Network Access Control
Knowledge Management Challenges Template Ppt Inspiration
This is a knowledge management challenges template ppt inspiration. This is a eight stage process. The stages in this process are effectiveness, performance support, access to experts, social networking and collaboration, knowledge management, relevance, structured learning, organization.
Small Business Management Diagram Presentation Pictures
This is a small business management diagram presentation pictures. This is a seven stage process. The stages in this process are output and exports, taxes govt revenues, poverty alleviation, youth entrepreneurship, networks mentoring and coaching, supportive environment, access to capital.
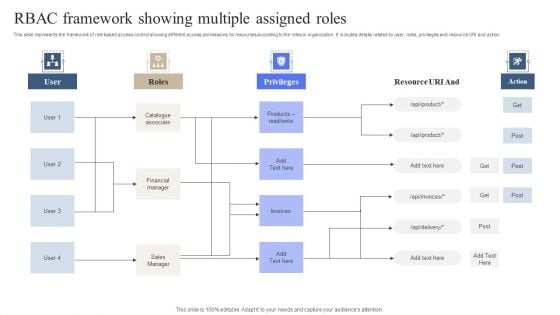
RBAC Framework Showing Multiple Assigned Roles Download PDF
This slide represents the framework of role based access control showing different access permissions for resources according to the roles in organization. It includes details related to user, roles, privileges and resource URI and action. Pitch your topic with ease and precision using this RBAC Framework Showing Multiple Assigned Roles Download PDF. This layout presents information on Catalogue Associate, Financial Manager, Sales Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Learning Solutions Layout Powerpoint Shapes
This is a learning solutions layout powerpoint shapes. This is a six stage process. The stages in this process are structured learning, management, organization, learning solutions layout, social networking and collaboration, performance support, access to experts.
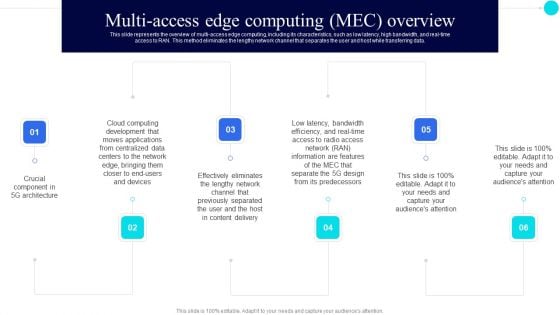
Multiaccess Edge Computing Mec Overview 5G Functional Architecture Themes PDF
This slide represents the overview of multi-access edge computing, including its characteristics, such as low latency, high bandwidth, and real-time access to RAN. This method eliminates the lengthy network channel that separates the user and host while transferring data.This is a Multiaccess Edge Computing Mec Overview 5G Functional Architecture Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Previously Separated, Centralized Data, Low Latency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
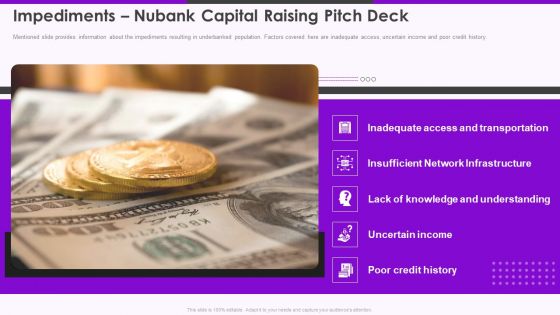
Impediments Nubank Capital Raising Pitch Deck Slide2 Ppt Slides Template PDF
Mentioned slide provides information about the impediments resulting in underbanked population. Factors covered here are inadequate access, uncertain income and poor credit history. This is a impediments nubank capital raising pitch deck slide2 ppt slides template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insufficient network infrastructure, inadequate access and transportation, lack of knowledge and understanding, uncertain income, poor credit history. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
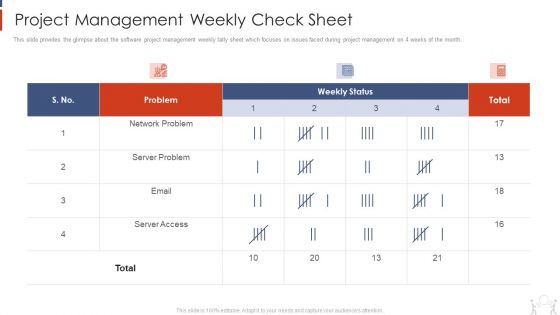
Project Management Modelling Techniques IT Project Management Weekly Check Sheet Inspiration PDF
This slide provides the glimpse about the software project management weekly tally sheet which focuses on issues faced during project management on 4 weeks of the month. Deliver and pitch your topic in the best possible manner with this project management modelling techniques it project management weekly check sheet inspiration pdf. Use them to share invaluable insights on network problem, server problem, server access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Endpoint Initiated Vs Service Initiated Portrait PDF
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Endpoint Initiated Vs Service Initiated Portrait PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
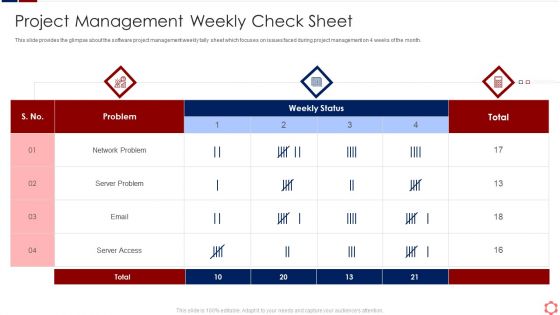
Business Operation Modeling Approaches Project Management Weekly Check Sheet Sample PDF
This slide provides the glimpse about the software project management weekly tally sheet which focuses on issues faced during project management on 4 weeks of the month.Deliver and pitch your topic in the best possible manner with this business operation modeling approaches project management weekly check sheet sample pdf Use them to share invaluable insights on server problem, network problem, server access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

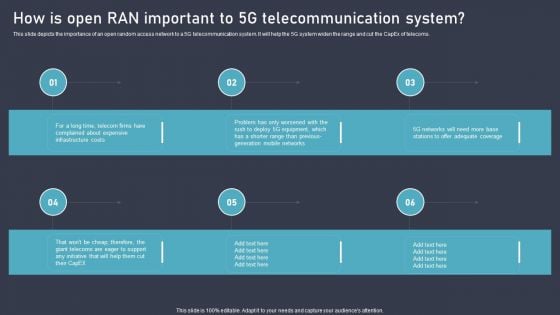
How Is Open RAN Important To 5G Unlocking The Potential Of Open RAN Topics Pdf
This slide depicts the importance of an open random access network to a 5G telecommunication system. It will help the 5G system widen the range and cut the CapEx of telecoms. Slidegeeks is here to make your presentations a breeze with How Is Open RAN Important To 5G Unlocking The Potential Of Open RAN Topics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide depicts the importance of an open random access network to a 5G telecommunication system. It will help the 5G system widen the range and cut the CapEx of telecoms.
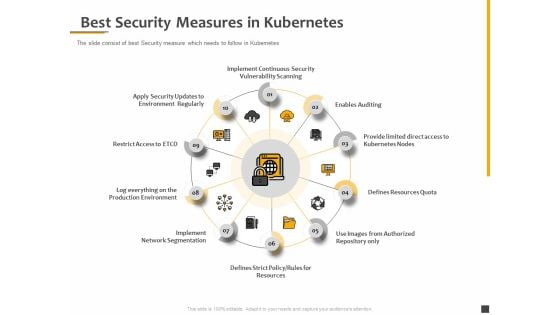
Understanding The Kubernetes Components Through Diagram Best Security Measures In Kubernetes Themes PDF
Presenting this set of slides with name understanding the kubernetes components through diagram best security measures in kubernetes themes pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
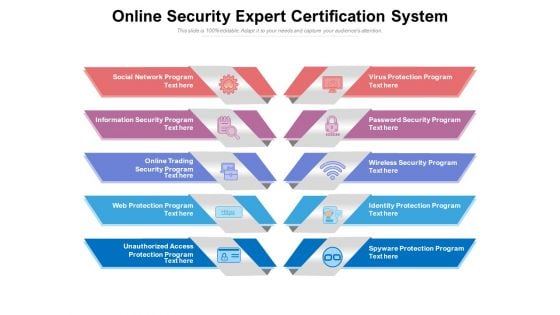
Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Example PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security prepare and deploy strong it policies ppt icon graphics example pdf bundle. Topics like management, it policies, network access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

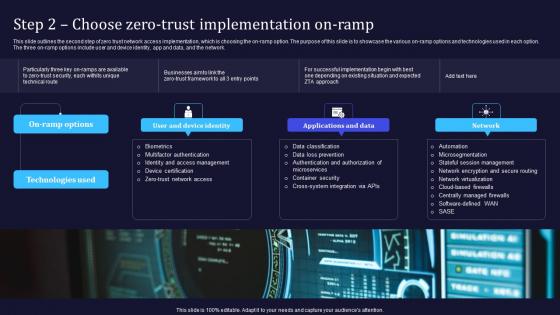
Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Want to ace your presentation in front of a live audience Our Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
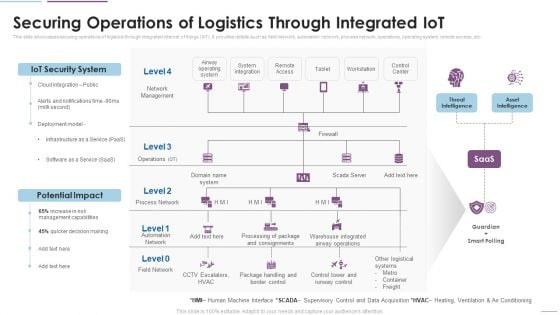
Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF
This slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. This is a Supply Chain Management Securing Operations Of Logistics Through Integrated Iot Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IoT Security System, Potential Impact, Network Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Model Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Boost your pitch with our creative Zero Trust Model Role Of ZTNA To Improve Business Operations And Security. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
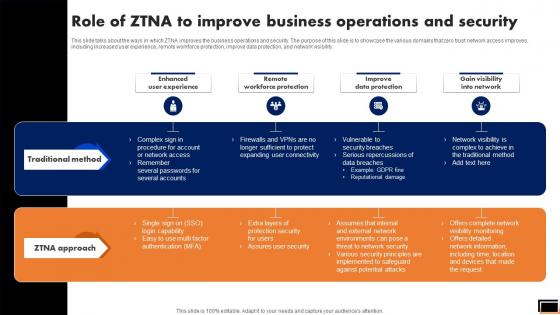
Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
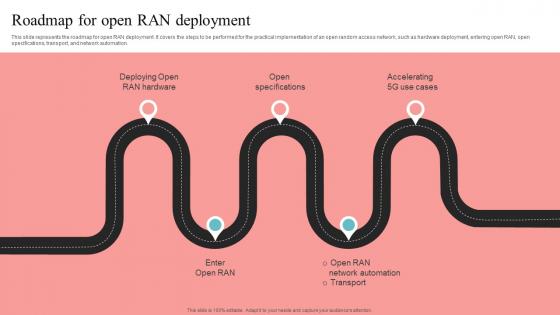
Roadmap For Open RAN Deployment Unlocking The Potential Of Open RAN Demonstration Pdf
This slide represents the roadmap for open RAN deployment. It covers the steps to be performed for the practical implementation of an open random access network, such as hardware deployment, entering open RAN, open specifications, transport, and network automation. Explore a selection of the finest Roadmap For Open RAN Deployment Unlocking The Potential Of Open RAN Demonstration Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Roadmap For Open RAN Deployment Unlocking The Potential Of Open RAN Demonstration Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide represents the roadmap for open RAN deployment. It covers the steps to be performed for the practical implementation of an open random access network, such as hardware deployment, entering open RAN, open specifications, transport, and network automation.
Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.

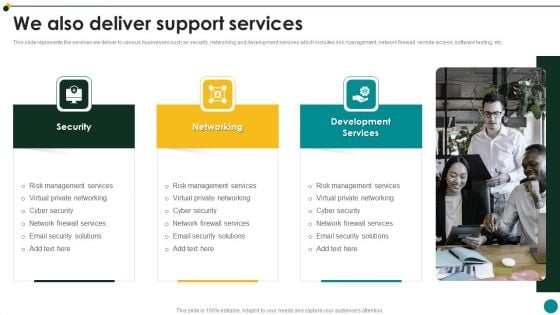
Information Technology Solutions Business Profile We Also Deliver Support Services Clipart PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a Information Technology Solutions Business Profile We Also Deliver Support Services Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Private Networking, Network Firewall. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Overview Of Zero Trust Solution Categories Background PDF
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Boost your pitch with our creative Overview Of Zero Trust Solution Categories Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
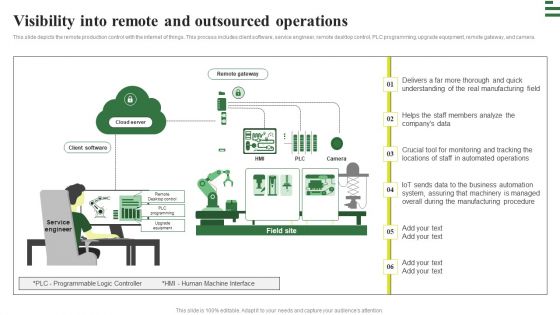
Transforming Manufacturing With Automation Visibility Into Remote And Outsourced Guidelines PDF
This slide depicts the remote production control with the internet of things. This process includes client software, service engineer, remote desktop control, PLC programming, upgrade equipment, remote gateway, and camera. Retrieve professionally designed Transforming Manufacturing With Automation Visibility Into Remote And Outsourced Guidelines PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Internet Security Threats Management Framework Icons PDF
This slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Showcasing this set of slides titled internet security threats management framework icons pdf. The topics addressed in these templates are asset, control topic, evaluation questions, response, threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
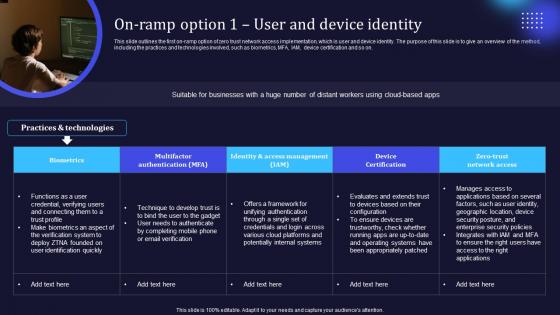
Zero Trust Model On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Retrieve professionally designed Zero Trust Model On Ramp Option 1 User And Device Identity to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
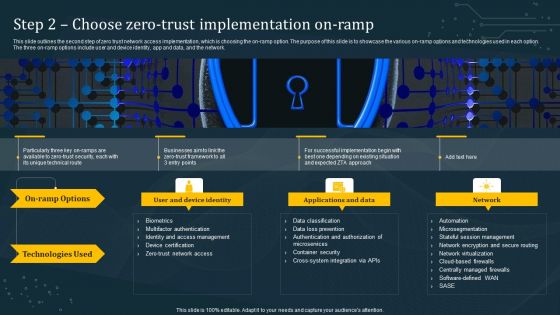
Step 2 Choose Zero Trust Implementation On Ramp Information PDF
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is here to make your presentations a breeze with Step 2 Choose Zero Trust Implementation On Ramp Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
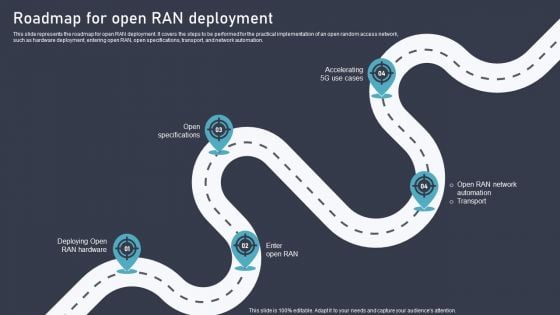
O RAN Architecture Roadmap For Open RAN Deployment Ppt Portfolio Graphics Download PDF
This slide represents the roadmap for open RAN deployment. It covers the steps to be performed for the practical implementation of an open random access network, such as hardware deployment, entering open RAN, open specifications, transport, and network automation. The O RAN Architecture Roadmap For Open RAN Deployment Ppt Portfolio Graphics Download PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
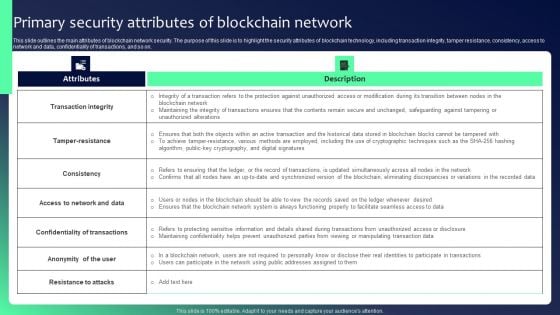
Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF
This slide outlines the main attributes of blockchain network security. The purpose of this slide is to highlight the security attributes of blockchain technology, including transaction integrity, tamper resistance, consistency, access to network and data, confidentiality of transactions, and so on. The Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
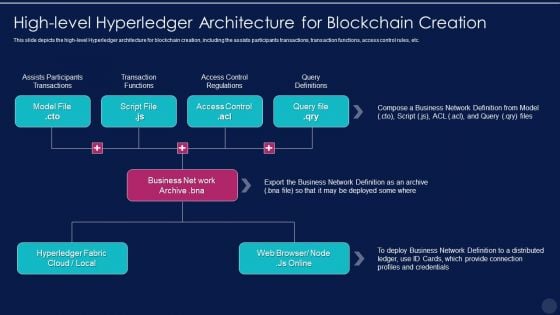
Blockchain Technology Framework IT High Level Hyperledger Architecture For Blockchain Creation Rules PDF
This slide depicts the high level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Presenting blockchain technology framework it high level hyperledger architecture for blockchain creation rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like high level hyperledger architecture for blockchain creation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
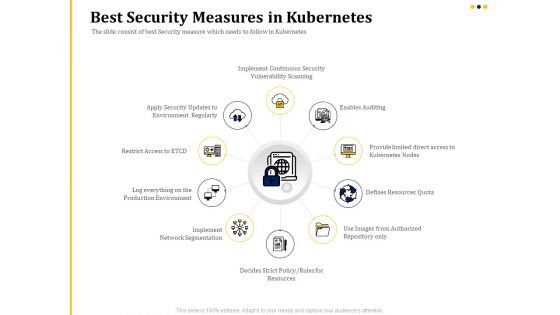
Understanding The Kubernetes Concepts And Architecture Best Security Measures In Kubernetes Ppt Outline Templates PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture best security measures in kubernetes ppt outline templates pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
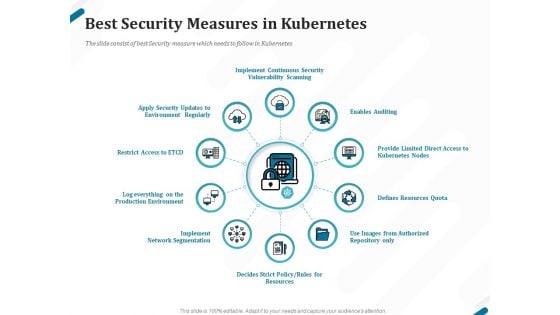
Kubernetes Containers Architecture Overview Best Security Measures In Kubernetes Ppt Pictures File Formats PDF
Presenting this set of slides with name kubernetes containers architecture overview best security measures in kubernetes ppt pictures file formats pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Services And Consulting Company Profile We Also Deliver Support Services Guidelines PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a IT Services And Consulting Company Profile We Also Deliver Support Services Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Virtual Private Networking, Management Services You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Small Business Venture Company Profile We Also Deliver Support Services Summary PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a Small Business Venture Company Profile We Also Deliver Support Services Summary PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Services, Private Networking, Firewall Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
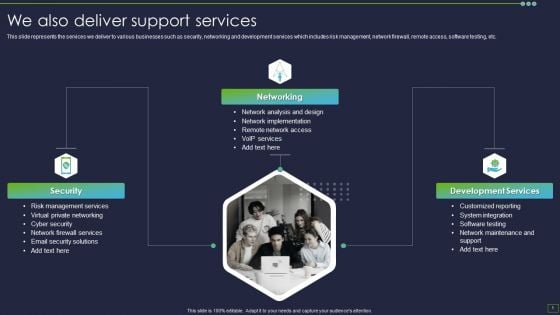
IT Consultancy Services Company Profile We Also Deliver Support Services Structure PDF
This slide represents the services we deliver to various businesses such as security, networking and development services which includes risk management, network firewall, remote access, software testing, etc.This is a IT Consultancy Services Company Profile We Also Deliver Support Services Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Services, Management Services, Network Implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Driving Digital Transformation Through Kubernetes And Containers Best Security Measures In Kubernetes Template PDF
Presenting this set of slides with name driving digital transformation through kubernetes and containers best security measures in kubernetes template pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Key Drivers For SASE Adoption Ppt Styles Visual Aids PDF
This slide outlines the critical drivers for secure access service edge adoption. This slide aims to demonstrate the key drivers that boost SASE adoption among different organizations, including cloud adoption, increased flexibility and agility, cost-effective network traffic management, etc. There are so many reasons you need a Key Drivers For SASE Adoption Ppt Styles Visual Aids PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
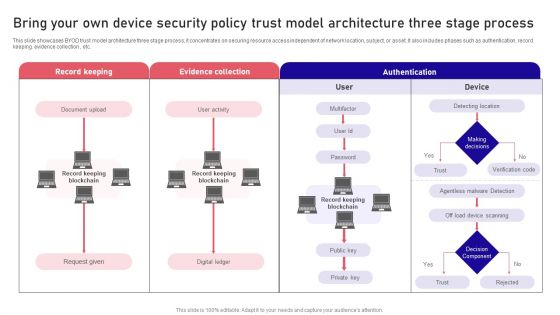
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
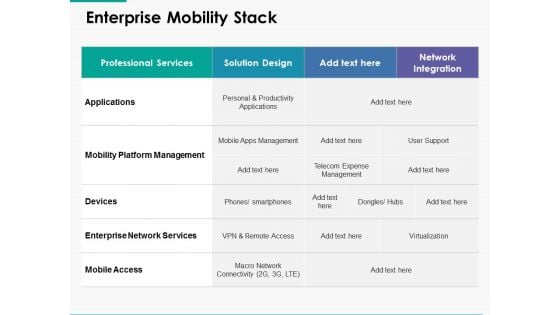
Enterprise Mobility Stack Ppt Powerpoint Presentation Gallery Format Ideas
This is a enterprise mobility stack ppt powerpoint presentation gallery format ideas. This is a four stage process. The stages in this process are applications, mobility platform management, devices, enterprise network services, mobile access.
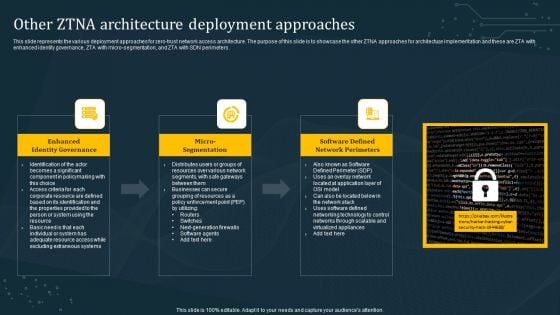
Other ZTNA Architecture Deployment Approaches Formats PDF
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Find a pre-designed and impeccable Other ZTNA Architecture Deployment Approaches Formats PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Difference Between ZTNA And Software Defined Perimeter Diagrams PDF
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Make sure to capture your audiences attention in your business displays with our gratis customizable Difference Between ZTNA And Software Defined Perimeter Diagrams PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
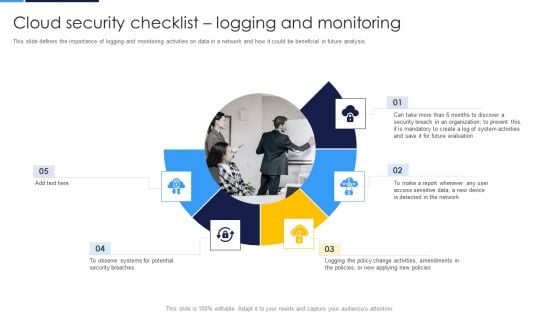
Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Unified Communications Strategy Good Ppt Example
This is a unified communications strategy good ppt example. This is a five stage process. The stages in this process are unified communications strategy, network building, coordination, deployment, access, support.
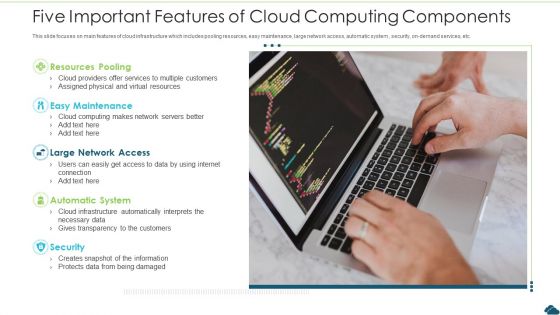
Five Important Features Of Cloud Computing Components Inspiration PDF
This slide focuses on main features of cloud infrastructure which includes pooling resources, easy maintenance, large network access, automatic system , security, on-demand services, etc. Presenting five important features of cloud computing components inspiration pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including resources pooling, easy maintenance, large network access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
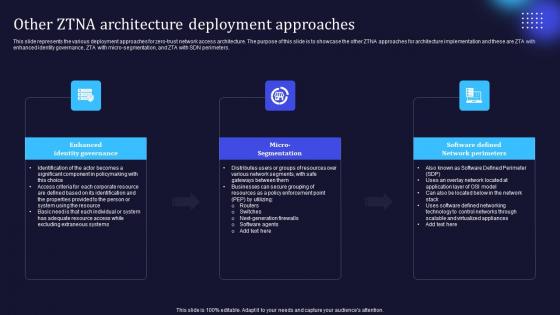
Zero Trust Model Other ZTNA Architecture Deployment Approaches
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Model Other ZTNA Architecture Deployment Approaches to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Model Other ZTNA Architecture Deployment Approaches. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.

Example Of Security Testing Services Ppt Powerpoint Guide
This is a example of security testing services ppt powerpoint guide. This is a eight stage process. The stages in this process are security management, access security, application security, networking security, test delivery, results and analysis, technology enablement, test development and publishing.
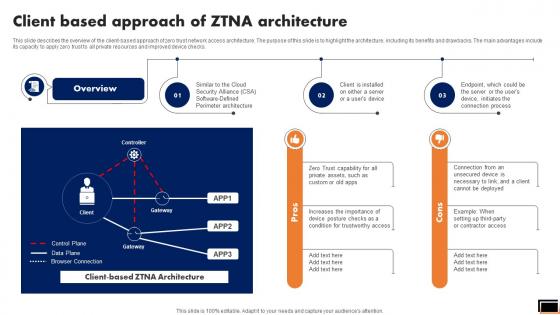
Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.

Zero Trust Model Client Based Approach Of ZTNA Architecture
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Model Client Based Approach Of ZTNA Architecture. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Model Client Based Approach Of ZTNA Architecture today and make your presentation stand out from the rest This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
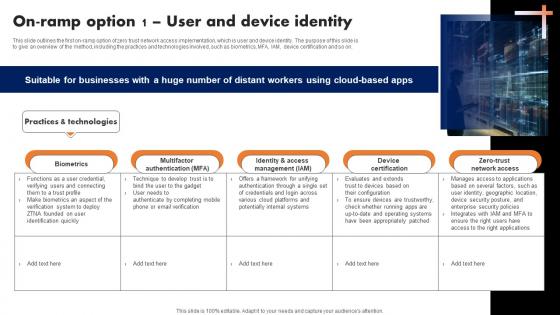
On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.

Zero Trust Model Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Difference Between ZTNA And Software Defined Perimeter and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
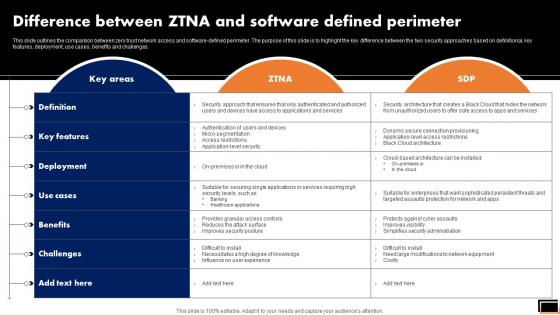
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.

Web App Firewall Services IT Web Application Firewall With Traditional Firewall Professional PDF
This slide represents the difference between a web application firewall and a traditional firewall based on functionality, implementation, threat prevention, OSI layers, and access control. Deliver an awe inspiring pitch with this creative web app firewall services it web application firewall with traditional firewall professional pdf bundle. Topics like organization, applications, implementation, networks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
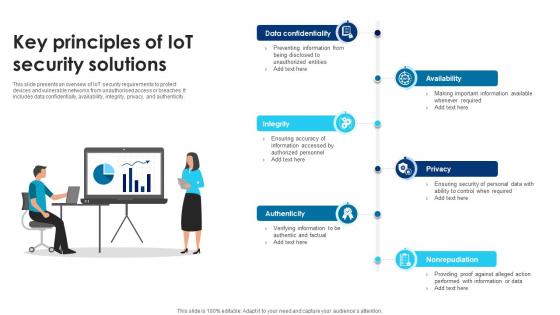
Building Trust With IoT Security Key Principles Of IoT Security Solutions IoT SS V
This slide presents an overview of IoT security requirements to protect devices and vulnerable networks from unauthorised access or breaches. It includes data confidentially, availability, integrity, privacy, and authenticity. Do you know about Slidesgeeks Building Trust With IoT Security Key Principles Of IoT Security Solutions IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide presents an overview of IoT security requirements to protect devices and vulnerable networks from unauthorised access or breaches. It includes data confidentially, availability, integrity, privacy, and authenticity.

Laptop With Email Sign Communication PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Laptop With Email Sign Communication PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Internet PowerPoint Templates because this slide is Designed to help bullet-point your views and thoughts. Present our Technology PowerPoint Templates because displaying your ideas and highlighting your ability will accelerate the growth of your company and yours. Download our Computer PowerPoint Templates because our template will help pinpoint their viability. Download our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Present our Business PowerPoint Templates because you have selected your team man for man.Use these PowerPoint slides for presentations relating to Email icon at the laptop, computer, internet, marketing, technology, business. The prominent colors used in the PowerPoint template are Green, Black, White. Professionals tell us our Laptop With Email Sign Communication PowerPoint Templates PPT Backgrounds For Slides 1212 are Breathtaking. Use our the PowerPoint templates and PPT Slides are second to none. We assure you our Laptop With Email Sign Communication PowerPoint Templates PPT Backgrounds For Slides 1212 are Attractive. We assure you our technology PowerPoint templates and PPT Slides are Clever. Presenters tell us our Laptop With Email Sign Communication PowerPoint Templates PPT Backgrounds For Slides 1212 effectively help you save your valuable time. PowerPoint presentation experts tell us our laptop PowerPoint templates and PPT Slides are Exuberant. Take control with our Laptop With Email Sign Communication PowerPoint Templates Ppt Backgrounds For Slides 1212. Do not be fatalistic in your approach.
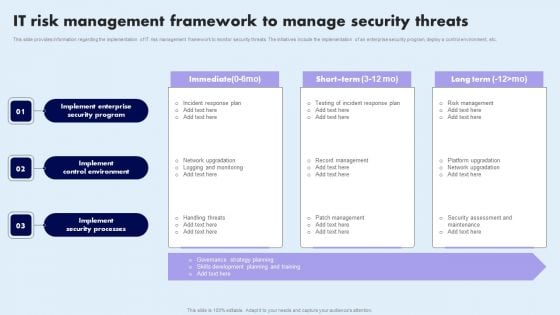
IT Risk Management Framework To Manage Security Threats Summary PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Retrieve professionally designed IT Risk Management Framework To Manage Security Threats Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
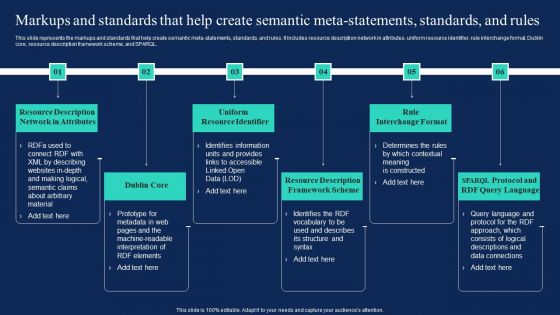
Markups And Standards That Help Create Semantic Meta Statements Standards And Rules Elements PDF
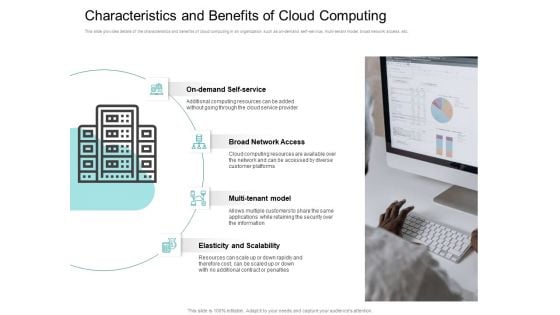
Cloud Based Marketing Characteristics And Benefits Of Cloud Computing Ppt PowerPoint Presentation Professional Layouts PDF
This slide provides details of the characteristics and benefits of cloud computing in an organization such as on demand self service, multi tenant model, broad network access, etc. Presenting cloud based marketing characteristics and benefits of cloud computing ppt powerpoint presentation professional layouts pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like on demand self service, broad network access, multi tenant model, elasticity and scalability. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
O RAN Architecture How Is Open Ran Important To 5G Telecommunication System Demonstration PDF
This slide depicts the importance of an open random access network to a 5G telecommunication system. It will help the 5G system widen the range and cut the CapEx of telecoms. Present like a pro with O RAN Architecture How Is Open Ran Important To 5G Telecommunication System Demonstration PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Markups And Standards That Help Create Semantic Meta Statements Standards And Rules Infographics PDF
This slide represents the markups and standards that help create semantic meta-statements, standards, and rules. It includes resource description network in attributes, uniform resource identifier, rule interchange format, Dublin core, resource description framework scheme, and SPARQL. Retrieve professionally designed Markups And Standards That Help Create Semantic Meta Statements Standards And Rules Infographics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Key CIO Initiatives Responsibilities Managed By Cios Across Workplace Inspiration PDF
This slide provides information regarding responsibilities managed by CIOs across firm in terms of task delegation to improve productivity, management of IT dept., administer network and system deployment, etc. Retrieve professionally designed Key CIO Initiatives Responsibilities Managed By Cios Across Workplace Inspiration PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.


 Continue with Email
Continue with Email

 Home
Home


































