Network Security
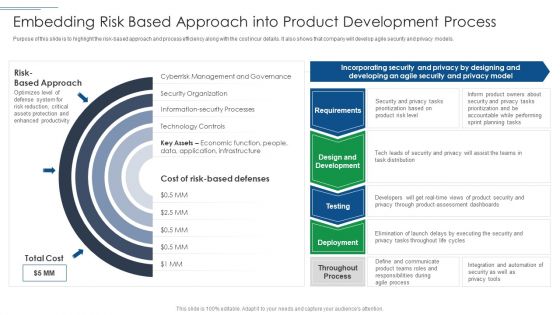
IT Security Risk Management Approach Introduction Embedding Risk Based Approach Into Product Information PDF
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Embedding Risk Based Approach Into Product Information PDF bundle. Topics like Technology Controls, Information Security Processes, Security Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
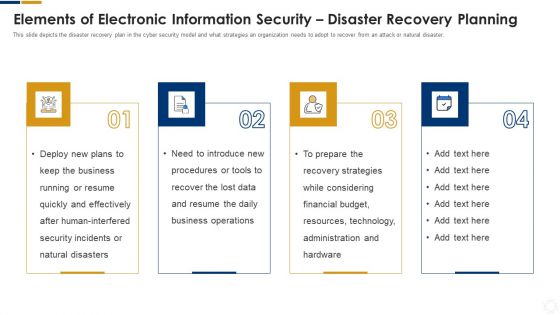
Cybersecurity Elements Of Electronic Information Security Disaster Recovery Planning Ppt Gallery Graphics PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting cybersecurity elements of electronic information security disaster recovery planning ppt gallery graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, plans, security, financial, budget. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
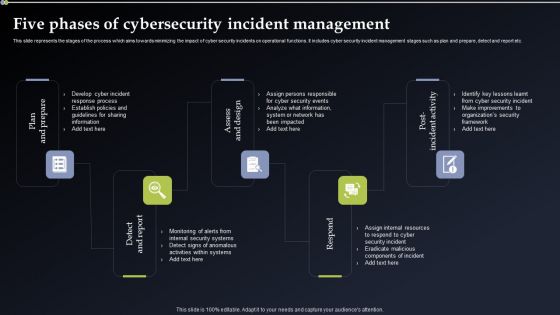
Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Five Phases Of Cybersecurity Incident Management Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
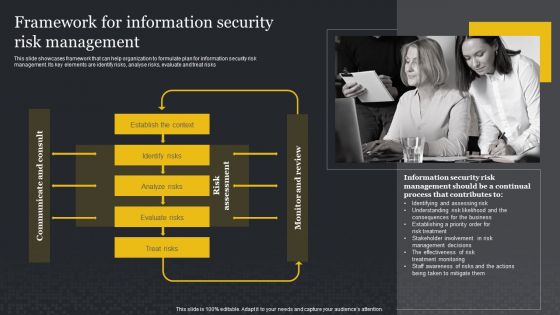
Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks. Presenting this PowerPoint presentation, titled Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Security Management Plan Steps In Detail Adopting Access Controls Download PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls download pdf bundle. Topics like logical access controls, control implementation costs, physical access controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Devops Engineer Capabilities Software Security Skills Ppt Slides Graphics Template PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. This is a devops engineer capabilities software security skills ppt slides graphics template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like vulnerability management, threat investigation, compliance monitoring, security training, code analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
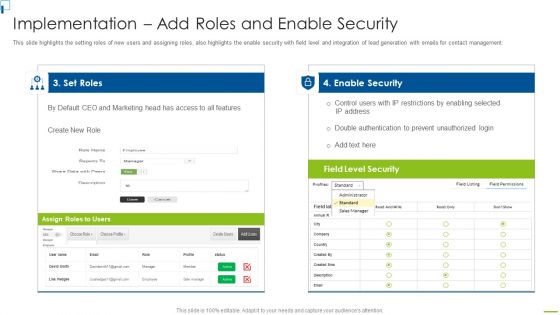
Designing And Deployment Implementation Add Roles And Enable Security Sample PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Deliver and pitch your topic in the best possible manner with this designing and deployment implementation add roles and enable security sample pdf. Use them to share invaluable insights on set roles, enable security, assign roles to users, field level security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
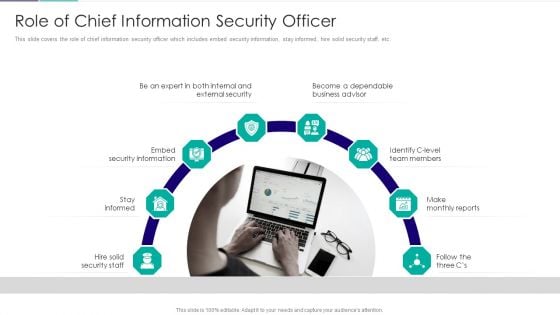
Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc.This is a Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Become A Dependable, Identify C Level Team Members, Make Monthly Reports You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Major Saas Cloud Security Challenges For IT Department Ppt PowerPoint Presentation Gallery Design Templates PDF
The following slide highlights some SaaS security challenges faced by IT team to plan mitigation actions. It mainly includes file security, insider threat, privilege access etc. Presenting Major Saas Cloud Security Challenges For It Department Ppt PowerPoint Presentation Gallery Design Templates PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including File Security, Insider Threat, Imposing Minimum, Privilege Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
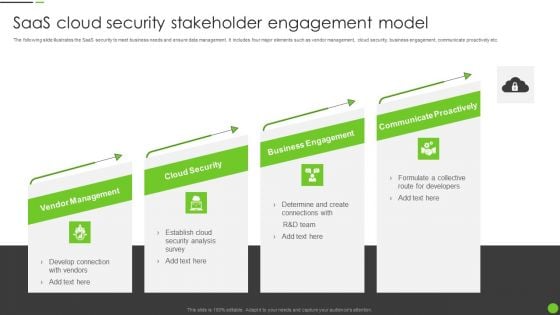
Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide illustrates the SaaS security to meet business needs and ensure data management. It includes four major elements such as vendor management, cloud security, business engagement, communicate proactively etc. Presenting Saas Cloud Security Stakeholder Engagement Model Ppt PowerPoint Presentation Gallery Design Ideas PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Vendor Management, Cloud Security, Business Engagement, Communicate Proactively. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
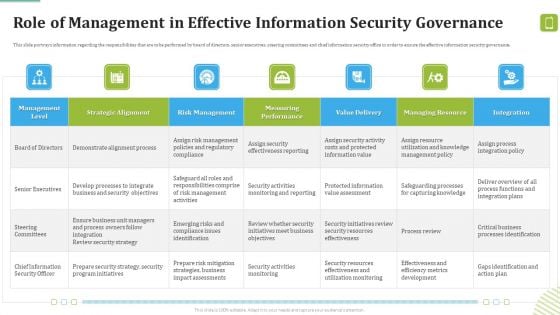
MDM Strategies At Office Role Of Management In Effective Information Security Governance Ideas PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver an awe inspiring pitch with this creative MDM Strategies At Office Role Of Management In Effective Information Security Governance Ideas PDF bundle. Topics like Demonstrate Alignment, Business Security, Program Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF
The following slide highlights multistep process of digitization of security systems. The company can detect security breach after following steps such as investigating the steps of IT analyst, determining responsive action, eradication and closing the ticked. Presenting Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF
The following slide highlights a comprehensive checklist for digitization of security systems. The checklist covers key points such as deciding the budget, selecting the right tools, deciding the tasks for automation etc. Presenting Multistep Digitization Of Security Systems Checklist Ppt Portfolio Example File PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security Automation, Checklist, Security Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
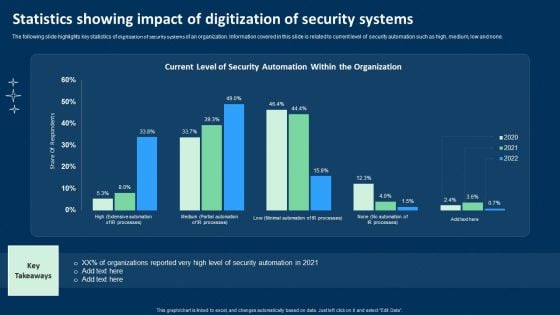
Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF
The following slide highlights key statistics of digitization of security systems of an organization. Information covered in this slide is related to current level of security automation such as high, medium, low and none. Showcasing this set of slides titled Statistics Showing Impact Of Digitization Of Security Systems Ppt Show Ideas PDF. The topics addressed in these templates are Current Level, Security Automation, Organization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
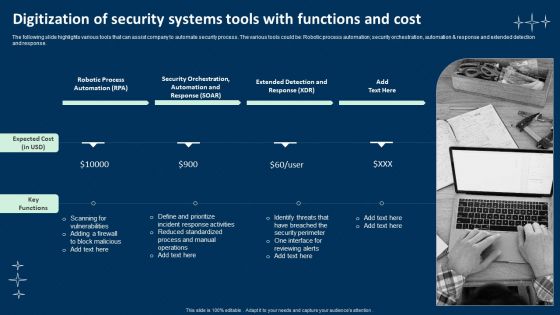
Digitization Of Security Systems Tools With Functions And Cost Mockup PDF
The following slide highlights various tools that can assist company to automate security process. The various tools could be Robotic process automation, security orchestration, automation and response and extended detection and response. Presenting Digitization Of Security Systems Tools With Functions And Cost Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Robotic Process Automation, Security Orchestration, Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Manpower Corporate Security Business Profile Executive Leadership And Management Team Template PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Manpower Corporate Security Business Profile Executive Leadership And Management Team Template PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Business, Security Operations, Resource Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
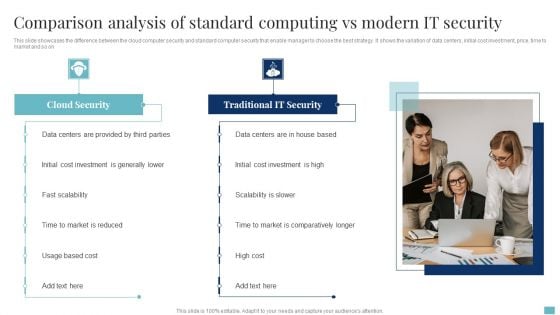
Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF
This slide showcases the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market and so on. Persuade your audience using this Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Data Centers, Cloud Security, Cost Investment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
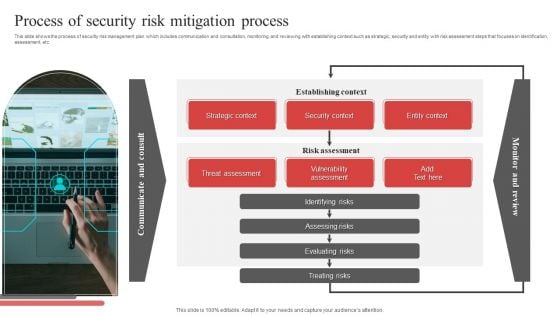
Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide shows the process of security risk management plan which includes communication and consultation, monitoring and reviewing with establishing context such as strategic, security and entity with risk assessment steps that focuses on identification, assessment, etc. Presenting Process Of Security Risk Mitigation Process Ppt PowerPoint Presentation File Visual Aids PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Strategic Context, Security Context, Entity Context, Establishing Context. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Management Plan Steps In Detail Risk Assessment And Analysis Introduction PDF
This slide provides information about the third step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Risk Assessment and Analysis. Deliver an awe inspiring pitch with this creative security management plan steps in detail risk assessment and analysis introduction pdf bundle. Topics like information, system, risks, measures can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Techniques And Strategies To Reduce Security Management Risks Measures And Ways To Mitigate Clipart PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks measures and ways to mitigate clipart pdf Use them to share invaluable insights on potential insider threats, external security breaches, centric breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
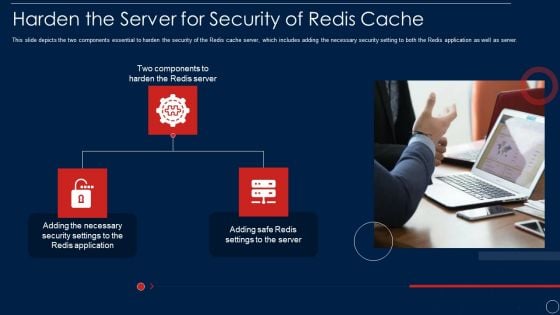
Redis Cache Data Structure IT Harden The Server For Security Of Redis Cache Template PDF
This slide depicts the two components essential to harden the security of the Redis cache server, which includes adding the necessary security setting to both the Redis application as well as server. This is a redis cache data structure it harden the server for security of redis cache template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like harden the server for security of redis cache. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development quality control, and evaluation of the companys security regulatory compliance.Presenting IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Systems, Applications, Correcting Security, Regulatory Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Systems Security And Risk Management Plan Meet Our Team Template PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Impact Of Information Security Loss On Organization Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF
Pitch your topic with ease and precision using this Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF. This layout presents information on Pathway Change Framework, Food Security Sustainable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Governance Plan Framework For Data Security Ppt PowerPoint Presentation Gallery Model PDF
Presenting governance plan framework for data security ppt powerpoint presentation gallery model pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including data security, data governance, physical data governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Data Management Plan Framework With Security And Auditing Ppt Icon File Formats PDF
Presenting data management plan framework with security and auditing ppt icon file formats pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including data lifestyle management, data security, capability needs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings. Get a simple yet stunning designed Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Introduction To Smart Locks Used For Enhancing Safety And Security Utilizing Smart Appliances IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides an overview of the smart lock system used for increased security. The slide includes features of the smart lock security system that are it helps in real-time monitoring, improve connectivity, create entry codes and allow auto-lock settings.

Project Security Administration IT Contingency Plan For Managing Threats To Ensure It Project Safety Mockup PDF
This slide provides information regarding contingency plan for managing threats to ensure IT project safety with aid of technical equipment ensuring contingency plans. Deliver an awe inspiring pitch with this creative project security administration it contingency plan for managing threats to ensure it project safety mockup pdf bundle. Topics like distributes systems, mainframe systems, wide area network, local area network, website can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
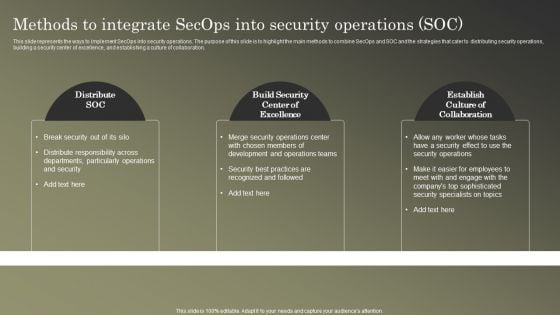
Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF
This slide represents the ways to implement SecOps into security operations. The purpose of this slide is to highlight the main methods to combine SecOps and SOC and the strategies that cater to distributing security operations, building a security center of excellence, and establishing a culture of collaboration. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
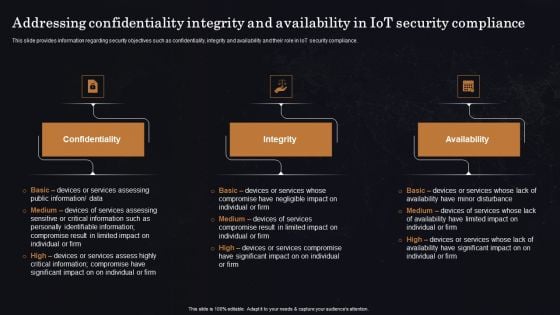
Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF
This slide provides information regarding security objectives such as confidentiality, integrity and availability and their role in IoT security compliance. Boost your pitch with our creative Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
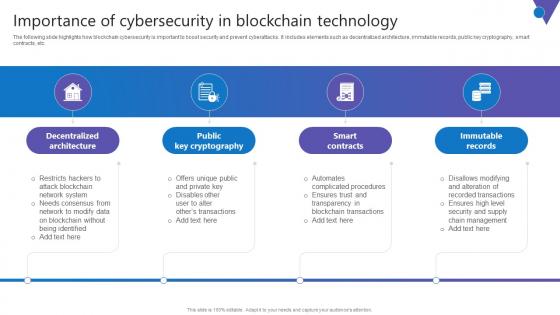
Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Find highly impressive Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Importance Of Cybersecurity In Comprehensive Guide To Blockchain Digital Security Summary Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc.
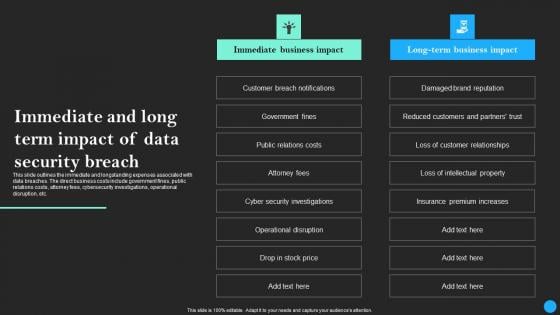
Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Retrieve professionally designed Immediate And Long Term Impact Of Data Security Breach Data Breach Prevention Topics Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc.
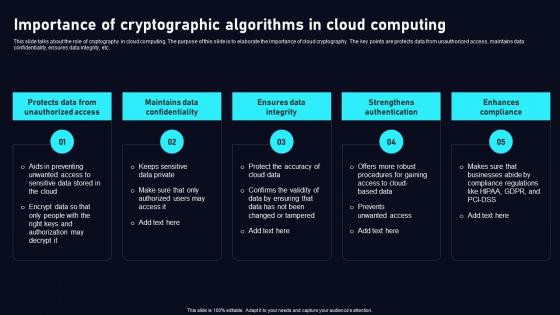
Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Boost your pitch with our creative Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF
This slide outlines the roles and responsibilities of the security operations center team. The purpose of this slide is to showcase the roles as well as duties of the SOC team. The prominent roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Welcome to our selection of the Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Email Security Market Research Report Ppt PowerPoint Presentation Complete Deck With Slides

Global Cloud Based Email Security Market Ppt PowerPoint Presentation Complete Deck With Slides
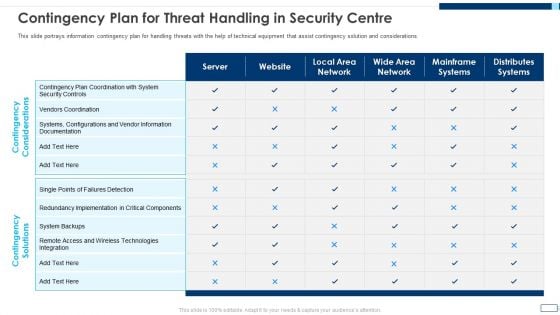
Evolving BI Infrastructure Contingency Plan For Threat Handling In Security Centre Pictures PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this evolving bi infrastructure contingency plan for threat handling in security centre pictures pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems, distributes systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Develop Corporate Cyber Security Risk Mitigation Plan Why Us For Organization Cyber Protection Services Sample PDF
Presenting develop corporate cyber security risk mitigation plan why us for organization cyber protection services sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like knowledge, system security, net development, it support services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
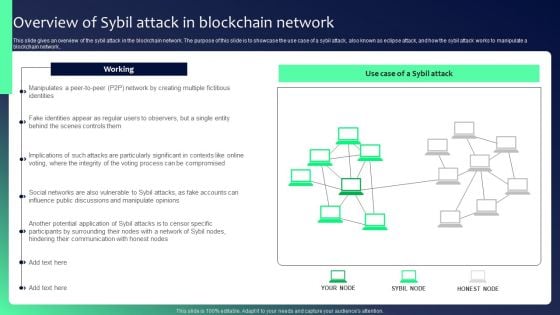
Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF
This slide gives an overview of the sybil attack in the blockchain network. The purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network.. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Blockchain Security Solutions Deployment Overview Of Sybil Attack In Blockchain Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
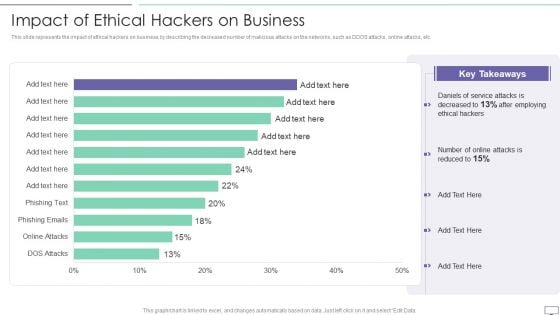
IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF
This slide represents the impact of ethical hackers on business by describing the decreased number of malicious attacks on the networks, such as DDOS attacks, online attacks, etc.Deliver an awe inspiring pitch with this creative IT Security Hacker Impact Of Ethical Hackers On Business Slides PDF bundle. Topics like Key Takeaways, Daniels Of Service, After Employing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT Ss V
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable IoT Device Management Fundamentals Best Practices For Optimising IoT Healthcare Security IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Get a simple yet stunning designed Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF
This slide covers quarterly cyber security planning roadmap by management to reduce risk with program maturity and cost .It consist secure , defend, contain, manage and anticipate. Persuade your audience using this Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Management, Level Risk Reduction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
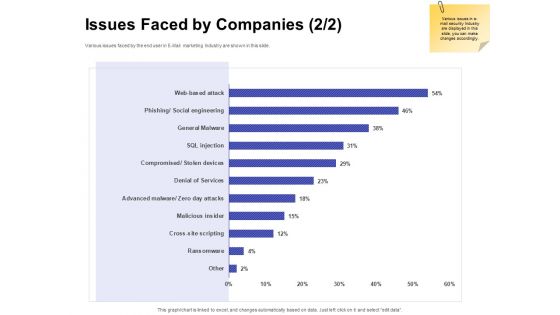
Global Cloud Based Email Security Market Issues Faced By Companies Services Portrait PDF
Presenting this set of slides with name global cloud based email security market issues faced by companies services portrait pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
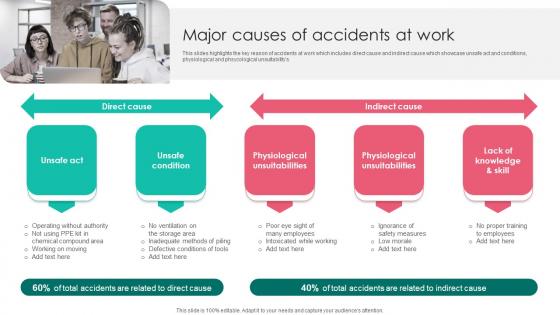
Major Causes Of Accidents Workplace Safety Protocol And Security Practices Portrait Pdf
This slides highlights the key reason of accidents at work which includes direct cause and indirect cause which showcase unsafe act and conditions, physiological and phsycological unsuitabilitys. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Major Causes Of Accidents Workplace Safety Protocol And Security Practices Portrait Pdf from Slidegeeks and deliver a wonderful presentation. This slides highlights the key reason of accidents at work which includes direct cause and indirect cause which showcase unsafe act and conditions, physiological and phsycological unsuitabilitys.
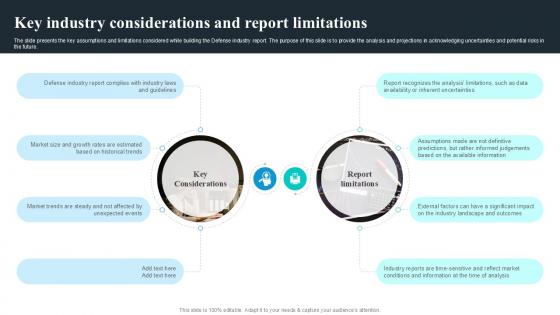
Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. The slide presents the key assumptions and limitations considered while building the Defense industry report. The purpose of this slide is to provide the analysis and projections in acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile.

Products And Services Offered Voice Assistance Security Platform Investor Funding Rules Pdf
This slide represents product and solution categories offered by business which are session replays, heatmaps, team dashboards, user journeys, user segmentation, funnel analytics, events analytics, issue analytics, 3rd party integrations, understand UX, increase conversions, drive engagement and resolve issues. Do you know about Slidesgeeks Products And Services Offered Voice Assistance Security Platform Investor Funding Rules Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide represents product and solution categories offered by business which are session replays, heatmaps, team dashboards, user journeys, user segmentation, funnel analytics, events analytics, issue analytics, 3rd party integrations, understand UX, increase conversions, drive engagement and resolve issues.

Cyber Security Implementation Framework Impact Analysis Implementing Cybersecurity Framework Ppt Show Graphics PDF
Presenting this set of slides with name cyber security implementation framework impact analysis implementing cybersecurity framework ppt show graphics pdf. The topics discussed in these slides are csf metric, controls met, nist core functions, target, trend. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF
This template covers tools to measure marketing analytics such as google analytics for all web tracking, google data studio to build real-time reporting dashboards and google data studio reports.Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Google Analytics For All Web Tracking Mockup PDF. Use them to share invaluable insights on Demographics, Social Networks, Sessions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Stages To Develop Security Analysis Approach Documentation Ppt PowerPoint Presentation File Graphics PDF
Showcasing this set of slides titled stages to develop security analysis approach documentation ppt powerpoint presentation file graphics pdf. The topics addressed in these templates are relevant frameworks, stages to develop security, analysis approach documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
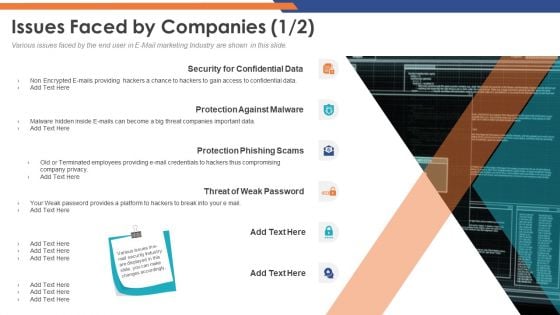
Email Security Market Research Report Issues Faced By Companies Professional PDF
Presenting this set of slides with name email security market research report issues faced by companies professional pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
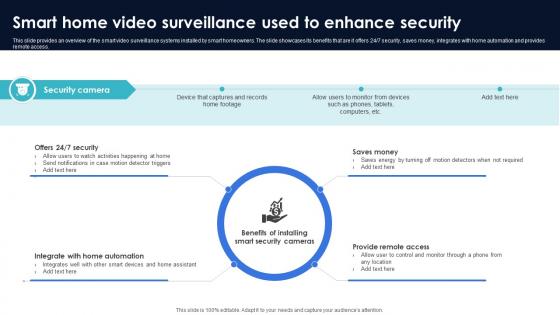
Optimization Of IoT Remote Monitoring Smart Home Video Surveillance Used To Enhance Security IoT SS V
This slide provides an overview of the smart video surveillance systems installed by smart homeowners. The slide showcases its benefits that are it offers 24x7 security, saves money, integrates with home automation and provides remote access. Slidegeeks has constructed Optimization Of IoT Remote Monitoring Smart Home Video Surveillance Used To Enhance Security IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide provides an overview of the smart video surveillance systems installed by smart homeowners. The slide showcases its benefits that are it offers 24x7 security, saves money, integrates with home automation and provides remote access.

About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.

Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Retrieve professionally designed Implementing Cybersecurity Awareness Program To Prevent Attacks Need For Cyber Security Awareness Training Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. There are so many reasons you need a Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Template PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Implementation Framework Budget For Effective Cybersecurity Management Ppt PowerPoint Presentation Layouts Vector PDF
Presenting this set of slides with name cyber security implementation framework budget for effective cybersecurity management ppt powerpoint presentation layouts vector pdf. This is a one stage process. The stages in this process are functional area, software, implement duration, cost implementation, incident management, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


 Continue with Email
Continue with Email

 Home
Home


































