Network Security
Global Cyber Terrorism Incidents On The Rise IT Roadmap To Implement Cyber Security Icons PDF
This slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. This is a global cyber terrorism incidents on the rise it roadmap to implement cyber security icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like keep the hardware and software updated, awareness training for employees, creating personal accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
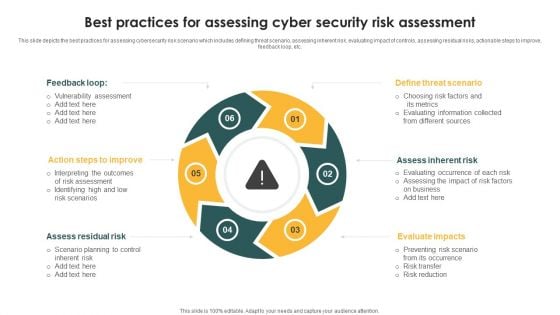
Best Practices For Assessing Cyber Security Risk Assessment Ppt PowerPoint Presentation File Graphics Template PDF
This slide depicts the best practices for assessing cybersecurity risk scenario which includes defining threat scenario, assessing inherent risk, evaluating impact of controls, assessing residual risks, actionable steps to improve, Presenting Best Practices For Assessing Cyber Security Risk Assessment Ppt PowerPoint Presentation File Graphics Template PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Feedback Loop, Assess Residual Risk, Evaluate Impacts, Assess Inherent Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
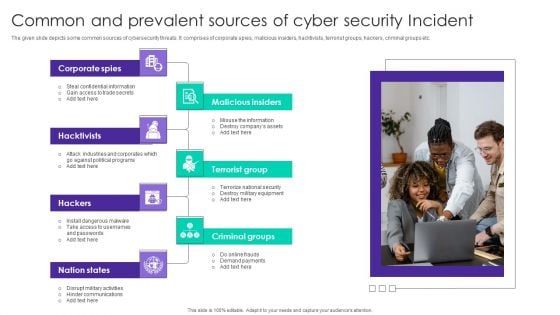
Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
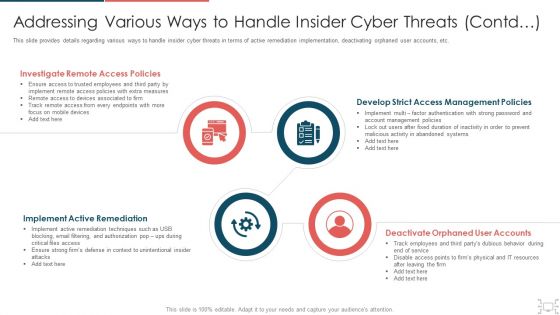
cyber security administration in organization addressing various ways to handle insider cyber active template pdf
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting cyber security administration in organization addressing various ways to handle insider cyber active template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like investigate, access, policies, remediation, implement . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
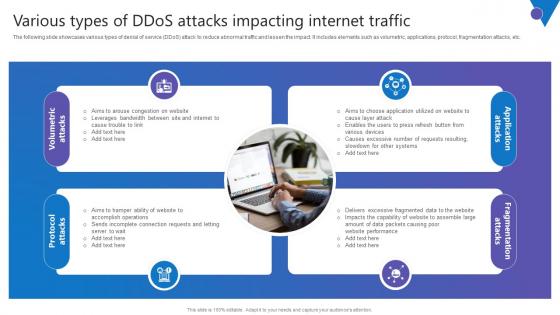
Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf
The following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Get a simple yet stunning designed Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Various Types Of DDoS Attacks Comprehensive Guide To Blockchain Digital Security Introduction Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. The following slide showcases various types of denial of service DDoS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc.

Impact On Food Demand And Food Security Due To Covid Crisis Ppt Pictures Layout PDF
This template covers Impact On Food Demand And Food Security such as demand of food has affected due to reduction in income and purchasing capacity. It also covers the impact of school closure on childrens who are dependent on school meal programs. This is a impact on food demand and food security due to covid crisis ppt pictures layout pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management strategy, price, source, services, production. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with IT System Risk Management Guide Financial Burden To Company From IT Security Breaches Background PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
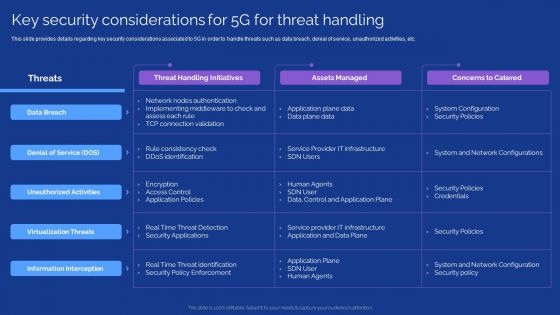
Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. This modern and well arranged Development Guide For 5G World Key Security Considerations For 5G For Threat Handling Slides PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
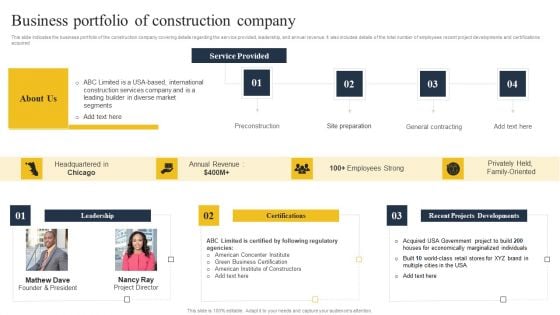
Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF
This slide indicates the business portfolio of the construction company covering details regarding the service provided, leadership, and annual revenue. It also includes details of the total number of employees recent project developments and certifications acquired. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Security Control Techniques For Real Estate Project Business Portfolio Of Construction Company Professional PDF

Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF
This slide showcases identifying inherent risk factors and measures. It provides information about customer base, products, services, delivery channels, jurisdictions, qualitative factors, location, customer risk rating, transparency, fund transfer, etc. Create an editable KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Security Software Company Investor Funding Pitch Deck Value Proposition USP Introduction PDF
This slide showcases unique selling propositions of solution offered by IT company differentiates product from others. Differentiators are quick time-to-value , high effectiveness for detection and response , platform-as-a-service technique and have patents for Ava, EntityiQ and adversarial modeling. Explore a selection of the finest Security Software Company Investor Funding Pitch Deck Value Proposition USP Introduction PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Security Software Company Investor Funding Pitch Deck Value Proposition USP Introduction PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF
This slide gives an overview of the compliance pillar of cloud access security broker. The purpose of this slide is to showcase how compliance is a vital factor for an organization migrating its data and systems to the cloud. Compliance can help industries such as healthcare, retail, and financial services. Present like a pro with Cloud Access Security Broker Pillar Compliance Ppt PowerPoint Presentation File Layouts PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
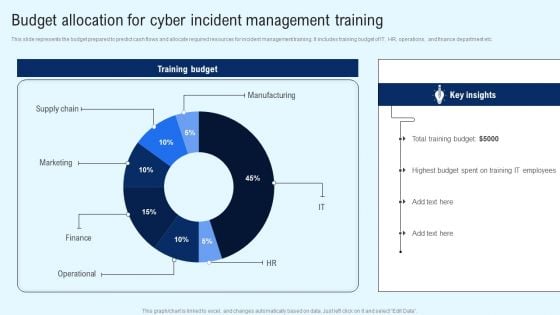
Implementing Cyber Security Incident Budget Allocation For Cyber Incident Portrait PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Find a pre designed and impeccable Implementing Cyber Security Incident Budget Allocation For Cyber Incident Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Companys Data Safety Recognition Security Awareness New Strategies For Learning Diagrams PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver and pitch your topic in the best possible manner with this companys data safety recognition security awareness new strategies for learning diagrams pdf. Use them to share invaluable insights on learning management, methodologies, risk profile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
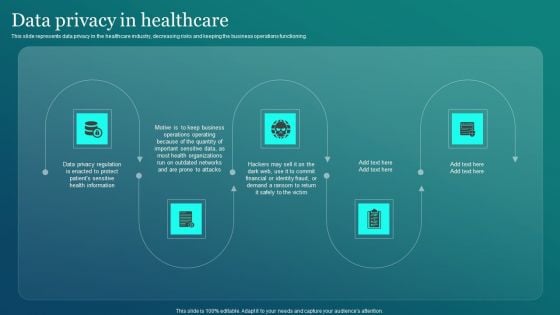
Information Security Data Privacy In Healthcare Ppt PowerPoint Presentation File Layouts PDF
This slide represents data privacy in the healthcare industry, decreasing risks and keeping the business operations functioning. There are so many reasons you need a Information Security Data Privacy In Healthcare Ppt PowerPoint Presentation File Layouts PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Table Of Contents For Integrating Data Privacy System To Enhance Security Themes PDF
Want to ace your presentation in front of a live audience Our Table Of Contents For Integrating Data Privacy System To Enhance Security Themes PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
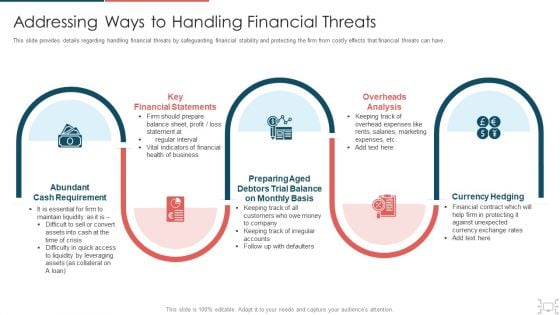
cyber security administration in organization addressing ways to handling financial threats summary pdf
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. This is a cyber security administration in organization addressing ways to handling financial threats summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, statements, requirement, preparing, balance . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
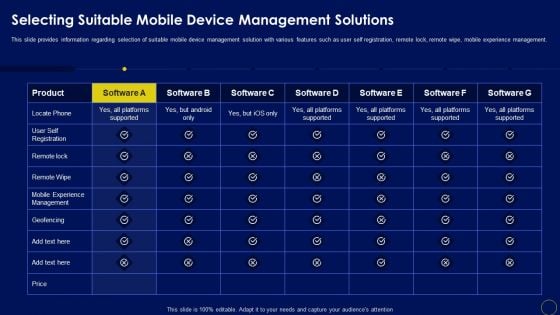
Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF
This slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Find highly impressive Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
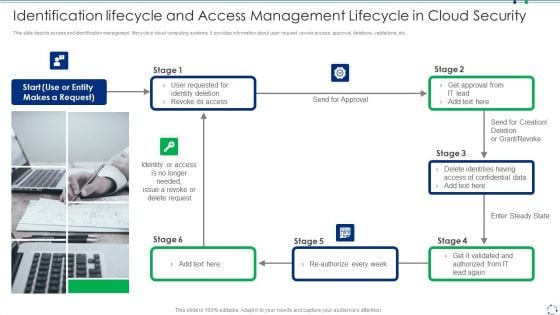
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
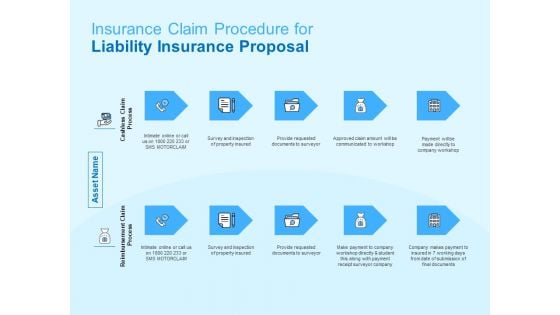
Damage Security Insurance Proposal Insurance Claim Procedure For Liability Insurance Proposal Ppt Infographic Template Summary PDF
This is a damage security insurance proposal insurance claim procedure for liability insurance proposal ppt infographic template summary pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cashless claim process, reimbursement claim process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
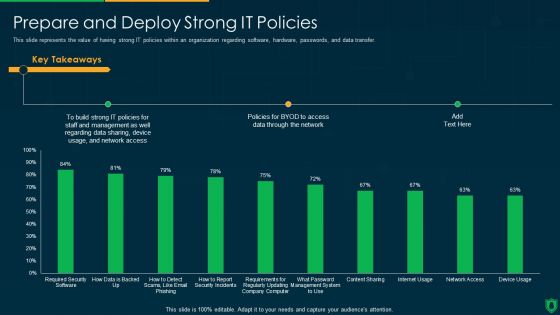
Info Security Prepare And Deploy Strong IT Policies Ppt PowerPoint Presentation File Model PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative info security prepare and deploy strong it policies ppt powerpoint presentation file model pdf bundle. Topics like build strong, it policies, data sharing, access data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Damage Security Insurance Proposal Our Offerings For Liability Insurance Proposal Ppt Show Ideas PDF
Presenting damage security insurance proposal our offerings for liability insurance proposal ppt show ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like people, assets, liability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Cover Letter For Liability Insurance Proposal Ppt Slides Graphic Tips PDF
Presenting damage security insurance proposal cover letter for liability insurance proposal ppt slides graphic tips pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like cover letter. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Insurance Outline For Liability Insurance Proposal Ppt Visual Aids Show PDF
This is a damage security insurance proposal insurance outline for liability insurance proposal ppt visual aids show pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like opportunity, legally, liability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Damage Security Insurance Proposal Next Step For Liability Insurance Proposal Ppt Summary Outline PDF
Presenting damage security insurance proposal next step for liability insurance proposal ppt summary outline pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like next step. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Our Major Clients For Liability Insurance Proposal Ppt Inspiration Backgrounds PDF
Presenting damage security insurance proposal our major clients for liability insurance proposal ppt inspiration backgrounds pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like major clients liability insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Damage Security Insurance Proposal Project Context For Liability Insurance Proposal Ppt File Examples PDF
This is a damage security insurance proposal project context for liability insurance proposal ppt file examples pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like liability, human resource, insurance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
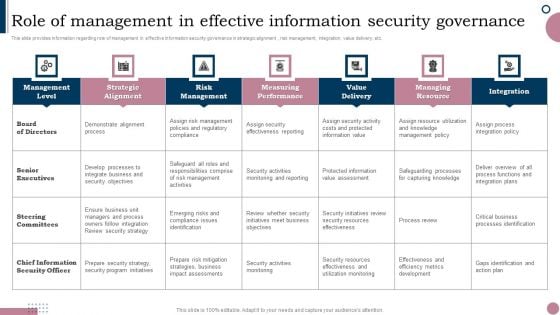
Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Retrieve professionally designed Cios Guide To Optimize Role Of Management In Effective Information Security Governance Diagrams PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
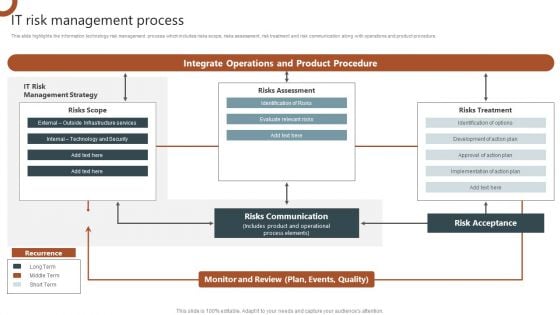
IT Risk Management Process Organizations Risk Management And IT Security Slides PDF
This slide highlights the information technology risk management process which includes risks scope, risks assessment, risk treatment and risk communication along with operations and product procedure. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Risk Management Process Organizations Risk Management And IT Security Slides PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Risk Management Process Organizations Risk Management And IT Security Slides PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Organizations Risk Management And IT Security Need Of IT Risk Management Portrait PDF
The following slide highlights the importance of information risk management which includes safer environment, reduce unexpected events, financial benefits, saves time and effort, and improves security. Present like a pro with Organizations Risk Management And IT Security Need Of IT Risk Management Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
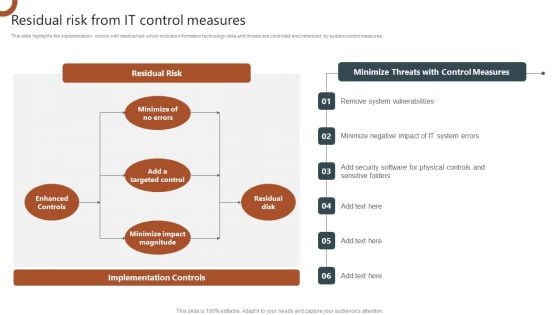
Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF
This slide highlights the implementation control with residual risk which includes information technology risks and threats are controlled and minimized by system control measures. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF today and make your presentation stand out from the rest.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.
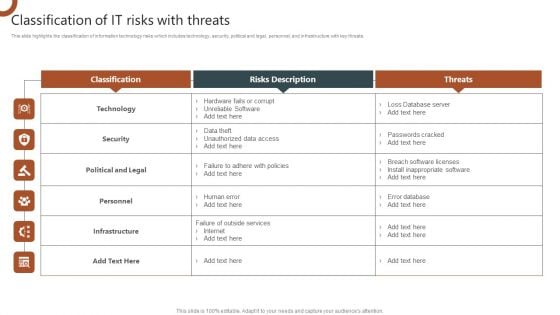
Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
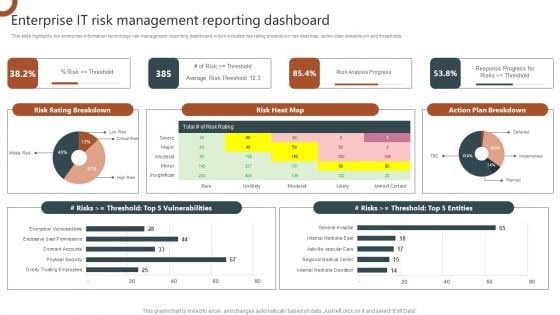
Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF
This slide highlights the enterprise information technology risk management reporting dashboard which includes risk rating breakdown risk heat map, action plan breakdown and thresholds. This Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
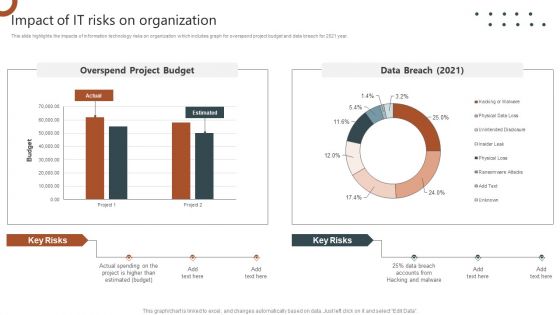
Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF
This slide highlights the impacts of information technology risks on organization which includes graph for overspend project budget and data breach for 2021 year. Explore a selection of the finest Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
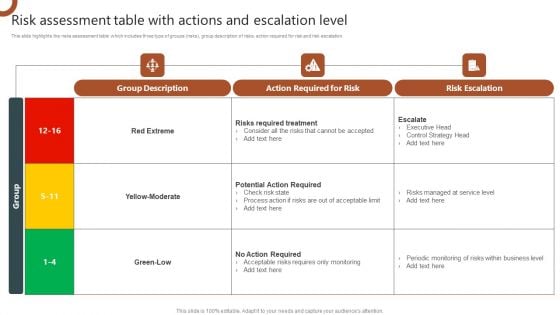
Organizations Risk Management And IT Security Risk Assessment Table With Actions And Escalation Level Background PDF
This slide highlights the risks assessment table which includes three type of groups risks, group description of risks, action required for risk and risk escalation. Retrieve professionally designed Organizations Risk Management And IT Security Technical Security Control Model With Supporting Function Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Certified Information Systems Security Professional CISSP Examination Details IT Certifications To Enhance Pictures PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc.Find highly impressive Certified Information Systems Security Professional CISSP Examination Details IT Certifications To Enhance Pictures PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Certified Information Systems Security Professional CISSP Examination Details IT Certifications To Enhance Pictures PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Present like a pro with Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets.Are you searching for a Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF from Slidegeeks today.

Matrix For Threat Solution And Risk Management Information Security Risk Administration Inspiration PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack.Welcome to our selection of the Matrix For Threat Solution And Risk Management Information Security Risk Administration Inspiration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
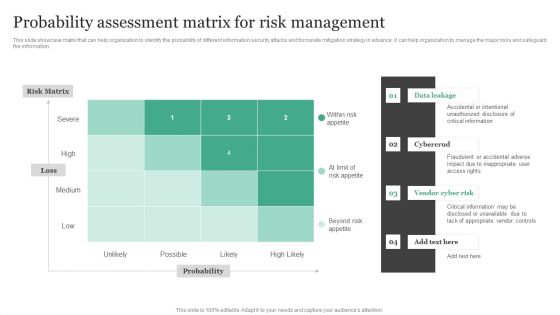
Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.This Probability Assessment Matrix For Risk Management Information Security Risk Administration Pictures PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
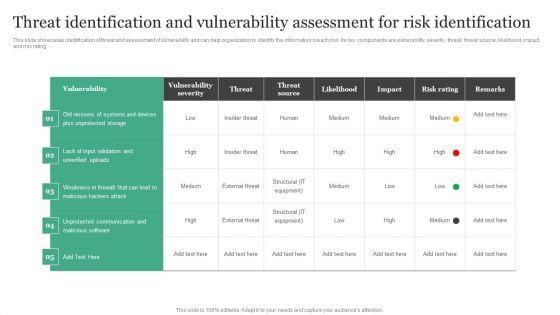
Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Get a simple yet stunning designed Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
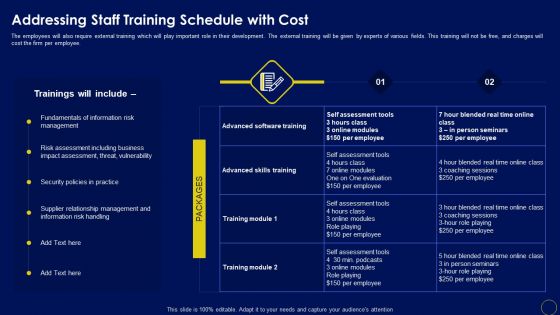
Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Addressing Staff Training Schedule With Cost Business Mobile Device Security Management And Mitigation Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
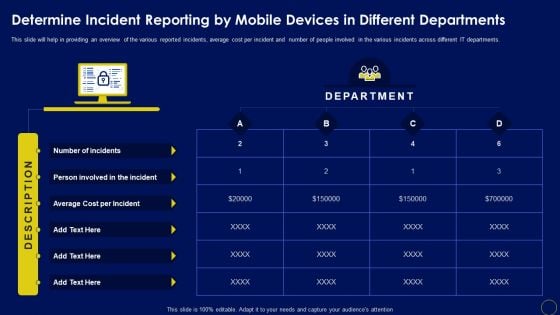
Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different IT departments. Are you searching for a Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Determine Incident Reporting By Mobile Devices In Business Mobile Device Security Management Designs PDF from Slidegeeks today.
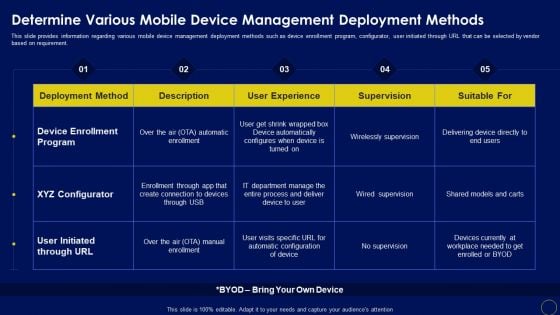
Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF.
Key Features Associated To Mobile Device Management Business Mobile Device Security Icons PDF
This slide provides information regarding key features associated to mobile device management such as mobile device enrolment, user profile management, mobile device management support. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Key Features Associated To Mobile Device Management Business Mobile Device Security Icons PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Key Features Associated To Mobile Device Management Business Mobile Device Security Icons PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Table Of Contents For Business Mobile Device Security Management And Mitigation Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
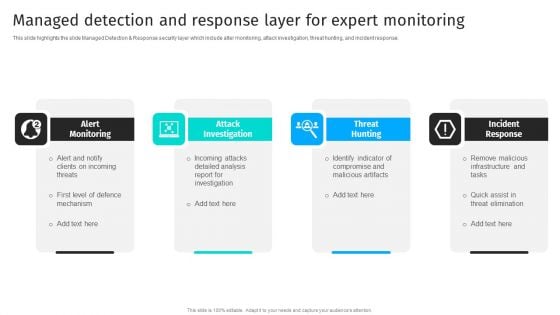
Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF
This slide highlights the slide Managed Detection Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
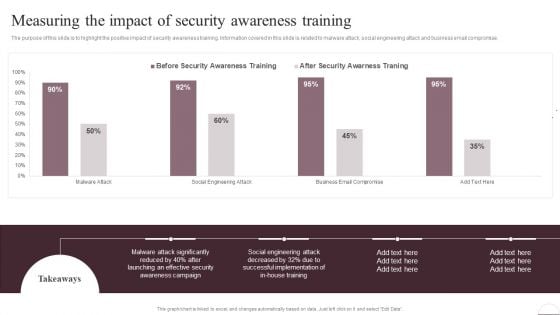
Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. The Prevention Of Information Measuring The Impact Of Security Awareness Training Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF
This slide represents the seven principles of GDPR law, including lawfulness and transparency, purpose limitation, data minimization, accuracy, storage limitation, integrity and confidentiality, accountability. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Information Security Seven Principles Of GDPR Law Ppt PowerPoint Presentation File Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
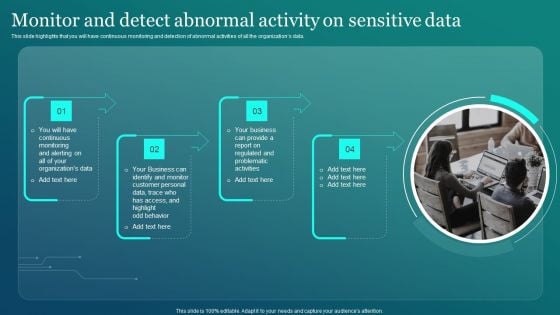
Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Are you searching for a Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF from Slidegeeks today.
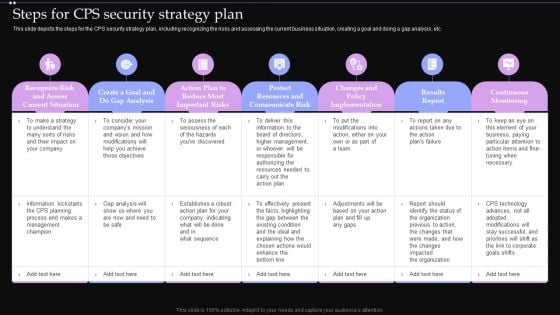
Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Do you know about Slidesgeeks Steps For CPS Security Strategy Plan Ppt PowerPoint Presentation File Portfolio PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Retrieve professionally designed Techniques To Monitor Transactions Major Roles And Responsibilities Of Financial Security Team Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
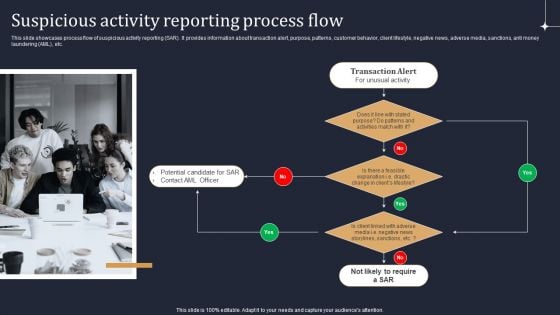
KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF
This slide showcases process flow of suspicious activity reporting SAR. It provides information about transaction alert, purpose, patterns, customer behavior, client lifestyle, negative news, adverse media, sanctions, anti money laundering AML, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF
This slide showcases blockchain technology for anti money laundering AML and transaction monitoring. It provides information about transaction subsets, input data, monitoring, analysis, alerts, record, red flags, Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF.

KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF
This slide showcases cryptocurrency transaction monitoring with alert status. It provides information about address, risk level, currencies, bitcoin, Ethereum, date added, deposits, case status, alerts, deposits, darknet, etc. This KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The KYC Transaction Monitoring System Business Security Cryptocurrency Transaction Monitoring Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
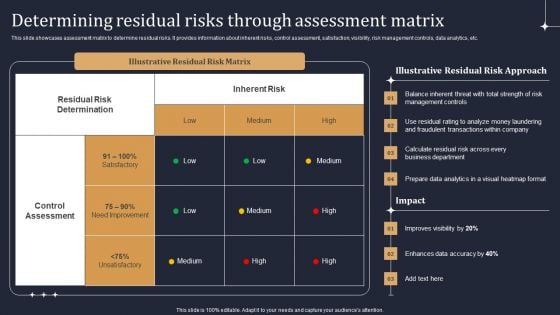
KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Explore a selection of the finest KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our KYC Transaction Monitoring System Business Security Determining Residual Risks Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.


 Continue with Email
Continue with Email

 Home
Home


































