Outline
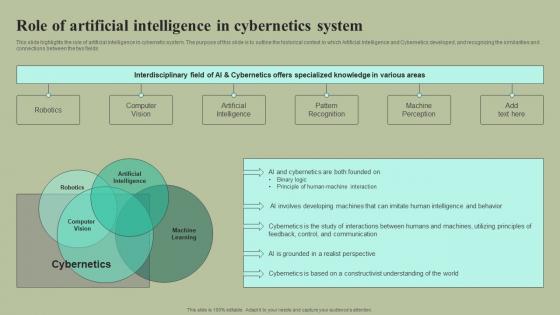
Role Of Artificial Intelligence In Cybernetics System Cybernetic Integration Professional Pdf
This slide highlights the role of artificial intelligence in cybernetic system. The purpose of this slide is to outline the historical context in which Artificial Intelligence and Cybernetics developed, and recognizing the similarities and connections between the two fields. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Role Of Artificial Intelligence In Cybernetics System Cybernetic Integration Professional Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide highlights the role of artificial intelligence in cybernetic system. The purpose of this slide is to outline the historical context in which Artificial Intelligence and Cybernetics developed, and recognizing the similarities and connections between the two fields.
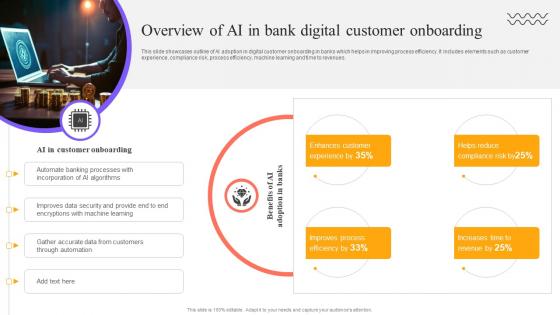
Digital Approach To Client Overview Of AI In Bank Digital Customer Onboarding
This slide showcases outline of AI adoption in digital customer onboarding in banks which helps in improving process efficiency. It includes elements such as customer experience, compliance risk, process efficiency, machine learning and time to revenues. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Digital Approach To Client Overview Of AI In Bank Digital Customer Onboarding to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases outline of AI adoption in digital customer onboarding in banks which helps in improving process efficiency. It includes elements such as customer experience, compliance risk, process efficiency, machine learning and time to revenues.

Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain
This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.Get a simple yet stunning designed Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.

Overview Of Business Disruption Caused Man In The Middle Phishing IT
This slide discusses the impact of phishing attacks on businesses. The purpose of this slide is to outline the amount of money lost by well-reputed companies due to phishing scams. The companies included are Facebook and Google, Crelan Bank in Belgium, etc. Create an editable Overview Of Business Disruption Caused Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Overview Of Business Disruption Caused Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide discusses the impact of phishing attacks on businesses. The purpose of this slide is to outline the amount of money lost by well-reputed companies due to phishing scams. The companies included are Facebook and Google, Crelan Bank in Belgium, etc.

About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. Create an editable About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.
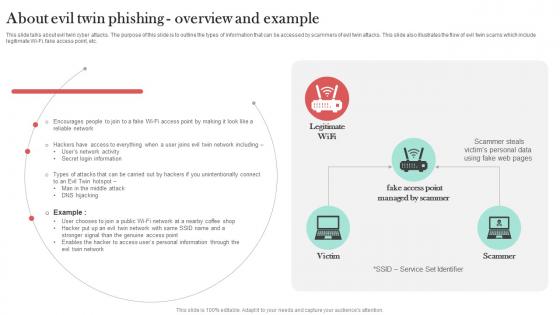
About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc.

Local Marketing Overview Introduction To Niche Marketing Audience Segmentation Background Pdf
The following slide showcases brief outline of local marketing and some promotional tips to facilitate brand to connect with local communities. It includes elements such as offering printed materials, sponsoring sports events, organizing contests, suggestion box etc. Retrieve professionally designed Local Marketing Overview Introduction To Niche Marketing Audience Segmentation Background Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide showcases brief outline of local marketing and some promotional tips to facilitate brand to connect with local communities. It includes elements such as offering printed materials, sponsoring sports events, organizing contests, suggestion box etc.
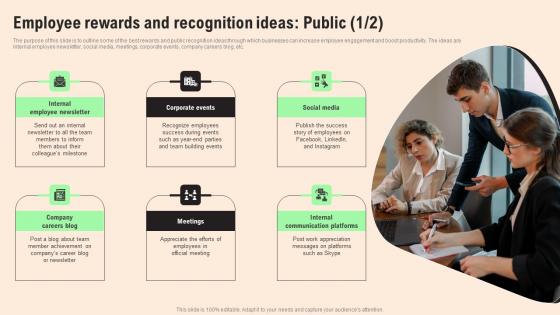
Employee Rewards Recognition Public HR Retention Techniques For Business Owners Inspiration Pdf
The purpose of this slide is to outline some of the best rewards and public recognition ideas through which businesses can increase employee engagement and boost productivity. The ideas are internal employee newsletter, social media, meetings, corporate events, company careers blog, etc. Are you searching for a Employee Rewards Recognition Public HR Retention Techniques For Business Owners Inspiration Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Employee Rewards Recognition Public HR Retention Techniques For Business Owners Inspiration Pdf from Slidegeeks today. The purpose of this slide is to outline some of the best rewards and public recognition ideas through which businesses can increase employee engagement and boost productivity. The ideas are internal employee newsletter, social media, meetings, corporate events, company careers blog, etc.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
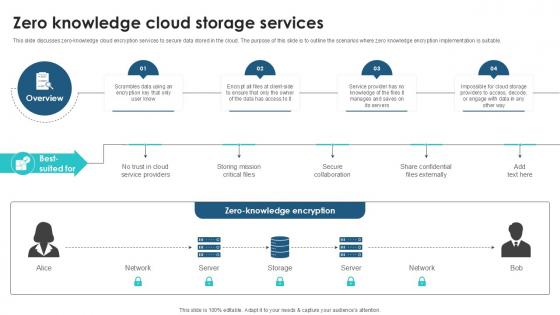
Zero Knowledge Cloud Storage Client Side Encryption PPT Template
This slide discusses zero-knowledge cloud encryption services to secure data stored in the cloud. The purpose of this slide is to outline the scenarios where zero knowledge encryption implementation is suitable. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Knowledge Cloud Storage Client Side Encryption PPT Template to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Knowledge Cloud Storage Client Side Encryption PPT Template. This slide discusses zero-knowledge cloud encryption services to secure data stored in the cloud. The purpose of this slide is to outline the scenarios where zero knowledge encryption implementation is suitable.
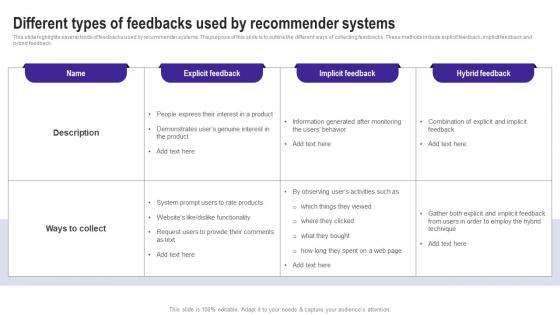
Different Types Of Feedbacks Used By Recommender Use Cases Of Filtering Methods Rules Pdf
This slide highlights several kinds of feedbacks used by recommender systems. The purpose of this slide is to outline the different ways of collecting feedbacks. These methods include explicit feedback, implicit feedback and hybrid feedback. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Different Types Of Feedbacks Used By Recommender Use Cases Of Filtering Methods Rules Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide highlights several kinds of feedbacks used by recommender systems. The purpose of this slide is to outline the different ways of collecting feedbacks. These methods include explicit feedback, implicit feedback and hybrid feedback.

Key Future Trends Shaping The IAC Tools For Performance Analysis PPT Slide
This slide showcases the future trends of infrastructure as code. The purpose of this slide is to outline the future trends such as cross-cloud and hybrid portability, gitops adoptions, empowering developers, integration with CD pipeline, etc. Do you know about Slidesgeeks Key Future Trends Shaping The IAC Tools For Performance Analysis PPT Slide These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide showcases the future trends of infrastructure as code. The purpose of this slide is to outline the future trends such as cross-cloud and hybrid portability, gitops adoptions, empowering developers, integration with CD pipeline, etc.

Recommendation Techniques Approaches To Build Good Recommendation Engine Elements PDF
This slide illustrates the methods to build an effective recommender system. The purpose of this slide is to outline various ways by which company can deploy a good recommender in their business. The key points include AI or ML, business rules, trends and optimization. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Recommendation Techniques Approaches To Build Good Recommendation Engine Elements PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Recommendation Techniques Approaches To Build Good Recommendation Engine Elements PDF today and make your presentation stand out from the rest This slide illustrates the methods to build an effective recommender system. The purpose of this slide is to outline various ways by which company can deploy a good recommender in their business. The key points include AI or ML, business rules, trends and optimization.

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc.

Implementing SEO Basics To Rank Website Higher In Effective General Insurance Marketing Portrait Pdf
This slide presents an outline of a strategic SEO plan to optimize websites to rank better on search engines. It includes information about SEO basics such as keyword research, content creation, on-page optimization, mobile responsiveness, site speed, and link building. Welcome to our selection of the Implementing SEO Basics To Rank Website Higher In Effective General Insurance Marketing Portrait Pdf . These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide presents an outline of a strategic SEO plan to optimize websites to rank better on search engines. It includes information about SEO basics such as keyword research, content creation, on-page optimization, mobile responsiveness, site speed, and link building.

Creating Guerilla Marketing Digital Marketing Strategies Improve Enterprise Sales Designs Pdf
The following slide showcases outline of guerilla marketing campaign which can assist firms in promoting the brand in unconventional manner and increase revenue. The campaign covers information about objectives, time, target audience segmentation, expected cost, and major strategies. If you are looking for a format to display your unique thoughts, then the professionally designed Creating Guerilla Marketing Digital Marketing Strategies Improve Enterprise Sales Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Creating Guerilla Marketing Digital Marketing Strategies Improve Enterprise Sales Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide showcases outline of guerilla marketing campaign which can assist firms in promoting the brand in unconventional manner and increase revenue. The campaign covers information about objectives, time, target audience segmentation, expected cost, and major strategies.

Cylindrical Robot Configuration Benefits Applications Of Industrial Robots Guidelines Pdf
This slide talks about the advantages and structural arrangement of cylindrical robot. The purpose of this slide is to outline the various applications of cylindrical robot. Their key applications are spot welding automation, casting and molding, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Cylindrical Robot Configuration Benefits Applications Of Industrial Robots Guidelines Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cylindrical Robot Configuration Benefits Applications Of Industrial Robots Guidelines Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the advantages and structural arrangement of cylindrical robot. The purpose of this slide is to outline the various applications of cylindrical robot. Their key applications are spot welding automation, casting and molding, etc.

Understanding The Banks Operational Banking Start Up B Plan Go To Market Strategy Guidelines Pdf
The purpose of this slide is to outline the key objectives and goals of an organization and how to reach them by crafting an operational plan. It keeps teams on track while guiding them in making crucial decisions about the banks long term strategy Do you know about Slidesgeeks Understanding The Banks Operational Banking Start Up B Plan Go To Market Strategy Guidelines Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. The purpose of this slide is to outline the key objectives and goals of an organization and how to reach them by crafting an operational plan. It keeps teams on track while guiding them in making crucial decisions about the banks long term strategy
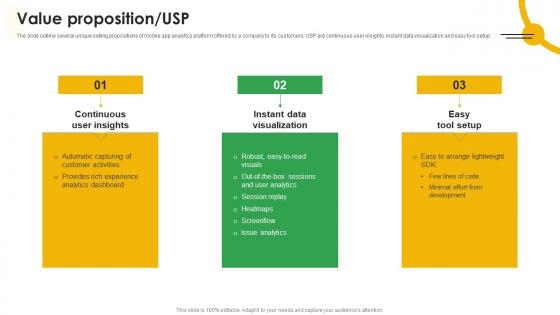
Value Proposition USP Mobile App Analytics Company Fund Raising Pitch Deck Mockup Pdf
The slide outline several unique selling propositions of mobile app analytics platform offered by a company to its customers. USP are continuous user insights, instant data visualization and easy tool setup. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Value Proposition USP Mobile App Analytics Company Fund Raising Pitch Deck Mockup Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The slide outline several unique selling propositions of mobile app analytics platform offered by a company to its customers. USP are continuous user insights, instant data visualization and easy tool setup.

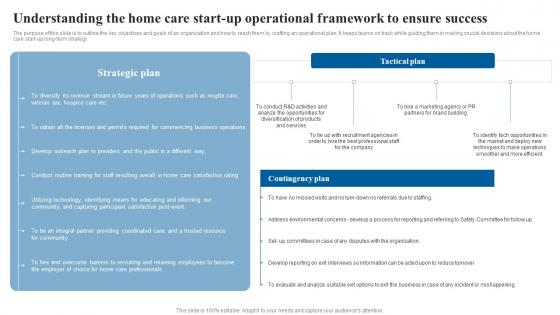
Understanding The Home Care Start Up Operational In Home Care Business Plan Guidelines Pdf
The purpose of this slide is to outline the key objectives and goals of an organization and how to reach them by crafting an operational plan. It keeps teams on track while guiding them in making crucial decisions about the home care start-up long-term strategy. This Understanding The Home Care Start Up Operational In Home Care Business Plan Guidelines Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The purpose of this slide is to outline the key objectives and goals of an organization and how to reach them by crafting an operational plan. It keeps teams on track while guiding them in making crucial decisions about the home care start-up long-term strategy.

Terms And Conditions For Next Generation Intelligent Intrusion Prevention System Ppt Sample
This slide illustrates the outline for the terms and conditions based on which the organization will sign a contract with the agreement party. It covers service And payment, contract cancellation, notice and renewal of the agreement, and liability.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Terms And Conditions For Next Generation Intelligent Intrusion Prevention System Ppt Sample and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide illustrates the outline for the terms and conditions based on which the organization will sign a contract with the agreement party. It covers service and payment, contract cancellation, notice and renewal of the agreement, and liability.
Recommendation Techniques Steps For Building And Deploying Recommender Systems Icons PDF
This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Recommendation Techniques Steps For Building And Deploying Recommender Systems Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Recommendation Techniques Steps For Building And Deploying Recommender Systems Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering.
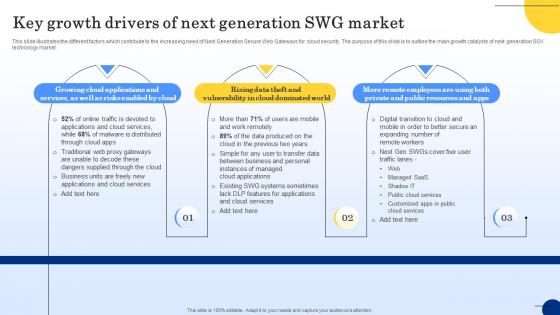
Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Explore a selection of the finest Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.
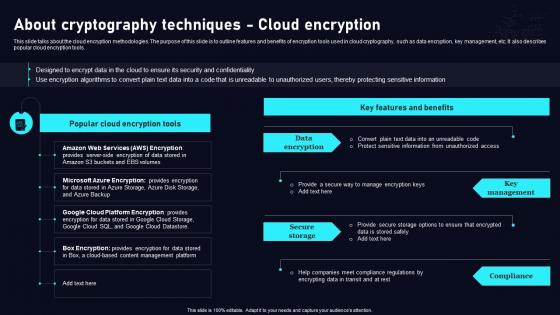
Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf
This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Data Security Using Cryptography About Cryptography Techniques Cloud Download Pdf This slide talks about the cloud encryption methodologies. The purpose of this slide is to outline features and benefits of encryption tools used in cloud cryptography, such as data encryption, key management, etc. It also describes popular cloud encryption tools.
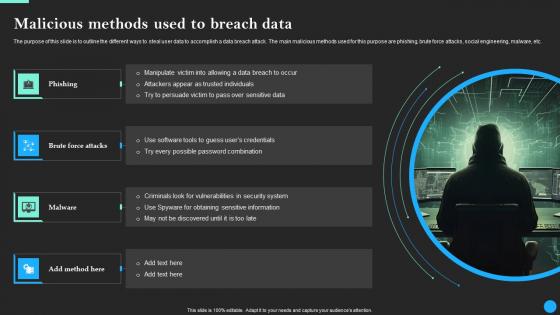
Malicious Methods Used To Breach Data Data Breach Prevention Topics Pdf
The purpose of this slide is to outline the different ways to steal user data to accomplish a data breach attack. The main malicious methods used for this purpose are phishing, brute force attacks, social engineering, malware, etc. This Malicious Methods Used To Breach Data Data Breach Prevention Topics Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. The purpose of this slide is to outline the different ways to steal user data to accomplish a data breach attack. The main malicious methods used for this purpose are phishing, brute force attacks, social engineering, malware, etc.
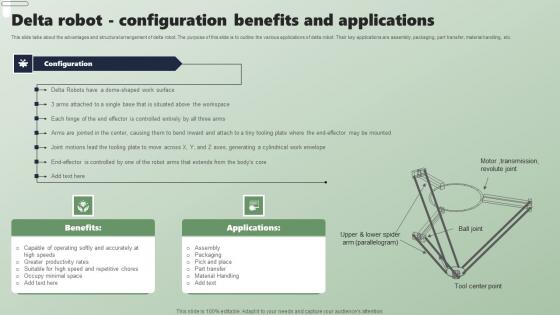
Delta Robot Configuration Benefits Applications Of Industrial Robots Inspiration Pdf
This slide talks about the advantages and structural arrangement of delta robot. The purpose of this slide is to outline the various applications of delta robot. Their key applications are assembly, packaging, part transfer, material handling, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Delta Robot Configuration Benefits Applications Of Industrial Robots Inspiration Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide talks about the advantages and structural arrangement of delta robot. The purpose of this slide is to outline the various applications of delta robot. Their key applications are assembly, packaging, part transfer, material handling, etc.
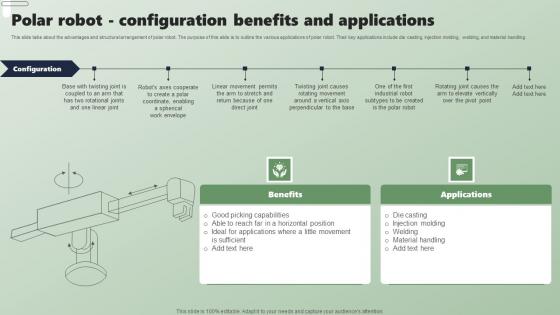
Polar Robot Configuration Benefits And Applications Applications Of Industrial Robots Infographics Pdf
This slide talks about the advantages and structural arrangement of polar robot. The purpose of this slide is to outline the various applications of polar robot. Their key applications include die casting, injection molding, welding, and material handling. Presenting this PowerPoint presentation, titled Polar Robot Configuration Benefits And Applications Applications Of Industrial Robots Infographics Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Polar Robot Configuration Benefits And Applications Applications Of Industrial Robots Infographics Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Polar Robot Configuration Benefits And Applications Applications Of Industrial Robots Infographics Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide talks about the advantages and structural arrangement of polar robot. The purpose of this slide is to outline the various applications of polar robot. Their key applications include die casting, injection molding, welding, and material handling.
Role Of Robotics In Electronics And Semiconductor Applications Of Industrial Robots Inspiration Pdf
This slide demonstrates the purpose of robotics in electronic and semiconductor industry. The purpose of this slide is to outline the use of various robots and their benefits in electronic industry. This slide also shows the future market development due to robots utilization. Create an editable Role Of Robotics In Electronics And Semiconductor Applications Of Industrial Robots Inspiration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Role Of Robotics In Electronics And Semiconductor Applications Of Industrial Robots Inspiration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the purpose of robotics in electronic and semiconductor industry. The purpose of this slide is to outline the use of various robots and their benefits in electronic industry. This slide also shows the future market development due to robots utilization.
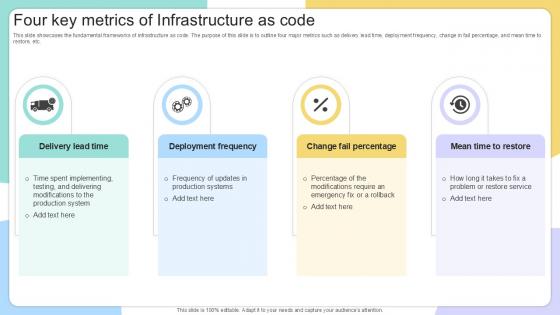
Four Key Metrics Of Infrastructure IAC Tools For Performance Analysis PPT PowerPoint
This slide showcases the fundamental frameworks of infrastructure as code. The purpose of this slide is to outline four major metrics such as delivery lead time, deployment frequency, change in fail percentage, and mean time to restore, etc. Explore a selection of the finest Four Key Metrics Of Infrastructure IAC Tools For Performance Analysis PPT PowerPoint here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Four Key Metrics Of Infrastructure IAC Tools For Performance Analysis PPT PowerPoint to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide showcases the fundamental frameworks of infrastructure as code. The purpose of this slide is to outline four major metrics such as delivery lead time, deployment frequency, change in fail percentage, and mean time to restore, etc.
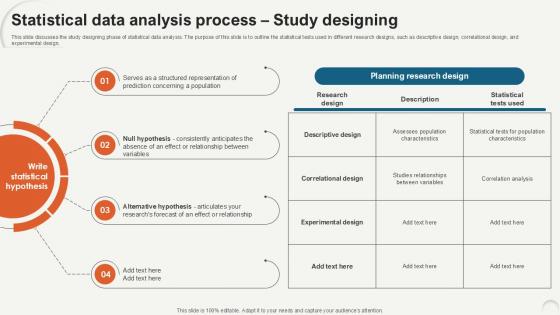
Statistical Data Analysis Process Study Designing Ppt Presentation
This slide discusses the study designing phase of statistical data analysis. The purpose of this slide is to outline the statistical tests used in different research designs, such as descriptive design, correlational design, and experimental design. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Statistical Data Analysis Process Study Designing Ppt Presentation a try. Our experts have put a lot of knowledge and effort into creating this impeccable Statistical Data Analysis Process Study Designing Ppt Presentation. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide discusses the study designing phase of statistical data analysis. The purpose of this slide is to outline the statistical tests used in different research designs, such as descriptive design, correlational design, and experimental design.
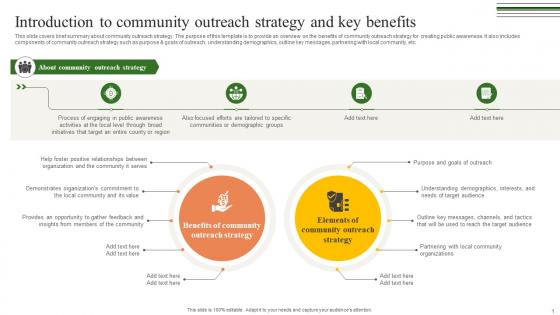
Introduction To Community Outreach Building A Winning Community Outreach Strategy SS V
This slide covers brief summary about community outreach strategy. The purpose of this template is to provide an overview on the benefits of community outreach strategy for creating public awareness. It also includes components of community outreach strategy such as purpose and goals of outreach, understanding demographics, outline key messages, partnering with local community, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Introduction To Community Outreach Building A Winning Community Outreach Strategy SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers brief summary about community outreach strategy. The purpose of this template is to provide an overview on the benefits of community outreach strategy for creating public awareness. It also includes components of community outreach strategy such as purpose and goals of outreach, understanding demographics, outline key messages, partnering with local community, etc.
Understanding The Home Care Start Up Elderly Care Business Plan Go To Market Strategy Introduction Pdf
The purpose of this slide is to outline the key objectives and goals of an organization and how to reach them by crafting an operational plan. It keeps teams on track while guiding them in making crucial decisions about the home care start up long term strategy Boost your pitch with our creative Understanding The Home Care Start Up Elderly Care Business Plan Go To Market Strategy Introduction Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The purpose of this slide is to outline the key objectives and goals of an organization and how to reach them by crafting an operational plan. It keeps teams on track while guiding them in making crucial decisions about the home care start up long term strategy
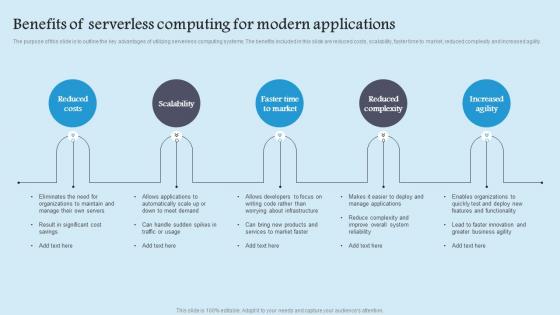
Benefits Serverless Computing Role Serverless Computing Modern Technology Slides Pdf
The purpose of this slide is to outline the key advantages of utilizing serverless computing systems. The benefits included in this slide are reduced costs, scalability, faster time to market, reduced complexity and increased agility. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Benefits Serverless Computing Role Serverless Computing Modern Technology Slides Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The purpose of this slide is to outline the key advantages of utilizing serverless computing systems. The benefits included in this slide are reduced costs, scalability, faster time to market, reduced complexity and increased agility.
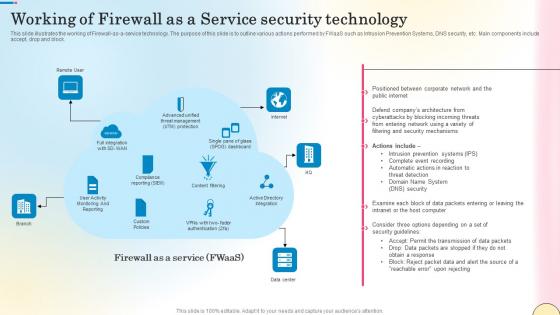
Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf
This slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block. Find highly impressive Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block.

Increasing Business Awareness Implementing SEO Basics To Rank Website Higher Strategy SS V
This slide presents an outline of a strategic SEO plan to optimize websites to rank better on search engines. It includes information about SEO basics such as keyword research, content creation, on-page optimization, mobile responsiveness, site speed, and link building. This Increasing Business Awareness Implementing SEO Basics To Rank Website Higher Strategy SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Increasing Business Awareness Implementing SEO Basics To Rank Website Higher Strategy SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide presents an outline of a strategic SEO plan to optimize websites to rank better on search engines. It includes information about SEO basics such as keyword research, content creation, on-page optimization, mobile responsiveness, site speed, and link building.

Complete Us Crypto Tax Guide Cryptocurrency Management With Blockchain
This slide discusses the taxes in the crypto market. The purpose of this slide is to outline the crypto tax criteria used in the United States of America on Bitcoin and Crypto. It also includes the tax range for long-term and short-term capital gains.If you are looking for a format to display your unique thoughts, then the professionally designed Complete Us Crypto Tax Guide Cryptocurrency Management With Blockchain is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Complete Us Crypto Tax Guide Cryptocurrency Management With Blockchain and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide discusses the taxes in the crypto market. The purpose of this slide is to outline the crypto tax criteria used in the United States of America on Bitcoin and Crypto. It also includes the tax range for long-term and short-term capital gains.
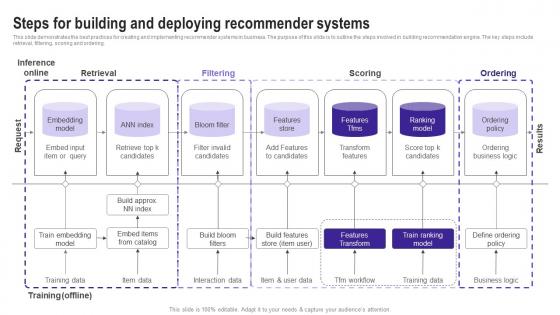
Steps For Building And Deploying Recommender Use Cases Of Filtering Methods Clipart Pdf
This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Steps For Building And Deploying Recommender Use Cases Of Filtering Methods Clipart Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide demonstrates the best practices for creating and implementing recommender systems in business. The purpose of this slide is to outline the steps involved in building recommendation engine. The key steps include retrieval, filtering, scoring and ordering.

Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain
This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain can be your best option for delivering a presentation. Represent everything in detail using Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.
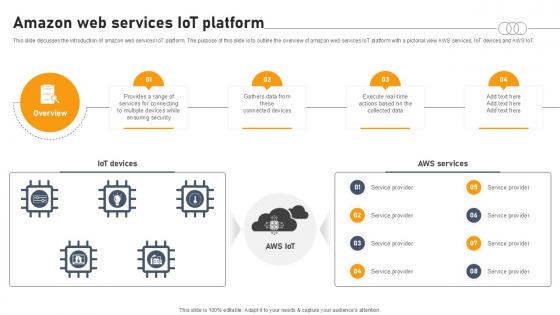
Amazon Web Services IOT Platform Aws IOT Platform Ppt Slide
This slide discusses the introduction of amazon web services IoT platform. The purpose of this slide is to outline the overview of amazon web services IoT platform with a pictorial view AWS services, IoT devices and AWS IoT. This Amazon Web Services IOT Platform Aws IOT Platform Ppt Slide is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Amazon Web Services IOT Platform Aws IOT Platform Ppt Slide features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide discusses the introduction of amazon web services IoT platform. The purpose of this slide is to outline the overview of amazon web services IoT platform with a pictorial view AWS services, IoT devices and AWS IoT.

Data Breach Awareness Training Program Data Breach Prevention Professional Pdf
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs. Find highly impressive Data Breach Awareness Training Program Data Breach Prevention Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Breach Prevention Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Data Breach Awareness Training Program Data Fortification Strengthening Defenses
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.Find highly impressive Data Breach Awareness Training Program Data Fortification Strengthening Defenses on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Fortification Strengthening Defenses for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.

Challenges Faced By Managers HR Retention Techniques For Business Owners Infographics Pdf
The purpose of this slide is to outline the top issues faced by human resource HR managers in retaining the workforce. The major challenges mentioned in the slide are salary dissatisfaction, better growth opportunities, selecting the wrong candidate, no job rotation and unrealistic expectations of employees. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Challenges Faced By Managers HR Retention Techniques For Business Owners Infographics Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Challenges Faced By Managers HR Retention Techniques For Business Owners Infographics Pdf The purpose of this slide is to outline the top issues faced by human resource HR managers in retaining the workforce. The major challenges mentioned in the slide are salary dissatisfaction, better growth opportunities, selecting the wrong candidate, no job rotation and unrealistic expectations of employees.
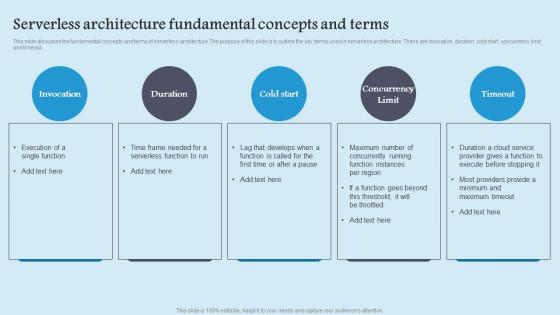
Serverless Architecture Fundamental Role Serverless Computing Modern Technology Structure Pdf
This slide discusses the fundamental concepts and terms of serverless architecture. The purpose of this slide is to outline the key terms used in serverless architecture. These are invocation, duration, cold start, concurrency limit and timeout. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Serverless Architecture Fundamental Role Serverless Computing Modern Technology Structure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Serverless Architecture Fundamental Role Serverless Computing Modern Technology Structure Pdf This slide discusses the fundamental concepts and terms of serverless architecture. The purpose of this slide is to outline the key terms used in serverless architecture. These are invocation, duration, cold start, concurrency limit and timeout.
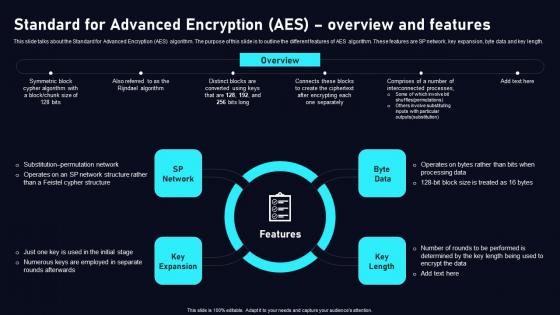
Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Standard For Advanced Encryption AES Cloud Data Security Using Cryptography Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length.
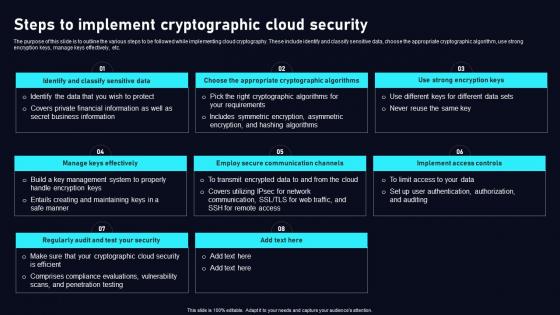
Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Find highly impressive Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.
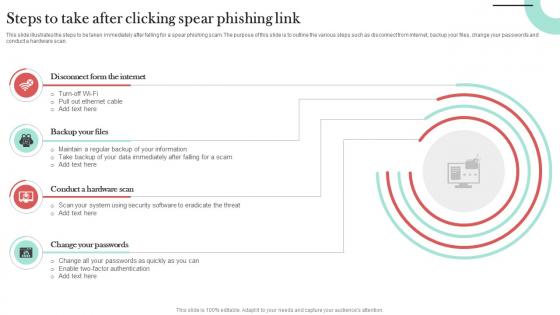
Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT
This slide illustrates the steps to be taken immediately after falling for a spear phishing scam. The purpose of this slide is to outline the various steps such as disconnect from internet, backup your files, change your passwords and conduct a hardware scan. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide illustrates the steps to be taken immediately after falling for a spear phishing scam. The purpose of this slide is to outline the various steps such as disconnect from internet, backup your files, change your passwords and conduct a hardware scan.
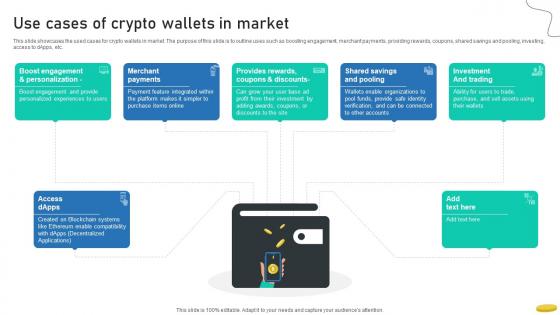
Use Cases Of Crypto Wallets In Market Cryptocurrency Management With Blockchain
This slide showcases the used cases for crypto wallets in market. The purpose of this slide is to outline uses such as boosting engagement, merchant payments, providing rewards, coupons, shared savings and pooling, investing, access to dApps, etc.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Use Cases Of Crypto Wallets In Market Cryptocurrency Management With Blockchain was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Use Cases Of Crypto Wallets In Market Cryptocurrency Management With Blockchain. This slide showcases the used cases for crypto wallets in market. The purpose of this slide is to outline uses such as boosting engagement, merchant payments, providing rewards, coupons, shared savings and pooling, investing, access to dApps, etc.
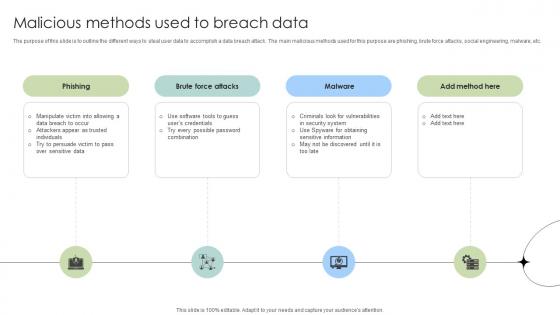
Malicious Methods Used To Breach Data Fortification Strengthening Defenses
The purpose of this slide is to outline the different ways to steal user data to accomplish a data breach attack. The main malicious methods used for this purpose are phishing, brute force attacks, social engineering, malware, etc.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Malicious Methods Used To Breach Data Fortification Strengthening Defenses to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Malicious Methods Used To Breach Data Fortification Strengthening Defenses. The purpose of this slide is to outline the different ways to steal user data to accomplish a data breach attack. The main malicious methods used for this purpose are phishing, brute force attacks, social engineering, malware, etc.
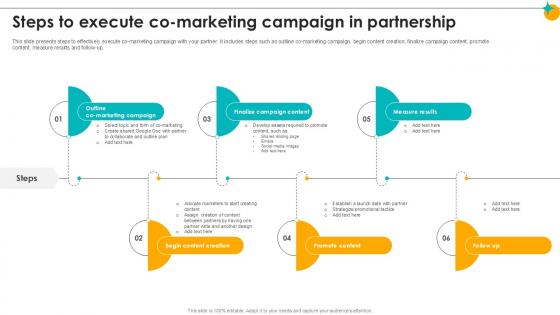
Steps To Execute Co Marketing Campaign In Partnership Partner Relationship Ppt Slides
This slide presents steps to effectively execute co-marketing campaign with your partner. It includes steps such as outline co-marketing campaign, begin content creation, finalize campaign content, promote content, measure results and follow-up. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Steps To Execute Co Marketing Campaign In Partnership Partner Relationship Ppt Slides and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide presents steps to effectively execute co marketing campaign with your partner. It includes steps such as outline co marketing campaign, begin content creation, finalize campaign content, promote content, measure results and follow up.

Factors To Consider While Choosing Tokenization Over Encryption Securing Your Data Ppt Example
This slide showcases the aspects to consider while choosing tokenization over encryption. The purpose of this slide is to outline the aspects such as reduction of compliance scope, format attributes, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Factors To Consider While Choosing Tokenization Over Encryption Securing Your Data Ppt Example was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Factors To Consider While Choosing Tokenization Over Encryption Securing Your Data Ppt Example This slide showcases the aspects to consider while choosing tokenization over encryption. The purpose of this slide is to outline the aspects such as reduction of compliance scope, format attributes, etc.

Corrective Regression Testing In Software Engineering Corrective Regression Testing Ppt Slide
This slide discusses about the characteristics of corrective regression testing. The purpose of this slide is to outline the various attributes such as performance, test case creation, area of focus and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Corrective Regression Testing In Software Engineering Corrective Regression Testing Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Corrective Regression Testing In Software Engineering Corrective Regression Testing Ppt Slide This slide discusses about the characteristics of corrective regression testing. The purpose of this slide is to outline the various attributes such as performance, test case creation, area of focus and so on.

Types Of Stress Testing For Software Smoke Testing Ppt Sample
This slide highlights the variety of stress testing in software development. The purpose of this slide is to outline the types of stress testing, which include historical, hypothetical, stylized stress testing, etc. Presenting this PowerPoint presentation, titled Types Of Stress Testing For Software Smoke Testing Ppt Sample, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Types Of Stress Testing For Software Smoke Testing Ppt Sample. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Types Of Stress Testing For Software Smoke Testing Ppt Sample that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide highlights the variety of stress testing in software development. The purpose of this slide is to outline the types of stress testing, which include historical, hypothetical, stylized stress testing, etc.
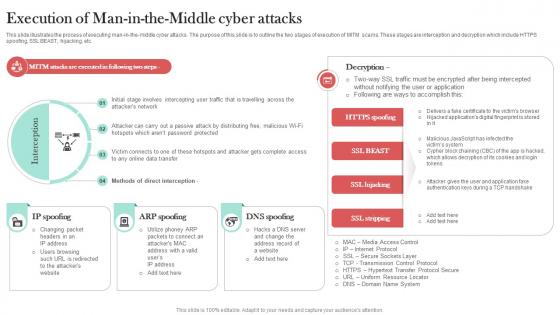
Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT
This slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc. Welcome to our selection of the Execution Of Man In The Middle Cyber Attacks Man In The Middle Phishing IT. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption which include HTTPS spoofing, SSL BEAST, hijacking, etc.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc.
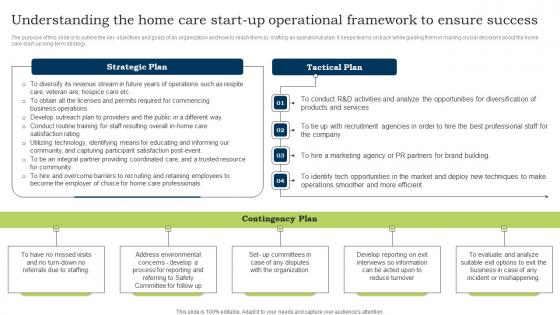
Go To Market Strategy Understanding The Home Care Start Up Operational Demonstration Pdf
The purpose of this slide is to outline the key objectives and goals of an organization and how to reach them by crafting an operational plan. It keeps teams on track while guiding them in making crucial decisions about the home care start-up long-term strategy Presenting this PowerPoint presentation, titled Go To Market Strategy Understanding The Home Care Start Up Operational Demonstration Pdf with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Go To Market Strategy Understanding The Home Care Start Up Operational Demonstration Pdf Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Go To Market Strategy Understanding The Home Care Start Up Operational Demonstration Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. The purpose of this slide is to outline the key objectives and goals of an organization and how to reach them by crafting an operational plan. It keeps teams on track while guiding them in making crucial decisions about the home care start-up long-term strategy
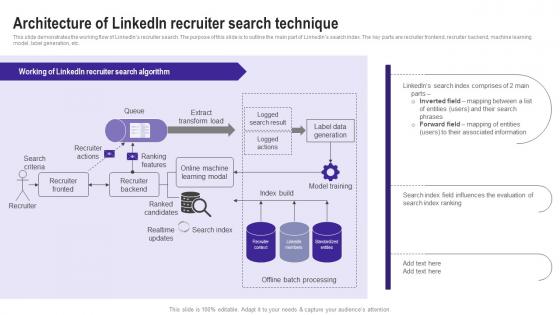
Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf
This slide demonstrates the working flow of LinkedIns recruiter search. The purpose of this slide is to outline the main part of LinkedIns search index. The key parts are recruiter frontend, recruiter backend, machine learning model, label generation, etc. Get a simple yet stunning designed Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Architecture Of Linkedin Use Cases Of Filtering Methods Rules Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide demonstrates the working flow of LinkedIns recruiter search. The purpose of this slide is to outline the main part of LinkedIns search index. The key parts are recruiter frontend, recruiter backend, machine learning model, label generation, etc.
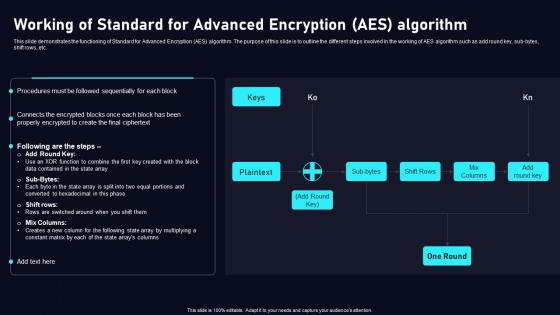
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc.
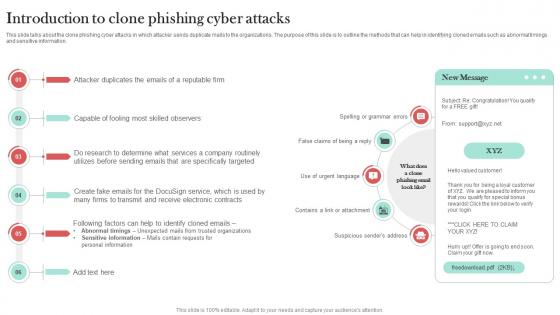
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.
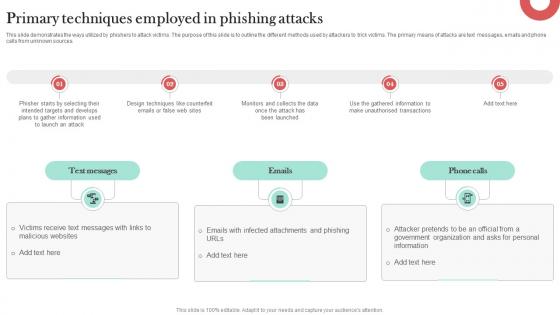
Primary Techniques Employed In Phishing Man In The Middle Phishing IT
This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Slidegeeks is here to make your presentations a breeze with Primary Techniques Employed In Phishing Man In The Middle Phishing IT With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources.
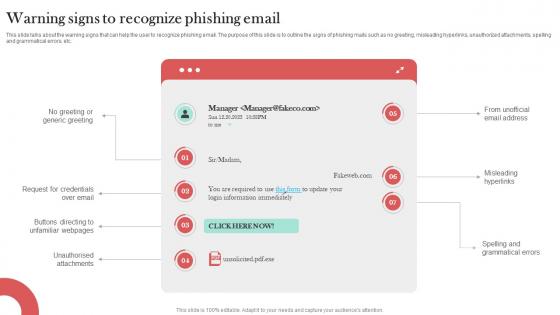
Warning Signs To Recognize Phishing Email Man In The Middle Phishing IT
This slide talks about the warning signs that can help the user to recognize phishing email. The purpose of this slide is to outline the signs of phishing mails such as no greeting, misleading hyperlinks, unauthorized attachments, spelling and grammatical errors, etc. Slidegeeks has constructed Warning Signs To Recognize Phishing Email Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the warning signs that can help the user to recognize phishing email. The purpose of this slide is to outline the signs of phishing mails such as no greeting, misleading hyperlinks, unauthorized attachments, spelling and grammatical errors, etc.


 Continue with Email
Continue with Email

 Home
Home


































