Problem
Cyber Security Breach Icon To Prevent Threat Brochure Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon To Prevent Threat Brochure Pdf This layout presents information on Cyber Security Breach, Icon To Prevent Threat It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Our Cyber Security Breach Icon To Prevent Threat Brochure Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
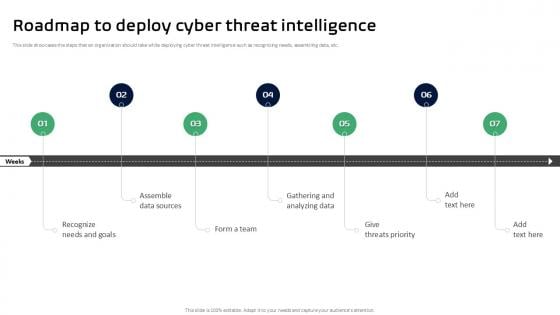
Roadmap To Deploy Cyber Threat Intelligence Ppt Slides
This slide showcases the steps that an organization should take while deploying cyber threat intelligence such as recognizing needs, assembling data, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Roadmap To Deploy Cyber Threat Intelligence Ppt Slides from Slidegeeks and deliver a wonderful presentation. This slide showcases the steps that an organization should take while deploying cyber threat intelligence such as recognizing needs, assembling data, etc.
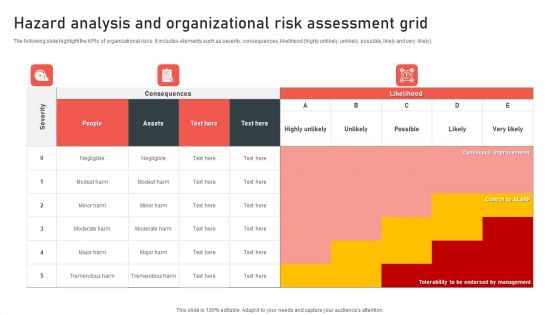
Hazard Analysis And Organizational Risk Assessment Grid Topics PDF
The following slide highlight the KPIs of organizational risks. It includes elements such as severity, consequences, likelihood highly unlikely, unlikely, possible, likely and very likely. Showcasing this set of slides titled Hazard Analysis And Organizational Risk Assessment Grid Topics PDF. The topics addressed in these templates are Hazard Analysis And Organizational, Risk Assessment Grid. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
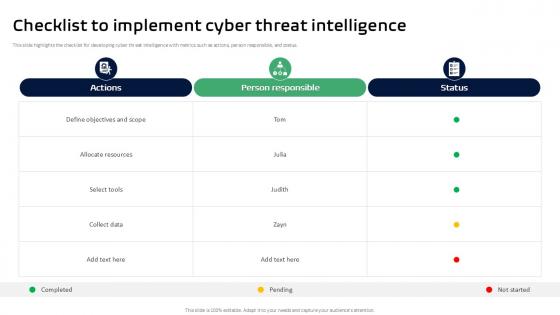
Checklist To Implement Cyber Threat Intelligence Ppt Slides
This slide highlights the checklist for developing cyber threat intelligence with metrics such as actions, person responsible, and status. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Implement Cyber Threat Intelligence Ppt Slides a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Implement Cyber Threat Intelligence Ppt Slides. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights the checklist for developing cyber threat intelligence with metrics such as actions, person responsible, and status.

Various Platforms Of Cyber Threat Intelligence Ppt Slides
This slide discusses the different platforms of cyber threat intelligence which include Anomali ThreatStream, Dataminr Pulse, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Various Platforms Of Cyber Threat Intelligence Ppt Slides to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Various Platforms Of Cyber Threat Intelligence Ppt Slides. This slide discusses the different platforms of cyber threat intelligence which include Anomali ThreatStream, Dataminr Pulse, etc.

Risk Based Methodology Hazard Operability Analysis HAZOP Download PDF
This slide covers quality risk management tool such as Hazard Operability Analysis including deviation, causes, consequences, safeguards and recommendation. Explore a selection of the finest Risk Based Methodology Hazard Operability Analysis HAZOP Download PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Risk Based Methodology Hazard Operability Analysis HAZOP Download PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Solutions To Overcome Organization Resource Planning Challenges Slides Pdf
This slide represents solutions to overcome organization resource planning challenges. This includes unbalanced resources across unbalanced resources, awareness about resources, arbitrary deadlines, and communication issues.Pitch your topic with ease and precision using this Solutions To Overcome Organization Resource Planning Challenges Slides Pdf This layout presents information on Awareness Resources, Communication Issues, Understand Responsibilities It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents solutions to overcome organization resource planning challenges. This includes unbalanced resources across unbalanced resources, awareness about resources, arbitrary deadlines, and communication issues.

Deploy Warehouse Hazard Control And Risk Management Plan Professional PDF
This slide outlines a hazard control and risk management plan for ensuring warehouse safety. It details about potential risk or hazard, likelihood of risk, actions, whom and proof of action. This Deploy Warehouse Hazard Control And Risk Management Plan Professional PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Deploy Warehouse Hazard Control And Risk Management Plan Professional PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
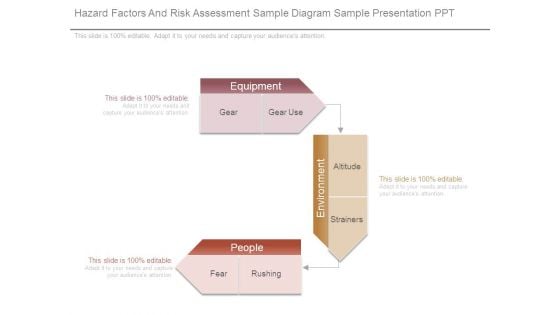
Hazard Factors And Risk Assessment Sample Diagram Sample Presentation Ppt
This is a hazard factors and risk assessment sample diagram sample presentation ppt. This is a three stage process. The stages in this process are equipment, gear, gear use, altitude, strainers, environment, people, fear, rushing.
Data Governance Threats Management Process Ppt Icon Templates PDF
This slide covers governance approach process to manage data risk. It includes steps such as identify risks, develop policies, execute control, monitor and report on control outputs. Presenting Data Governance Threats Management Process Ppt Icon Templates PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Risk, Develop Policy, Develop Control, Execute Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
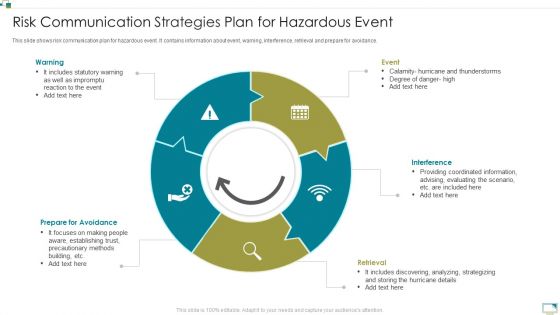
Risk Communication Strategies Plan For Hazardous Event Professional PDF
This slide shows risk communication plan for hazardous event. It contains information about event, warning, interference, retrieval and prepare for avoidance. Presenting Risk Communication Strategies Plan For Hazardous Event Professional PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Warning, Event, Interference, Retrieval, Prepare For Avoidance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cert Insider Threat Reports In Powerpoint And Google Slides Cpb
Introducing our well-designed Cert Insider Threat Reports In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cert Insider Threat Reports. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Cert Insider Threat Reports In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents Web Threat Protection System Ppt Grids
Find highly impressive Table Of Contents Web Threat Protection System Ppt Grids on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Web Threat Protection System Ppt Grids for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now Our Table Of Contents Web Threat Protection System Ppt Grids are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Budget Allocation For Cyber Threat Intelligence Ppt Sample
This slide discusses the budget allocation for cyber threat intelligence design which includes components such as categories, estimated and actual cost. Want to ace your presentation in front of a live audience Our Budget Allocation For Cyber Threat Intelligence Ppt Sample can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide discusses the budget allocation for cyber threat intelligence design which includes components such as categories, estimated and actual cost.

Digital Security Metrics Used By Threat Analysts Graphics Pdf
Showcasing this set of slides titled Digital Security Metrics Used By Threat Analysts Graphics Pdf The topics addressed in these templates are Regulatory Requirements, Large Increase, Scanning Outweighs All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the cybersecurity KPIs used by threat analysts which helps an organization to drive strategic decision making particularly in regard to long term objectives. It include details such as cost per incident, uptime, regulatory requirements, etc.
Obstacles To Entrepreneurial Success Good Ppt Example
This is a obstacles to entrepreneurial success good ppt example. This is a five stage process. The stages in this process are roadmap, signboard, business, marketing.
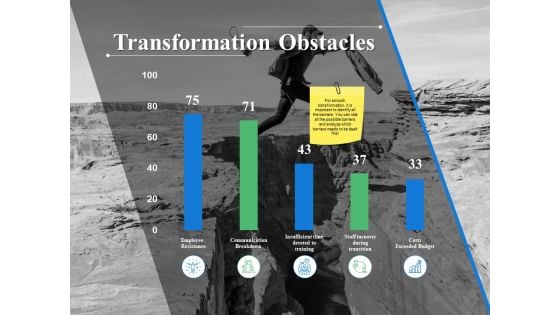
Transformation Obstacles Ppt PowerPoint Presentation Summary Microsoft
This is a transformation obstacles ppt powerpoint presentation summary microsoft. This is a five stage process. The stages in this process are finance, analysis, business, investment, marketing.
Triangular Warning Symbol Vector Icon Ppt PowerPoint Presentation Portfolio Graphics Example
Presenting this set of slides with name triangular warning symbol vector icon ppt powerpoint presentation portfolio graphics example. This is a one stage process. The stages in this process are high low risk, risk con, warning. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
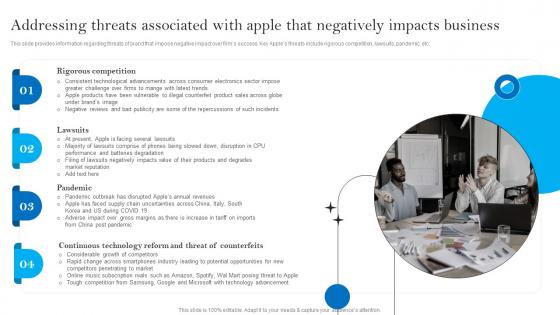
Addressing Threats Associated With Apple Apples Brand Promotional Measures Summary Pdf
This slide provides information regarding threats of brand that impose negative impact over firm success. Key Apple threats include rigorous competition, lawsuits, pandemic, etc. Find a pre-designed and impeccable Addressing Threats Associated With Apple Apples Brand Promotional Measures Summary Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides information regarding threats of brand that impose negative impact over firm success. Key Apple threats include rigorous competition, lawsuits, pandemic, etc.
Addressing Threats Associated Apple Brand Story Journey Of Iconic Enterprise Ideas Pdf
This slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Find a pre designed and impeccable Addressing Threats Associated Apple Brand Story Journey Of Iconic Enterprise Ideas Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc.
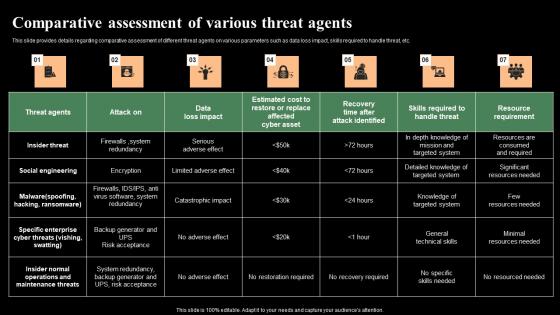
Comparative Assessment Of Various Threat Agents Monitoring Digital Assets Sample Pdf
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Find a pre-designed and impeccable Comparative Assessment Of Various Threat Agents Monitoring Digital Assets Sample Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc.
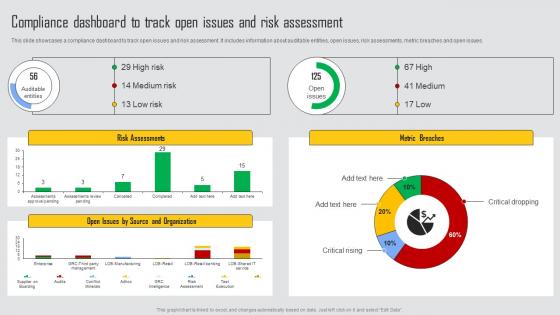
Compliance Dashboard To Track Managing Risks And Establishing Trust Through Efficient Rules Pdf
This slide showcases a compliance dashboard to track open issues and risk assessment. It includes information about auditable entities, open issues, risk assessments, metric breaches and open issues. This modern and well arranged Compliance Dashboard To Track Managing Risks And Establishing Trust Through Efficient Rules Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide showcases a compliance dashboard to track open issues and risk assessment. It includes information about auditable entities, open issues, risk assessments, metric breaches and open issues.
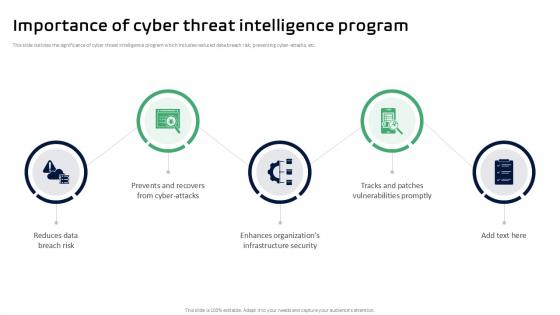
Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides
This slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber attacks, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber attacks, etc.

Checklist To Implement Secure Web Gateway Web Threat Protection System
This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Get a simple yet stunning designed Checklist To Implement Secure Web Gateway Web Threat Protection System. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Checklist To Implement Secure Web Gateway Web Threat Protection System can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor.

Threat Intelligence Framework Powerpoint Presentation Slides PPT Template

Obstacles Solution Ppt PowerPoint Presentation Samples Cpb
Presenting this set of slides with name obstacles solution ppt powerpoint presentation samples cpb. This is a six stage process. The stages in this process are obstacles solution. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Hazard Edifice Pyramid Risk Management Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name hazard edifice pyramid risk management ppt powerpoint presentation complete deck. The topics discussed in these slides are pyramid, risk management, hierarchy, pyramid shape, mutual funds. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
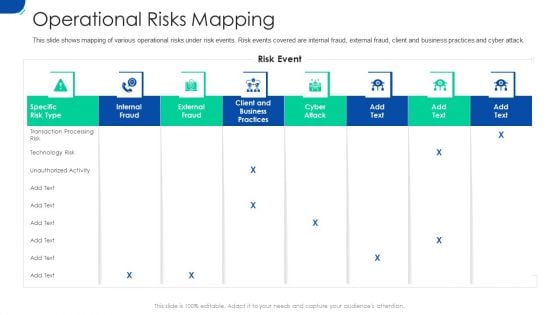
Initiating Hazard Managing Structure Firm Operational Risks Mapping Ideas PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver an awe-inspiring pitch with this creative initiating hazard managing structure firm operational risks mapping ideas pdf bundle. Topics like internal fraud, external fraud, cyber attack, client, business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
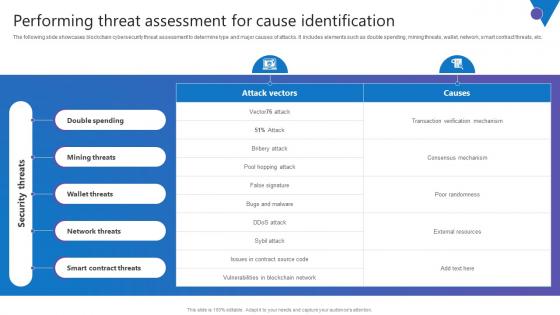
Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf
The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Performing Threat Assessment Comprehensive Guide To Blockchain Digital Security Professional Pdf. The following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc.

Business Management Program Hazards Scoring Template PDF
The following slides provides the various risk associated in a business along with their risk scoring which helps managers to take priority based action for resolution. Key components are risk category, severity, resolving priority, status and additional comments.Showcasing this set of slides titled Business Management Program Hazards Scoring Template PDF. The topics addressed in these templates are Operational Risk, Financial Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
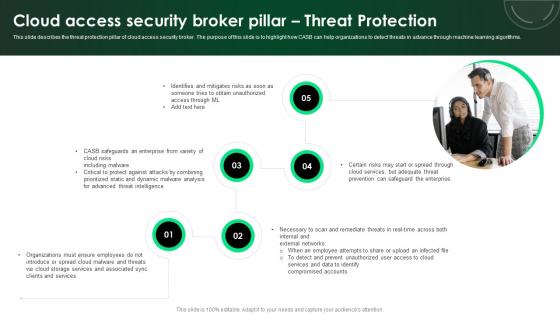
CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Retrieve professionally designed CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms.

Elements Of Anti Fraud Threat Evaluation Program Rules Pdf
This slide showcases the elements of anti fraud risk assessment program which helps an organization to check the prevalence and seriousness of the misconduct.it include details such as risk assessment, tone from the top, training, data analytics. Showcasing this set of slides titled Elements Of Anti Fraud Threat Evaluation Program Rules Pdf The topics addressed in these templates are Risk Assessment, Training, Data Analytics All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the elements of anti fraud risk assessment program which helps an organization to check the prevalence and seriousness of the misconduct.it include details such as risk assessment, tone from the top, training, data analytics.
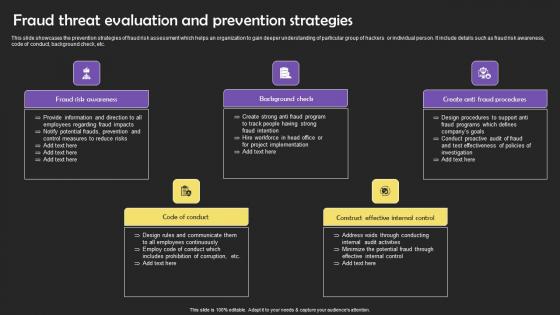
Fraud Threat Evaluation And Prevention Strategies Clipart Pdf
This slide showcases the prevention strategies of fraud risk assessment which helps an organization to gain deeper understanding of particular group of hackers or individual person. It include details such as fraud risk awareness, code of conduct, background check, etc. Showcasing this set of slides titled Fraud Threat Evaluation And Prevention Strategies Clipart Pdf The topics addressed in these templates are Fraud Risk Awareness, Background Check, Code Of Conduct All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases the prevention strategies of fraud risk assessment which helps an organization to gain deeper understanding of particular group of hackers or individual person. It include details such as fraud risk awareness, code of conduct, background check, etc.

Fraud Threat Evaluation Ppt Powerpoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Fraud Threat Evaluation Ppt Powerpoint Presentation Complete Deck With Slides This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twenty three slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now. Our Fraud Threat Evaluation Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Estimated Budget Of Secure Web Gateway Web Threat Protection System
This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Estimated Budget Of Secure Web Gateway Web Threat Protection System can be your best option for delivering a presentation. Represent everything in detail using Estimated Budget Of Secure Web Gateway Web Threat Protection System and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc.
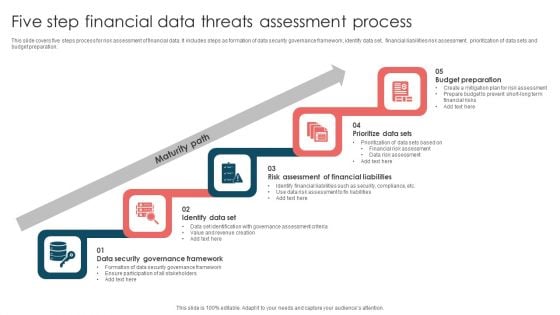
Five Step Financial Data Threats Assessment Process Ppt Infographic Template File Formats PDF
This slide covers five steps process for risk assessment of financial data. It includes steps as formation of data security governance framework, identify data set, financial liabilities risk assessment, prioritization of data sets and budget preparation. Presenting Five Step Financial Data Threats Assessment Process Ppt Infographic Template File Formats PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Maturity Path, Budget Preparation, Prioritize Data Sets, Identify Data Set. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
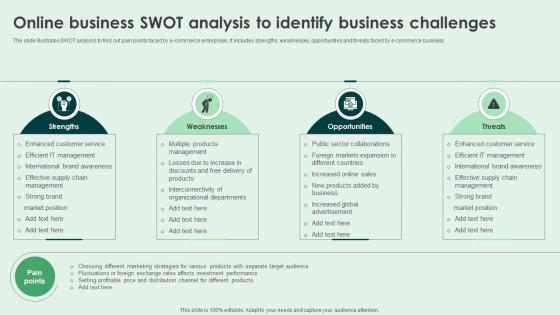
Online Business SWOT Analysis To Identify Business Challenges Brochure Pdf
The slide illustrates SWOT analysis to find out pain points faced by e-commerce enterprises. It includes strengths, weaknesses, opportunities and threats faced by e-commerce business. Showcasing this set of slides titled Online Business SWOT Analysis To Identify Business Challenges Brochure Pdf. The topics addressed in these templates are Strengths, Weaknesses, Opportunities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide illustrates SWOT analysis to find out pain points faced by e-commerce enterprises. It includes strengths, weaknesses, opportunities and threats faced by e-commerce business.
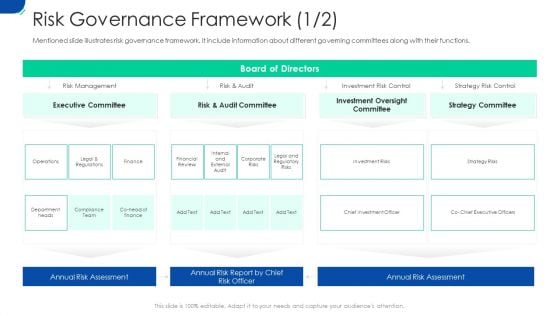
Initiating Hazard Managing Structure Firm Risk Governance Framework Graphics PDF
Mentioned slide illustrates risk governance framework. It include information about different governing committees along with their functions. Deliver and pitch your topic in the best possible manner with this initiating hazard managing structure firm risk governance framework graphics pdf. Use them to share invaluable insights on executive committee, risk and audit committee, investment oversight committee, strategy committee and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Online Business Challenges And Best Practices Brochure Pdf
The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc. Pitch your topic with ease and precision using this Online Business Challenges And Best Practices Brochure Pdf. This layout presents information on Pain Points, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The slide displays pain points in e-commerce along with best practices to prevent facing these issues. It includes challenges such as limited capital, huge marketing efforts, cyber security issues, etc and best practices such as government support, public relation strategy, etc.
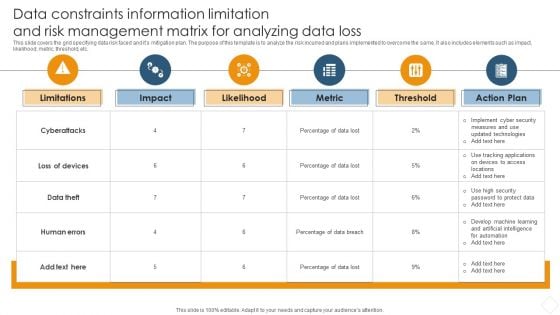
Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF
This slide covers the grid specifying data risk faced and its mitigation plan. The purpose of this template is to analyze the risk incurred and plans implemented to overcome the same. It also includes elements such as impact, likelihood, metric, threshold, etc.Showcasing this set of slides titled Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF. The topics addressed in these templates are Data Distribution, Secure Computation, Verifiable Computation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Enterprise Risk Management And Mitigation Program Enterprise Risk Planning And Management Procedure Icons PDF
This slide represents the process to help management identify potential hazards before they occur and mitigate them timely. It includes steps of ERM such as risk planning, identification, quantification and analysis, evaluation and treatment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Enterprise Risk Management And Mitigation Program Enterprise Risk Planning And Management Procedure Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Enterprise Risk Management And Mitigation Program Enterprise Risk Planning And Management Procedure Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Secure Web Gateway Implementation Scenarios Web Threat Protection System
This slide represents the different types of Secure Web Gateway deployment methods. The purpose of this slide is to outline SWG implementation methodologies. These are inline, explicit, transparent and SPAN Switched Port Analyzer port. isolations, etc. This slide represents the different types of Secure Web Gateway deployment methods. The purpose of this slide is to outline SWG implementation methodologies. These are inline, explicit, transparent and SPAN Switched Port Analyzer port. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Secure Web Gateway Implementation Scenarios Web Threat Protection System for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the different types of Secure Web Gateway deployment methods. The purpose of this slide is to outline SWG implementation methodologies. These are inline, explicit, transparent and SPAN Switched Port Analyzer port. isolations, etc.
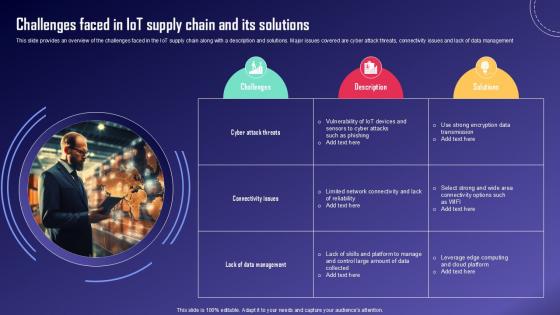
Challenges Faced In IoT Supply IoT Fleet Monitoring Ppt Slide IoT SS V
This slide provides an overview of the challenges faced in the IoT supply chain along with a description and solutions. Major issues covered are cyber attack threats, connectivity issues and lack of data management From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Challenges Faced In IoT Supply IoT Fleet Monitoring Ppt Slide IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide provides an overview of the challenges faced in the IoT supply chain along with a description and solutions. Major issues covered are cyber attack threats, connectivity issues and lack of data management
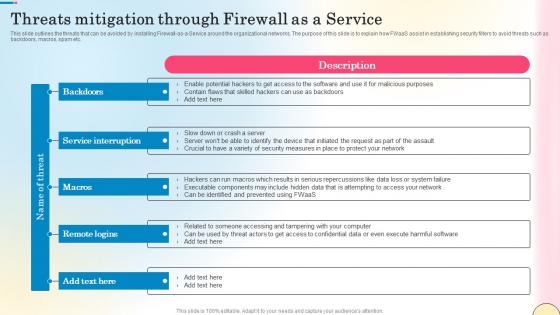
Threats Mitigation Through Firewall As A Service Network Security Guidelines Pdf
This slide outlines the threats that can be avoided by installing Firewall-as-a-Service around the organizational networks. The purpose of this slide is to explain how FWaaS assist in establishing security filters to avoid threats such as backdoors, macros, spam etc. Present like a pro with Threats Mitigation Through Firewall As A Service Network Security Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the threats that can be avoided by installing Firewall-as-a-Service around the organizational networks. The purpose of this slide is to explain how FWaaS assist in establishing security filters to avoid threats such as backdoors, macros, spam etc.
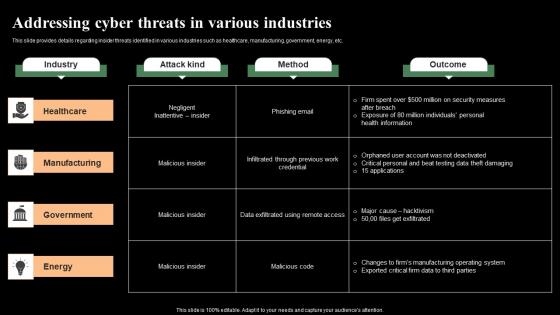
Addressing Cyber Threats In Various Industries Monitoring Digital Assets Designs Pdf
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Slidegeeks has constructed Addressing Cyber Threats In Various Industries Monitoring Digital Assets Designs Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc.
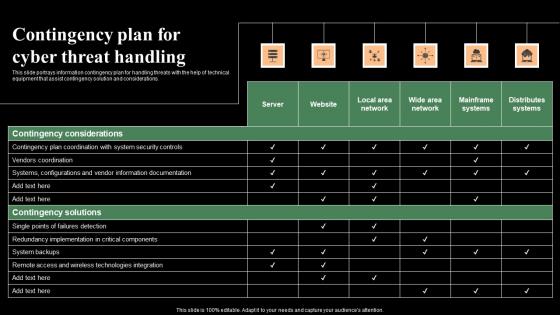
Contingency Plan For Cyber Threat Handling Monitoring Digital Assets Formats Pdf
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Boost your pitch with our creative Contingency Plan For Cyber Threat Handling Monitoring Digital Assets Formats Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations.
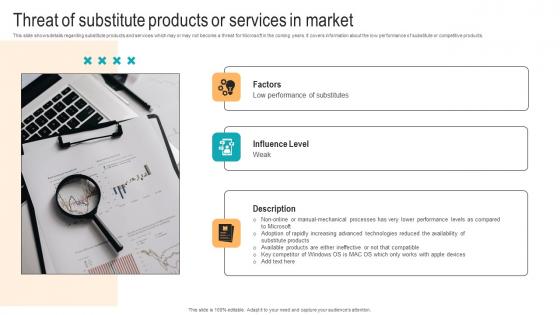
Threat Of Substitute Products Or Services In Market Strategic Advancements By Microsofts Template Pdf
This slide shows details regarding substitute products and services which may or may not become a threat for Microsoft in the coming years. It covers information about the low performance of substitute or competitive products. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Threat Of Substitute Products Or Services In Market Strategic Advancements By Microsofts Template Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide shows details regarding substitute products and services which may or may not become a threat for Microsoft in the coming years. It covers information about the low performance of substitute or competitive products.
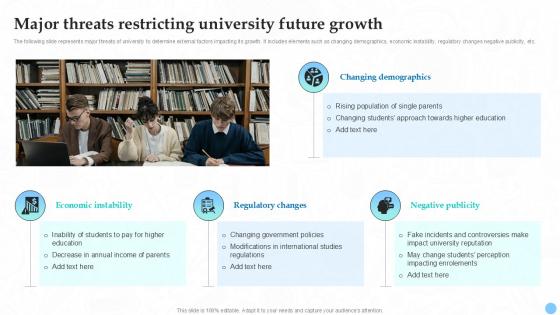
Major Threats Restricting University Future Growth Higher Education Ppt Slides Strategy SS V
The following slide represents major threats of university to determine external factors impacting its growth. It includes elements such as changing demographics, economic instability, regulatory changes negative publicity, etc. Retrieve professionally designed Major Threats Restricting University Future Growth Higher Education Ppt Slides Strategy SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The following slide represents major threats of university to determine external factors impacting its growth. It includes elements such as changing demographics, economic instability, regulatory changes negative publicity, etc.
Risk Based Testing Methodology With Threat Symbol Ppt PowerPoint Presentation Icon Inspiration PDF
Presenting risk based testing methodology with threat symbol ppt powerpoint presentation icon inspiration pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including risk based testing methodology with threat symbol. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
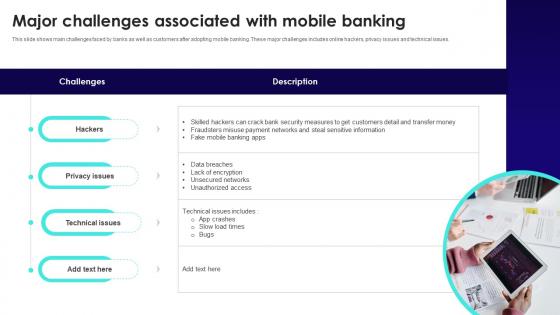
Wireless Banking To Improve Major Challenges Associated With Mobile Fin SS V
This slide shows main challenges faced by banks as well as customers after adopting mobile banking. These major challenges includes online hackers, privacy issues and technical issues. Want to ace your presentation in front of a live audience Our Wireless Banking To Improve Major Challenges Associated With Mobile Fin SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide shows main challenges faced by banks as well as customers after adopting mobile banking. These major challenges includes online hackers, privacy issues and technical issues.
Risk Levels Dashboard Ppt PowerPoint Presentation Icon Files
Presenting this set of slides with name risk levels dashboard ppt powerpoint presentation icon files. This is a one stage process. The stages in this process are hazard symbol, risk icon, risk management icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
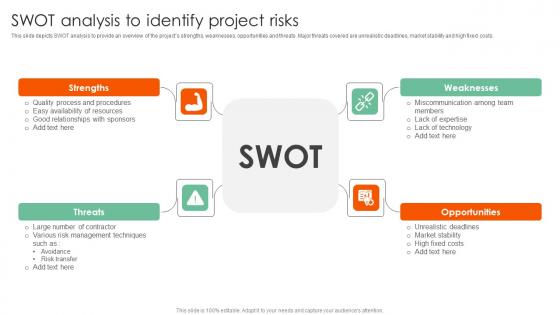
SWOT Analysis To Identify Project Risks Complete Guide On How To Mitigate Formats Pdf
This slide depicts SWOT analysis to provide an overview of the projects strengths, weaknesses, opportunities and threats. Major threats covered are unrealistic deadlines, market stability and high fixed costs. Want to ace your presentation in front of a live audience Our SWOT Analysis To Identify Project Risks Complete Guide On How To Mitigate Formats Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use. This slide depicts SWOT analysis to provide an overview of the projects strengths, weaknesses, opportunities and threats. Major threats covered are unrealistic deadlines, market stability and high fixed costs.
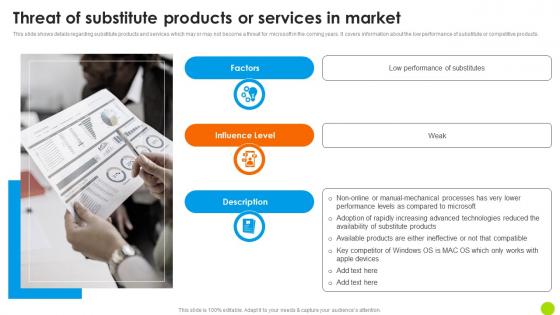
Threat Of Substitute Products Or Services In Market Microsoft Long Term Business Infographics PDF
This slide shows details regarding substitute products and services which may or may not become a threat for microsoft in the coming years. It covers information about the low performance of substitute or competitive products. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Threat Of Substitute Products Or Services In Market Microsoft Long Term Business Infographics PDF can be your best option for delivering a presentation. Represent everything in detail using Threat Of Substitute Products Or Services In Market Microsoft Long Term Business Infographics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide shows details regarding substitute products and services which may or may not become a threat for microsoft in the coming years. It covers information about the low performance of substitute or competitive products.

Micosoft Intensive Growth Threat Of Substitute Products Or Services In Market Strategy SS V
This slide shows details regarding substitute products and services which may or may not become a threat for microsoft in the coming years. It covers information about the low performance of substitute or competitive products. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Micosoft Intensive Growth Threat Of Substitute Products Or Services In Market Strategy SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Micosoft Intensive Growth Threat Of Substitute Products Or Services In Market Strategy SS V today and make your presentation stand out from the rest This slide shows details regarding substitute products and services which may or may not become a threat for microsoft in the coming years. It covers information about the low performance of substitute or competitive products.

Web Threat Protection System Ppt Powerpoint Presentation Complete Deck With Slides

Impact Of Secure Web Gateway On Application Security Web Threat Protection System
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Secure Web Gateway On Application Security Web Threat Protection System template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Secure Web Gateway On Application Security Web Threat Protection System that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc.

Safety Measures To Avoid Common Robotic Accidents In Workspace Introduction PDF
This slide demonstrates the basic precautions to be taken in industries to avoid common robotic accidents. The purpose of this slide is to explain the way in which we can avoid robotic hazards by following some fundamental rules while operating robots in industries. Presenting this PowerPoint presentation, titled Safety Measures To Avoid Common Robotic Accidents In Workspace Introduction PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Safety Measures To Avoid Common Robotic Accidents In Workspace Introduction PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Safety Measures To Avoid Common Robotic Accidents In Workspace Introduction PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Factors Influencing Consumer Risk Assessment Ppt Ideas Show PDF
This slide showcases the overview of the customer risk assessment program to ensure adequate information is collected from the prospective customer before providing services or goods. It includes customer due diligence, periodic monitoring, simplified due diligence, etc. Persuade your audience using this Factors Influencing Consumer Risk Assessment Ppt Ideas Show PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Place Business, Customer Profile, Delivery Channel. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Agile Threat Modeling Overview About Duration Process Guide For Ethical Technology Icons Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Process Guide For Ethical Technology Icons Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Process Guide For Ethical Technology Icons Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc.
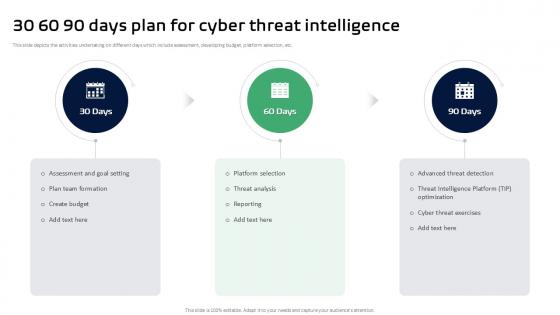
30 60 90 Days Plan For Cyber Threat Intelligence Ppt Slides
This slide depicts the activities undertaking on different days which include assessment, developing budget, platform selection, etc. Find a pre-designed and impeccable 30 60 90 Days Plan For Cyber Threat Intelligence Ppt Slides. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide depicts the activities undertaking on different days which include assessment, developing budget, platform selection, etc.


 Continue with Email
Continue with Email

 Home
Home


































