Process Overview
How To Create Cost Effective How Often To Post Content On Facebook Strategy SS V
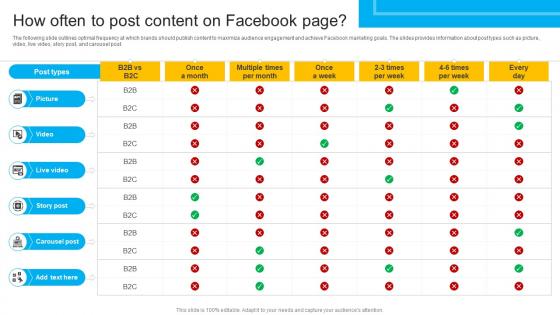
The following slide outlines optimal frequency at which brands should publish content to maximize audience engagement and achieve Facebook marketing goals. The slides provides information about post types such as picture, video, live video, story post, and carousel post. Are you searching for a How To Create Cost Effective How Often To Post Content On Facebook Strategy SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download How To Create Cost Effective How Often To Post Content On Facebook Strategy SS V from Slidegeeks today. The following slide outlines optimal frequency at which brands should publish content to maximize audience engagement and achieve Facebook marketing goals. The slides provides information about post types such as picture, video, live video, story post, and carousel post.
How To Create Cost Effective Impact Of Current Social Media Marketing Strategy SS V
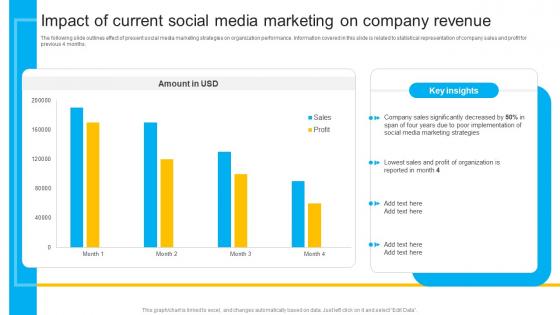
The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download How To Create Cost Effective Impact Of Current Social Media Marketing Strategy SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the How To Create Cost Effective Impact Of Current Social Media Marketing Strategy SS V. The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months.

How To Create Cost Effective Projected Cost Of Running Ads On Facebook Strategy SS V
The following slide outlines projected expenses which company incur while running paid advertising campaign on Facebook. Information covered in this slide is related to cost-per-click CPC, click-through rate CTR, cost-per-thousand CPM, cost-per-like CPL, cost-per-download, and cost-per-action CPA. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give How To Create Cost Effective Projected Cost Of Running Ads On Facebook Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable How To Create Cost Effective Projected Cost Of Running Ads On Facebook Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide outlines projected expenses which company incur while running paid advertising campaign on Facebook. Information covered in this slide is related to cost-per-click CPC, click-through rate CTR, cost-per-thousand CPM, cost-per-like CPL, cost-per-download, and cost-per-action CPA.
How To Create Cost Effective Target Customer Segmentation For Facebook Strategy SS V
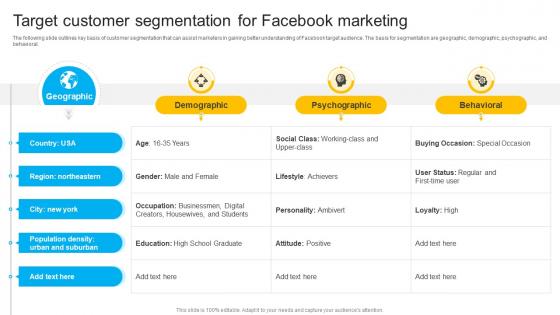
The following slide outlines key basis of customer segmentation that can assist marketers in gaining better understanding of Facebook target audience. The basis for segmentation are geographic, demographic, psychographic, and behavioral. Whether you have daily or monthly meetings, a brilliant presentation is necessary. How To Create Cost Effective Target Customer Segmentation For Facebook Strategy SS V can be your best option for delivering a presentation. Represent everything in detail using How To Create Cost Effective Target Customer Segmentation For Facebook Strategy SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide outlines key basis of customer segmentation that can assist marketers in gaining better understanding of Facebook target audience. The basis for segmentation are geographic, demographic, psychographic, and behavioral.

Zero Trust Model Before Vs After Zero Trust Network Access
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Before Vs After Zero Trust Network Access a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Before Vs After Zero Trust Network Access. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems.

Zero Trust Model Checklist To Build Zero Trust Network Access
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Checklist To Build Zero Trust Network Access With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Model Future And Emerging Trends In ZTNA Model
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. This Zero Trust Model Future And Emerging Trends In ZTNA Model is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Future And Emerging Trends In ZTNA Model features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.

Zero Trust Model Key Characteristics Of Modern ZTNA Solution
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Welcome to our selection of the Zero Trust Model Key Characteristics Of Modern ZTNA Solution. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.
Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp
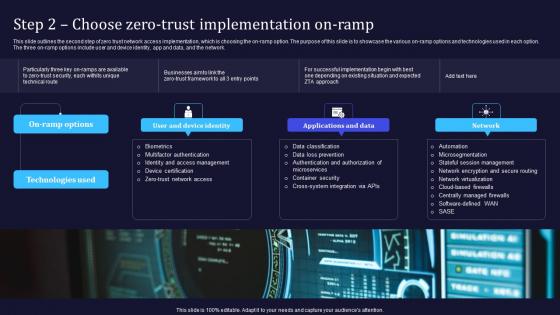
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Model Step 2 Choose Zero Trust Implementation On Ramp. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network.

Zero Trust Model Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Slidegeeks is here to make your presentations a breeze with Zero Trust Model Steps To Implement Zero Trust Network Access Model With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Various Type Of Seo Marketing Techniques For Restaurant Create An Effective Restaurant
The following slide showcases various types of search engine optimization SEO through which marketing teams can increase visitors to websites and gain competitive edge. The types outlined in slide are on-page, off-page, technical and local SEO. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Various Type Of Seo Marketing Techniques For Restaurant Create An Effective Restaurant to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide showcases various types of search engine optimization SEO through which marketing teams can increase visitors to websites and gain competitive edge. The types outlined in slide are on-page, off-page, technical and local SEO.
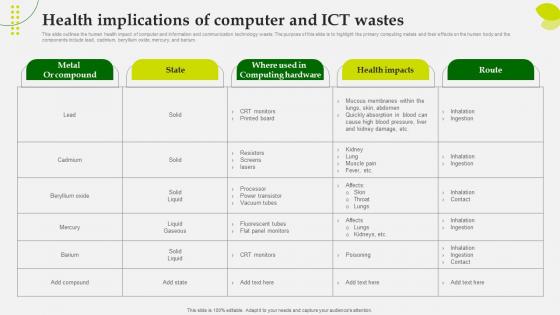
Green Computing Health Implications Of Computer And Ict Wastes
This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium. This Green Computing Health Implications Of Computer And Ict Wastes is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Green Computing Health Implications Of Computer And Ict Wastes features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium.

Green Computing Timeline To Implement Green Cloud Computing
This slide outlines the timeline to implement green cloud computing in an organization. The purpose of this slide is to showcase the steps to be taken by businesses to implement green cloud computing, including selecting a carbon-aware provider, optimizing the cloud environment, ensuring solid carbon measurement and reporting plans, etc. Present like a pro with Green Computing Timeline To Implement Green Cloud Computing Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide outlines the timeline to implement green cloud computing in an organization. The purpose of this slide is to showcase the steps to be taken by businesses to implement green cloud computing, including selecting a carbon-aware provider, optimizing the cloud environment, ensuring solid carbon measurement and reporting plans, etc.

Sustainable Health Implications Of Computer And ICT Wastes
This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium. Take your projects to the next level with our ultimate collection of Sustainable Health Implications Of Computer And ICT Wastes. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide outlines the human health impact of computer and information and communication technology waste. The purpose of this slide is to highlight the primary computing metals and their effects on the human body and the components include lead, cadmium, beryllium oxide, mercury, and barium.
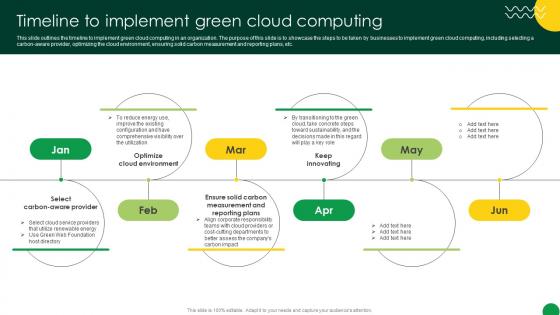
Sustainable Timeline To Implement Green Cloud Computing
This slide outlines the timeline to implement green cloud computing in an organization. The purpose of this slide is to showcase the steps to be taken by businesses to implement green cloud computing, including selecting a carbon-aware provider, optimizing the cloud environment, ensuring solid carbon measurement and reporting plans, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Sustainable Timeline To Implement Green Cloud Computing to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the timeline to implement green cloud computing in an organization. The purpose of this slide is to showcase the steps to be taken by businesses to implement green cloud computing, including selecting a carbon-aware provider, optimizing the cloud environment, ensuring solid carbon measurement and reporting plans, etc.
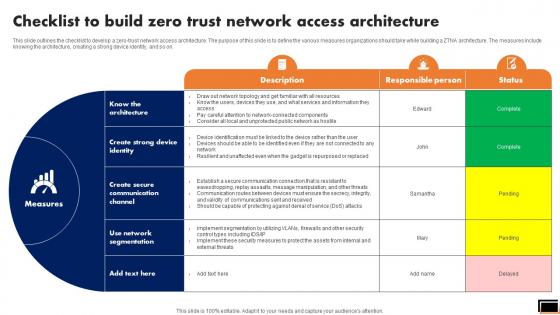
Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP a try. Our experts have put a lot of knowledge and effort into creating this impeccable Checklist To Build Zero Trust Network Access Architecture Software Defined Perimeter SDP. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.
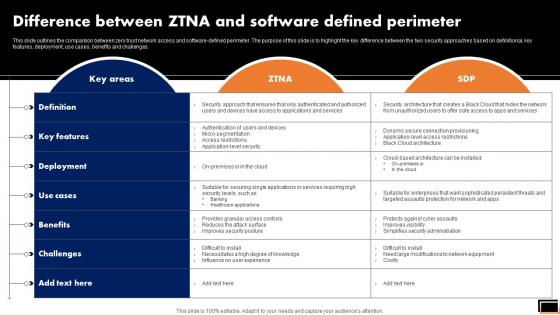
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.

Key Characteristics Of Modern Ztna Solution Software Defined Perimeter SDP
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Characteristics Of Modern Ztna Solution Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.

Main Pillars Of Zero Network Trust Access Software Defined Perimeter SDP
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Welcome to our selection of the Main Pillars Of Zero Network Trust Access Software Defined Perimeter SDP. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation.

Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Steps To Implement Zero Trust Network Access Model Software Defined Perimeter SDP will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the business security model, etc.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response.

Types Of IoT Sensors Utilised In Space Exploration IoT In Orbit Unleashing The Power IoT SS V
This slide outlines key sensors and devices utilized in space exploration missions in order to monitor spacecraft performance and celestial bodies in space. It includes sensors such as atmospheric sensors, radiation sensors, imaging sensors, thermal sensors and magnetometers. This Types Of IoT Sensors Utilised In Space Exploration IoT In Orbit Unleashing The Power IoT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide outlines key sensors and devices utilized in space exploration missions in order to monitor spacecraft performance and celestial bodies in space. It includes sensors such as atmospheric sensors, radiation sensors, imaging sensors, thermal sensors and magnetometers.
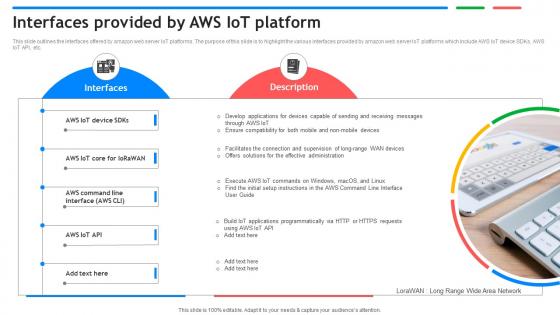
Interfaces Provided By Aws IoT Platform Exploring Google Cloud IoT Platform
This slide outlines the interfaces offered by amazon web server IoT platforms. The purpose of this slide is to highlight the various interfaces provided by amazon web server IoT platforms which include AWS IoT device SDKs, AWS IoT API, etc. This modern and well arranged Interfaces Provided By Aws IoT Platform Exploring Google Cloud IoT Platform provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide outlines the interfaces offered by amazon web server IoT platforms. The purpose of this slide is to highlight the various interfaces provided by amazon web server IoT platforms which include AWS IoT device SDKs, AWS IoT API, etc.

Key Benefits For Samsung Artik Customers Exploring Google Cloud IoT Platform
This slide outlines the various advantages for customers of Samsung ARTIK. The purpose of this slide is to highlight the key benefits for Samsung ARTIK customers which include quicker pace, amplified speed of application, etc. Retrieve professionally designed Key Benefits For Samsung Artik Customers Exploring Google Cloud IoT Platform to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide outlines the various advantages for customers of Samsung ARTIK. The purpose of this slide is to highlight the key benefits for Samsung ARTIK customers which include quicker pace, amplified speed of application, etc.

Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform
This slide outlines the various advantages of IoT platform utilization. The purpose of this slide is to showcase the key benefits of using IoT platforms which include scalability, security, cost saving, etc. Presenting this PowerPoint presentation, titled Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Key Benefits Of Using IoT Platforms Exploring Google Cloud IoT Platform that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the various advantages of IoT platform utilization. The purpose of this slide is to showcase the key benefits of using IoT platforms which include scalability, security, cost saving, etc.

Roadmap For Implementing Internet Of Things Exploring Google Cloud IoT Platform
This slide outlines the deployment for IoT platforms. The purpose of this slide is to highlight the steps that an organization should take while utilizing IoT platforms which include planning, requirement gathering, connectivity, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Roadmap For Implementing Internet Of Things Exploring Google Cloud IoT Platform a try. Our experts have put a lot of knowledge and effort into creating this impeccable Roadmap For Implementing Internet Of Things Exploring Google Cloud IoT Platform You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the deployment for IoT platforms. The purpose of this slide is to highlight the steps that an organization should take while utilizing IoT platforms which include planning, requirement gathering, connectivity, etc.

Audience And Influencer Analysis Of Social Media Analytics Cracking The Code Of Social Media
This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc. Create an editable Audience And Influencer Analysis Of Social Media Analytics Cracking The Code Of Social Media that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Audience And Influencer Analysis Of Social Media Analytics Cracking The Code Of Social Media is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc.
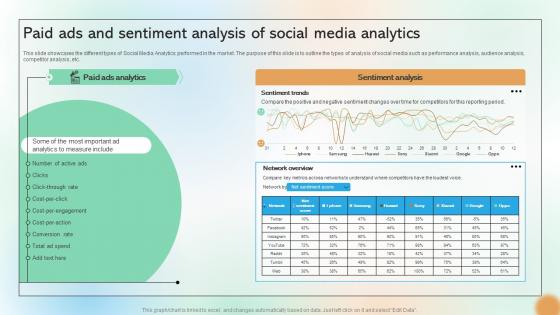
Paid Ads And Sentiment Analysis Of Social Media Analytics Cracking The Code Of Social Media
This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Paid Ads And Sentiment Analysis Of Social Media Analytics Cracking The Code Of Social Media a try. Our experts have put a lot of knowledge and effort into creating this impeccable Paid Ads And Sentiment Analysis Of Social Media Analytics Cracking The Code Of Social Media. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc.
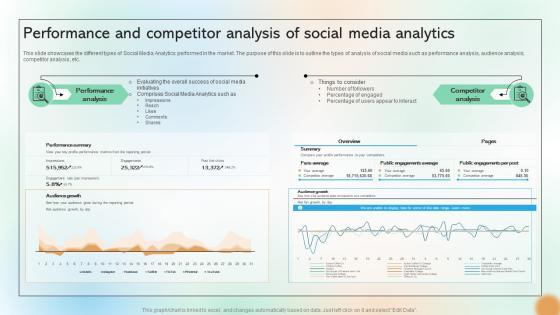
Performance And Competitor Analysis Of Social Media Analytics Cracking The Code Of Social Media
This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc. Get a simple yet stunning designed Performance And Competitor Analysis Of Social Media Analytics Cracking The Code Of Social Media. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Performance And Competitor Analysis Of Social Media Analytics Cracking The Code Of Social Media can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide showcases the different types of Social Media Analytics performed in the market. The purpose of this slide is to outline the types of analysis of social media such as performance analysis, audience analysis, competitor analysis, etc.

Third Party Tools For Resource Maximization In Social Media Cracking The Code Of Social Media
This slide outlines the third party tools for resource maximization in social media. The purpose of this slide is to highlight the third party tools for resource maximization such as artificial intelligence, chatbots, interactive voice response, etc. Get a simple yet stunning designed Third Party Tools For Resource Maximization In Social Media Cracking The Code Of Social Media. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Third Party Tools For Resource Maximization In Social Media Cracking The Code Of Social Media can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the third party tools for resource maximization in social media. The purpose of this slide is to highlight the third party tools for resource maximization such as artificial intelligence, chatbots, interactive voice response, etc.
Facebook Marketing Plan Best Time And Day To Post Content On Facebook Strategy SS V
Facebook Marketing Plan Facebook Ad Performance Benchmark By Different Strategy SS V
Facebook Marketing Plan Facebook Giveaway Post Example To Increase Strategy SS V
Facebook Marketing Plan Fictional Representation Of Buyer Persona Strategy SS V
Facebook Marketing Plan How Often To Post Content On Facebook Page Strategy SS V
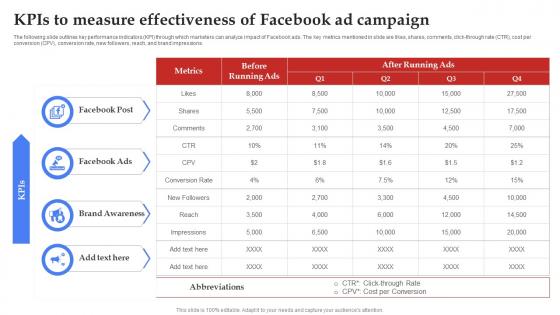
Facebook Marketing Plan Kpis To Measure Effectiveness Of Facebook Ad Strategy SS V
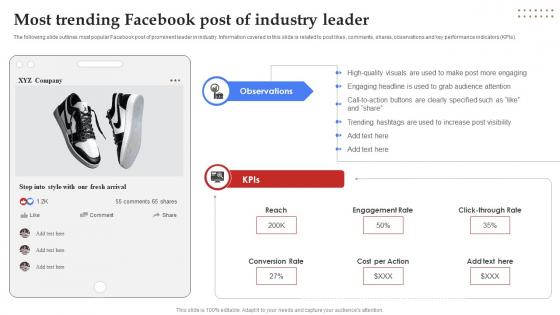
Facebook Marketing Plan Most Trending Facebook Post Of Industry Leader Strategy SS V
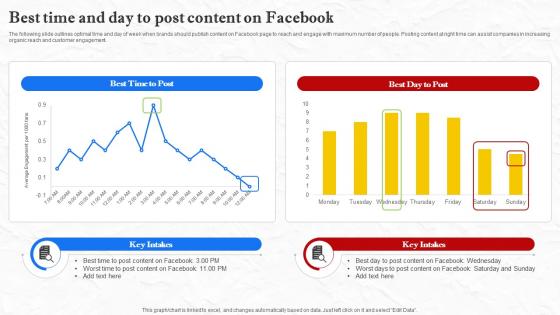
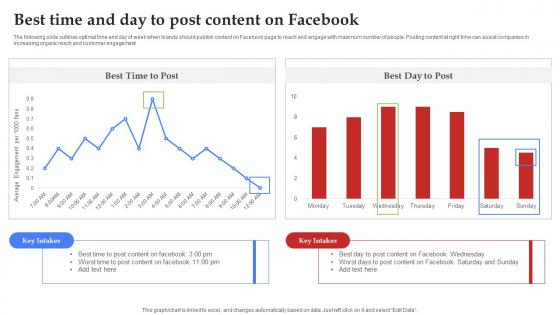
Facebook Marketing Techniques Best Time And Day To Post Content On Facebook Strategy SS V
The following slide outlines optimal time and day of week when brands should publish content on Facebook page to reach and engage with maximum number of people. Posting content at right time can assist companies in increasing organic reach and customer engagement. Present like a pro with Facebook Marketing Techniques Best Time And Day To Post Content On Facebook Strategy SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The following slide outlines optimal time and day of week when brands should publish content on Facebook page to reach and engage with maximum number of people. Posting content at right time can assist companies in increasing organic reach and customer engagement.
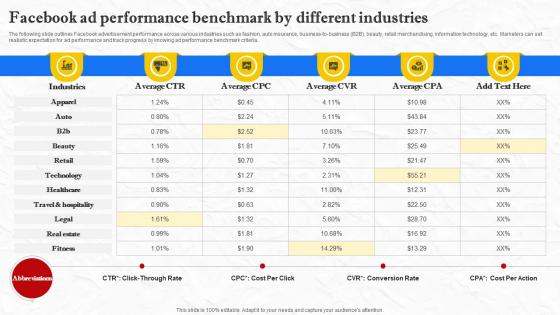
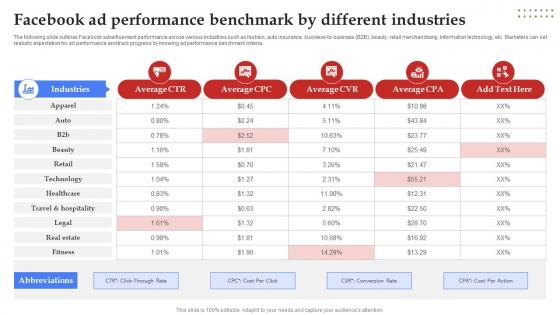
Facebook Marketing Techniques Facebook Ad Performance Benchmark Strategy SS V
The following slide outlines Facebook advertisement performance across various industries such as fashion, auto insurance, business-to-business B2B , beauty, retail merchandising, information technology, etc. Marketers can set realistic expectation for ad performance and track progress by knowing ad performance benchmark criteria. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Facebook Marketing Techniques Facebook Ad Performance Benchmark Strategy SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Facebook Marketing Techniques Facebook Ad Performance Benchmark Strategy SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The following slide outlines Facebook advertisement performance across various industries such as fashion, auto insurance, business-to-business B2B , beauty, retail merchandising, information technology, etc. Marketers can set realistic expectation for ad performance and track progress by knowing ad performance benchmark criteria.
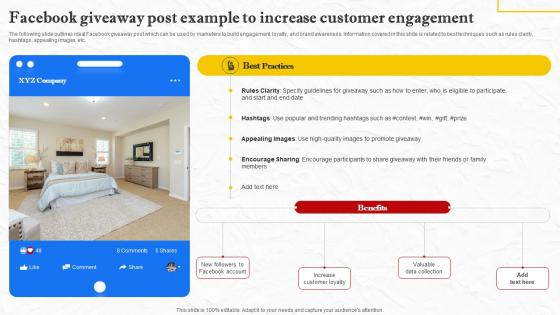
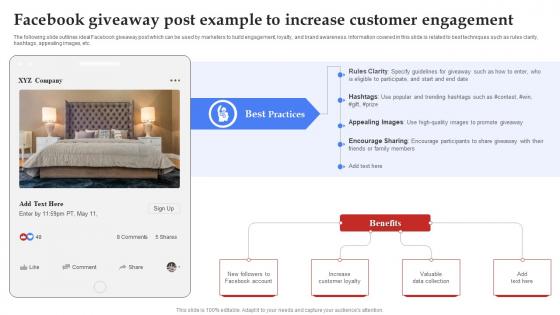
Facebook Marketing Techniques Facebook Giveaway Post Example To Increase Strategy SS V
The following slide outlines ideal Facebook giveaway post which can be used by marketers to build engagement, loyalty, and brand awareness. Information covered in this slide is related to best techniques such as rules clarity, hashtags, appealing images, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Facebook Marketing Techniques Facebook Giveaway Post Example To Increase Strategy SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide outlines ideal Facebook giveaway post which can be used by marketers to build engagement, loyalty, and brand awareness. Information covered in this slide is related to best techniques such as rules clarity, hashtags, appealing images, etc.

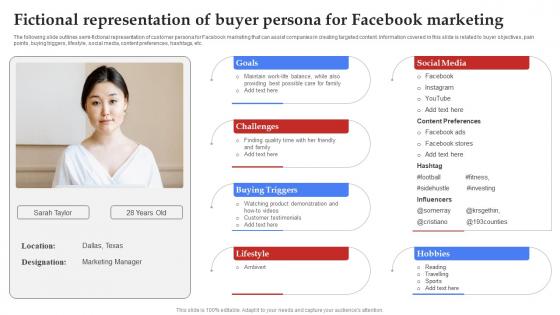
Facebook Marketing Techniques Fictional Representation Of Buyer Persona Strategy SS V
The following slide outlines semi-fictional representation of customer persona for Facebook marketing that can assist companies in creating targeted content. Information covered in this slide is related to buyer objectives, pain points, buying triggers, lifestyle, social media, content preferences, hashtags, etc. This Facebook Marketing Techniques Fictional Representation Of Buyer Persona Strategy SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Facebook Marketing Techniques Fictional Representation Of Buyer Persona Strategy SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The following slide outlines semi-fictional representation of customer persona for Facebook marketing that can assist companies in creating targeted content. Information covered in this slide is related to buyer objectives, pain points, buying triggers, lifestyle, social media, content preferences, hashtags, etc.
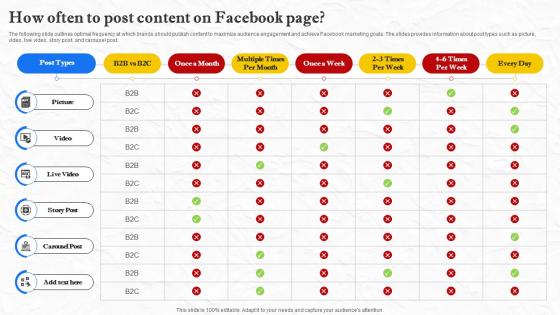
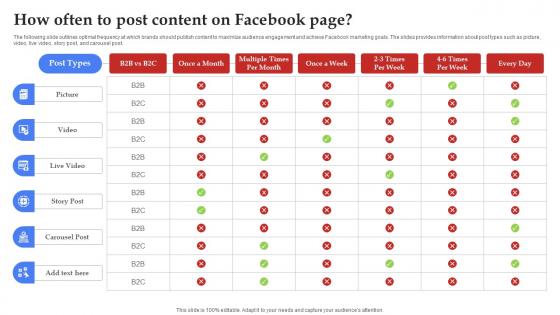
Facebook Marketing Techniques How Often To Post Content On Facebook Page Strategy SS V
The following slide outlines optimal frequency at which brands should publish content to maximize audience engagement and achieve Facebook marketing goals. The slides provides information about post types such as picture, video, live video, story post, and carousel post. Are you searching for a Facebook Marketing Techniques How Often To Post Content On Facebook Page Strategy SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Facebook Marketing Techniques How Often To Post Content On Facebook Page Strategy SS V from Slidegeeks today. The following slide outlines optimal frequency at which brands should publish content to maximize audience engagement and achieve Facebook marketing goals. The slides provides information about post types such as picture, video, live video, story post, and carousel post.
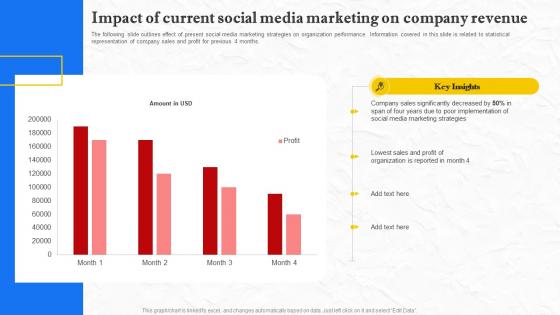
Facebook Marketing Techniques Impact Of Current Social Media Marketing Strategy SS V
The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Facebook Marketing Techniques Impact Of Current Social Media Marketing Strategy SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Facebook Marketing Techniques Impact Of Current Social Media Marketing Strategy SS V. The following slide outlines effect of present social media marketing strategies on organization performance. Information covered in this slide is related to statistical representation of company sales and profit for previous 4 months.
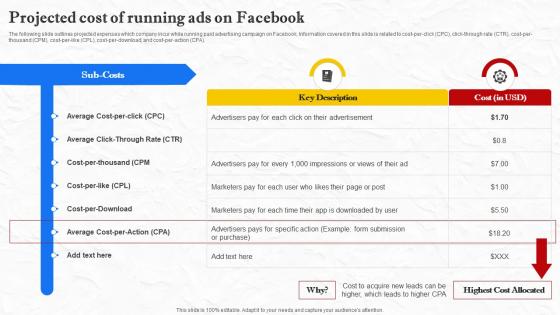
Facebook Marketing Techniques Projected Cost Of Running Ads On Facebook Strategy SS V
The following slide outlines projected expenses which company incur while running paid advertising campaign on Facebook. Information covered in this slide is related to cost-per-click CPC , click-through rate CTR , cost-per-thousand CPM , cost-per-like CPL , cost-per-download, and cost-per-action CPA . Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Facebook Marketing Techniques Projected Cost Of Running Ads On Facebook Strategy SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Facebook Marketing Techniques Projected Cost Of Running Ads On Facebook Strategy SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The following slide outlines projected expenses which company incur while running paid advertising campaign on Facebook. Information covered in this slide is related to cost-per-click CPC , click-through rate CTR , cost-per-thousand CPM , cost-per-like CPL , cost-per-download, and cost-per-action CPA .
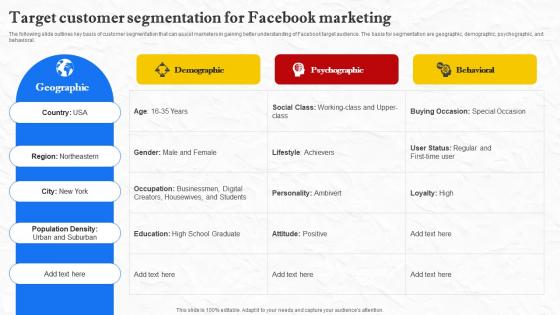
Facebook Marketing Techniques Target Customer Segmentation For Facebook Marketing Strategy SS V
The following slide outlines key basis of customer segmentation that can assist marketers in gaining better understanding of Facebook target audience. The basis for segmentation are geographic, demographic, psychographic, and behavioral. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Facebook Marketing Techniques Target Customer Segmentation For Facebook Marketing Strategy SS V can be your best option for delivering a presentation. Represent everything in detail using Facebook Marketing Techniques Target Customer Segmentation For Facebook Marketing Strategy SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide outlines key basis of customer segmentation that can assist marketers in gaining better understanding of Facebook target audience. The basis for segmentation are geographic, demographic, psychographic, and behavioral.
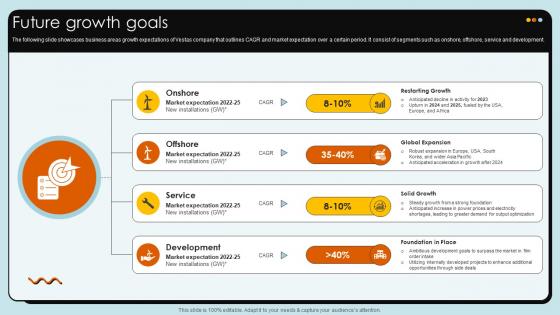
Future Growth Goals Wind Turbines Manufacturer Company Profile CP SS V
The following slide showcases business areas growth expectations of Vestas company that outlines CAGR and market expectation over a certain period. It consist of segments such as onshore, offshore, service and development.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Future Growth Goals Wind Turbines Manufacturer Company Profile CP SS V can be your best option for delivering a presentation. Represent everything in detail using Future Growth Goals Wind Turbines Manufacturer Company Profile CP SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. The following slide showcases business areas growth expectations of Vestas company that outlines CAGR and market expectation over a certain period. It consist of segments such as onshore, offshore, service and development.
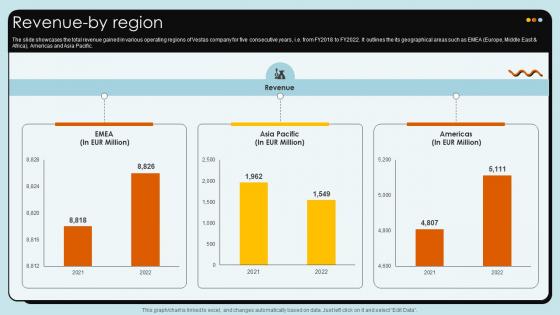
Revenue By Region Wind Turbines Manufacturer Company Profile CP SS V
The slide showcases the total revenue gained in various operating regions of Vestas company for five consecutive years, i.e. from FY2018 to FY2022. It outlines the its geographical areas such as EMEA Europe, Middle East and Africa, Americas and Asia Pacific.Retrieve professionally designed Revenue By Region Wind Turbines Manufacturer Company Profile CP SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. The slide showcases the total revenue gained in various operating regions of Vestas company for five consecutive years, i.e. from FY2018 to FY2022. It outlines the its geographical areas such as EMEA Europe, Middle East and Africa, Americas and Asia Pacific.
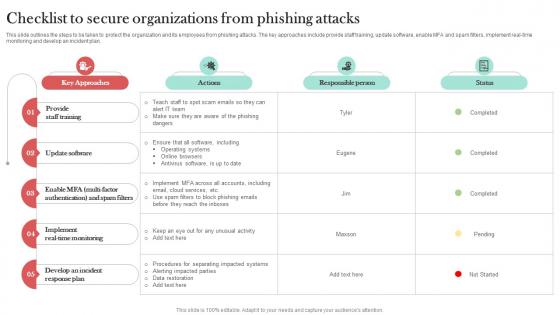
Checklist To Secure Organizations From Man In The Middle Phishing IT
This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Checklist To Secure Organizations From Man In The Middle Phishing IT template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Checklist To Secure Organizations From Man In The Middle Phishing IT that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan.
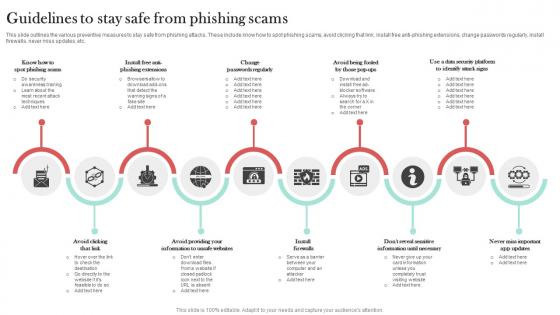
Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT
This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc. Explore a selection of the finest Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Guidelines To Stay Safe From Phishing Scams Man In The Middle Phishing IT to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc.
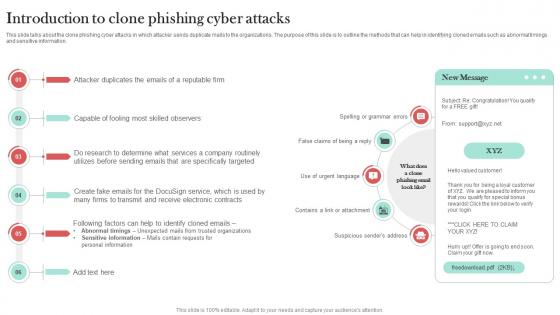
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information.
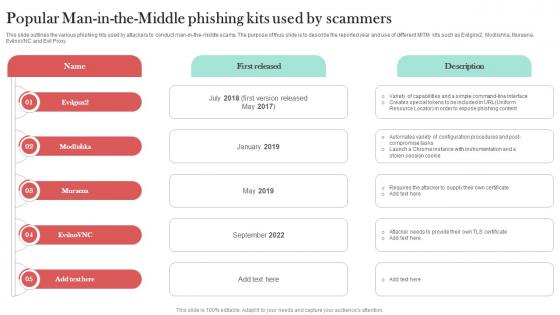
Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT
This slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and Evil Proxy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable Popular Man In The Middle Phishing Kits Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide outlines the various phishing kits used by attackers to conduct man-in-the-middle scams. The purpose of thus slide is to describe the reported year and use of different MITM kits such as Evilginx2, Modlishka, Muraena, EvilnoVNC and Evil Proxy.
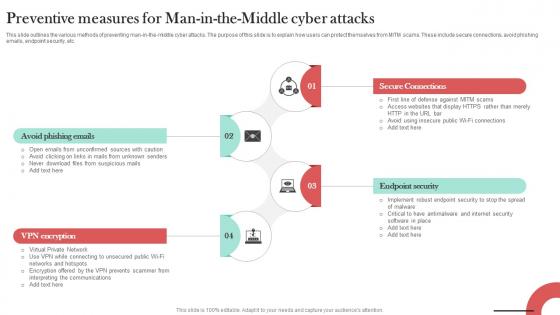
Preventive Measures For Man In The Middle Man In The Middle Phishing IT
This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Get a simple yet stunning designed Preventive Measures For Man In The Middle Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Preventive Measures For Man In The Middle Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc.
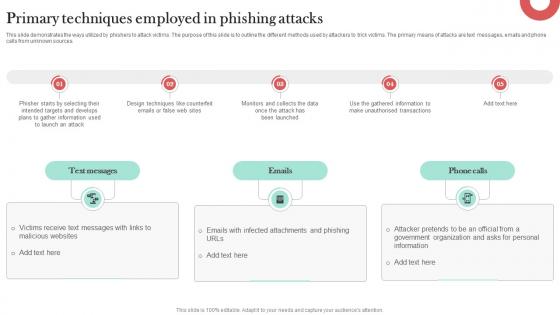
Primary Techniques Employed In Phishing Man In The Middle Phishing IT
This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Slidegeeks is here to make your presentations a breeze with Primary Techniques Employed In Phishing Man In The Middle Phishing IT With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources.
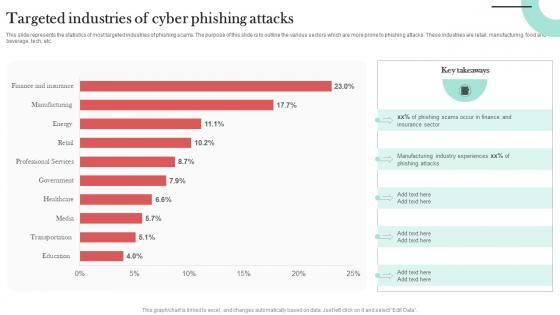
Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT
This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc.
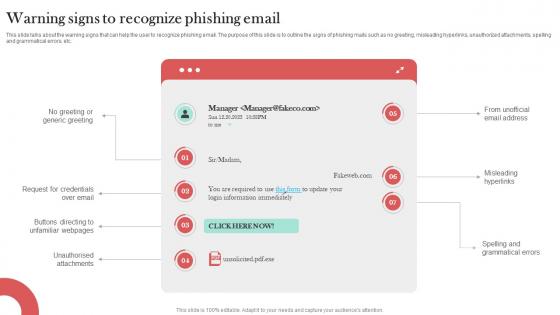
Warning Signs To Recognize Phishing Email Man In The Middle Phishing IT
This slide talks about the warning signs that can help the user to recognize phishing email. The purpose of this slide is to outline the signs of phishing mails such as no greeting, misleading hyperlinks, unauthorized attachments, spelling and grammatical errors, etc. Slidegeeks has constructed Warning Signs To Recognize Phishing Email Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide talks about the warning signs that can help the user to recognize phishing email. The purpose of this slide is to outline the signs of phishing mails such as no greeting, misleading hyperlinks, unauthorized attachments, spelling and grammatical errors, etc.

Increasing Business Awareness Implementing SEO Basics To Rank Website Higher Strategy SS V
This slide presents an outline of a strategic SEO plan to optimize websites to rank better on search engines. It includes information about SEO basics such as keyword research, content creation, on-page optimization, mobile responsiveness, site speed, and link building. This Increasing Business Awareness Implementing SEO Basics To Rank Website Higher Strategy SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Increasing Business Awareness Implementing SEO Basics To Rank Website Higher Strategy SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide presents an outline of a strategic SEO plan to optimize websites to rank better on search engines. It includes information about SEO basics such as keyword research, content creation, on-page optimization, mobile responsiveness, site speed, and link building.

Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Network Access Checklist To Build Zero Trust Network Access Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on.

Zero Trust Network Access Future And Emerging Trends In ZTNA Model
This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Future And Emerging Trends In ZTNA Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Future And Emerging Trends In ZTNA Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Future And Emerging Trends In ZTNA Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs. This slide outlines the future outlook and emerging trends in the zero trust network architecture model. The purpose of this slide is to showcase the various emerging future trends in the ZTNA model, including artificial intelligence, SASE, edge computing, the Internet of Things, and so on.

Zero Trust Network Access Key Characteristics Of Modern ZTNA Solution
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Network Access Key Characteristics Of Modern ZTNA Solution to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Network Access Key Characteristics Of Modern ZTNA Solution. This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering.


 Continue with Email
Continue with Email

 Home
Home


































