Network Administration

Classification Of Enterprise Network Ppt PowerPoint Presentation Gallery Examples PDF
Presenting this set of slides with name classification of enterprise network ppt powerpoint presentation gallery examples pdf. This is a four stage process. The stages in this process are virtual private network, enterprise private network, passive optical area network, virtual private network, user can send and receive data remotely. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
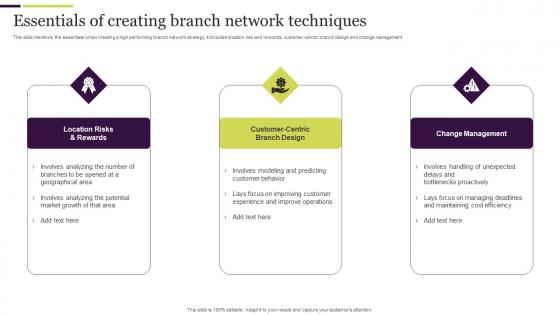
Essentials Of Creating Branch Network Techniques Topics Pdf
This slide mentions the essentials when creating a high performing branch network strategy. It includes location risk and rewards, customer-centric branch design and change management. Pitch your topic with ease and precision using this Essentials Of Creating Branch Network Techniques Topics Pdf. This layout presents information on Location Risks And Rewards, Customer Centric Branch Design, Change Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide mentions the essentials when creating a high performing branch network strategy. It includes location risk and rewards, customer-centric branch design and change management.
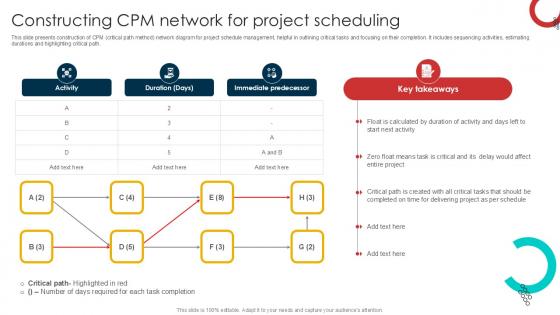
Constructing CPM Network For Schedule Management Techniques PPT Presentation
This slide presents construction of CPM critical path method network diagram for project schedule management, helpful in outlining critical tasks and focusing on their completion. It includes sequencing activities, estimating durations and highlighting critical path. Get a simple yet stunning designed Constructing CPM Network For Schedule Management Techniques PPT Presentation. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Constructing CPM Network For Schedule Management Techniques PPT Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide presents construction of CPM critical path method network diagram for project schedule management, helpful in outlining critical tasks and focusing on their completion. It includes sequencing activities, estimating durations and highlighting critical path.
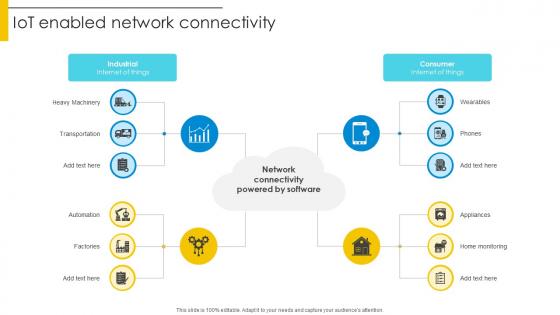
IoT Enabled Network Connectivity Optimizing Inventory Management IoT SS V
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. IoT Enabled Network Connectivity Optimizing Inventory Management IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Our IoT Enabled Network Connectivity Optimizing Inventory Management IoT SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Zero Trust Model Zero Trust Network Access User Flow Overview
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Retrieve professionally designed Zero Trust Model Zero Trust Network Access User Flow Overview to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Network Access Overview Of Zero Trust Solution Categories for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

Zero Trust Network Access System Use Cases Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Present like a pro with Zero Trust Network Access System Use Cases Themes Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.
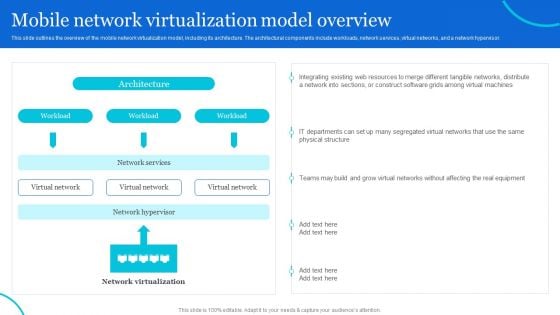
Naas Architectural Framework Mobile Network Virtualization Model Overview Background PDF
This slide outlines the overview of the mobile network virtualization model, including its architecture. The architectural components include workloads, network services, virtual networks, and a network hypervisor. Make sure to capture your audiences attention in your business displays with our gratis customizable Naas Architectural Framework Mobile Network Virtualization Model Overview Background PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Top Employee Network Monitoring Ppt PowerPoint Presentation Inspiration Visuals Cpb
This is a top employee network monitoring ppt powerpoint presentation inspiration visuals cpb. This is a three stage process. The stages in this process are top employee network monitoring, business, management, marketing.

Money Network Marketing Ppt PowerPoint Presentation Show Outline Cpb
This is a money network marketing ppt powerpoint presentation show outline cpb. This is a four stage process. The stages in this process are money network marketing, management, marketing, business.

Angel Investment Network Ppt PowerPoint Presentation Slides Background Cpb
This is a angel investment network ppt powerpoint presentation slides background cpb. This is a three stage process. The stages in this process are angel investment network, process, management, marketing.
Network Marketing Forums Ppt PowerPoint Presentation Show Backgrounds Cpb
This is a network marketing forums ppt powerpoint presentation show backgrounds cpb. This is a three stage process. The stages in this process are network marketing forums, business, marketing, management.
Network Marketing Prospecting Software Ppt PowerPoint Presentation Show Slides Cpb
This is a network marketing prospecting software ppt powerpoint presentation show slides cpb. This is a six stage process. The stages in this process are network marketing prospecting software.
Network Marketing Business Opportunity Ppt Powerpoint Presentation Portfolio Outline Cpb
This is a network marketing business opportunity ppt powerpoint presentation portfolio outline cpb. This is a seven stage process. The stages in this process are network marketing business opportunity.

Network Marketing Sales Leads Ppt Powerpoint Presentation Layouts Sample Cpb
This is a network marketing sales leads ppt powerpoint presentation layouts sample cpb. This is a four stage process. The stages in this process are network marketing sales leads.
Small Business Marketing Network Ppt PowerPoint Presentation Inspiration Display Cpb
This is a small business marketing network ppt powerpoint presentation inspiration display cpb. This is a five stage process. The stages in this process are small business marketing network.
Icons Slide For Zero Trust Network Access Ppt Diagram Images
Present like a pro with Icons Slide For Zero Trust Network Access Ppt Diagram Images. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. Our Icons Slide For Zero Trust Network Access Ppt Diagram Images are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Pillars Of Cloud Security Network Security Rules PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. This is a Pillars Of Cloud Security Network Security Rules PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secure, Network, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
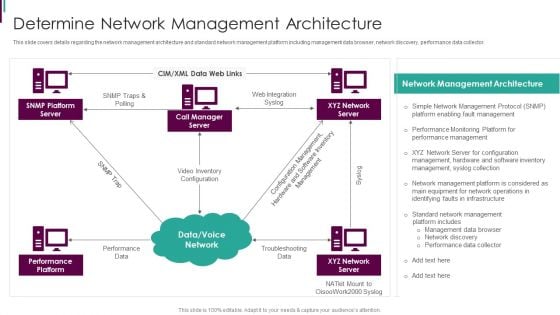
Developing Business Analytics Framework Determine Network Management Architecture Designs PDF
This slide covers details regarding the network management architecture and standard network management platform including management data browser, network discovery, performance data collector. Presenting Developing Business Analytics Framework Determine Network Management Architecture Designs PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Platform Server, Manager Server, Network Server In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
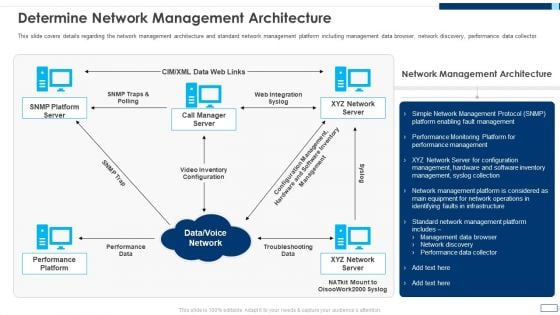
Evolving BI Infrastructure Determine Network Management Architecture Elements PDF
This slide covers details regarding the network management architecture and standard network management platform including management data browser, network discovery, performance data collector. This is a evolving bi infrastructure determine network management architecture elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like web integration syslog, performance data, troubleshooting data, network management architecture. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Four Business Person For Social Network Powerpoint Slides
Our above PowerPoint template displays team network design. This PPT slide may be used for building and managing team network. You may download this PPT slide to present topics like team strategy and success.
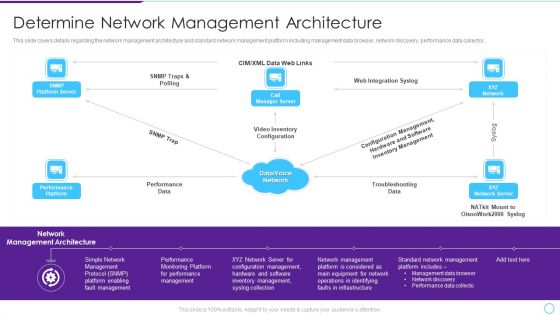
Intelligent Infrastructure Determine Network Management Architecture Formats PDF
This slide covers details regarding the network management architecture and standard network management platform including management data browser, network discovery, performance data collector. Presenting Intelligent Infrastructure Determine Network Management Architecture Formats PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Performance, Data, SNMP Trap, Web Integration Syslog, XYZ Network Server. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
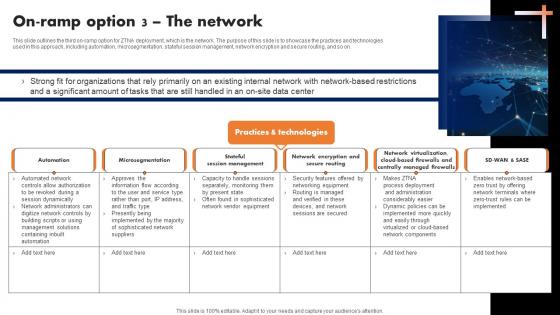
On Ramp Option 3 The Network Software Defined Perimeter SDP
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Software Defined Perimeter SDP from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Zero Trust Network Access Architectural Models Ideas Pdf
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. There are so many reasons you need a Zero Trust Network Access Architectural Models Ideas Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Zero Trust Model Benefits Of Zero Trust Network Access ZTNA
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Get a simple yet stunning designed Zero Trust Model Benefits Of Zero Trust Network Access ZTNA. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Model Benefits Of Zero Trust Network Access ZTNA can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation.

Social Network System Communication PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with a business team organization network diagram image Draft your plans with our Social Network System Communication PowerPoint Templates And PowerPoint Backgrounds 0511. Download without worries with our money back guaranteee.

Organisation Network Leadership PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with a business team organization network Deliver your address to your congregation. Give them a glimpse of the divine with our Organisation Network Leadership PowerPoint Templates And PowerPoint Backgrounds 0711.

Social Network System Communication PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with a business team organization network diagram image Depend on no one with our Social Network System Communication PowerPoint Themes And PowerPoint Slides 0511. You will come out on top.

Organisation Network Leadership PowerPoint Themes And PowerPoint Slides 0711
Microsoft PowerPoint Theme and Slide with a business team organization network Reveal the depth of your knowledge. Showcase your erudition on our Organisation Network Leadership PowerPoint Themes And PowerPoint Slides 0711.

Zero Trust Network Access User Flow Overview Download Pdf
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Slidegeeks is here to make your presentations a breeze with Zero Trust Network Access User Flow Overview Download Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.
Pairing 5G Network For Smart Logistics Icons PDF
This slide shows pairing 5G network for smart logistics. It provides information about supply chain risk management, latency reduction, self driven vehicles, device connections, network usage, downtime, etc. Deliver and pitch your topic in the best possible manner with this Pairing 5G Network For Smart Logistics Icons PDF. Use them to share invaluable insights on Mitigating Supply Chain Risks, Network, Synchronization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
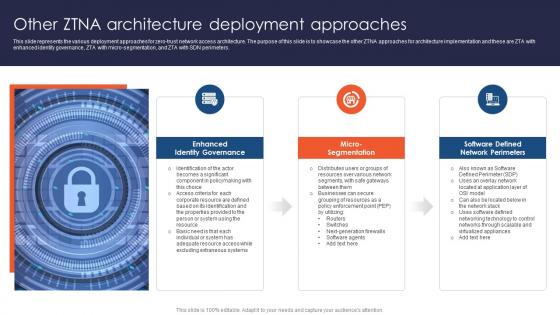
Zero Trust Network Access Other ZTNA Architecture Deployment Approaches
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Create an editable Zero Trust Network Access Other ZTNA Architecture Deployment Approaches that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access Other ZTNA Architecture Deployment Approaches is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.
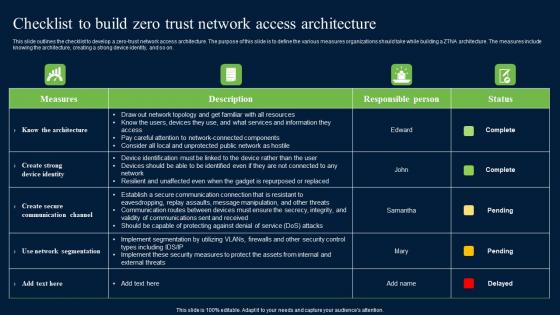
Checklist To Build Zero Trust Network Access Security Structure Pdf
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Security Structure Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Security Structure Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
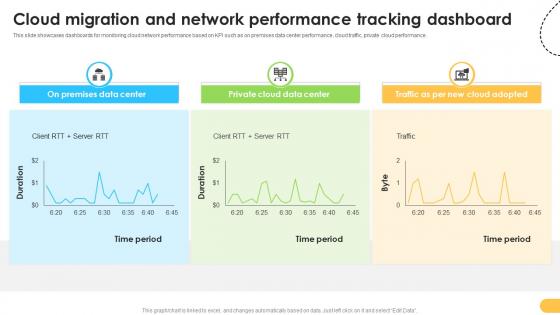
Cloud Migration And Network Performance Data Migration From On Premises
This slide showcases dashboards for monitoring cloud network performance based on KPI such as on premises data center performance, cloud traffic, private cloud performance. Present like a pro with Cloud Migration And Network Performance Data Migration From On Premises. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases dashboards for monitoring cloud network performance based on KPI such as on premises data center performance, cloud traffic, private cloud performance.
Effective Data Migration Cloud Migration And Network Performance Tracking
This slide showcases dashboards for monitoring cloud network performance based on KPI such as on premises data center performance, cloud traffic, private cloud performance. Present like a pro with Effective Data Migration Cloud Migration And Network Performance Tracking. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases dashboards for monitoring cloud network performance based on KPI such as on premises data center performance, cloud traffic, private cloud performance.
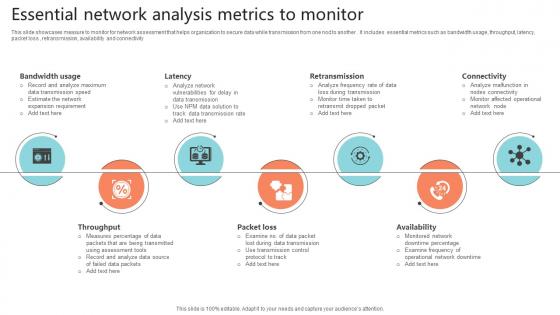
Essential Network Analysis Metrics To Monitor Portrait Pdf
This slide showcases measure to monitor for network assessment that helps organization to secure data while transmission from one nod to another . It includes essential metrics such as bandwidth usage, throughput, latency, packet loss , retransmission, availability and connectivity.Pitch your topic with ease and precision using this Essential Network Analysis Metrics To Monitor Portrait Pdf This layout presents information on Bandwidth Usage, Retransmission, Throughput It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases measure to monitor for network assessment that helps organization to secure data while transmission from one nod to another . It includes essential metrics such as bandwidth usage, throughput, latency, packet loss , retransmission, availability and connectivity
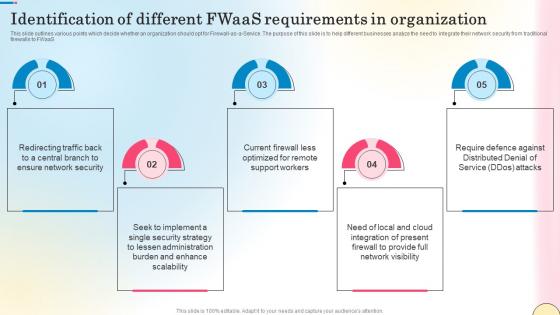
Identification Of Different Fwaas Requirements In Network Security Template Pdf
This slide outlines various points which decide whether an organization should opt for Firewall-as-a-Service. The purpose of this slide is to help different businesses analyze the need to integrate their network security from traditional firewalls to FWaaS. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Identification Of Different Fwaas Requirements In Network Security Template Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines various points which decide whether an organization should opt for Firewall-as-a-Service. The purpose of this slide is to help different businesses analyze the need to integrate their network security from traditional firewalls to FWaaS.

Risk Analysis Process Of It Network Infographics Pdf
This slide illustrates risk assessment life cycle steps that helps the organization to identify all potential risk associate with network operation and to formulating effective mitigation action plan. It includes steps such as evaluation, vulnerability identification, exposure determination, threat determination, risk assessment and risk mitigation.Pitch your topic with ease and precision using this Risk Analysis Process Of It Network Infographics Pdf This layout presents information on Threat Determination, Vulnerability Identification, Exposure Determination It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide illustrates risk assessment life cycle steps that helps the organization to identify all potential risk associate with network operation and to formulating effective mitigation action plan. It includes steps such as evaluation, vulnerability identification, exposure determination, threat determination, risk assessment and risk mitigation

Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf
This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.Showcasing this set of slides titled Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf The topics addressed in these templates are Evaluate Possible Risk, Interpret Scan Results, Create Mitigation Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.

Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model
This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory. Make sure to capture your audiences attention in your business displays with our gratis customizable Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide describes the overview of the endpoint-initiated zero trust network topology model of ZTNA deployment. The purpose of this slide is to showcase the conceptual model of the approach along with its benefits and drawbacks. The model components include the end-user device, SDP controller, gateway, and directory.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Zero Trust Model Service Initiated Zero Trust Network Topology Model
This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Model Service Initiated Zero Trust Network Topology Model for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector.

Zero Trust Network Access Implementation Challenges Mockup Pdf
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Get a simple yet stunning designed Zero Trust Network Access Implementation Challenges Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Zero Trust Network Access Implementation Challenges Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on.
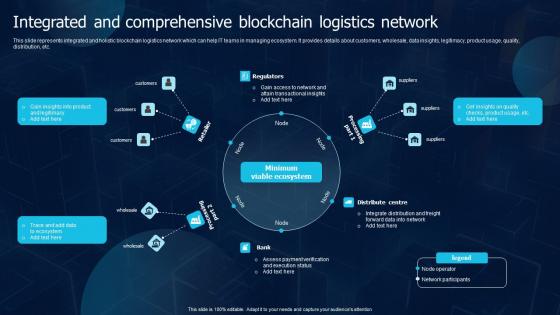
Integrated And Comprehensive Blockchain Logistics Network Blockchain Transportation Formats Pdf
This slide represents integrated and holistic blockchain logistics network which can help IT teams in managing ecosystem. It provides details about customers, wholesale, data insights, legitimacy, product usage, quality, distribution, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Integrated And Comprehensive Blockchain Logistics Network Blockchain Transportation Formats Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents integrated and holistic blockchain logistics network which can help IT teams in managing ecosystem. It provides details about customers, wholesale, data insights, legitimacy, product usage, quality, distribution, etc.
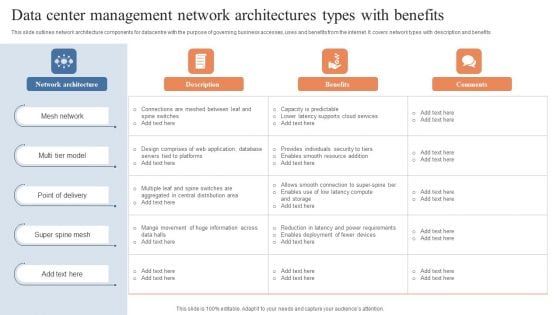
Data Center Management Network Architectures Types With Benefits Brochure PDF
This slide outlines network architecture components for datacentre with the purpose of governing business accesses, uses and benefits from the internet. It covers network types with description and benefits. Showcasing this set of slides titled Data Center Management Network Architectures Types With Benefits Brochure PDF. The topics addressed in these templates are Mesh Network, Point Delivery, Super Spine Mesh. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Corporate Profile IT Organization Companys Distribution Network Mockup PDF
The slide provides the details about distribution network OEMs, Direct Network, Distributors and sellers etc. of the company. Presenting corporate profile it organization companys distribution network mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like direct network, distributors and resellers, original equipment manufacturers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Benefits Of Zero Trust Network Security Portrait Pdf
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Security Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control AND visibility, invisible infrastructure, and simple app segmentation.

Architecture Of Content Delivery Network Ppt Gallery Infographic Template PDF
This slide explains the content delivery network architecture in which point of presence and regional data Centre is the basic foundation of CDN systems. Deliver an awe inspiring pitch with this creative architecture of content delivery network ppt gallery infographic template pdf bundle. Topics like architecture of content delivery network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
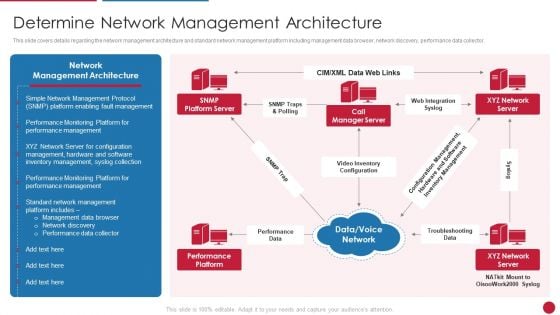
Facilitating IT Intelligence Architecture Determine Network Management Architecture Infographics PDF
This slide covers details regarding the network management architecture and standard network management platform including management data browser, network discovery, performance data collector. Presenting Facilitating IT Intelligence Architecture Determine Network Management Architecture Infographics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Performance Platform, Configuration Management, Inventory Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
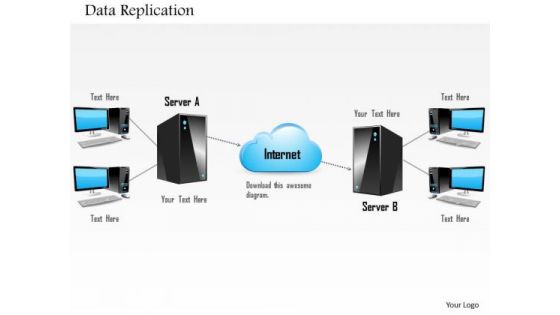
1 Data Replication From Primary To Replica Over Local Area Network Or Wide Are Network Ppt Slides
This image slide displays data replication. This image slide has been designed with graphic of cloud, two servers and clients over network. This image slide depicts process of data replication. Database replication can be used on many database management systems, usually with a master slave relationship between the original and the copies. The master logs the updates, which then pass through to the slaves. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concept of data replication and cloud computing. This image slide will enhance the quality of your presentations.
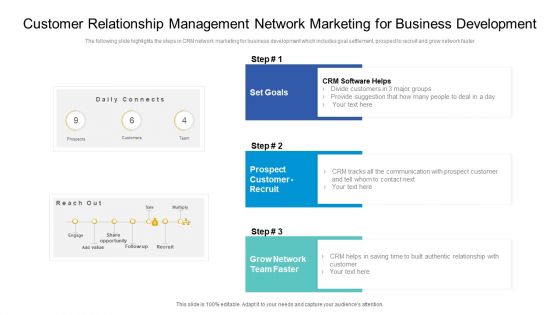
Customer Relationship Management Network Marketing For Business Development Elements PDF
The following slide highlights the steps in CRM network marketing for business development which includes goal settlement, prospect to recruit and grow network faster. Presenting customer relationship management network marketing for business development elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including set goals, prospect customer recruit, grow network team faster. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
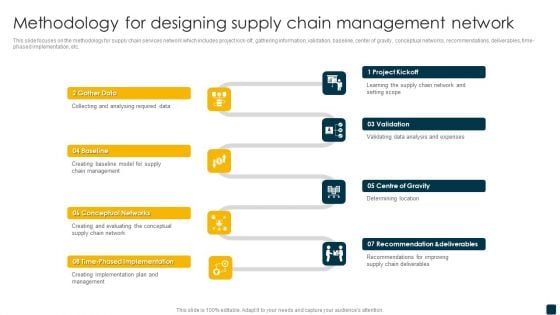
Methodology For Designing Supply Chain Management Network Background PDF
This slide focuses on the methodology for supply chain services network which includes project kick off, gathering information, validation, baseline, center of gravity, conceptual networks, recommendations, deliverables, time phased implementation, etc. Presenting Methodology For Designing Supply Chain Management Network Background PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Conceptual Networks, Gather Data, Validation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Zero Trust Model Checklist To Build Zero Trust Network Access
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Checklist To Build Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
Ppt Slide Diagram For Social Network Marketing Plan
With Our PPT Slide Diagram For Social Network Marketing Plan Powerpoint Templates You Will Be Doubly Sure. They Possess That Stamp Of Authority.
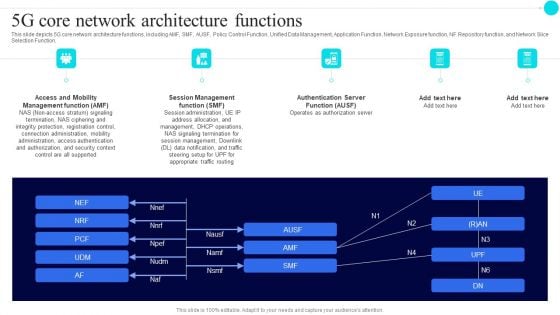
5G Core Network Architecture Functions 5G Functional Architecture Background PDF
This slide depicts 5G core network architecture functions, including AMF, SMF, AUSF, Policy Control Function, Unified Data Management, Application Function, Network Exposure function, NF Repository function, and Network Slice Selection Function.Presenting 5G Core Network Architecture Functions 5G Functional Architecture Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like session management, authentication server, management function. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Vitality And Network Effects Lunchclub Investor Capitalizing Elevator Infographics Pdf
This template covers lunchclub companys number natural global networks effects and professional connection span for multiple cities. Presenting vitality and network effects lunchclub investor capitalizing elevator infographics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like vitality and network effects. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Wireless Remote Control For Network Security System Themes PDF
Persuade your audience using this wireless remote control for network security system themes pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including wireless remote control for network security system. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


 Continue with Email
Continue with Email

 Home
Home


































