Privacy Security

Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. Create an editable Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Organizing Security Awareness Security Awareness Packages Offered By Third Party Information PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
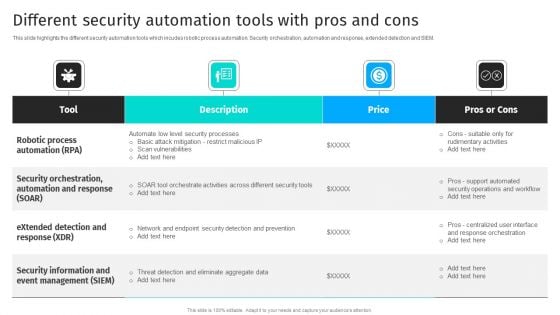
Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF can be your best option for delivering a presentation. Represent everything in detail using Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
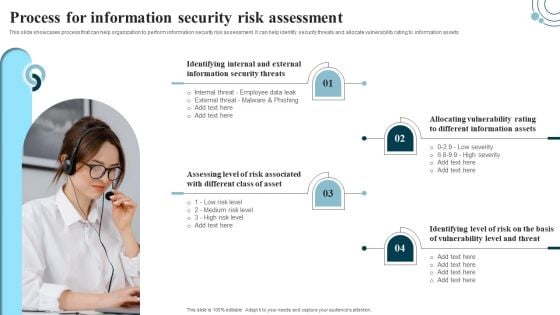
Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF.
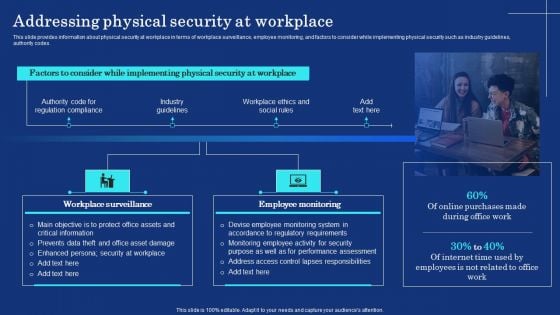
Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF
This slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Create an editable Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
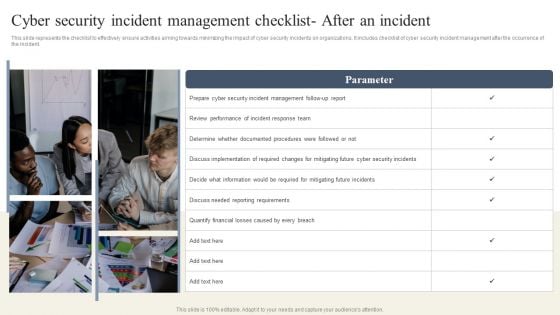
CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Whether you have daily or monthly meetings, a brilliant presentation is necessary. CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF can be your best option for delivering a presentation. Represent everything in detail using CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist After An Incident Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Find highly impressive CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Create an editable CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Implementing Cyber Security Incident Cyber Security Incident Checklist After An Incident Infographics PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Create an editable Implementing Cyber Security Incident Cyber Security Incident Checklist After An Incident Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Cyber Security Incident Checklist After An Incident Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
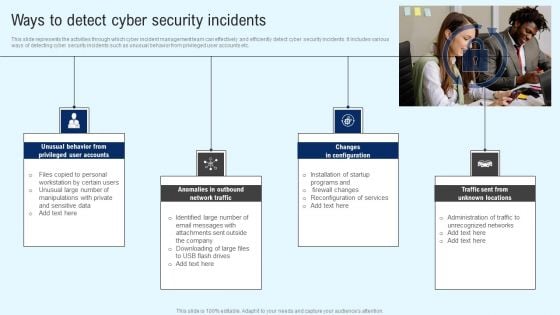
Implementing Cyber Security Incident Ways To Detect Cyber Security Incidents Designs PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Find highly impressive Implementing Cyber Security Incident Ways To Detect Cyber Security Incidents Designs PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cyber Security Incident Ways To Detect Cyber Security Incidents Designs PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
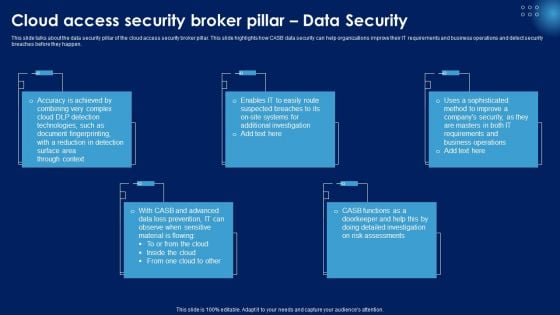
Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Slidegeeks is here to make your presentations a breeze with Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
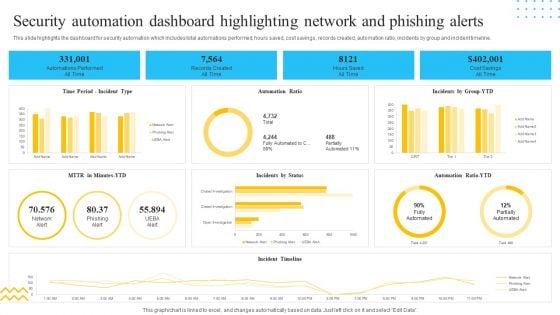
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF bundle. Topics like Records Created, All Time, Hours Saved, Cost Savings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
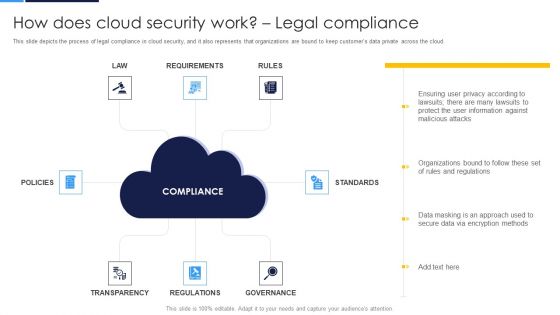
Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Deliver an awe inspiring pitch with this creative Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF bundle. Topics like Provide Limited, Personnel To Protect, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
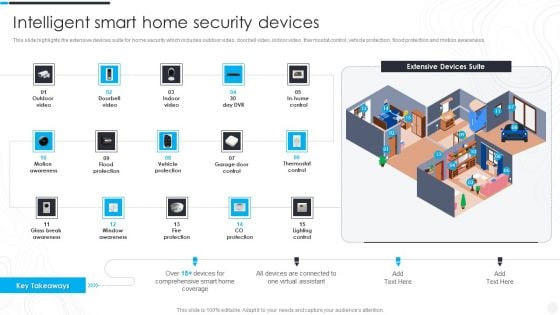
Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF bundle. Topics like Flood Protection, Motion Awareness, Vehicle Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Email Security Encryption And Data Loss Prevention Your Investment For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed investment of your client into various security softwares. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention your investment for e mail security proposal diagrams pdf bundle. Topics like product, free version, starting price, frequency, per user can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Cloud Security Best Practices Ppt Infographic Template Example Topics PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Cloud Security Best Practices Ppt Infographic Template Example Topics PDF. Use them to share invaluable insights onSecure Cloud, Cloud Protection, Cloud Utilization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
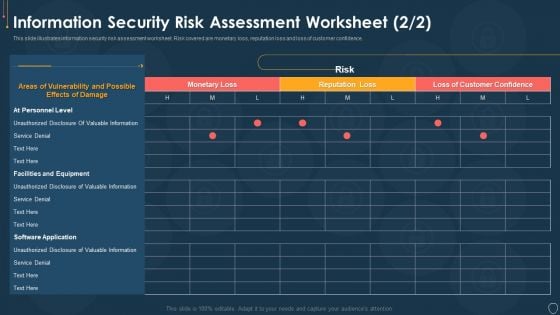
Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Service Graphics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan information security risk assessment worksheet service graphics pdf. Use them to share invaluable insights on monetary loss, reputation loss, loss of customer confidence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
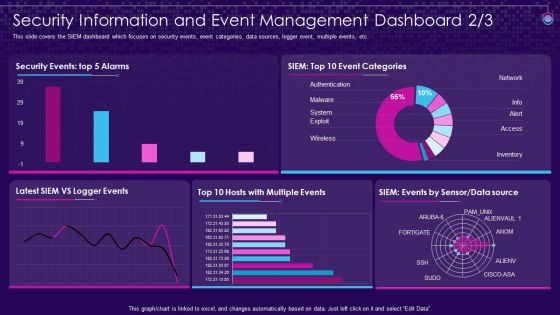
SIEM Services Security Information And Event Management Security Ppt Layouts Ideas PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this siem services security information and event management security ppt layouts ideas pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
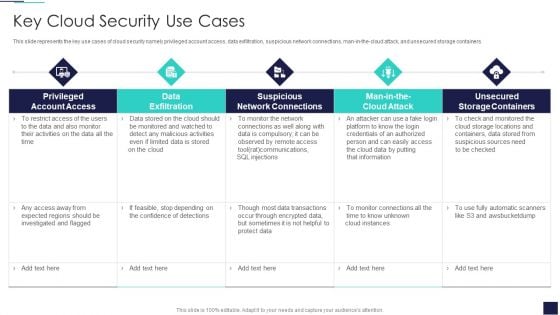
Cloud Information Security Key Cloud Security Use Cases Ppt Gallery Templates PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers. Deliver an awe inspiring pitch with this creative Cloud Information Security Key Cloud Security Use Cases Ppt Gallery Templates PDF bundle. Topics like Privileged Account, Data Exfiltration, Suspicious Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
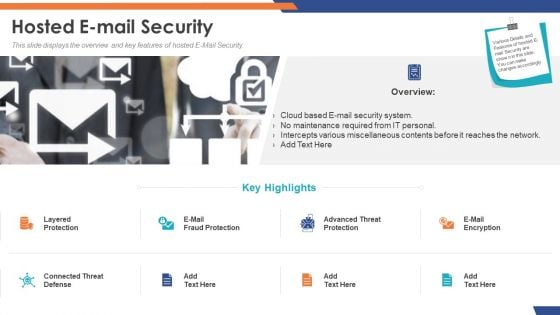
Email Security Market Research Report Hosted E Mail Security Formats PDF
Presenting this set of slides with name email security market research report hosted e mail security formats pdf. This is a two stage process. The stages in this process are cloud based e mail security system, no maintenance required from it personal, intercepts various miscellaneous contents before it reaches the network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Hosted E Mail Security Portrait PDF
Presenting this set of slides with name global cloud based email security market hosted e mail security portrait pdf. This is a two stage process. The stages in this process are cloud based e mail security system, no maintenance required from it personal, intercepts various miscellaneous contents before it reaches the network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
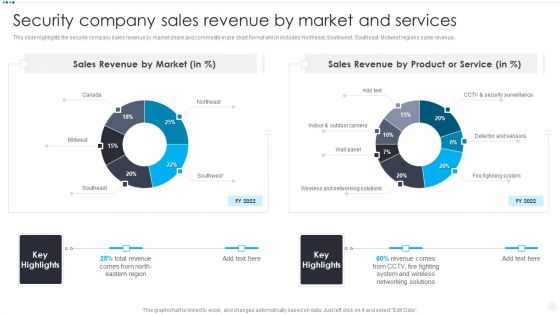
Smart Home Security Solutions Company Profile Security Company Sales Revenue By Market Themes PDF
This slide highlights the security company sales revenue by market share and commodity in pie chart format which includes Northeast, Southwest, Southeast, Midwest regions sales revenue. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Security Company Sales Revenue By Market Themes PDF bundle. Topics like Sales Revenue Market, Sales Revenue Product, Wireless And Networking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
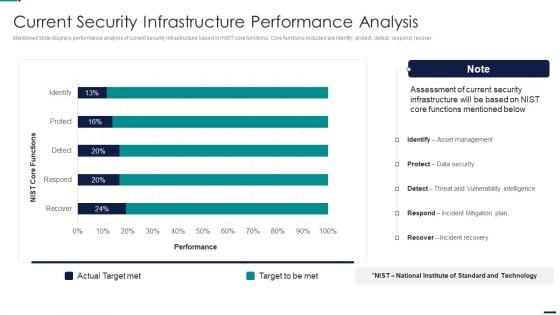
Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Current Security Infrastructure Performance Analysis Pictures PDF. Use them to share invaluable insights on Identify, Protect, Detect, Respond, Recover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
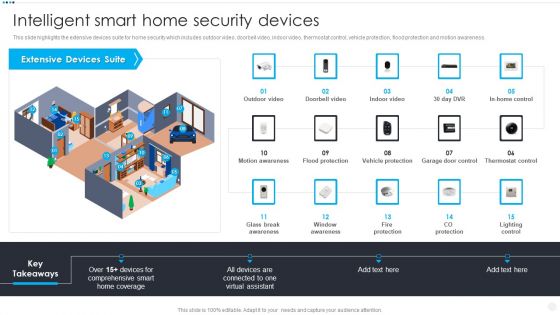
Smart Home Security Solutions Company Profile Intelligent Smart Home Security Devices Inspiration PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Intelligent Smart Home Security Devices Inspiration PDF bundle. Topics like Extensive Devices Suite, Comprehensive Smart Home, Glass Break Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
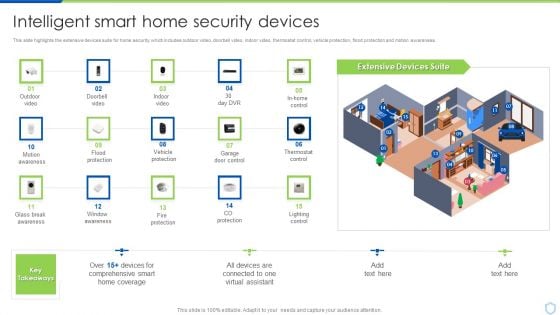
Security And Surveillance Company Profile Intelligent Smart Home Security Devices Brochure PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Intelligent Smart Home Security Devices Brochure PDF bundle. Topics like Awareness Campaign, Empower And Educate, Empowering Lives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
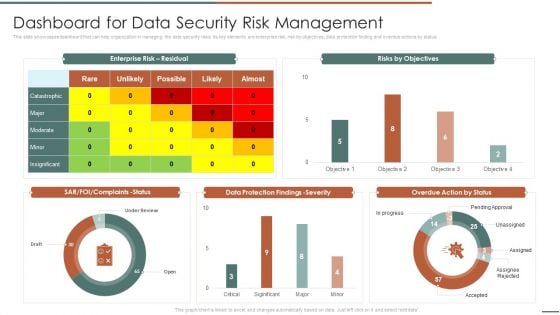
Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF bundle. Topics like Complaints Status, Protection Findings, Overdue Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
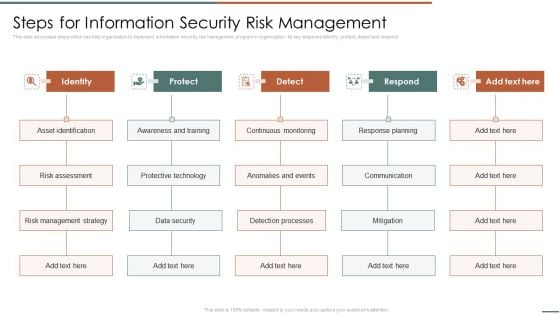
Information Security Risk Evaluation Steps For Information Security Risk Management Themes PDF
This slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Steps For Information Security Risk Management Themes PDF bundle. Topics like Awareness And Training, Protective Technology, Risk Assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
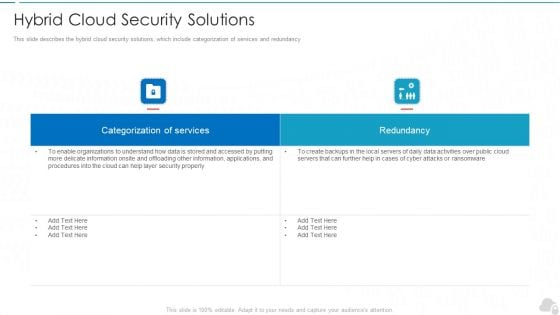
Hybrid Cloud Security Solutions Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
This slide describes the hybrid cloud security solutions, which include categorization of services and redundancy. Deliver an awe inspiring pitch with this creative hybrid cloud security solutions cloud computing security it ppt layouts slide portrait pdf bundle. Topics like categorization of services, redundancy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
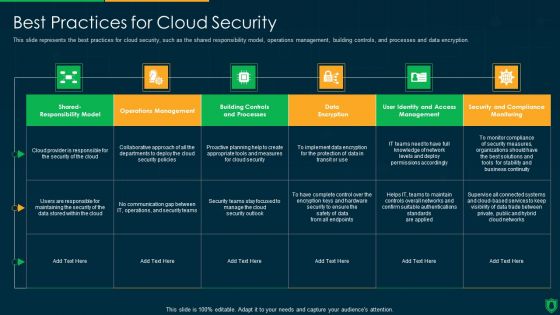
Info Security Best Practices For Cloud Security Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this info security best practices for cloud security ppt powerpoint presentation gallery visual aids pdf. Use them to share invaluable insights on communication gap, data encryption, operations management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
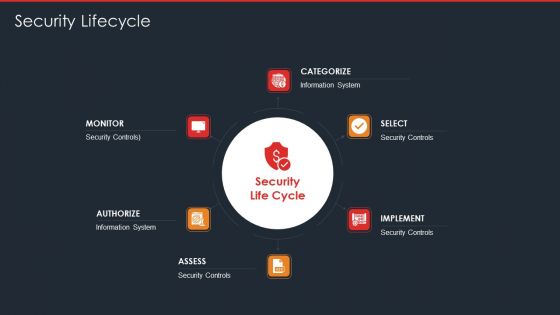
Data Safety Initiatives For Effective IT Security Threats Administration Security Lifecycle Template PDF
This is a data safety initiatives for effective it security threats administration security lifecycle template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information system, security controls, monitor, assess, implement, authorize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
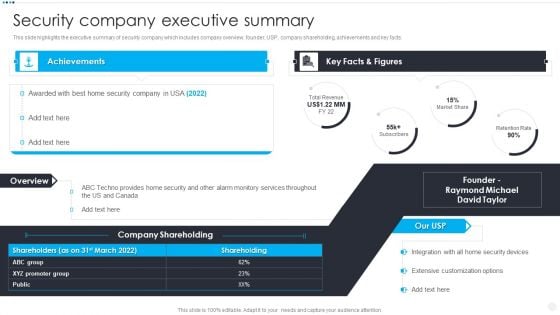
Smart Home Security Solutions Company Profile Security Company Executive Summary Summary PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Security Company Executive Summary Summary PDF. Use them to share invaluable insights on Key Facts Figures, ABC Techno Provides, Monitory Services Throughout and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Security Company Executive Summary Microsoft PDF. Use them to share invaluable insights on Monitory Services, Company Shareholding, Extensive Customization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
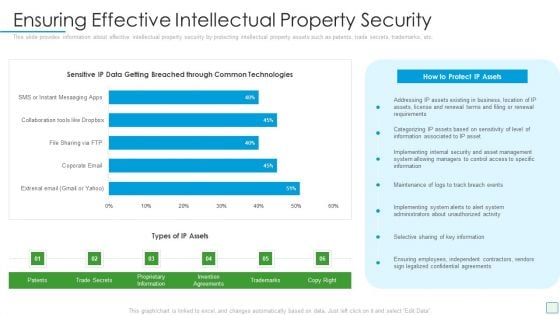
Developing Firm Security Strategy Plan Ensuring Effective Intellectual Property Security Download PDF
This slide provides information about effective intellectual property security by protecting intellectual property assets such as patents, trade secrets, trademarks, etc. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan ensuring effective intellectual property security download pdf. Use them to share invaluable insights on business, management, implementing, maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
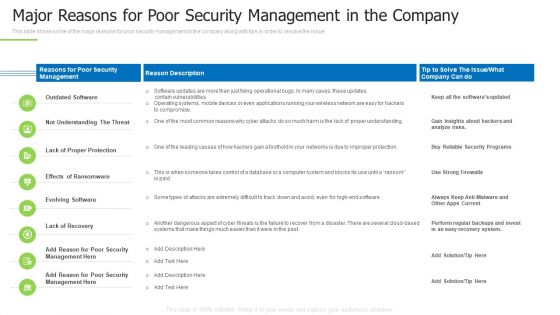
Techniques And Strategies To Reduce Security Management Risks Major Reasons For Poor Security Guidelines PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks major reasons for poor security guidelines pdf bundle. Topics like outdated software, lack of proper protection, another dangerous aspect can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
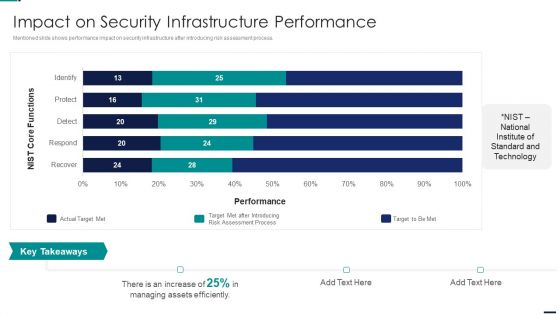
Risk Management Model For Data Security Impact On Security Infrastructure Performance Elements PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Impact On Security Infrastructure Performance Elements PDF. Use them to share invaluable insights on Identify, Protect, Detect, Respond, Recover and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Setting Scenario For Security Control Designs PDF bundle. Topics like Identify, Protect, Detect, Response, Recovery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
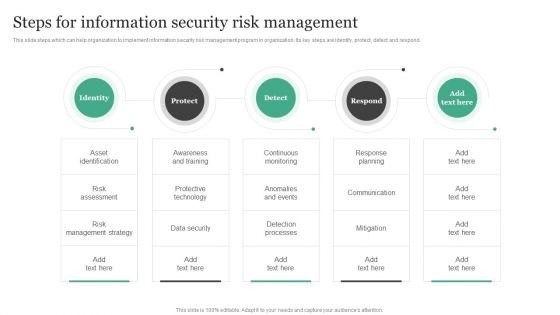
Steps For Information Security Risk Management Information Security Risk Administration Template PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond.There are so many reasons you need a Steps For Information Security Risk Management Information Security Risk Administration Template PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
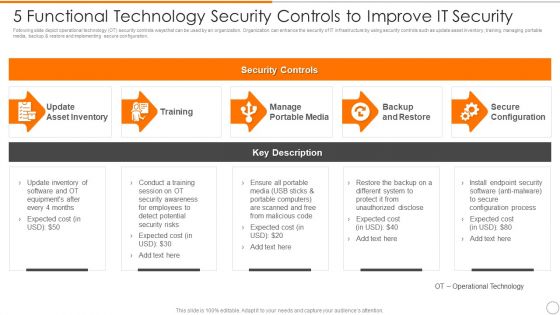
5 Functional Technology Security Controls To Improve IT Security Brochure PDF
Presenting 5 functional technology security controls to improve it security brochure pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including backup and restore, secure configuration, manage portable media. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
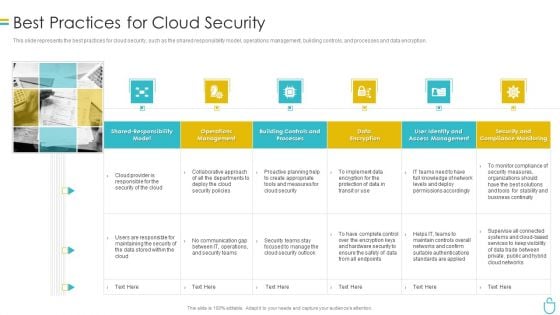
Information Security Best Practices For Cloud Security Ppt Ideas Deck PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting information security best practices for cloud security ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, measures, planning, teams, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
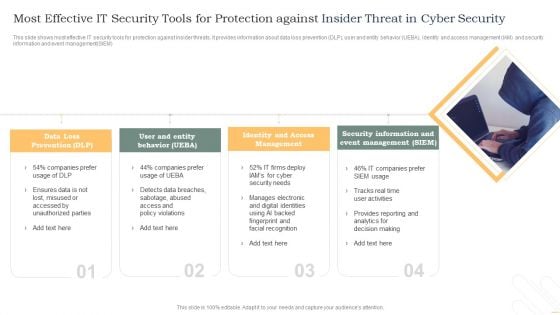
Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF
This slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM. Persuade your audience using this Most Effective It Security Tools For Protection Against Insider Threat In Cyber Security Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Loss Prevention, Identity And Access, Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Enhanced Protection Corporate Event Administration Role Of Security Operations Centre In Security Operations Brochure PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting enhanced protection corporate event administration role of security operations centre in security operations brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational, collaborate, security, analysts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Smart Home Security Solutions Company Profile Our Security Services And Solutions Slides PDF
This slide highlights the security company services which includes CCTV, mobile app and software, occupancy sensor, audio video solution. Co2 monitor, door sensor, leak detector, smoke detector and indoor camera. Presenting Smart Home Security Solutions Company Profile Our Security Services And Solutions Slides PDF to provide visual cues and insights. Share and navigate important information on thirteen stages that need your due attention. This template can be used to pitch topics like CCTV And Security, Wireless And Networking, Storage And Server, Fire Fighting System. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Best Data Security Software Why Us For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software why us for company online database security proposal themes pdf. This is a four stage process. The stages in this process are our team includes elite software engineers and cyber security experts to keep our culture fresh, innovative and energetic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
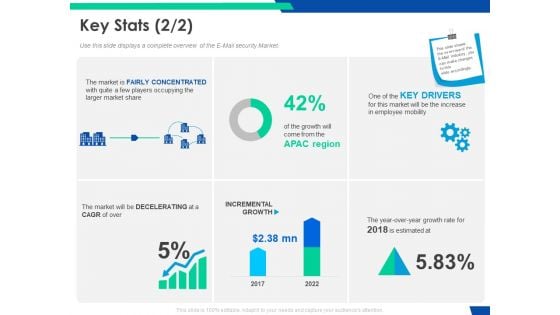
Cloud Based Email Security Market Report Key Stats Security Ppt Slides Demonstration PDF
Use this slide displays a complete overview of the E Mail security Market. Deliver and pitch your topic in the best possible manner with this cloud based email security market report key stats security ppt slides demonstration pdf. Use them to share invaluable insights on key stats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

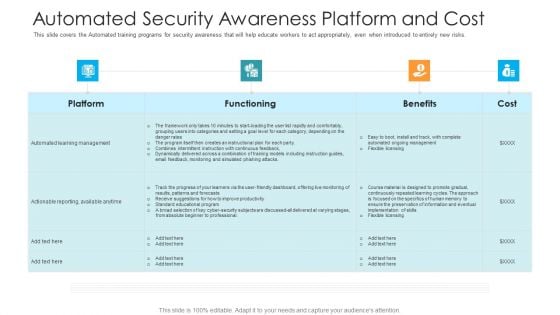
Workforce Security Realization Coaching Plan Automated Security Awareness Platform And Cost Elements PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan automated security awareness platform and cost elements pdf bundle. Topics like platform, functioning, benefits, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
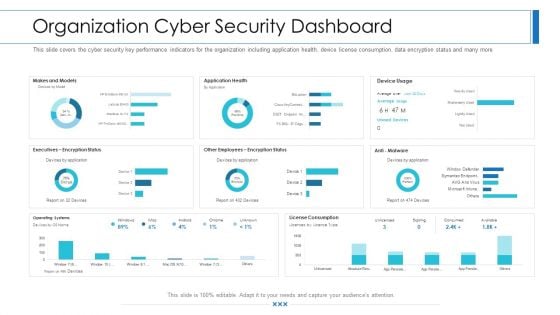
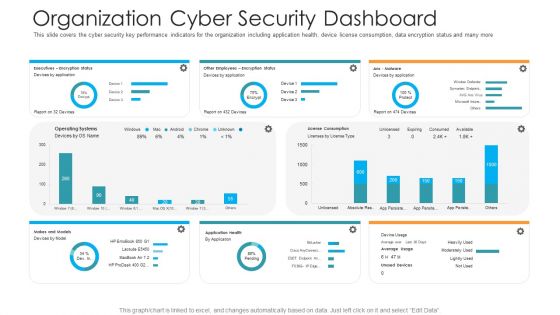
Workforce Security Realization Coaching Plan Organization Cyber Security Dashboard Template PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization cyber security dashboard template pdf bundle. Topics like makes and models, operating systems, encryption status, application health, license consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Automated Security Awareness Platform And Cost Hacking Prevention Awareness Training For IT Security Formats PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe inspiring pitch with this creative automated security awareness platform and cost hacking prevention awareness training for it security formats pdf bundle. Topics like platform, functioning, benefits, cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Training Program Frameworks Contd Hacking Prevention Awareness Training For IT Security Background PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative security training program frameworks contd hacking prevention awareness training for it security background pdf bundle. Topics like management, implement, security policy, monitor can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Organization Cyber Security Dashboard Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver and pitch your topic in the best possible manner with this organization cyber security dashboard hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on executives, license consumption, operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

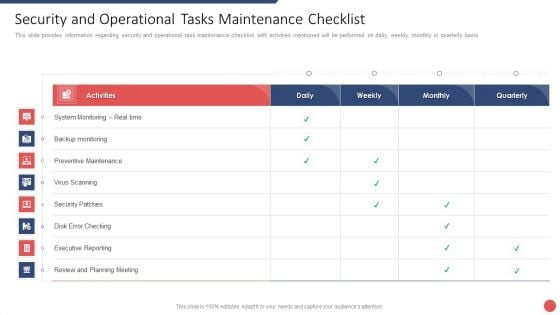
Information And Technology Security Operations Security And Operational Tasks Maintenance Checklist Pictures PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this information and technology security operations security and operational tasks maintenance checklist pictures pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
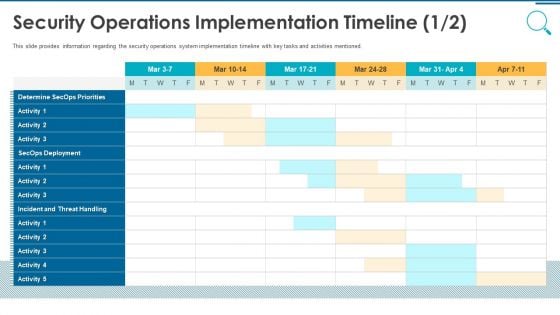
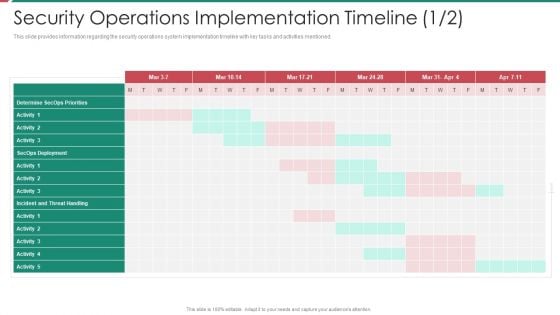
Information And Technology Security Operations Security Operations Implementation Timeline Activity Professional PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative information and technology security operations security operations implementation timeline activity professional pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
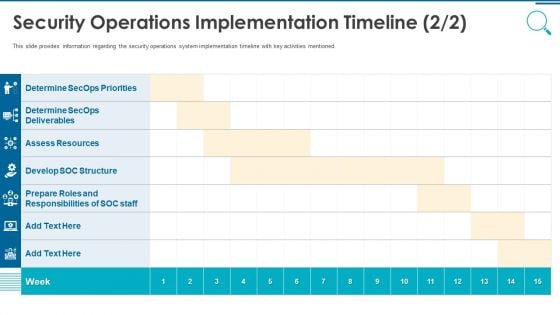
Information And Technology Security Operations Security Operations Implementation Timeline Staff Template PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this information and technology security operations security operations implementation timeline staff template pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
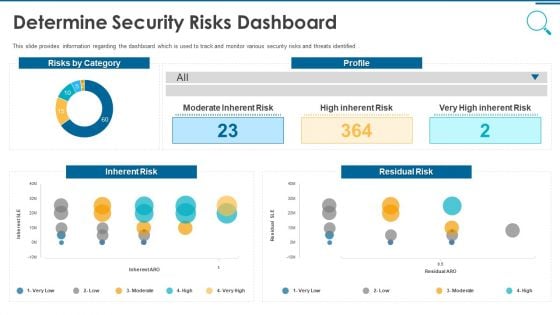
Information And Technology Security Operations Determine Security Risks Dashboard Themes PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified. Deliver and pitch your topic in the best possible manner with this information and technology security operations determine security risks dashboard themes pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizational Security Solutions Security And Operational Tasks Maintenance Checklist Pictures PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this organizational security solutions security and operational tasks maintenance checklist pictures pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
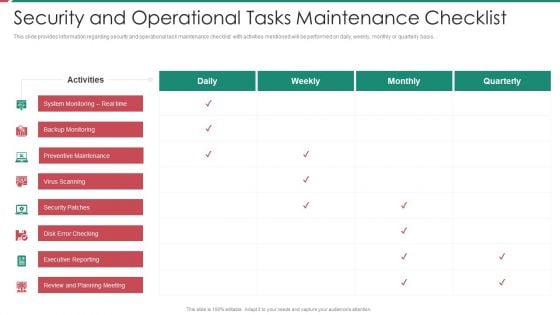
Security Functioning Centre Security And Operational Tasks Maintenance Checklist Inspiration PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security functioning centre security and operational tasks maintenance checklist inspiration pdf. Use them to share invaluable insights on executive reporting, review and planning meeting, system monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security And Process Integration Security And Operational Tasks Maintenance Checklist Diagrams PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security and process integration security and operational tasks maintenance checklist diagrams pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security And Process Integration Security Operations Implementation Timeline Activity Inspiration PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned. Deliver an awe inspiring pitch with this creative security and process integration security operations implementation timeline activity inspiration pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
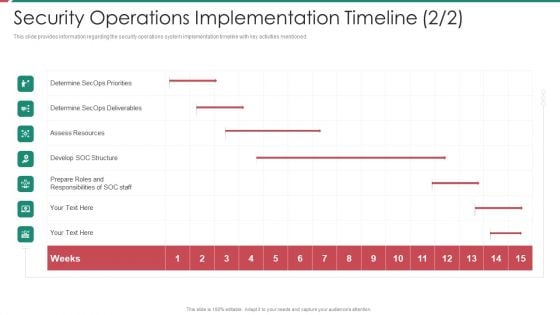
Security And Process Integration Security Operations Implementation Timeline Staff Ideas PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this security and process integration security operations implementation timeline staff ideas pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Defining The Information Security Management System Download PDF
Presenting security management plan steps in detail defining the information security management system download pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like processes, procedures, instructions, implementation, security management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
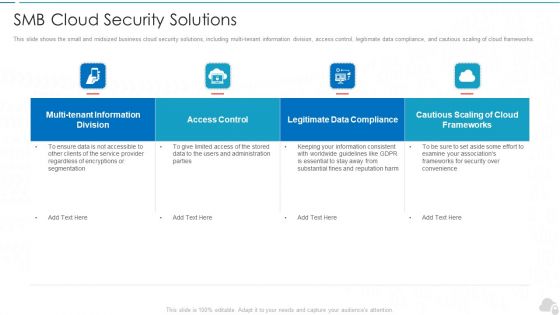
Smb Cloud Security Solutions Cloud Computing Security IT Ppt Portfolio Files PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. Deliver an awe inspiring pitch with this creative smb cloud security solutions cloud computing security it ppt portfolio files pdf bundle. Topics like access control, frameworks, legitimate data compliance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
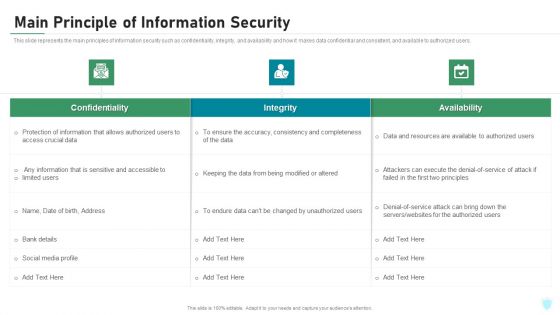
IT Security IT Main Principle Of Information Security Ppt Show Example Topics PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative it security it main principle of information security ppt show example topics pdf bundle. Topics like confidentiality, integrity, availability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


 Continue with Email
Continue with Email

 Home
Home


































