Privacy Security
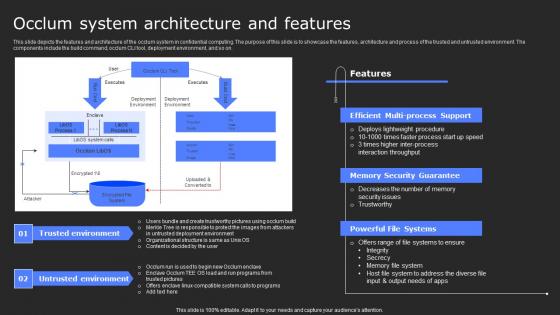
Occlum System Architecture And Features Secure Computing Framework Clipart Pdf
This slide depicts the features and architecture of the occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, occlum CLI tool, deployment environment, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Occlum System Architecture And Features Secure Computing Framework Clipart Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Occlum System Architecture And Features Secure Computing Framework Clipart Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide depicts the features and architecture of the occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, occlum CLI tool, deployment environment, and so on.
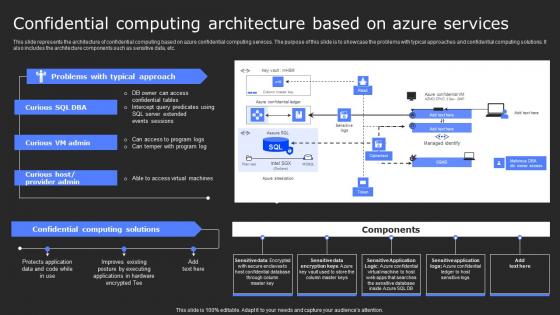
Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf
This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc.
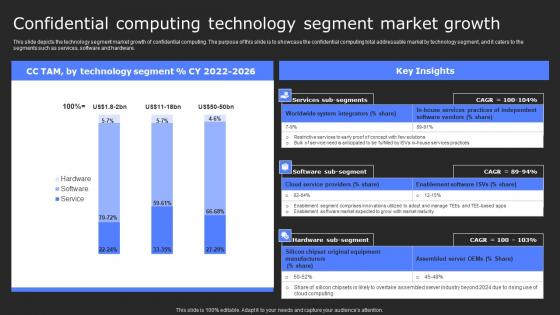
Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf
This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Explore a selection of the finest Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Technology Segment Secure Computing Framework Diagrams Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware.

Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF
This slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Ensure Secure Mobile Banking Ppt Inspiration Deck PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
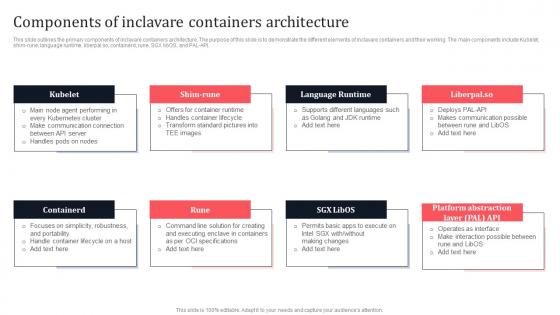
Components Of Inclavare Containers Architecture Secure Multi Party Information Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Components Of Inclavare Containers Architecture Secure Multi Party Information Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Components Of Inclavare Containers Architecture Secure Multi Party Information Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today. This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
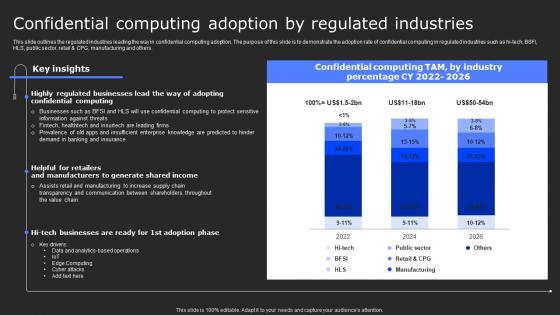
Confidential Computing Adoption By Secure Computing Framework Mockup Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Adoption By Secure Computing Framework Mockup Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Adoption By Secure Computing Framework Mockup Pdf today and make your presentation stand out from the rest This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.
Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. This Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Confidential Computing Performance Tracking Secure Computing Framework Microsoft Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.

Secure Web Gateway Architecture And Working Web Threat Protection System
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. This Secure Web Gateway Architecture And Working Web Threat Protection System from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc.

Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf
This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. Want to ace your presentation in front of a live audience Our Technical Stack For Evaluating Confidential Secure Computing Framework Information Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks.
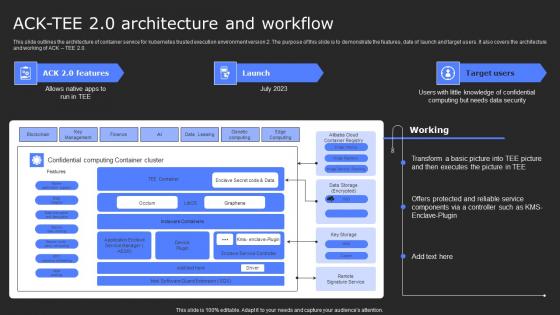
Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.
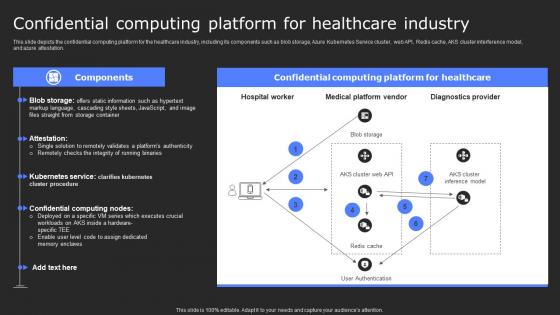
Confidential Computing Platform For Healthcare Secure Computing Framework Structure Pdf
This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation. Welcome to our selection of the Confidential Computing Platform For Healthcare Secure Computing Framework Structure Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today This slide depicts the confidential computing platform for the healthcare industry, including its components such as blob storage, Azure Kubernetes Service cluster, web API, Redis cache, AKS cluster interference model, and azure attestation.
Secure Payments Solution Ppt PowerPoint Presentation File Good Cpb
This is a secure payments solution ppt powerpoint presentation file good cpb. This is a three stage process. The stages in this process are secure payments solution.
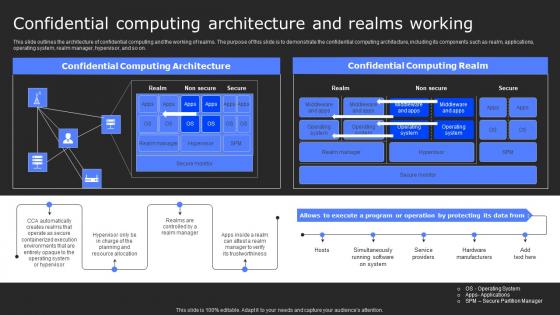
Confidential Computing Architecture And Secure Computing Framework Graphics Pdf
This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Confidential Computing Architecture And Secure Computing Framework Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on.
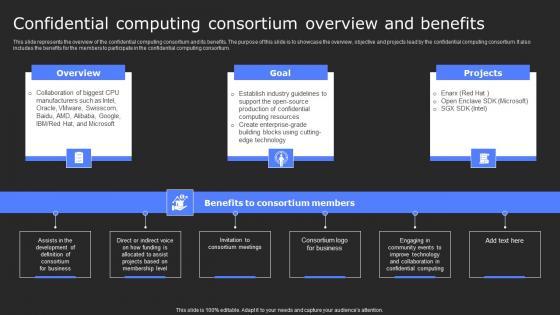
Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf
This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium. Make sure to capture your audiences attention in your business displays with our gratis customizable Confidential Computing Consortium Overview And Secure Computing Framework Inspiration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide represents the overview of the confidential computing consortium and its benefits. The purpose of this slide is to showcase the overview, objective and projects lead by the confidential computing consortium. It also includes the benefits for the members to participate in the confidential computing consortium.
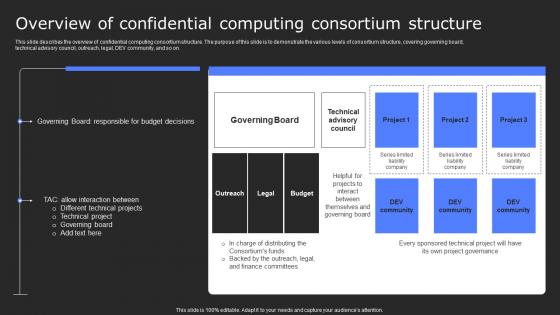
Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Overview Of Confidential Computing Consortium Secure Computing Framework Professional Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on.

Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc.

Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain
This slide represents overview and hardware devices of hardware crypto wallet. The purpose of this slide is to highlight some device used such as ledger nano x, trezor model t, ledge nano s, etc.Presenting this PowerPoint presentation, titled Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Hardware Wallets For Secure Crypto Storage Cryptocurrency Management With Blockchain that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide represents overview and hardware devices of hardware crypto wallet. The purpose of this slide is to highlight some device used such as ledger nano x, trezor model t, ledge nano s, etc.
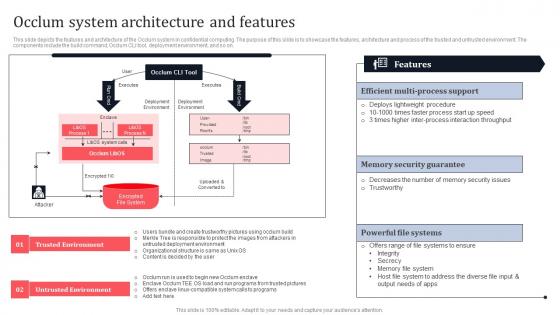
Occlum System Architecture And Features Secure Multi Party Slides Pdf
This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Want to ace your presentation in front of a live audience Our Occlum System Architecture And Features Secure Multi Party Slides Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on.

Future Of Confidential Computing Technology Secure Multi Party Rules Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Slidegeeks has constructed Future Of Confidential Computing Technology Secure Multi Party Rules Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment.
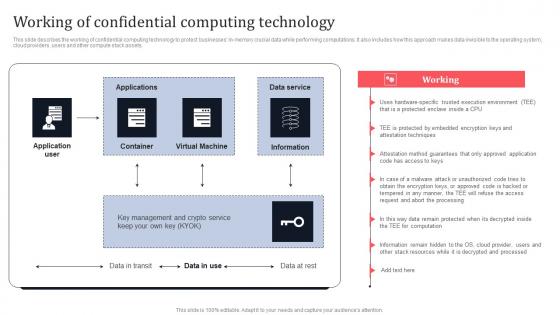
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
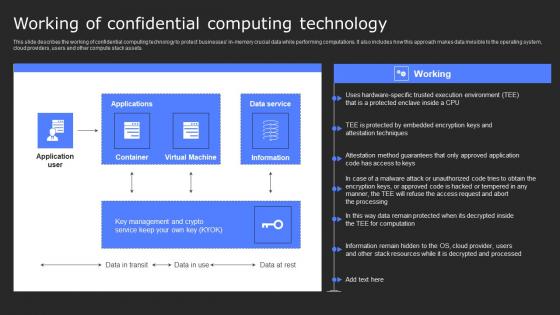
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets.
Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads.
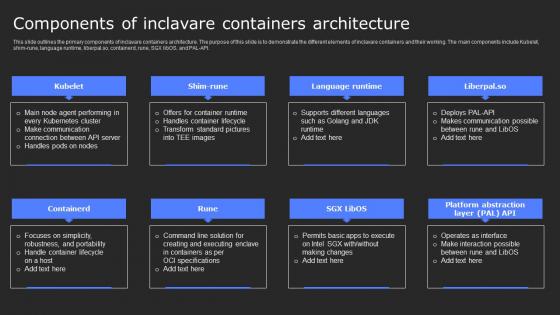
Components Of Inclavare Containers Secure Computing Framework Professional Pdf
This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API. Slidegeeks is here to make your presentations a breeze with Components Of Inclavare Containers Secure Computing Framework Professional Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the primary components of inclavare containers architecture. The purpose of this slide is to demonstrate the different elements of inclavare containers and their working. The main components include Kubelet, shim-rune, language runtime, liberpal.so, containerd, rune, SGX libOS, and PAL-API.
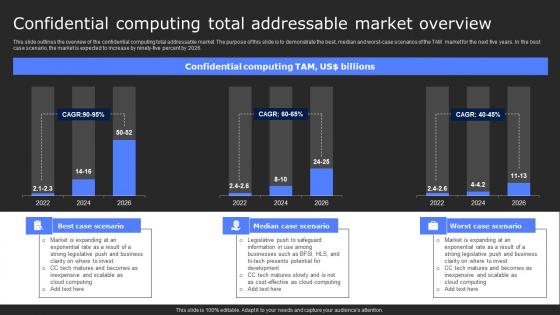
Confidential Computing Total Addressable Secure Computing Framework Themes Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Confidential Computing Total Addressable Secure Computing Framework Themes Pdf from Slidegeeks and deliver a wonderful presentation. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.
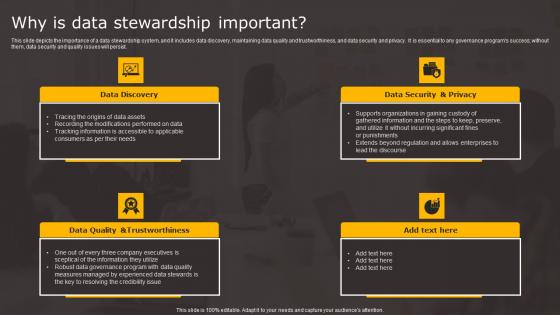
Data Stewardship In Business Processes Why Is Data Stewardship Important Download Pdf
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist. The Data Stewardship In Business Processes Why Is Data Stewardship Important Download Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance programs success without them, data security and quality issues will persist.
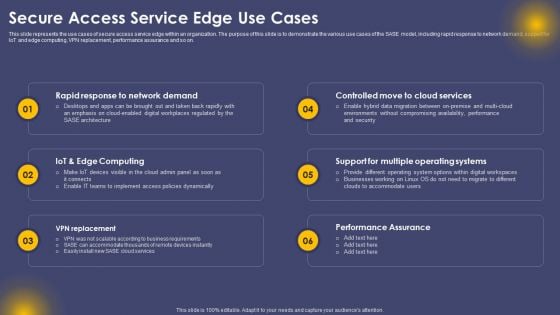
Secure Access Service Edge Use Cases Ppt Outline Images PDF
This slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Explore a selection of the finest Secure Access Service Edge Use Cases Ppt Outline Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Secure Access Service Edge Use Cases Ppt Outline Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Secure Dollar Finance PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with secure dollar Get endorsed by your boss with our Secure Dollar Finance PowerPoint Templates And PowerPoint Backgrounds 0811. Dont pass up this opportunity to shine.

Secure Dollar Finance PowerPoint Themes And PowerPoint Slides 0811
Microsoft PowerPoint Theme and Slide with secure dollar An array of colors give our Secure Dollar Finance PowerPoint Themes And PowerPoint Slides 0811 an alluring blend. They make your thoughts very enticing.
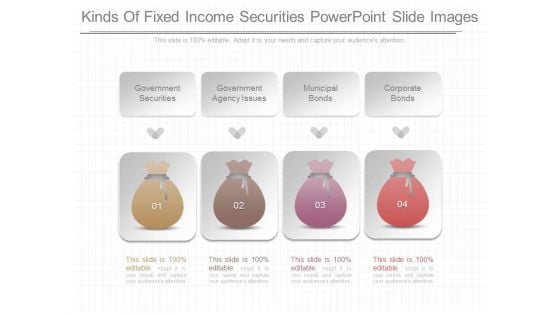
Kinds Of Fixed Income Securities Powerpoint Slide Images
This is a kinds of fixed income securities powerpoint slide images. This is a four stage process. The stages in this process are government securities, government agency issues, municipal bonds, corporate bonds.
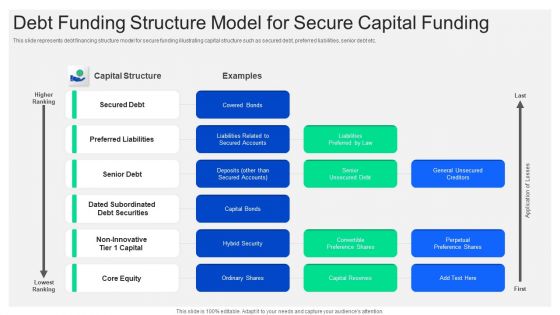
Debt Funding Structure Model For Secure Capital Funding Mockup PDF
This slide represents debt financing structure model for secure funding illustrating capital structure such as secured debt, preferred liabilities, senior debt etc. Showcasing this set of slides titled debt funding structure model for secure capital funding mockup pdf. The topics addressed in these templates are secured debt, capital structure, senior debt. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
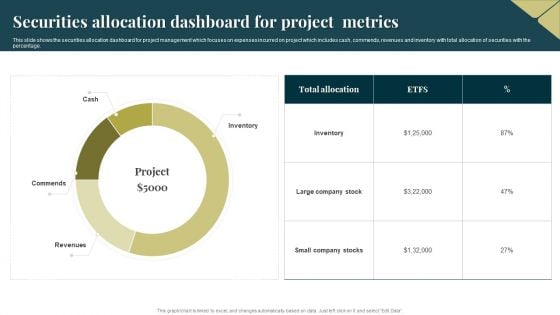
Securities Allocation Dashboard For Project Metrics Information PDF
This slide shows the securities allocation dashboard for project management which focuses on expenses incurred on project which includes cash, commends, revenues and inventory with total allocation of securities with the percentage. Showcasing this set of slides titled Securities Allocation Dashboard For Project Metrics Information PDF. The topics addressed in these templates are Inventory, Project, Revenues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Fixed Income And Leveraged Securities Ppt PowerPoint Presentation Slides Mockup
This is a fixed income and leveraged securities ppt powerpoint presentation slides mockup. This is a four stage process. The stages in this process are business, management, marketing.
Types Of Convertible Securities Ppt PowerPoint Presentation Show Ideas
This is a types of convertible securities ppt powerpoint presentation show ideas. This is a six stage process. The stages in this process are business, management, marketing.

Valuation Of Equity Securities Ppt PowerPoint Presentation Inspiration Outline
This is a valuation of equity securities ppt powerpoint presentation inspiration outline. This is a six stage process. The stages in this process are business, management, marketing.
Types Of Convertible Securities Ppt PowerPoint Presentation Model Portrait
This is a types of convertible securities ppt powerpoint presentation model portrait. This is a six stage process. The stages in this process are business, management, marketing, process.

Types Of Convertible Securities Ppt PowerPoint Presentation File Information
This is a types of convertible securities ppt powerpoint presentation file information. This is a six stage process. The stages in this process are business, management, marketing.
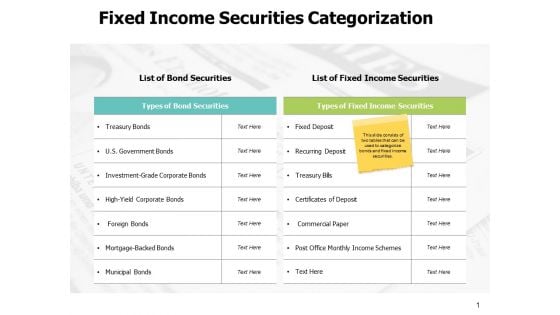
Fixed Income Securities Categorization Ppt PowerPoint Presentation Layout
This is a fixed income securities categorization ppt powerpoint presentation layout. This is a two stage process. The stages in this process are compare, marketing, business, management, planning.
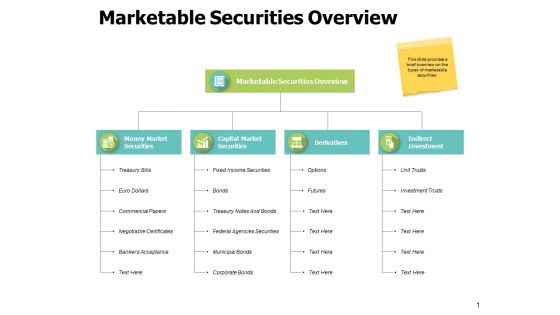
Marketable Securities Overview Ppt PowerPoint Presentation Gallery Demonstration
This is a marketable securities overview ppt powerpoint presentation gallery demonstration. This is a four stage process. The stages in this process are marketing, business, management, planning, strategy.
Secure VPN Vector Icon Ppt PowerPoint Presentation Layouts Images PDF
Pitch your topic with ease and precision using this secure vpn vector icon ppt powerpoint presentation layouts images pdf. This layout presents information on secure vpn vector icon . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Marketable Securities Ppt PowerPoint Presentation Show Images Cpb
Presenting this set of slides with name marketable securities ppt powerpoint presentation show images cpb. This is a three stage process. The stages in this process are marketable securities. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Safely Securing Business Machine Readable Data Ppt Ideas Diagrams PDF
Presenting safely securing business machine readable data ppt ideas diagrams pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including safely securing business machine readable data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Secure Online Banking For Customers Icon Guidelines PDF
Presenting secure online banking for customers icon guidelines pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including secure online banking for customers icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Online Banking For Money Transfer Background PDF
Persuade your audience using this secure online banking for money transfer background pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including secure online banking for money transfer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Virtual Coinage Icon For Secured Payment System Professional PDF
Presenting Virtual Coinage Icon For Secured Payment System Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Virtual Coinage Icon, Secured Payment System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Secure Hybrid Network Ppt PowerPoint Presentation Ideas Slides Cpb
Presenting this set of slides with name secure hybrid network ppt powerpoint presentation ideas slides cpb. This is an editable Powerpoint four stages graphic that deals with topics like secure hybrid network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Secure Network Construction Proposal Example Document Report Doc Pdf Ppt
Heres a predesigned Secure Network Construction Proposal Example Document Report Doc Pdf Ppt for you. Built on extensive research and analysis, this one-complete deck has all the center pieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Secure Network Construction Proposal Example Document Report Doc Pdf Ppt A4 One-pager now.
Timeline Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary Timeline Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Timeline Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.

Person Browsing Securely Internet PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with person sitting on the floor, chatting using a notebook Feed in some energy with our Person Browsing Securely Internet PowerPoint Templates And PowerPoint Backgrounds 0511. Your thoughts will drum up a catchy beat.

Person Browsing Securely Internet PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with person sitting on the floor, chatting using a notebook Pioneer changes with our Person Browsing Securely Internet PowerPoint Themes And PowerPoint Slides 0511. Download without worries with our money back guaranteee.

Income Securities Risk And Return Ppt Background Graphics
This is a income securities risk and return ppt background graphics. This is a four stage process. The stages in this process are cash, fixed interest, property, shares, risk.
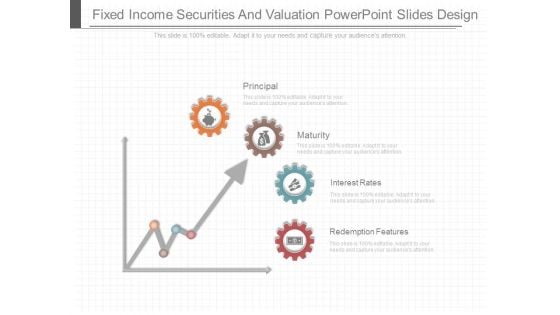
Fixed Income Securities And Valuation Powerpoint Slides Design
This is a fixed income securities and valuation powerpoint slides design. This is a four stage process. The stages in this process are principal, maturity, interest rates, redemption features.

Fixed Income And Leveraged Securities Ppt PowerPoint Presentation File Files
This is a fixed income and leveraged securities ppt powerpoint presentation file files. This is a four stage process. The stages in this process are business, management, marketing, process.
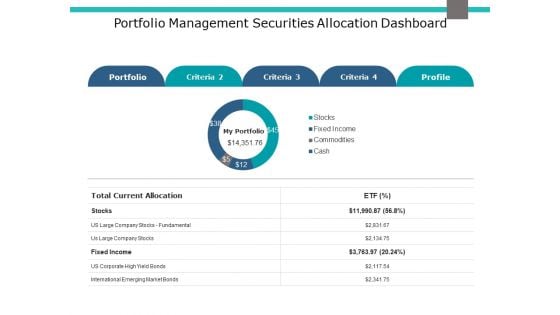
Portfolio Management Securities Allocation Dashboard Ppt PowerPoint Presentation Pictures Objects
This is a portfolio management securities allocation dashboard ppt powerpoint presentation pictures objects. This is a five stage process. The stages in this process are finance, marketing, management, investment.
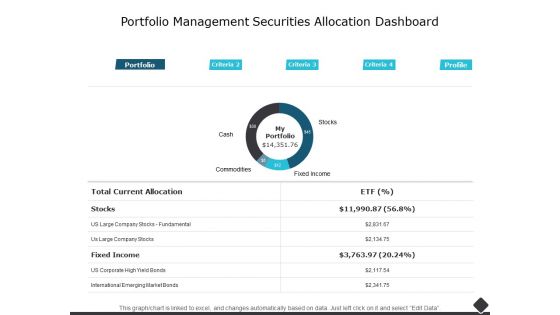
Portfolio Management Securities Allocation Dashboard Ppt PowerPoint Presentation Infographics Examples
This is a portfolio management securities allocation dashboard ppt powerpoint presentation infographics examples. The topics discussed in this diagram are finance, marketing, management, investment, analysis. This is a completely editable PowerPoint presentation, and is available for immediate download.

Valuation Of Equity Securities Ppt PowerPoint Presentation Outline Professional
This is a valuation of equity securities ppt powerpoint presentation outline professional. The topics discussed in this diagram are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation, and is available for immediate download.
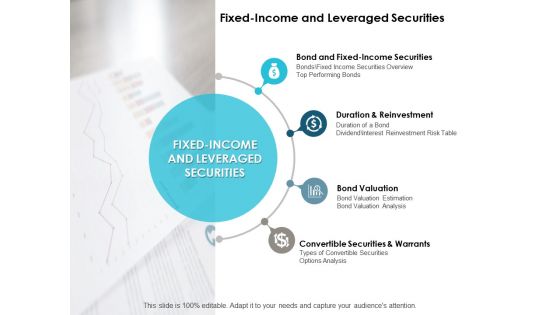
Fixed Income And Leveraged Securities Ppt PowerPoint Presentation Professional Inspiration
This is a fixed income and leveraged securities ppt powerpoint presentation professional inspiration. This is a four stage process. The stages in this process are bond valuation, management, marketing, business, strategy.
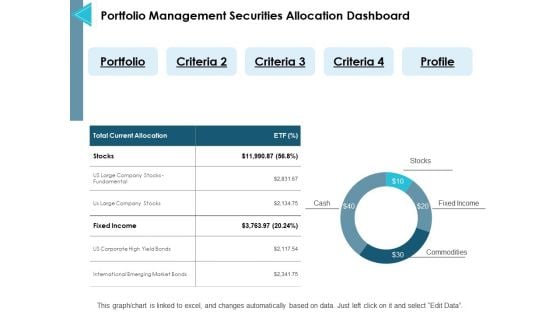
Portfolio Management Securities Allocation Dashboard Ppt PowerPoint Presentation Inspiration Files
This is a portfolio management securities allocation dashboard ppt powerpoint presentation inspiration files. The topics discussed in this diagram are management, marketing, business, strategy, planning. This is a completely editable PowerPoint presentation, and is available for immediate download.
Types Of Convertible Securities Ppt PowerPoint Presentation Layouts Graphics Template
This is a types of convertible securities ppt powerpoint presentation layouts graphics template. This is a six stage process. The stages in this process are management, marketing, business, strategy, process.

Valuation Of Equity Securities Ppt PowerPoint Presentation Inspiration Picture
This is a valuation of equity securities ppt powerpoint presentation inspiration picture. This is a six stage process. The stages in this process are management, marketing, business, strategy, process.
Convertible Fixed Income Securities Ppt PowerPoint Presentation Ideas Example
This is a convertible fixed income securities ppt powerpoint presentation ideas example. This is a six stage process. The stages in this process are marketing, business, management, planning, strategy.


 Continue with Email
Continue with Email

 Home
Home


































