Process Safety

Issues Addressed By Dcaas Elements PDF
This slide brings forth various issues which are addressed by data service centers to provide users a solution in order to improve current business performance. The various issues addressed are data management, hyper converged infrastructure, data security and file storage. Presenting Issues Addressed By Dcaas Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Management, Data Security, Converged Infrastructure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
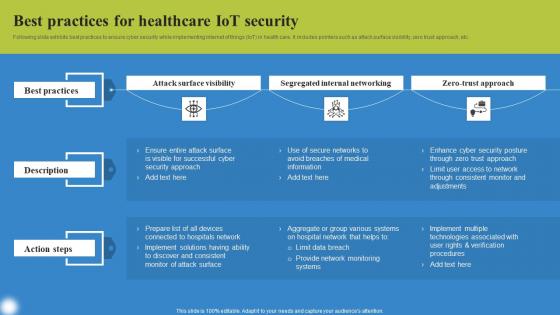
Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf
Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. This modern and well arranged Best Practices For Healthcare Deploying IoT Solutions For Enhanced Healthcare Template Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc.

Cloud Network Security Training Programs Timeline Download PDF
The slide showcases training programs to improve individuals level of awareness about security measures designed to protect cloud based infrastructure and data. The elements are SANS, infosec, ISC, edX with their completion timeline and pricing package . Showcasing this set of slides titled Cloud Network Security Training Programs Timeline Download PDF. The topics addressed in these templates are Training Programs, Models Controls, Offense Defense Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

KYC Transaction Monitoring System For Business Security Ppt PowerPoint Presentation Complete Deck With Slides
Incorporate this KYC Transaction Monitoring System For Business Security Ppt PowerPoint Presentation Complete Deck With Slides to define the objectives of business performance and how to drive results. List goals and outline a plan to achieve all your enterprise targets using this well crafted complete deck in seventy slides. Walk your audience through the key objectives of your business set-up, especially for customers and inspire them to work with diligence using this predesigned presentation template. Download now with the added assurance of a 100 percent customizable and editable product.
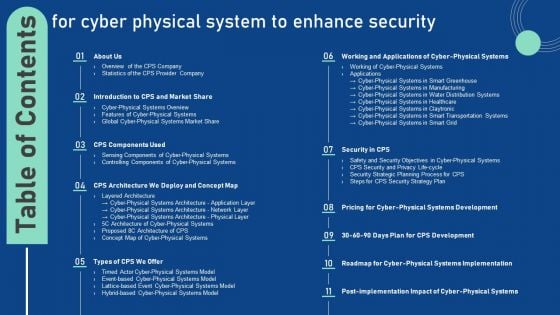
Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF.
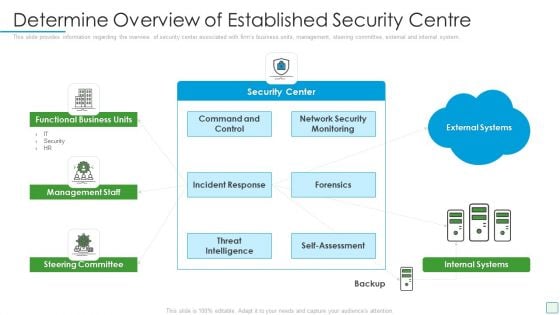
Developing Firm Security Strategy Plan Determine Overview Of Established Security Centre Download PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a developing firm security strategy plan determine overview of established security centre download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like functional business units, management staff, steering committee, internal systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Techniques And Strategies To Reduce Security Management Risks Security Risk Management Assessment Checklist Demonstration PDF
This slide shows a security risk management assessment checklist with multiple categories.Presenting techniques and strategies to reduce security management risks security risk management assessment checklist demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information security policy, security of third party access, responding to security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enterprise Resource Planning Assessment Checklist To Improve IT Security Brochure PDF
This slide signifies the enterprise resource planning evaluation to increase IT security. It covers information about automated testing tool, check system functionality and quality assurance etc. Pitch your topic with ease and precision using this Enterprise Resource Planning Assessment Checklist To Improve IT Security Brochure PDF. This layout presents information on Checklist, Execution, Functionality. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
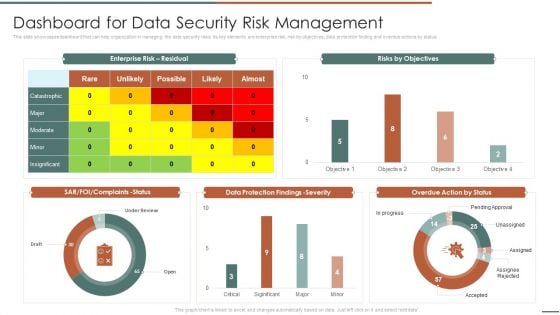
Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Dashboard For Data Security Risk Management Template PDF bundle. Topics like Complaints Status, Protection Findings, Overdue Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web App Firewall Services IT Impact Of Web Application Firewall Sample PDF
This slide represents the Web Application Firewall deployment pricing, and it covers the price list for resource types such as bot control, requests, and management. Deliver an awe inspiring pitch with this creative web app firewall services it impact of web application firewall sample pdf bundle. Topics like reduced, security expenses, revenue can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
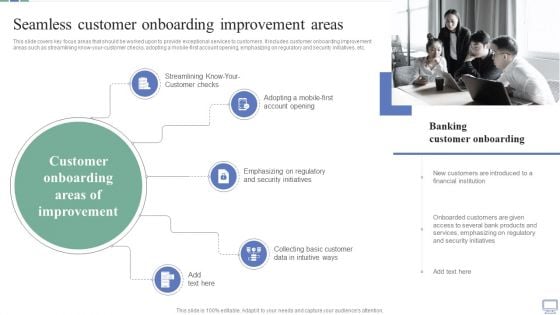
Omnichannel Banking Services Platform Seamless Customer Onboarding Improvement Areas Pictures PDF
This slide covers key focus areas that should be worked upon to provide exceptional services to customers. It includes customer onboarding improvement areas such as streamlining know your customer checks, adopting a mobile first account opening, emphasizing on regulatory and security initiatives, etc. This Omnichannel Banking Services Platform Seamless Customer Onboarding Improvement Areas Pictures PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Omnichannel Banking Services Platform Seamless Customer Onboarding Improvement Areas Pictures PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF
Showcasing this set of slides titled Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF. The topics addressed in these templates are Endpoint Security, Network Security, Messaging Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Desktop Security Management Managing Computer Security 90 Days Plan Professional PDF
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative desktop security management managing computer security 90 days plan professional pdf bundle. Topics like awareness, security, information, resources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective Mobile Device Security Management Mobile Device Security Management Professional PDF
This slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events associated to mobile device. Deliver an awe inspiring pitch with this creative Effective Mobile Device Security Management Mobile Device Security Management Professional PDF bundle. Topics like Security Requirement, Authorized Revoked, Access Violations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Best Practices Employees Ppt PowerPoint Presentation Styles Example Cpb
Presenting this set of slides with name information security best practices employees ppt powerpoint presentation styles example cpb. This is an editable Powerpoint four stages graphic that deals with topics like information security best practices employees to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Web App Security Practices Ppt PowerPoint Presentation Show Portfolio Cpb Pdf
Presenting this set of slides with name web app security practices ppt powerpoint presentation show portfolio cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like web app security practices to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. This is a IT Security Automation Tools Integration Unified Platform Integration For Security Automation Pictures PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Firewalls, IDPS, SIEM, Privileged Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Governance Procedure Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured security governance procedure management plan ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
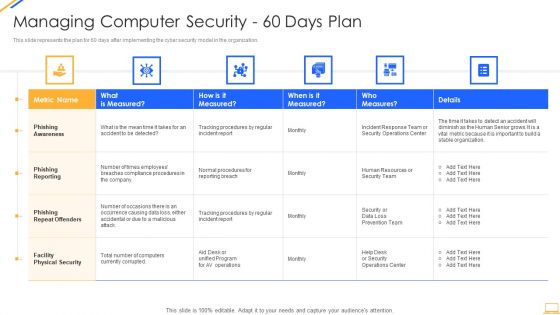
Desktop Security Management Managing Computer Security 60 Days Plan Ideas PDF
This slide represents the plan for 60 days after implementing the cyber security model in the organization. This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver and pitch your topic in the best possible manner with this desktop security management managing computer security 60 days plan ideas pdf. Use them to share invaluable insights on security, team, organization, awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
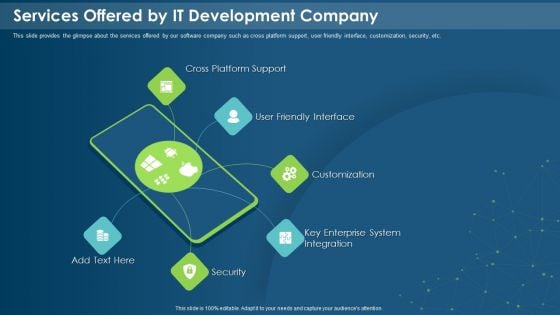
IT Development Company Pitch Deck Services Offered By IT Development Company Download PDF
This slide provides the glimpse about the services offered by our software company such as cross platform support, user friendly interface, customization, security, etc. Presenting it development company pitch deck services offered by it development company download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cross platform support, user friendly interface, customization, key enterprise system integration, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
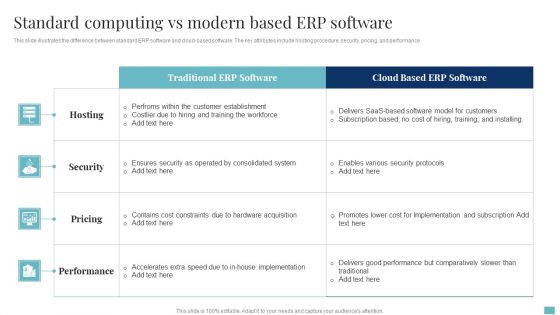
Standard Computing Vs Modern Based Erp Software Download PDF
This slide illustrates the difference between standard ERP software and cloud based software. The key attributes include hosting procedure, security, pricing, and performance. Showcasing this set of slides titled Standard Computing Vs Modern Based Erp Software Download PDF. The topics addressed in these templates are Security, Pricing, Performance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
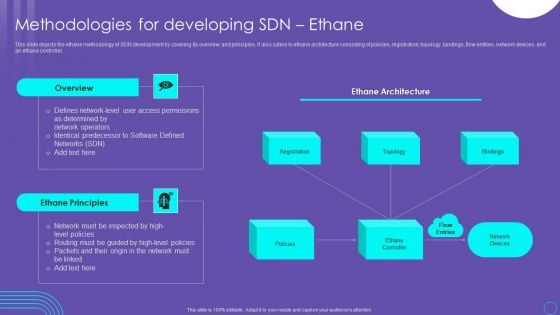
SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF
This slide depicts the ethane methodology of SDN development by covering its overview and principles. It also caters to ethane architecture consisting of policies, registration, topology, bindings, flow entities, network devices, and an ethane controller. This SDN Security Architecture Methodologies For Developing SDN Ethane Infographics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
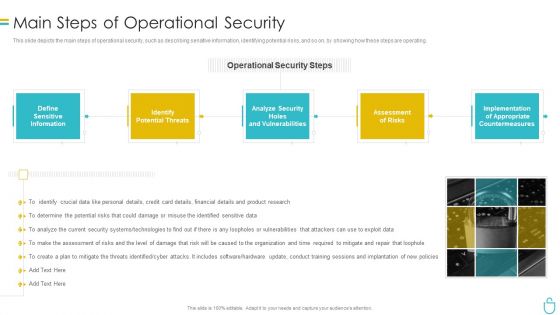
Information Security Main Steps Of Operational Security Ppt Inspiration Show PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting information security main steps of operational security ppt inspiration show pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like sensitive information, potential threats, analyze security, assessment of risks, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Risk Management Plan Information Security Risk Management Dashboard Sample PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative cyber security risk management plan information security risk management dashboard sample pdf bundle. Topics like vulnerabilities, entities, action plan, risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
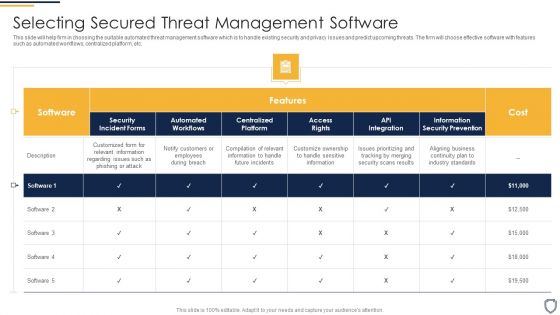
Corporate Security And Risk Management Selecting Secured Threat Management Software Introduction PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management selecting secured threat management software introduction pdf bundle. Topics like selecting secured threat management software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ITIL Strategy Service Excellence What Services Do We Offer To Clients Ppt PowerPoint Presentation Pictures Structure PDF
Presenting this set of slides with name itil strategy service excellence what services do we offer to clients ppt powerpoint presentation pictures structure pdf. The topics discussed in these slides are core offerings, server monitoring, network monitoring, backup monitoring, application monitoring, patch management, automated maintenance, performance reporting, endpoint security esm. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Find highly impressive CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download CYBER Security Breache Response Strategy Cyber Security Incident Management Checklist Before An Incident Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Techniques And Strategies To Reduce Security Management Risks Suggested Coverage For Security Management Plan Information PDF
This slide provides information about the areas that are covered under the security management plan.This is a techniques and strategies to reduce security management risks suggested coverage for security management plan information pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like governance arrangement, information including, personnel security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Prevention Recognition Security Training Program Frameworks Mockup PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security training program frameworks mockup pdf. Use them to share invaluable insights on target audience, training success, instruction information sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Training Program Frameworks Contd Ppt Pictures Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative Security Training Program Frameworks Contd Ppt Pictures Layout Ideas Pdf bundle. Topics like measures, implement, programs, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ITIL Service Design Overview Ppt Influencers PDF
This slide depicts the overview of ITIL service design, including easy to use services, to obtain ROI, balanced functionality, cost and performance, dependable and predictable IT service, etc. Presenting itil service design overview ppt influencers pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like services, potential risk, service, security, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icons Slide For Mobile Device Security Management Mobile Device Security Management Inspiration PDF
Download our innovative and attention grabbing Icons Slide For Mobile Device Security Management Mobile Device Security Management Inspiration PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
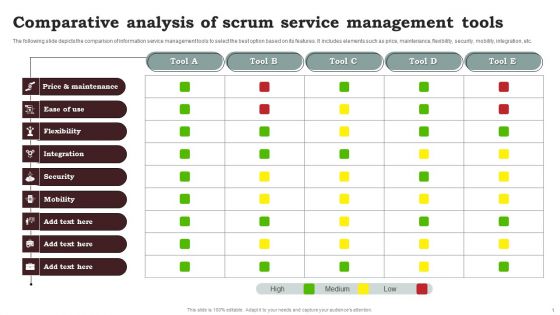
Comparative Analysis Of Scrum Service Management Tools Clipart PDF
The following slide depicts the comparison of information service management tools to select the best option based on its features. It includes elements such as price, maintenance, flexibility, security, mobility, integration, etc. Showcasing this set of slides titled Comparative Analysis Of Scrum Service Management Tools Clipart PDF. The topics addressed in these templates are Comparative Analysis, Scrum Service, Management Tools. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
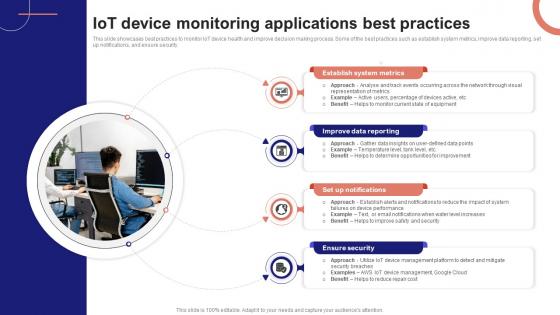
IoT Device Management Fundamentals IoT Device Monitoring Applications Best Practices IoT Ss V
This slide showcases best practices to monitor IoT device health and improve decision making process. Some of the best practices such as establish system metrics, improve data reporting, set up notifications, and ensure security. Present like a pro with IoT Device Management Fundamentals IoT Device Monitoring Applications Best Practices IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases best practices to monitor IoT device health and improve decision making process. Some of the best practices such as establish system metrics, improve data reporting, set up notifications, and ensure security.
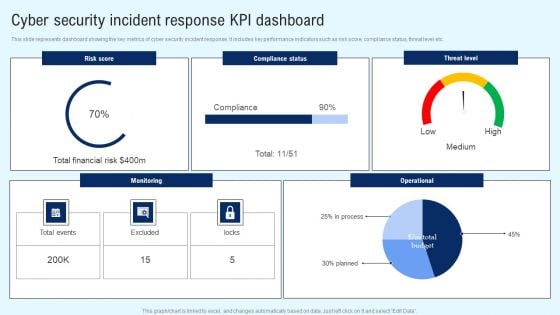
Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response KPI Dashboard Clipart PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
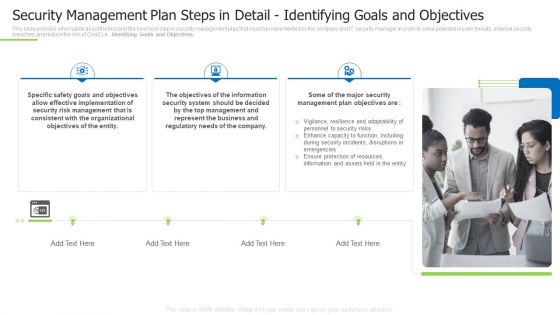
Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps In Detail Inspiration PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a techniques and strategies to reduce security management risks security management plan steps in detail inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like effective implementation, consistent with the organizational, represent the business You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
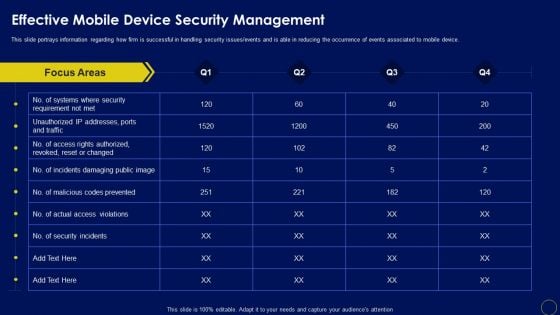
Effective Mobile Device Security Management Business Mobile Device Security Management And Mitigation Brochure PDF
This slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events associated to mobile device. Create an editable Effective Mobile Device Security Management Business Mobile Device Security Management And Mitigation Brochure PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Effective Mobile Device Security Management Business Mobile Device Security Management And Mitigation Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Security Implementation Framework Selecting Security Incident Management Software Microsoft PDF
Presenting this set of slides with name cyber security implementation framework selecting security incident management software microsoft pdf. The topics discussed in these slides are security incident forms, automated workflows, centralized platform, access rights, api integration, cost, information security prevention. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Risk Management Model For Data Security Budget For Information Security Management Sample PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Budget For Information Security Management Sample PDF bundle. Topics like Functional Area, Training Duration, Risk Management, Incident Management, Asset Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF
This slide represents the overview of the software development life cycle, including its goal, international standard, way of creating, designing, and developing software.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF.
Wireless Network Security System Camera Connected With Computer System Portrait PDF
Presenting wireless network security system camera connected with computer system portrait pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including wireless network security system camera connected with computer system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
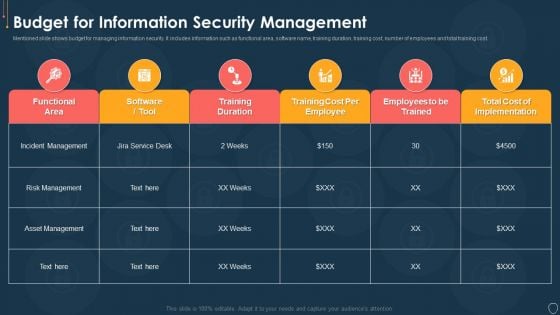
Cyber Security Risk Management Plan Budget For Information Security Management Brochure PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver an awe inspiring pitch with this creative cyber security risk management plan budget for information security management brochure pdf bundle. Topics like functional area, software name, training duration, training cost, number of employees, total training cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
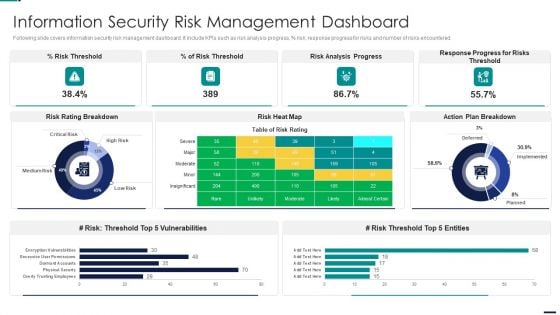
Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF bundle. Topics like Risk Threshold, Risk Analysis Progress, Response Progress For Risks Threshold, Action Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Risk Evaluation Framework For Information Security Risk Management Icons PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyze risks, evaluate and treat risks.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Framework For Information Security Risk Management Icons PDF. Use them to share invaluable insights on Establish The Context, Identify Risks, Analyze Risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
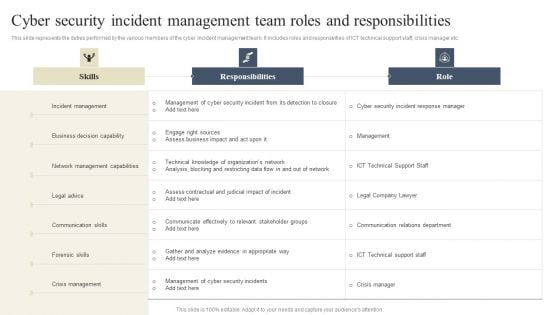
CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. If you are looking for a format to display your unique thoughts, then the professionally designed CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Incorporating HIS To Enhance Healthcare Services Comparative Analysis Of Health Management Information System Tools Summary PDF
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incorporating HIS To Enhance Healthcare Services Comparative Analysis Of Health Management Information System Tools Summary PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incorporating HIS To Enhance Healthcare Services Comparative Analysis Of Health Management Information System Tools Summary PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
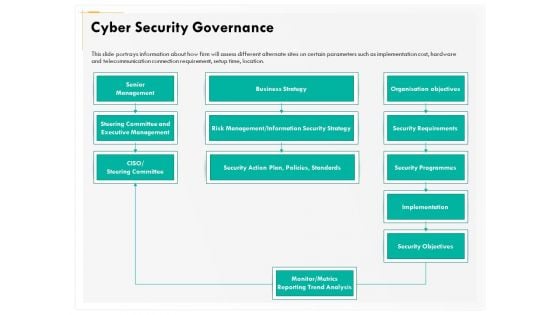
Computer Security Incident Handling Cyber Security Governance Ppt Gallery Summary PDF
Presenting this set of slides with name computer security incident handling cyber security governance ppt gallery summary pdf. The topics discussed in these slides are senior management, business strategy, security objectives, implementation, security requirements, risk management or information security strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
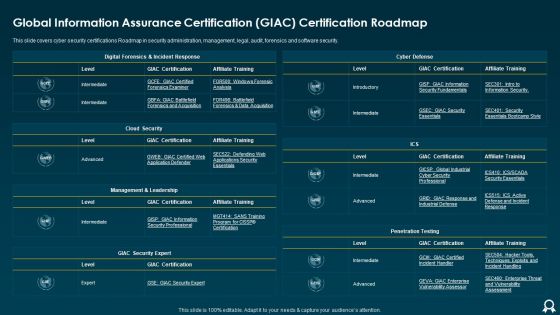
Global Information Assurance Certification GIAC Certification Roadmap Formats PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver an awe inspiring pitch with this creative Global Information Assurance Certification GIAC Certification Roadmap Formats PDF bundle. Topics like Cloud Security, Cyber Defense, Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Service Desk Incident Management Framework Digitalization Of Service Desk Administration Ppt File Design Inspiration PDF
This slide showcases service desk incident management framework. It provides information about incident identification, information security management, incident diagnosis, register incident, verify user issue, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Service Desk Incident Management Framework Digitalization Of Service Desk Administration Ppt File Design Inspiration PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Implementing Advanced Service Help Desk Administration Program Service Desk Incident Management Framework Pictures PDF
This slide showcases service desk incident management framework. It provides information about incident identification, information security management, incident diagnosis, register incident, verify user issue, etc. Find a pre-designed and impeccableImplementing Advanced Service Help Desk Administration Program Service Desk Incident Management Framework Pictures PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Competitor Analysis Grid Of Security Software Inspiration PDF
This slide provides an overview of the comparison among various software. The comparison is done on the basis of features that are antivirus, firewall, system cleansing, anti-spyware and parental control. Pitch your topic with ease and precision using this Competitor Analysis Grid Of Security Software Inspiration PDF. This layout presents information on System Cleansing, Everyday Backup Option, Anti Spyware. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
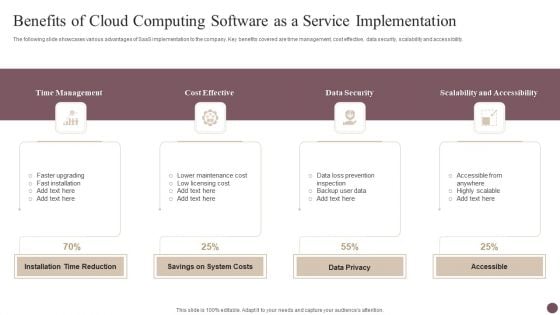
Benefits Of Cloud Computing Software As A Service Implementation Slides PDF
The following slide showcases various advantages of SaaS implementation to the company. Key benefits covered are time management, cost effective, data security, scalability and accessibility. Presenting Benefits Of Cloud Computing Software As A Service Implementation Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Time Management, Cost Effective, Data Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Roadmap For Information Technology Security Training Ppt Layouts Vector PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a it security roadmap for information technology security training ppt layouts vector pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring physical security, ensuring data security, mobile and remote computing best practices, safe and computing best practices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
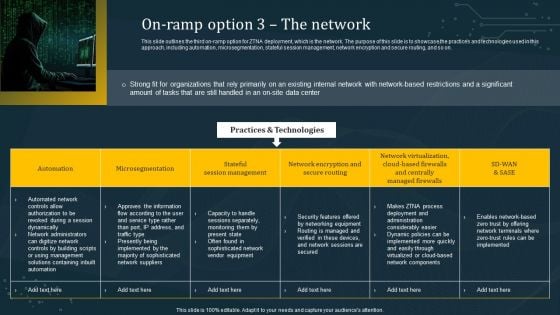
On Ramp Option 3 The Network Structure PDF
This slide outlines the third on-ramp option for ZTNA deployment, which is the network. The purpose of this slide is to showcase the practices and technologies used in this approach, including automation, microsegmentation, stateful session management, network encryption and secure routing, and so on. Do you know about Slidesgeeks On Ramp Option 3 The Network Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
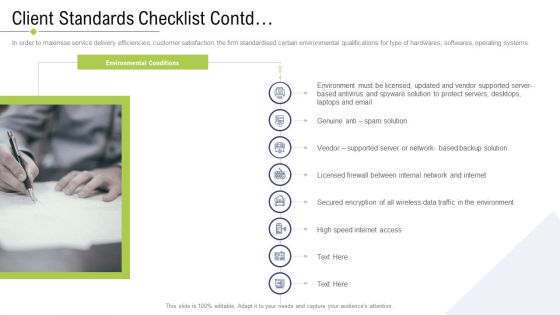
Technology Facility Maintenance And Provider Client Standards Checklist Contd Clipart PDF
In order to maximise service delivery efficiencies, customer satisfaction, the firm standardised certain environmental qualifications for type of hardwares, softwares, operating systems. This is a technology facility maintenance and provider client standards checklist contd clipart pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secured encryption, protect servers, internal network, high speed internet access . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
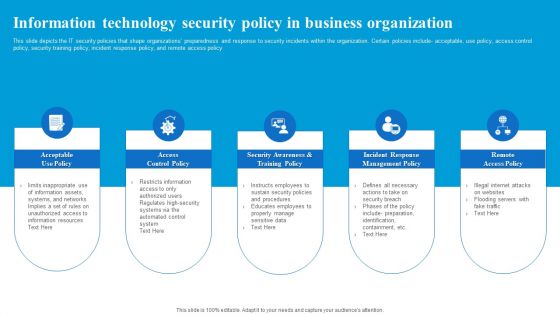
Information Technology Security Policy In Business Organization Download PDF
This slide depicts the IT security policies that shape organizations preparedness and response to security incidents within the organization. Certain policies include acceptable, use policy, access control policy, security training policy, incident response policy, and remote access policy. Presenting Information Technology Security Policy In Business Organization Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Access Control Policy, Acceptable Use Policy, Remote Access Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF
The following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Take your projects to the next level with our ultimate collection of Kpis To Evaluate Cyber Security Risk Management Ppt PowerPoint Presentation File Outline PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
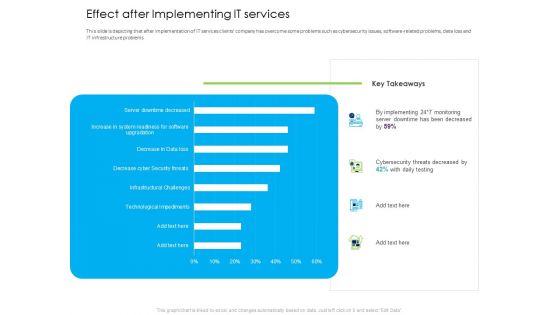
Managed IT Services Pricing Model Effect After Implementing IT Services Professional PDF
This slide is depicting that after implementation of IT services clients company has overcome some problems such as cybersecurity issues, software-related problems, data loss and IT infrastructure problems. Deliver and pitch your topic in the best possible manner with this managed it services pricing model effect after implementing it services professional pdf. Use them to share invaluable insights on infrastructural challenges, technological impediments, decrease cyber security threats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
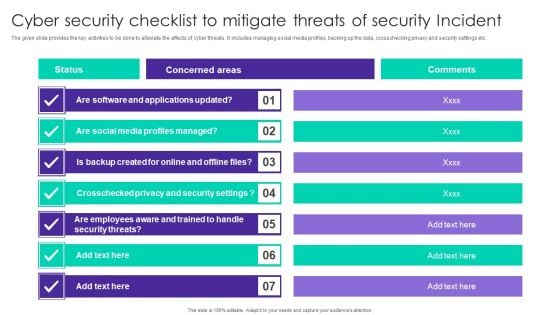
Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF
The given slide provides the key activities to be done to alleviate the effects of cyber threats. It includes managing social media profiles, backing up the data, crosschecking privacy and security settings etc. Showcasing this set of slides titled Cyber Security Checklist To Mitigate Threats Of Security Incident Ppt Model Example PDF. The topics addressed in these templates are Concerned Areas, Social Media Profiles, Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


 Continue with Email
Continue with Email

 Home
Home


































