Privacy Security
Icon Global Security In Powerpoint And Google Slides Cpb
Introducing our well designed Icon Global Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Icon Global Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Icon Global Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Reporting Template In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Security Reporting Template In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Security Reporting Template that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Security Reporting Template In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Internet Security Management In Powerpoint And Google Slides Cpb
Introducing our well designed Internet Security Management In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Internet Security Management. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Internet Security Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Unblocked Online Security Extension In Powerpoint And Google Slides Cpb
Introducing our well-designed Unblocked Online Security Extension In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Unblocked Online Security Extension. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Unblocked Online Security Extension In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Best Security Management In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Best Security Management In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Best Security Management that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Best Security Management In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Android Security Malware Detection In Powerpoint And Google Slides Cpb
Introducing our well-designed Android Security Malware Detection In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Android Security Malware Detection. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Android Security Malware Detection In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Spyware Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Spyware Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Spyware Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Spyware Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Mobile Android Devices Security In Powerpoint And Google Slides Cpb
Introducing our well designed Mobile Android Devices Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Mobile Android Devices Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Mobile Android Devices Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

E Commerce Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well-designed E Commerce Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like E Commerce Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our E Commerce Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Security Camera System Business In Powerpoint And Google Slides Cpb
Introducing our well-designed Security Camera System Business In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Camera System Business. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Camera System Business In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Flaw Cyber Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Tab Manager Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Tab Manager Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Tab Manager Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Tab Manager Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
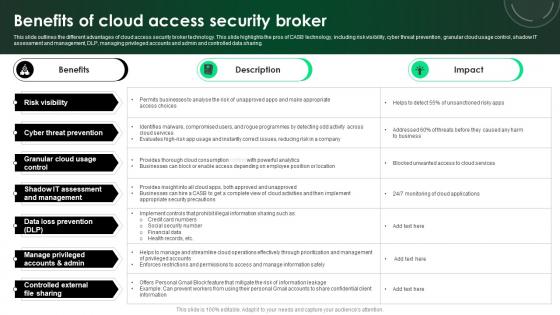
CASB 2 0 IT Benefits Of Cloud Access Security Broker
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. There are so many reasons you need a CASB 2 0 IT Benefits Of Cloud Access Security Broker. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing.
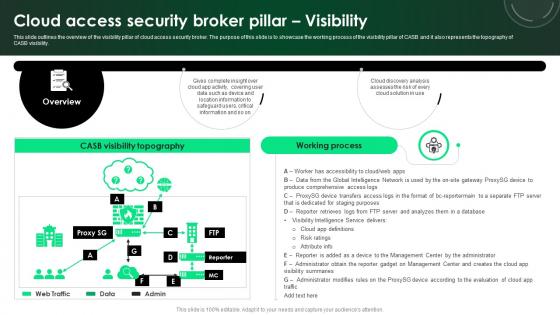
CASB 2 0 IT Cloud Access Security Broker Pillar Visibility
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Slidegeeks has constructed CASB 2 0 IT Cloud Access Security Broker Pillar Visibility after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility.

Existing It Security Infrastructure Constituents Corrective Regression Testing Ppt Slides
This slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Existing It Security Infrastructure Constituents Corrective Regression Testing Ppt Slides will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on.
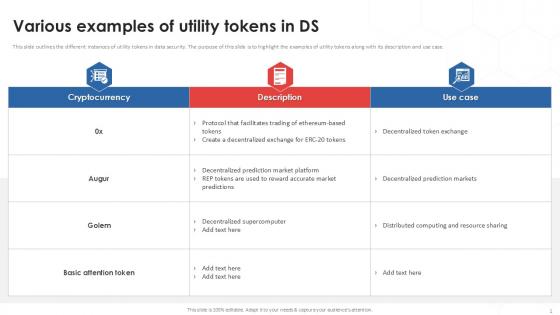
Various Examples Of Tokenization Strategies For Data Security PPT Slides
This slide outlines the different instances of utility tokens in data security. The purpose of this slide is to highlight the examples of utility tokens along with its description and use case. Boost your pitch with our creative Various Examples Of Tokenization Strategies For Data Security PPT Slides. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the different instances of utility tokens in data security. The purpose of this slide is to highlight the examples of utility tokens along with its description and use case.

Cloud Security Firewall Proposal Ppt Powerpoint Presentation Complete Deck
Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf
Pitch your topic with ease and precision using this Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf This layout presents information on Digital Security, Metrics Icon, Showcasing Threat Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Cyber Security Strategic Agenda For Data Protection Icon Template Pdf
Pitch your topic with ease and precision using this Cyber Security Strategic Agenda For Data Protection Icon Template Pdf. This layout presents information on Cyber Security Strategic, Agenda For Data Protection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Strategic Agenda For Data Protection Icon Template Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Locked Keyboard Security PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with abstract of locked keyboard security Fan the fervour with our Locked Keyboard Security PowerPoint Templates And PowerPoint Backgrounds 0311. The excitement will hit the ceiling.
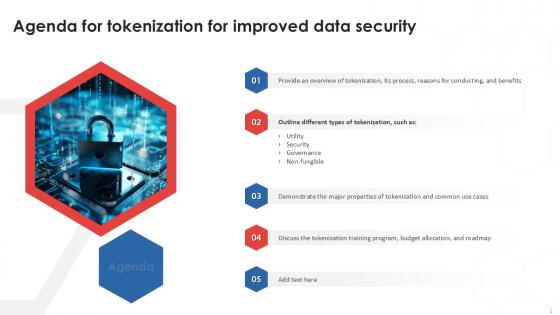
Agenda For Tokenization For Improved Data Security PPT Powerpoint
Find a pre-designed and impeccable Agenda For Tokenization For Improved Data Security PPT Powerpoint. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Our Agenda For Tokenization For Improved Data Security PPT Powerpoint are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
5G Wi Fi Signal Icon For Network Security Inspiration Pdf
Pitch your topic with ease and precision using this 5G Wi Fi Signal Icon For Network Security Inspiration Pdf. This layout presents information on 5G Wi Fi Signal, Network Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our 5G Wi Fi Signal Icon For Network Security Inspiration Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Default Network Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Default Network Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Default Network Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Default Network Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
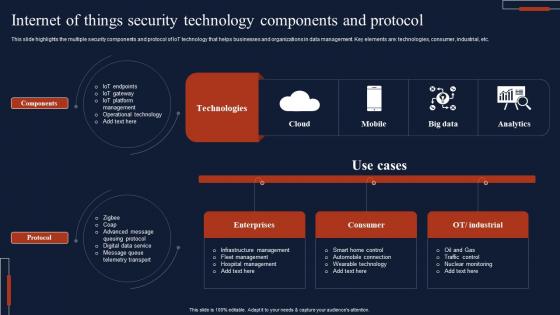
Internet Of Things Security Technology Components And Protocol Rules Pdf
This slide highlights the multiple security components and protocol of IoT technology that helps businesses and organizations in data management. Key elements are technologies, consumer, industrial, etc. Pitch your topic with ease and precision using this Internet Of Things Security Technology Components And Protocol Rules Pdf This layout presents information on Components, Protocol, Technologies, Consumer It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide highlights the multiple security components and protocol of IoT technology that helps businesses and organizations in data management. Key elements are technologies, consumer, industrial, etc.

Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf
This slide illustrate Cyber security incident communication plan flowchart across various members. It includes elements such as technical coordinator, incident manager, support coordinator, business owner and forensic partner Showcasing this set of slides titled Cyber Security Emergency Response Communication Plan Flowchart Infographics Pdf The topics addressed in these templates are Technical Coordinator, Incident Manager, Support Coordinator All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide illustrate Cyber security incident communication plan flowchart across various members. It includes elements such as technical coordinator, incident manager, support coordinator, business owner and forensic partner
Smart Radio Military And Security Applications Icon Structure Pdf
Pitch your topic with ease and precision using this Smart Radio Military And Security Applications Icon Structure Pdf. This layout presents information on Smart Radio Military, Security Applications Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Smart Radio Military And Security Applications Icon Structure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.
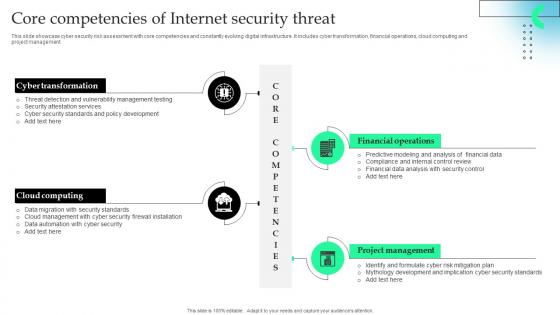
Core Competencies Of Internet Security Threat Portrait Pdf
This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.Showcasing this set of slides titled Core Competencies Of Internet Security Threat Portrait Pdf The topics addressed in these templates are Cyber Transformation, Cloud Computing, Financial Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.

Agenda For Application Security Testing Ppt Powerpoint Elements
Create an editable Agenda For Application Security Testing Ppt Powerpoint Elements that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Application Security Testing Ppt Powerpoint Elements is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. Our Agenda For Application Security Testing Ppt Powerpoint Elements are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
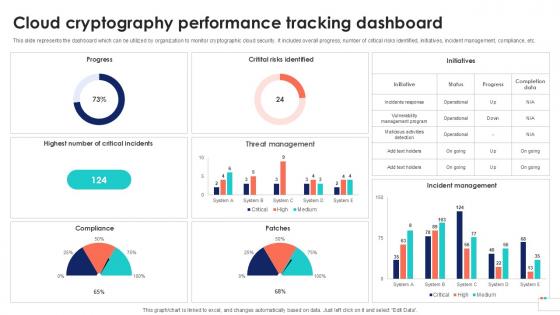
Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation
This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cloud Cryptography Performance Data Security In Cloud Computing Ppt Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the dashboard which can be utilized by organization to monitor cryptographic cloud security. It includes overall progress, number of critical risks identified, initiatives, incident management, compliance, etc.
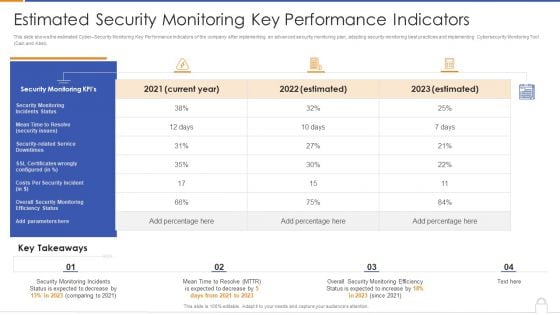
Estimated Security Monitoring Key Performance Indicators Diagrams PDF
Deliver and pitch your topic in the best possible manner with this estimated security monitoring key performance indicators diagrams pdf. Use them to share invaluable insights on security monitoring, security related service downtimes, overall security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Fibers IT Applications Of Photonics In Safety And Security
This slide depicts how photonics helps in peoples safety and security by developing contactless sensors and visual apps, avoiding pollution, detecting structural faults, biometrics and border safety, video surveillance, and detecting illegal goods. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Fibers IT Applications Of Photonics In Safety And Security. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Fibers IT Applications Of Photonics In Safety And Security today and make your presentation stand out from the rest This slide depicts how photonics helps in peoples safety and security by developing contactless sensors and visual apps, avoiding pollution, detecting structural faults, biometrics and border safety, video surveillance, and detecting illegal goods.
Protections Cyber Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Protections Cyber Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Protections Cyber Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Protections Cyber Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
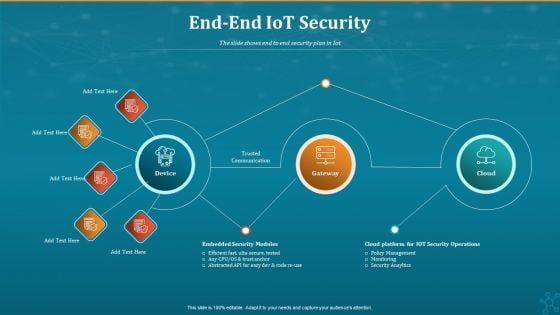
Machine To Machine Communication End End Iot Security Inspiration PDF
The slide shows end to end security plan in Iot.Deliver an awe-inspiring pitch with this creative machine to machine communication end end iot security inspiration pdf. bundle. Topics like trusted communication, gateway, embedded security modules, cloud platform for iot security operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Estimated Security Management Plan Critical Success Factors Infographics PDF
Deliver an awe inspiring pitch with this creative Estimated security management plan critical success factors infographics pdf bundle. Topics like security management, security incidents level, security implementation duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
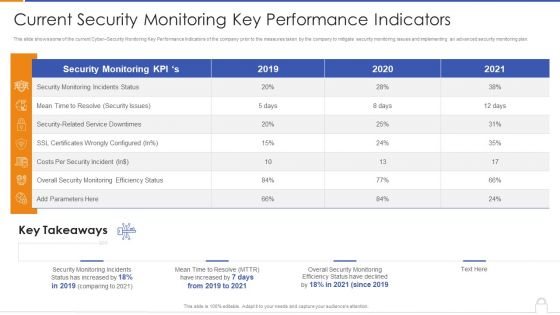
Current Security Monitoring Key Performance Indicators Formats PDF
Deliver and pitch your topic in the best possible manner with this current security monitoring key performance indicators formats pdf. Use them to share invaluable insights on security monitoring incidents, overall security monitoring, costs per security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
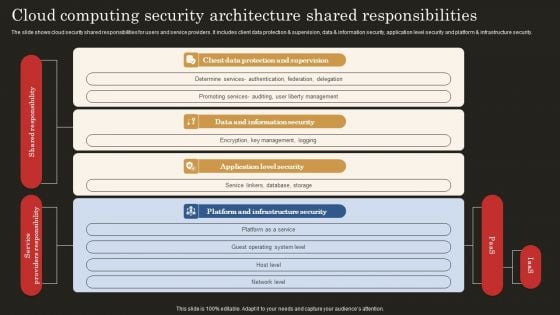
Cloud Computing Security Architecture Shared Responsibilities Brochure PDF
The slide shows cloud security shared responsibilities for users and service providers. It includes client data protection and supervision, data and information security, application level security and platform and infrastructure security. Showcasing this set of slides titled Cloud Computing Security Architecture Shared Responsibilities Brochure PDF. The topics addressed in these templates are Client Data Protection, Data Information Security, Application Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Statistics Of Cloud Data Security Client Side Encryption PPT Slide
This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. This Statistics Of Cloud Data Security Client Side Encryption PPT Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc.

Network Security Dark Overlord In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Network Security Dark Overlord In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Network Security Dark Overlord that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our Network Security Dark Overlord In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf
This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.Showcasing this set of slides titled Steps To Perform Vulnerability Analysis For Network Security Pictures Pdf The topics addressed in these templates are Evaluate Possible Risk, Interpret Scan Results, Create Mitigation Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase vulnerability assessment process that help organization to identify security vulnerabilities in network system and prioritize them to plan mitigation action plan. It includes steps such as identifying, scanning, identify type of scan, configure scan etc.
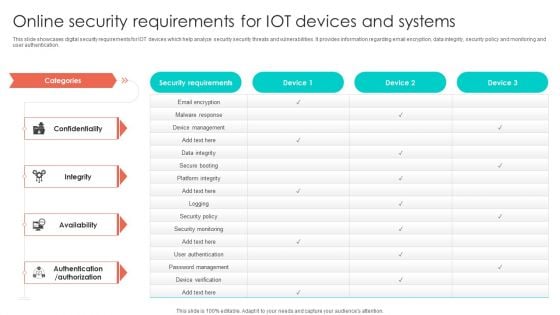
Online Security Requirements For Iot Devices And Systems Graphics PDF
This slide showcases digital security requirements for IOT devices which help analyze security security threats and vulnerabilities. It provides information regarding email encryption, data integrity, security policy and monitoring and user authentication. Pitch your topic with ease and precision using this Online Security Requirements For Iot Devices And Systems Graphics PDF. This layout presents information on Device Management, Security Policy, Security Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icons Slide Security Service Provider Business Model BMC SS V
Download our innovative and attention grabbing Icons Slide Security Service Provider Business Model BMC SS V template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide Security Service Provider Business Model BMC SS V are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Main Features For Robust Application Security Testing Ppt Powerpoint Icons
This slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc. Are you searching for a Main Features For Robust Application Security Testing Ppt Powerpoint Icons that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Main Features For Robust Application Security Testing Ppt Powerpoint Icons from Slidegeeks today. This slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc.
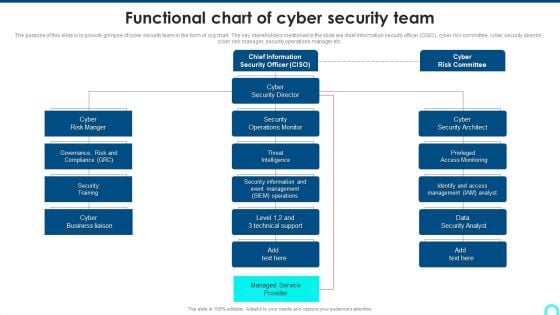
Functional Chart Of Cyber Security Team Diagrams PDF
The purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc.Deliver an awe inspiring pitch with this creative Functional Chart Of Cyber Security Team Diagrams PDF bundle. Topics like Access Monitoring, Security Architect, Security Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
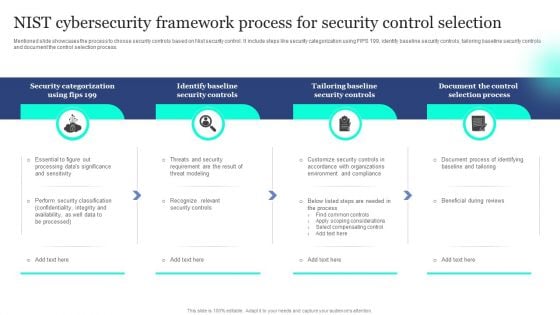
NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF
Mentioned slide showcases the process to choose security controls based on Nist security control. It include steps like security categorization using FIPS 199, identify baseline security controls, tailoring baseline security controls and document the control selection process. Presenting NIST Cybersecurity Framework Process For Security Control Selection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Controls, Tailoring Baseline, Selection Process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
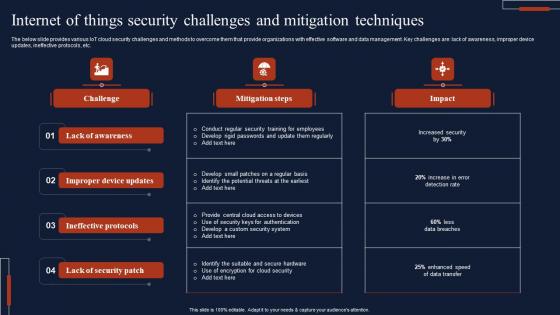
Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf
The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc. Pitch your topic with ease and precision using this Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf This layout presents information on Lack Of Awareness, Ineffective Protocols, Lack Of Security Patch It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc.
Computer Password Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Computer Password Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Computer Password Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Computer Password Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Password Managers Mac Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Password Managers Mac Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Password Managers Mac Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Password Managers Mac Security In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Security Password Generator In Powerpoint And Google Slides Cpb
Introducing our well designed Security Password Generator In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Password Generator. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Security Password Generator In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Icons Slide For Application Security Testing Ppt Powerpoint Formats
Download our innovative and attention grabbing Icons Slide For Application Security Testing Ppt Powerpoint Formats template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele. Our Icons Slide For Application Security Testing Ppt Powerpoint Formats are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
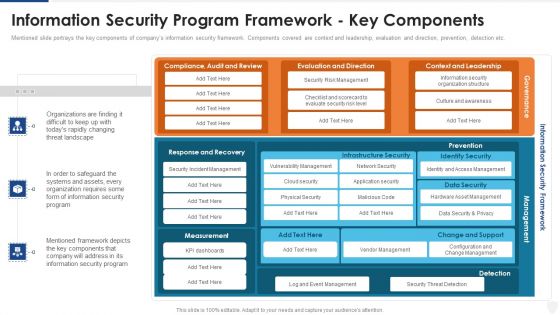
Information Security Program Framework Key Components Ppt Inspiration Ideas PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this information security program framework key components ppt inspiration ideas pdf. Use them to share invaluable insights on network security, application security, vendor management, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
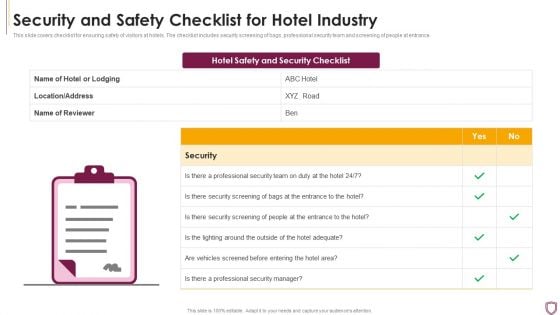
Security And Safety Checklist For Hotel Industry Summary PDF
This slide covers checklist for ensuring safety of visitors at hotels. The checklist includes security screening of bags, professional security team and screening of people at entrance.Showcasing this set of slides titled Security And Safety Checklist For Hotel Industry Summary PDF The topics addressed in these templates are Professional Security, Security Screening, Vehicles Screened All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
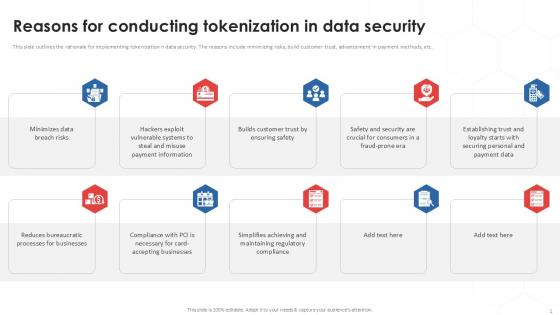
Reasons For Conducting Tokenization In Data Security PPT Template
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Boost your pitch with our creative Reasons For Conducting Tokenization In Data Security PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.
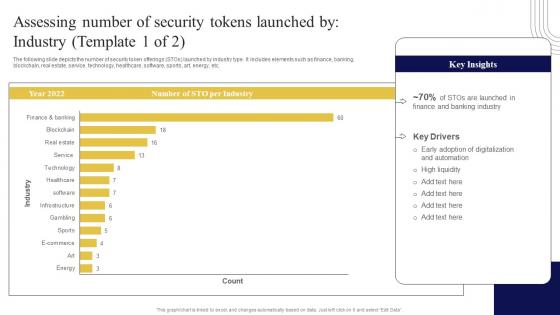
Assessing Number Of Security Tokens Exploring Investment Opportunities Introduction Pdf
The following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc. Want to ace your presentation in front of a live audience Our Assessing Number Of Security Tokens Exploring Investment Opportunities Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The following slide depicts the number of security token offerings STOs launched by industry type. It includes elements such as finance, banking, blockchain, real estate, service, technology, healthcare, software, sports, art, energy, etc.
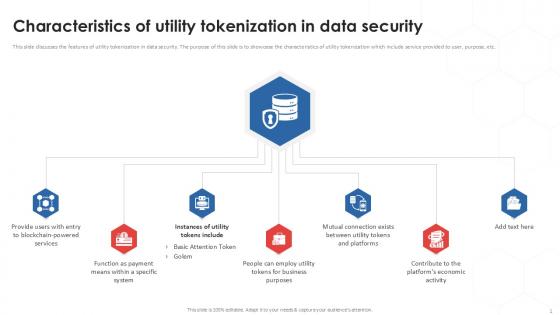
Characteristics Of Utility Tokenization In Data Security PPT Sample
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. Find a pre-designed and impeccable Characteristics Of Utility Tokenization In Data Security PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc.

Framework Of Information IT Security Action Program Slides PDF
This slide focuses on information security action program framework which covers governance plan, security standards, stakeholder engagement and operational management to manage risks, handling threat, data security management, etc.Showcasing this set of slides titled Framework Of Information IT Security Action Program Slides PDF The topics addressed in these templates are Security Standards, Data Protection, Response Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
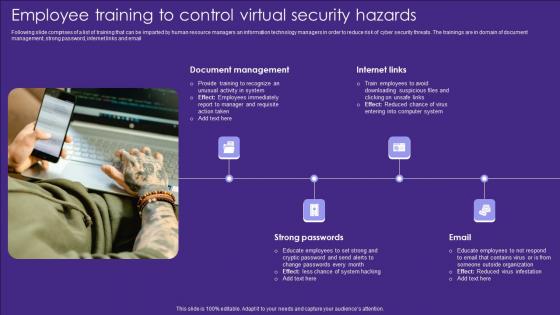
Employee Training To Control Virtual Security Hazards Designs Pdf
Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Pitch your topic with ease and precision using this Employee Training To Control Virtual Security Hazards Designs Pdf. This layout presents information on Internet Links, Email, Strong Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email

Data Encryption Method In Application Security Testing Ppt Powerpoint Formats
This slide discusses the introduction of encryption in application security for protection of specific fields in an application. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Encryption Method In Application Security Testing Ppt Powerpoint Formats to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide discusses the introduction of encryption in application security for protection of specific fields in an application.
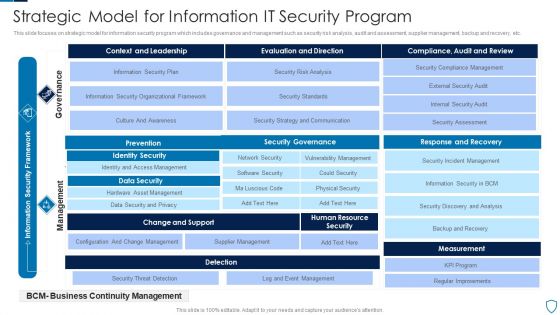
Strategic Model For Information IT Security Program Slides PDF
This slide focuses on strategic model for information security program which includes governance and management such as security risk analysis, audit and assessment, supplier management, backup and recovery, etc.Showcasing this set of slides titled Strategic Model For Information IT Security Program Slides PDF The topics addressed in these templates are Prevention, Identity Security, Data Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































