Network Analysis

Empowering The Future IoT Enabled Vehicle To Grid System IoT SS V
This slide exhibits vehicle to grid network overview that allows electric vehicles to discharge excess energy during peak hours. It includes benefits such as reduction in peak load times, reduction in energy cost, and increase in price stability. Create an editable Empowering The Future IoT Enabled Vehicle To Grid System IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Empowering The Future IoT Enabled Vehicle To Grid System IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide exhibits vehicle to grid network overview that allows electric vehicles to discharge excess energy during peak hours. It includes benefits such as reduction in peak load times, reduction in energy cost, and increase in price stability.
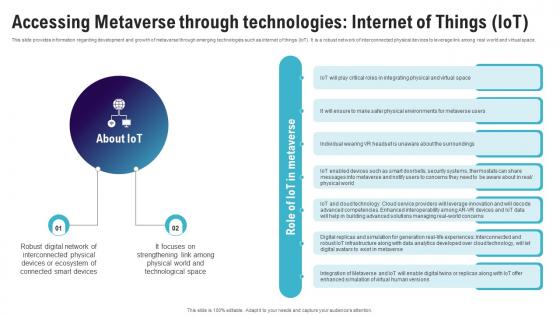
Accessing Metaverse Through Technologies Internet Continuum Of Technology Revamping Business AI SS V
This slide provides information regarding development and growth of metaverse through emerging technologies such as internet of things IoT. It is a robust network of interconnected physical devices to leverage link among real world and virtual space. Present like a pro with Accessing Metaverse Through Technologies Internet Continuum Of Technology Revamping Business AI SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides information regarding development and growth of metaverse through emerging technologies such as internet of things IoT. It is a robust network of interconnected physical devices to leverage link among real world and virtual space.

Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf
This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc. Showcasing this set of slides titled Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf. The topics addressed in these templates are Risk Assessment, Cybersecurity Governance, Access Controls. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc.

Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.

Data Breach Response Plan Fix Vulnerabilities Data Fortification Strengthening Defenses
This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Breach Response Plan Fix Vulnerabilities Data Fortification Strengthening Defenses to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.
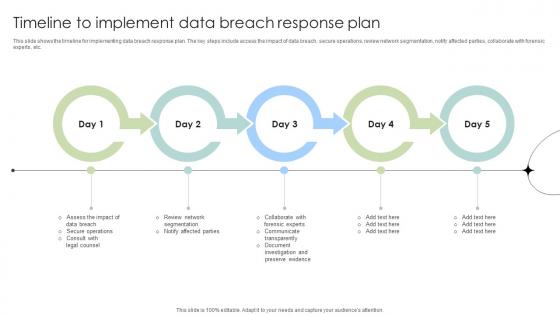
Timeline To Implement Data Breach Response Plan Data Fortification Strengthening Defenses
This slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline To Implement Data Breach Response Plan Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc.

Data Breach Response Plan Fix Vulnerabilities Data Breach Prevention Information Pdf
This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc. This modern and well-arranged Data Breach Response Plan Fix Vulnerabilities Data Breach Prevention Information Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc.
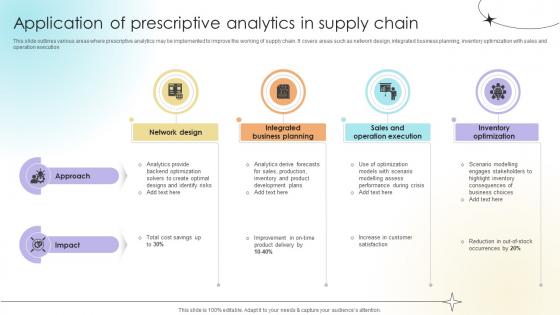
Application Of Prescriptive Analytics In Supply Chain Data Analytics SS V
This slide outlines various areas where prescriptive analytics may be implemented to improve the working of supply chain. It covers areas such as network design, integrated business planning, inventory optimization with sales and operation execution There are so many reasons you need a Application Of Prescriptive Analytics In Supply Chain Data Analytics SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines various areas where prescriptive analytics may be implemented to improve the working of supply chain. It covers areas such as network design, integrated business planning, inventory optimization with sales and operation execution
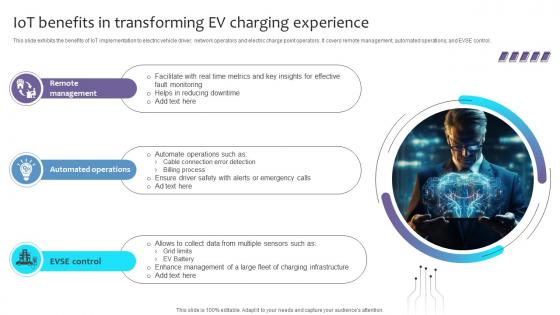
Empowering The Future IoT Benefits In Transforming Ev Charging Experience IoT SS V
This slide exhibits the benefits of IoT implementation to electric vehicle driver, network operators and electric charge point operators. It covers remote management, automated operations, and EVSE control. Find a pre-designed and impeccable Empowering The Future IoT Benefits In Transforming Ev Charging Experience IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide exhibits the benefits of IoT implementation to electric vehicle driver, network operators and electric charge point operators. It covers remote management, automated operations, and EVSE control.
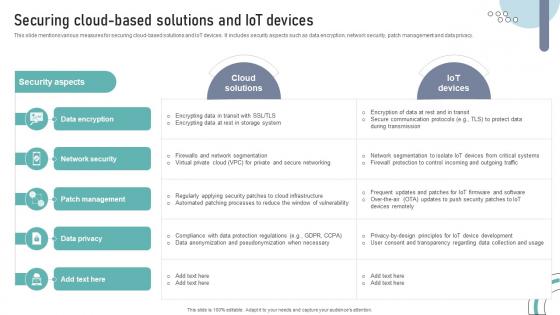
Securing Cloud Based Solutions And IOT Devices DT SS V
This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy. Slidegeeks has constructed Securing Cloud Based Solutions And IOT Devices DT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide mentions various measures for securing cloud-based solutions and IoT devices. It includes security aspects such as data encryption, network security, patch management and data privacy.
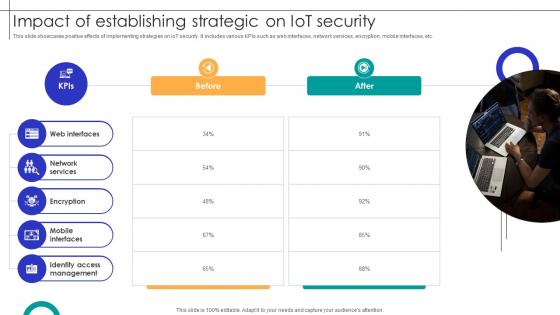
Impact Of Establishing Strategic On IOT Security Streamlining Production Ppt Presentation
This slide showcases positive effects of implementing strategies on IoT security. It includes various KPIs such as web interfaces, network services, encryption, mobile interfaces, etc. Retrieve professionally designed Impact Of Establishing Strategic On IOT Security Streamlining Production Ppt Presentation to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide showcases positive effects of implementing strategies on IoT security. It includes various KPIs such as web interfaces, network services, encryption, mobile interfaces, etc.
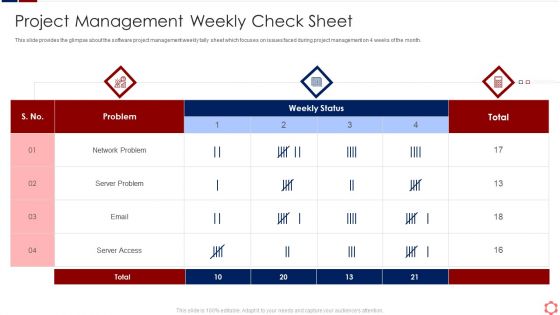
Business Operation Modeling Approaches Project Management Weekly Check Sheet Sample PDF
This slide provides the glimpse about the software project management weekly tally sheet which focuses on issues faced during project management on 4 weeks of the month.Deliver and pitch your topic in the best possible manner with this business operation modeling approaches project management weekly check sheet sample pdf Use them to share invaluable insights on server problem, network problem, server access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
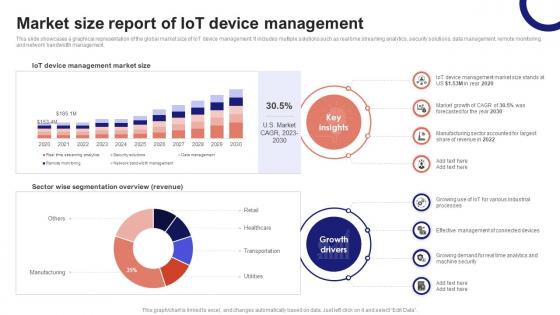
IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT Ss V
This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management. Slidegeeks has constructed IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management.
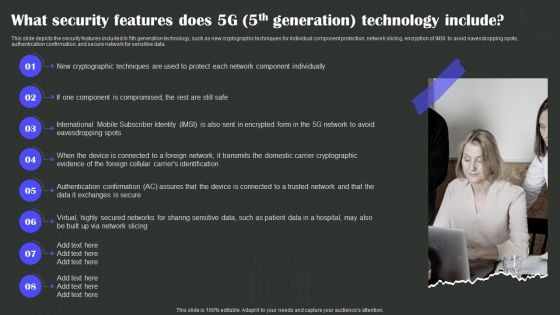
What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Present like a pro with What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
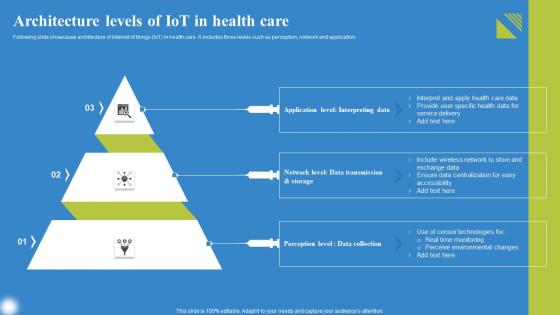
Architecture Levels Of IoT In Health deploying IoT Solutions For Enhanced Healthcare Ideas Pdf
Following slide showcases architecture of internet of things IoT in health care. It includes three levels such as perception, network and application. If you are looking for a format to display your unique thoughts, then the professionally designed Architecture Levels Of IoT In Health deploying IoT Solutions For Enhanced Healthcare Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Architecture Levels Of IoT In Health deploying IoT Solutions For Enhanced Healthcare Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. Following slide showcases architecture of internet of things IoT in health care. It includes three levels such as perception, network and application.

Accessing Metaverse Through Technologies Edge Continuum Of Technology Revamping Business AI SS V
This slide provides information regarding development and growth of metaverse through emerging technologies such as edge computing. It enables processing of data on-site for faster information processing to reduce network latency. Get a simple yet stunning designed Accessing Metaverse Through Technologies Edge Continuum Of Technology Revamping Business AI SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Accessing Metaverse Through Technologies Edge Continuum Of Technology Revamping Business AI SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides information regarding development and growth of metaverse through emerging technologies such as edge computing. It enables processing of data on-site for faster information processing to reduce network latency.

Naas Architectural Framework How Small Businesses Can Take Advantage Template PDF
This slide represents how small businesses can be benefitted from a network as a service model to delegate day-to-day equipment maintenance, reduce networking bandwidth as per need and increase online operations, fulfill increasing demands, and experiment with new technologies quickly. Find highly impressive Naas Architectural Framework How Small Businesses Can Take Advantage Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Naas Architectural Framework How Small Businesses Can Take Advantage Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
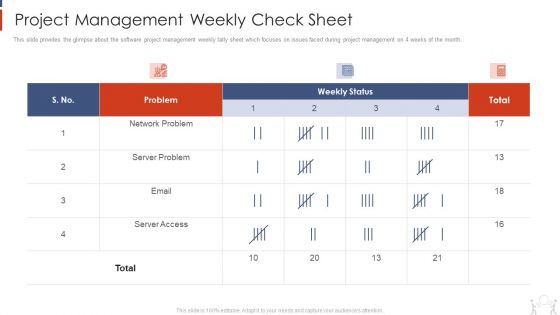
Project Management Modelling Techniques IT Project Management Weekly Check Sheet Inspiration PDF
This slide provides the glimpse about the software project management weekly tally sheet which focuses on issues faced during project management on 4 weeks of the month. Deliver and pitch your topic in the best possible manner with this project management modelling techniques it project management weekly check sheet inspiration pdf. Use them to share invaluable insights on network problem, server problem, server access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
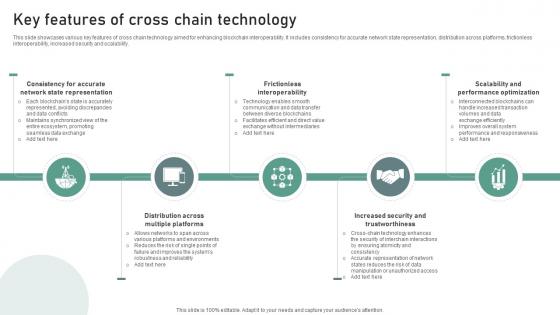
Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Slidegeeks has constructed Bridging Blockchains A Deep Key Features Of Cross Chain Technology BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.
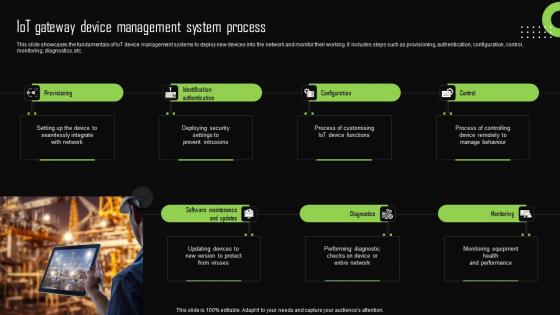
Iot Gateway Device Management System Process Iot Device Management Portrait Pdf
This slide showcases the fundamentals of IoT device management systems to deploy new devices into the network and monitor their working. It includes steps such as provisioning, authentication, configuration, control, monitoring, diagnostics, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Iot Gateway Device Management System Process Iot Device Management Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide showcases the fundamentals of IoT device management systems to deploy new devices into the network and monitor their working. It includes steps such as provisioning, authentication, configuration, control, monitoring, diagnostics, etc.

Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc. Create an editable Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc.

How Is Open RAN Important To 5G Unlocking The Potential Of Open RAN Topics Pdf
This slide depicts the importance of an open random access network to a 5G telecommunication system. It will help the 5G system widen the range and cut the CapEx of telecoms. Slidegeeks is here to make your presentations a breeze with How Is Open RAN Important To 5G Unlocking The Potential Of Open RAN Topics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first. This slide depicts the importance of an open random access network to a 5G telecommunication system. It will help the 5G system widen the range and cut the CapEx of telecoms.
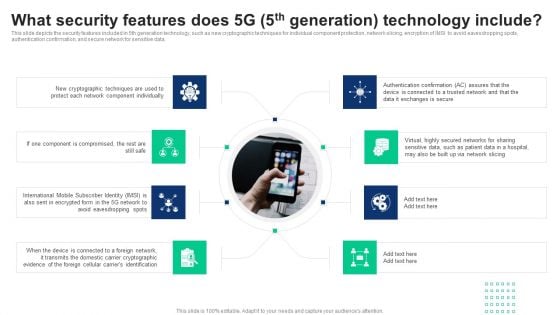
1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Welcome to our selection of the 1G To 5G Cellular What Security Features Does 5G 5Th Generation Technology Include Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
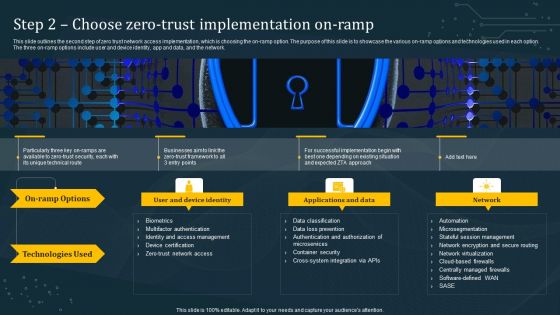
Step 2 Choose Zero Trust Implementation On Ramp Information PDF
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is here to make your presentations a breeze with Step 2 Choose Zero Trust Implementation On Ramp Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Naas Architectural Framework Naas Expenditure Accounting Treatment Capex Inspiration PDF
This slide describes the nature of a network as a service expenditure accounting treatment, whether it is a capital or an operating expenditure. It tells how the network as a service is considered both a CapEx model as well as an OpEx model. This Naas Architectural Framework Naas Expenditure Accounting Treatment Capex Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. TheNaas Architectural Framework Naas Expenditure Accounting Treatment Capex Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
Stock Photo 3d Laptops Graphic Connected With Server PowerPoint Slide
Graphic of 3d laptop and servers has been used to design this power point template. This image template contains the concept of data transfer with networking. This image template can be used to show the networking related presentations.
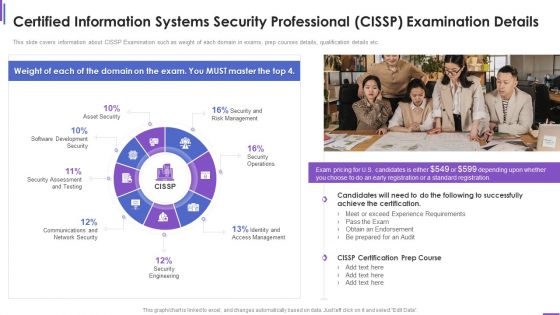
Certified Information Systems Security Professional Cissp Examination Details Elements PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. Deliver an awe inspiring pitch with this creative certified information systems security professional cissp examination details elements pdf bundle. Topics like requirements, network security, security engineering, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cisco Certified Internetwork Expert Ccie Examination Details Icons PDF
This slide covers CCIE examination details including certification, exam number, exam name duration and fees per attempt along with specialist courses Deliver an awe inspiring pitch with this creative Cisco Certified Internetwork Expert Ccie Examination Details Icons PDF bundle. Topics like Routing And Switching, Service Provider, Network Specialist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
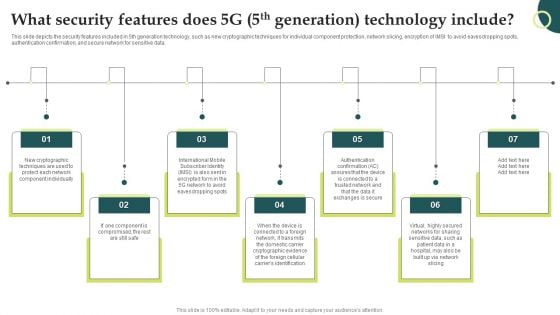
Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Key Activities Travel Technology Company Business Model BMC SS V
This slide covers the most curtail activity the company performs in order to operate business successfully. It includes activities such as technology platform development, network management and customer support. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Key Activities Travel Technology Company Business Model BMC SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers the most curtail activity the company performs in order to operate business successfully. It includes activities such as technology platform development, network management and customer support.
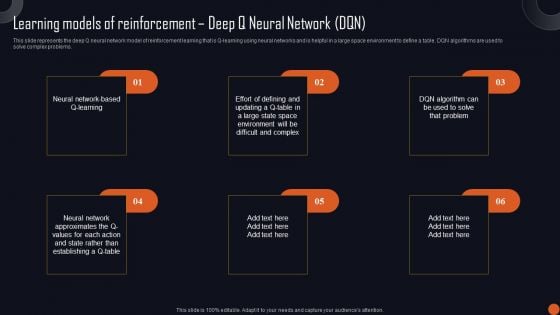
Reinforcement Learning Principles And Techniques Learning Models Of Reinforcement Deep Q Neural Slides PDF
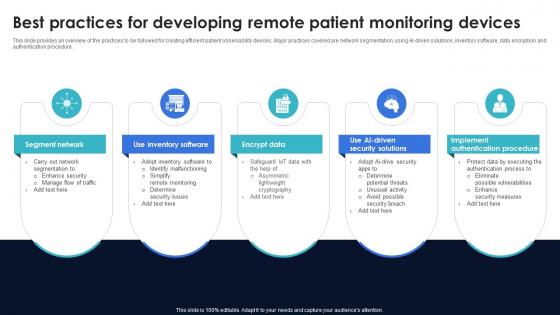
Optimization Of IoT Remote Monitoring Best Practices For Developing Remote Patient Monitoring IoT SS V
This slide provides an overview of the practices to be followed for creating efficient patient observability devices. Major practices covered are network segmentation, using AI-driven solutions, inventory software, data encryption and authentication procedure. Present like a pro with Optimization Of IoT Remote Monitoring Best Practices For Developing Remote Patient Monitoring IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide provides an overview of the practices to be followed for creating efficient patient observability devices. Major practices covered are network segmentation, using AI-driven solutions, inventory software, data encryption and authentication procedure.
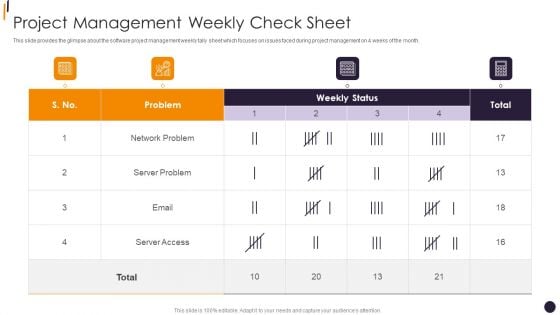
PMP Tools Project Management Weekly Check Sheet Introduction PDF
This slide provides the glimpse about the software project management weekly tally sheet which focuses on issues faced during project management on 4 weeks of the month.Deliver and pitch your topic in the best possible manner with this PMP Tools Project Management Weekly Check Sheet Introduction PDF Use them to share invaluable insights on Server Access, Network Problem, Server Problem and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Naas Architectural Framework Comparison Between Naas Iaas And Saas Template PDF
This slide depicts the comparison between network as a service, infrastructure as a service and software as a service cloud models based on billing options and services offered by these models. The NaaS model is completely based on networking hardware and software services. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Naas Architectural Framework Comparison Between Naas Iaas And Saas Template PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Naas Architectural Framework Comparison Between Naas Iaas And Saas Template PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Endpoint Initiated Vs Service Initiated Portrait PDF
This slide represents the comparison between the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Endpoint Initiated Vs Service Initiated Portrait PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
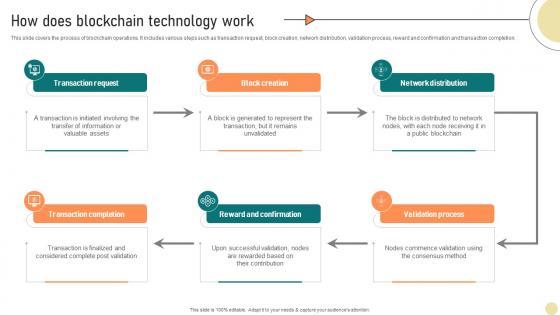
Visionary Guide To Blockchain How Does Blockchain Technology Work BCT SS V
This slide covers the process of blockchain operations. It includes various steps such as transaction request, block creation, network distribution, validation process, reward and confirmation and transaction completion. This Visionary Guide To Blockchain How Does Blockchain Technology Work BCT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Visionary Guide To Blockchain How Does Blockchain Technology Work BCT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide covers the process of blockchain operations. It includes various steps such as transaction request, block creation, network distribution, validation process, reward and confirmation and transaction completion.
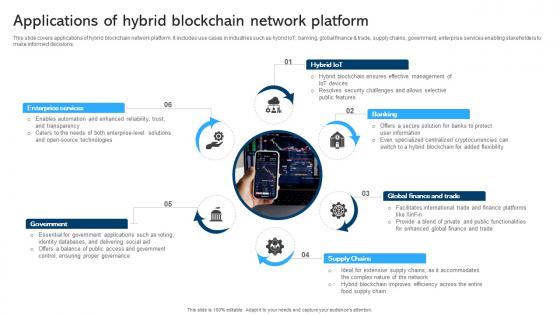
Comprehensive Manual For Blockchain Applications Of Hybrid Blockchain BCT SS V
This slide covers applications of hybrid blockchain network platform. It includes use cases in industries such as hybrid IoT, banking, global finance and trade, supply chains, government, enterprise services enabling stakeholders to make informed decisions. Want to ace your presentation in front of a live audience Our Comprehensive Manual For Blockchain Applications Of Hybrid Blockchain BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide covers applications of hybrid blockchain network platform. It includes use cases in industries such as hybrid IoT, banking, global finance and trade, supply chains, government, enterprise services enabling stakeholders to make informed decisions.
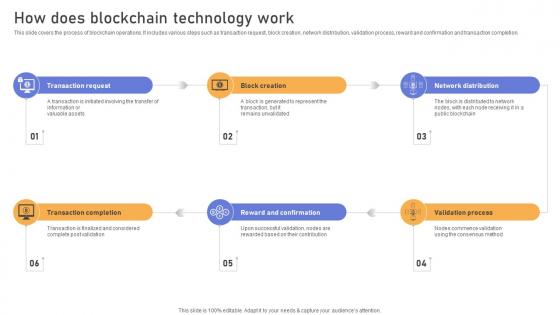
Comprehensive Look At Blockchain How Does Blockchain Technology Work BCT SS V
This slide covers the process of blockchain operations. It includes various steps such as transaction request, block creation, network distribution, validation process, reward and confirmation and transaction completion. This modern and well-arranged Comprehensive Look At Blockchain How Does Blockchain Technology Work BCT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide covers the process of blockchain operations. It includes various steps such as transaction request, block creation, network distribution, validation process, reward and confirmation and transaction completion.
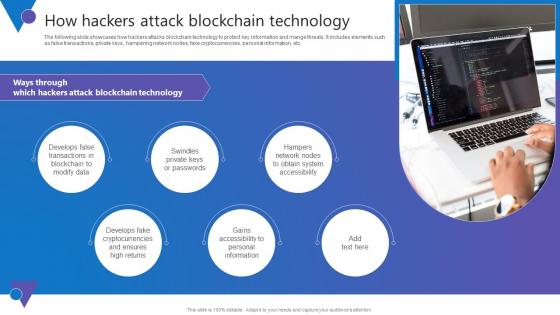
How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf
The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. How Hackers Attack Comprehensive Guide To Blockchain Digital Security Information Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc.

IT Systems Automation Playbook For Strategic Actions To Improve IT Performance Elements Pdf
This slide provides information regarding automation of IT systems through infrastructure provisioning in terms of server provisioning, user provisioning, network provisioning and service provisioning. Take your projects to the next level with our ultimate collection of IT Systems Automation Playbook For Strategic Actions To Improve IT Performance Elements Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide provides information regarding automation of IT systems through infrastructure provisioning in terms of server provisioning, user provisioning, network provisioning and service provisioning.
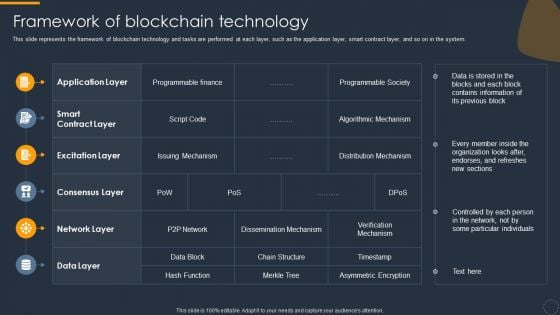
Cryptocurrency Ledger Framework Of Blockchain Technology Designs PDF
This slide represents the framework of blockchain technology and tasks are performed at each layer, such as the application layer, smart contract layer, and so on in the system. Deliver an awe inspiring pitch with this creative Cryptocurrency Ledger Framework Of Blockchain Technology Designs PDF bundle. Topics like Excitation Layer, Application Layer, Network Layer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
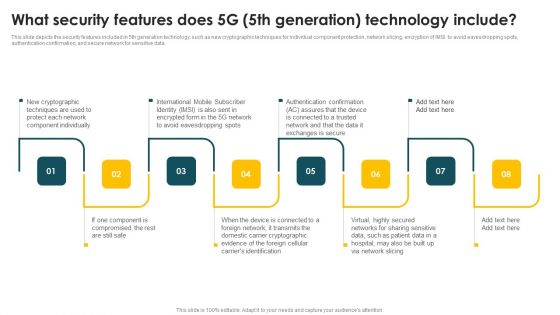
Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Explore a selection of the finest Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Aftersales Installation Services For Increasing Client Retention Through Efficient Inspiration Pdf
This slide covers various software installation services for customers, such as unattended installations, in place upgrades, remote network installations, and clean installs. Boost your pitch with our creative Aftersales Installation Services For Increasing Client Retention Through Efficient Inspiration Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide covers various software installation services for customers, such as unattended installations, in place upgrades, remote network installations, and clean installs.

Best Practices To Perform Successful CPA Marketing Executing Cost Per Action Marketing Slides Pdf
Mentioned slide showcases some of the best practices to implement an effective CPA marketing campaign. It includes hiring professional manager, tracking campaign performance, CPA network selection and proactive behaviour. Want to ace your presentation in front of a live audience Our Best Practices To Perform Successful CPA Marketing Executing Cost Per Action Marketing Slides Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. Mentioned slide showcases some of the best practices to implement an effective CPA marketing campaign. It includes hiring professional manager, tracking campaign performance, CPA network selection and proactive behaviour.

Wireless Banking To Improve Man In The Middle Mobile Banking Attacking Fin SS V
This slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. There are so many reasons you need a Wireless Banking To Improve Man In The Middle Mobile Banking Attacking Fin SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM . It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware

Comprehensive Manual For Blockchain Applications Of Public Blockchain BCT SS V
This slide covers applications of public blockchain network platform. It includes use cases such as cryptocurrencies, smart contracts, decentralized finance, supply chain management, voting and governance, intellectual property protection, charity and donations, gaming and collectibles, etc. There are so many reasons you need a Comprehensive Manual For Blockchain Applications Of Public Blockchain BCT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide covers applications of public blockchain network platform. It includes use cases such as cryptocurrencies, smart contracts, decentralized finance, supply chain management, voting and governance, intellectual property protection, charity and donations, gaming and collectibles, etc.
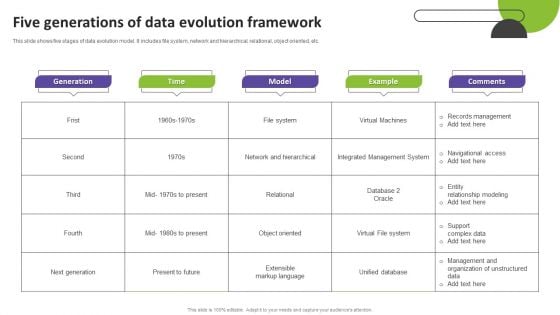
Five Generations Of Data Evolution Framework Portrait PDF
This slide shows five stages of data evolution model. It includes file system, network and hierarchical, relational, object oriented, etc. Showcasing this set of slides titled Five Generations Of Data Evolution Framework Portrait PDF. The topics addressed in these templates are Generation, Time, Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Role Of IT In Business Communication Components Role Of IT In Business Communication Pictures PDF
This slide talks about the telecommunications that connect hardware to form a network. The network can be established through wires, ethernet cables, fiber optics, or wireless technologies like wifi. Get a simple yet stunning designed Role Of IT In Business Communication Components Role Of IT In Business Communication Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Role Of IT In Business Communication Components Role Of IT In Business Communication Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
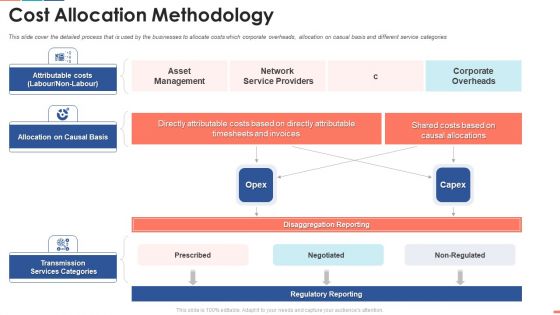
Cost Allocation Methodology Ppt Slides Example PDF
This slide cover the detailed process that is used by the businesses to allocate costs which corporate overheads, allocation on casual basis and different service categories Deliver and pitch your topic in the best possible manner with this cost allocation methodology ppt slides example pdf. Use them to share invaluable insights on asset management, network service providers, corporate overheads and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
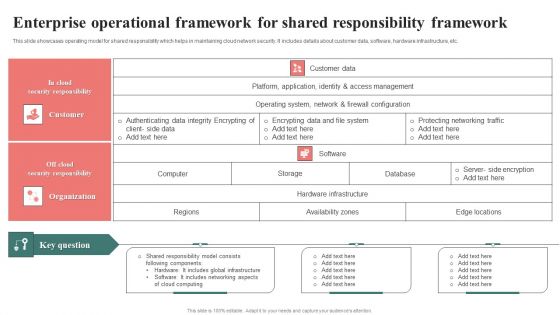
Enterprise Operational Framework For Shared Responsibility Framework Template PDF
This slide showcases operating model for shared responsibility which helps in maintaining cloud network security. It includes details about customer data, software, hardware infrastructure, etc. Showcasing this set of slides titled Enterprise Operational Framework For Shared Responsibility Framework Template PDF. The topics addressed in these templates are Customer, Organization, Responsibility Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
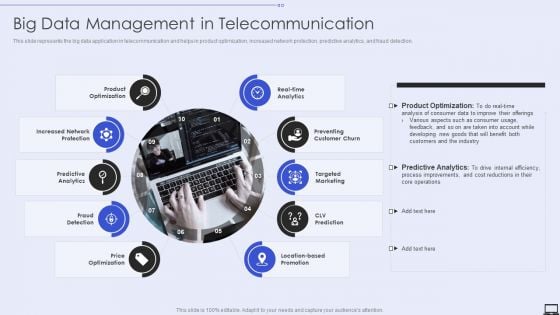
Big Data Management In Telecommunication Ppt PowerPoint Presentation File Background Images PDF
This is a Big Data Management In Telecommunication Ppt PowerPoint Presentation File Background Images PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Product Optimization, Increased Network Protection, Predictive Analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comprehensive Manual For Blockchain Hybrid Vs Consortium Blockchain BCT SS V
This slide covers comparing and contrasting hybrid and consortium blockchain network technologies. It includes basis of comparison such as assess, authority, consensus, data handling, efficiency, immutability, transaction cost and speed. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Comprehensive Manual For Blockchain Hybrid Vs Consortium Blockchain BCT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Comprehensive Manual For Blockchain Hybrid Vs Consortium Blockchain BCT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide covers comparing and contrasting hybrid and consortium blockchain network technologies. It includes basis of comparison such as assess, authority, consensus, data handling, efficiency, immutability, transaction cost and speed.
Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf
The following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Slidegeeks is here to make your presentations a breeze with Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc.

Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security Slidegeeks is here to make your presentations a breeze with Strategies For Every Phase Enhancing Workload Efficiency Through Cloud Architecture Ideas Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security
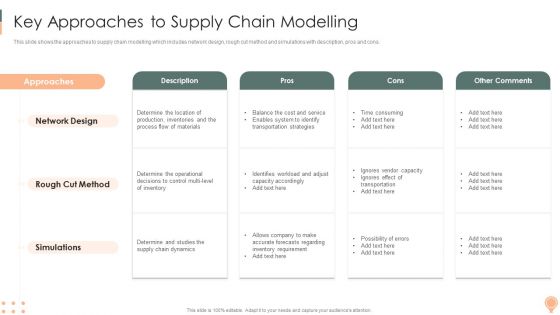
Supply Chain Approaches Key Approaches Tosupply Chain Modelling Demonstration PDF
This slide shows the approaches to supply chain modelling which includes network design, rough cut method and simulations with description, pros and cons.Deliver an awe inspiring pitch with this creative Supply Chain Approaches Key Approaches Tosupply Chain Modelling Demonstration PDF bundle. Topics like Production Inventories, Determine Operational, Chain Dynamics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
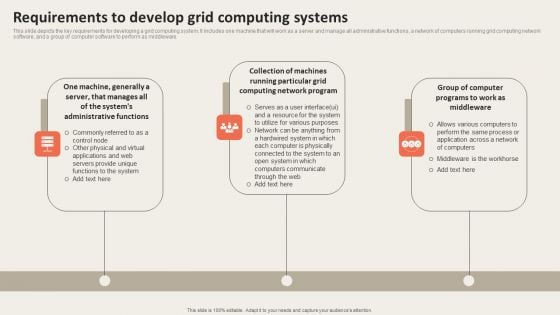
Grid Computing Applications Requirements To Develop Grid Computing Systems Information PDF
This slide depicts the key requirements for developing a grid computing system. It includes one machine that will work as a server and manage all administrative functions, a network of computers running grid computing network software, and a group of computer software to perform as middleware. Explore a selection of the finest Grid Computing Applications Requirements To Develop Grid Computing Systems Information PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Grid Computing Applications Requirements To Develop Grid Computing Systems Information PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
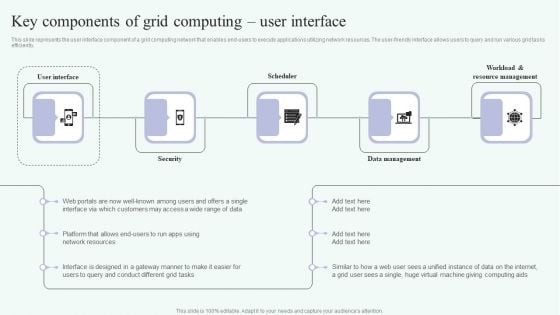
Grid Computing For High Performance Solutions Key Components Of Grid Computing User Interface Elements PDF
This slide represents the user interface component of a grid computing network that enables end-users to execute applications utilizing network resources. The user-friendly interface allows users to query and run various grid tasks efficiently. Explore a selection of the finest Grid Computing For High Performance Solutions Key Components Of Grid Computing User Interface Elements PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Grid Computing For High Performance Solutions Key Components Of Grid Computing User Interface Elements PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
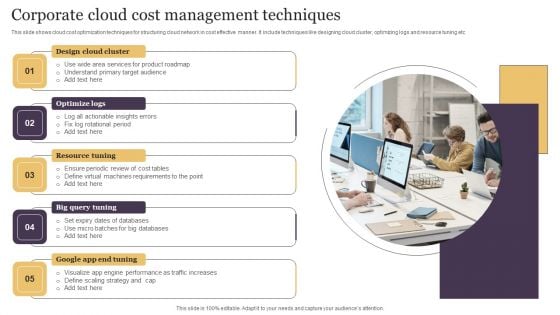
Corporate Cloud Cost Management Techniques Template PDF
This slide shows cloud cost optimization techniques for structuring cloud network in cost effective manner. It include techniques like designing cloud cluster, optimizing logs and resource tuning etc. Presenting Corporate Cloud Cost Management Techniques Template PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Design Cloud Cluster, Optimize Logs, Resource Tuning. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
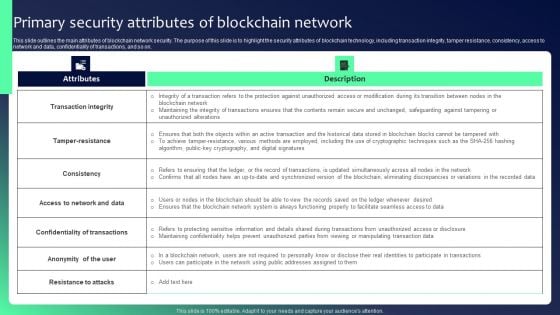
Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF
This slide outlines the main attributes of blockchain network security. The purpose of this slide is to highlight the security attributes of blockchain technology, including transaction integrity, tamper resistance, consistency, access to network and data, confidentiality of transactions, and so on. The Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Requirements To Develop Grid Computing Systems Pictures PDF
This slide depicts the key requirements for developing a grid computing system. It includes one machine that will work as a server and manage all administrative functions, a network of computers running grid computing network software, and a group of computer software to perform as middleware. The Requirements To Develop Grid Computing Systems Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.


 Continue with Email
Continue with Email

 Home
Home


































