Password Security

Cloud Computing Project Analysis Diagram Powerpoint Template
Our above PPT slide contains graphics of cloud with technology icons. This PowerPoint template may be used for project related to cloud computing. Use this diagram to impart more clarity to data and to create more sound impact on viewers.
Traffic Cones Around Road Powerpoint Templates
Traffic cones around road have been used to design this power point template. Use this diagram to display traffic rules and safety. Download this diagram to display information in visual manner.

Keyhole Circular Infographic Design Powerpoint Templates
This slide has been designed with circular infographic with key hole in center. This PowerPoint template is suitable to present key steps of success. This professional slide helps in making an instant impact on viewers.
Keyhole Circular Puzzle Layout Powerpoint Templates
This slide has been designed with circular puzzle with key hole in center. This Powerpoint template is suitable to present key steps of success. This professional slide helps in making an instant impact on viewers.
Ppt Continual Way To Prevent Manufacture Losses Seven Steps PowerPoint Templates
PPT continual way to prevent manufacture losses seven steps PowerPoint Templates-This PowerPoint Diagram shows you the continual way to prevent manufacture losses in any Business related Activities. It is shown by different shades of Brown color. -PPT continual way to prevent manufacture losses seven steps PowerPoint Templates-Anti-Virus, Caution, Computer, Computing, Concept, Crime, Danger, Encrypt, Encryption, Firewall, Fraud, Hazard, Hazardous, Internet, Lose, Loss, Network, Networking, Online, Password, Piracy, Precaution, Prevent, Prevention, Privacy, Private, Protect, Protection, Risk, Screen, Secure, Security, Site, Steal, Stealing, Text, Theft, Thievery, Viral, Virus, Warn, Web, Website, Words Review your plans with our Ppt Continual Way To Prevent Manufacture Losses Seven Steps PowerPoint Templates. Download without worries with our money back guaranteee.
Ppt Successive Representation Of 7 Stages An Arrow PowerPoint Templates
PPT successive representation of 7 stages an arrow PowerPoint Templates-This PowerPoint Diagram shows you the Successive Representation of five approaches on the Arrow. It shows the successive concepts used in a procedure. You can change color, size and orientation of any icon to your liking.-PPT successive representation of 7 stages an arrow PowerPoint Templates-Anti-Virus, Caution, Computer, Computing, Concept, Crime, Danger, Encrypt, Encryption, Firewall, Fraud, Hazard, Hazardous, Internet, Lose, Loss, Network, Networking, Online, Password, Piracy, Precaution, Prevent, Prevention, Privacy, Private, Protect, Protection, Risk, Screen, Secure, Security, Site, Steal, Stealing, Text, Theft, Thievery, Viral, Virus, Warn, Web, Website, Words Let the audience decide with our Ppt Successive Representation Of 7 Stages An Arrow PowerPoint Templates. Make sure your presentation gets the attention it deserves.
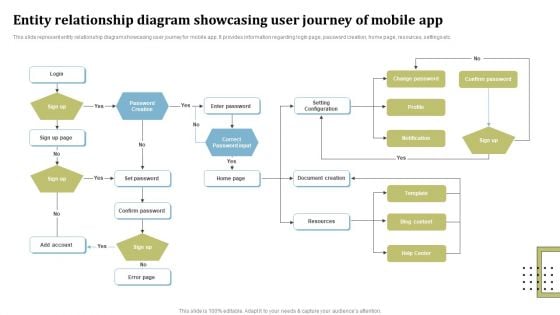
Entity Relationship Diagram Showcasing User Journey Of Mobile App Topics PDF
This slide represent entity relationship diagram showcasing user journey for mobile app. It provides information regarding login page, password creation, home page, resources, settings etc. Presenting Entity Relationship Diagram Showcasing User Journey Of Mobile App Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Password Creation, Correct Password Input, Setting Configuration, Document Creation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
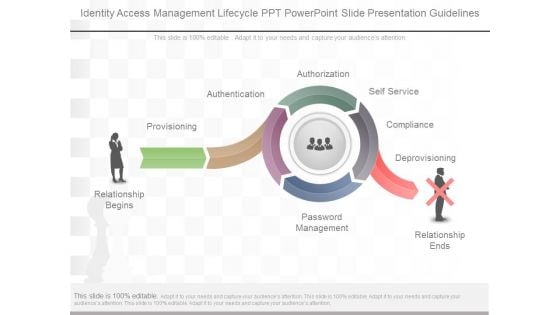
Identity Access Management Lifecycle Ppt Powerpoint Slide Presentation Guidelines
This is a identity access management lifecycle ppt powerpoint slide presentation guidelines. This is a five stage process. The stages in this process are relationship begins, provisioning, authentication, authorization, self service, compliance, deprovisioning, password management, relationship ends.

Authentication Process Flow Of Verification Factors From Client And Server Side Structure PDF
Pitch your topic with ease and precision using thisauthentication process flow of verification factors from client and server side structure pdf This layout presents information on individual enters password, second form of authentication, one time password entered manually. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Five Key Steps For Business Analysis Powerpoint Template
This PowerPoint template has been designed with five icons around key. This PowerPoint template helps to exhibit directions for strategic planning. Use this diagram slide to build an exclusive presentation.
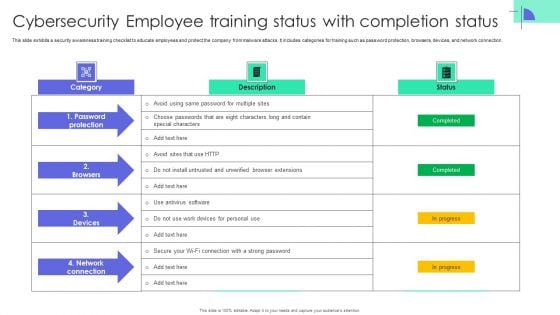
Cybersecurity Employee Training Status With Completion Status Structure PDF
This slide exhibits a security awareness training checklist to educate employees and protect the company from malware attacks. It includes categories for training such as password protection, browsers, devices, and network connection. Pitch your topic with ease and precision using this Cybersecurity Employee Training Status With Completion Status Structure PDF. This layout presents information on Training Status Completion Status, Cybersecurity Employee. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
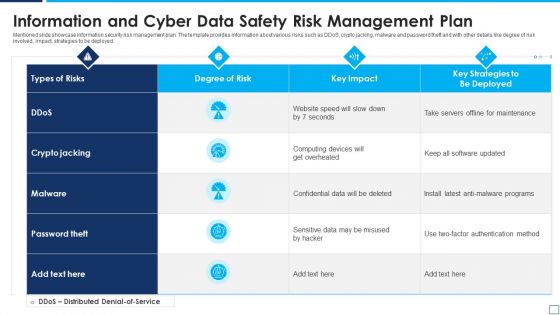
Information And Cyber Data Safety Risk Management Plan Summary PDF
Mentioned slide showcase information security risk management plan. The template provides information about various risks such as DDoS, crypto jacking, malware and password theft and with other details like degree of risk involved, impact, strategies to be deployed. Showcasing this set of slides titled information and cyber data safety risk management plan summary pdf. The topics addressed in these templates are information and cyber data safety risk management plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Prevention Of Information In House Training Schedule We Will Implement Professional PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Prevention Of Information In House Training Schedule We Will Implement Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cybersecurity Awareness Program To Prevent Attacks In House Training Schedule We Will Implement Themes PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

ESO System Center System Ppt PowerPoint Presentation File Portrait PDF
This slide covers enterprise security operation center system. It involves business security, data security, infrastructure, office network and application security. Showcasing this set of slides titled ESO System Center System Ppt PowerPoint Presentation File Portrait PDF. The topics addressed in these templates are Security Risks, Business Security, Data Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
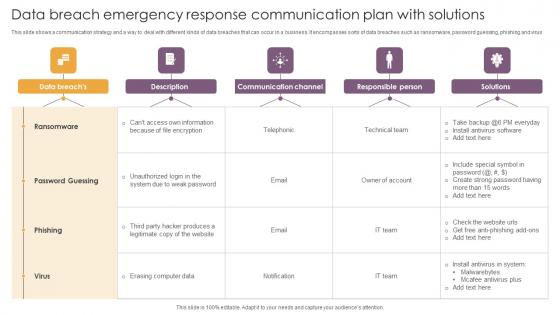
Data Breach Emergency Response Communication Plan With Solutions Introduction Pdf
This slide shows a communication strategy and a way to deal with different kinds of data breaches that can occur in a business. It encompasses sorts of data breaches such as ransomware, password guessing, phishing and virus Showcasing this set of slides titled Data Breach Emergency Response Communication Plan With Solutions Introduction Pdf The topics addressed in these templates are Ransomware, Password Guessing, Communication Channel All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows a communication strategy and a way to deal with different kinds of data breaches that can occur in a business. It encompasses sorts of data breaches such as ransomware, password guessing, phishing and virus

Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf
This slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments Showcasing this set of slides titled Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf. The topics addressed in these templates are Security Assessments, Building Security, Facility Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments
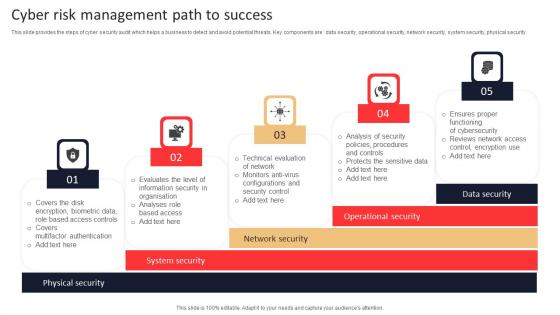
Cyber Risk Management Path To Success Inspiration Pdf
This slide provides the steps of cyber security audit which helps a business to detect and avoid potential threats. Key components are data security, operational security, network security, system security, physical security. Showcasing this set of slides titled Cyber Risk Management Path To Success Inspiration Pdf. The topics addressed in these templates are Biometric Data, Information Security, Analyses. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide provides the steps of cyber security audit which helps a business to detect and avoid potential threats. Key components are data security, operational security, network security, system security, physical security.
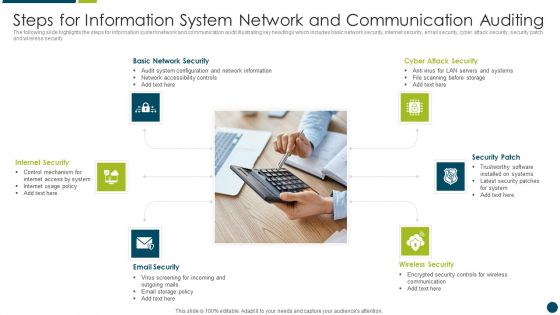
Steps For Information System Network And Communication Auditing Topics PDF
The following slide highlights the steps for information system network and communication audit illustrating key headings which includes basic network security, internet security, email security, cyber attack security, security patch and wireless security Presenting Steps For Information System Network And Communication Auditing Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Basic Network Security, Internet Security, Security Patch. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully
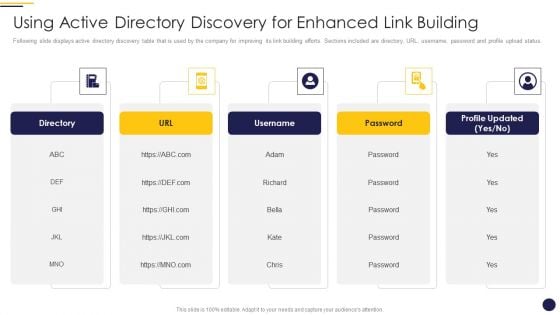
Internet Marketing Playbook Using Active Directory Discovery For Enhanced Link Building Graphics PDF
Following slide displays active directory discovery table that is used by the company for improving its link building efforts. Sections included are directory, URL, username, password and profile upload status. This is a Internet Marketing Playbook Using Active Directory Discovery For Enhanced Link Building Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Directory URL Username, Password Profile Updated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Client Acquisition Journey Plan Best Practices For Customers Registration Sample PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Client Acquisition Journey Plan Best Practices For Customers Registration Sample PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
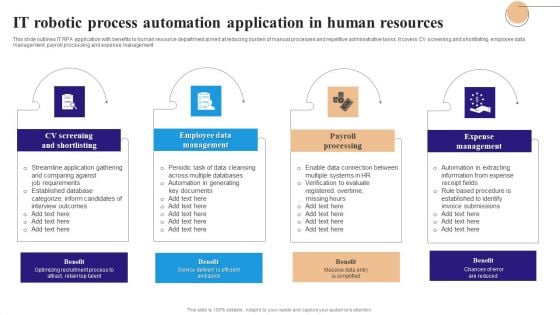
IT Robotic Process Automation Application In Human Resources Topics PDF
This slide highlights use cases of robotic process automation in information technology sector aimed at standardizing key processes to reduce human error. It covers the following cases backup and patch management, password resets, server and app monitoring, routine monitoring and email processing Showcasing this set of slides titled IT Robotic Process Automation Application In Human Resources Topics PDF. The topics addressed in these templates are Backup Patch Management, Password Resets, Server App Monitoring . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
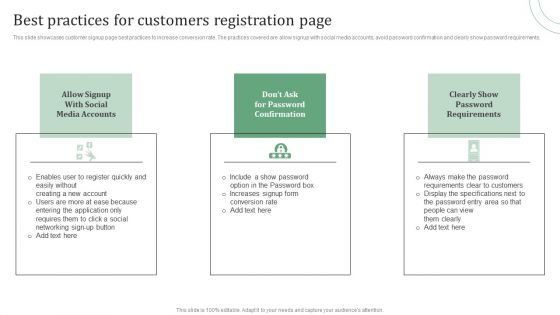
Standard Approaches For Client Onboarding Journey Best Practices For Customers Formats PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Want to ace your presentation in front of a live audience Our Standard Approaches For Client Onboarding Journey Best Practices For Customers Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
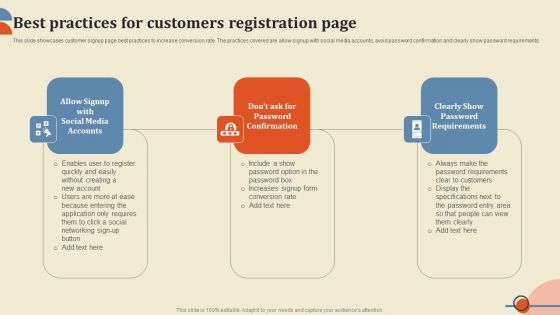
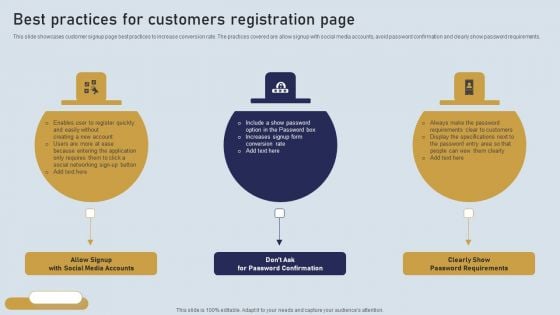
Best Practices For Customers Registration Page Ppt PowerPoint Presentation File Infographics PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Take your projects to the next level with our ultimate collection of Best Practices For Customers Registration Page Ppt PowerPoint Presentation File Infographics PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
Onboarding Journey For Effective Client Communication Best Practices For Customers Registration Page Pictures PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Onboarding Journey For Effective Client Communication Best Practices For Customers Registration Page Pictures PDF from Slidegeeks and deliver a wonderful presentation.
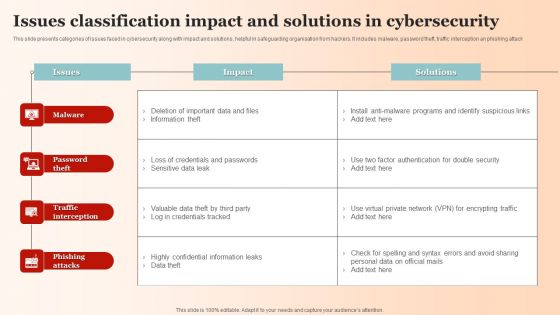
Issues Classification Impact And Solutions In Cybersecurity Pictures PDF
This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack Pitch your topic with ease and precision using this Issues Classification Impact And Solutions In Cybersecurity Pictures PDF. This layout presents information on Malware, Password Theft, Traffic Interception. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Techniques To Enhance User Onboarding Journey Best Practices For Customers Registration Page Guidelines PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Techniques To Enhance User Onboarding Journey Best Practices For Customers Registration Page Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Stock Photo 3d Combination Lock For Safety Image Graphics For PowerPoint Slide
This image slide has been crafted with graphic of combination lock on database icon. This image explains the concept of security. Define total security concept with this exclusive image. Use this image slide for business and security related presentations.
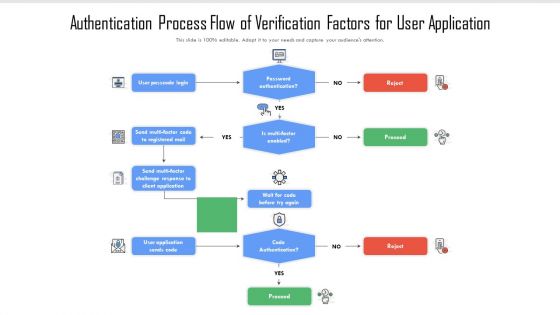
Authentication Process Flow Of Verification Factors For User Application Rules PDF
Pitch your topic with ease and precision using this authentication process flow of verification factors for user application rules pdf. This layout presents information on password authentication, code authentication, user passcode login. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Tracking Sheet To Monitor The Performance Of Employees Demonstration PDF
Deliver an awe inspiring pitch with this creative Tracking Sheet To Monitor The Performance Of Employees Demonstration PDF bundle. Topics like Social Engineering, Ransomware, Password Attack can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Tools Provided By Google To Prevent Man In The Middle Phishing IT
This slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc. Welcome to our selection of the Tools Provided By Google To Prevent Man In The Middle Phishing IT. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc.

Client Side Encryption Using Nordlocker Client Side Encryption PPT Presentation
This slide discusses the NordLocker software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with NordLocker software, such as downloading and installing, creating a password, using the password to view the encrypted files, etc. Get a simple yet stunning designed Client Side Encryption Using Nordlocker Client Side Encryption PPT Presentation. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Side Encryption Using Nordlocker Client Side Encryption PPT Presentation can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide discusses the NordLocker software for cloud data encryption. The purpose of this slide is to highlight the steps involved in working with NordLocker software, such as downloading and installing, creating a password, using the password to view the encrypted files, etc.
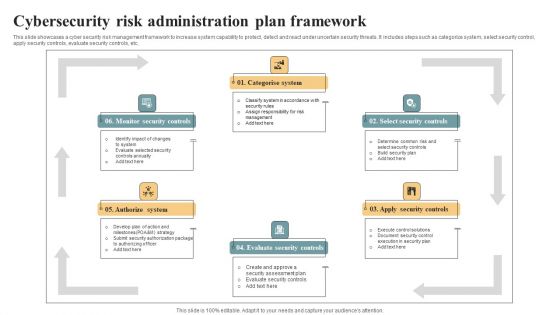
Cybersecurity Risk Administration Plan Framework Ideas PDF
This slide showcases a cyber security risk management framework to increase system capability to protect, detect and react under uncertain security threats. It includes steps such as categorize system, select security control, apply security controls, evaluate security controls, etc. Presenting Cybersecurity Risk Administration Plan Framework Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Categorise System, Select Security Controls, Apply Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Convergence Strategy Information IT OT Team Responsibilities Based On Target Slides PDF bundle. Topics like OT Security Functions, Security Architecture And Engineering, Primary Responsibility, Shared Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
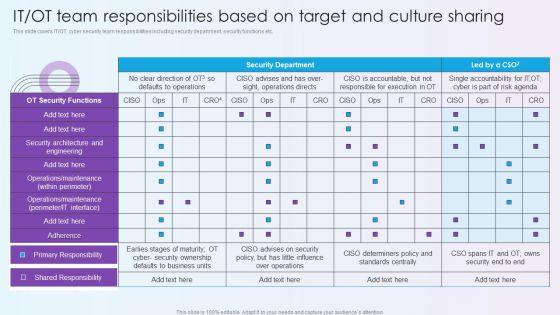
Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF
This slide covers IT or OT cyber security team responsibilities including security department, security functions etc. Deliver and pitch your topic in the best possible manner with this Digitalization Of Operative Enterprises IT OT Team Responsibilities Based On Target And Culture Sharing Microsoft PDF. Use them to share invaluable insights on Security Functions, Security Ownership, Determiners and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
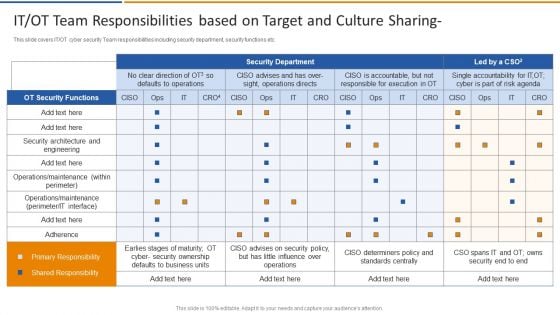
Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF
This slide covers IT or OT cyber security Team responsibilities including security department, security functions etc. Deliver an awe inspiring pitch with this creative Smart Venture Digitial Transformation IT OT Team Responsibilities Based On Target Structure PDF bundle. Topics like OT Security Functions, Security architecture, Primary Responsibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
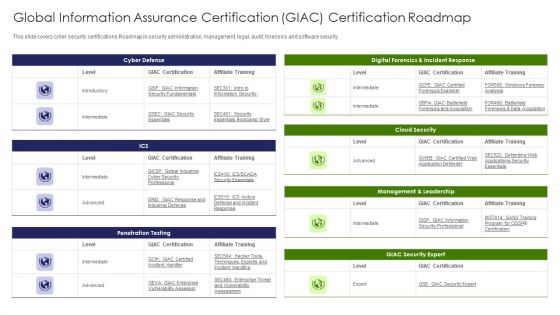
IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver and pitch your topic in the best possible manner with this IT Professional Data Certification Program Global Information Assurance Certification GIAC Certification Roadmap Sample PDF. Use them to share invaluable insights on Cloud Security, Management, Security Expert and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
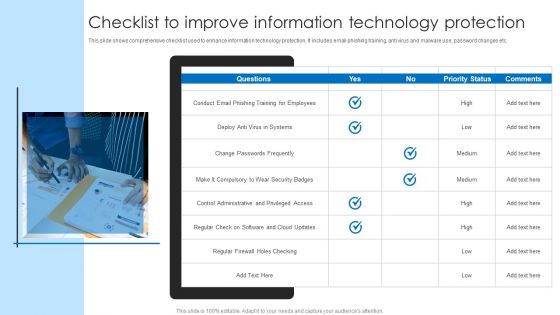
Checklist To Improve Information Technology Protection Inspiration PDF
This slide shows comprehensive checklist used to enhance information technology protection. It includes email phishing training, anti virus and malware use, password changes etc. Presenting Checklist To Improve Information Technology Protection Inspiration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security, Employees, Information Technology Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
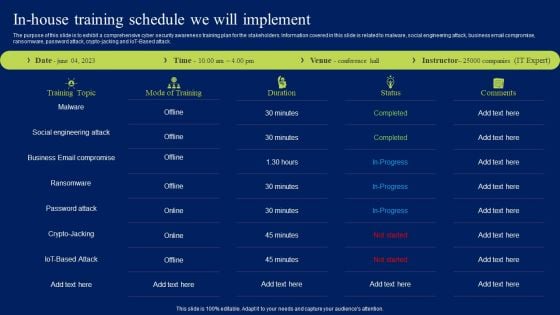
In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
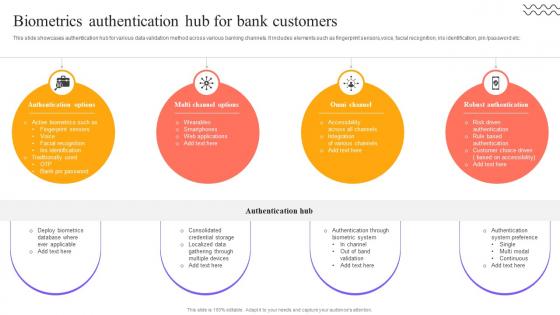
Digital Approach To Client Biometrics Authentication Hub For Bank Customers
This slide showcases authentication hub for various data validation method across various banking channels. It includes elements such as fingerprint sensors,voice, facial recognition, iris identification, pin or password etc. Find highly impressive Digital Approach To Client Biometrics Authentication Hub For Bank Customers on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Digital Approach To Client Biometrics Authentication Hub For Bank Customers for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases authentication hub for various data validation method across various banking channels. It includes elements such as fingerprint sensors,voice, facial recognition, iris identification, pin or password etc.

Stock Photo 3d Globe Green Glass PowerPoint Slide
This graphic image has been crafted with globe and chain. In this image globe is secured with chain which shows the concept of global security. Use this image to display global security issues and benefits in any presentation.
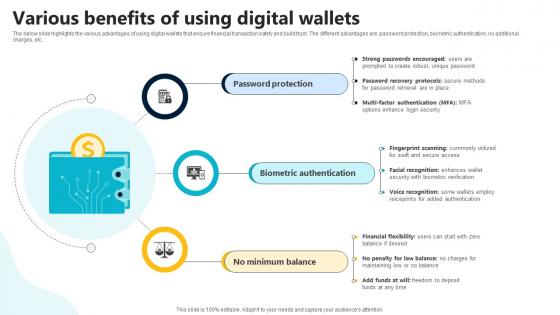
Various Benefits Of Using Digital Wallets In Depth Guide To Digital Wallets Fin SS V
The below slide highlights the various advantages of using digital wallets that ensure financial transaction safety and build trust. The different advantages are password protection, biometric authentication, no additional charges, etc. The Various Benefits Of Using Digital Wallets In Depth Guide To Digital Wallets Fin SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The below slide highlights the various advantages of using digital wallets that ensure financial transaction safety and build trust. The different advantages are password protection, biometric authentication, no additional charges, etc.

Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V
This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection. Are you searching for a Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Empowering The Future Strategies To Reduce Cybersecurity Concerns In IoT SS V from Slidegeeks today. This slide exhibits key cybersecurity concerns solving methods for IoT-enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection.
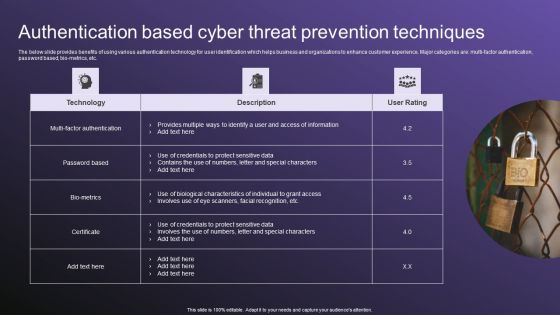
Authentication Based Cyber Threat Prevention Techniques Download PDF
The below slide provides benefits of using various authentication technology for user identification which helps business and organizations to enhance customer experience. Major categories are multi factor authentication, password based, bio-metrics, etc. Showcasing this set of slides titled Authentication Based Cyber Threat Prevention Techniques Download PDF. The topics addressed in these templates are Techniques, Authentication, Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Top To Down Approach For Business Information Protection Demonstration PDF
This slide covers top to down approach for business security which includes security leadership, program, policies and management. Further, it includes user management and information asset security.Pitch your topic with ease and precision using this Top To Down Approach For Business Information Protection Demonstration PDF. This layout presents information on Security Leadership, Security Program, Security Policies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
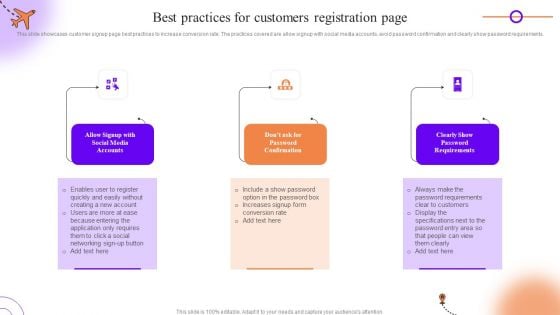
Client Onboarding Journey Impact On Business Best Practices For Customers Registration Page Brochure PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Client Onboarding Journey Impact On Business Best Practices For Customers Registration Page Brochure PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
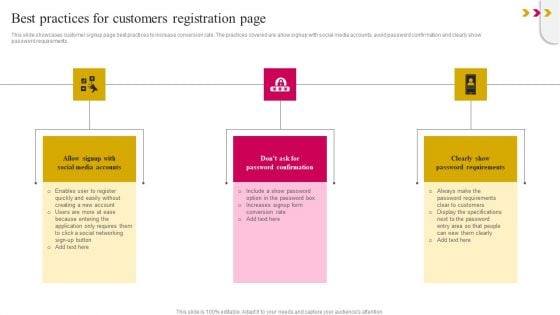
Best Practices For Customers Registration Page Brochure PDF
This slide showcases customer signup page best practices to increase conversion rate. The practices covered are allow signup with social media accounts, avoid password confirmation and clearly show password requirements. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Best Practices For Customers Registration Page Brochure PDF can be your best option for delivering a presentation. Represent everything in detail using Best Practices For Customers Registration Page Brochure PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
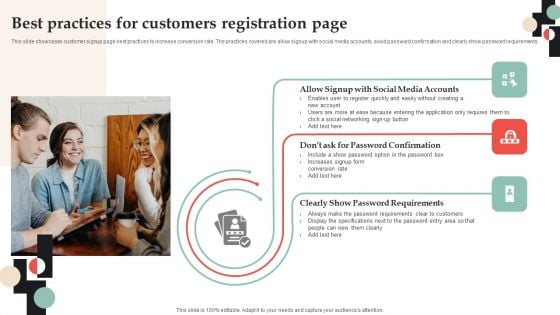
Customer Onboarding Journey Optimization Plan Best Practices For Customers Registration Page Infographics PDF

Effective Checklist For Cybersecurity In Medical Industry Brochure Pdf
This slide presents effective checklist for setting up cybersecurity in healthcare helpful for organisations to check completion of important tasks. It includes mobility policy, disaster recovery provider, proper password policy and encryption Showcasing this set of slides titled Effective Checklist For Cybersecurity In Medical Industry Brochure Pdf. The topics addressed in these templates are Factors, Description, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide presents effective checklist for setting up cybersecurity in healthcare helpful for organisations to check completion of important tasks. It includes mobility policy, disaster recovery provider, proper password policy and encryption

Clone Phishing Attacks Preventive Measures Man In The Middle Phishing IT
This slide talks about the various steps that can be taken to prevent clone phishing attacks. These include review senders address, preview links before opening them, use a password manager, investigate spoofed replies, double check URL addresses, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Clone Phishing Attacks Preventive Measures Man In The Middle Phishing IT. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the various steps that can be taken to prevent clone phishing attacks. These include review senders address, preview links before opening them, use a password manager, investigate spoofed replies, double check URL addresses, etc.
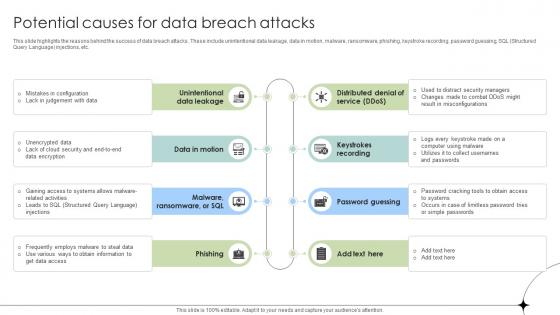
Potential Causes For Data Breach Attacks Data Fortification Strengthening Defenses
This slide highlights the reasons behind the success of data breach attacks. These include unintentional data leakage, data in motion, malware, ransomware, phishing, keystroke recording, password guessing, SQL Structured Query Language injections, etc.Find a pre-designed and impeccable Potential Causes For Data Breach Attacks Data Fortification Strengthening Defenses. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide highlights the reasons behind the success of data breach attacks. These include unintentional data leakage, data in motion, malware, ransomware, phishing, keystroke recording, password guessing, SQL Structured Query Language injections, etc.

Categories Of Issues Impact And Solutions In Cybersecurity PPT Template SS
This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack. Explore a selection of the finest Categories Of Issues Impact And Solutions In Cybersecurity PPT Template SS here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Categories Of Issues Impact And Solutions In Cybersecurity PPT Template SS to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack.
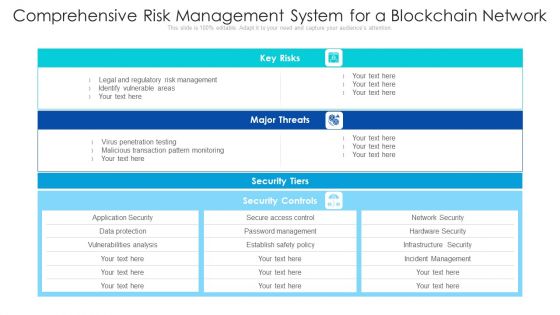
Comprehensive Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Professional Background Images PDF
Pitch your topic with ease and precision using this comprehensive risk management system for a blockchain network ppt powerpoint presentation professional background images pdf. This layout presents information on password management, malicious transaction pattern, identify vulnerable areas. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
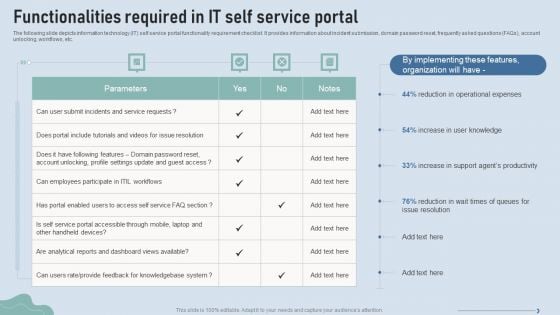
Improve IT Service Desk Functionalities Required In IT Self Service Portal Structure PDF
The following slide depicts information technology IT self service portal functionality requirement checklist. It provides information about incident submission, domain password reset, frequently asked questions FAQs, account unlocking, workflows, etc. Deliver an awe inspiring pitch with this creative Improve IT Service Desk Functionalities Required In IT Self Service Portal Structure PDF bundle. Topics like Operational Expenses, Agents Productivity, Issue Resolution can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
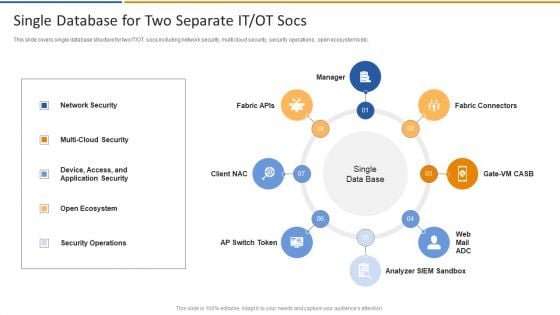
Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Network Security, Multi Cloud Security, Device Access, Application Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
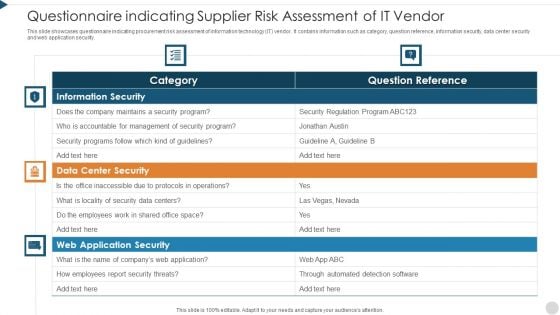
Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Steps Risk Management Process Of Insurance Process Mockup PDF
This slide show the risk management process which can be used by banking insurance company. It includes information security program, security codes, cyber security and training. Pitch your topic with ease and precision using this Five Steps Risk Management Process Of Insurance Process Mockup PDF. This layout presents information on Information Security Program, Security Codes, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers major products and services provided by email security enterprise to its customers. It includes solutions such as email security email suite, email security marketing, and email security email API.

Stock Photo Blue Umbrella Over Usa Flag Print Text PowerPoint Slide
This Power Point slide has been designed with graphic of blue umbrella and US flag design. This image slide contains the concept of USA security and protection schemes. Use this professional design to build presentation for security related topics.
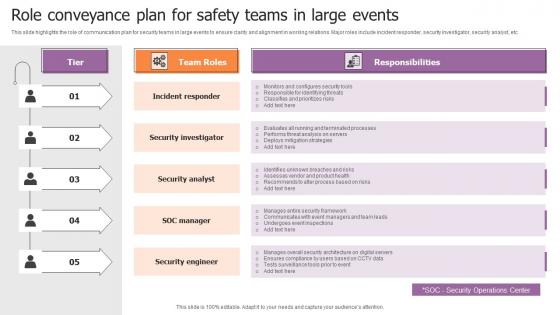
Role Conveyance Plan For Safety Teams In Large Events Ideas Pdf
This slide highlights the role of communication plan for security teams in large events to ensure clarity and alignment in working relations. Major roles include incident responder, security investigator, security analyst, etc. Showcasing this set of slides titled Role Conveyance Plan For Safety Teams In Large Events Ideas Pdf. The topics addressed in these templates are Incident Responder, Security Investigator, Security Analyst. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide highlights the role of communication plan for security teams in large events to ensure clarity and alignment in working relations. Major roles include incident responder, security investigator, security analyst, etc.


 Continue with Email
Continue with Email

 Home
Home


































