Network
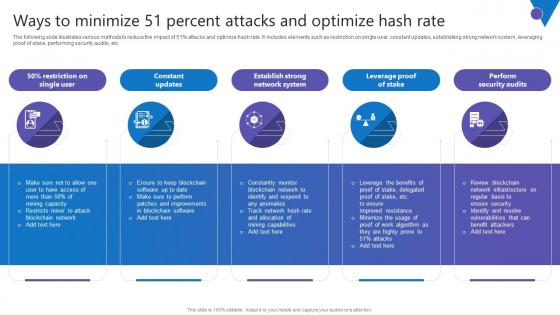
Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf
The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc. Present like a pro with Ways To Minimize 51 Percent Comprehensive Guide To Blockchain Digital Security Ideas Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide illustrates various methods to reduce the impact of 51percent attacks and optimize hash rate. It includes elements such as restriction on single user, constant updates, establishing strong network system, leveraging proof of stake, performing security audits, etc.
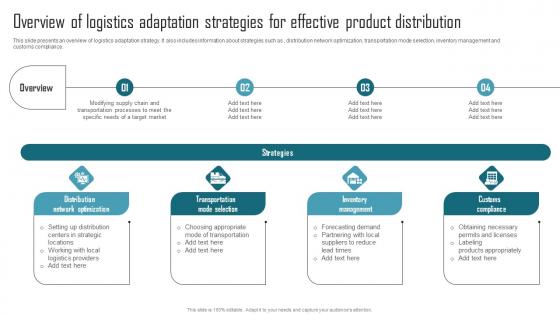
Effective Product Adaptation Overview Of Logistics Adaptation Strategies For Effective Product Diagrams PDF
This slide presents an overview of logistics adaptation strategy. It also includes information about strategies such as , distribution network optimization, transportation mode selection, inventory management and customs compliance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Effective Product Adaptation Overview Of Logistics Adaptation Strategies For Effective Product Diagrams PDF can be your best option for delivering a presentation. Represent everything in detail using Effective Product Adaptation Overview Of Logistics Adaptation Strategies For Effective Product Diagrams PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide presents an overview of logistics adaptation strategy. It also includes information about strategies such as , distribution network optimization, transportation mode selection, inventory management and customs compliance.

Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf
This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Implementation Budget Data Breach Prevention Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the estimated and actual cost of implementing data breach prevention measures in an organization. The cost categories are security software and tools, employee training, security consultants, data encryption, and network security.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.
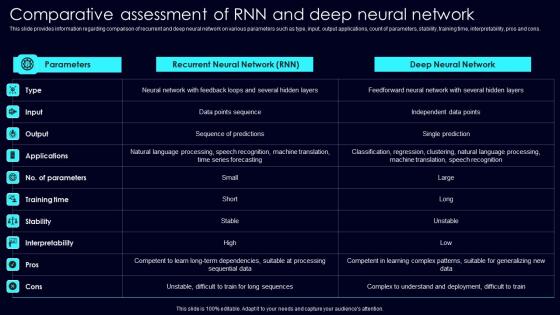
Comparative Assessment Exploring Rise Of Generative AI In Artificial Intelligence Topics Pdf
This slide provides information regarding comparison of recurrent and deep neural network on various parameters such as type, input, output applications, count of parameters, stability, training time, interpretability, pros and cons. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Assessment Exploring Rise Of Generative AI In Artificial Intelligence Topics Pdf can be your best option for delivering a presentation. Represent everything in detail using Comparative Assessment Exploring Rise Of Generative AI In Artificial Intelligence Topics Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide provides information regarding comparison of recurrent and deep neural network on various parameters such as type, input, output applications, count of parameters, stability, training time, interpretability, pros and cons.

IT Asset Management Audit Checklist RFID Solutions For Asset Traceability Graphics Pdf
This slide covers audit checklist of IT asset to ensure effective workflow processes. It involves key activities such as manage registry of IT assets, track IT asset orders, create maintenance schedules and review IT network workflow. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Asset Management Audit Checklist RFID Solutions For Asset Traceability Graphics Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Asset Management Audit Checklist RFID Solutions For Asset Traceability Graphics Pdf This slide covers audit checklist of IT asset to ensure effective workflow processes. It involves key activities such as manage registry of IT assets, track IT asset orders, create maintenance schedules and review IT network workflow.

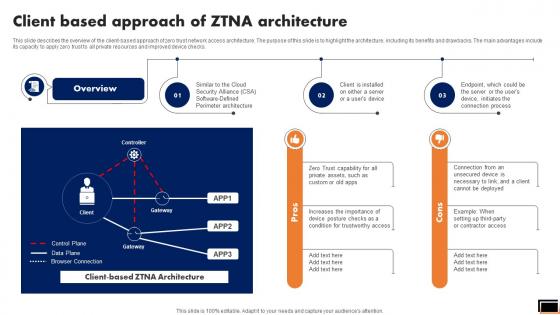
Zero Trust Model Client Based Approach Of ZTNA Architecture
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Model Client Based Approach Of ZTNA Architecture. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Model Client Based Approach Of ZTNA Architecture today and make your presentation stand out from the rest This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.

Zero Trust Model Difference Between ZTNA And Software Defined Perimeter
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Difference Between ZTNA And Software Defined Perimeter and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
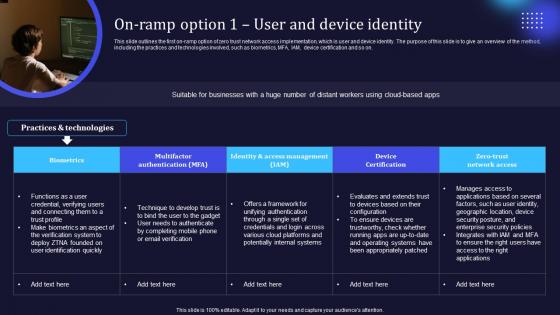
Zero Trust Model On Ramp Option 1 User And Device Identity
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. Retrieve professionally designed Zero Trust Model On Ramp Option 1 User And Device Identity to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
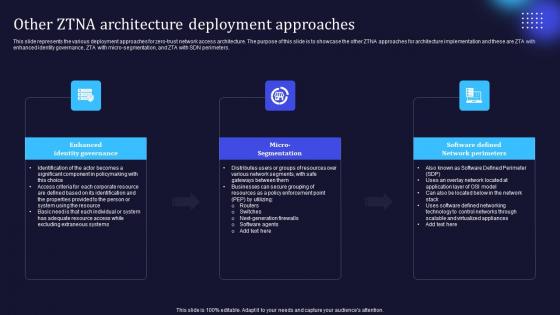
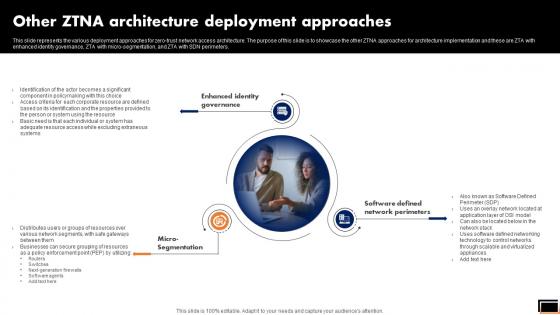
Zero Trust Model Other ZTNA Architecture Deployment Approaches
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Model Other ZTNA Architecture Deployment Approaches to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Model Other ZTNA Architecture Deployment Approaches. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.

Zero Trust Model Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. This Zero Trust Model Overview Of Zero Trust Solution Categories from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.

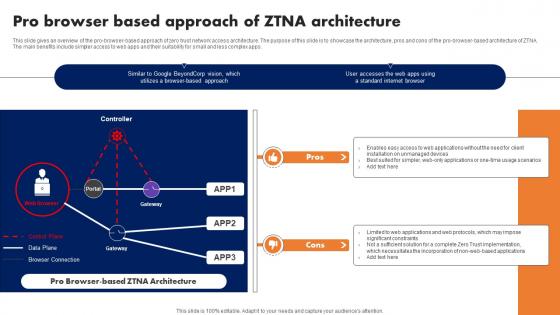
Zero Trust Model Pro Browser Based Approach Of ZTNA Architecture
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Take your projects to the next level with our ultimate collection of Zero Trust Model Pro Browser Based Approach Of ZTNA Architecture. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
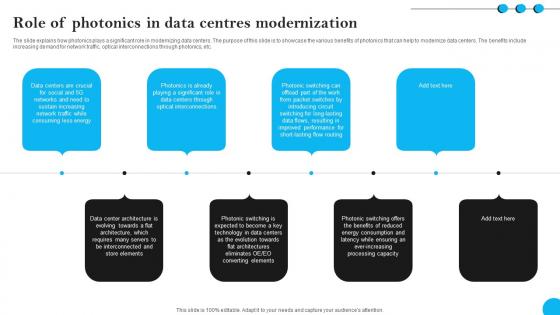
Fibers IT Role Of Photonics In Data Centres Modernization
The slide explains how photonics plays a significant role in modernizing data centers. The purpose of this slide is to showcase the various benefits of photonics that can help to modernize data centers. The benefits include increasing demand for network traffic, optical interconnections through photonics, etc. Find highly impressive Fibers IT Role Of Photonics In Data Centres Modernization on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Fibers IT Role Of Photonics In Data Centres Modernization for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The slide explains how photonics plays a significant role in modernizing data centers. The purpose of this slide is to showcase the various benefits of photonics that can help to modernize data centers. The benefits include increasing demand for network traffic, optical interconnections through photonics, etc.
Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks.
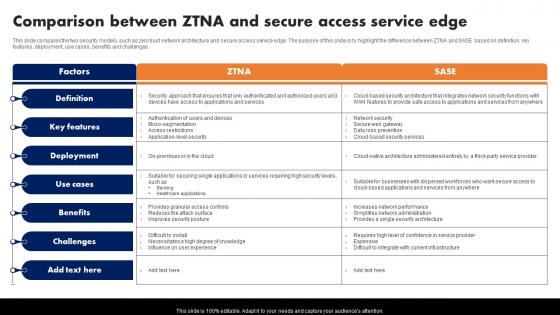
Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between Ztna And Secure Access Service Edge Software Defined Perimeter SDP With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges.
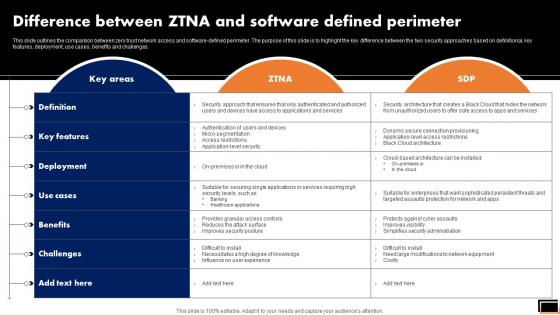
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
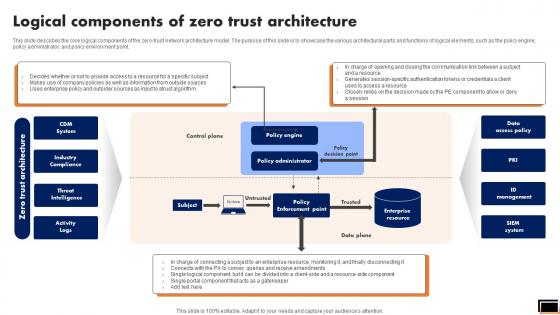
Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point.
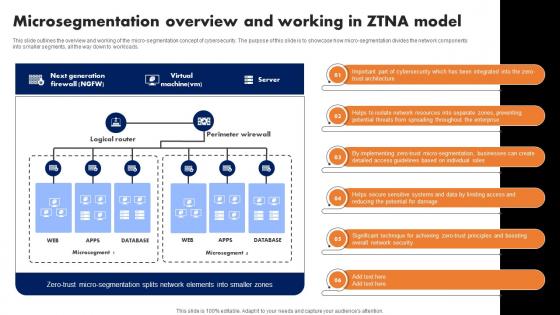
Microsegmentation Overview And Working In Ztna Model Software Defined Perimeter SDP
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In Ztna Model Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In Ztna Model Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
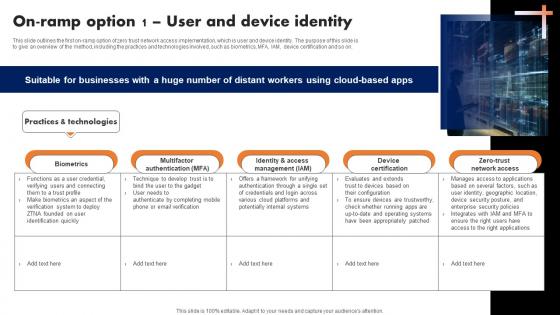
On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP
This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download On Ramp Option 1 User And Device Identity Software Defined Perimeter SDP from Slidegeeks and deliver a wonderful presentation. This slide outlines the first on-ramp option of zero trust network access implementation, which is user and device identity. The purpose of this slide is to give an overview of the method, including the practices and technologies involved, such as biometrics, MFA, IAM, device certification and so on.
Other Ztna Architecture Deployment Approaches Software Defined Perimeter SDP
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other Ztna Architecture Deployment Approaches Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters.

Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits.
Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of Ztna Architecture Software Defined Perimeter SDP that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps.
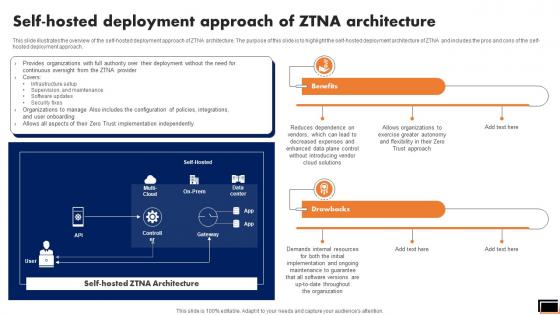
Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Do you know about Slidesgeeks Self-Hosted Deployment Approach Of Ztna Architecture Software Defined Perimeter SDP These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach.

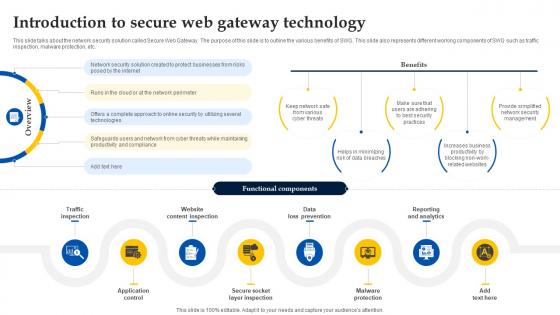
Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.

Prominent Users Of Secure Web Gateway Web Threat Protection System
This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc. Retrieve professionally designed Prominent Users Of Secure Web Gateway Web Threat Protection System to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.

Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V
This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc. Get a simple yet stunning designed Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Manual For Blockchain Best Practices For Effectively Using BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers tips to develop private network based blockchain platform. It includes practices such as identifying the participants or stakeholders ensuring their commitments, selecting appropriate consensus mechanism, regularly updating and monitoring security measures, conducting thorough testing and quality assurance, implementing effective communication, etc.
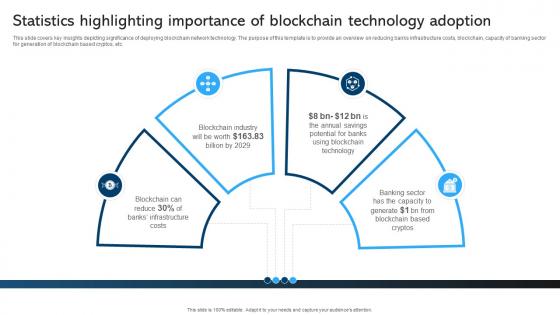
Comprehensive Manual For Blockchain Statistics Highlighting Importance BCT SS V
This slide covers key insights depicting significance of deploying blockchain network technology. The purpose of this template is to provide an overview on reducing banks infrastructure costs, blockchain, capacity of banking sector for generation of blockchain based cryptos, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Comprehensive Manual For Blockchain Statistics Highlighting Importance BCT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Comprehensive Manual For Blockchain Statistics Highlighting Importance BCT SS V. This slide covers key insights depicting significance of deploying blockchain network technology. The purpose of this template is to provide an overview on reducing banks infrastructure costs, blockchain, capacity of banking sector for generation of blockchain based cryptos, etc.

Comprehensive Manual For Blockchain Use Cases Of Consortium Blockchain BCT SS V
This slide covers applications of consortium blockchain network platform. It includes use cases such as healthcare, finance, identity verification, real estate for securely storing data, facilitating trade financing, enabling identity verification, simplifying real estate transactions, etc. Do you know about Slidesgeeks Comprehensive Manual For Blockchain Use Cases Of Consortium Blockchain BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide covers applications of consortium blockchain network platform. It includes use cases such as healthcare, finance, identity verification, real estate for securely storing data, facilitating trade financing, enabling identity verification, simplifying real estate transactions, etc.

Generative AI Tool Competent In Solving Anything ChatGPT How Generative AI Tools Work AI SS V
This slide provides information regarding the insights about ChatGPT platform , an AI-based language model that is developed on deep learning methodology which uses an artificial neural network for generating humanoid text. It includes details related to its owner, userbase, cloud infrastructure, purpose of ChatGPT, etc. Retrieve professionally designed Generative AI Tool Competent In Solving Anything ChatGPT How Generative AI Tools Work AI SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide provides information regarding the insights about ChatGPT platform , an AI-based language model that is developed on deep learning methodology which uses an artificial neural network for generating humanoid text. It includes details related to its owner, userbase, cloud infrastructure, purpose of ChatGPT, etc.

Google Ads Categories Identifying And Listing Of Targeting On The Google Search MKT SS V
This slide covers an overview of key criterias for targeting on search and display network for Google Ads. The purpose of this template is to provide guidelines on using keywords for Google ads, ad schedules and different devices targeted. It includes use of words or phrases, keyword match type, negative keywords, selecting hours to show ads, adjusting bids by hours, etc. Find a pre-designed and impeccable Google Ads Categories Identifying And Listing Of Targeting On The Google Search MKT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide covers an overview of key criterias for targeting on search and display network for Google Ads. The purpose of this template is to provide guidelines on using keywords for Google ads, ad schedules and different devices targeted. It includes use of words or phrases, keyword match type, negative keywords, selecting hours to show ads, adjusting bids by hours, etc.

Google Ads Categories Introduction To Google App Ads Campaign Strategy MKT SS V
This slide covers brief summary of app Ads on Google network used to increase application installations . The purpose of this template is to provide an overview on benefits of using Google apps Ads along with different app ad design elements . It includes benefits such as improving app rankings, acquiring new users, offering cost effective method and providing performance metrics, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Google Ads Categories Introduction To Google App Ads Campaign Strategy MKT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide covers brief summary of app Ads on Google network used to increase application installations . The purpose of this template is to provide an overview on benefits of using Google apps Ads along with different app ad design elements . It includes benefits such as improving app rankings, acquiring new users, offering cost effective method and providing performance metrics, etc.
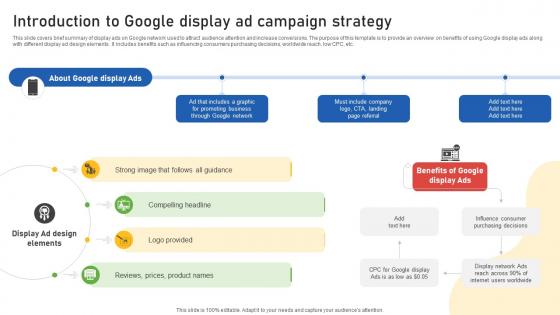
Google Ads Categories Introduction To Google Display Ad Campaign Strategy MKT SS V
This slide covers brief summary of display ads on Google network used to attract audience attention and increase conversions. The purpose of this template is to provide an overview on benefits of using Google display ads along with different display ad design elements . It includes benefits such as influencing consumers purchasing decisions, worldwide reach, low CPC, etc. Present like a pro with Google Ads Categories Introduction To Google Display Ad Campaign Strategy MKT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide covers brief summary of display ads on Google network used to attract audience attention and increase conversions. The purpose of this template is to provide an overview on benefits of using Google display ads along with different display ad design elements . It includes benefits such as influencing consumers purchasing decisions, worldwide reach, low CPC, etc.
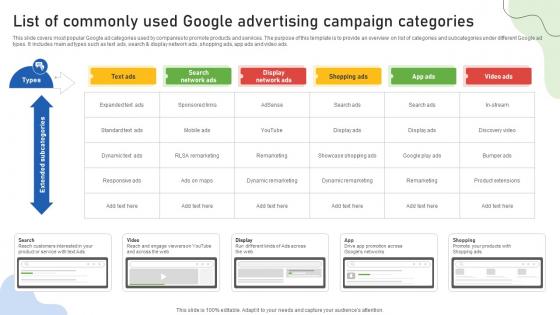
Google Ads Categories List Of Commonly Used Google Advertising Campaign Categories MKT SS V
This slide covers most popular Google ad categories used by companies to promote products and services. The purpose of this template is to provide an overview on list of categories and subcategories under different Google ad types. It includes main ad types such as text ads, search and display network ads, shopping ads, app ads and video ads. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Google Ads Categories List Of Commonly Used Google Advertising Campaign Categories MKT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Google Ads Categories List Of Commonly Used Google Advertising Campaign Categories MKT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide covers most popular Google ad categories used by companies to promote products and services. The purpose of this template is to provide an overview on list of categories and subcategories under different Google ad types. It includes main ad types such as text ads, search and display network ads, shopping ads, app ads and video ads.

Select The Best University Marketing Strategy Key Step To Implementation University Strategy SS V
The following slide showcases comparative analysis of various university marketing techniques to select the best alternative. It includes elements such as goals, reach, targeting, average per month costs, user engagement, retention rate, alumni network etc.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Select The Best University Marketing Strategy Key Step To Implementation University Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Select The Best University Marketing Strategy Key Step To Implementation University Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide showcases comparative analysis of various university marketing techniques to select the best alternative. It includes elements such as goals, reach, targeting, average per month costs, user engagement, retention rate, alumni network etc.
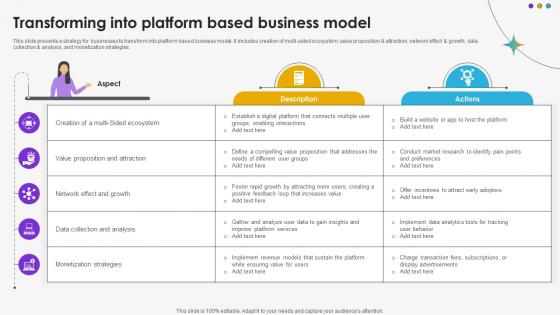
Transforming Into Platform Based Business Model DT SS V
This slide presents a strategy for businesses to transform into platform based business model. It includes creation of multi-sided ecosystem, value proposition and attraction, network effect and growth, data collection and analysis, and monetization strategies.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Transforming Into Platform Based Business Model DT SS V can be your best option for delivering a presentation. Represent everything in detail using Transforming Into Platform Based Business Model DT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide presents a strategy for businesses to transform into platform based business model. It includes creation of multi-sided ecosystem, value proposition and attraction, network effect and growth, data collection and analysis, and monetization strategies.

Select The Best University Marketing Strategy Running Marketing Campaigns Strategy SS V
The following slide showcases comparative analysis of various university marketing techniques to select the best alternative. It includes elements such as goals, reach, targeting, average per month costs, user engagement, retention rate, alumni network etc. Presenting this PowerPoint presentation, titled Select The Best University Marketing Strategy Running Marketing Campaigns Strategy SS V, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Select The Best University Marketing Strategy Running Marketing Campaigns Strategy SS V. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Select The Best University Marketing Strategy Running Marketing Campaigns Strategy SS V that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The following slide showcases comparative analysis of various university marketing techniques to select the best alternative. It includes elements such as goals, reach, targeting, average per month costs, user engagement, retention rate, alumni network etc.
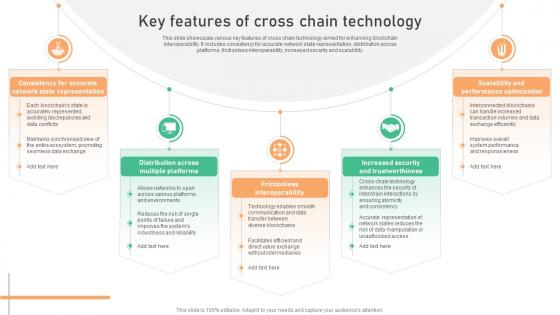
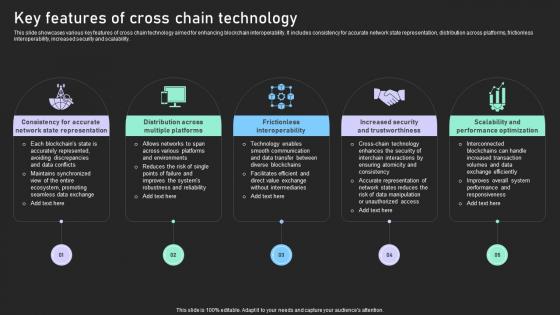
Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Are you searching for a Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V from Slidegeeks today. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Understanding Various Blockchain Key Features Of Cross Chain Technology BCT SS V. This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability.

Guide To Building A Successful Key Challenges Faced By Dealers Without An Efficient Strategy SS V
This slide covers top barriers faced by dealers network in absence of dealer management system. The purpose of this template is to provide an overview of top challenges comprising of inefficient process, lack of visibility, non existent reporting for vehicle dealers. Welcome to our selection of the Guide To Building A Successful Key Challenges Faced By Dealers Without An Efficient Strategy SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers top barriers faced by dealers network in absence of dealer management system. The purpose of this template is to provide an overview of top challenges comprising of inefficient process, lack of visibility, non existent reporting for vehicle dealers.

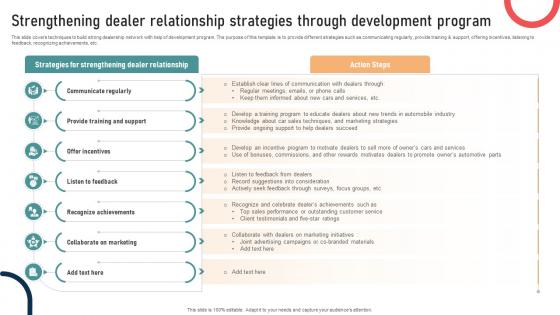
Guide To Building A Successful Strengthening Dealer Relationship Strategies Through Strategy SS V
This slide covers techniques to build strong dealership network with help of development program. The purpose of this template is to provide different strategies such as communicating regularly, provide training and support, offering incentives, listening to feedback, recognizing achievements, etc. Get a simple yet stunning designed Guide To Building A Successful Strengthening Dealer Relationship Strategies Through Strategy SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Guide To Building A Successful Strengthening Dealer Relationship Strategies Through Strategy SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers techniques to build strong dealership network with help of development program. The purpose of this template is to provide different strategies such as communicating regularly, provide training and support, offering incentives, listening to feedback, recognizing achievements, etc.

Ultimate Guide To Developing Key Challenges Faced By Dealers Without An Efficient Strategy SS V
This slide covers top barriers faced by dealers network in absence of dealer management system. The purpose of this template is to provide an overview of top challenges comprising of inefficient process, lack of visibility, non existent reporting for vehicle dealers. Welcome to our selection of the Ultimate Guide To Developing Key Challenges Faced By Dealers Without An Efficient Strategy SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers top barriers faced by dealers network in absence of dealer management system. The purpose of this template is to provide an overview of top challenges comprising of inefficient process, lack of visibility, non existent reporting for vehicle dealers.
Ultimate Guide To Developing Strengthening Dealer Relationship Strategies Through Strategy SS V
This slide covers techniques to build strong dealership network with help of development program. The purpose of this template is to provide different strategies such as communicating regularly, provide training and support, offering incentives, listening to feedback, recognizing achievements, etc. Get a simple yet stunning designed Ultimate Guide To Developing Strengthening Dealer Relationship Strategies Through Strategy SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Ultimate Guide To Developing Strengthening Dealer Relationship Strategies Through Strategy SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide covers techniques to build strong dealership network with help of development program. The purpose of this template is to provide different strategies such as communicating regularly, provide training and support, offering incentives, listening to feedback, recognizing achievements, etc.

Unlocking The Potential Of Testing Process Of Blockchain Based Gaming BCT SS V
This slide highlights testing process of Blockchain games ensuring the game runs smoothly and provides the players with an excellent gaming experience. It includes testing for bugs, optimizing game performance, network deployment, smart contract auditing and gas optimization. Retrieve professionally designed Unlocking The Potential Of Testing Process Of Blockchain Based Gaming BCT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide highlights testing process of Blockchain games ensuring the game runs smoothly and provides the players with an excellent gaming experience. It includes testing for bugs, optimizing game performance, network deployment, smart contract auditing and gas optimization.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.

Factors Influencing Bitcoin Transactions Everything About Bitcoin PPT Template Fin SS V
This slide shows information about various factors which can impact the confirmation timings of a Bitcoin transaction. These factors are transaction fees, network activity, hash rate and spam attacks. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Factors Influencing Bitcoin Transactions Everything About Bitcoin PPT Template Fin SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Factors Influencing Bitcoin Transactions Everything About Bitcoin PPT Template Fin SS V This slide shows information about various factors which can impact the confirmation timings of a Bitcoin transaction. These factors are transaction fees, network activity, hash rate and spam attacks.
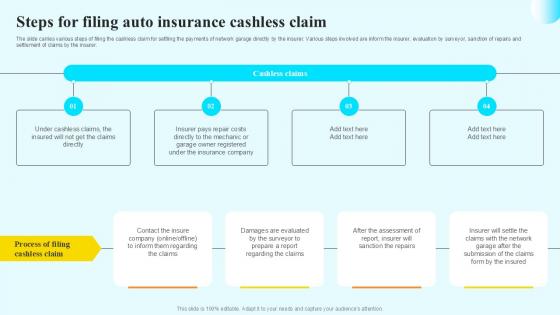
Steps For Filing Auto Insurance Steps By Step Guide For Claiming Car PPT PowerPoint
The slide carries various steps of filing the cashless claim for settling the payments of network garage directly by the insurer. Various steps involved are inform the insurer, evaluation by surveyor, sanction of repairs and settlement of claims by the insurer. Explore a selection of the finest Steps For Filing Auto Insurance Steps By Step Guide For Claiming Car PPT PowerPoint here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Steps For Filing Auto Insurance Steps By Step Guide For Claiming Car PPT PowerPoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The slide carries various steps of filing the cashless claim for settling the payments of network garage directly by the insurer. Various steps involved are inform the insurer, evaluation by surveyor, sanction of repairs and settlement of claims by the insurer.

Non Ethereum Standards Of NFT Ppt Ideas PDF
This slide shows the NFT standards for tokens using non Ethereum networks the high gas prices of networks pushed developers to alternate public DLTs. This is a non ethereum standards of nft ppt ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, prices, performance, developers, potentially. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
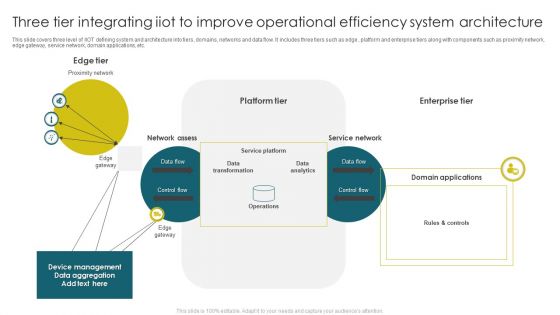
Three Tier Integrating Iiot To Improve Operational Efficiency System Architecture Microsoft PDF
This slide covers three level of IIOT defining system and architecture into tiers, domains, networks and data flow. It includes three tiers such as edge , platform and enterprise tiers along with components such as proximity network, edge gateway, service network, domain applications, etc. Showcasing this set of slides titled Three Tier Integrating Iiot To Improve Operational Efficiency System Architecture Microsoft PDF. The topics addressed in these templates are Data Transformation, Service Platform, Data Analytics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Human Project Resource Management Phases Techniques Summary Pdf
This following slide illustrates the tools and techniques essential for boosting efficiency and reducing HRM costs. The tools used are organisational charts, responsibility matrix, text, networking, SWOT Showcasing this set of slides titled Human Project Resource Management Phases Techniques Summary Pdf. The topics addressed in these templates are Organisational Charts, Responsibility Matrix, Networking . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This following slide illustrates the tools and techniques essential for boosting efficiency and reducing HRM costs. The tools used are organisational charts, responsibility matrix, text, networking, SWOT

Key Considerations To Raise Series A Funding Structure Pdf
This slide highlight key focus areas to be considered before raising funds from series A funding round. It provides information regarding business valuation, paperwork, develop networks, create pitch decks and identify investors . Pitch your topic with ease and precision using this Key Considerations To Raise Series A Funding Structure Pdf. This layout presents information on Business Valuation, Identify Investor, Develop Networks to create a unique layout. This slide highlight key focus areas to be considered before raising funds from series A funding round. It provides information regarding business valuation, paperwork, develop networks, create pitch decks and identify investors .
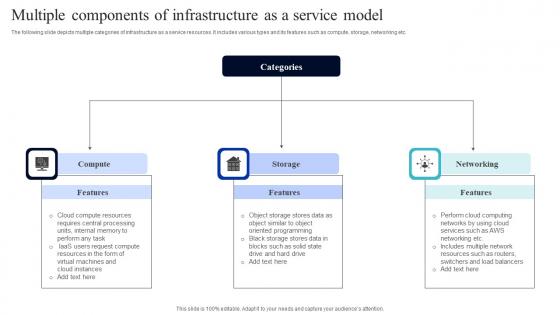
Multiple Components Of Infrastructure As A Service Model Structure Pdf
The following slide depicts multiple categories of infrastructure as a service resources. It includes various types and its features such as compute, storage, networking etc. Pitch your topic with ease and precision using this Multiple Components Of Infrastructure As A Service Model Structure Pdf. This layout presents information on Compute, Storage, Networking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide depicts multiple categories of infrastructure as a service resources. It includes various types and its features such as compute, storage, networking etc.
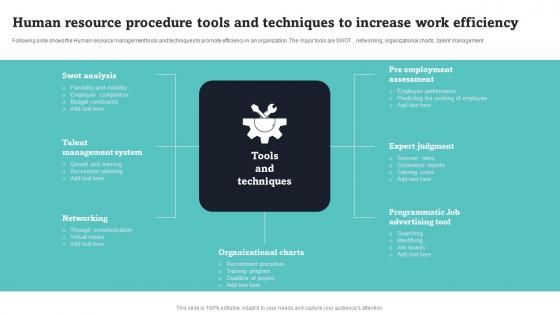
Human Resource Procedure Tools And Techniques To Increase Work Efficiency Introduction Pdf
Following slide shows the Human resource management tools and techniques to promote efficiency in an organization. The major tools are SWOT, networking, organizational charts, talent management. Showcasing this set of slides titled Human Resource Procedure Tools And Techniques To Increase Work Efficiency Introduction Pdf. The topics addressed in these templates are Talent Management System, Networking Organizational Charts. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Following slide shows the Human resource management tools and techniques to promote efficiency in an organization. The major tools are SWOT, networking, organizational charts, talent management.
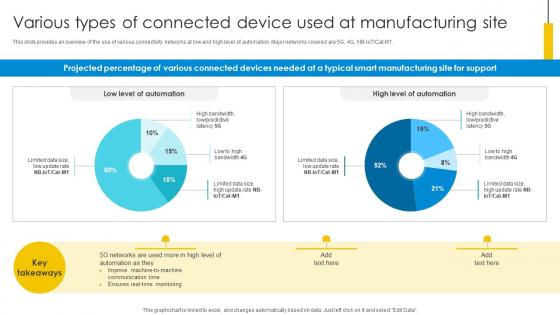
Various Types Of Connected Device Used At Manufacturing Site Optimizing Inventory Management IoT SS V
This slide provides an overview of the use of various connectivity networks at low and high level of automation. Major networks covered are 5G, 4G, NB-IoT or Cat-M1. Create an editable Various Types Of Connected Device Used At Manufacturing Site Optimizing Inventory Management IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Various Types Of Connected Device Used At Manufacturing Site Optimizing Inventory Management IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the use of various connectivity networks at low and high level of automation. Major networks covered are 5G, 4G, NB-IoT or Cat-M1.

Accessing Metaverse Through Technologies Internet Of Things Iot Ppt Portfolio Infographics PDF
This slide provides information regarding development and growth of metaverse through emerging technologies such as internet of things IoT. It is a robust network of interconnected physical devices to leverage link among real world and virtual space. Create an editable Accessing Metaverse Through Technologies Internet Of Things Iot Ppt Portfolio Infographics PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Accessing Metaverse Through Technologies Internet Of Things Iot Ppt Portfolio Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
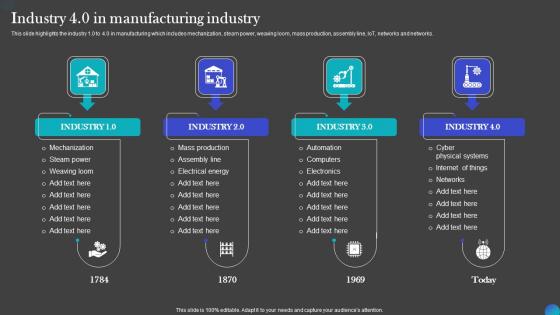
Industry 40 In Manufacturing Industry IOT Adoption Manufacturing Formats PDF
This slide highlights the industry 1.0 to 4.0 in manufacturing which includes mechanization, steam power, weaving loom, mass production, assembly line, IoT, networks and networks. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Industry 40 In Manufacturing Industry IOT Adoption Manufacturing Formats PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide highlights the industry 1.0 to 4.0 in manufacturing which includes mechanization, steam power, weaving loom, mass production, assembly line, IoT, networks and networks.

Sample Of Three Types Of Internet Of Things Diagram Ppt Slides
This is a sample of three types of internet of things diagram ppt slides. This is a three stage process. The stages in this process are things with networked sensors, analytic engines, data storage.

Iot Applications For Manufacturing Industry Exponential Value Creation Opportunity Using Iot Background PDF
This slide highlights the Value creation opportunity by implementing a complete smart factory or network of smart factories across the enterprise. Explore a selection of the finest ns For Manufacturing Industry Exponential Value Creation Opportunity Using Iot Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our ns For Manufacturing Industry Exponential Value Creation Opportunity Using Iot Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
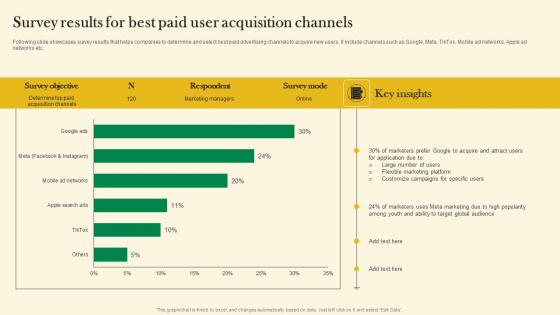
Survey Results For Best Paid User Acquisition Channels Online Customer Acquisition Rules Pdf
Following slide showcases survey results that helps companies to determine and select best paid advertising channels to acquire new users. It include channels such as Google, Meta, TikTok, Mobile ad networks, Apple ad networks etc. This Survey Results For Best Paid User Acquisition Channels Online Customer Acquisition Rules Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. Following slide showcases survey results that helps companies to determine and select best paid advertising channels to acquire new users. It include channels such as Google, Meta, TikTok, Mobile ad networks, Apple ad networks etc.
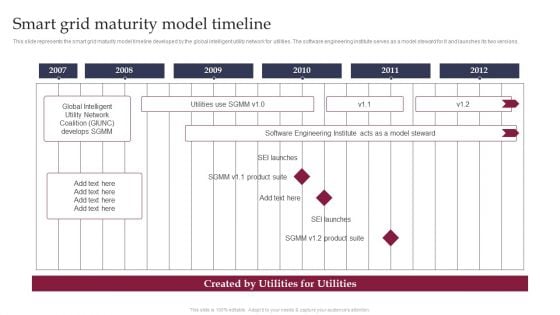
Smart Grid Technology Smart Grid Maturity Model Timeline Download PDF


 Continue with Email
Continue with Email

 Home
Home


































