Problem
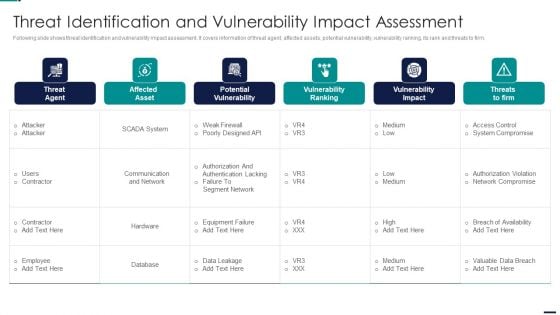
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
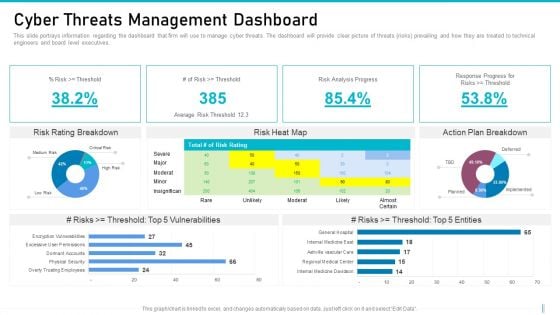
Risk Management For Organization Essential Assets Cyber Threats Management Dashboard Graphics PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver and pitch your topic in the best possible manner with this risk management for organization essential assets cyber threats management dashboard graphics pdf. Use them to share invaluable insights on risk analysis, vulnerabilities, entities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Deploying Corporate Aligned IT Strategy Risk Management Plan To Manage Cyber Threats Microsoft PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Make sure to capture your audiences attention in your business displays with our gratis customizable Deploying Corporate Aligned IT Strategy Risk Management Plan To Manage Cyber Threats Microsoft PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
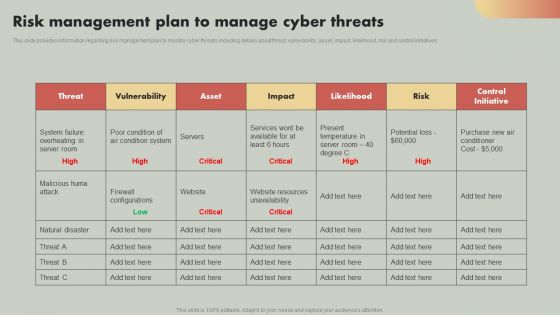
IT Reducing Costs And Management Tips Risk Management Plan To Manage Cyber Threats Formats PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. IT Reducing Costs And Management Tips Risk Management Plan To Manage Cyber Threats Formats PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
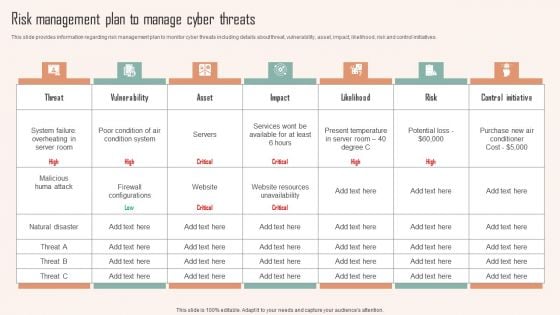
Risk Management Plan To Manage Cyber Threats Ppt PowerPoint Presentation File Professional PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Want to ace your presentation in front of a live audience Our Risk Management Plan To Manage Cyber Threats Ppt PowerPoint Presentation File Professional PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Mitigation Strategies For Operational Threat Risk Governance Framework Manager Ppt Outline Images PDF
Following slide displays risk governance framework for managing operational risk. It includes information of risk management board, committee and departments along with their functions. Deliver an awe inspiring pitch with this creative mitigation strategies for operational threat risk governance framework manager ppt outline images pdf bundle. Topics like management department, business, operational risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
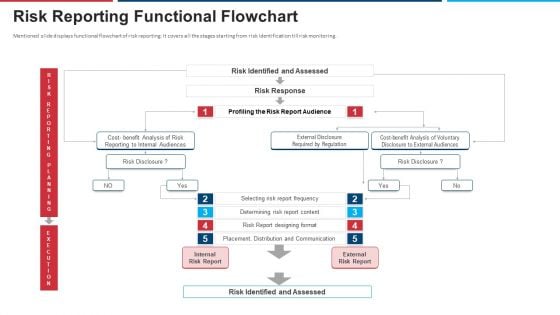
Mitigation Strategies For Operational Threat Risk Reporting Functional Flowchart Ppt Portfolio Clipart Images PDF
Mentioned slide displays functional flowchart of risk reporting. It covers all the stages starting from risk identification till risk monitoring. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat risk reporting functional flowchart ppt portfolio clipart images pdf. Use them to share invaluable insights on communication, analysis, determining, risk response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
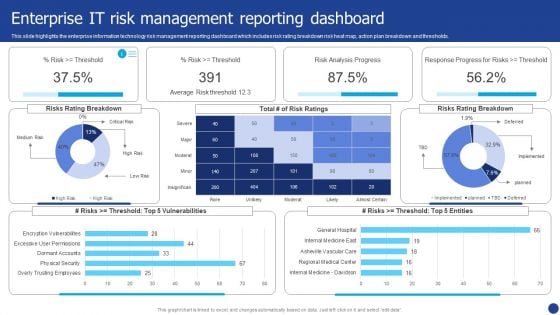
Information Technology Threat Mitigation Methods Enterprise IT Risk Management Reporting Dashboard Download PDF
This slide highlights the enterprise information technology risk management reporting dashboard which includes risk rating breakdown risk heat map, action plan breakdown and thresholds. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Enterprise IT Risk Management Reporting Dashboard Download PDF bundle. Topics like Enterprise IT Risk, Management Reporting Dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
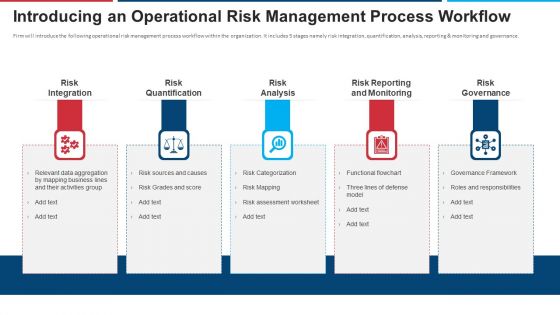
Mitigation Strategies For Operational Threat Introducing An Operational Risk Management Process Workflow Ppt Layouts Brochure PDF
Firm will introduce the following operational risk management process workflow within the organization. It includes 5 stages namely risk integration, quantification, analysis, reporting and monitoring and governance. Presenting mitigation strategies for operational threat introducing an operational risk management process workflow ppt layouts brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like risk integration, risk quantification, risk analysis, risk reporting and monitoring, risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
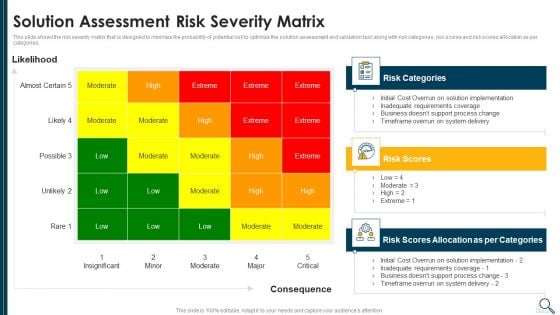
Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment Risk Infographics PDF
This slide shows the risk severity matrix that is designed to minimize the probability of potential risk to optimize the solution assessment and validation task along with risk categories, risk scores and risk scores allocation as per categories. Deliver and pitch your topic in the best possible manner with this solution evaluation criteria assessment and threat impact matrix solution assessment risk infographics pdf. Use them to share invaluable insights on risk categories, risk scores, system, requirements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Threat Management At Workplace How Financial Risk Can Be Controlled Download Pdf
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. This is a threat management at workplace how financial risk can be controlled download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
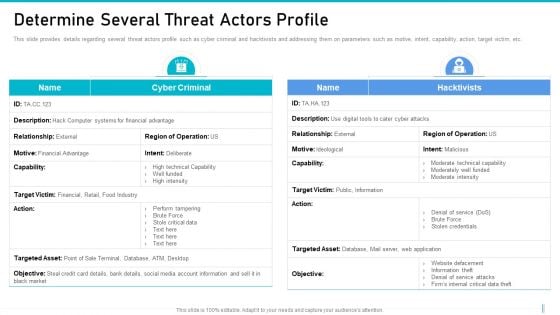
Risk Management For Organization Essential Assets Determine Several Threat Actors Profile Inspiration PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative risk management for organization essential assets determine several threat actors profile inspiration pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management For Organization Essential Assets Determine Threat Scenario Analysis Background PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative risk management for organization essential assets determine threat scenario analysis background pdf bundle. Topics like actions and objectives, installation, exploitation, reconnaissance, weaponization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
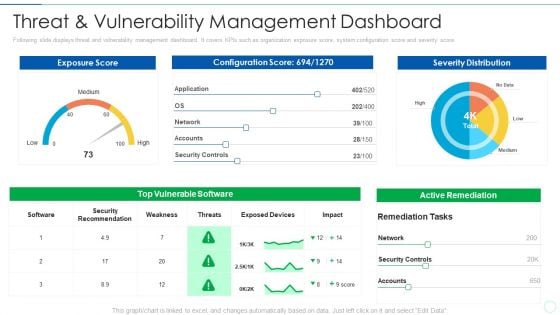
Effective IT Risk Management Process Threat And Vulnerability Management Rules PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this effective it risk management process threat and vulnerability management rules pdf. Use them to share invaluable insights on threat and vulnerability management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Determine Several Threat Actors Profile Clipart PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management determine several threat actors profile clipart pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
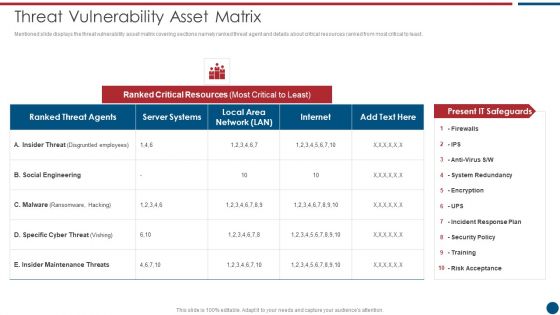
Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF bundle. Topics like Ranked Critical, Server Systems, Social Engineering can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
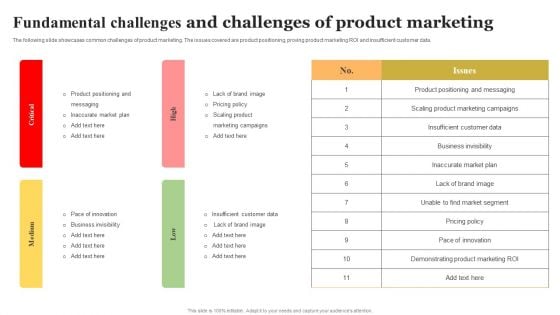
Fundamental Challenges And Challenges Of Product Marketing Ideas PDF
The following slide showcases common challenges of product marketing. The issues covered are product positioning, proving product marketing ROI and insufficient customer data. Showcasing this set of slides titled Fundamental Challenges And Challenges Of Product Marketing Ideas PDF. The topics addressed in these templates are High, Critical, Medium, Low. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Management Word Cloud With Threat Probability And Goals Ppt Powerpoint Presentation Show Designs Download
This is a risk management word cloud with threat probability and goals ppt powerpoint presentation show designs download. This is a four stage process. The stages in this process are success, business, motivation, management, always, objectives, item, organizational, money, taking.
Risk Impact And Probability Analysis Performance Ppt Powerpoint Presentation Inspiration Picture Ppt Powerpoint Presentation Icon Skills
This is a risk impact and probability analysis performance ppt powerpoint presentation inspiration picture ppt powerpoint presentation icon skills. This is a three stage process. The stages in this process are business, management, planning, strategy, marketing.
Risk Tolerance Business Ppt Powerpoint Presentation Inspiration Clipart Images Ppt Powerpoint Presentation Icon Template
This is a risk tolerance business ppt powerpoint presentation inspiration clipart images ppt powerpoint presentation icon template. This is a FOUR stage process. The stages in this process are business, management, planning, strategy, marketing.
Real Time Cyber Threat Risk Management Ppt PowerPoint Presentation Visual Aids Diagrams Cpb Pdf
Presenting this set of slides with name real time cyber threat risk management ppt powerpoint presentation visual aids diagrams cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like real time cyber threat risk management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Risk Mitigation Process To Reduce The Potential Business Threats Ppt PowerPoint Presentation Layouts Portrait PDF
Persuade your audience using this risk mitigation process to reduce the potential business threats ppt powerpoint presentation layouts portrait pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including risk mitigation process to reduce the potential business threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
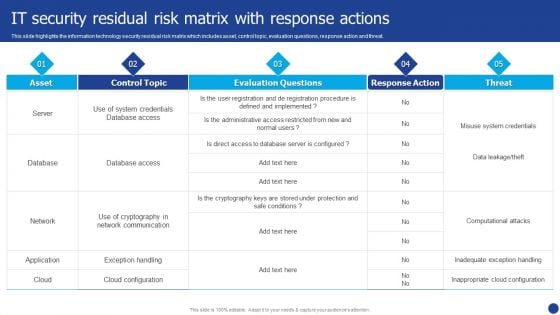
Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Risk Analysis Vector Icon Ppt PowerPoint Presentation Pictures Infographic Template PDF
Presenting this set of slides with name risk analysis vector icon ppt powerpoint presentation pictures infographic template pdf. This is a three stage process. The stages in this process are risk analysis vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Risk Mitigation Icon With Document Evaluation Ppt PowerPoint Presentation Inspiration Summary PDF
Presenting this set of slides with name risk mitigation icon with document evaluation ppt powerpoint presentation inspiration summary pdf. This is a three stage process. The stages in this process are risk mitigation icon with document evaluation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Business Risk With Cash Bag Vector Icon Ppt PowerPoint Presentation Gallery Styles PDF
Presenting this set of slides with name business risk with cash bag vector icon ppt powerpoint presentation gallery styles pdf. This is a three stage process. The stages in this process are business risk with cash bag vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Credit Card Payment Risk Vector Icon Ppt PowerPoint Presentation File Inspiration PDF
Presenting this set of slides with name credit card payment risk vector icon ppt powerpoint presentation file inspiration pdf. This is a three stage process. The stages in this process are credit card payment risk vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Operational Risk Analysis In Business Process Vector Icon Ppt PowerPoint Presentation File Visual Aids PDF
Presenting this set of slides with name operational risk analysis in business process vector icon ppt powerpoint presentation file visual aids pdf. This is a three stage process. The stages in this process are operational risk analysis in business process vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Financial Risk Analysis Vector Icon Ppt PowerPoint Presentation Gallery Structure PDF
Presenting this set of slides with name financial risk analysis vector icon ppt powerpoint presentation gallery structure pdf. This is a two stage process. The stages in this process are financial risk analysis vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
High Financial Risk Analysis Vector Icon Ppt PowerPoint Presentation File Infographics PDF
Presenting this set of slides with name high financial risk analysis vector icon ppt powerpoint presentation file infographics pdf. This is a one stage process. The stage in this process is high financial risk analysis vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Meter Showing High Risk Level Vector Icon Ppt PowerPoint Presentation Gallery Clipart PDF
Presenting this set of slides with name meter showing high risk level vector icon ppt powerpoint presentation gallery clipart pdf. This is a one stage process. The stage in this process is meter showing high risk level vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icon Of Macroeconomic Analysis Illustrating Risk Reduction In Economy Formats PDF
Presenting Icon Of Macroeconomic Analysis Illustrating Risk Reduction In Economy Formats PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Icon Of Macroeconomic Analysis Illustrating Risk Reduction In Economy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
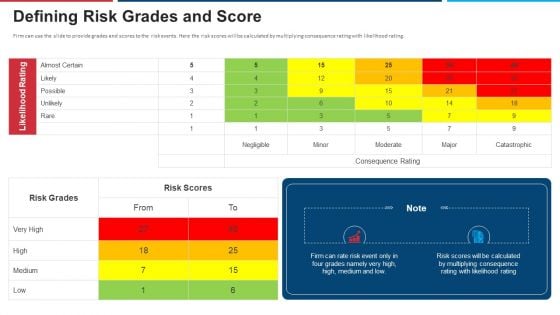
Mitigation Strategies For Operational Threat Defining Risk Grades And Score Ppt Outline PDF
Firm can use the slide to provide grades and scores to the risk events. Here the risk scores will be calculated by multiplying consequence rating with likelihood rating. Deliver an awe inspiring pitch with this creative mitigation strategies for operational threat defining risk grades and score ppt outline pdf bundle. Topics like defining risk grades and score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Risk Management KPI Dashboard With Loss Ppt Slides PDF
Following slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an awe inspiring pitch with this creative handling cyber threats digital era risk management kpi dashboard with loss ppt slides pdf bundle. Topics like gement kpi dashboard with loss events and actions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
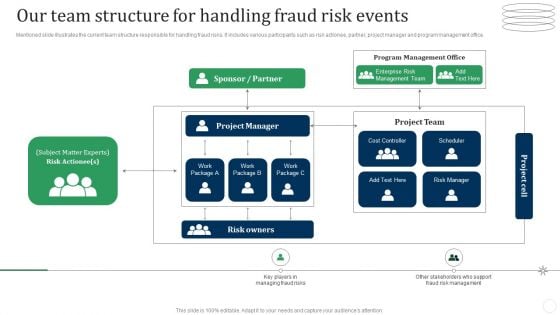
Our Team Structure For Handling Fraud Risk Events Fraud Threat Administration Guide Sample PDF
Mentioned slide illustrates the current team structure responsible for handling fraud risks. It includes various participants such as risk actionee, partner, project manager and program management office. Deliver an awe inspiring pitch with this creative Our Team Structure For Handling Fraud Risk Events Fraud Threat Administration Guide Sample PDF bundle. Topics like Enterprise Risk, Management Team, Program Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Workforce Issues Powerpoint Slides
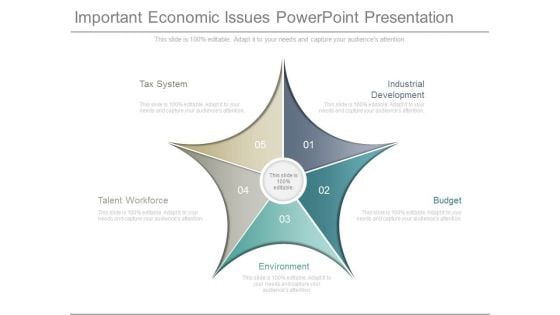
Important Economic Issues Powerpoint Presentation
This is a important economic issues powerpoint presentation. This is a five stage process. The stages in this process are tax system, industrial development, budget, environment, talent workforce.
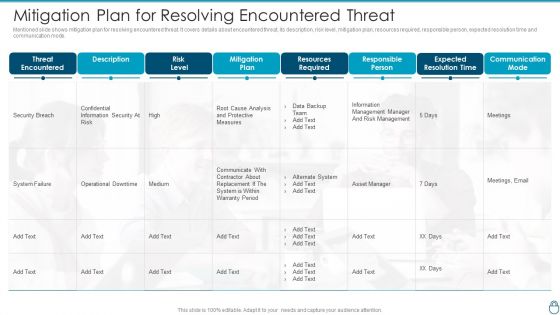
Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF Use them to share invaluable insights on Resources Required, Responsible Person, Expected Resolution Time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
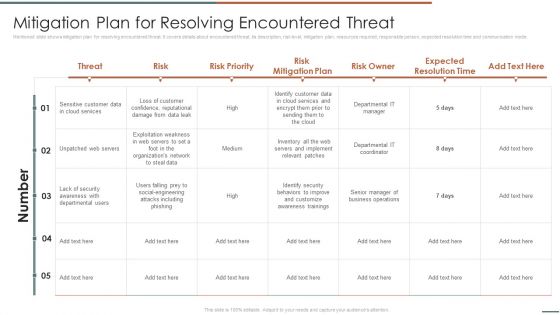
Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF. Use them to share invaluable insights on Unpatched Servers, Attacks Including, Awareness Trainings and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
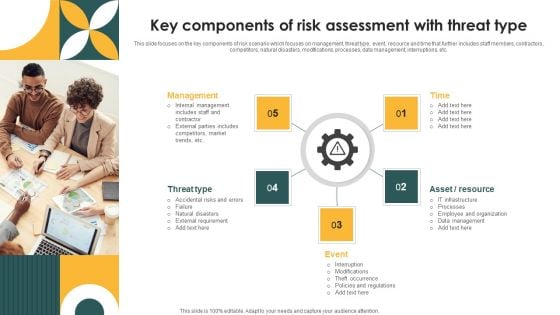
Key Components Of Risk Assessment With Threat Type Ppt PowerPoint Presentation File Summary PDF
This slide focuses on the key components of risk scenario which focuses on management, threat type, event, resource and time that further includes staff members, contractors, competitors, natural disasters, modifications, processes, data management, interruptions, etc. Persuade your audience using this Key Components Of Risk Assessment With Threat Type Ppt PowerPoint Presentation File Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Management, Threat Type, Event, Time. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
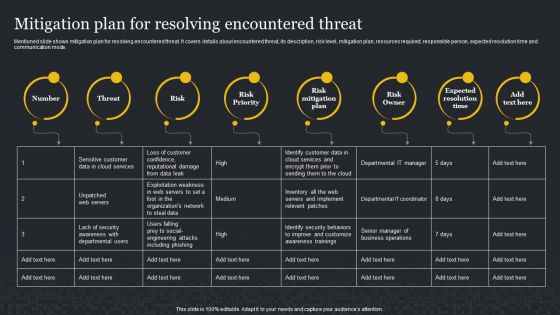
Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mitigation Plan For Resolving Encountered Threat Cybersecurity Risk Assessment Demonstration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
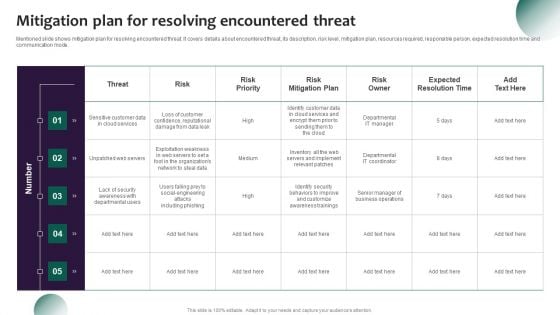
Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. The Developing IT Security Strategy Threat Identification And Vulnerability Assessment For Risk Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management.. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. This Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
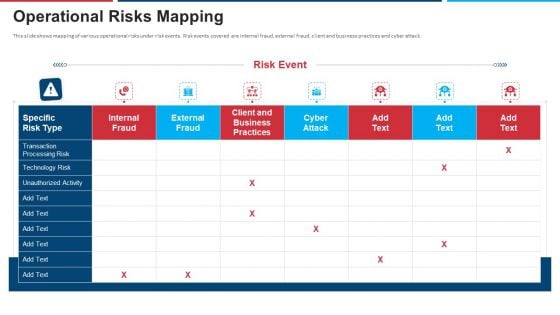
Mitigation Strategies For Operational Threat Operational Risks Mapping Ppt File Graphics PDF
This slide shows mapping of various operational risks under risk events. Risk events covered are internal fraud, external fraud, client and business practices and cyber attack. Deliver and pitch your topic in the best possible manner with this mitigation strategies for operational threat operational risks mapping ppt file graphics pdf. Use them to share invaluable insights on technology risk, transaction processing risk, unauthorized activity, business practices and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
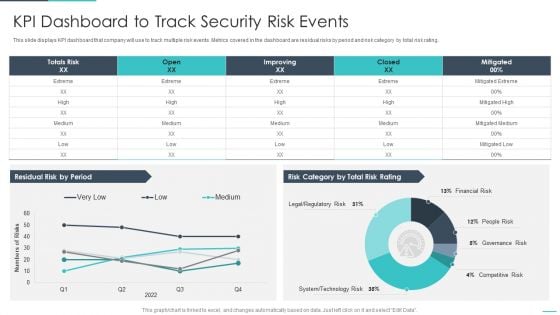
Handling Cyber Threats Digital Era KPI Dashboard To Track Security Risk Events Ppt Inspiration PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era kpi dashboard to track security risk events ppt inspiration pdf. Use them to share invaluable insights on kpi dashboard to track security risk events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Effective Financial Risk Management Strategies Challenges To Credit Risk Management Information PDF
This slide shows the challenges related to credit risk management which includes insufficient data management, constant rework, insuffuicient risk tools, etc. Presenting Effective Financial Risk Management Strategies Challenges To Credit Risk Management Information PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Challenges, Description. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
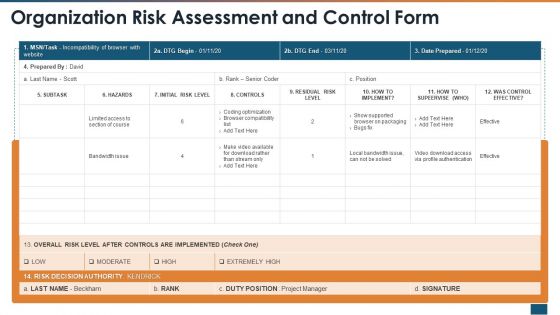
Threat Administration Bundle Organization Risk Assessment And Control Form Demonstration PDF
Deliver and pitch your topic in the best possible manner with this threat administration bundle organization risk assessment and control form demonstration pdf. Use them to share invaluable insights on organization risk assessment and control form and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
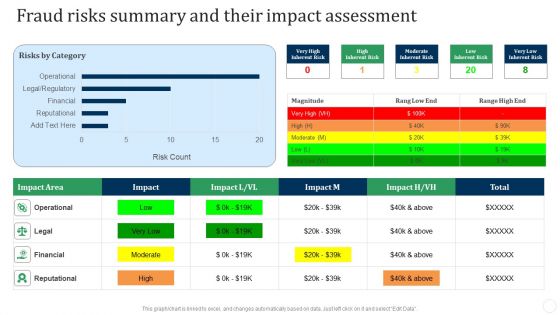
Fraud Risks Summary And Their Impact Assessment Fraud Threat Administration Guide Summary PDF
Deliver an awe inspiring pitch with this creative Fraud Risks Summary And Their Impact Assessment Fraud Threat Administration Guide Summary PDF bundle. Topics like Inherent Risk, High Inherent, Moderate Inherent can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Balance Risk Reward Vector Icon Ppt PowerPoint Presentation Show Clipart Images PDF
Presenting this set of slides with name balance risk reward vector icon ppt powerpoint presentation show clipart images pdf. This is a two stage process. The stages in this process are reward, risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Up Down Risk Reward Arrows Vector Icon Ppt PowerPoint Presentation Show Mockup PDF
Presenting this set of slides with name up down risk reward arrows vector icon ppt powerpoint presentation show mockup pdf. This is a two stage process. The stages in this process are reward, risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cloud Security Risks Or Threats Cloud Computing Security IT Ppt Icon PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting cloud security risks or threats cloud computing security it ppt icon pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like revenue losses, loss of data, shared vulnerabilities, compliance violations, malware attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
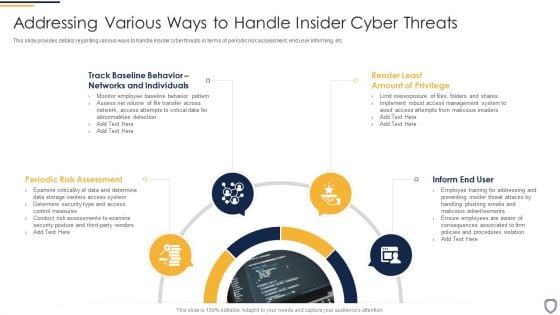
Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Infographics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a corporate security and risk management addressing various ways to handle insider cyber threats infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, inform end user, render least amount of privilege, track baseline behavior networks and individuals . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
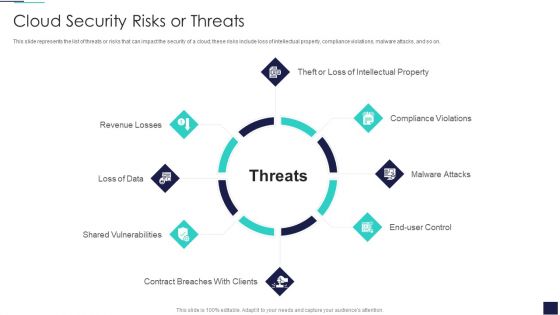
Cloud Information Security Cloud Security Risks Or Threats Ppt Model Clipart PDF
This slide represents the list of threats or risks that can impact the security of a cloud, these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Information Security Cloud Security Risks Or Threats Ppt Model Clipart PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Shared Vulnerabilities, Malware Attacks, Compliance Violations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
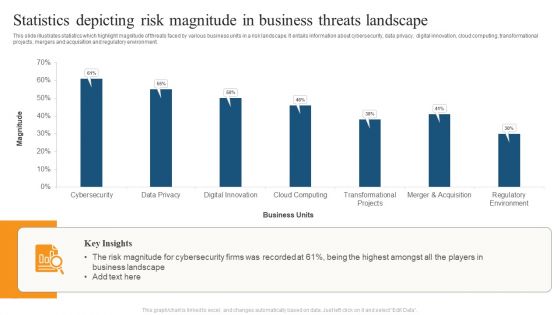
Statistics Depicting Risk Magnitude In Business Threats Landscape Ppt File Example Introduction PDF
This slide illustrates statistics which highlight magnitude of threats faced by various business units in a risk landscape. It entails information about cybersecurity, data privacy, digital innovation, cloud computing, transformational projects, mergers and acquisition and regulatory environment. Pitch your topic with ease and precision using this Statistics Depicting Risk Magnitude In Business Threats Landscape Ppt File Example Introduction PDF. This layout presents information on Business Units, Risk Magnitude, Business Landscape. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Explore a selection of the finest Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Software Development Life Cycle Planning Prioritized Cyber Security Threats With Risk Mitigation Plan Template PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
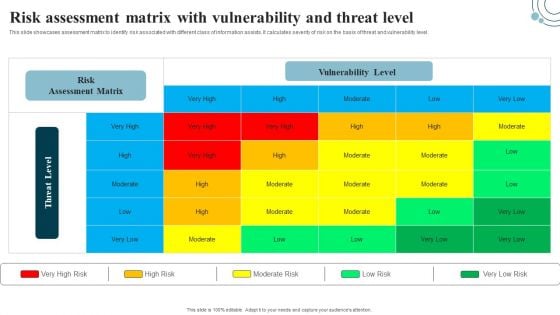
Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF
This slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. This Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Risk Assessment Matrix With Vulnerability And Threat Level Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
Swot Analysis Template 4 Ppt PowerPoint Presentation Outline Graphics Example
This is a swot analysis template 4 ppt powerpoint presentation outline graphics example. This is a one stage process. The stages in this process are threat, business, marketing, management.
Swot Analysis Template 5 Ppt PowerPoint Presentation Icon Guide
This is a swot analysis template 5 ppt powerpoint presentation icon guide. This is a one stage process. The stages in this process are threats, strengths, weaknesses, opportunities, business, analysis.

Swot Analysis Template 5 Ppt PowerPoint Presentation Layouts Graphics Design
This is a swot analysis template 5 ppt powerpoint presentation layouts graphics design. This is a one stage process. The stages in this process are threats, strengths, weaknesses, opportunities.


 Continue with Email
Continue with Email

 Home
Home


































