People Profiles
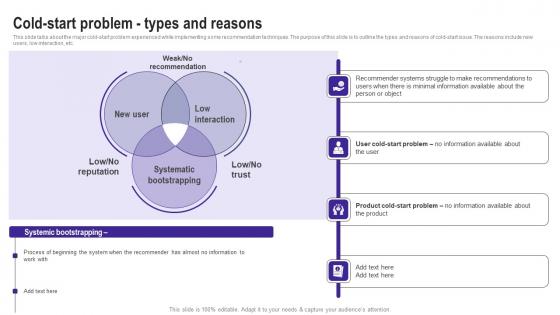
Cold Start Problem Types And Reasons Use Cases Of Filtering Methods Slides Pdf
This slide talks about the major cold start problem experienced while implementing some recommendation techniques. The purpose of this slide is to outline the types and reasons of cold start issue. The reasons include new users, low interaction, etc. Find highly impressive Cold Start Problem Types And Reasons Use Cases Of Filtering Methods Slides Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cold Start Problem Types And Reasons Use Cases Of Filtering Methods Slides Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the major cold start problem experienced while implementing some recommendation techniques. The purpose of this slide is to outline the types and reasons of cold start issue. The reasons include new users, low interaction, etc.
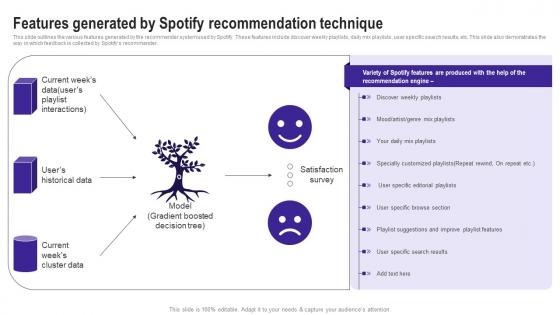
Features Generated By Spotify Recommendation Use Cases Of Filtering Methods Introduction Pdf
This slide outlines the various features generated by the recommender system used by Spotify. These features include discover weekly playlists, daily mix playlists, user specific search results, etc. This slide also demonstrates the way in which feedback is collected by Spotifys recommender. Explore a selection of the finest Features Generated By Spotify Recommendation Use Cases Of Filtering Methods Introduction Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Features Generated By Spotify Recommendation Use Cases Of Filtering Methods Introduction Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the various features generated by the recommender system used by Spotify. These features include discover weekly playlists, daily mix playlists, user specific search results, etc. This slide also demonstrates the way in which feedback is collected by Spotifys recommender.
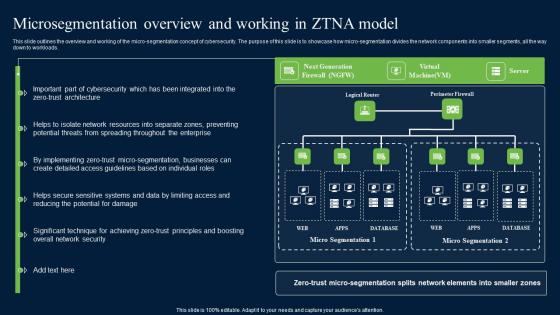
Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In ZTNA Zero Trust Network Security Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
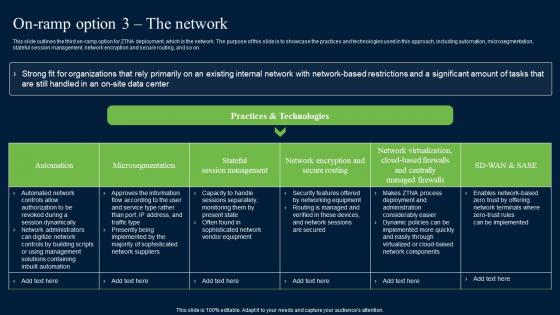
On Ramp Option 3 The Network Zero Trust Network Security Information Pdf
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Zero Trust Network Security Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Zero Trust Network Security Information Pdf from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.
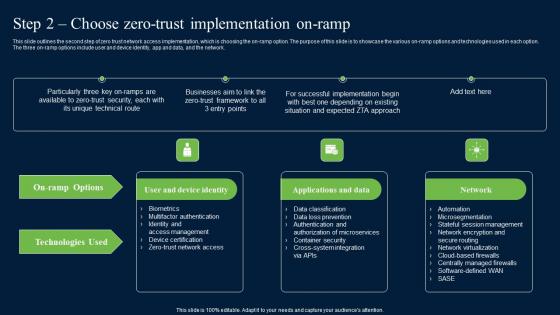
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
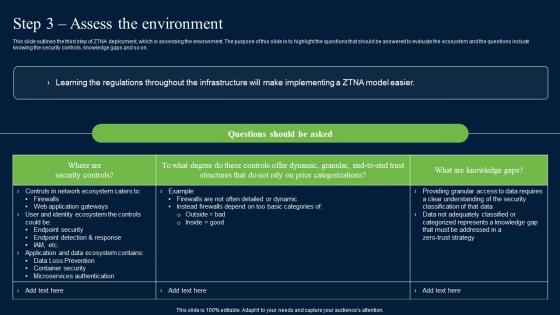
Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf
This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Want to ace your presentation in front of a live audience Our Step 3 Assess The Environment Zero Trust Network Security Brochure Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on.
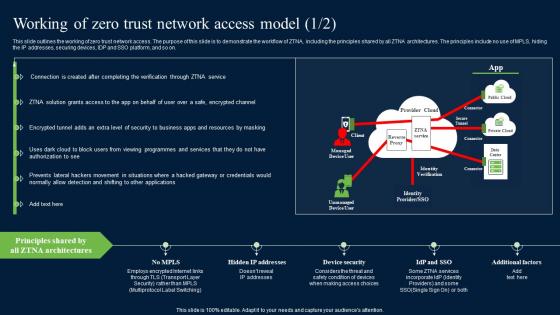
Working Of Zero Trust Network Access Model Security Pictures Pdf
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Working Of Zero Trust Network Access Model Security Pictures Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.
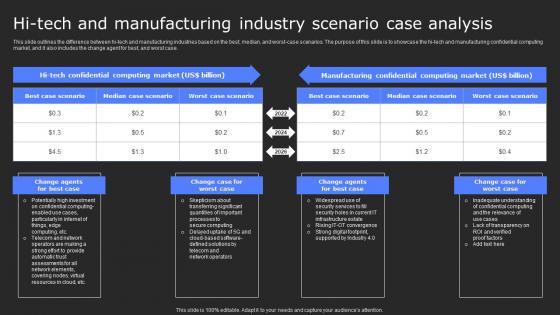
Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf
This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Hi Tech And Manufacturing Industry Scenario Secure Computing Framework Rules Pdf. This slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case.
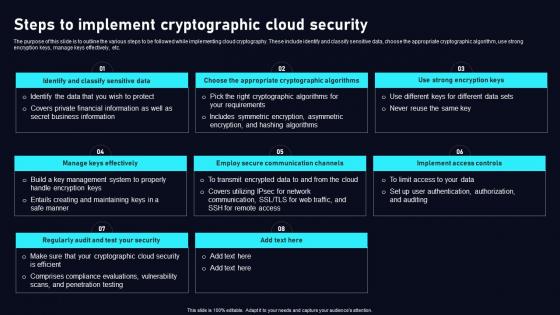
Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf
The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Find highly impressive Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Steps To Implement Cryptographic Cloud Data Security Using Cryptography Brochure Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc.

Data Breach Awareness Training Program Data Breach Prevention Professional Pdf
This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs. Find highly impressive Data Breach Awareness Training Program Data Breach Prevention Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Breach Awareness Training Program Data Breach Prevention Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide represents the training program for data breach awareness which will help organizations to prevent various cyber security scams. The purpose of this slide is to outline the mode, cost, agenda, and schedule for the training programs.
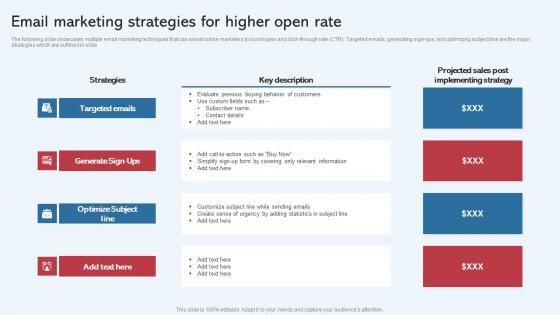
Email Marketing Strategies For Higher Open Rate Effective Startup Promotion Plan Guidelines Pdf
The following slide showcases multiple email marketing techniques that can assist online marketers to boost open and click through rate CTR. Targeted emails, generating sign ups, and optimizing subject line are the major strategies which are outlined in slide. Find highly impressive Email Marketing Strategies For Higher Open Rate Effective Startup Promotion Plan Guidelines Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Email Marketing Strategies For Higher Open Rate Effective Startup Promotion Plan Guidelines Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. The following slide showcases multiple email marketing techniques that can assist online marketers to boost open and click through rate CTR. Targeted emails, generating sign ups, and optimizing subject line are the major strategies which are outlined in slide.

Major Types Of Search Engine Optimization Effective Startup Promotion Plan Introduction Pdf
The following slide showcases various types of search engine optimization SEO through which marketing teams can increase visitors to website and gain competitive edge. The types outlined in slide are on page, off page, technical and local SEO. Explore a selection of the finest Major Types Of Search Engine Optimization Effective Startup Promotion Plan Introduction Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Major Types Of Search Engine Optimization Effective Startup Promotion Plan Introduction Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. The following slide showcases various types of search engine optimization SEO through which marketing teams can increase visitors to website and gain competitive edge. The types outlined in slide are on page, off page, technical and local SEO.
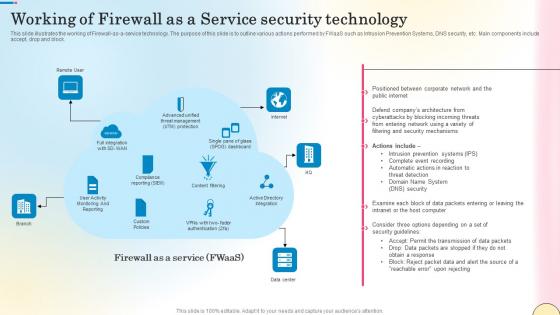
Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf
This slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block. Find highly impressive Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block.

Key Facts Healthcare Product Company Fund Raising Pitch Deck Elements Pdf
The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of out of stock rate, average time to sell, on time in full deliveries, sold products within freshness date, cash to cash cycle time and on shelf availability rate. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Key Facts Healthcare Product Company Fund Raising Pitch Deck Elements Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of out of stock rate, average time to sell, on time in full deliveries, sold products within freshness date, cash to cash cycle time and on shelf availability rate.
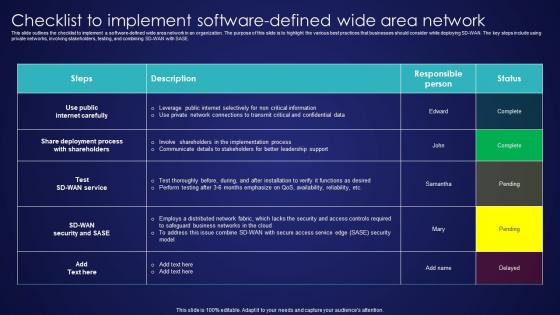
Checklist To Implement Software Defined Wide Area Network Wide Area Network Services Ideas Pdf
This slide outlines the checklist to implement a software-defined wide area network in an organization. The purpose of this slide is to highlight the various best practices that businesses should consider while deploying SD-WAN. The key steps include using private networks, involving stakeholders, testing, and combining SD-WAN with SASE. Want to ace your presentation in front of a live audience Our Checklist To Implement Software Defined Wide Area Network Wide Area Network Services Ideas Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the checklist to implement a software-defined wide area network in an organization. The purpose of this slide is to highlight the various best practices that businesses should consider while deploying SD-WAN. The key steps include using private networks, involving stakeholders, testing, and combining SD-WAN with SASE.
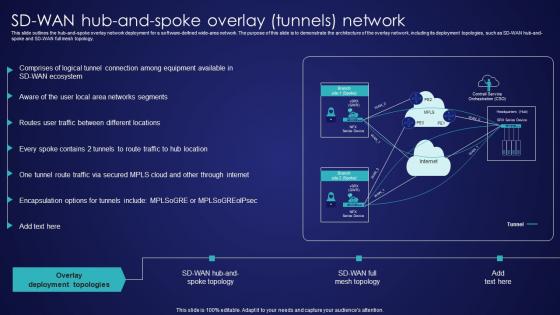
SD Wan Hub And Spoke Overlay Tunnels Network Wide Area Network Services Pictures Pdf
This slide outlines the hub-and-spoke overlay network deployment for a software-defined wide-area network. The purpose of this slide is to demonstrate the architecture of the overlay network, including its deployment topologies, such as SD-WAN hub-and-spoke and SD-WAN full mesh topology. Are you searching for a SD Wan Hub And Spoke Overlay Tunnels Network Wide Area Network Services Pictures Pdf that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SD Wan Hub And Spoke Overlay Tunnels Network Wide Area Network Services Pictures Pdf from Slidegeeks today. This slide outlines the hub-and-spoke overlay network deployment for a software-defined wide-area network. The purpose of this slide is to demonstrate the architecture of the overlay network, including its deployment topologies, such as SD-WAN hub-and-spoke and SD-WAN full mesh topology.

Key Facts E Commerce Logistics Management Funding Pitch Deck Graphics Pdf
The following slide showcases various statistics outlining a company overview that assists investors to gain an understanding of business performance. It consists of elements such as destination countries, courier partners, order fulfilment rate, on time delivery, order accuracy and return rate. Find highly impressive Key Facts E Commerce Logistics Management Funding Pitch Deck Graphics Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Key Facts E Commerce Logistics Management Funding Pitch Deck Graphics Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide showcases various statistics outlining a company overview that assists investors to gain an understanding of business performance. It consists of elements such as destination countries, courier partners, order fulfilment rate, on time delivery, order accuracy and return rate.
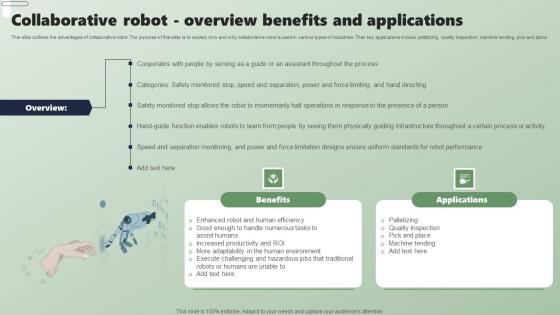
Collaborative Robot Overview Benefits Applications Of Industrial Robots Infographics Pdf
This slide outlines the advantages of collaborative robot. The purpose of this slide is to explain how and why collaborative robot is used in various types of industries. Their key applications include palletizing, quality inspection, machine tending, pick and place. Find highly impressive Collaborative Robot Overview Benefits Applications Of Industrial Robots Infographics Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Collaborative Robot Overview Benefits Applications Of Industrial Robots Infographics Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the advantages of collaborative robot. The purpose of this slide is to explain how and why collaborative robot is used in various types of industries. Their key applications include palletizing, quality inspection, machine tending, pick and place.
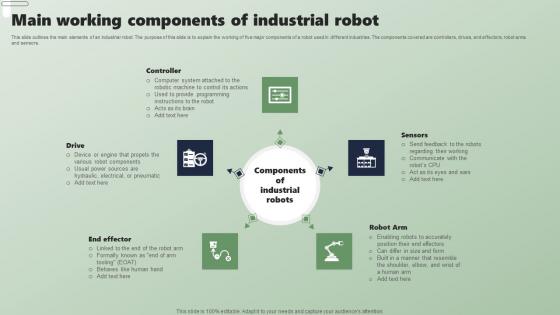
Main Working Components Of Industrial Robot Applications Of Industrial Robots Information Pdf
This slide outlines the main elements of an industrial robot. The purpose of this slide is to explain the working of five major components of a robot used in different industries. The components covered are controllers, drives, end effectors, robot arms and sensors. Are you searching for a Main Working Components Of Industrial Robot Applications Of Industrial Robots Information Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Main Working Components Of Industrial Robot Applications Of Industrial Robots Information Pdf from Slidegeeks today. This slide outlines the main elements of an industrial robot. The purpose of this slide is to explain the working of five major components of a robot used in different industries. The components covered are controllers, drives, end effectors, robot arms and sensors.
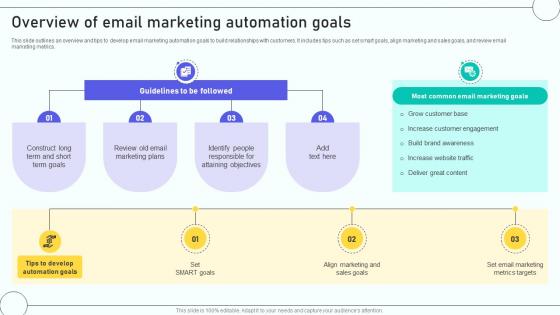
Email Marketing Automation Process Overview Of Email Marketing Automation
This slide outlines an overview and tips to develop email marketing automation goals to build relationships with customers. It includes tips such as set smart goals, align marketing and sales goals, and review email marketing metrics. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Email Marketing Automation Process Overview Of Email Marketing Automation to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Email Marketing Automation Process Overview Of Email Marketing Automation. This slide outlines an overview and tips to develop email marketing automation goals to build relationships with customers. It includes tips such as set smart goals, align marketing and sales goals, and review email marketing metrics.
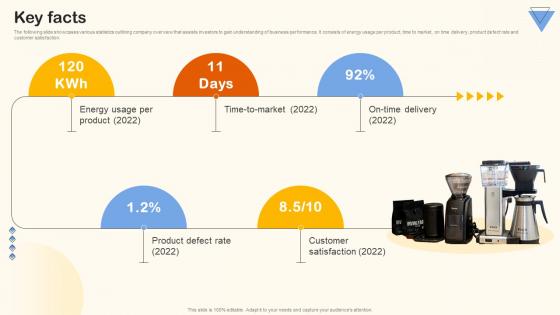
Key Facts Home Appliance Investor Funding Elevator Pitch Deck
The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of energy usage per product, time to market, on time delivery, product defect rate and customer satisfaction. Find highly impressive Key Facts Home Appliance Investor Funding Elevator Pitch Deck on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Key Facts Home Appliance Investor Funding Elevator Pitch Deck for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide showcases various statistics outlining company overview that assists investors to gain understanding of business performance. It consists of energy usage per product, time to market, on time delivery, product defect rate and customer satisfaction.

AIOT Platform 1 Overview And Key Services Offered AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase brief introduction to Microsoft Azure that offers various types of Artificial Intelligence of Things AIoT services. Azure IoT Hub, Azure IoT central, and Azure IoT edge are some of the major services that are outlined in slide along with projected cost of each service. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate AIOT Platform 1 Overview And Key Services Offered AIOT Applications For Various Industries IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The purpose of this slide is to showcase brief introduction to Microsoft Azure that offers various types of Artificial Intelligence of Things AIoT services. Azure IoT Hub, Azure IoT central, and Azure IoT edge are some of the major services that are outlined in slide along with projected cost of each service.
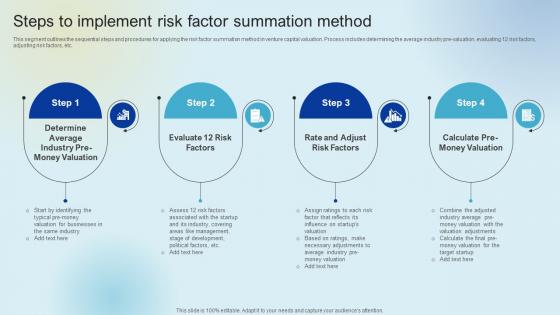
Steps To Implement Risk Factor Summation Raising Venture Capital A Holistic Approach Fin SS V
This segment outlines the sequential steps and procedures for applying the risk factor summation method in venture capital valuation. Process includes determining the average industry pre-valuation, evaluating 12 risk factors, adjusting risk factors, etc. Find highly impressive Steps To Implement Risk Factor Summation Raising Venture Capital A Holistic Approach Fin SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Steps To Implement Risk Factor Summation Raising Venture Capital A Holistic Approach Fin SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This segment outlines the sequential steps and procedures for applying the risk factor summation method in venture capital valuation. Process includes determining the average industry pre-valuation, evaluating 12 risk factors, adjusting risk factors, etc.

Top Valuation Methods For Raising Venture Capital A Holistic Approach Fin SS V
This slide outlines the most effective and commonly used valuation methods for startups seeking venture capital assisting entrepreneurs in determining the value of their business. The methods are market comparable method, scorecard valuation method, etc. Explore a selection of the finest Top Valuation Methods For Raising Venture Capital A Holistic Approach Fin SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Top Valuation Methods For Raising Venture Capital A Holistic Approach Fin SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the most effective and commonly used valuation methods for startups seeking venture capital assisting entrepreneurs in determining the value of their business. The methods are market comparable method, scorecard valuation method, etc.
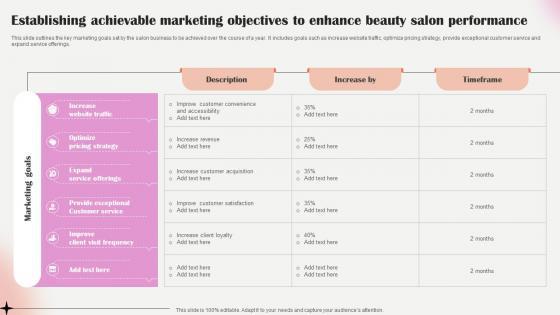
Salon Marketing Plan To Optimize Establishing Achievable Marketing Objectives Strategy SS V
This slide outlines the key marketing goals set by the salon business to be achieved over the course of a year. It includes goals such as increase website traffic, optimize pricing strategy, provide exceptional customer service and expand service offerings. Explore a selection of the finest Salon Marketing Plan To Optimize Establishing Achievable Marketing Objectives Strategy SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Salon Marketing Plan To Optimize Establishing Achievable Marketing Objectives Strategy SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the key marketing goals set by the salon business to be achieved over the course of a year. It includes goals such as increase website traffic, optimize pricing strategy, provide exceptional customer service and expand service offerings.

How To Create Cost Effective Facebook Ad Performance Benchmark By Strategy SS V
The following slide outlines Facebook advertisement performance across various industries such as fashion, auto insurance, business-to-business B2B, beauty, retail merchandising, information technology, etc. Marketers can set realistic expectation for ad performance and track progress by knowing ad performance benchmark criteria. Find highly impressive How To Create Cost Effective Facebook Ad Performance Benchmark By Strategy SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download How To Create Cost Effective Facebook Ad Performance Benchmark By Strategy SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide outlines Facebook advertisement performance across various industries such as fashion, auto insurance, business-to-business B2B, beauty, retail merchandising, information technology, etc. Marketers can set realistic expectation for ad performance and track progress by knowing ad performance benchmark criteria.
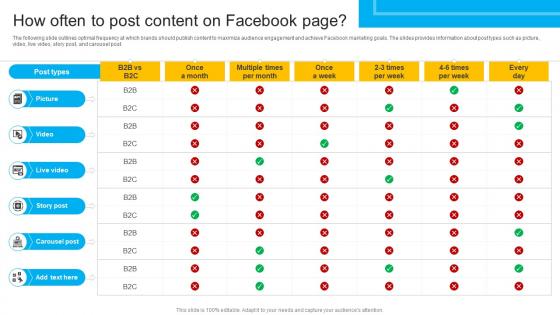
How To Create Cost Effective How Often To Post Content On Facebook Strategy SS V
The following slide outlines optimal frequency at which brands should publish content to maximize audience engagement and achieve Facebook marketing goals. The slides provides information about post types such as picture, video, live video, story post, and carousel post. Are you searching for a How To Create Cost Effective How Often To Post Content On Facebook Strategy SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download How To Create Cost Effective How Often To Post Content On Facebook Strategy SS V from Slidegeeks today. The following slide outlines optimal frequency at which brands should publish content to maximize audience engagement and achieve Facebook marketing goals. The slides provides information about post types such as picture, video, live video, story post, and carousel post.
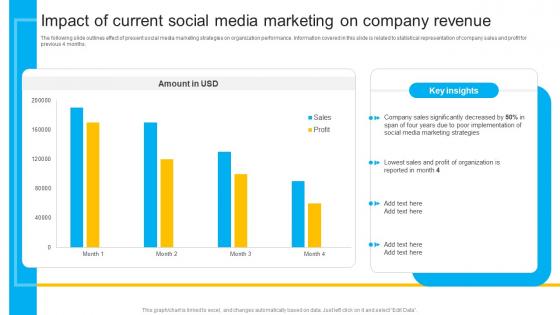
How To Create Cost Effective Impact Of Current Social Media Marketing Strategy SS V
The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download How To Create Cost Effective Impact Of Current Social Media Marketing Strategy SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the How To Create Cost Effective Impact Of Current Social Media Marketing Strategy SS V. The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months.

How To Create Cost Effective Types Of Facebook Ads To Drive Conversions Strategy SS V
The following slide outlines overview of different Facebook ads which can assist marketers in reaching target market, boost conversion rate and increases revenue. Information covered in this slide is related to image, video, and carousel ads along with major statistics. Find highly impressive How To Create Cost Effective Types Of Facebook Ads To Drive Conversions Strategy SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download How To Create Cost Effective Types Of Facebook Ads To Drive Conversions Strategy SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide outlines overview of different Facebook ads which can assist marketers in reaching target market, boost conversion rate and increases revenue. Information covered in this slide is related to image, video, and carousel ads along with major statistics.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Model Zero Trust Network Access System Use Cases
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Model Zero Trust Network Access System Use Cases that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Model Zero Trust Network Access System Use Cases from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.
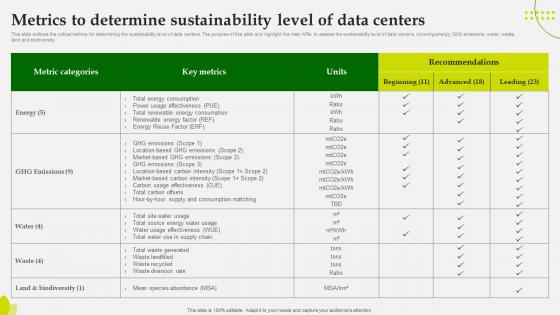
Green Computing Metrics To Determine Sustainability Level Of Data Centers
This slide outlines the critical metrics for determining the sustainability level of data centers. The purpose of this slide is to highlight the main KPIs to assess the sustainability level of datacenters, covering energy, GHS emissions, water, waste, land and biodiversity.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Green Computing Metrics To Determine Sustainability Level Of Data Centers to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Green Computing Metrics To Determine Sustainability Level Of Data Centers This slide outlines the critical metrics for determining the sustainability level of data centers. The purpose of this slide is to highlight the main KPIs to assess the sustainability level of datacenters, covering energy, GHS emissions, water, waste, land and biodiversity.
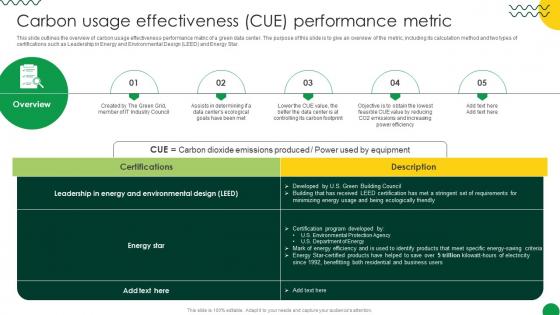
Sustainable Carbon Usage Effectiveness CUE Performance Metric
This slide outlines the overview of carbon usage effectiveness performance matric of a green data center. The purpose of this slide is to give an overview of the metric, including its calculation method and two types of certifications such as Leadership in Energy and Environmental Design LEED and Energy Star. Find highly impressive Sustainable Carbon Usage Effectiveness CUE Performance Metric on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Sustainable Carbon Usage Effectiveness CUE Performance Metric for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the overview of carbon usage effectiveness performance matric of a green data center. The purpose of this slide is to give an overview of the metric, including its calculation method and two types of certifications such as Leadership in Energy and Environmental Design LEED and Energy Star.

Sustainable Power Usage Effectiveness PUE Performance Metric
This slide outlines the power usage effectiveness performance metric of data center performance. The purpose of this slide is to showcase the methods to calculate the PUE of a data center and how it helps data center operators to reduce energy costs and improve the environmental impact of data center operations. Find highly impressive Sustainable Power Usage Effectiveness PUE Performance Metric on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Sustainable Power Usage Effectiveness PUE Performance Metric for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the power usage effectiveness performance metric of data center performance. The purpose of this slide is to showcase the methods to calculate the PUE of a data center and how it helps data center operators to reduce energy costs and improve the environmental impact of data center operations.
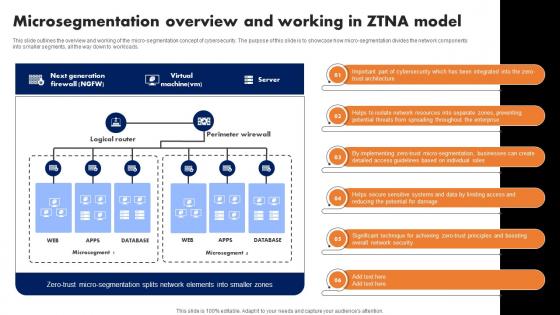
Microsegmentation Overview And Working In Ztna Model Software Defined Perimeter SDP
This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Explore a selection of the finest Microsegmentation Overview And Working In Ztna Model Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Microsegmentation Overview And Working In Ztna Model Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads.
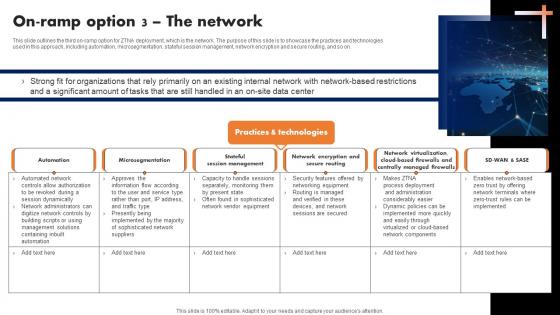
On Ramp Option 3 The Network Software Defined Perimeter SDP
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Are you searching for a On Ramp Option 3 The Network Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download On Ramp Option 3 The Network Software Defined Perimeter SDP from Slidegeeks today. This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on.

Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Want to ace your presentation in front of a live audience Our Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Zero Trust Network Access System Use Cases Software Defined Perimeter SDP
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Network Access System Use Cases Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access System Use Cases Software Defined Perimeter SDP from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.
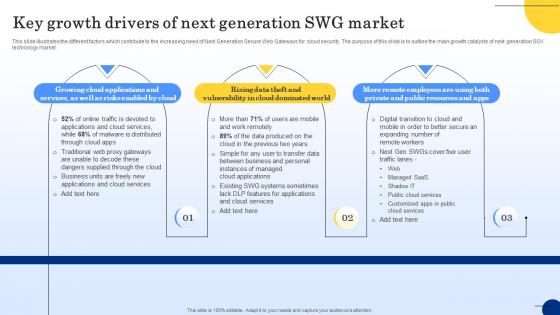
Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System
This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market. Explore a selection of the finest Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Growth Drivers Of Next Generation SWG Market Web Threat Protection System to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide illustrates the different factors which contribute to the increasing need of Next Generation Secure Web Gateways for cloud security. The purpose of this slide is to outline the main growth catalysts of next generation SGV technology market.

Facebook Marketing Plan Current Performance Of Social Media Marketing Strategy SS V
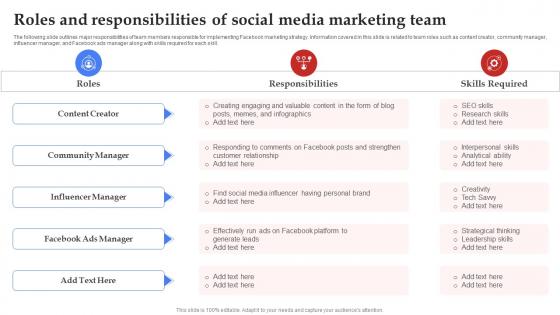
Facebook Marketing Plan For Ecommerce Roles And Responsibilities Of Social Strategy SS V

Facebook Marketing Plan Humorous Content Example To Boost Organic Strategy SS V
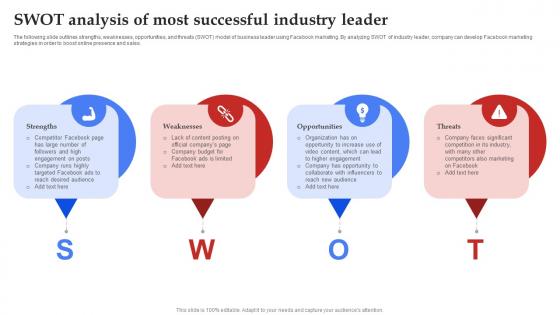
Facebook Marketing Plan Swot Analysis Of Most Successful Industry Leader Strategy SS V

Facebook Marketing Techniques Current Performance Of Social Media Marketing Strategy SS V
The following slide outlines current assessment of social media marketing platforms such as Instagram, Twitter, and YouTube. The monthly comparison is drawn on basis of new followers subscribers, customer engagement rate, reach, and conversion rate. Find highly impressive Facebook Marketing Techniques Current Performance Of Social Media Marketing Strategy SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Facebook Marketing Techniques Current Performance Of Social Media Marketing Strategy SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now The following slide outlines current assessment of social media marketing platforms such as Instagram, Twitter, and YouTube. The monthly comparison is drawn on basis of new followers subscribers, customer engagement rate, reach, and conversion rate.
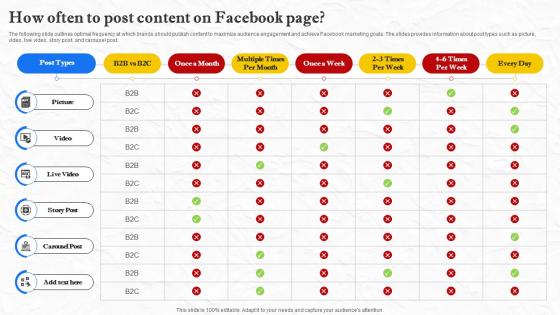
Facebook Marketing Techniques How Often To Post Content On Facebook Page Strategy SS V
The following slide outlines optimal frequency at which brands should publish content to maximize audience engagement and achieve Facebook marketing goals. The slides provides information about post types such as picture, video, live video, story post, and carousel post. Are you searching for a Facebook Marketing Techniques How Often To Post Content On Facebook Page Strategy SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Facebook Marketing Techniques How Often To Post Content On Facebook Page Strategy SS V from Slidegeeks today. The following slide outlines optimal frequency at which brands should publish content to maximize audience engagement and achieve Facebook marketing goals. The slides provides information about post types such as picture, video, live video, story post, and carousel post.
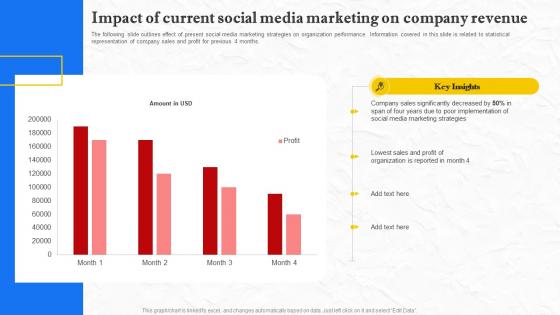
Facebook Marketing Techniques Impact Of Current Social Media Marketing Strategy SS V
The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Facebook Marketing Techniques Impact Of Current Social Media Marketing Strategy SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Facebook Marketing Techniques Impact Of Current Social Media Marketing Strategy SS V. The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months.
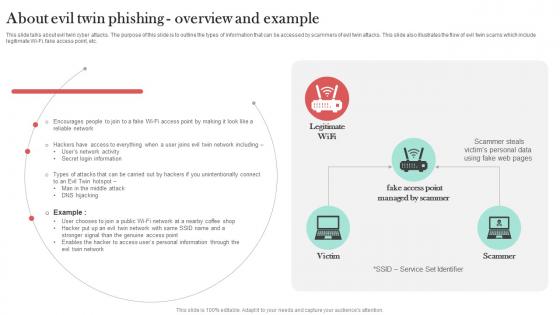
About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc.
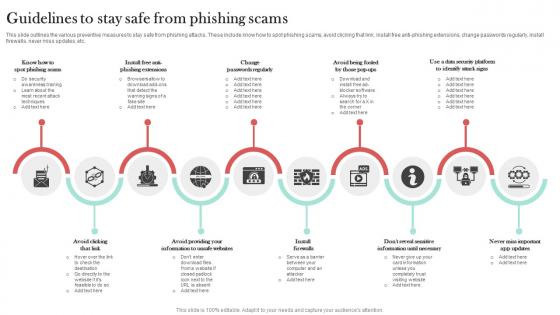
Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT
This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc. Explore a selection of the finest Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc.

Zero Trust Network Access Key Characteristics Of Modern ZTNA Solution
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access Key Characteristics Of Modern ZTNA Solution to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access Key Characteristics Of Modern ZTNA Solution. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.
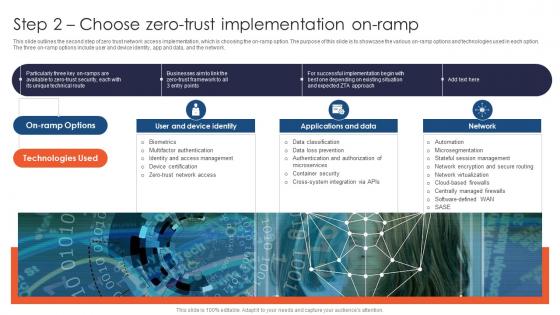
Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Find highly impressive Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Zero Trust Network Access Step 2 Choose Zero Trust Implementation On Ramp for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.
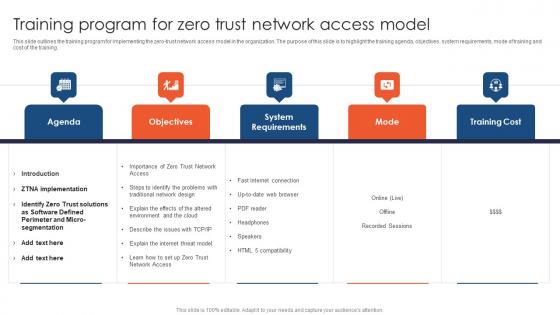
Zero Trust Network Access Training Program For Zero Trust Network Access Model
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Explore a selection of the finest Zero Trust Network Access Training Program For Zero Trust Network Access Model here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Training Program For Zero Trust Network Access Model to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

CASB 2 0 IT API Based Use Cases Of CASB Deployment
This slide outlines the use cases of API-based CASB deployment. This slide highlights the main use cases of API-based deployment of CASB deployment, including identifying malware in cloud services, implementing data transfer policies across different cloud services, auditing user access provisioning and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CASB 2 0 IT API Based Use Cases Of CASB Deployment for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the use cases of API-based CASB deployment. This slide highlights the main use cases of API-based deployment of CASB deployment, including identifying malware in cloud services, implementing data transfer policies across different cloud services, auditing user access provisioning and so on.

CASB 2 0 IT API Scanning CASB Deployment Model
This slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Want to ace your presentation in front of a live audience Our CASB 2 0 IT API Scanning CASB Deployment Model can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs.
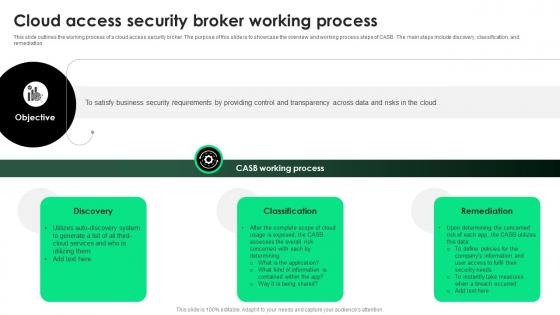
CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process. This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation.
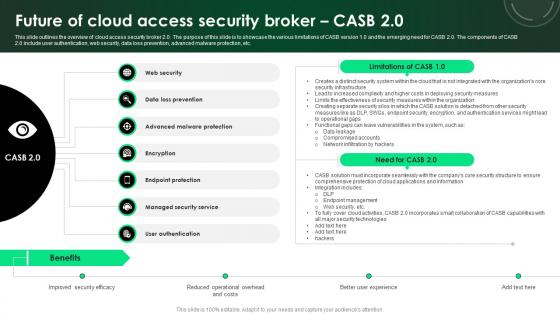
CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0
This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CASB 2 0 IT Future Of Cloud Access Security Broker CASB 2 0 for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide outlines the overview of cloud access security broker 2.0. The purpose of this slide is to showcase the various limitations of CASB version 1.0 and the emerging need for CASB 2.0. The components of CASB 2.0 include user authentication, web security, data loss prevention, advanced malware protection, etc.
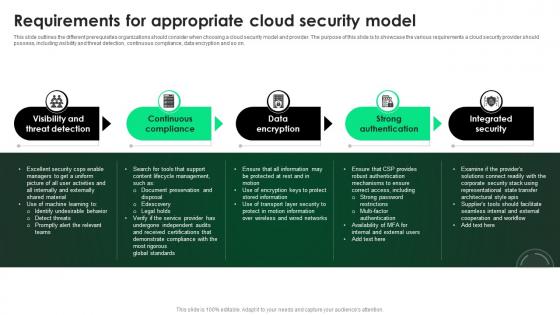
CASB 2 0 IT Requirements For Appropriate Cloud Security Model
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Find highly impressive CASB 2 0 IT Requirements For Appropriate Cloud Security Model on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CASB 2 0 IT Requirements For Appropriate Cloud Security Model for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on.

Timeline For Conducting Manual Testing In Organization Gray Box Testing Best Practices
This slide outlines the timeline for executing manual testing. The purpose of this slide is to showcase the different steps performed while implementing software testing, including preparation, strategy, test case design, and so on. Are you searching for a Timeline For Conducting Manual Testing In Organization Gray Box Testing Best Practices that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Timeline For Conducting Manual Testing In Organization Gray Box Testing Best Practices from Slidegeeks today. This slide outlines the timeline for executing manual testing. The purpose of this slide is to showcase the different steps performed while implementing software testing, including preparation, strategy, test case design, and so on.
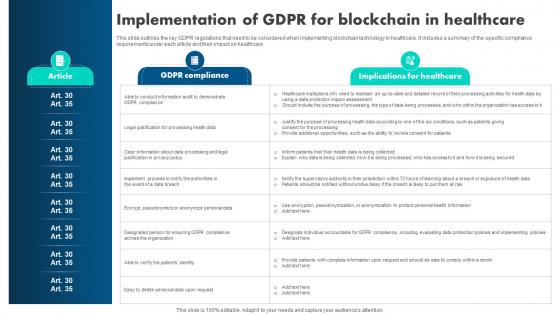
How Blockchain Is Reshaping Implementation Of GDPR For Blockchain In Healthcare BCT SS V
This slide outlines the key GDPR regulations that need to be considered when implementing blockchain technology in healthcare. It includes a summary of the specific compliance requirements under each article and their impact on healthcare. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download How Blockchain Is Reshaping Implementation Of GDPR For Blockchain In Healthcare BCT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the How Blockchain Is Reshaping Implementation Of GDPR For Blockchain In Healthcare BCT SS V. This slide outlines the key GDPR regulations that need to be considered when implementing blockchain technology in healthcare. It includes a summary of the specific compliance requirements under each article and their impact on healthcare.
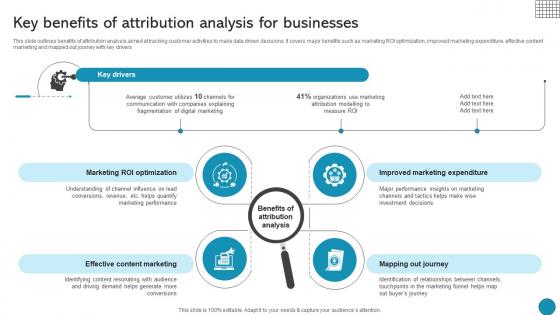
Key Benefits Of Attribution Analysis For Businesses Driving Business Success Integrating Product
This slide outlines benefits of attribution analysis aimed at tracking customer activities to make data driven decisions. It covers major benefits such as marketing ROI optimization, improved marketing expenditure, effective content marketing and mapped out journey with key drivers Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Key Benefits Of Attribution Analysis For Businesses Driving Business Success Integrating Product to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Key Benefits Of Attribution Analysis For Businesses Driving Business Success Integrating Product. This slide outlines benefits of attribution analysis aimed at tracking customer activities to make data driven decisions. It covers major benefits such as marketing ROI optimization, improved marketing expenditure, effective content marketing and mapped out journey with key drivers


 Continue with Email
Continue with Email

 Home
Home


































