Mobile Security

Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF
The following slide showcases solution offered by IT company for its customers which are see the new network, know current threats and protect with high ROI. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
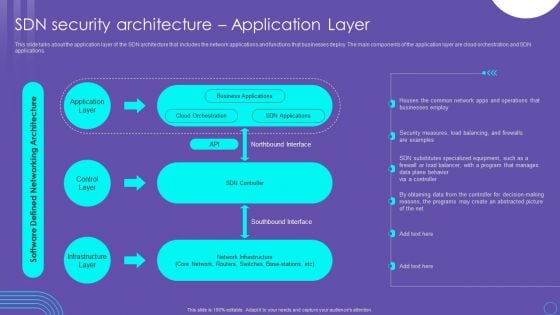
SDN Security Architecture Application Layer Ppt PowerPoint Presentation File Inspiration PDF
This slide talks about the application layer of the SDN architecture that includes the network applications and functions that businesses deploy. The main components of the application layer are cloud orchestration and SDN applications. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit SDN Security Architecture Application Layer Ppt PowerPoint Presentation File Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF
This template depicts that Facebook Ads needs three parts to run such as a campaign, ad set, and ad. All these parts are called campaign structure and help run ads the way the company wants and reach the right prospects.his is a Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Powerful Consisting, Features Campaigns, Define Creative. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
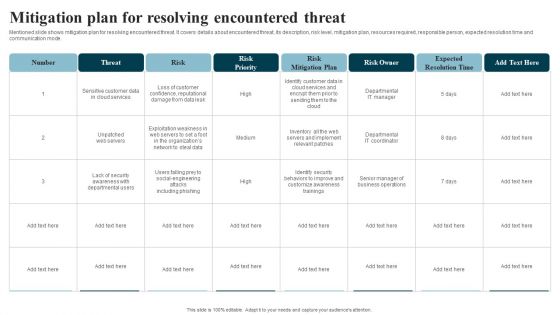
Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Developing IT Security Strategy Mitigation Plan For Resolving Encountered Threat Diagrams PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
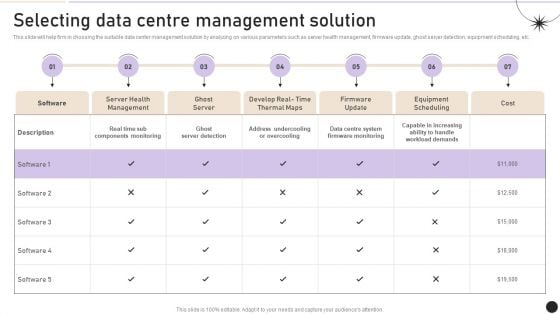
Selecting Data Centre Management Solution Workplace Security Management Program Information PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Selecting Data Centre Management Solution Workplace Security Management Program Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf
The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc.

Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Endpoint Initiated Zero Trust Network Topology Zero Trust Network Security Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Consequence Worksite Injuries Workplace Safety Protocol And Security Practices Infographics Pdf
This slide highlights the consequences of accidents on workers and employers which includes loss of job, loss of income, and damage to organization equipments etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Consequence Worksite Injuries Workplace Safety Protocol And Security Practices Infographics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide highlights the consequences of accidents on workers and employers which includes loss of job, loss of income, and damage to organization equipments etc.

Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Beginners Guide To Commercial Biometric Technology For Enhancing Online Security Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data.
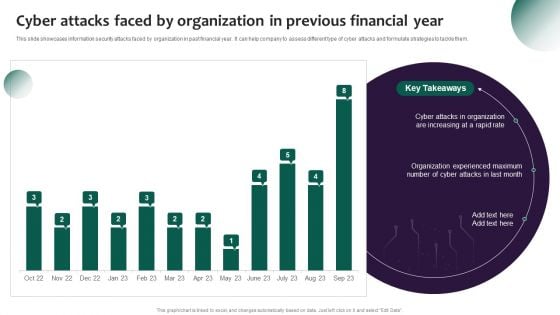
Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
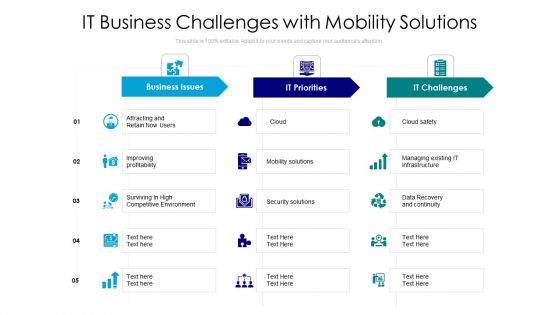
IT Business Challenges With Mobility Solutions Ppt PowerPoint Presentation File Example Topics PDF
Presenting it business challenges with mobility solutions ppt powerpoint presentation file example topics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including mobility solutions, cloud safety, security solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Enterprise Mobility Management Template Sample Ppt Files
This is a enterprise mobility management template sample ppt files. This is a eight stage process. The stages in this process are expense management, security management, application management, service management, policy and governance, sourcing, change management macd, device management.
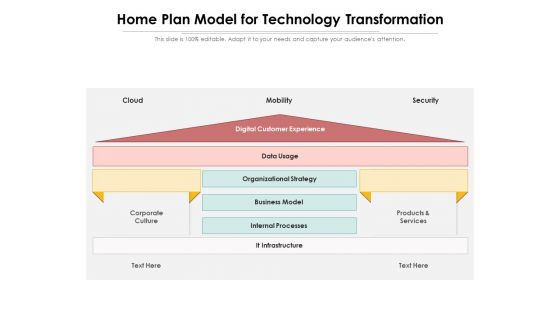
Home Plan Model For Technology Transformation Ppt PowerPoint Presentation Gallery Model PDF
Presenting home plan model for technology transformation ppt powerpoint presentation gallery model pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including cloud, mobility, security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
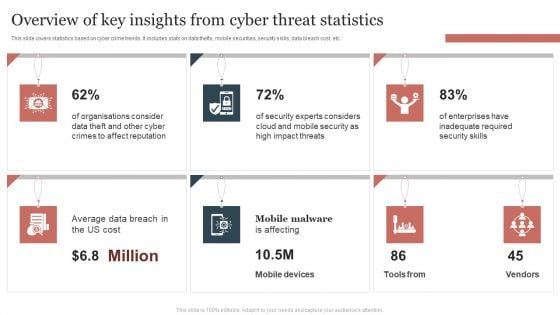
Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
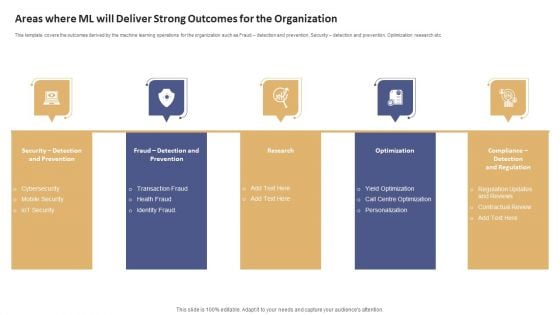
Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF
This template covers the outcomes derived by the machine learning operations for the organization such as Fraud detection and prevention, Security detection and prevention, Optimization research etc. Presenting Data Processing Services Delivery Areas Where ML Will Deliver Strong Outcomes Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Mobile Security, IoT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Advertising Website Template Powerpoint Templates
This is a advertising website template powerpoint templates. This is a eight stage process. The stages in this process are pay per click, online shop, mobile advertising, security, social network, advertising, email marketing, affiliate marketing.
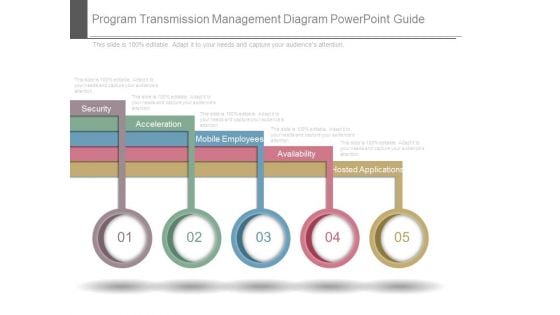
Program Transmission Management Diagram Powerpoint Guide
This is a program transmission management diagram powerpoint guide. This is a five stage process. The stages in this process are security, acceleration, mobile employees, availability, hosted applications.

Secure Online Banking For Money Transfer Background PDF
Persuade your audience using this secure online banking for money transfer background pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including secure online banking for money transfer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Process Of Enterprise Mobility Solutions Ppt Powerpoint Slide Themes
This is a process of enterprise mobility solutions ppt powerpoint slide themes. This is a eight stage process. The stages in this process are user and app access, app and data protection, device management, threat protection, secure file sharing, cost and resources, augment income, easy access to confidential data.
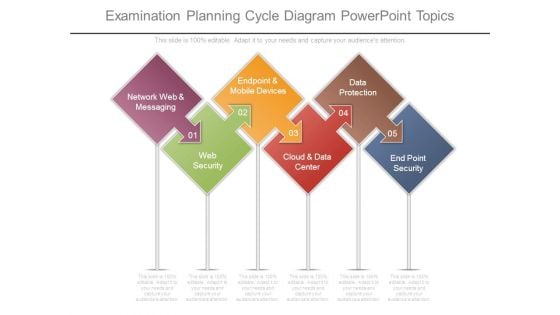
Examination Planning Cycle Diagram Powerpoint Topics
This is a examination planning cycle diagram powerpoint topics. This is a five stage process. The stages in this process are network web and messaging, web security, endpoint and mobile devices, cloud and data center, data protection, end point security.
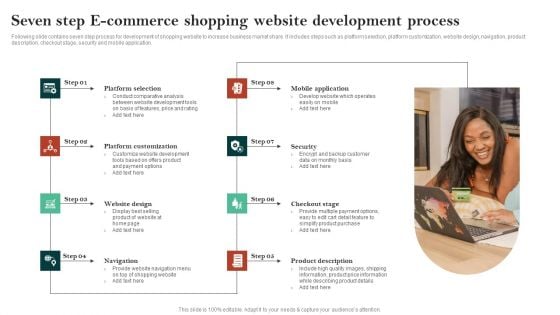
Seven Step E Commerce Shopping Website Development Process Guidelines PDF
Following slide contains seven step process for development of shopping website to increase business market share. It includes steps such as platform selection, platform customization, website design, navigation, product description, checkout stage, security and mobile application. Presenting Seven Step E Commerce Shopping Website Development Process Guidelines PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Platform Selection, Mobile Application, Security, Checkout Stage, Product Description. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
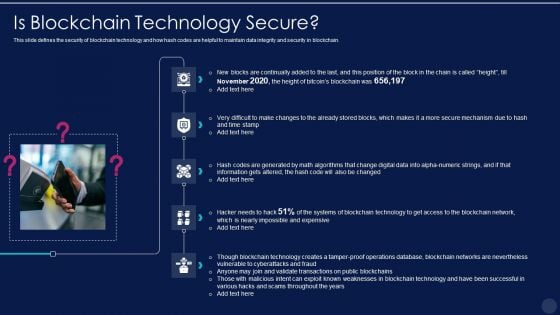
Blockchain Technology Framework IT Is Blockchain Technology Secure Demonstration PDF
This slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. This is a blockchain technology framework it is blockchain technology secure demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like expensive, systems, blockchain network, operations database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
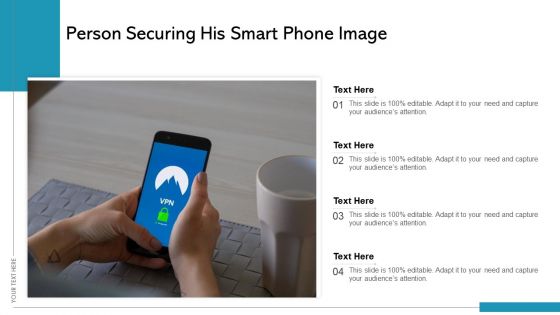
Person Securing His Smart Phone Image Ppt Gallery Ideas PDF
Persuade your audience using this person securing his smart phone image ppt gallery ideas pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including person securing his smart phone image. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Banking Application For Secure Fund Transfer Icon Ppt Summary Designs Download PDF
Persuade your audience using this Banking Application For Secure Fund Transfer Icon Ppt Summary Designs Download PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Banking Application, Secure Fund Transfer, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Secured Video Hosting Platform Investor Capital Funding Future Initiatives By Online Video Hosting Platform Sample PDF
This slide caters details about future initiatives by online video hosting platform that will focus on leveraging relationships with members or clients or subscribers across globe. This is a secured video hosting platform investor capital funding future initiatives by online video hosting platform sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like future initiatives by online video hosting platform. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
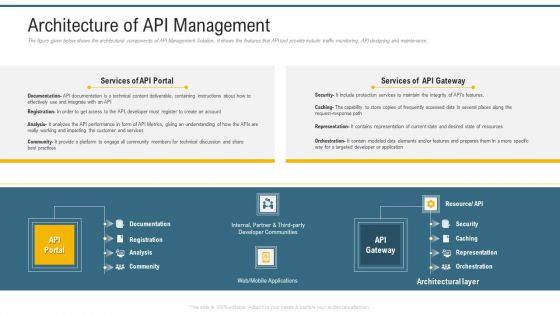
Application Programming Interface Administrative Marketplace Architecture Of API Management Clipart PDF
The figure given below shows the architectural components of API Management Solution. It shows the features that API tool provide include traffic monitoring, API designing and maintenance. Deliver and pitch your topic in the best possible manner with this application programming interface administrative marketplace architecture of api management clipart pdf. Use them to share invaluable insights on analysis, community, mobile applications, security, resource and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
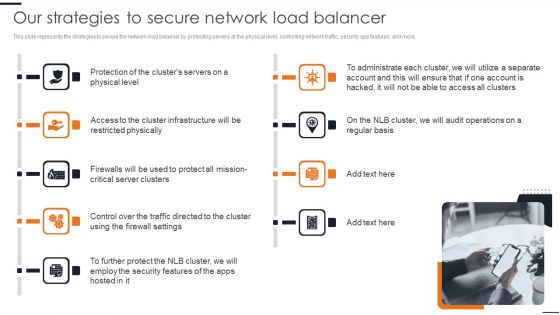
Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. This modern and well arranged Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Smart Phone Data Transfer Via Secured Network Image Ppt Show Graphics PDF
Presenting smart phone data transfer via secured network image ppt show graphics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including smart phone data safety application with protection shield. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
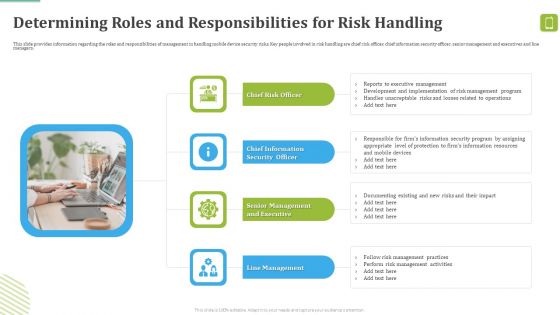
MDM Strategies At Office Determining Roles And Responsibilities For Risk Handling Formats PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Presenting MDM Strategies At Office Determining Roles And Responsibilities For Risk Handling Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Chief Information, Senior Management, Line Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
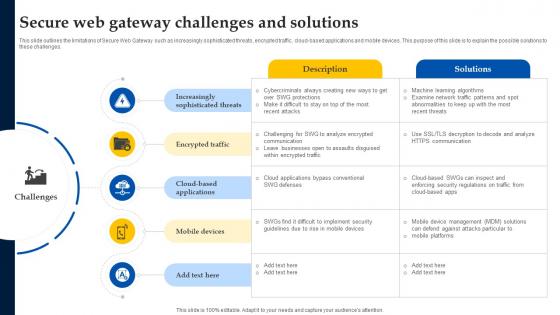
Web Access Control Solution Secure Web Gateway Challenges And Solutions
This slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges. Want to ace your presentation in front of a live audience Our Web Access Control Solution Secure Web Gateway Challenges And Solutions can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges.

Secure Web Gateway Challenges And Solutions Web Threat Protection System
This slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges. Take your projects to the next level with our ultimate collection of Secure Web Gateway Challenges And Solutions Web Threat Protection System. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges.
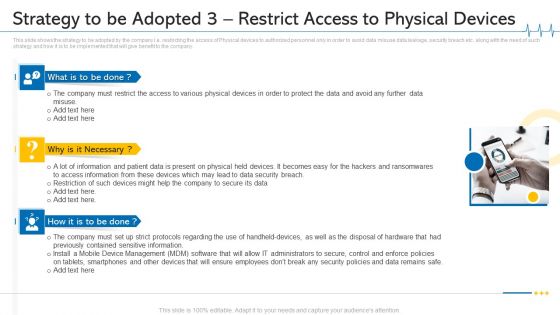
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 3 Restrict Access To Physical Devices Ideas PDF
This slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. This is a minimize cloud risks medical care business case competition strategy to be adopted 3 restrict access to physical devices ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like mobile device management, data security breach, physical devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secure Internet Access Computer PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with transparent internet browser with a large chrome key protruding out from the window Recognize your calling with our Secure Internet Access Computer PowerPoint Templates And PowerPoint Backgrounds 0811. Download without worries with our money back guaranteee.

Secured Money Finance PowerPoint Templates And PowerPoint Themes 1112
We present our Secured Money Finance PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because,To strive to give true form to your great dream. Use our Success PowerPoint Templates because, Highlight your ideas broad- based on strong fundamentals and illustrate how they step by step acheive the set growth factor. Use our Signs PowerPoint Templates because, Develop your marketing strategy and communicate your ethusiasm and motivation to raise the bar. Use our Money PowerPoint Templates because, Anticipate the doubts and questions in the minds of your colleagues and enlighten them with your inspired strategy to garner desired success. Use our Business PowerPoint Templates because,Marketing Strategy Business Template:- Maximising sales of your product is the intended destination.Use these PowerPoint slides for presentations relating to Protection of money, security, success, money, signs, business. The prominent colors used in the PowerPoint template are Blue navy, Black, Yellow Make a great career call with our Secured Money Finance PowerPoint Templates And PowerPoint Themes 1112. Put your ideas across emphatically.

Future Of Secure Web Gateway Technology Web Threat Protection System
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Future Of Secure Web Gateway Technology Web Threat Protection System and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.

Zero Trust Model Comparison Between ZTNA And Secure Access Service
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Model Comparison Between ZTNA And Secure Access Service and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
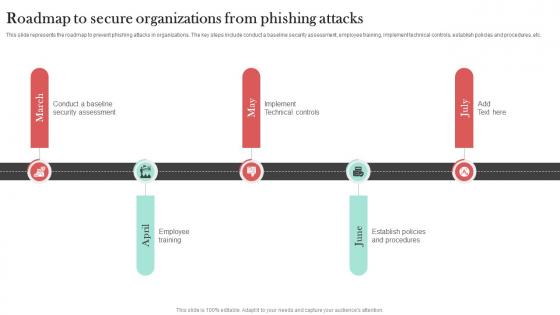
Roadmap To Secure Organizations Man In The Middle Phishing IT
This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Roadmap To Secure Organizations Man In The Middle Phishing IT and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
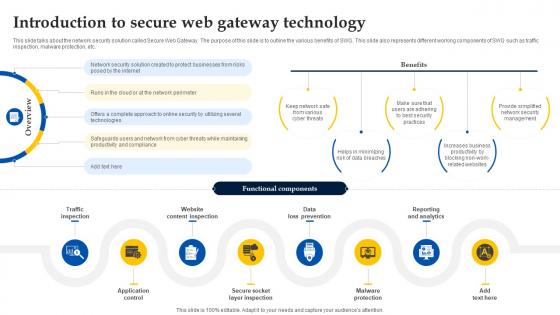
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.

Web Access Control Solution Checklist To Implement Secure Web Gateway
This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Web Access Control Solution Checklist To Implement Secure Web Gateway and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.

Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. This Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Data Breach Response Plan Secure Operations Data Fortification Strengthening Defenses features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc.
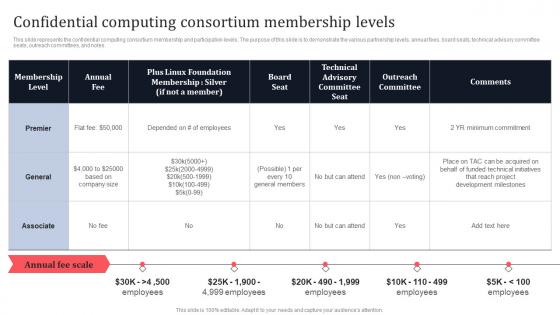
Confidential Computing Consortium Membership Levels Secure Multi Party Themes Pdf
This slide represents the confidential computing consortium membership and participation levels. The purpose of this slide is to demonstrate the various partnership levels, annual fees, board seats, technical advisory committee seats, outreach committees, and notes. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Confidential Computing Consortium Membership Levels Secure Multi Party Themes Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents the confidential computing consortium membership and participation levels. The purpose of this slide is to demonstrate the various partnership levels, annual fees, board seats, technical advisory committee seats, outreach committees, and notes.
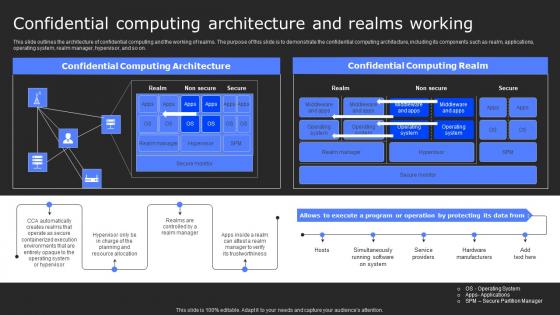
Confidential Computing Architecture And Secure Computing Framework Graphics Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Confidential Computing Architecture And Secure Computing Framework Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.

Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.
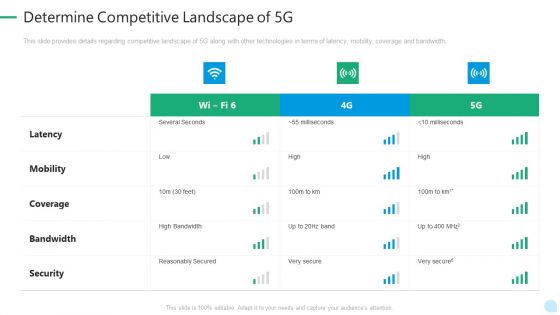
5G Network Technology Determine Competitive Landscape Of 5G Ppt Summary Visual Aids PDF
This slide provides details regarding competitive landscape of 5G along with other technologies in terms of latency, mobility, coverage and bandwidth. Deliver and pitch your topic in the best possible manner with this 5g network technology determine competitive landscape of 5g ppt summary visual aids pdf. Use them to share invaluable insights on latency, mobility, coverage, bandwidth, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
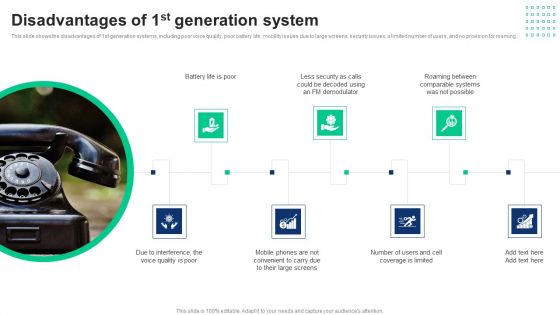
1G To 5G Cellular Disadvantages Of 1St Generation System Microsoft PDF
This slide shows the disadvantages of 1st generation systems, including poor voice quality, poor battery life, mobility issues due to large screens, security issues, a limited number of users, and no provision for roaming. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 1G To 5G Cellular Disadvantages Of 1St Generation System Microsoft PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 1G To 5G Cellular Disadvantages Of 1St Generation System Microsoft PDF.
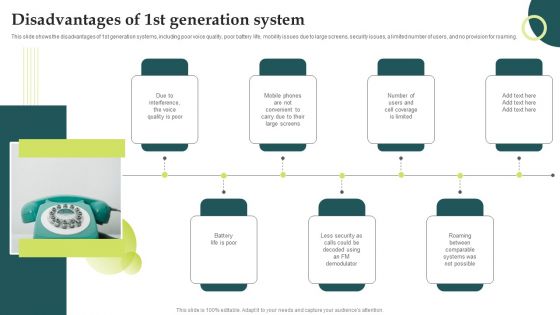
Evolution Of Wireless Technologies Disadvantages Of 1St Generation System Brochure PDF
This slide shows the disadvantages of 1st generation systems, including poor voice quality, poor battery life, mobility issues due to large screens, security issues, a limited number of users, and no provision for roaming. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Evolution Of Wireless Technologies Disadvantages Of 1St Generation System Brochure PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Evolution Of Wireless Technologies Disadvantages Of 1St Generation System Brochure PDF today and make your presentation stand out from the rest.
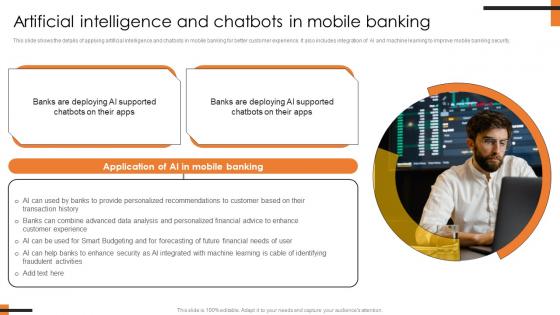
Artificial Intelligence And Chatbots In Comprehensive Smartphone Banking Download Pdf
This slide shows the details of applying artificial intelligence and chatbots in mobile banking for better customer experience. It also includes integration of AI and machine learning to improve mobile banking security.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Artificial Intelligence And Chatbots In Comprehensive Smartphone Banking Download Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide shows the details of applying artificial intelligence and chatbots in mobile banking for better customer experience. It also includes integration of AI and machine learning to improve mobile banking security.

Benefits Of Migrating Legacy Application To Cloud Technology Themes PDF
This slide defines the reasons of migrating legacy system to the cloud technology. It includes information related to scalability, cost saving, security, mobility and business continuity. Showcasing this set of slides titled Benefits Of Migrating Legacy Application To Cloud Technology Themes PDF. The topics addressed in these templates are Cost Savings, Mobility, Business Continuity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
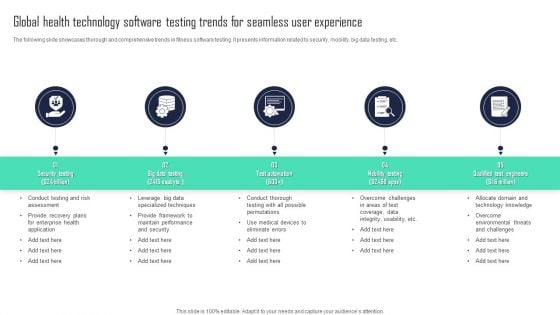
Global Health Technology Software Testing Trends For Seamless User Experience Inspiration PDF
The following slide showcases thorough and comprehensive trends in fitness software testing. It presents information related to security, mobility, big data testing, etc. Presenting Global Health Technology Software Testing Trends For Seamless User Experience Inspiration PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Mobility Testing, Test Automation, Qualified Test Engineers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Workplace Portable Device Monitoring And Administration Determining Roles And Responsibilities For Risk Handling Designs PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. This modern and well arranged Workplace Portable Device Monitoring And Administration Determining Roles And Responsibilities For Risk Handling Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint
This slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Applications And Use Cases Of Tokenization Securing Your Data Ppt Powerpoint from Slidegeeks and deliver a wonderful presentation. This slide discusses various application fields of tokenization. The purpose of this slide is to highlight the areas of application which include mobile wallet services, online retail platforms, etc.

Industry Transformation Approaches Banking Sector Employee Development Top Digital Industry Trends Of Banking Mockup PDF
This slide shows some of the top digital industry trends in banking that are most widely adopted such as seamless payments, next gen and digital banks, mobile applications, robotics process automation and ai artificial intelligence, cybersecurity etc. This is a industry transformation approaches banking sector employee development top digital industry trends of banking mockup pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like seamless payments, mobile applications, cyber security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
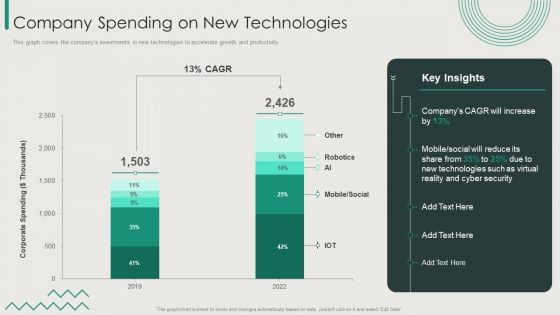
Organization Transition Company Spending On New Technologies Ppt PowerPoint Presentation Gallery Good PDF
This graph covers the companys investments in new technologies to accelerate growth and productivity. Deliver an awe inspiring pitch with this creative Organization Transition Company Spending On New Technologies Ppt PowerPoint Presentation Gallery Good PDF bundle. Topics like Mobile, Social, Cyber Security, New Technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Transformational IT Trends In Oil And Gas Industry Download PDF
This slide highlights mega trends in oil and gas industry aimed at facing legislation, competition, changes in market to maintain increased sustainability. It covers cloud messaging, security and operational risk management, smart mobility and smart and oil gas fields. Persuade your audience using this Transformational IT Trends In Oil And Gas Industry Download PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Messaging, Smart Mobility, Smart Oil Gas Fields, Security And Operational, Risk Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Six Online Marketing For Ecommerce Businesses Strategies For Hotels To Increase Customer Rules PDF
This slide covers six ecommerce strategies to increase customers for hospitality sector. This includes strategies such as use high resolution photos, build your credibility, make it extremely easy to book room in hotel, make your website easy to navigate, website is mobile friendly and secure for financial transactions. Showcasing this set of slides titled six online marketing for ecommerce businesses strategies for hotels to increase customer rules pdf. The topics addressed in these templates are build credibility, financial transactions, resolution photos. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
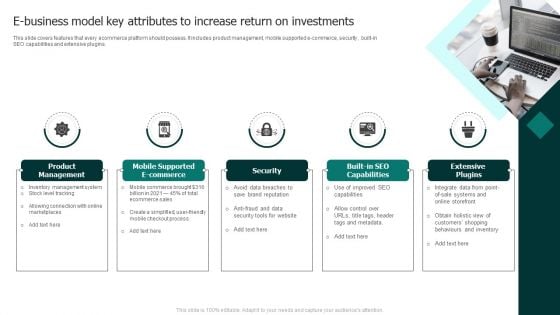
E Business Model Key Attributes To Increase Return On Investments Guidelines PDF
This slide covers features that every ecommerce platform should possess. It includes product management, mobile supported e commerce, security , built-in SEO capabilities and extensive plugins.Presenting E Business Model Key Attributes To Increase Return On Investments Guidelines PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Product Management, Mobile Supported, Built SEO Capabilities . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Page Experience Signals In Google Search Console Training Ppt
This slide covers search signals for page experience largely known as core web vitals. It also includes KPIs such as mobile-friendly experience, safe browsing experience, HTTPS security and no intrusive interstitials.
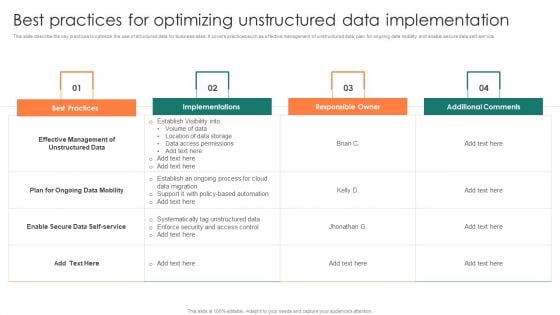
Best Practices For Optimizing Unstructured Data Implementation Ideas PDF
This slide describe the key practices to optimize the use of structured data for business sites. It covers practices such as effective management of unstructured data, plan for ongoing data mobility and enable secure data self-service. Showcasing this set of slides titled Best Practices For Optimizing Unstructured Data Implementation Ideas PDF. The topics addressed in these templates are Best Practices, Implementations, Responsible Owner, Additional Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































