Privacy Security
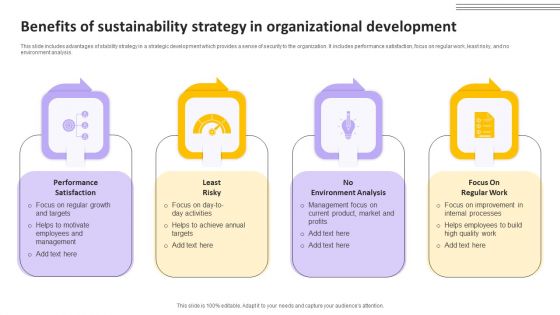
Benefits Of Sustainability Strategy In Organizational Development Background PDF
This slide includes advantages of stability strategy in a strategic development which provides a sense of security to the organization. It includes performance satisfaction, focus on regular work, least risky, and no environment analysis. Presenting Benefits Of Sustainability Strategy In Organizational Development Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Performance Satisfaction, Least Risky, No Environment Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
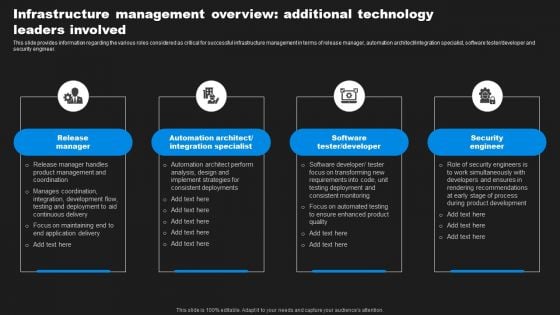
Enhancing Information Technology With Strategic Infrastructure Management Technology Guidelines PDF
This slide provides information regarding the various roles considered as critical for successful infrastructure management in terms of release manager, automation architect integration specialist, software tester developer and security engineer. Make sure to capture your audiences attention in your business displays with our gratis customizable Enhancing Information Technology With Strategic Infrastructure Management Technology Guidelines PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
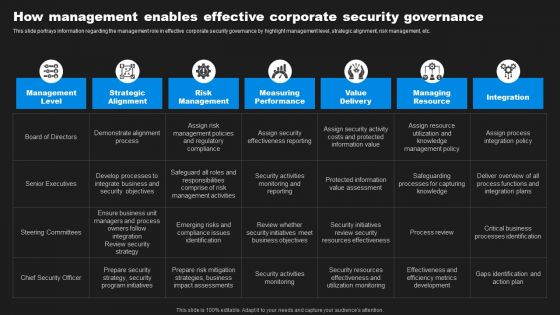
Enhancing Information Technology With Strategic How Management Enables Effective Summary PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Get a simple yet stunning designed Enhancing Information Technology With Strategic How Management Enables Effective Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Enhancing Information Technology With Strategic How Management Enables Effective Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
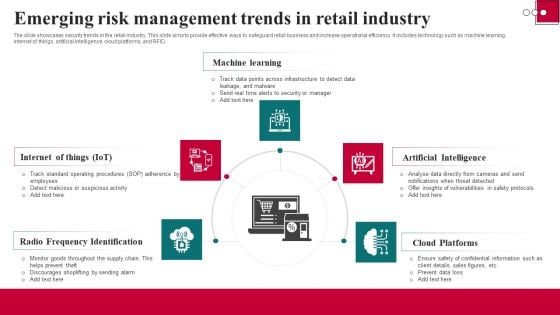
Emerging Risk Management Trends In Retail Industry Background PDF
The slide showcases security trends in the retail industry. This slide aims to provide effective ways to safeguard retail business and increase operational efficiency. It includes technology such as machine learning, internet of things, artificial intelligence, cloud platforms, and RFID. Persuade your audience using this Emerging Risk Management Trends In Retail Industry Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Radio Frequency Identification, Artificial Intelligence, Cloud Platforms. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Implementation Of Digital Advancement Techniques Essential Personnel Required Pictures PDF
The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists. There are so many reasons you need a Implementation Of Digital Advancement Techniques Essential Personnel Required Pictures PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
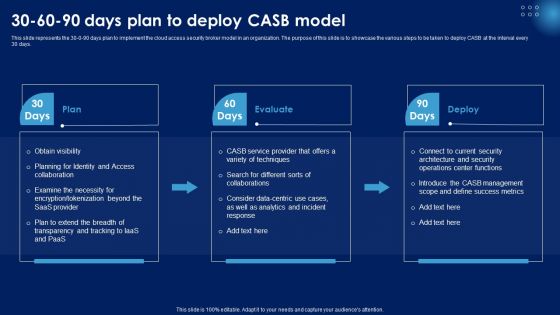
30 60 90 Days Plan To Deploy CASB Model Ppt PowerPoint Presentation File Infographics PDF
This slide represents the 30-0-90 days plan to implement the cloud access security broker model in an organization. The purpose of this slide is to showcase the various steps to be taken to deploy CASB at the interval every 30 days. Find a pre designed and impeccable 30 60 90 Days Plan To Deploy CASB Model Ppt PowerPoint Presentation File Infographics PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Comparison Between CASB And Data Loss Prevention DLP Ppt PowerPoint Presentation File Portfolio PDF
This slide describes the difference between cloud access security broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Comparison Between CASB And Data Loss Prevention DLP Ppt PowerPoint Presentation File Portfolio PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
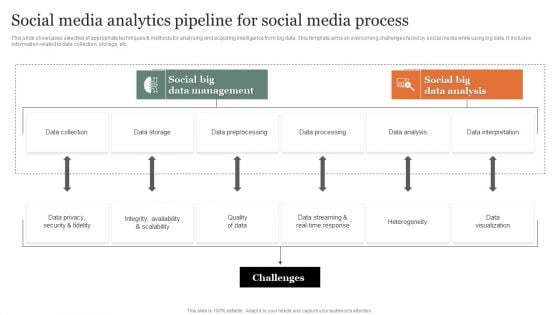
Social Media Analytics Pipeline For Social Media Process Slides PDF
This slide showcases selection of appropriate techniques and methods for analysing and acquiring intelligence from big data. This template aims on overcoming challenges faced by social media while using big data. It includes information related to data collection, storage, etc. Pitch your topic with ease and precision using thisSocial Media Analytics Pipeline For Social Media Process Slides PDF Inspiration. This layout presents information on Data Collection, Data Preprocessing, Security And Fidelity. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
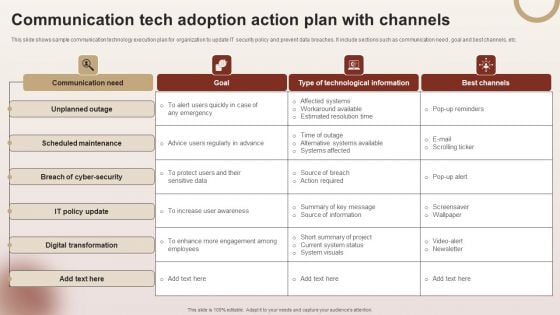
Communication Tech Adoption Action Plan With Channels Ideas PDF
This slide shows sample communication technology execution plan for organization to update IT security policy and prevent data breaches. It include sections such as communication need , goal and best channels, etc. Showcasing this set of slides titled Communication Tech Adoption Action Plan With Channels Ideas PDF. The topics addressed in these templates are Goal, Technological Information, Best Channels. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
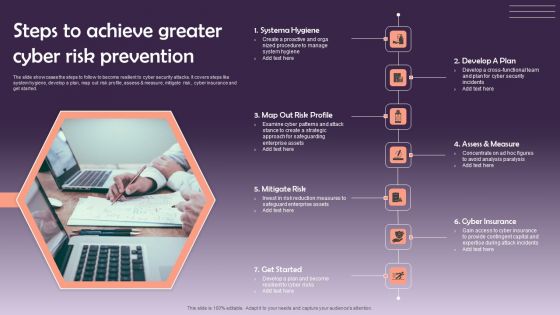
Steps To Achieve Greater Cyber Risk Prevention Infographics PDF
The slide showcases the steps to follow to become resilient to cyber security attacks. It covers steps like system hygiene, develop a plan, map out risk profile, assess and measure, mitigate risk, cyber insurance and get started. Presenting Steps To Achieve Greater Cyber Risk Prevention Infographics PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Systema Hygiene, Develop A Plan, Mitigate Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
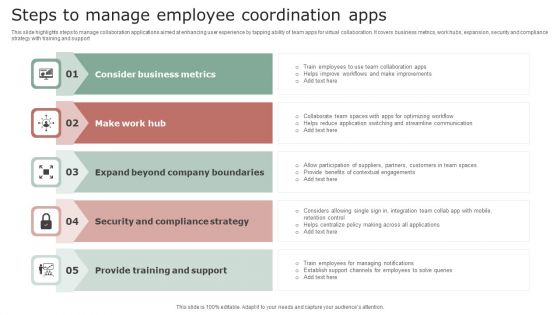
Steps To Manage Employee Coordination Apps Clipart PDF
This slide highlights steps to manage collaboration applications aimed at enhancing user experience by tapping ability of team apps for virtual collaboration. It covers business metrics, work hubs, expansion, security and compliance strategy with training and support. Presenting Steps To Manage Employee Coordination Apps Clipart PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Consider Business Metrics, Make Work Hub, Expand Beyond Company. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
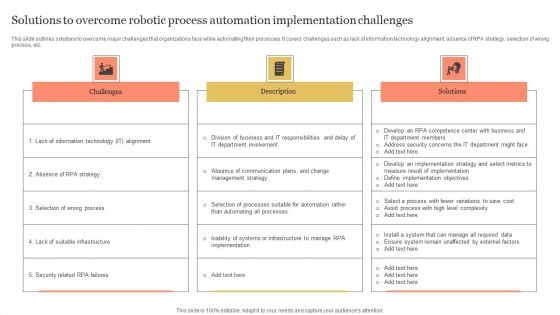
Solutions To Overcome Robotic Process Automation Implementation Challenges Topics PDF
This slide outlines solutions to overcome major challenges that organizations face while automating their processes. It covers challenges such as lack of information technology alignment, absence of RPA strategy, selection of wrong process, etc. Showcasing this set of slides titled Solutions To Overcome Robotic Process Automation Implementation Challenges Topics PDF. The topics addressed in these templates are Absence RPA Strategy, Selection Wrong Process, Security Related RPA Failures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
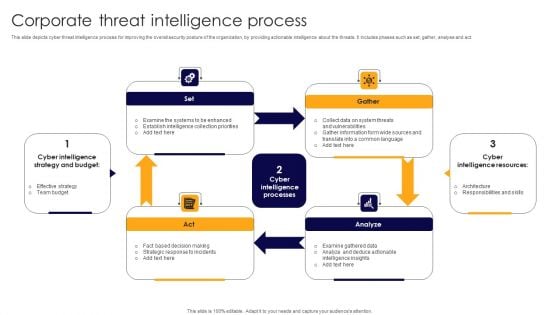
Corporate Threat Intelligence Process Demonstration PDF
This slide depicts cyber threat intelligence process for improving the overall security posture of the organization, by providing actionable intelligence about the threats. It includes phases such as set, gather, analyse and act. Presenting Corporate Threat Intelligence Process Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Fact Based Decision Making, Strategic Response Incidents, Collect Data System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
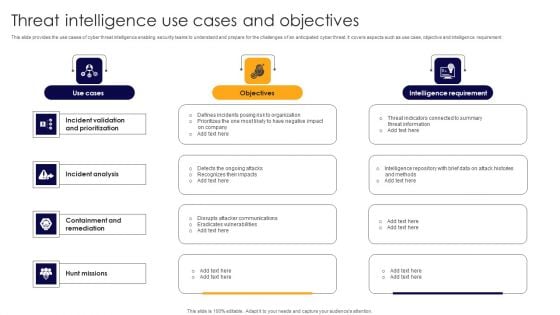
Threat Intelligence Use Cases And Objectives Demonstration PDF
This slide provides the use cases of cyber threat intelligence enabling security teams to understand and prepare for the challenges of an anticipated cyber threat. It covers aspects such as use case, objective and intelligence requirement. Presenting Threat Intelligence Use Cases And Objectives Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Analysis, Containment Remediation, Hunt Missions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Use Case Of Online Risk Management For Health Care Sector Background PDF
This slide represents a use case of digital risk management in health care sector to understand its impact. It includes components like goal, issues faced by hospital, risk mitigation action steps and result. Presenting Use Case Of Online Risk Management For Health Care Sector Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Threats, Risk Mitigation Action Steps, Results. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
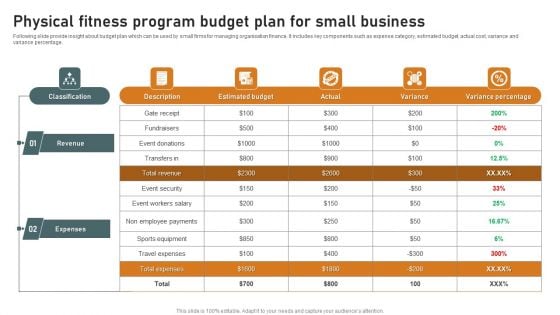
Physical Fitness Program Budget Plan For Small Business Guidelines PDF
Following slide provide insight about budget plan which can be used by small firms for managing organisation finance. It includes key components such as expense category, estimated budget, actual cost, variance and variance percentage. Showcasing this set of slides titled Physical Fitness Program Budget Plan For Small Business Guidelines PDF. The topics addressed in these templates are Revenue, Expenses, Event Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
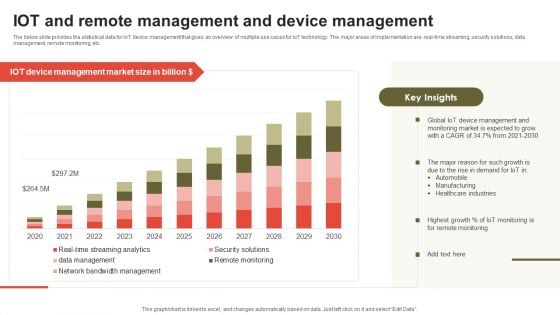
IOT And Remote Management And Device Management Brochure PDF
The below slide provides the statistical data for IoT device management that gives an overview of multiple use cases for IoT technology. The major areas of implementation are real-time streaming, security solutions, data management, remote monitoring, etc. Showcasing this set of slides titled IOT And Remote Management And Device Management Brochure PDF. The topics addressed in these templates are Automobile, Manufacturing, Healthcare Industries. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
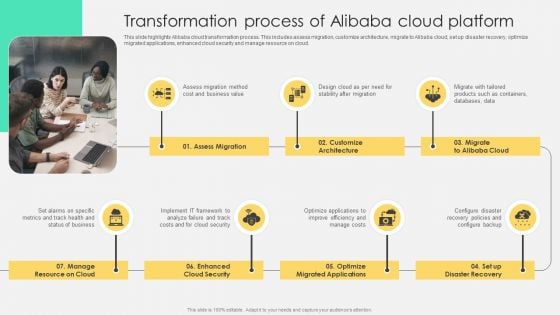
Transformation Process Of Alibaba Cloud Platform Introduction PDF
This slide highlights Alibaba cloud transformation process. This includes assess migration, customize architecture, migrate to Alibaba cloud, set up disaster recovery, optimize migrated applications, enhanced cloud security and manage resource on cloud. Find a pre-designed and impeccable Transformation Process Of Alibaba Cloud Platform Introduction PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
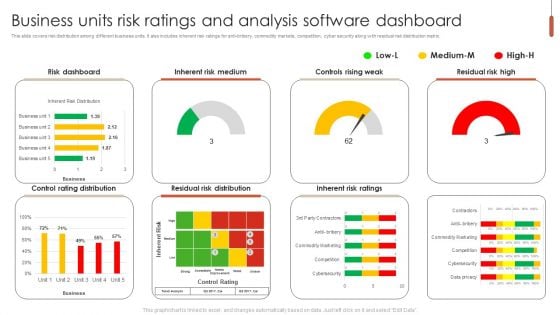
Business Units Risk Ratings And Analysis Software Dashboard Ideas PDF
This slide covers risk distribution among different business units. It also includes inherent risk ratings for anti-bribery, commodity markets, competition, cyber security along with residual risk distribution matrix. Pitch your topic with ease and precision using this Business Units Risk Ratings And Analysis Software Dashboard Ideas PDF. This layout presents information on Risk Dashboard, Inherent Risk Medium, Controls Rising Weak. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
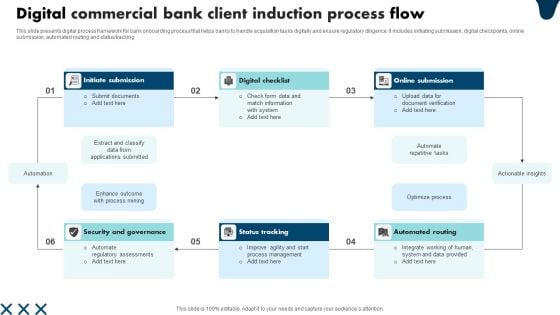
Digital Commercial Bank Client Induction Process Flow Background PDF
This slide presents digital process framework for bank onboarding process that helps banks to handle acquisition tasks digitally and ensure regulatory diligence. It includes initiating submission, digital checkpoints, online submission, automated routing and status tracking. Presenting Digital Commercial Bank Client Induction Process Flow Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security And Governance, Status Tracking, Automated Routing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Project Risk Optimization Strategic Approaches Formats PDF
This slide comprises different ways to assess portfolio risk in order to make asset allocation and security selection decisions. Some of the best practices include portfolio standard deviation, shortfall risk, tracking error, Sharpe ratio, and beta. Persuade your audience using this Project Risk Optimization Strategic Approaches Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Portfolio Standard Deviation, Shortfall Risk, Tracking Error. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
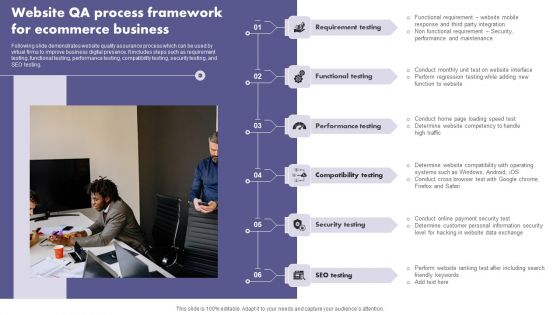
Website QA Process Framework For Ecommerce Business Brochure PDF
Following slide demonstrates website quality assurance process which can be used by virtual firms to improve business digital presence. It includes steps such as requirement testing, functional testing, performance testing, compatibility testing, security testing, and SEO testing. Presenting Website QA Process Framework For Ecommerce Business Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Compatibility Testing, Performance Testing, Functional Testing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
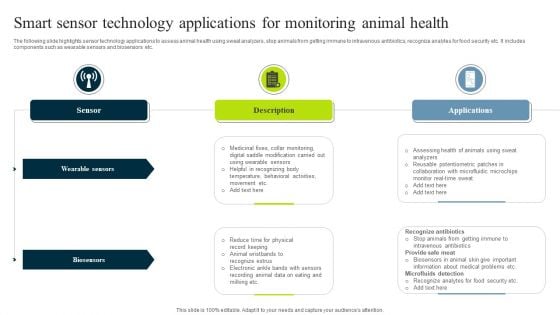
Smart Sensor Technology Applications For Monitoring Animal Health Clipart PDF
The following slide highlights sensor technology applications to assess animal health using sweat analyzers, stop animals from getting immune to intravenous antibiotics, recognize analytes for food security etc. It includes components such as wearable sensors and biosensors etc. Persuade your audience using this Smart Sensor Technology Applications For Monitoring Animal Health Clipart PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Wearable Sensors, Biosensors, Description. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
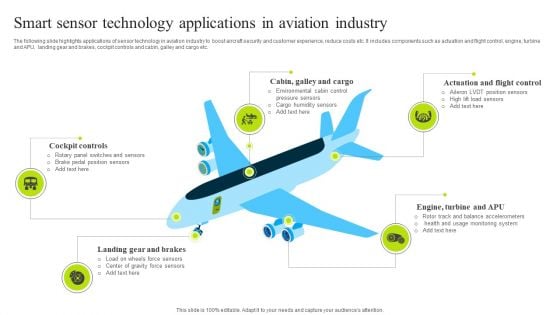
Smart Sensor Technology Applications In Aviation Industry Introduction PDF
The following slide highlights applications of sensor technology in aviation industry to boost aircraft security and customer experience, reduce costs etc. It includes components such as actuation and flight control, engine, turbine and APU, landing gear and brakes, cockpit controls and cabin, galley and cargo etc. Presenting Smart Sensor Technology Applications In Aviation Industry Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Cockpit Controls, Brakes, Industry. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Benefits Of Choosing Decoupled Over Non Decoupled CMS Diagrams PDF
The slide showcases the benefits associated with choosing a headless content management system over a non-headless CMS. It compares on the basis of parameters like priority, time efficiency, freedom and flexibility, security and scalability. Showcasing this set of slides titled Business Benefits Of Choosing Decoupled Over Non Decoupled CMS Diagrams PDF. The topics addressed in these templates are Priority, Time Efficiency, Freedom Flexibility. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
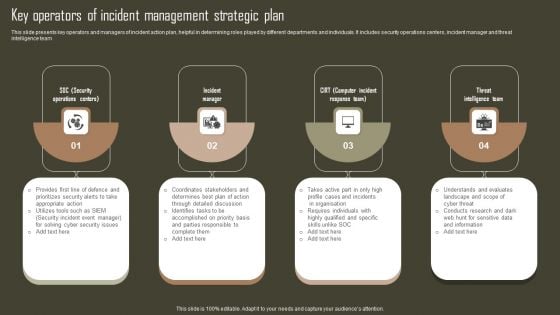
Key Operators Of Incident Management Strategic Plan Professional PDF
This slide presents key operators and managers of incident action plan, helpful in determining roles played by different departments and individuals. It includes security operations centers, incident manager and threat intelligence team. Presenting Key Operators Of Incident Management Strategic Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Manager, Threat Intelligence Team, Sensitive Data And Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
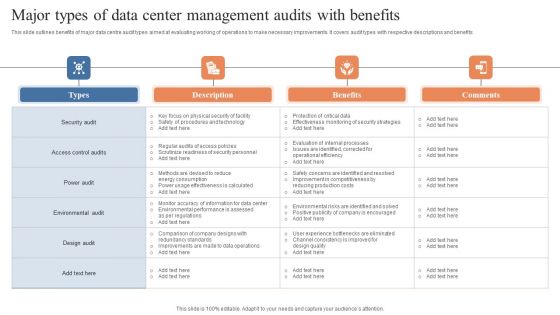
Major Types Of Data Center Management Audits With Benefits Pictures PDF
This slide outlines benefits of major data centre audit types aimed at evaluating working of operations to make necessary improvements. It covers audit types with respective descriptions and benefits. Showcasing this set of slides titled Major Types Of Data Center Management Audits With Benefits Pictures PDF. The topics addressed in these templates are Security Audit, Access Control Audits, Power Audit . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
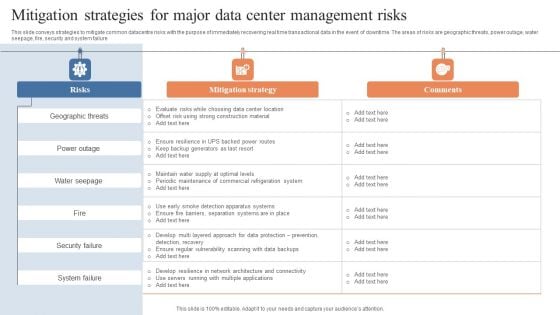
Mitigation Strategies For Major Data Center Management Risks Designs PDF
This slide conveys strategies to mitigate common datacentre risks with the purpose of immediately recovering real time transactional data in the event of downtime. The areas of risks are geographic threats, power outage, water seepage, fire, security and system failure. Showcasing this set of slides titled Mitigation Strategies For Major Data Center Management Risks Designs PDF. The topics addressed in these templates are Geographic Threats, Power Outage, Water Seepage . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Strategies To Optimize Data Center Management Technology Operations Icons PDF
This slide highlights strategies to optimize datacentre with the purpose of improving infrastructural efficiency to make datacentre central hub for all technologies. It covers hiring data security officer, utilizing cloud computing, upgrading hardware, virtualization, management transparency and automation. Presenting Strategies To Optimize Data Center Management Technology Operations Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Utilize Cloud Computing, Upgrade Hardware, Virtualization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
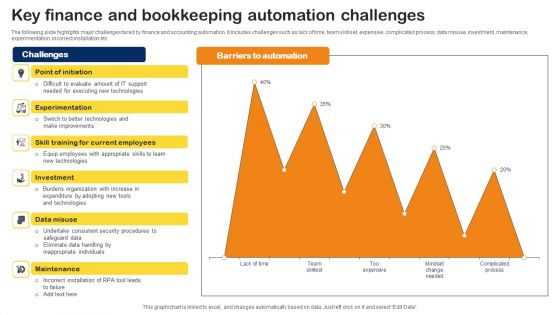
Key Finance And Bookkeeping Automation Challenges Professional PDF
The following slide highlights major challenges faced by finance and accounting automation. It includes challenges such as lack of time, team skillset, expensive, complicated process, data misuse, investment, maintenance, experimentation, incorrect installation etc. Showcasing this set of slides titled Key Finance And Bookkeeping Automation Challenges Professional PDF. The topics addressed in these templates are Burdens Organization, Investment, Consistent Security Procedures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Milestones Achieved Conglomerate Company Fund Raising Rules Pdf
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Major Milestones Achieved Conglomerate Company Fund Raising Rules Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide represents major awards and recognition achieved by diversified manufacturers and technology company. It includes awards such as reddot design award, top 100 internship programs winner, security sales and integration award, the world most admired company, etc.

BYOD Policy Challenges And Mitigation Tips
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit BYOD Policy Challenges And Mitigation Tips and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide highlights challenges in implementing a Bring Your Own Device BYOD policy, including challenges like device loss, malicious apps, and insecure cloud storage. It also provides practical solutions to mitigate these risks and enhance security in the workplace.
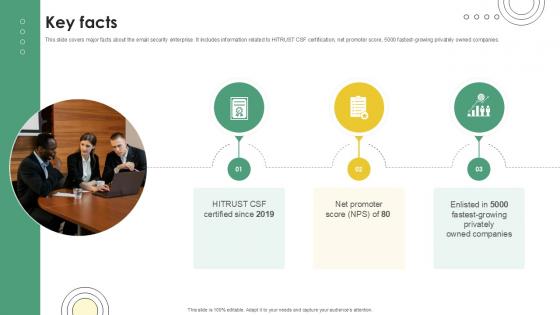
Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint
This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies. If you are looking for a format to display your unique thoughts, then the professionally designed Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Facts Email And Data Protection Platform Capital Funding Pitch Deck PPT PowerPoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers major facts about the email security enterprise. It includes information related to HITRUST CSF certification, net promoter score, 5000 fastest-growing privately owned companies.

Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide
This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution. If you are looking for a format to display your unique thoughts, then the professionally designed Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Major Milestones Achieved Email And Data Protection Platform Capital Funding Pitch Deck PPT Slide and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers key awards and recognitions achieved by the company. It includes awards such as top rated software, rising star of email security software, highest rated HIPAA compliant messaging solution.

Overview Cybersecurity And Data Protection In Digital Transformation DT SS V
This slide presents an overview into the landscape of cybersecurity and data protection with its advantages. It also presents a survey analysis on share of SMEs that have implemented essential and basic IT security initiatives.Find highly impressive Overview Cybersecurity And Data Protection In Digital Transformation DT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Overview Cybersecurity And Data Protection In Digital Transformation DT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide presents an overview into the landscape of cybersecurity and data protection with its advantages. It also presents a survey analysis on share of SMEs that have implemented essential and basic IT security initiatives.

Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf
This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on. Present like a pro with Technologies Used To Protect Data In Confidential Computing Technologies Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide depicts the related technologies used to protect the information in processing. The purpose of this slide is to showcase the technologies and comparison between these technologies based on security and scalability. The technologies include homomorphic encryption, multi-party computation, and so on.
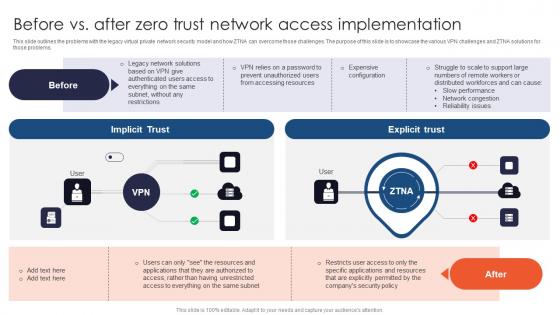
Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Network Access Before Vs After Zero Trust Network Access Implementation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Integration Methods Data Integration As A Service Data Integration Strategies For Business
This slide discusses the fifth approach to data integration which is data integration as a service. The purpose of this slide is to explain the approach and highlights its benefits and limitation including enhances efficiency and provides global accessibility, security concerns arise, respectively, and so on. Boost your pitch with our creative Integration Methods Data Integration As A Service Data Integration Strategies For Business. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide discusses the fifth approach to data integration which is data integration as a service. The purpose of this slide is to explain the approach and highlights its benefits and limitation including enhances efficiency and provides global accessibility, security concerns arise, respectively, and so on.

Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
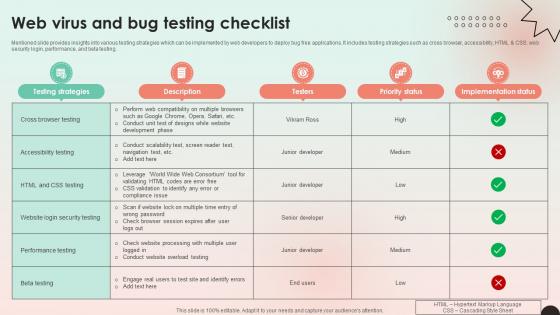
Web Consulting Business Web Virus And Bug Testing Checklist
Mentioned slide provides insights into various testing strategies which can be implemented by web developers to deploy bug free applications. It includes testing strategies such as cross browser, accessibility, HTML and CSS, web security login, performance, and beta testing. Explore a selection of the finest Web Consulting Business Web Virus And Bug Testing Checklist here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Web Consulting Business Web Virus And Bug Testing Checklist to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. Mentioned slide provides insights into various testing strategies which can be implemented by web developers to deploy bug free applications. It includes testing strategies such as cross browser, accessibility, HTML and CSS, web security login, performance, and beta testing.

Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V
This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Are you searching for a Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Wireless Banking To Improve Two Factor Authentication Process Flow For Enhanced Fin SS V from Slidegeeks today. This slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc.
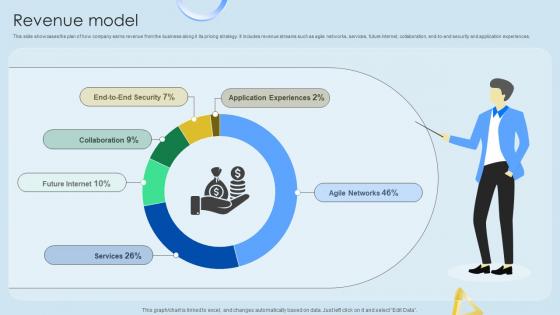
Revenue Model Cloud Networking Service Provider Business Model BMC SS V
This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences. Find highly impressive Revenue Model Cloud Networking Service Provider Business Model BMC SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Revenue Model Cloud Networking Service Provider Business Model BMC SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide showcases the plan of how company earns revenue from the business along it its pricing strategy. It includes revenue streams such as agile networks, services, future internet, collaboration, end-to-end security and application experiences.

Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain
This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.Get a simple yet stunning designed Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.

Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.
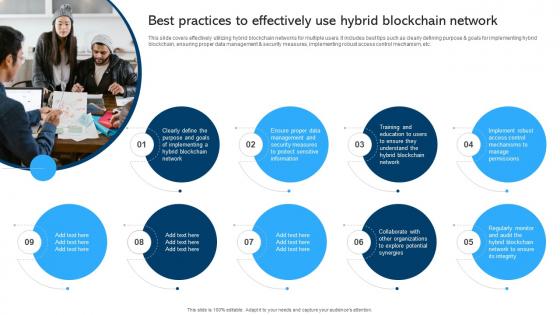
Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V
This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc. Welcome to our selection of the Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc.
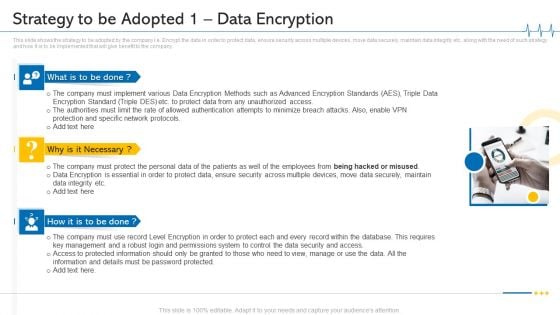
Minimize Cloud Risks Medical Care Business Case Competition Strategy To Be Adopted 1 Data Encryption Microsoft PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting minimize cloud risks medical care business case competition strategy to be adopted 1 data encryption microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protection And Specific Network Protocols, Protect Data, Permissions System, Key Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Network Access Architectural Models Software Defined Perimeter SDP
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Network Access Architectural Models Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Network Access Architectural Models Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption.

Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF
This slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Challenges And Solutions For SASE Implementation Ppt Infographics Slideshow PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Applications Of Photonics In Safety Silicon Photonics SiPh It Ppt PowerPoint
This slide depicts how photonics helps in peoples safety and security by developing contactless sensors and visual apps, avoiding pollution, detecting structural faults, biometrics and border safety, video surveillance, and detecting illegal goods.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Applications Of Photonics In Safety Silicon Photonics SiPh It Ppt PowerPoint a try. Our experts have put a lot of knowledge and effort into creating this impeccable Applications Of Photonics In Safety Silicon Photonics SiPh It Ppt PowerPoint. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide depicts how photonics helps in peoples safety and security by developing contactless sensors and visual apps, avoiding pollution, detecting structural faults, biometrics and border safety, video surveillance, and detecting illegal goods.
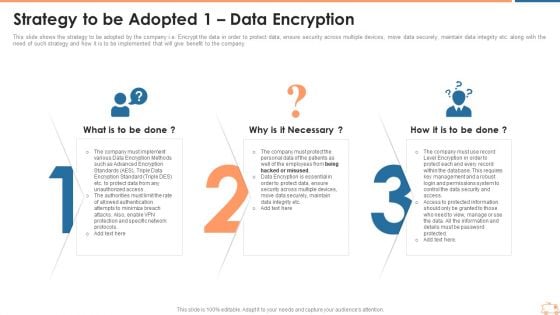
Strategy To Be Adopted 1 Data Encryption Ppt Gallery Skills PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt gallery skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
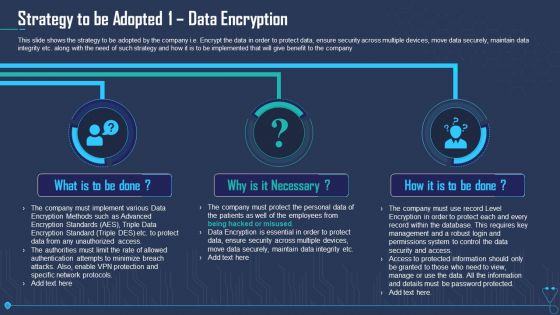
Strategy To Be Adopted 1 Data Encryption Ppt Outline PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt outline pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
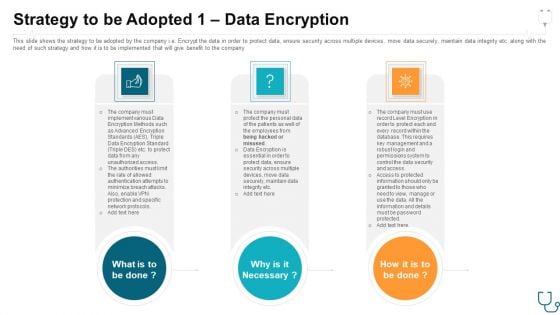
Strategy To Be Adopted 1 Data Encryption Ppt Model Deck PDF
This slide shows the strategy to be adopted by the company i.e. Encrypt the data in order to protect data, ensure security across multiple devices, move data securely, maintain data integrity etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Presenting strategy to be adopted 1 data encryption ppt model deck pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like strategy to be adopted 1 data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
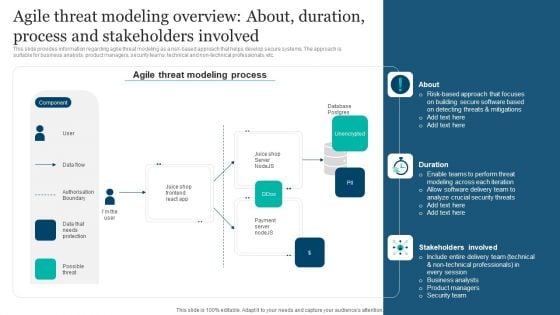
Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. This modern and well-arranged Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

WAF Introduction Web Application Firewall Use Cases Topics PDF
This slide outlines the main application areas of web application firewall systems. The purpose of this slide is to showcase the various use cases of WAF, including patching vulnerabilities, complying with security and regulatory regulations, enforcing content policies, securing websites and applications, and so on. Presenting this PowerPoint presentation, titledWAF Introduction Web Application Firewall Use Cases Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting thisWAF Introduction Web Application Firewall Use Cases Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizableWAF Introduction Web Application Firewall Use Cases Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Structure PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Boost your pitch with our creative Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Structure PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Graphics Template PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Boost your pitch with our creative Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Graphics Template PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
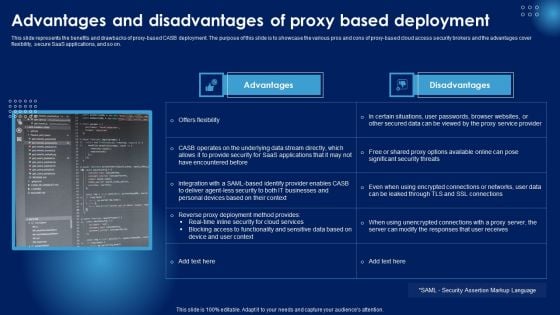
Advantages And Disadvantages Of Proxy Based Deployment Ppt PowerPoint Presentation Diagram Images PDF
This slide represents the benefits and drawbacks of proxy-based CASB deployment. The purpose of this slide is to showcase the various pros and cons of proxy-based cloud access security brokers and the advantages cover flexibility, secure SaaS applications, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Advantages And Disadvantages Of Proxy Based Deployment Ppt PowerPoint Presentation Diagram Images PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Advantages And Disadvantages Of Proxy Based Deployment Ppt PowerPoint Presentation Diagram Images PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
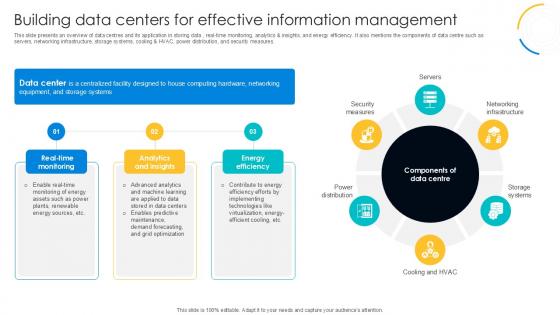
Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V
This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures. If you are looking for a format to display your unique thoughts, then the professionally designed Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.


 Continue with Email
Continue with Email

 Home
Home


































