Privacy Security

Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs.Presenting Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Compliance Violations, Access Control, Daniel Of Service In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Security Framework In Cloud Computing Demonstration PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a desktop security management security framework in cloud computing demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, detect, respond, recover, identify. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Complete Computer Security Implementation Checklist Demonstration PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting desktop security management complete computer security implementation checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, organizations, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.This is a Cloud Security Assessment Cloud Security Threats Malware Attacks Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Information Exfiltration, Protection Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
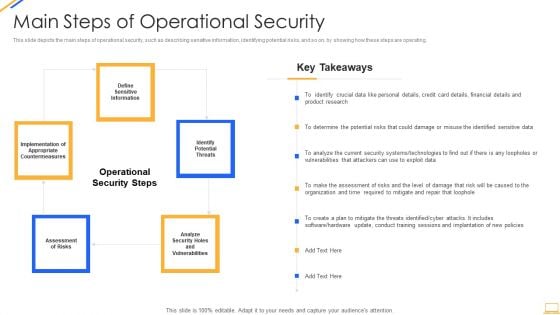
Desktop Security Management Main Steps Of Operational Security Inspiration PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting desktop security management main steps of operational security inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, determine, analyze, systems, technologies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
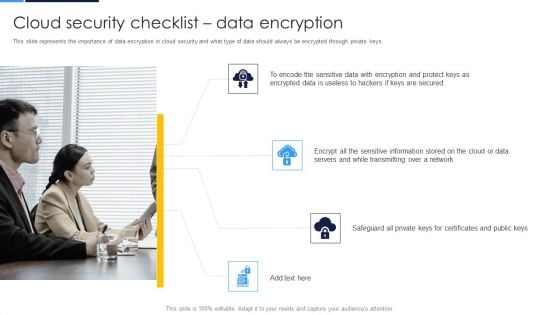
Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.This is a Cloud Security Assessment Cloud Security Checklist Data Encryption Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Encrypted Data, Sensitive Information You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
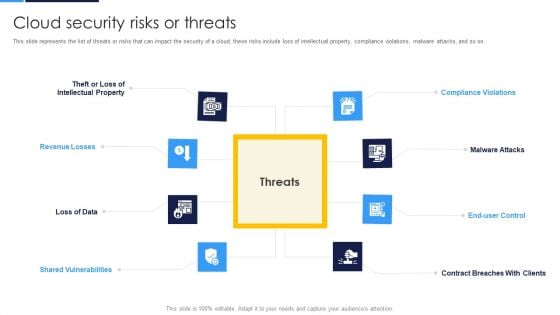
Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on.Presenting Cloud Security Assessment Cloud Security Risks Or Threats Topics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Compliance Violations In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
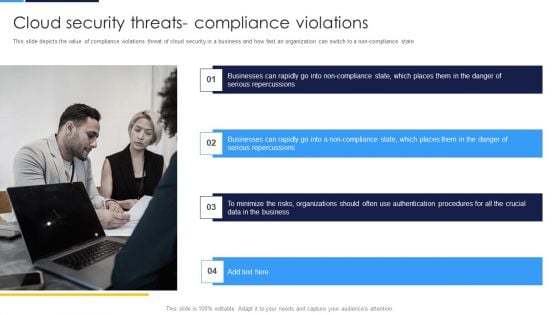
Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.This is a Cloud Security Assessment Cloud Security Threats Compliance Violations Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Serious Repercussions, Data In The Business, Organizations Should You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
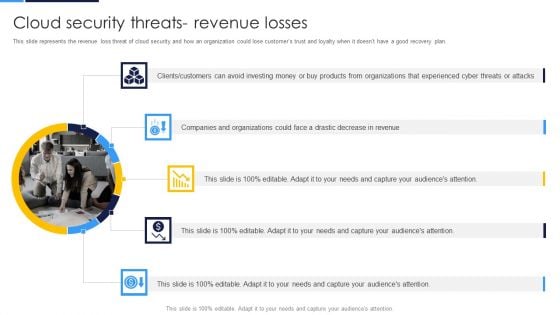
Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Presenting Cloud Security Assessment Cloud Security Threats Revenue Losses Introduction PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Clients Or Customers, Companies And Organizations, Organizations That Experienced. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
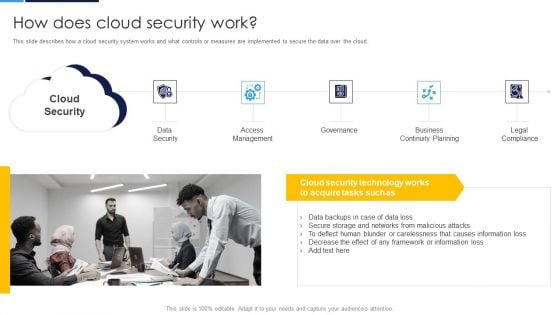
Cloud Security Assessment How Does Cloud Security Work Formats PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Security Assessment How Does Cloud Security Work Formats PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Information Against, Transparency, Regulations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
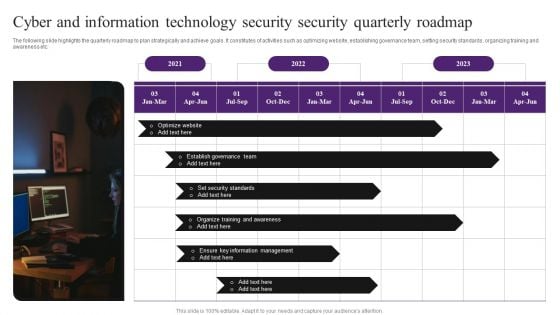
Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF
The following slide highlights the quarterly roadmap to plan strategically and achieve goals. It constitutes of activities such as optimizing website, establishing governance team, setting security standards, organizing training and awareness etc. Presenting Cyber And Information Technology Security Security Quarterly Roadmap Elements PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Optimize Website, Information Management, Organize Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Identity Security PowerPoint Template 1110
Blue Earth globe and padlock isolated over white background Enhance your chances of asset creation. Diversify your base with our Identity Security PowerPoint Template 1110.
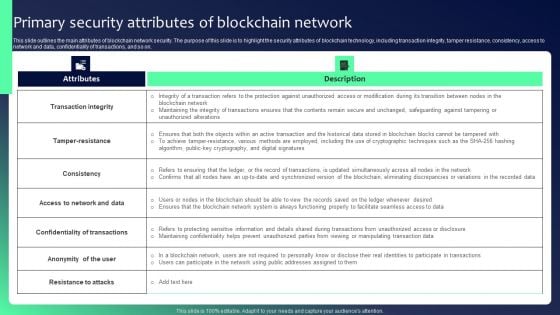
Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF
This slide outlines the main attributes of blockchain network security. The purpose of this slide is to highlight the security attributes of blockchain technology, including transaction integrity, tamper resistance, consistency, access to network and data, confidentiality of transactions, and so on. The Blockchain Security Solutions Deployment Primary Security Attributes Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Organizing Security Awareness Running Cyber Security Awareness Campaign Graphics PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Boost your pitch with our creative Organizing Security Awareness Running Cyber Security Awareness Campaign Graphics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Organizing Security Awareness Comparative Assessment Of Security Awareness Clipart PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizing Security Awareness Comparative Assessment Of Security Awareness Clipart PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Desktop Security Management Latest Threats In Computer Security Inspiration PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting desktop security management latest threats in computer security inspiration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like financial, information, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Methodology Diagram Powerpoint Topics
This is a security methodology diagram powerpoint topics. This is a six stage process. The stages in this process are device protection, data separation, security operation, security organization, leak protection, sharing protection.
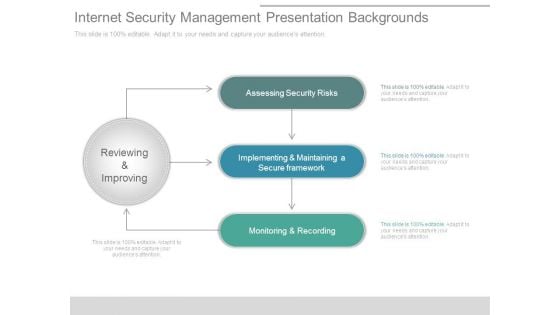
Internet Security Management Presentation Backgrounds
This is a internet security management presentation backgrounds. This is a three stage process. The stages in this process are assessing security risks, implementing and maintaining a secure framework, monitoring and recording, reviewing and improving.

Network Security Model PPT Example

Internet Protocol Security PPT Example

Security Services Presentation Background Images
This is a security services presentation background images. This is an eight stage process. The stages in this process are payment services, security services, authorization services, configuration manager, persistence services, stock control services, user interface services, core cash services.
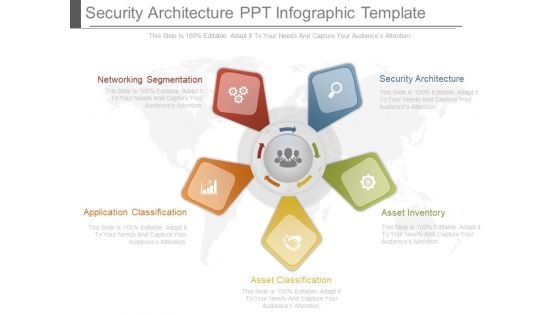
Security Architecture Ppt Infographic Template
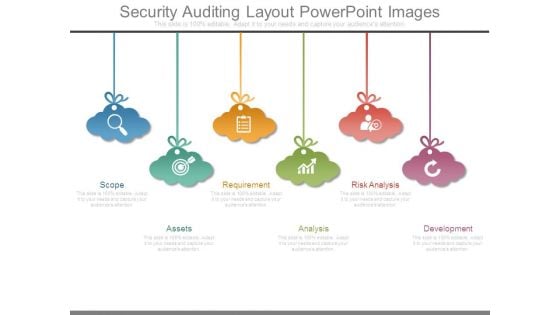
Security Auditing Layout Powerpoint Images
This is a security auditing layout powerpoint images. This is a six stage process. The stages in this process are scope, assets, requirement, analysis, risk analysis, development.
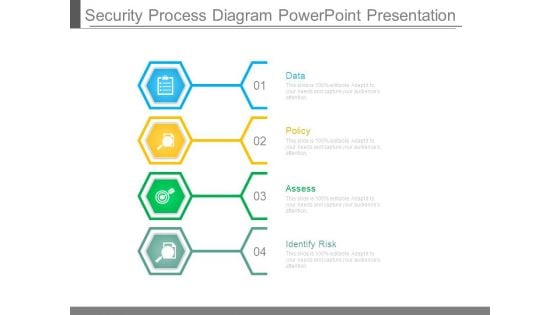
Security Process Diagram Powerpoint Presentation
This is a security process diagram powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.
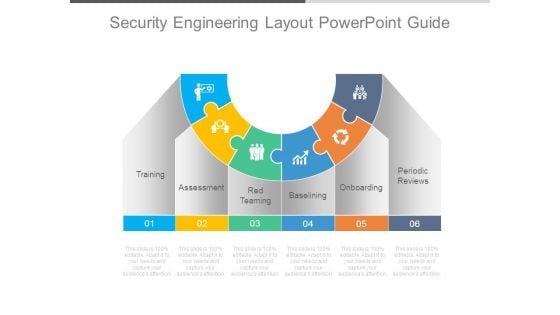
Security Engineering Layout Powerpoint Guide
This is a security engineering layout powerpoint guide. This is a six stage process. The stages in this process are training, assessment, red teaming, baselining, onboarding, periodic reviews.
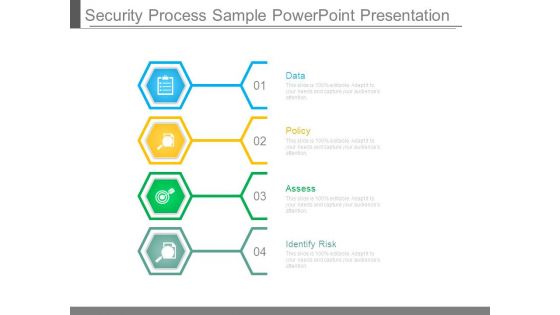
Security Process Sample Powerpoint Presentation
This is a security process sample powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.
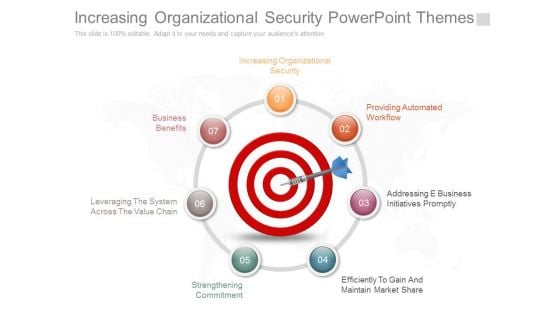
Increasing Organizational Security Powerpoint Themes
This is a increasing organizational security powerpoint themes. This is a seven stage process. The stages in this process are increasing organizational security, business benefits, leveraging the system across the value chain, strengthening commitment, providing automated workflow, addressing e business initiatives promptly, efficiently to gain and maintain market share.
Security Analysis Trends Ppt Example
This is a security analysis trends ppt example. This is a one stage process. The stages in this process are open, pt close, high, low, mcap, pe, eps, div, pv, p bv, ev sales, ev ebidta.

CCTV Security Services PPT Template
Drive the power of innovation with our revolutionary CCTV Security Services PPT Template. This dynamic tool empowers you to create visually-stunning presentations that leave a lasting impression. With its user-friendly interface and 100 percent editable features, you can effortlessly customize every aspect of your slides, ensuring they align perfectly with your message. No design skills No problem. Our expertly crafted template provides a solid foundation for your ideas, allowing you to focus on what matters most delivering a compelling presentation. Do not settle for mediocrity, choose excellence with our template today.
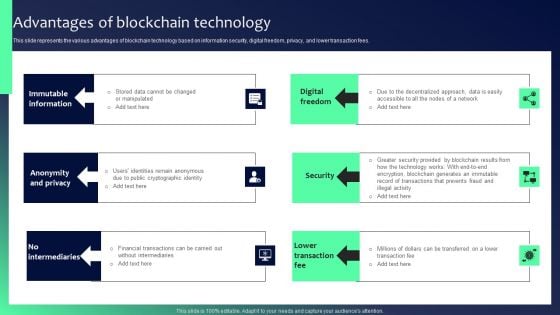
Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. Find a pre-designed and impeccable Blockchain Security Solutions Deployment Advantages Of Blockchain Technology Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Protection Icon Security Icon Wall Security Security Shield Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name protection icon security icon wall security security shield ppt powerpoint presentation complete deck. The topics discussed in these slides are security icon, wall security, security shield, security lock, money shield. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
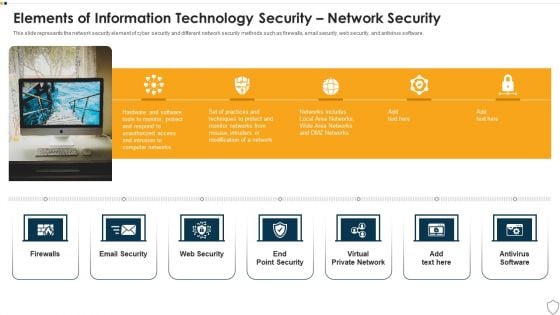
IT Security Elements Of Information Technology Security Network Security Ppt Pictures Graphics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting it security elements of information technology security network security ppt pictures graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like web security, end point security, virtual private network, email security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
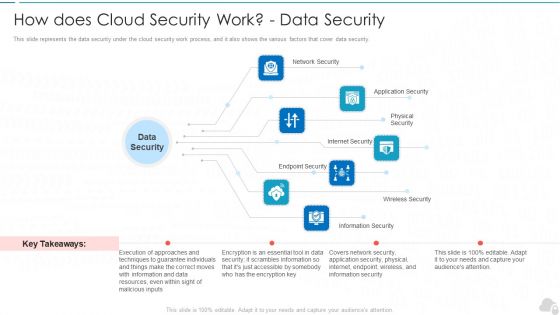
How Does Cloud Security Work Data Security Cloud Computing Security IT Ppt Ideas Slide Download PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Presenting how does cloud security work data security cloud computing security it ppt ideas slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network security, internet security, endpoint security, wireless security, physical security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
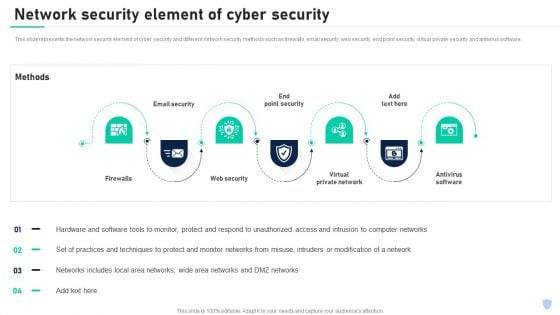
Cyber Security Components To Enhance Processes Network Security Element Of Cyber Security Ideas PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, end point security, virtual private security and antivirus software. There are so many reasons you need a Cyber Security Components To Enhance Processes Network Security Element Of Cyber Security Ideas PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
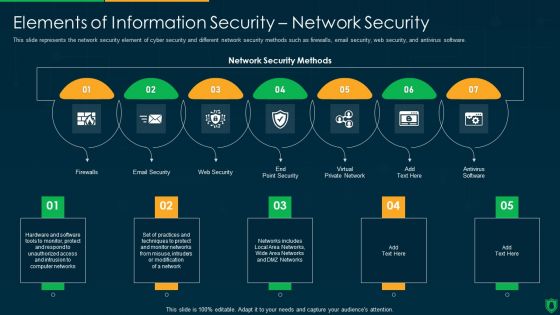
Info Security Elements Of Information Security Network Security Ppt PowerPoint Presentation File Vector PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting info security elements of information security network security ppt powerpoint presentation file vector pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like email security, web security, virtual private network, firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cloud Information Security How Does Cloud Security Work Data Security Ppt Icon Layout PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Presenting Cloud Information Security How Does Cloud Security Work Data Security Ppt Icon Layout PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Information Security, Wireless Security, Endpoint Security, Internet Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
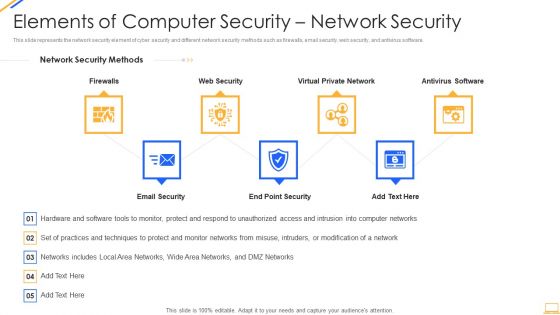
Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
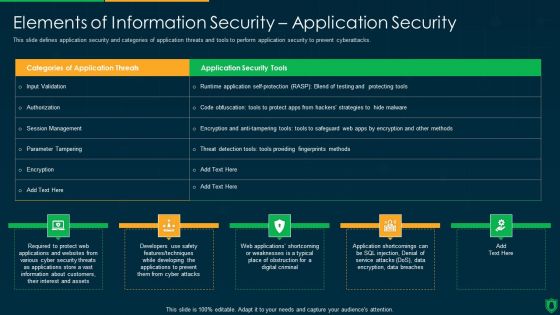
Info Security Elements Of Information Security Application Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Deliver and pitch your topic in the best possible manner with this info security elements of information security application security ppt powerpoint presentation file graphics download pdf. Use them to share invaluable insights on application security tools, parameter tampering, encryption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
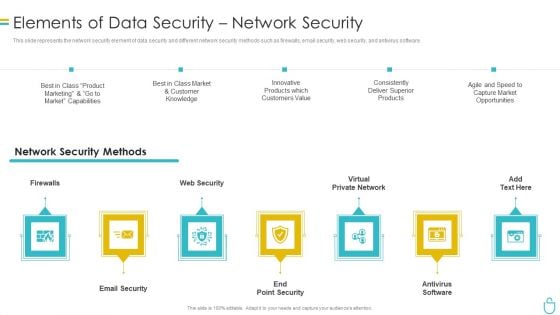
Information Security Elements Of Data Security Network Security Ppt Visual Aids Infographics PDF
This slide represents the network security element of data security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting information security elements of data security network security ppt visual aids infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like customer, market, product, opportunities, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Pillars Of Cloud Security Identity Security Cloud Computing Security IT Ppt Model Slides PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. This is a pillars of cloud security identity security cloud computing security it ppt model slides pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like pillars of cloud security identity security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Elements Of Computer Security Operational Security Themes PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a desktop security management elements of computer security operational security themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, resources, require, security, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
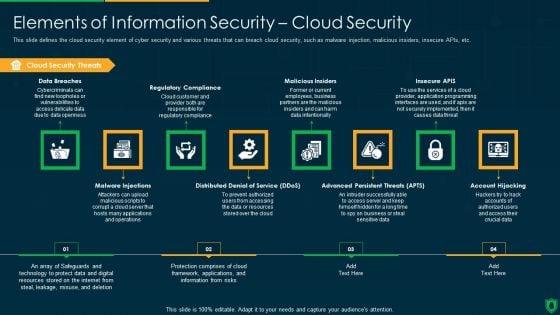
Info Security Elements Of Information Security Cloud Security Ppt PowerPoint Presentation Gallery Graphics Download PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting info security elements of information security cloud security ppt powerpoint presentation gallery graphics download pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like cloud security threats, regulatory compliance, malicious insiders, insecure apis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Checklist Security Patches And Updates Ppt Show Background Designs PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. This is a Cloud Information Security Cloud Security Checklist Security Patches And Updates Ppt Show Background Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Measures, New Technologies, Security Tool. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
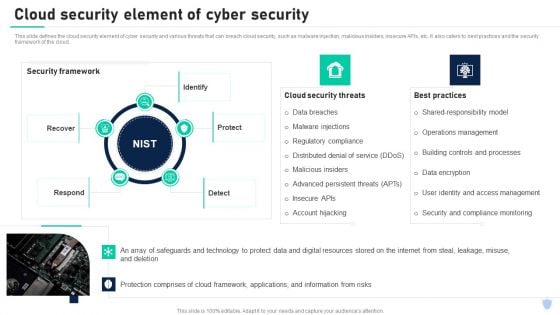
Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. It also caters to best practices and the security framework of the cloud. Create an editable Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Components To Enhance Processes Cloud Security Element Of Cyber Security Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
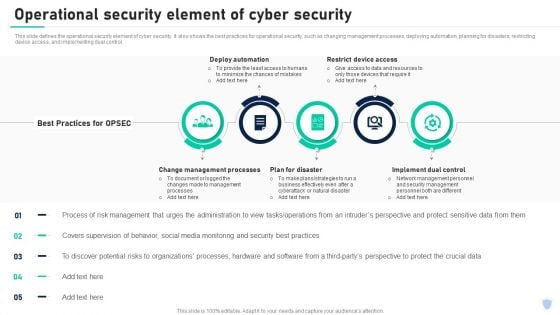
Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security, such as changing management processes, deploying automation, planning for disasters, restricting device access, and implementing dual control. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Pillars Of Cloud Security Network Security Cloud Computing Security IT Ppt Summary Guidelines PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. Presenting pillars of cloud security network security cloud computing security it ppt summary guidelines pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like performing, traffic security, micro segmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Elements Of Computer Security Information Security Portrait PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Presenting desktop security management elements of computer security information security portrait pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like social media, information security, organization, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
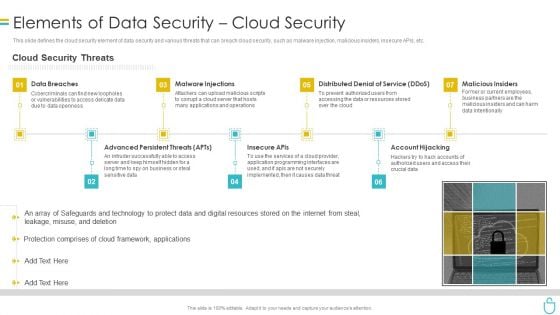
Information Security Elements Of Data Security Cloud Security Ppt Model Rules PDF
This slide defines the cloud security element of data security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Presenting information security elements of data security cloud security ppt model rules pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like data breaches, malware injections, distributed denial of service, malicious insiders, account hijacking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Elements Of Computer Security Cloud Security Diagrams PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a desktop security management elements of computer security cloud security diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
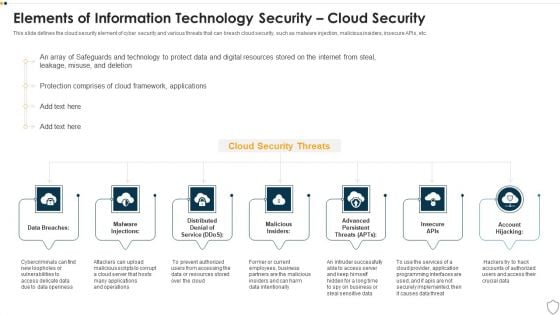
IT Security Elements Of Information Technology Security Cloud Security Ppt Outline Background Images PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a it security elements of information technology security cloud security ppt outline background images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data breaches, malware injections, malicious insiders, account hijacking, distributed denial of service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pillars Of Cloud Security Process Based Security Cloud Computing Security IT Ppt Slides Skills PDF
This slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a pillars of cloud security process based security cloud computing security it ppt slides skills pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like movement, cloud security, vulnerabilities, lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Security Elements Of Data Security Operational Security Ppt Icon Background Designs PDF
This slide defines the operational security element of data security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a information security elements of data security operational security ppt icon background designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control, restrict device access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Elements Of Information Technology Security Operational Security Ppt Professional Format Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a it security elements of information technology security operational security ppt professional format ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, restrict device access, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
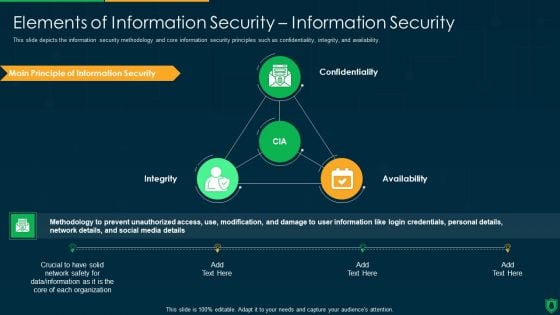
Info Security Elements Of Information Security Information Security Ppt PowerPoint Presentation Gallery Smartart PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. This is a info security elements of information security information security ppt powerpoint presentation gallery smartart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like confidentiality, availability, integrity, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
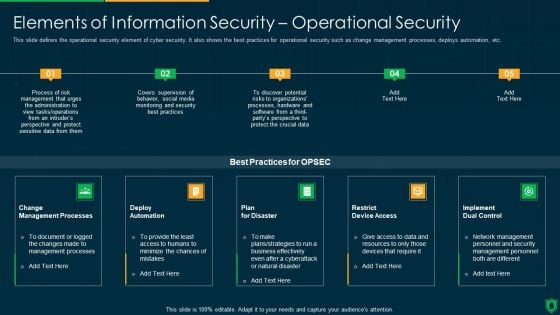
Info Security Elements Of Information Security Operational Security Ppt PowerPoint Presentation File Backgrounds PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a info security elements of information security operational security ppt powerpoint presentation file backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Security Assessment Cloud Security Checklist Security Patches And Updates Icons PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly.This is a Cloud Security Assessment Cloud Security Checklist Security Patches And Updates Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Measures, Latest Or Advanced, Patches On Developed You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Pillars Of Cloud Security Process Based Security Mockup PDF
This slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take.This is a Cloud Security Assessment Pillars Of Cloud Security Process Based Security Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Management, Recognizes Vulnerabilities, Operational Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
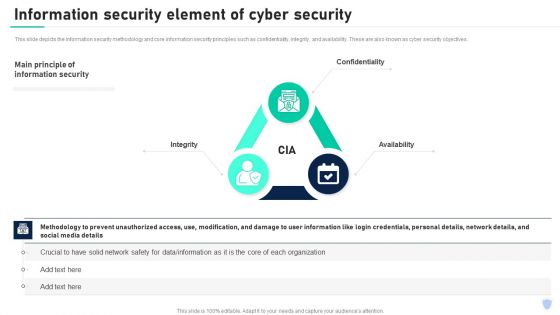
Cyber Security Components To Enhance Processes Information Security Element Of Cyber Security Mockup PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. These are also known as cyber security objectives. Want to ace your presentation in front of a live audience Our Cyber Security Components To Enhance Processes Information Security Element Of Cyber Security Mockup PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.


 Continue with Email
Continue with Email

 Home
Home


































