Phishing Icon
Phishing Attacks Awareness Training Icon Designs PDF
Presenting Phishing Attacks Awareness Training Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Attacks Awareness, Training Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Email Phishing And Internet Security Icon Microsoft Pdf
Showcasing this set of slides titled Email Phishing And Internet Security Icon Microsoft Pdf The topics addressed in these templates are Email Phishing, Internet Security Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Email Phishing And Internet Security Icon Microsoft Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Phishing Attacks Awareness Training Program Icon Demonstration PDF
Presenting Phishing Attacks Awareness Training Program Icon Demonstration PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Attacks Awareness, Training Program Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Insider Threat Icon For Financial Information Phishing Mockup PDF
Presenting Insider Threat Icon For Financial Information Phishing Mockup PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Insider Threat Icon, Financial Information Phishing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Phishing Attacks Awareness Training For Employees Icon Clipart PDF
Presenting Phishing Attacks Awareness Training For Employees Icon Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing Attacks Awareness Training, Employees Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Phishing Scams And Attacks Icon To Steal Confidential Data Elements PDF
Showcasing this set of slides titled cyber phishing scams and attacks icon to steal confidential data elements pdf. The topics addressed in these templates are cyber phishing scams and attacks icon to steal confidential data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Phishing Incident Management Dashboard For Attacks Awareness Training Icons PDF
This slide covers phishing incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Pitch your topic with ease and precision using this Phishing Incident Management Dashboard For Attacks Awareness Training Icons PDF. This layout presents information on Phishing Incident Management Dashboard, Attacks Awareness Training. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF
Pitch your topic with ease and precision using this Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF. This layout presents information on Phishing Cyber Securit, Attack Unprotected, Web Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icon Of Hacker Launching Cyber Phishing Scams And Attacks Background PDF
Presenting icon of hacker launching cyber phishing scams and attacks background pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including icon of hacker launching cyber phishing scams and attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icons Slide For Man In The Middle Phishing IT Ppt Infographics
Retrieve professionally designed Icons Slide For Man In The Middle Phishing IT Ppt Infographics to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. Our Icons Slide For Man In The Middle Phishing IT Ppt Infographics are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
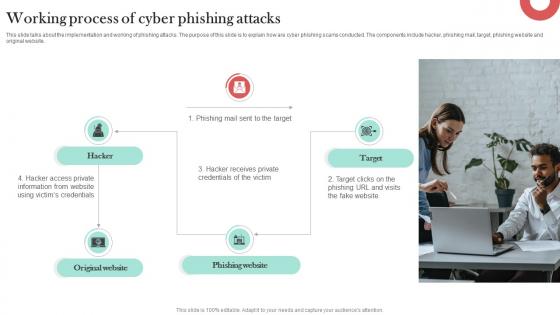
Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT
This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website. Do you know about Slidesgeeks Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website.
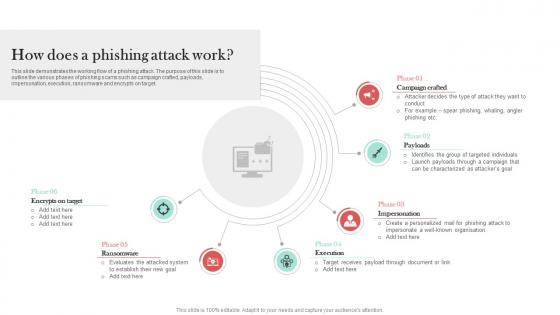
How Does A Phishing Attack Work Man In The Middle Phishing IT
This slide demonstrates the working flow of a phishing attack. The purpose of this slide is to outline the various phases of phishing scams such as campaign crafted, payloads, impersonation, execution, ransomware and encrypts on target. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download How Does A Phishing Attack Work Man In The Middle Phishing IT from Slidegeeks and deliver a wonderful presentation. This slide demonstrates the working flow of a phishing attack. The purpose of this slide is to outline the various phases of phishing scams such as campaign crafted, payloads, impersonation, execution, ransomware and encrypts on target.
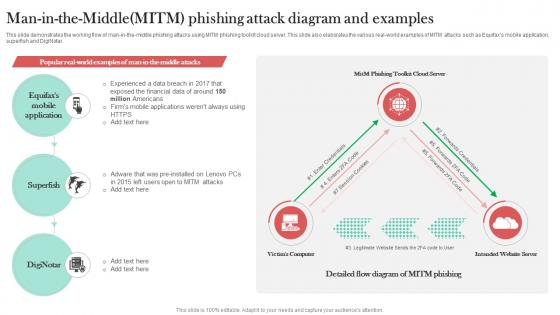
Man In The Middlemitm Phishing Attack Man In The Middle Phishing IT
This slide demonstrates the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server. This slide also elaborates the various real-world examples of MITM attacks such as Equifaxs mobile application, superfish and DigiNotar. Do you know about Slidesgeeks Man In The Middlemitm Phishing Attack Man In The Middle Phishing IT These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide demonstrates the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server. This slide also elaborates the various real-world examples of MITM attacks such as Equifaxs mobile application, superfish and DigiNotar.
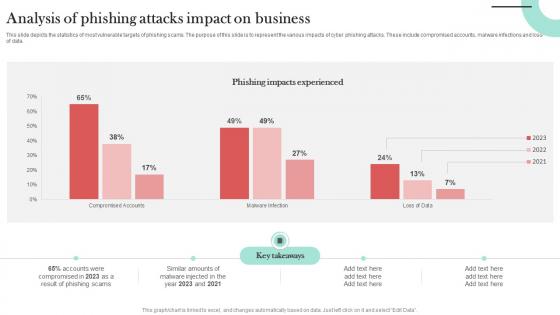
Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT
This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. If you are looking for a format to display your unique thoughts, then the professionally designed Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data.
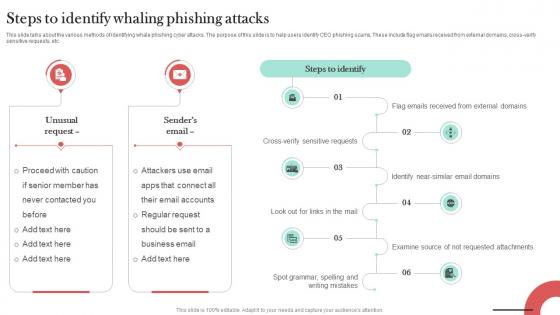
Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT
This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc.
Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT
This slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT This slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk.
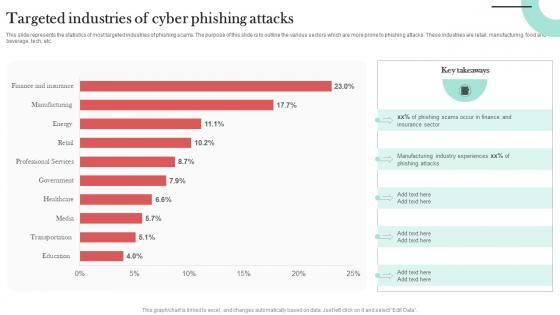
Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT
This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc.
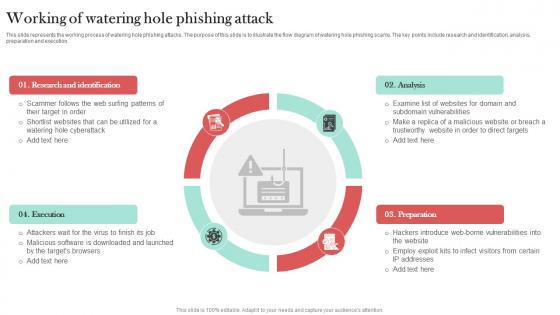
Working Of Watering Hole Phishing Attack Man In The Middle Phishing IT
This slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. This Working Of Watering Hole Phishing Attack Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution.

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names.

Key Techniques In Phishing Attacks Awareness Training Program Themes PDF
This slide covers strategies to consider in phishing awareness training program. It involves strategies such as verify email address, consider every email as phishing attempt and update security software. Presenting Key Techniques In Phishing Attacks Awareness Training Program Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Implement, Secure Network Connectivity, Payment Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Statistics Of Cyber Phishing Scams And Attacks Designs PDF
Mentioned slide showcases key facts of cyber phishing attack. The facts covered in the slide are loss of confidential data, compromised accounts, ransomware attacks, financial loss and other malware attacks such as trojans. Pitch your topic with ease and precision using this major statistics of cyber phishing scams and attacks designs pdf. This layout presents information on major statistics of cyber phishing scams and attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
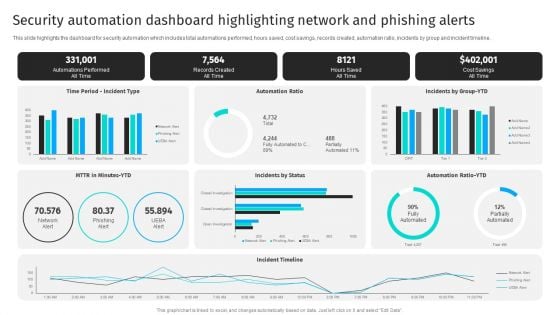
Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Best Practices For Phishing Attacks Awareness Training Topics PDF
This slide covers best practices for phishing awareness training plan for successful implementation. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting Best Practices For Phishing Attacks Awareness Training Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Getting Into Compliance, Establishing Basics, Including Everyone. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phishing Attacks Awareness Training Program Process Brochure PDF
This slide covers phishing awareness training program and development procedure to ensure effectiveness. It involves steps such as identify training need, determine type of training, identify goals and objectives, implement and evaluate program. Presenting Phishing Attacks Awareness Training Program Process Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Training Need, Evaluate Training Program, Identify Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
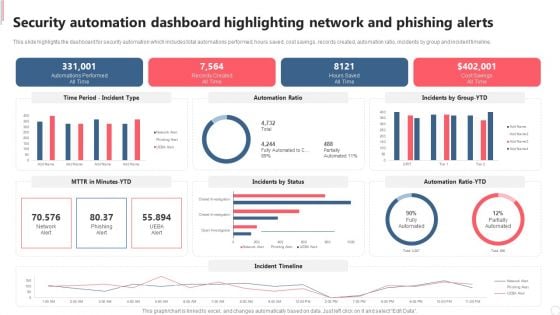
Security Automation Dashboard Highlighting Network And Phishing Alerts Demonstration PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Welcome to our selection of the Security Automation Dashboard Highlighting Network And Phishing Alerts Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. This modern and well arranged Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Phishing Attacks Awareness Training Ppt PowerPoint Presentation Complete With Slides
Share a great deal of information on the topic by deploying this Phishing Attacks Awareness Training Ppt PowerPoint Presentation Complete With Slides. Support your ideas and thought process with this prefabricated set. It includes a set of seventeen slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Man In The Middle Phishing IT Ppt Powerpoint Presentation Complete Deck With Slides
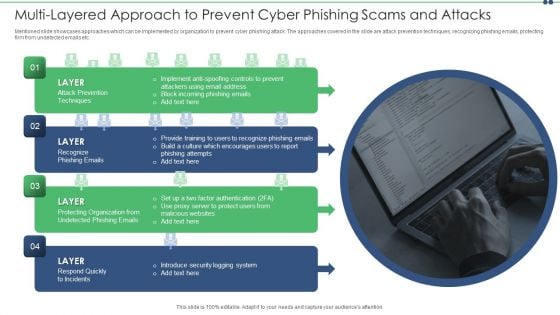
Multi Layered Approach To Prevent Cyber Phishing Scams And Attacks Themes PDF
Mentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting multi layered approach to prevent cyber phishing scams and attacks themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including email, implement, system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Phishing Scams And Attacks Dashboard With Improvement Curve Sample PDF
Mentioned slide showcases a comprehensive dashboard used to measure the cyber phishing attacks. Information covered in this slide is related to organization health risk, attack vendors, most vulnerable employees to attacks, improvement curve. Pitch your topic with ease and precision using this cyber phishing scams and attacks dashboard with improvement curve sample pdf. This layout presents information on cyber phishing scams and attacks dashboard with improvement curve. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
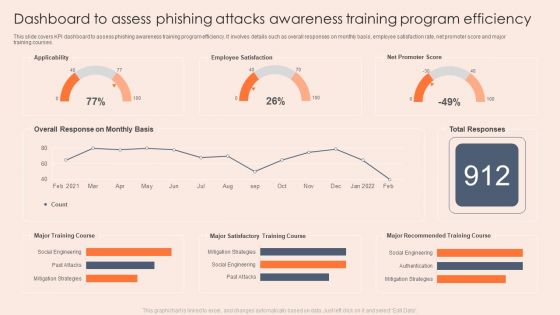
Dashboard To Assess Phishing Attacks Awareness Training Program Efficiency Professional PDF
This slide covers KPI dashboard to assess phishing awareness training program efficiency. It involves details such as overall responses on monthly basis, employee satisfaction rate, net promoter score and major training courses. Showcasing this set of slides titled Dashboard To Assess Phishing Attacks Awareness Training Program Efficiency Professional PDF. The topics addressed in these templates are Applicability, Employee Satisfaction, Mitigation Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

5 Key Practices To Prevent Cyber Phishing Scams And Attacks Graphics PDF
Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. The practices are recognizing hyperlinks attached in an email, backup system copies, secure robust HTTPs connections, installing a firewall and using anti spam tools. Presenting 5 key practices to prevent cyber phishing scams and attacks graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including secure, device, reduced. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Why Phishing Attacks Awareness Training Is Essential For Employees Clipart PDF
This slide covers need of phishing awareness training within organization. It involves reasons such as increases employee awareness, assures educated staff, enhances organizational reputation and boosts confidence. Presenting Why Phishing Attacks Awareness Training Is Essential For Employees Clipart PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assures Staff Education, Enhances Organizational Reputation, Boosts Confidence. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT
This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam, LuckyMouse scam, International Civil Aviation OrganizationICAO scam, Ccleaner scam and Holy Water scam. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam, LuckyMouse scam, International Civil Aviation OrganizationICAO scam, Ccleaner scam and Holy Water scam.
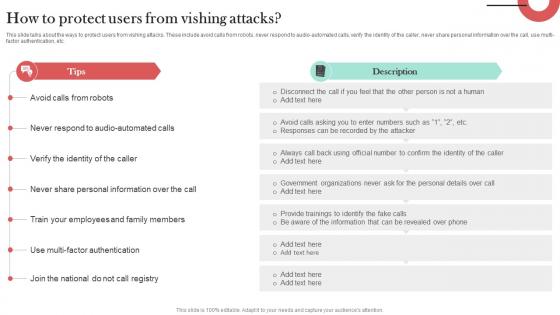
How To Protect Users From Vishing Attacks Man In The Middle Phishing IT
This slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc. Are you searching for a How To Protect Users From Vishing Attacks Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download How To Protect Users From Vishing Attacks Man In The Middle Phishing IT from Slidegeeks today. This slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc.
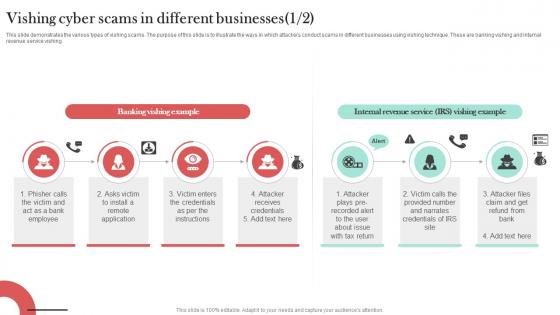
Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT
This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing. Are you searching for a Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Vishing Cyber Scams In Different Businesses Man In The Middle Phishing IT from Slidegeeks today. This slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing.
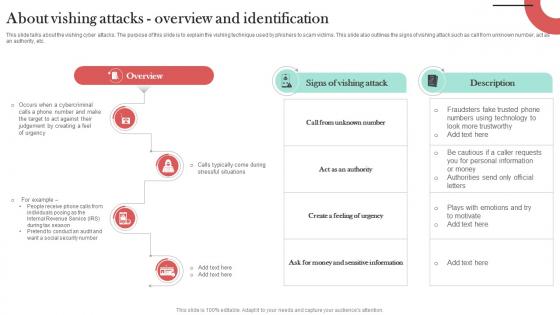
About Vishing Attacks Overview And Identification Man In The Middle Phishing IT
This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Vishing Attacks Overview And Identification Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using About Vishing Attacks Overview And Identification Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc.

Cyber Phishing Scams And Attacks Ppt PowerPoint Presentation Complete With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cyber phishing scams and attacks ppt powerpoint presentation complete with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the fourteen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
Info Security Managing Information Security 30 Days Plan Ppt PowerPoint Presentation Icon Show PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative info security managing information security 30 days plan ppt powerpoint presentation icon show pdf bundle. Topics like phishing aware, phishing reporting, phishing repeat offenders, facility physical security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Icons PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach icons pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like, frequent malware attacks and lack of awareness among employees.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF bundle. Topics like Frequent Malware, Phishing Attacks, Ransomware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Percent Of Risk Events Occurred Over Last Two Years Icons PDF bundle. Topics like Technical Failures, Phishing Emails, Data Breaching can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF
This slide represents 3 year cyber security plan road map of a company for website enhancement and implementing security to operational work with specific standards. It consists security standards, training and awareness phishing users and sensitive data management. Showcasing this set of slides titled Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF. The topics addressed in these templates are Website Enhancement, Governance Subcommittee, Security Standards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Impact Of Trojan Virus On Mobile Banking Ppt Icon Background Designs PDF
This slide shows information regarding banking trojans which can be used to understand meaning and impact of trojan virus. It also includes key channels used to spread banking trojan which are phishing emails, rogue websites and phone mobile apps. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Impact Of Trojan Virus On Mobile Banking Ppt Icon Background Designs PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Impact Of Trojan Virus On Mobile Banking Ppt Icon Background Designs PDF today and make your presentation stand out from the rest.
Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF
This slide showcases risk and threats landscape which can be referred by businesses to be aware of cybersecurity issues and attacks. It contains information about phishing, malware and blackmail hacking. Presenting Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing, Malware, Blackmail Hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring Security Awareness Campaign Icons PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring Security Awareness Campaign Icons PDF from Slidegeeks and deliver a wonderful presentation.
Threats Affecting Infra Cyber Security In Market Icons PDF
The following slide showcases threats in infrastructure security which can cause electrical blackouts, breaches of national secrets, etc. It presents information related to phishing, ransomware, botnets, etc. Presenting Threats Affecting Infra Cyber Security In Market Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Phishing, Ransomware, Botnets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
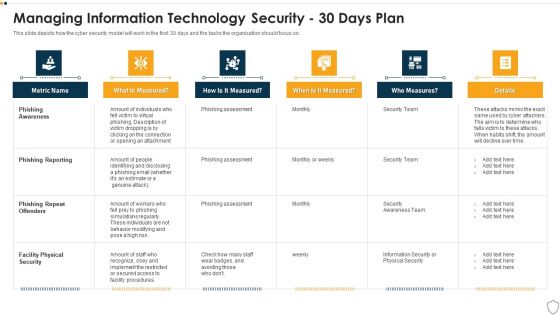
IT Security Managing Information Technology Security 30 Days Plan Themes PDF
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 30 days plan themes pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
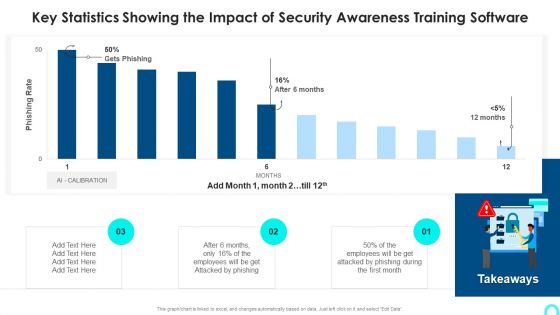
Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF
Deliver an awe inspiring pitch with this creative Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF bundle. Topics like Attacked Phishing, Employees Will, Phishing During can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
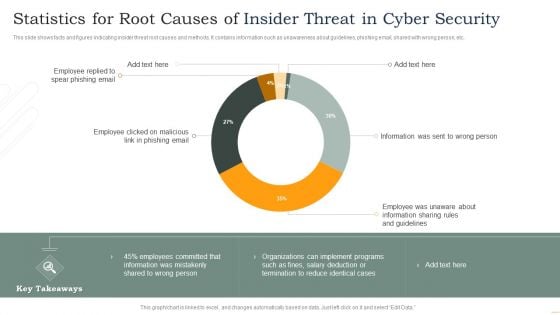
Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF
This slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Persuade your audience using this IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Attack Vector, Examples, Objective Problem Identifier. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach professional pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
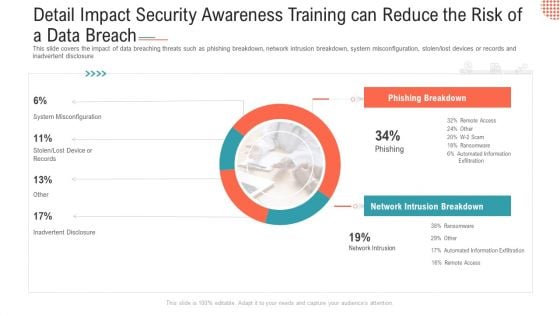
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Layouts Examples PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach ppt layouts examples pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Information PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach information pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
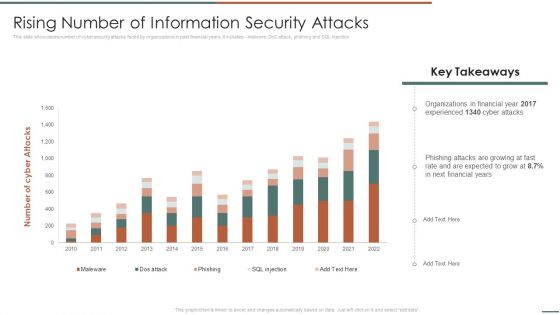
Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF. Use them to share invaluable insights on Organizations In Financial, Experienced, Phishing Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
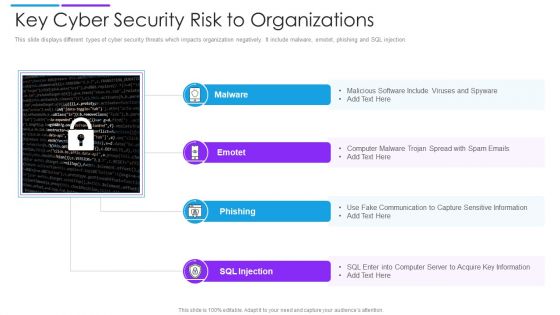
Key Cyber Security Risk To Organizations Structure PDF
This slide displays different types of cyber security threats which impacts organization negatively. It include malware, emotet, phishing and SQL injection. Presenting key cyber security risk to organizations structure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including malware, phishing, sql injection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Leveraging Ai To Tackle Banking Fraudulent Activities Artificial Intelligence Applications Icons Pdf
This slide showcases key fraudulent activities faced by banking institutions and solutions to tackle them through AI models. Key frauds faced by banking institutions are email phishing, identity theft, credit card theft and documents fogery.This Leveraging Ai To Tackle Banking Fraudulent Activities Artificial Intelligence Applications Icons Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases key fraudulent activities faced by banking institutions and solutions to tackle them through AI models. Key frauds faced by banking institutions are email phishing, identity theft, credit card theft and documents fogery.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
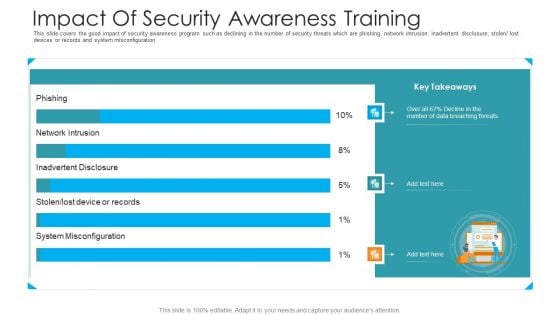
Impact Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Infographics PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe inspiring pitch with this creative impact of security awareness training hacking prevention awareness training for it security infographics pdf bundle. Topics like system misconfiguration, network intrusion breakdown, phishing breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































