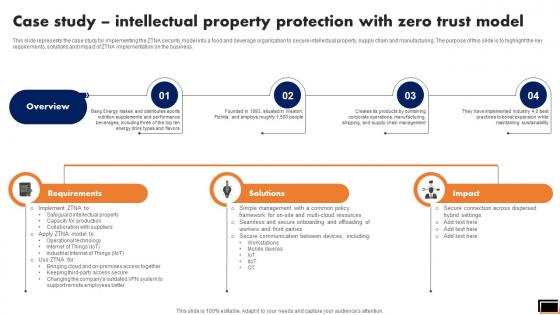
Case Study Intellectual Property Protection With Zero Trust Model Software Defined Perimeter SDP
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Want to ace your presentation in front of a live audience Our Case Study Intellectual Property Protection With Zero Trust Model Software Defined Perimeter SDP can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
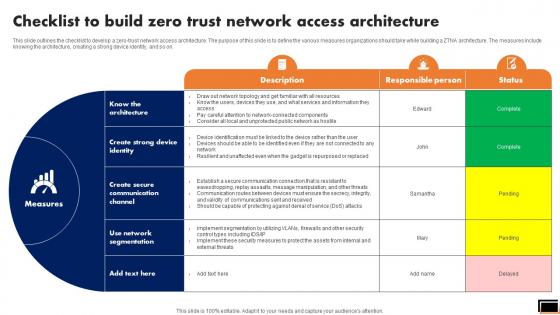
Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
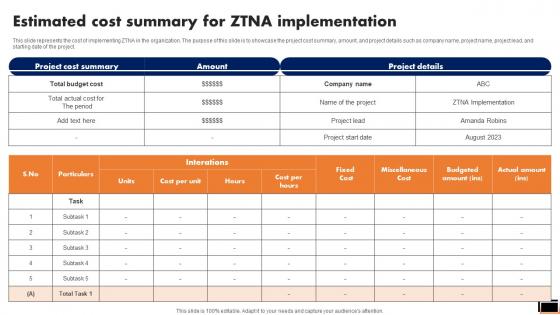
Estimated Cost Summary For Ztna Implementation Software Defined Perimeter SDP
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. If you are looking for a format to display your unique thoughts, then the professionally designed Estimated Cost Summary For Ztna Implementation Software Defined Perimeter SDP is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Estimated Cost Summary For Ztna Implementation Software Defined Perimeter SDP and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.

Key Points To Choose Zero Trust Solution Software Defined Perimeter SDP
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This modern and well-arranged Key Points To Choose Zero Trust Solution Software Defined Perimeter SDP provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.

Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc.

Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc.
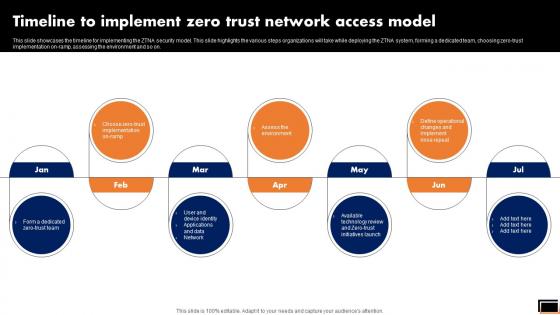
Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Zero Trust Network Access Model Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.

Training Program For Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Training Program For Zero Trust Network Access Model Software Defined Perimeter SDP template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Training Program For Zero Trust Network Access Model Software Defined Perimeter SDP that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

Chat GPT Prompts For Market ChatGPT For Identifying Competition ChatGPT SS V
This slide represents use of which an artificial intelligence technology which possesses capability to produce different types of content for market research. It includes details related to use of ChatGPT for identifying competition in organizations industry. Slidegeeks is here to make your presentations a breeze with Chat GPT Prompts For Market ChatGPT For Identifying Competition ChatGPT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents use of which an artificial intelligence technology which possesses capability to produce different types of content for market research. It includes details related to use of ChatGPT for identifying competition in organizations industry.
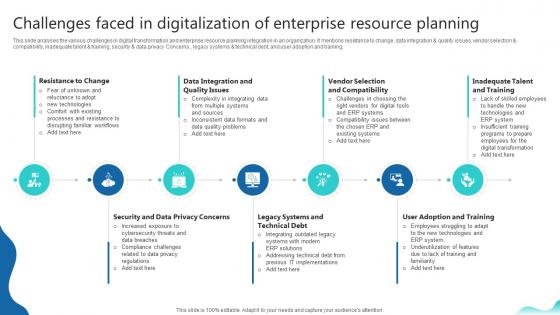
Challenges Faced In Digitalization Of Enterprise Erp And Digital Transformation For Maximizing DT SS V
This slide analyses the various challenges in digital transformation and enterprise resource planning integration in an organization. It mentions resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy Concerns , legacy systems and technical debt, and user adoption and training.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Challenges Faced In Digitalization Of Enterprise Erp And Digital Transformation For Maximizing DT SS V can be your best option for delivering a presentation. Represent everything in detail using Challenges Faced In Digitalization Of Enterprise Erp And Digital Transformation For Maximizing DT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide analyses the various challenges in digital transformation and enterprise resource planning integration in an organization. It mentions resistance to change, data integration and quality issues, vendor selection and compatibility, inadequate talent and training, security and data privacy Concerns , legacy systems and technical debt, and user adoption and training.
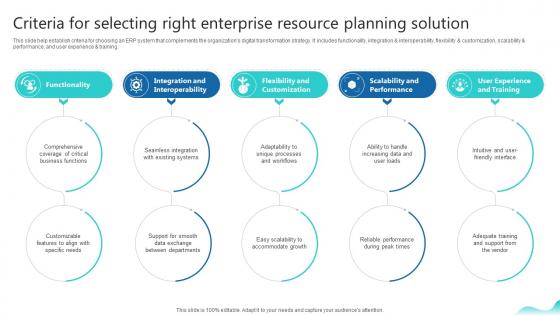
Criteria For Selecting Right Enterprise Resource Planning Erp And Digital Transformation For Maximizing DT SS V
This slide help establish criteria for choosing an ERP system that complements the organizations digital transformation strategy. It includes functionality, integration and interoperability, flexibility and customization, scalability and performance, and user experience and training. If you are looking for a format to display your unique thoughts, then the professionally designed Criteria For Selecting Right Enterprise Resource Planning Erp And Digital Transformation For Maximizing DT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Criteria For Selecting Right Enterprise Resource Planning Erp And Digital Transformation For Maximizing DT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide help establish criteria for choosing an ERP system that complements the organizations digital transformation strategy. It includes functionality, integration and interoperability, flexibility and customization, scalability and performance, and user experience and training.
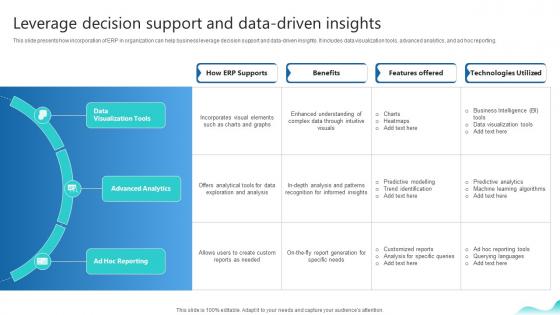
Leverage Decision Support And Data Driven Insights Erp And Digital Transformation For Maximizing DT SS V
This slide presents how incorporation of ERP in organization can help business leverage decision support and data-driven insights. It includes data visualization tools, advanced analytics, and ad hoc reporting.If you are looking for a format to display your unique thoughts, then the professionally designed Leverage Decision Support And Data Driven Insights Erp And Digital Transformation For Maximizing DT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Leverage Decision Support And Data Driven Insights Erp And Digital Transformation For Maximizing DT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents how incorporation of ERP in organization can help business leverage decision support and data-driven insights. It includes data visualization tools, advanced analytics, and ad hoc reporting.
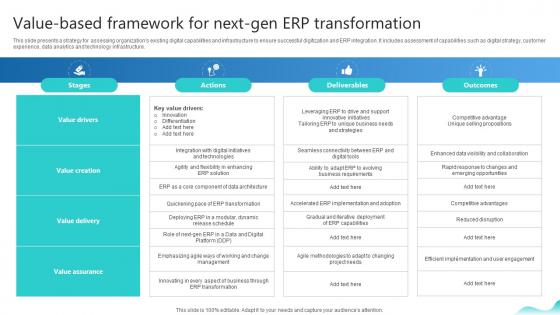
Value Based Framework For Next Gen Erp Transformation Erp And Digital Transformation For Maximizing DT SS V
This slide presents a strategy for assessing organizations existing digital capabilities and infrastructure to ensure successful digitization and ERP integration. It includes assessment of capabilities such as digital strategy, customer experience, data analytics and technology infrastructure. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Value Based Framework For Next Gen Erp Transformation Erp And Digital Transformation For Maximizing DT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Value Based Framework For Next Gen Erp Transformation Erp And Digital Transformation For Maximizing DT SS V today and make your presentation stand out from the rest This slide presents a strategy for assessing organizations existing digital capabilities and infrastructure to ensure successful digitization and ERP integration. It includes assessment of capabilities such as digital strategy, customer experience, data analytics and technology infrastructure.

Online Bookstore Business Plan Exploring Growth Drivers For Bookstore Industry BP SS V
This slide caters to details about various growth drivers resulting in bookstore industrys progress, such as increasing literacy rate to drive demand, increasing student population, increasing interest in reading, etc. It also gives confidence in the organization to achieve business goals. If you are looking for a format to display your unique thoughts, then the professionally designed Online Bookstore Business Plan Exploring Growth Drivers For Bookstore Industry BP SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Online Bookstore Business Plan Exploring Growth Drivers For Bookstore Industry BP SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide caters to details about various growth drivers resulting in bookstore industrys progress, such as increasing literacy rate to drive demand, increasing student population, increasing interest in reading, etc. It also gives confidence in the organization to achieve business goals.

Online Bookstore Business Plan Quarterly Milestones For Successful Bookstore Growth BP SS V
The slide covers particular objectives or goals the organization intends to attain as part of its business plan. These are short-term quantifiable milestones to check off as the company progresses toward its overall goals of the firm. Presenting this PowerPoint presentation, titled Online Bookstore Business Plan Quarterly Milestones For Successful Bookstore Growth BP SS V, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Online Bookstore Business Plan Quarterly Milestones For Successful Bookstore Growth BP SS V. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Online Bookstore Business Plan Quarterly Milestones For Successful Bookstore Growth BP SS V that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The slide covers particular objectives or goals the organization intends to attain as part of its business plan. These are short-term quantifiable milestones to check off as the company progresses toward its overall goals of the firm.

Roadmap For Implementing Internet Of Things Exploring Google Cloud IoT Platform
This slide outlines the deployment for IoT platforms. The purpose of this slide is to highlight the steps that an organization should take while utilizing IoT platforms which include planning, requirement gathering, connectivity, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Roadmap For Implementing Internet Of Things Exploring Google Cloud IoT Platform a try. Our experts have put a lot of knowledge and effort into creating this impeccable Roadmap For Implementing Internet Of Things Exploring Google Cloud IoT Platform You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the deployment for IoT platforms. The purpose of this slide is to highlight the steps that an organization should take while utilizing IoT platforms which include planning, requirement gathering, connectivity, etc.

Training Schedule For It Teams To Utilize IoT Platforms Exploring Google Cloud IoT Platform
This slide represents the training schedule for IT teams in an organization to efficiently carry out tokenization. It includes the time slots for training, total days of training, and the modules to be covered in the training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Training Schedule For It Teams To Utilize IoT Platforms Exploring Google Cloud IoT Platform With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Training Schedule For It Teams To Utilize IoT Platforms Exploring Google Cloud IoT Platform today and make your presentation stand out from the rest This slide represents the training schedule for IT teams in an organization to efficiently carry out tokenization. It includes the time slots for training, total days of training, and the modules to be covered in the training.

Estimated Budget Of Secure Web Gateway Web Threat Protection System
This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Estimated Budget Of Secure Web Gateway Web Threat Protection System can be your best option for delivering a presentation. Represent everything in detail using Estimated Budget Of Secure Web Gateway Web Threat Protection System and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.

Secure Web Gateway For Remote And On Site Workers Web Threat Protection System
This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Do you know about Slidesgeeks Secure Web Gateway For Remote And On Site Workers Web Threat Protection System These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees.

Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Understanding Real World Use Cases Of Secure Web Gateway Web Threat Protection System and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.
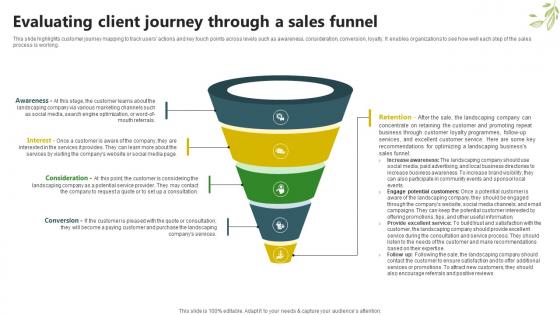
Sample Trugreen Business Plan Evaluating Client Journey Through A Sales Funnel BP SS V
This slide highlights customer journey mapping to track users actions and key touch points across levels such as awareness, consideration, conversion, loyalty. It enables organizations to see how well each step of the sales process is working. If you are looking for a format to display your unique thoughts, then the professionally designed Sample Trugreen Business Plan Evaluating Client Journey Through A Sales Funnel BP SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Sample Trugreen Business Plan Evaluating Client Journey Through A Sales Funnel BP SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide highlights customer journey mapping to track users actions and key touch points across levels such as awareness, consideration, conversion, loyalty. It enables organizations to see how well each step of the sales process is working.

Brand Equity Management To Raise Strategies To Establish Brand Differentiation
This slide presents the overview of brand positioning while discussing various strategies that allow the organization to differentiate itself from competitors and help reposition the brand. It includes techniques such as price positioning, quality or performance positioning, beneficiary positioning, category positioning, and psychological positioning. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Brand Equity Management To Raise Strategies To Establish Brand Differentiation. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Brand Equity Management To Raise Strategies To Establish Brand Differentiation today and make your presentation stand out from the rest. This slide presents the overview of brand positioning while discussing various strategies that allow the organization to differentiate itself from competitors and help reposition the brand. It includes techniques such as price positioning, quality or performance positioning, beneficiary positioning, category positioning, and psychological positioning.
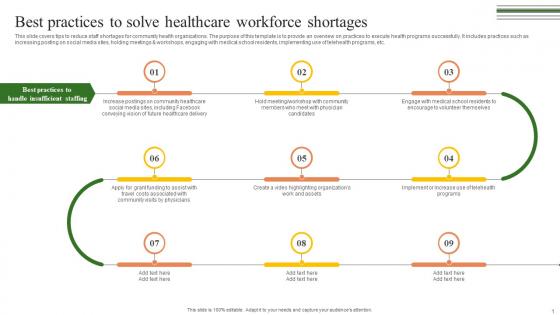
Best Practices To Solve Healthcare Building A Winning Community Outreach Strategy SS V
This slide covers tips to reduce staff shortages for community health organizations. The purpose of this template is to provide an overview on practices to execute health programs successfully. It includes practices such as increasing posting on social media sites, holding meetings and workshops, engaging with medical school residents, implementing use of telehealth programs, etc. Create an editable Best Practices To Solve Healthcare Building A Winning Community Outreach Strategy SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Best Practices To Solve Healthcare Building A Winning Community Outreach Strategy SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide covers tips to reduce staff shortages for community health organizations. The purpose of this template is to provide an overview on practices to execute health programs successfully. It includes practices such as increasing posting on social media sites, holding meetings and workshops, engaging with medical school residents, implementing use of telehealth programs, etc.

Community Health Outreach Program Building A Winning Community Outreach Strategy SS V
This slide covers schedule for the health campaign to be launched by community organizations. The purpose of this template is to provide an overview on time, date assigned for different locations to provide medical aid to public under health programs. It also includes key highlights of the program with contact information. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Community Health Outreach Program Building A Winning Community Outreach Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers schedule for the health campaign to be launched by community organizations. The purpose of this template is to provide an overview on time, date assigned for different locations to provide medical aid to public under health programs. It also includes key highlights of the program with contact information
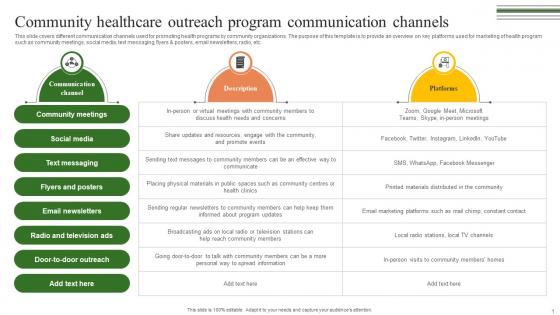
Community Healthcare Outreach Program Building A Winning Community Outreach Strategy SS V
This slide covers different communication channels used for promoting health programs by community organizations. The purpose of this template is to provide an overview on key platforms used for marketing of health program such as community meetings, social media, text messaging, flyers and posters, email newsletters, radio, etc. Present like a pro with Community Healthcare Outreach Program Building A Winning Community Outreach Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers different communication channels used for promoting health programs by community organizations. The purpose of this template is to provide an overview on key platforms used for marketing of health program such as community meetings, social media, text messaging, flyers and posters, email newsletters, radio, etc.
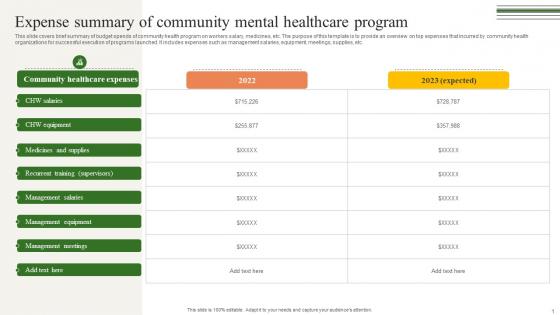
Expense Summary Of Community Mental Building A Winning Community Outreach Strategy SS V
This slide covers brief summary of budget spends of community health program on workers salary, medicines, etc. The purpose of this template is to provide an overview on top expenses that incurred by community health organizations for successful execution of programs launched. It includes expenses such as management salaries, equipment, meetings, supplies, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Expense Summary Of Community Mental Building A Winning Community Outreach Strategy SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide covers brief summary of budget spends of community health program on workers salary, medicines, etc. The purpose of this template is to provide an overview on top expenses that incurred by community health organizations for successful execution of programs launched. It includes expenses such as management salaries, equipment, meetings, supplies, etc.

Infrastructural Requirements For Building A Winning Community Outreach Strategy SS V
This slide covers requirements of infrastructure for community health programs and organizations. The purpose of this template is to provide guide to the health workers on arranging the infrastructure best suited such as office space, examination rooms, storage spaces, tele health equipment, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Infrastructural Requirements For Building A Winning Community Outreach Strategy SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Infrastructural Requirements For Building A Winning Community Outreach Strategy SS V This slide covers requirements of infrastructure for community health programs and organizations. The purpose of this template is to provide guide to the health workers on arranging the infrastructure best suited such as office space, examination rooms, storage spaces, tele health equipment, etc.

Mental Health Awareness Activities Planned Building A Winning Community Outreach Strategy SS V
This slide covers key activities that are expected to be performed by community health organizations under various schemes launched. The purpose of this template is to provide an overview on calendar defining activities scheduled along with dates for new financial year. The Mental Health Awareness Activities Planned Building A Winning Community Outreach Strategy SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide covers key activities that are expected to be performed by community health organizations under various schemes launched. The purpose of this template is to provide an overview on calendar defining activities scheduled along with dates for new financial year.

Mental Health Campaign Launched With Building A Winning Community Outreach Strategy SS V
This slide covers launching of mental health campaign by community organizations. The purpose of this template is to provide an overview on benefits of launching health programs along with requirement of minimum members of board. It includes benefits such as raising awareness about importance of mental health, providing information about local mental health resources and services, etc. Are you searching for a Mental Health Campaign Launched With Building A Winning Community Outreach Strategy SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Mental Health Campaign Launched With Building A Winning Community Outreach Strategy SS V from Slidegeeks today. This slide covers launching of mental health campaign by community organizations. The purpose of this template is to provide an overview on benefits of launching health programs along with requirement of minimum members of board. It includes benefits such as raising awareness about importance of mental health, providing information about local mental health resources and services, etc.
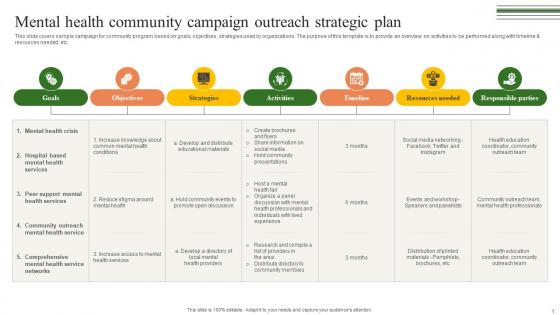
Mental Health Community Campaign Building A Winning Community Outreach Strategy SS V
This slide covers sample campaign for community program based on goals, objectives, strategies used by organizations. The purpose of this template is to provide an overview on activities to be performed along with timeline and resources needed, etc. Retrieve professionally designed Mental Health Community Campaign Building A Winning Community Outreach Strategy SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide covers sample campaign for community program based on goals, objectives, strategies used by organizations. The purpose of this template is to provide an overview on activities to be performed along with timeline and resources needed, etc.
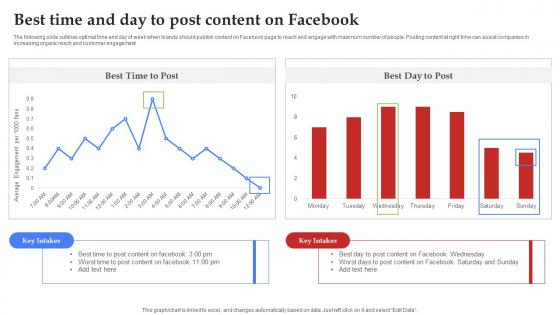
Facebook Marketing Plan Best Time And Day To Post Content On Facebook Strategy SS V
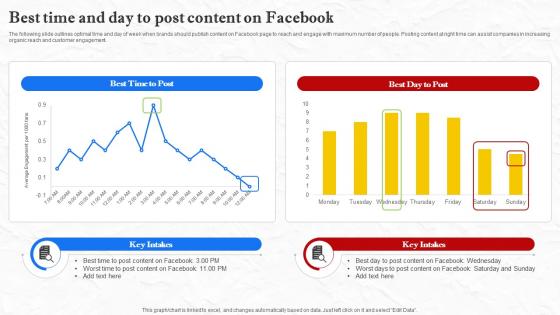
Facebook Marketing Techniques Best Time And Day To Post Content On Facebook Strategy SS V
The following slide outlines optimal time and day of week when brands should publish content on Facebook page to reach and engage with maximum number of people. Posting content at right time can assist companies in increasing organic reach and customer engagement. Present like a pro with Facebook Marketing Techniques Best Time And Day To Post Content On Facebook Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide outlines optimal time and day of week when brands should publish content on Facebook page to reach and engage with maximum number of people. Posting content at right time can assist companies in increasing organic reach and customer engagement.
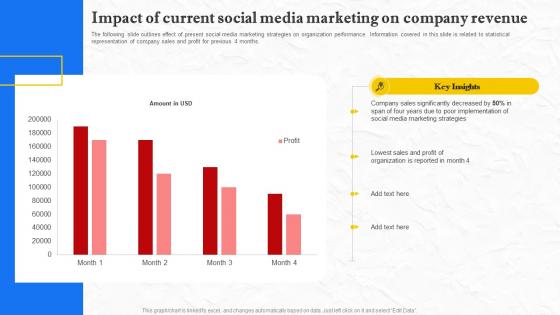
Facebook Marketing Techniques Impact Of Current Social Media Marketing Strategy SS V
The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Facebook Marketing Techniques Impact Of Current Social Media Marketing Strategy SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Facebook Marketing Techniques Impact Of Current Social Media Marketing Strategy SS V. The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months.
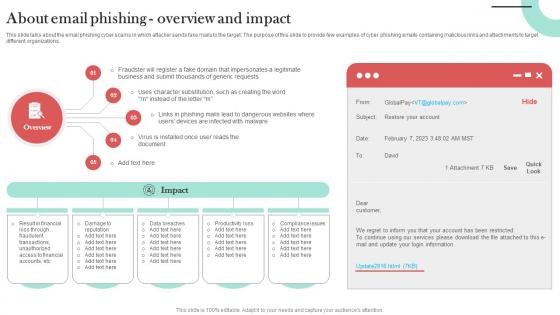
About Email Phishing Overview And Impact Man In The Middle Phishing IT
This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations. Create an editable About Email Phishing Overview And Impact Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Email Phishing Overview And Impact Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations.
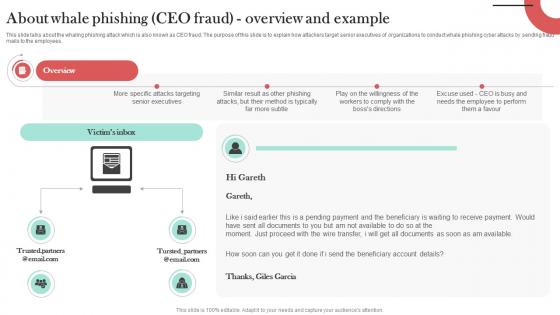
About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT
This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees. Find highly impressive About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees.

Benefits Of Comprehensive Training Programs Man In The Middle Phishing IT
This slide outlines the benefits of comprehensive training programs in organizations. These include align with companys database, instructional library, auto-enrolment service, inform about real risks, track and evaluate and plan a year ahead. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Benefits Of Comprehensive Training Programs Man In The Middle Phishing IT and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the benefits of comprehensive training programs in organizations. These include align with companys database, instructional library, auto-enrolment service, inform about real risks, track and evaluate and plan a year ahead.
Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT
This slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT This slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk.
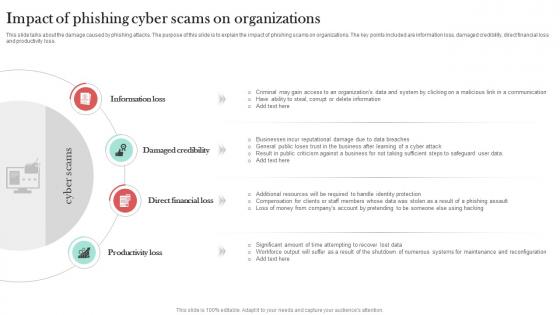
Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT
This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT. This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss.
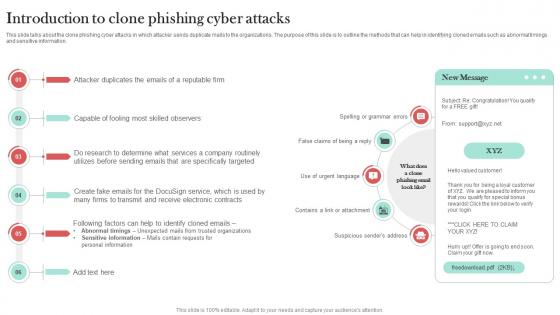
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.
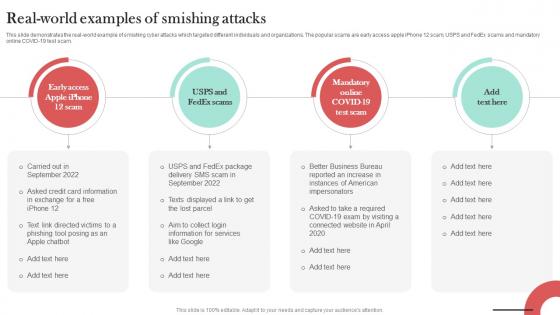
Real World Examples Of Smishing Attacks Man In The Middle Phishing IT
This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Real World Examples Of Smishing Attacks Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Real World Examples Of Smishing Attacks Man In The Middle Phishing IT today and make your presentation stand out from the rest This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam.
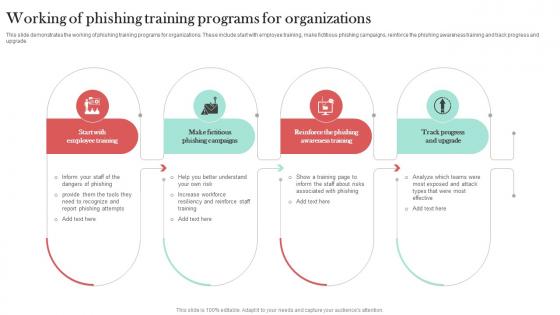
Working Of Phishing Training Programs Man In The Middle Phishing IT
This slide demonstrates the working of phishing training programs for organizations. These include start with employee training, make fictitious phishing campaigns, reinforce the phishing awareness training and track progress and upgrade. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Working Of Phishing Training Programs Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Working Of Phishing Training Programs Man In The Middle Phishing IT. This slide demonstrates the working of phishing training programs for organizations. These include start with employee training, make fictitious phishing campaigns, reinforce the phishing awareness training and track progress and upgrade.

Wine Lounge Business Plan Implementing Quarterly Milestones For Successful Business BP SS V
The slide covers particular objectives or goals that the organization intends to attain as part of its business plan. These are short-term quantifiable milestones to check off as the company progresses toward its overall goals of the firm. This modern and well-arranged Wine Lounge Business Plan Implementing Quarterly Milestones For Successful Business BP SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide covers particular objectives or goals that the organization intends to attain as part of its business plan. These are short-term quantifiable milestones to check off as the company progresses toward its overall goals of the firm.
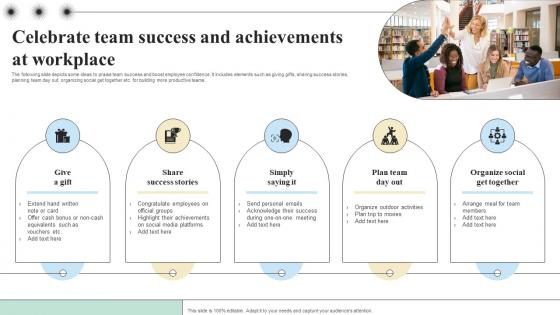
Celebrate Team Success And Achievements Objectives And Key Result Methodology For Business
The following slide depicts some ideas to praise team success and boost employee confidence. It includes elements such as giving gifts, sharing success stories, planning team day out, organizing social get together etc. for building more productive teams. Get a simple yet stunning designed Celebrate Team Success And Achievements Objectives And Key Result Methodology For Business. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Celebrate Team Success And Achievements Objectives And Key Result Methodology For Business can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide depicts some ideas to praise team success and boost employee confidence. It includes elements such as giving gifts, sharing success stories, planning team day out, organizing social get together etc. for building more productive teams.
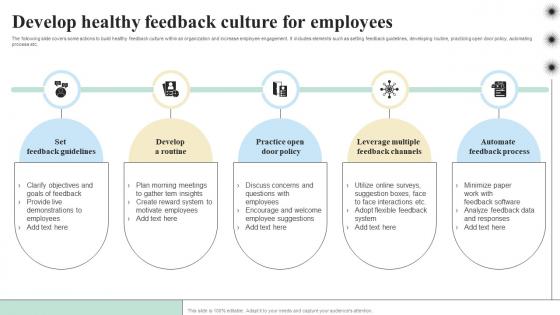
Develop Healthy Feedback Culture Fo Objectives And Key Result Methodology For Business
The following slide covers some actions to build healthy feedback culture within an organization and increase employee engagement. It includes elements such as setting feedback guidelines, developing routine, practicing open door policy, automating process etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Develop Healthy Feedback Culture Fo Objectives And Key Result Methodology For Business. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Develop Healthy Feedback Culture Fo Objectives And Key Result Methodology For Business today and make your presentation stand out from the rest The following slide covers some actions to build healthy feedback culture within an organization and increase employee engagement. It includes elements such as setting feedback guidelines, developing routine, practicing open door policy, automating process etc.
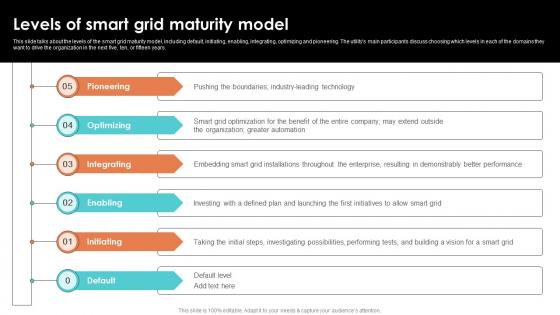
Levels Of Smart Grid Maturity Model Smart Grid Working
This slide talks about the levels of the smart grid maturity model, including default, initiating, enabling, integrating, optimizing and pioneering. The utilitys main participants discuss choosing which levels in each of the domains they want to drive the organization in the next five, ten, or fifteen years. This modern and well arranged Levels Of Smart Grid Maturity Model Smart Grid Working provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide talks about the levels of the smart grid maturity model, including default, initiating, enabling, integrating, optimizing and pioneering. The utilitys main participants discuss choosing which levels in each of the domains they want to drive the organization in the next five, ten, or fifteen years.
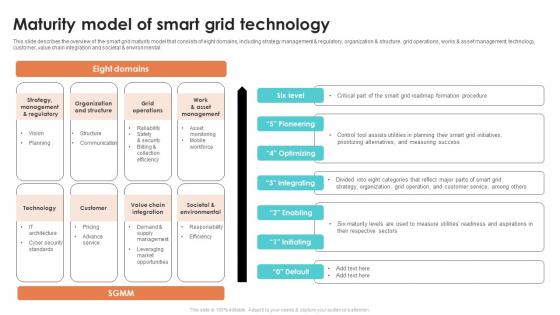
Maturity Model Of Smart Grid Technology Smart Grid Working
This slide describes the overview of the smart grid maturity model that consists of eight domains, including strategy management and regulatory, organization and structure, grid operations, works and asset management, technology, customer, value chain integration and societal and environmental. Welcome to our selection of the Maturity Model Of Smart Grid Technology Smart Grid Working These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today. This slide describes the overview of the smart grid maturity model that consists of eight domains, including strategy management and regulatory, organization and structure, grid operations, works and asset management, technology, customer, value chain integration and societal and environmental.

Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
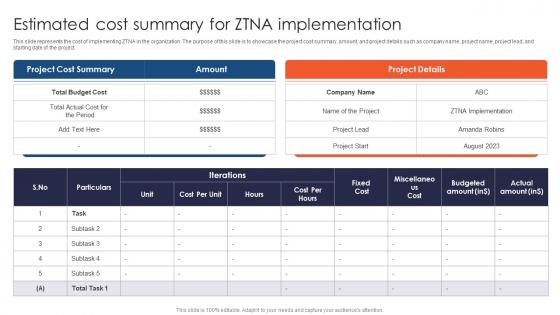
Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation
This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Are you searching for a Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access Estimated Cost Summary For ZTNA Implementation from Slidegeeks today. This slide represents the cost of implementing ZTNA in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project.

Zero Trust Network Access Key Points To Choose Zero Trust Solution
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This Zero Trust Network Access Key Points To Choose Zero Trust Solution from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Zero Trust Network Access Timeline To Implement Zero Trust Network Access Model This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on.
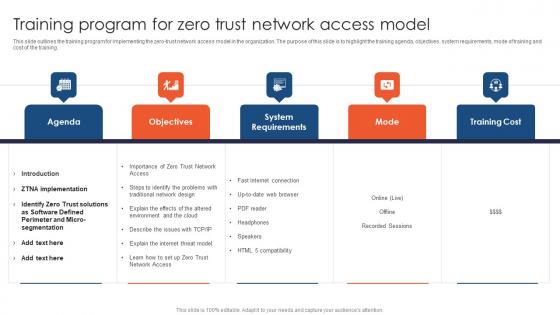
Zero Trust Network Access Training Program For Zero Trust Network Access Model
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Explore a selection of the finest Zero Trust Network Access Training Program For Zero Trust Network Access Model here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Training Program For Zero Trust Network Access Model to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Get a simple yet stunning designed CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit CASB 2 0 IT Best Practices To Implement Cloud Access Security Broker can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB.
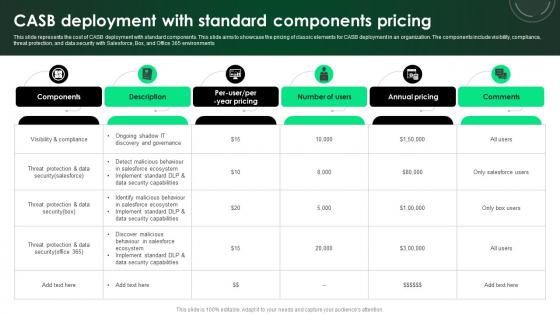
CASB 2 0 IT CASB Deployment With Standard Components Pricing
This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CASB 2 0 IT CASB Deployment With Standard Components Pricing can be your best option for delivering a presentation. Represent everything in detail using CASB 2 0 IT CASB Deployment With Standard Components Pricing and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the cost of CASB deployment with standard components. This slide aims to showcase the pricing of classic elements for CASB deployment in an organization. The components include visibility, compliance, threat protection, and data security with Salesforce, Box, and Office 365 environments
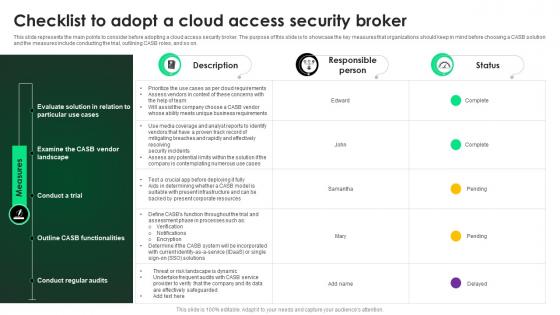
CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Checklist To Adopt A Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers. This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on.
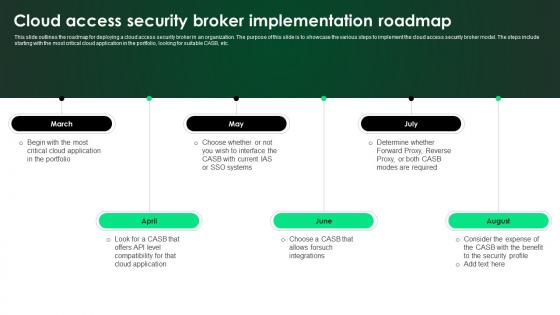
CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Welcome to our selection of the CASB 2 0 IT Cloud Access Security Broker Implementation Roadmap. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc.
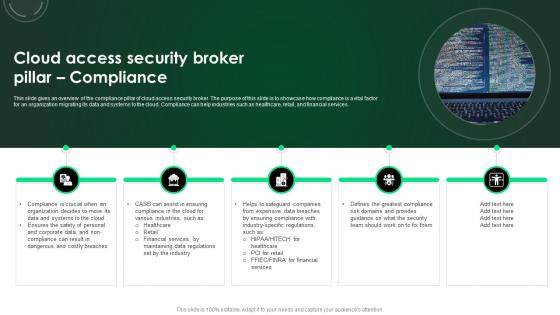
CASB 2 0 IT Cloud Access Security Broker Pillar Compliance
This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CASB 2 0 IT Cloud Access Security Broker Pillar Compliance from Slidegeeks and deliver a wonderful presentation. This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services.
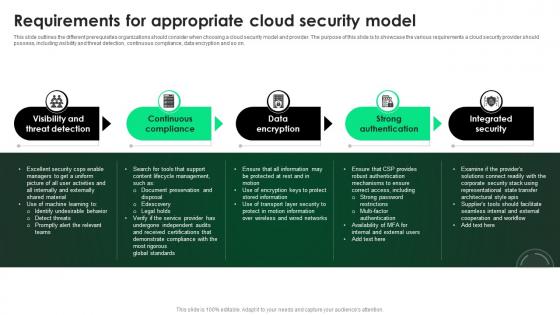
CASB 2 0 IT Requirements For Appropriate Cloud Security Model
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Find highly impressive CASB 2 0 IT Requirements For Appropriate Cloud Security Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CASB 2 0 IT Requirements For Appropriate Cloud Security Model for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on.

CASB 2 0 IT Steps To Deploy Cloud Access Security Broker
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CASB 2 0 IT Steps To Deploy Cloud Access Security Broker template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CASB 2 0 IT Steps To Deploy Cloud Access Security Broker that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model.


 Continue with Email
Continue with Email

 Home
Home


































