Problem
Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf
Showcasing this set of slides titled Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf The topics addressed in these templates are Fraud Threat Evaluation, Icon Showcasing Hacker All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. Our Fraud Threat Evaluation Icon Showcasing Hacker Mockup Pdf are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Assessment And Workflow Risks And Mitigation Strategies For Data Center Relocation Icons PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency. This modern and well-arranged Assessment And Workflow Risks And Mitigation Strategies For Data Center Relocation Icons PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
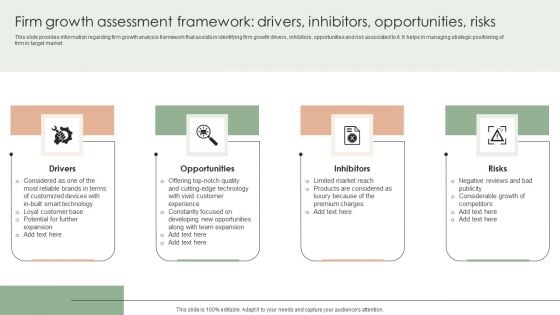
Implementing Effective Strategy Firm Growth Assessment Framework Drivers Themes PDF
This slide provides information regarding firm growth analysis framework that assists in identifying firm growth drivers, inhibitors, opportunities and risk associated to it. It helps in managing strategic positioning of firm in target market. Get a simple yet stunning designed Implementing Effective Strategy Firm Growth Assessment Framework Drivers Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Implementing Effective Strategy Firm Growth Assessment Framework Drivers Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
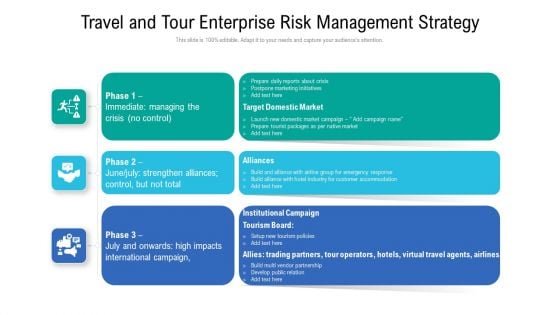
Travel And Tour Enterprise Risk Management Strategy Microsoft PDF
Persuade your audience using this travel and tour enterprise risk management strategy microsoft pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including target domestic market, strengthen, develop. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Challenges In Issue Escalation Management With Solutions Themes PDF
The following slide showcases some common threats in implementing incident escalation. It includes insufficient incident, absence of incident prioritization, inappropriate tools for communication etc. Persuade your audience using this Challenges In Issue Escalation Management With Solutions Themes PDF. This PPT design covers Two stages, thus making it a great tool to use. It also caters to a variety of topics including Insufficient Incident Context, Absence Of Incident. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Product Branding Strategy Of Apple Addressing Threats Associated Download Pdf
This slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Product Branding Strategy Of Apple Addressing Threats Associated Download Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc.
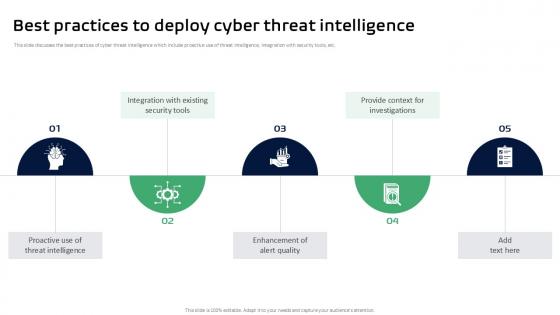
Best Practices To Deploy Cyber Threat Intelligence Ppt Slides
This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices To Deploy Cyber Threat Intelligence Ppt Slides for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc.
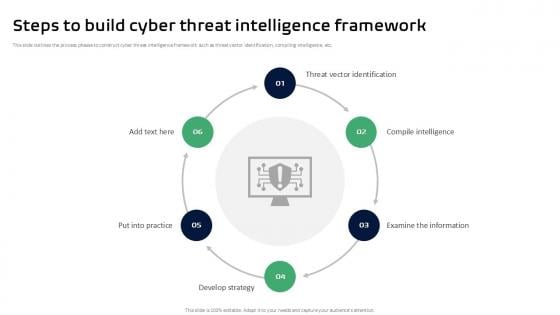
Steps To Build Cyber Threat Intelligence Framework Ppt Sample
This slide outlines the process phases to construct cyber threat intelligence framework such as threat vector identification, compiling intelligence, etc. The Steps To Build Cyber Threat Intelligence Framework Ppt Sample is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide outlines the process phases to construct cyber threat intelligence framework such as threat vector identification, compiling intelligence, etc.
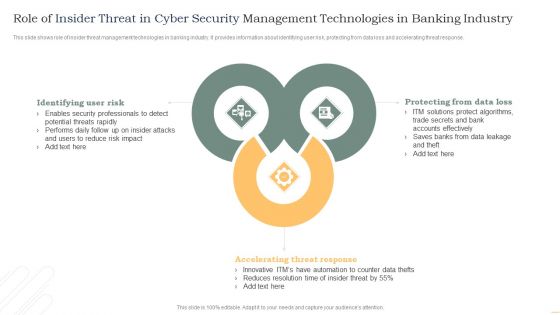
Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF
This slide shows role of insider threat management technologies in banking industry. It provides information about identifying user risk, protecting from data loss and accelerating threat response. Presenting Role Of Insider Threat In Cyber Security Management Technologies In Banking Industry Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Identifying User Risk, Accelerating Threat Response, Protecting Data Loss. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Case Competition Petroleum Sector Issues Major Risks And Risk Management Strategies Ppt Gallery Portfolio PDF
The slide provides the major risks faced by the oil and gas companies along with type of risk and risk mitigation strategies. Key risk include commodity price, natural disasters, industrial accidents, political instability, resources availability etc. Deliver and pitch your topic in the best possible manner with this case competition petroleum sector issues major risks and risk management strategies ppt gallery portfolio pdf. Use them to share invaluable insights on commodity price, production cycle, risk mitigation strategy, property and business, technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
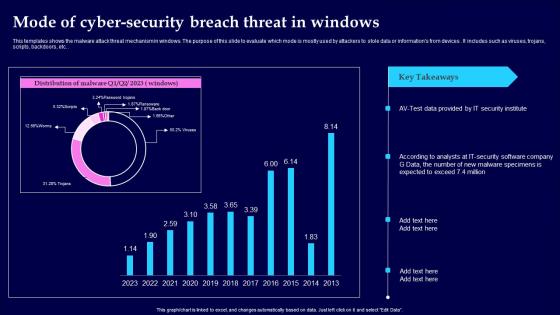
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc.
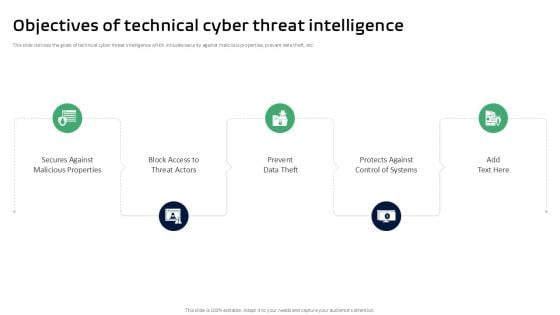
Objectives Of Technical Cyber Threat Intelligence Ppt Slides
This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc. This Objectives Of Technical Cyber Threat Intelligence Ppt Slides is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Objectives Of Technical Cyber Threat Intelligence Ppt Slides features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc.
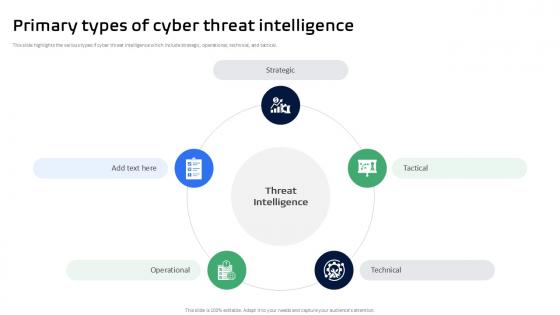
Primary Types Of Cyber Threat Intelligence Ppt Template
This slide highlights the various types if cyber threat intelligence which include strategic, operational, technical, and tactical. Explore a selection of the finest Primary Types Of Cyber Threat Intelligence Ppt Template here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Primary Types Of Cyber Threat Intelligence Ppt Template to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide highlights the various types if cyber threat intelligence which include strategic, operational, technical, and tactical.
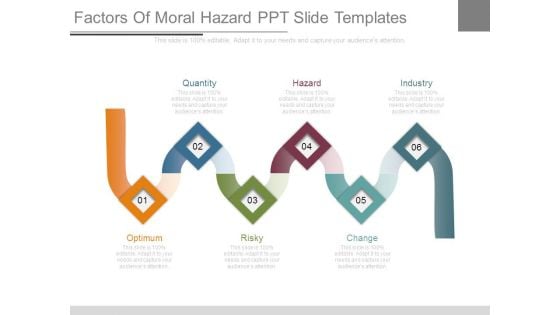
Factors Of Moral Hazard Ppt Slide Templates
This is a factors of moral hazard ppt slide templates. This is a six stage process. The stages in this process are quantity, hazard, industry, optimum, risky, change.
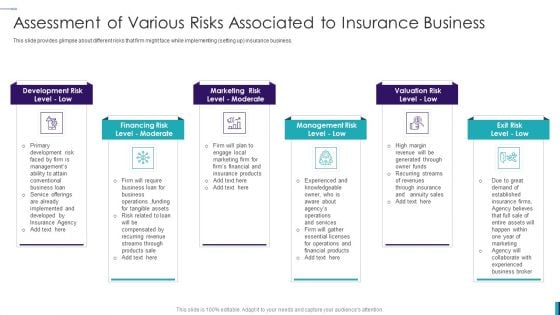
Establishing Insurance Company Assessment Of Various Risks Associated To Insurance Business Diagrams PDF
This slide provides glimpse about different risks that firm might face while implementing setting up insurance business. Presenting Establishing Insurance Company Assessment Of Various Risks Associated To Insurance Business Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Development Risk, Marketing Risk, Valuation Risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
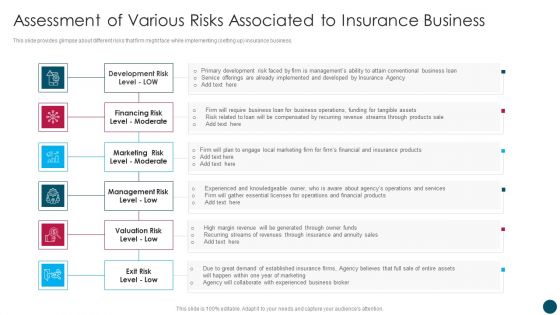
Insurance And Financial Product Assessment Of Various Risks Associated To Insurance Business Download PDF
This slide provides glimpse about different risks that firm might face while implementing setting up insurance business. This is a Insurance And Financial Product Assessment Of Various Risks Associated To Insurance Business Download PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Risk, Financing Risk, Marketing Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Assessment Highlighting Indicators And Implications Ppt PowerPoint Presentation Gallery Elements PDF
This slide focuses on the risk scenario that highlights leading indicators, scenario and emerging risks, business implications, etc. Which covers high inflation, increasing taxes and spending by government, etc. That helps in making risk control strategies by company. Persuade your audience using this Risk Assessment Highlighting Indicators And Implications Ppt PowerPoint Presentation Gallery Elements PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Leading Indications, Scenario Emerging Risk, Business Implications. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Obstacles To Effectiveness Legal Compliance Tactics Background PDF
The following slide highlights hindrances to legal compliance strategy to mitigate risks ad adhering to regulations. It includes strategies such s insufficient innovative technology, multiple silos, global regulations and unstructured data. Presenting Obstacles To Effectiveness Legal Compliance Tactics Background PDF to dispense important information. This template comprises yyyyyyyyyyyyyyyyyyyyyy stages. It also presents valuable insights into the topics including Insufficient Innovative Technology, Multiple Silos, Global Regulations . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

SWOT Analysis Of IBN Outsourcing Company Threats PPT Presentation SS
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Intense Competition , Declining Customer Retention Rate, Government Regulations and Political Instability etc. Retrieve professionally designed SWOT Analysis Of IBN Outsourcing Company Threats PPT Presentation SS to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Intense Competition , Declining Customer Retention Rate, Government Regulations and Political Instability etc.
Stereotype Threat In Powerpoint And Google Slides Cpb
Introducing our well-designed Stereotype Threat In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Stereotype Threat. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Stereotype Threat In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Threats Internal Validity In Powerpoint And Google Slides Cpb
Introducing our well-designed Threats Internal Validity In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Threats Internal Validity. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience. Our Threats Internal Validity In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Table Of Contents For Web Threat Protection System Ppt Formates
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Table Of Contents For Web Threat Protection System Ppt Formates can be your best option for delivering a presentation. Represent everything in detail using Table Of Contents For Web Threat Protection System Ppt Formates and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. Our Table Of Contents For Web Threat Protection System Ppt Formates are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
History Threat Internal Validity In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled History Threat Internal Validity In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits History Threat Internal Validity that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design. Our History Threat Internal Validity In Powerpoint And Google Slides Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
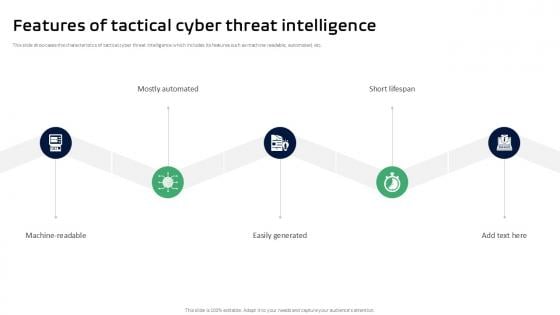
Features Of Tactical Cyber Threat Intelligence Ppt Template
This slide showcases the characteristics of tactical cyber threat intelligence which includes its features such as machine readable, automated, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Features Of Tactical Cyber Threat Intelligence Ppt Template and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the characteristics of tactical cyber threat intelligence which includes its features such as machine readable, automated, etc.
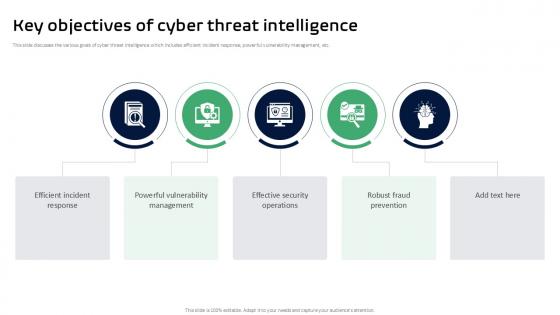
Key Objectives Of Cyber Threat Intelligence Ppt Sample
This slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Objectives Of Cyber Threat Intelligence Ppt Sample to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc.

Agenda For Web Threat Protection System Ppt Infographics
Boost your pitch with our creative Agenda For Web Threat Protection System Ppt Infographics. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Our Agenda For Web Threat Protection System Ppt Infographics are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
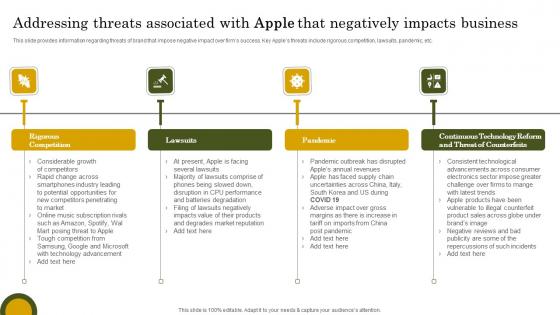
Addressing Threats Associated Apple Branding Strategy To Become Market Leader Themes Pdf
This slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Find a pre designed and impeccable Addressing Threats Associated Apple Branding Strategy To Become Market Leader Themes Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc.
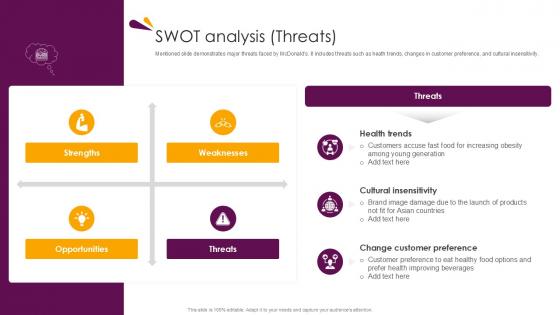
Swot Analysis Threats Food And Beverages Company Profile Ppt Sample CP SS V
Mentioned slide demonstrates major threats faced by McDonalds. it includes threats such as heath trends, changes in customer preference, and cultural insensitivity. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Swot Analysis Threats Food And Beverages Company Profile Ppt Sample CP SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. Mentioned slide demonstrates major threats faced by McDonalds. it includes threats such as heath trends, changes in customer preference, and cultural insensitivity.
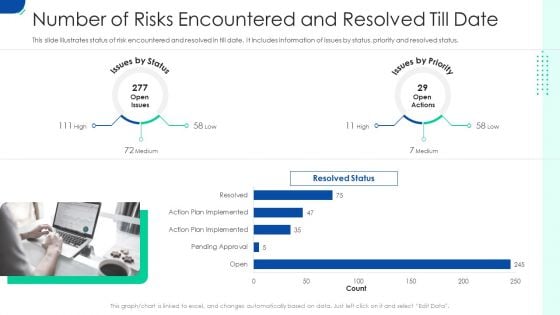
Initiating Hazard Managing Structure Firm Number Of Risks Encountered And Resolved Till Date Infographics PDF
This slide illustrates status of risk encountered and resolved in till date. It includes information of issues by status, priority and resolved status. Deliver and pitch your topic in the best possible manner with this initiating hazard managing structure firm number of risks encountered and resolved till date infographics pdf. Use them to share invaluable insights on number of risks encountered and resolved till date and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
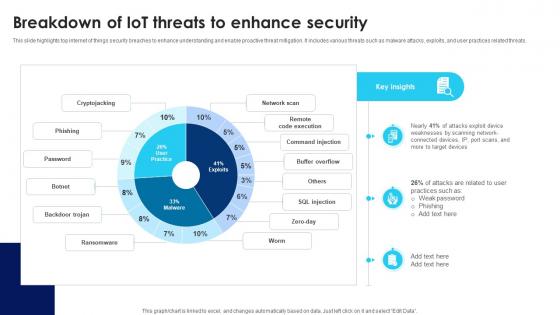
Building Trust With IoT Security Breakdown Of IoT Threats To Enhance Security IoT SS V
This slide highlights top internet of things security breaches to enhance understanding and enable proactive threat mitigation. It includes various threats such as malware attacks, exploits, and user practices related threats. Present like a pro with Building Trust With IoT Security Breakdown Of IoT Threats To Enhance Security IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide highlights top internet of things security breaches to enhance understanding and enable proactive threat mitigation. It includes various threats such as malware attacks, exploits, and user practices related threats.
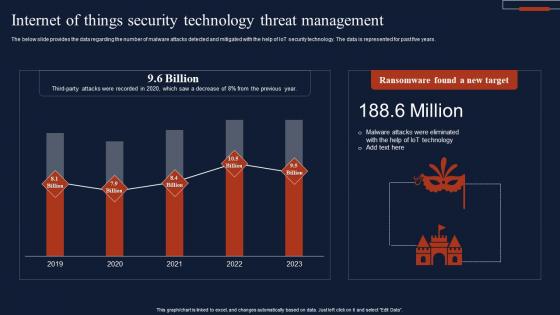
Internet Of Things Security Technology Threat Management Summary Pdf
The below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years. Pitch your topic with ease and precision using this Internet Of Things Security Technology Threat Management Summary Pdf This layout presents information on Ransomware Found, New Target, Threat Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years.
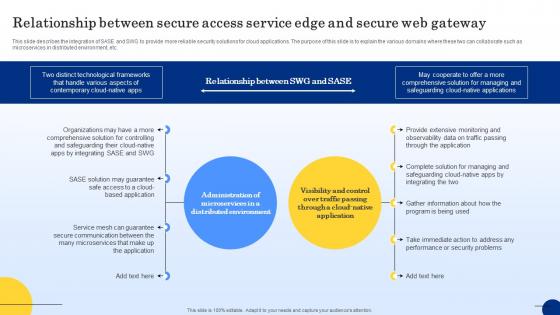
Relationship Between Secure Access Service Edge Web Threat Protection System
This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Presenting this PowerPoint presentation, titled Relationship Between Secure Access Service Edge Web Threat Protection System, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Relationship Between Secure Access Service Edge Web Threat Protection System. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Relationship Between Secure Access Service Edge Web Threat Protection System that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc.
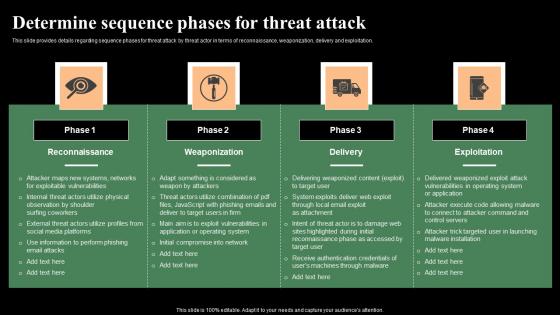
Determine Sequence Phases For Threat Attack Monitoring Digital Assets Infographics Pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Create an editable Determine Sequence Phases For Threat Attack Monitoring Digital Assets Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Determine Sequence Phases For Threat Attack Monitoring Digital Assets Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation.

Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks.
Business Environment Risk Intelligence Management Motivation Risk Management Ppt PowerPoint Presentation Icon Show
This is a business environment risk intelligence management motivation risk management ppt powerpoint presentation icon show. This is a four stage process. The stages in this process are business environment risk intelligence, management motivation, risk management.
Secure Web Gateway Performance Tracking Dashboard Web Threat Protection System
Want to ace your presentation in front of a live audience Our Secure Web Gateway Performance Tracking Dashboard Web Threat Protection System can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents a dashboard to maintain the record of various functions of Secure Web Gateway. The main components are top blocked web malware, web usage trend, top web application categories, risky web
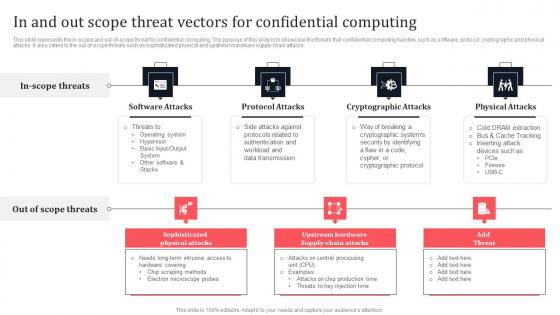
In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the In And Out Scope Threat Vectors For Confidential Computing Secure Multi Party Elements Pdf This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.
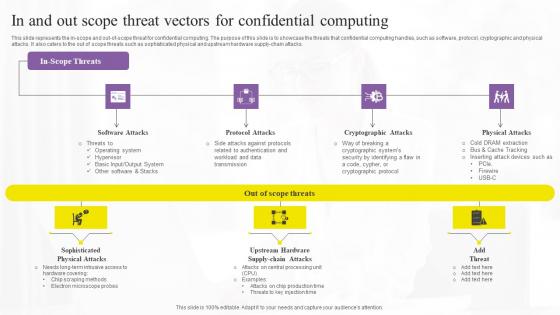
In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Are you searching for a In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download In And Out Scope Threat Vectors For Confidential Computing Technologies Infographics Pdf from Slidegeeks today. This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.
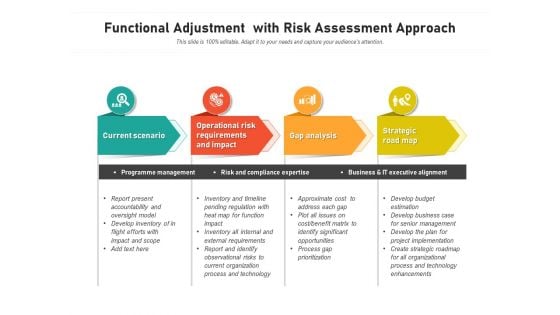
Functional Adjustment With Risk Assessment Approach Ppt PowerPoint Presentation Layouts Format PDF
Persuade your audience using this functional adjustment with risk assessment approach ppt powerpoint presentation layouts format pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including current scenario, operational risk requirements and impact, gap analysis, strategic road map. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
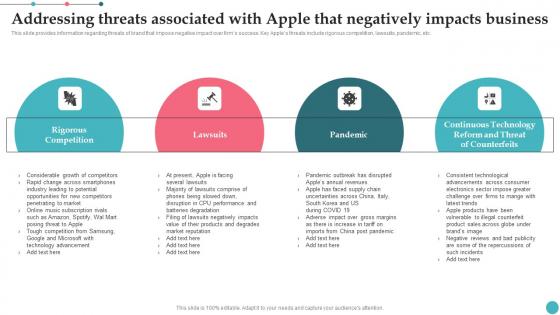
Addressing Threats Associated With Apple That Negatively Apples Proficiency In Optimizing Elements Pdf
This slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Addressing Threats Associated With Apple That Negatively Apples Proficiency In Optimizing Elements Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc.

Smart Home System Security Threats Utilizing Smart Appliances IoT SS V
This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft. Take your projects to the next level with our ultimate collection of Smart Home System Security Threats Utilizing Smart Appliances IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft.

Swot Threats Branded Clothing Company Profile PPT Sample CP SS V
This slide showcase SWOT Strengths, Weaknesses, Opportunities and Threats analysis of Zara company that helps in converting company weakness into strengths and threats into opportunities. Do you know about Slidesgeeks Swot Threats Branded Clothing Company Profile PPT Sample CP SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide showcase SWOT Strengths, Weaknesses, Opportunities and Threats analysis of Zara company that helps in converting company weakness into strengths and threats into opportunities.
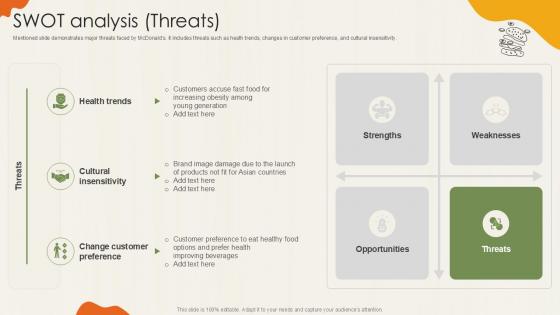
Swot Analysis Threats Food Retailer Company Profile Ppt Presentation CP SS V
Mentioned slide demonstrates major threats faced by McDonalds. it includes threats such as heath trends, changes in customer preference, and cultural insensitivity. Boost your pitch with our creative Swot Analysis Threats Food Retailer Company Profile Ppt Presentation CP SS V Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. Mentioned slide demonstrates major threats faced by McDonalds. it includes threats such as heath trends, changes in customer preference, and cultural insensitivity.

Industry Wise Market Segmentation Of SWG Web Threat Protection System
This slide demonstrates the contribution of different industries in growth of Secure Web Gateway market. The purpose of this slide is to represent the industry wise market share of different sectors such as BFSI, IT and telecom, retail and e-Commerce, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Industry Wise Market Segmentation Of SWG Web Threat Protection System was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Industry Wise Market Segmentation Of SWG Web Threat Protection System This slide demonstrates the contribution of different industries in growth of Secure Web Gateway market. The purpose of this slide is to represent the industry wise market share of different sectors such as BFSI, IT and telecom, retail and e-Commerce, etc.

Introduction To Secure Web Gateway Technology Web Threat Protection System
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. This Introduction To Secure Web Gateway Technology Web Threat Protection System is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Introduction To Secure Web Gateway Technology Web Threat Protection System features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc.
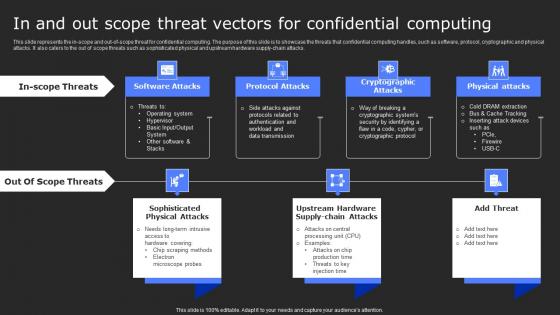
In And Out Scope Threat Vectors For Confidential Secure Computing Framework Inspiration Pdf
This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Take your projects to the next level with our ultimate collection of In And Out Scope Threat Vectors For Confidential Secure Computing Framework Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks.

Future Of Secure Web Gateway Technology Web Threat Protection System
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Future Of Secure Web Gateway Technology Web Threat Protection System and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud.

Key Secure Web Gateway Solution Providers Web Threat Protection System
This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Secure Web Gateway Solution Providers Web Threat Protection System from Slidegeeks and deliver a wonderful presentation. This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc.
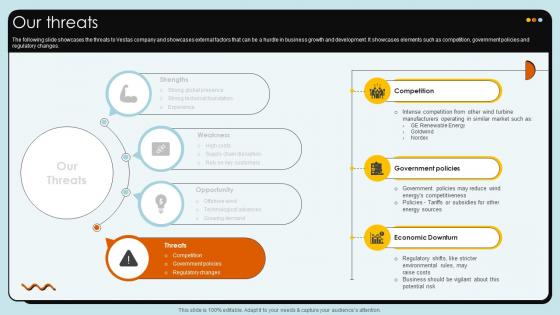
Our Threats Wind Turbines Manufacturer Company Profile CP SS V
The following slide showcases the weakness of Vestas company and showcases internal factors that are limitations of companys business model. It showcases elements such as high costs, supply chain disruptions and rely onThe Our Threats Wind Turbines Manufacturer Company Profile CP SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The following slide showcases the weakness of Vestas company and showcases internal factors that are limitations of companys business model. It showcases elements such as high costs, supply chain disruptions and rely on
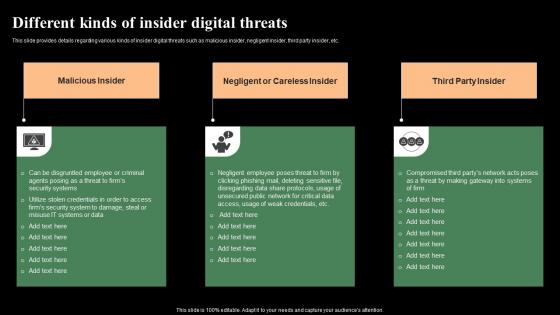
Different Kinds Of Insider Digital Threats Monitoring Digital Assets Graphics Pdf
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. There are so many reasons you need a Different Kinds Of Insider Digital Threats Monitoring Digital Assets Graphics Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc.
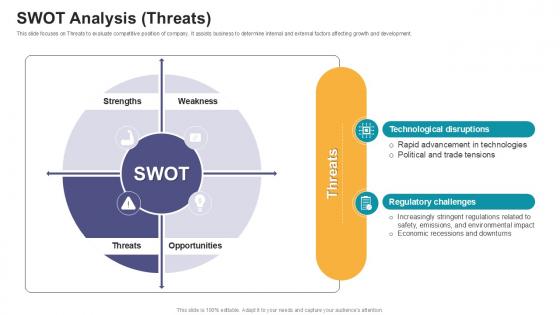
SWOT Analysis Threats Digital Marketings Strategies PPT Presentation CP SS V
This slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. There are so many reasons you need a SWOT Analysis Threats Digital Marketings Strategies PPT Presentation CP SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development.

Key Process For Governance Issues Management Ppt Ideas Mockup PDF
Persuade your audience using this key process for governance issues management ppt ideas mockup pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including risk management, corporate management, infrastructure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Key Components Of Safety Process With Hazard Control Ppt PowerPoint Presentation Icon Layouts PDF
Presenting key components of safety process with hazard control ppt powerpoint presentation icon layouts pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including management, program, risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
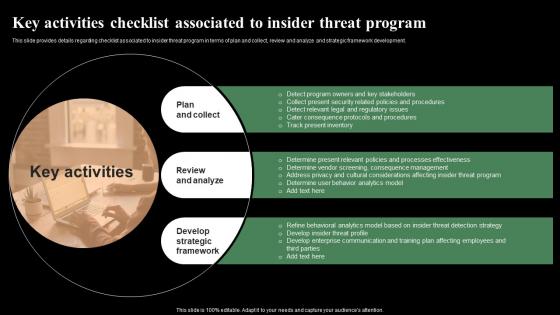
Key Activities Checklist Associated To Insider Threat Monitoring Digital Assets Summary Pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Get a simple yet stunning designed Key Activities Checklist Associated To Insider Threat Monitoring Digital Assets Summary Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Key Activities Checklist Associated To Insider Threat Monitoring Digital Assets Summary Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development.

Features Of Next Generation Secure Web Gateway Web Threat Protection System
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Find highly impressive Features Of Next Generation Secure Web Gateway Web Threat Protection System on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of Next Generation Secure Web Gateway Web Threat Protection System for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc.

Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities
Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Complete Guide To Launch Types Of Website Security Threats And Vulnerabilities that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools.

Major Threats Restricting University Future Growth Running Marketing Campaigns Strategy SS V
The following slide represents major threats of university to determine external factors impacting its growth. It includes elements such as changing demographics, economic instability, regulatory changes negative publicity etc. Are you searching for a Major Threats Restricting University Future Growth Running Marketing Campaigns Strategy SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Major Threats Restricting University Future Growth Running Marketing Campaigns Strategy SS V from Slidegeeks today. The following slide represents major threats of university to determine external factors impacting its growth. It includes elements such as changing demographics, economic instability, regulatory changes negative publicity etc.

SWOT Analysis Threats Luxury Automobile Vehicles PPT Sample CP SS V
This slide focuses on strengths, weakness, opportunities and threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Get a simple yet stunning designed SWOT Analysis Threats Luxury Automobile Vehicles PPT Sample CP SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit SWOT Analysis Threats Luxury Automobile Vehicles PPT Sample CP SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide focuses on strengths, weakness, opportunities and threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development.

SWOT Analysis Threats Vehicle Manufacturer Company Profile PPT Example CP SS V
This slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download SWOT Analysis Threats Vehicle Manufacturer Company Profile PPT Example CP SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the SWOT Analysis Threats Vehicle Manufacturer Company Profile PPT Example CP SS V. This slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development.
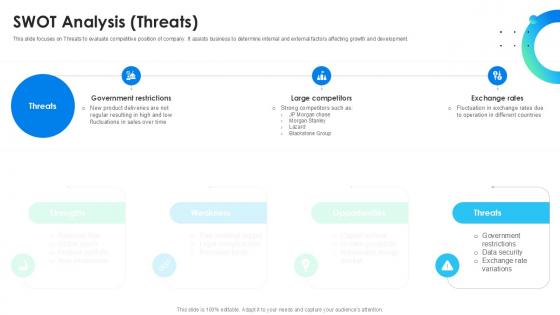
SWOT Analysis Threats Global Energy Company Profile PPT Presentation CP SS V
This slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development. Get a simple yet stunning designed SWOT Analysis Threats Global Energy Company Profile PPT Presentation CP SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit SWOT Analysis Threats Global Energy Company Profile PPT Presentation CP SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide focuses on Threats to evaluate competitive position of company. It assists business to determine internal and external factors affecting growth and development.


 Continue with Email
Continue with Email

 Home
Home


































