Privacy Security
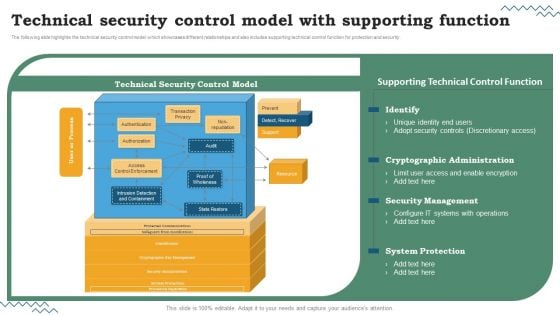
Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Are you searching for a Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF from Slidegeeks today.

One Pager Proposal For Security Personnel Services PDF Document PPT Template
Presenting you a fantastic One Pager Proposal For Security Personnel Services PDF Document PPT Template. This one-pager document is crafted on hours of research and professional design efforts to ensure you have the best resource. It is completely editable and its design allow you to rehash its elements to suit your needs. Get this One Pager Proposal For Security Personnel Services PDF Document PPT Template Download now.

30 60 90 Days Plan For Security Guard Services Proposal Ppt Show PDF
This is a 30 60 90 days plan for security guard services proposal ppt show pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan, security guard services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Roadmap For Security Guard Services Proposal Ppt Icon Graphic Images PDF
This is a roadmap for security guard services proposal ppt icon graphic images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap, security guard services, 2014 to 2020. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Testimonials In The Security Guard Services Proposal Ppt Gallery Format Ideas PDF
This is a testimonials in the security guard services proposal ppt gallery format ideas pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like testimonials, security guard services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
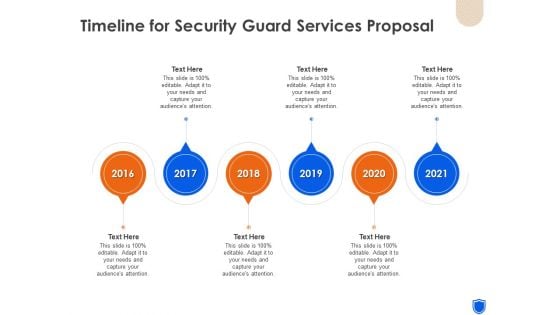
Timeline For Security Guard Services Proposal Ppt Visual Aids Slides PDF
Presenting timeline for security guard services proposal ppt visual aids slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like timeline, security guard services, 2016 to 2021. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
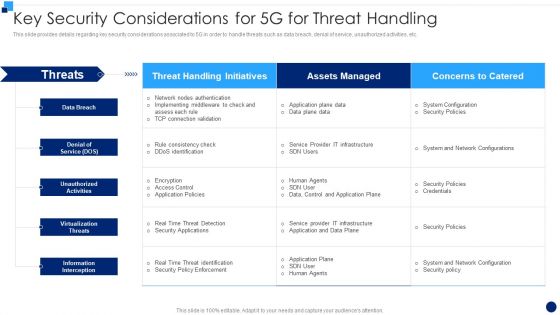
Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF bundle. Topics like Information Interception, Virtualization Threats, Denial Of Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
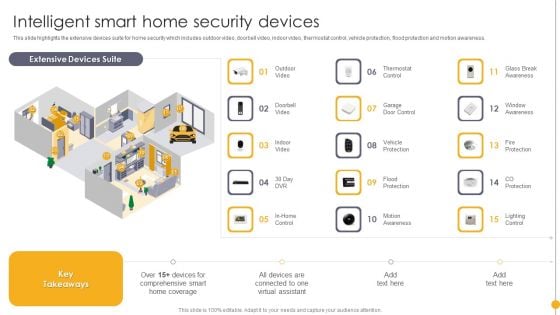
Portable Home Safety Systems Company Profile Intelligent Smart Home Security Devices Structure PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Portable Home Safety Systems Company Profile Intelligent Smart Home Security Devices Structure PDF bundle. Topics like Extensive Devices Suite, Comprehensive Smart, Virtual Assistant can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF
The following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Presenting this PowerPoint presentation, titled Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Impact Of Cyber Security Policies And Practices Ppt PowerPoint Presentation Diagram Graph Charts PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Cloud Network Security Dimensions And Sections Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud network security dimensions and sections ppt powerpoint presentation icon background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, service, threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Safety And Security System Services Proposal Example Document Report Doc Pdf Ppt
Heres a predesigned Safety And Security System Services Proposal Example Document Report Doc Pdf Ppt for you. Built on extensive research and analysis, this one-complete deck has all the center pieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Safety And Security System Services Proposal Example Document Report Doc Pdf Ppt A4 One-pager now.

Contact Us For Safety And Security System Services Proposal One Pager Sample Example Document
Presenting you an exemplary Contact Us For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Contact Us For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
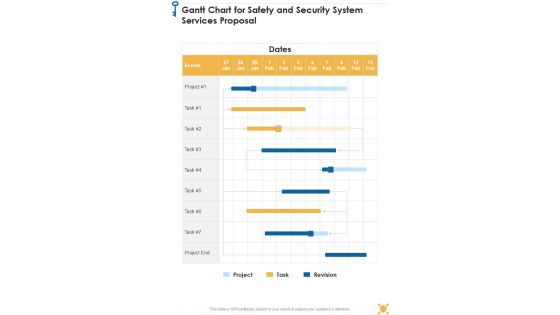
Gantt Chart For Safety And Security System Services Proposal One Pager Sample Example Document
Presenting you an exemplary Gantt Chart For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Gantt Chart For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
Icons Slide For Safety And Security System Services Proposal One Pager Sample Example Document
Presenting you an exemplary Icons Slide For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Icons Slide For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.
Roadmap For Safety And Security System Services Proposal One Pager Sample Example Document
Presenting you an exemplary Roadmap For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Roadmap For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Table Of Contents Safety And Security System Services Proposal One Pager Sample Example Document
Presenting you an exemplary Table Of Contents Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Our Services For Security And Safety System Proposal One Pager Sample Example Document
Presenting you an exemplary Our Services For Security And Safety System Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Services For Security And Safety System Proposal One Pager Sample Example Document brilliant piece now.
Icons Slide For Security Camera Proposal Template One Pager Sample Example Document
Presenting you an exemplary Icons Slide For Security Camera Proposal Template One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Icons Slide For Security Camera Proposal Template One Pager Sample Example Document brilliant piece now.
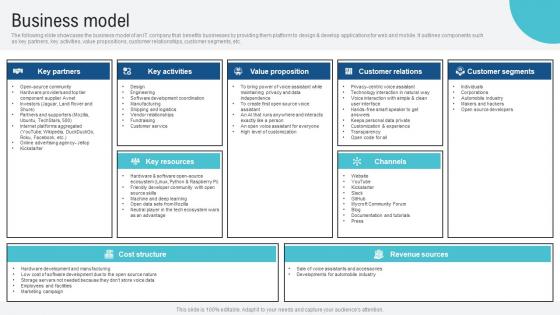
Business Model Voice Assistance Security Platform Investor Funding Presentation Guidelines Pdf
The following slide showcases the business model of an IT company that benefits businesses by providing them platform to design and develop applications for web and mobile. It outlines components such as key partners, key activities, value propositions, customer relationships, customer segments, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Business Model Voice Assistance Security Platform Investor Funding Presentation Guidelines Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The following slide showcases the business model of an IT company that benefits businesses by providing them platform to design and develop applications for web and mobile. It outlines components such as key partners, key activities, value propositions, customer relationships, customer segments, etc.

Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V
The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry.
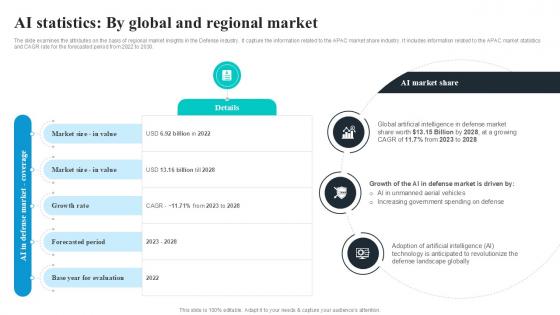
AI Statistics By Global And Regional Global Security Industry PPT Template IR SS V
The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030. Boost your pitch with our creative AI Statistics By Global And Regional Global Security Industry PPT Template IR SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The slide examines the attributes on the basis of regional market insights in the Defense industry. It capture the information related to the APAC market share industry. It includes information related to the APAC market statistics and CAGR rate for the forecasted period from 2022 to 2030.

Challenges For New Entrants In Global Security Industry PPT Example IR SS V
The slide showcases the barriers to entry in Defense industry. The main purpose of this slide is to recognize the variables that may impede or make it difficult for new entrants to enter the market successfully. By identifying these impediments, aspiring Defense companies can make educated judgements and establish appropriate strategies to overcome or manage them efficiently. Want to ace your presentation in front of a live audience Our Challenges For New Entrants In Global Security Industry PPT Example IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. The slide showcases the barriers to entry in Defense industry. The main purpose of this slide is to recognize the variables that may impede or make it difficult for new entrants to enter the market successfully. By identifying these impediments, aspiring Defense companies can make educated judgements and establish appropriate strategies to overcome or manage them efficiently.

Market Restraints Impacting The Global Security Industry PPT Template IR SS V
The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry. This modern and well-arranged Market Restraints Impacting The Global Security Industry PPT Template IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc.

Dollar Sign With Key Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with Money sign of dollar and key Empower yourself with our Dollar Sign With Key Security PowerPoint Templates And PowerPoint Backgrounds 0211. Put extra force behind your thoughts.

Golden Key With Men Security PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with a man standing in a circle around a golden key Encourage entry into the area of excellence. Ease the doors open with our Golden Key With Men Security PowerPoint Templates And PowerPoint Backgrounds 0511.

Key With Dollar Finance Security PowerPoint Templates And PowerPoint Backgrounds 0911
Microsoft PowerPoint Template and Background with key made up of dollar sign and some dollars Our Key With Dollar Finance Security PowerPoint Templates And PowerPoint Backgrounds 0911 ensure a fair exchange. They give you many a penny for your thoughts.
Golden Key With Men Security PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with a man standing in a circle around a golden key Bite the bullet with our Golden Key With Men Security PowerPoint Themes And PowerPoint Slides 0511. Face the issues head-on.

Investment And Security Analysis Portfolio Management Ppt PowerPoint Presentation Complete Deck With Slides
This is a investment and security analysis portfolio management ppt powerpoint presentation complete deck with slides. This is a one stage process. The stages in this process are planning, business, strategy, management, marketing.
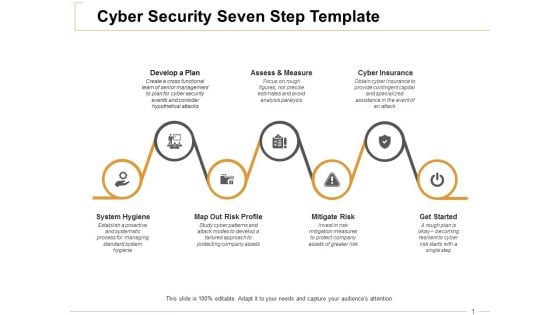
Cyber Security Seven Step Cyber Insurance Ppt PowerPoint Presentation Infographic Template Graphic Tips
This is a cyber security seven step cyber insurance ppt powerpoint presentation infographic template graphic tips. This is a seven stage process. The stages in this process are develop a plan, assess and measure, cyber insurance, mitigate risk, get started.

Operations Compliance And Security Testing Ppt PowerPoint Presentation Slides Master Slide
This is a operations compliance and security testing ppt powerpoint presentation slides master slide. This is a three stage process. The stages in this process are quality assurance, quality analysis, qa, testing process, bugs analysis.
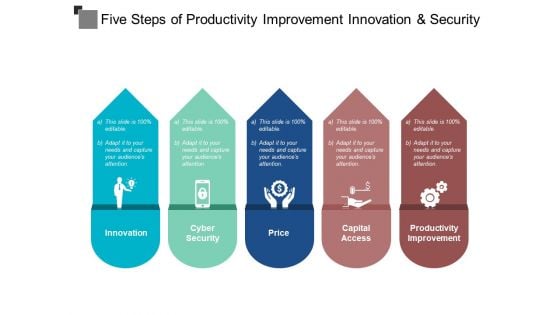
Five Steps Of Productivity Improvement Innovation And Security Ppt PowerPoint Presentation Layouts Inspiration
This is a five steps of productivity improvement innovation and security ppt powerpoint presentation layouts inspiration. This is a five stage process. The stages in this process are risk management, risk factors, risk variable.
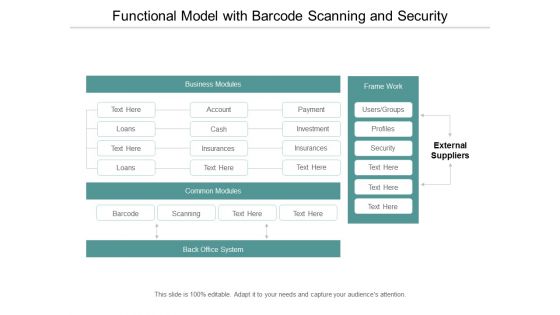
Functional Model With Barcode Scanning And Security Ppt Powerpoint Presentation Layouts Design Ideas
This is a functional model with barcode scanning and security ppt powerpoint presentation layouts design ideas. This is a four stage process. The stages in this process are functional architecture, functional planning, functional designing.

Cloud Computing Security And Compliance Ppt Powerpoint Presentation File Graphic Tips
This is a cloud computing security and compliance ppt powerpoint presentation file graphic tips. This is a three stage process. The stages in this process are cloud computing, cloud management, cloud governance.
Cloud Data Storage Infrastructure And Security Ppt Powerpoint Presentation Model Show
This is a cloud data storage infrastructure and security ppt powerpoint presentation model show. This is a four stage process. The stages in this process are data management, data centre, storage system.
Digital Infrastructure Data Storage And Security Ppt Powerpoint Presentation Show Layout Ideas
This is a digital infrastructure data storage and security ppt powerpoint presentation show layout ideas. This is a six stage process. The stages in this process are data management, data centre, storage system.
Enterprise Content Management Security Cost And User Friendly Ppt Powerpoint Presentation Gallery Demonstration
This is a enterprise content management security cost and user friendly ppt powerpoint presentation gallery demonstration. This is a five stage process. The stages in this process are cms, content management system.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Gallery Example
This is a recent global security market trends behavior ppt powerpoint presentation gallery example. This is a six stage process. The stages in this process are marketing, business, management.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Pictures Shapes
This is a recent global security market trends behavior ppt powerpoint presentation pictures shapes. This is a six stage process. The stages in this process are business, management, marketing.

Recent Global Security Market Trends Behavior Marketing Ppt PowerPoint Presentation Model Slideshow
This is a recent global security market trends behavior marketing ppt powerpoint presentation model slideshow. This is a six stage process. The stages in this process are business, management, marketing.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Professional Picture
This is a recent global security market trends behavior ppt powerpoint presentation professional picture. This is a six stage process. The stages in this process are business, management, marketing.

Recent Global Security Market Trends Behavior Ppt PowerPoint Presentation Styles Clipart
This is a recent global security market trends behavior ppt powerpoint presentation styles clipart. This is a six stage process. The stages in this process are management, marketing, business, strategy, planning.
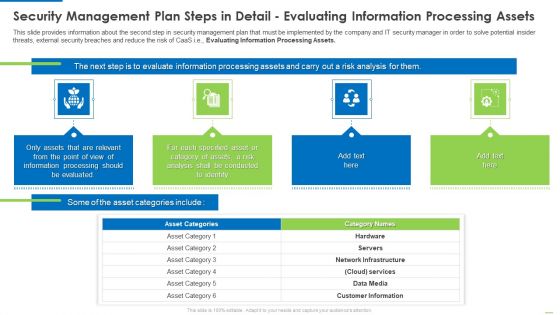
Security Management Plan Steps In Detail Evaluating Information Processing Assets Summary PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e.Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processing should be evaluated, conducted to identify, category of assets You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Summary PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. Presenting security management plan steps in detail system maintenance and monitoring summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like types of system maintenance, installation costs, types of system monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
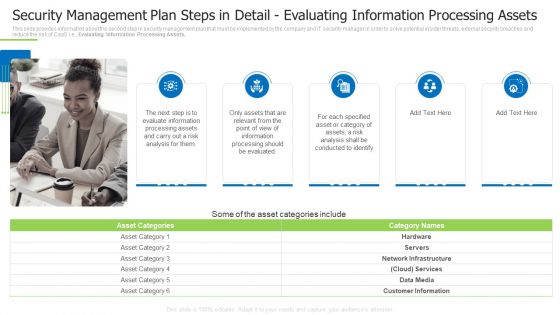
Security Management Plan Steps In Detail Evaluating Information Processing Assets Demonstration PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, conducted to identify, specified asset You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Template PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge or problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a way to overcome security monitoring challenges setting up an advanced cybersecurity template pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like establish security, monitoring strategy, supporting policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
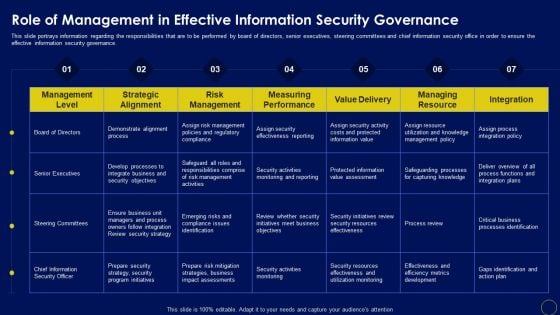
Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF can be your best option for delivering a presentation. Represent everything in detail using Role Of Management In Effective Business Mobile Device Security Management And Mitigation Slides PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks.If you are looking for a format to display your unique thoughts, then the professionally designed Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
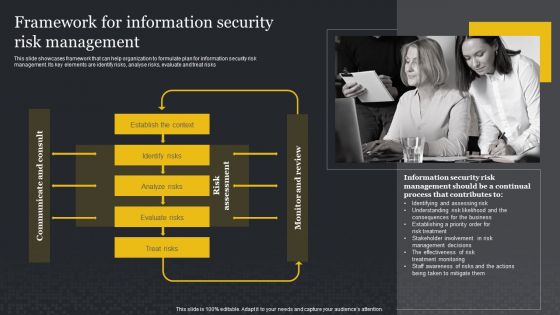
Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks. Presenting this PowerPoint presentation, titled Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF today and make your presentation stand out from the rest.
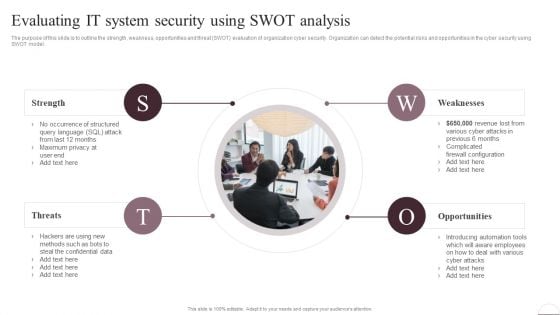
Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest
Prevention Of Information Roles And Responsibilities Of Cyber Security Team Icons PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Boost your pitch with our creative Prevention Of Information Roles And Responsibilities Of Cyber Security Team Icons PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Prevention Of Information Running Cyber Security Awareness Campaign For Employees Brochure PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Create an editable Prevention Of Information Running Cyber Security Awareness Campaign For Employees Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Prevention Of Information Running Cyber Security Awareness Campaign For Employees Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
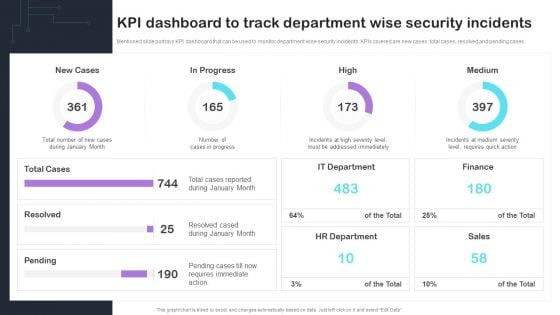
Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases. Presenting this PowerPoint presentation, titled Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cyber Risks And Incident Response Playbook KPI Dashboard To Track Department Wise Security Incidents Mockup PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
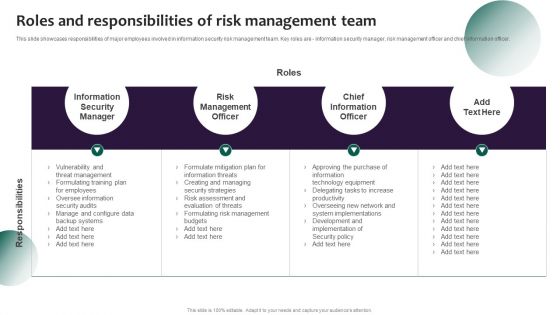
Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are - information security manager, risk management officer and chief information officer. Are you searching for a Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF from Slidegeeks today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.

Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF
The purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. Take your projects to the next level with our ultimate collection of Implementing Cybersecurity Awareness Program To Prevent Attacks Practices To Improve Security Awareness Level Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Implementing Cybersecurity Awareness Program To Prevent Attacks Roles And Responsibilities Of Cyber Security Team Information PDF
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Boost your pitch with our creative Implementing Cybersecurity Awareness Program To Prevent Attacks Roles And Responsibilities Of Cyber Security Team Information PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF
The purpose of this slide is to provide an overview of cyber security awareness campaign which can be used to educate staff members. The campaign covers information about the objectives, security awareness topics to cover and various activities which will be covered. Create an editable Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cybersecurity Awareness Program To Prevent Attacks Running Cyber Security Awareness Campaign Themes PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Comparison Of Various Security Awareness Training Software Ppt Model Aids PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Boost your pitch with our creative Comparison Of Various Security Awareness Training Software Ppt Model Aids PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.


 Continue with Email
Continue with Email

 Home
Home


































