Process Safety
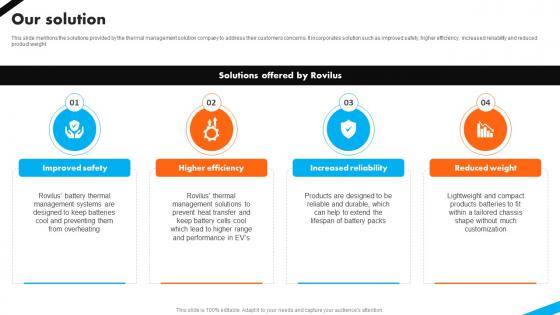
Our Solution Automotive Battery Manufacturer Investor Funding Elevator Pitch Deck
This slide mentions the solutions provided by the thermal management solution company to address their customers concerns. It incorporates solution such as improved safety, higher efficiency, increased reliability and reduced product weight.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Our Solution Automotive Battery Manufacturer Investor Funding Elevator Pitch Deck template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Our Solution Automotive Battery Manufacturer Investor Funding Elevator Pitch Deck that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide mentions the solutions provided by the thermal management solution company to address their customers concerns. It incorporates solution such as improved safety, higher efficiency, increased reliability and reduced product weight.

Ethical Considerations In Artificial Intelligence Of Things AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society. Make sure to capture your audiences attention in your business displays with our gratis customizable Ethical Considerations In Artificial Intelligence Of Things AIOT Applications For Various Industries IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society.

Hospitality Sector Laws And Regulations Lodging And Accommodation Industry IR SS V
This slide showcases the hospitality industry laws and regulations which includes licensing and permits, health and safety, employment laws and alcohol regulations. Welcome to our selection of the Hospitality Sector Laws And Regulations Lodging And Accommodation Industry IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide showcases the hospitality industry laws and regulations which includes licensing and permits, health and safety, employment laws and alcohol regulations.
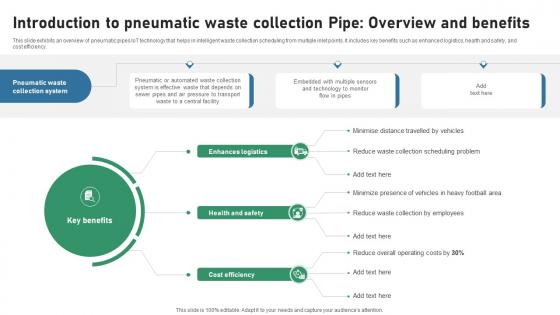
Introduction To Pneumatic Waste Collection Pipe Overview IOT Applications In Smart Waste IoT SS V
This slide exhibits an overview of pneumatic pipes IoT technology that helps in intelligent waste collection scheduling from multiple inlet points. It includes key benefits such as enhanced logistics, health and safety, and cost efficiency. This modern and well-arranged Introduction To Pneumatic Waste Collection Pipe Overview IOT Applications In Smart Waste IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide exhibits an overview of pneumatic pipes IoT technology that helps in intelligent waste collection scheduling from multiple inlet points. It includes key benefits such as enhanced logistics, health and safety, and cost efficiency.
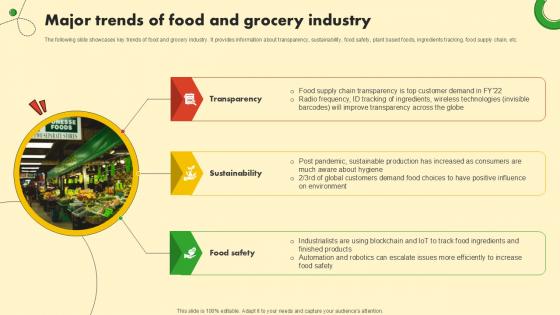
Major Trends Of Food And Grocery Industry Food And Grocery Retail Ppt Presentation
The following slide showcases key trends of food and grocery industry. It provides information about transparency, sustainability, food safety, plant based foods, ingredients tracking, food supply chain, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Major Trends Of Food And Grocery Industry Food And Grocery Retail Ppt Presentation and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates The following slide showcases key trends of food and grocery industry. It provides information about transparency, sustainability, food safety, plant based foods, ingredients tracking, food supply chain, etc.
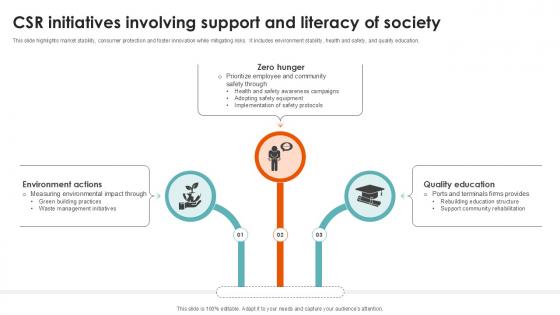
Csr Initiatives Involving Sup Port Terminal Industry Ppt Example
This slide highlights market stability, consumer protection and foster innovation while mitigating risks. It includes environment stability, health and safety, and quality education. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Csr Initiatives Involving Sup Port Terminal Industry Ppt Example a try. Our experts have put a lot of knowledge and effort into creating this impeccable Csr Initiatives Involving Sup Port Terminal Industry Ppt Example. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide highlights market stability, consumer protection and foster innovation while mitigating risks. It includes environment stability, health and safety, and quality education.

Optimization Of IoT Remote Monitoring Security System Used In Smart Homes For Protection IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. This Optimization Of IoT Remote Monitoring Security System Used In Smart Homes For Protection IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Optimization Of IoT Remote Monitoring Security System Used In Smart Homes For Protection IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities.
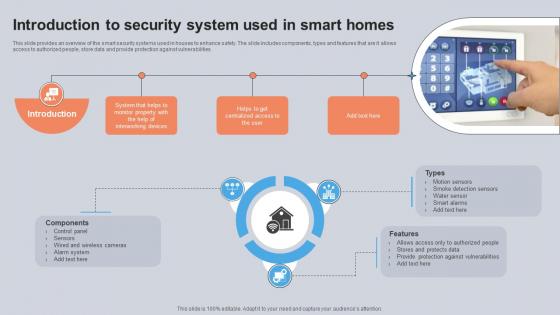
Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Create an editable Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities.

Unlocking Potential IoTs Application Role Of IoT In Transportation Industry With Benefits IoT SS V
This slide showcases the role of IoT in the transportation industry to improve system processes. It incorporates the advantages of deploying IoT, such as improved efficiency, increased safety, enhanced security, reduced cost, and improved customer experiences. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Unlocking Potential IoTs Application Role Of IoT In Transportation Industry With Benefits IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide showcases the role of IoT in the transportation industry to improve system processes. It incorporates the advantages of deploying IoT, such as improved efficiency, increased safety, enhanced security, reduced cost, and improved customer experiences.
Business Benefits Of IoT Analytics Internet Of Things Analysis Icons Pdf
This slide gives benefits of using IoT analytics in business. The purpose of this slide is to explain how IoT analytics can help in optimizing operational efficiency, reducing cost, enhancing customer experience, improving safety, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Business Benefits Of IoT Analytics Internet Of Things Analysis Icons Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Business Benefits Of IoT Analytics Internet Of Things Analysis Icons Pdf today and make your presentation stand out from the rest. This slide gives benefits of using IoT analytics in business. The purpose of this slide is to explain how IoT analytics can help in optimizing operational efficiency, reducing cost, enhancing customer experience, improving safety, etc.

Major Drivers For Adopting Industrial Internet Of Things Optimizing Inventory Management IoT SS V
This slide provides an overview of the main drivers for adopting IoT in manufacturing and streamlining operations. Major drivers covered are reduced cost, shorter marketing time, mass personalization and better safety. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Major Drivers For Adopting Industrial Internet Of Things Optimizing Inventory Management IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide provides an overview of the main drivers for adopting IoT in manufacturing and streamlining operations. Major drivers covered are reduced cost, shorter marketing time, mass personalization and better safety.

Why Should Organizations Invest In Cobots Cobots For Improved Productivity Brochure PDF
This slide describes the reasons for organizations to invest in cobots. It includes low-cost, safety, flexibility, more straightforward automation for all sizes of organizations, and is designed to work in a shared environment. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Why Should Organizations Invest In Cobots Cobots For Improved Productivity Brochure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Why Should Organizations Invest In Cobots Cobots For Improved Productivity Brochure PDF This slide describes the reasons for organizations to invest in cobots. It includes low-cost, safety, flexibility, more straightforward automation for all sizes of organizations, and is designed to work in a shared environment.
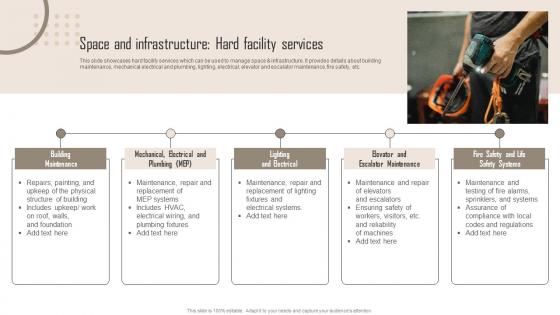
Space And Comprehensive Guide For Building Management Themes Pdf
This slide showcases hard facility services which can be used to manage space and infrastructure. It provides details about building maintenance, mechanical electrical and plumbing, lighting, electrical, elevator and escalator maintenance, fire safety, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Space And Comprehensive Guide For Building Management Themes Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Space And Comprehensive Guide For Building Management Themes Pdf. This slide showcases hard facility services which can be used to manage space and infrastructure. It provides details about building maintenance, mechanical electrical and plumbing, lighting, electrical, elevator and escalator maintenance, fire safety, etc.

IoT Solutions For Oil IoT Applications To Enhance Environment Monitoring IoT SS V
This slide highlights applications of IoT technology to reduce environmental footprint and enhance safety. It includes applications such as air quality monitoring, water and soil monitoring, and weather and climate monitoring. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IoT Solutions For Oil IoT Applications To Enhance Environment Monitoring IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IoT Solutions For Oil IoT Applications To Enhance Environment Monitoring IoT SS V. This slide highlights applications of IoT technology to reduce environmental footprint and enhance safety. It includes applications such as air quality monitoring, water and soil monitoring, and weather and climate monitoring.
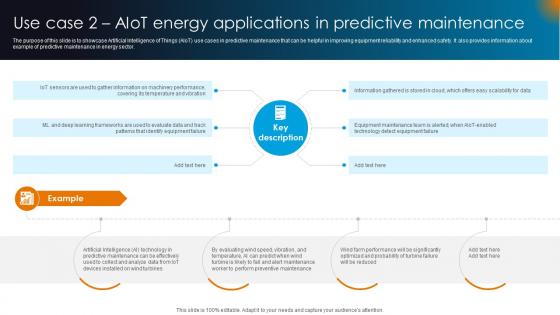
Integrating AI With IoT Use Case 2 AIoT Energy Applications In Predictive Maintenance IoT SS V
The purpose of this slide is to showcase Artificial Intelligence of Things AIoT use cases in predictive maintenance that can be helpful in improving equipment reliability and enhanced safety. It also provides information about example of predictive maintenance in energy sector. This Integrating AI With IoT Use Case 2 AIoT Energy Applications In Predictive Maintenance IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Integrating AI With IoT Use Case 2 AIoT Energy Applications In Predictive Maintenance IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The purpose of this slide is to showcase Artificial Intelligence of Things AIoT use cases in predictive maintenance that can be helpful in improving equipment reliability and enhanced safety. It also provides information about example of predictive maintenance in energy sector.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
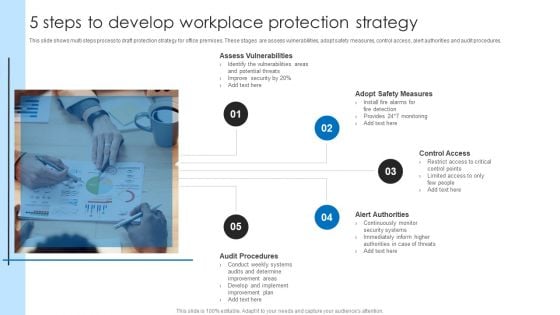
5 Steps To Develop Workplace Protection Strategy Sample PDF
This slide shows multi steps process to draft protection strategy for office premises. These stages are assess vulnerabilities, adopt safety measures, control access, alert authorities and audit procedures. Presenting 5 Steps To Develop Workplace Protection Strategy Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assess Vulnerabilities, Control Access, Alert Authorities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Lean Operational Excellence Strategy Training Programs For Workplace Management Infographics PDF
This slide showcases lean training programs for process improvements and increase employees efficiency. Key programs highlighted here are practicing kata, TWI problem solving, equipment training, job safety etc. Pitch your topic with ease and precision using this Lean Operational Excellence Strategy Training Programs For Workplace Management Infographics PDF. This layout presents information on Training Program, Program Highlights, Duration. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
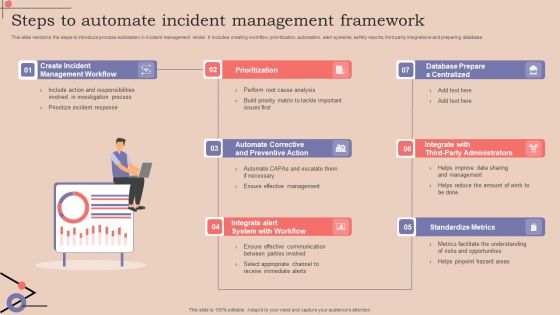
Steps To Automate Incident Management Framework Brochure PDF
This slide mentions the steps to introduce process automation in incident management model. It includes creating workflow, prioritization, automation, alert systems, safety reports, third party integrations and preparing database. Persuade your audience using this Steps To Automate Incident Management Framework Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Management, Analysis, Communication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Conceptual Structure For Organizational Compliance Risk Information PDF
Following slide shows business compliance risk process framework. Purpose of this slide is identify, evaluate and address business potential threats. It include steps such as identify potential threats, evaluate threats, develop prevention plans, evaluate preventive action results etc. Showcasing this set of slides titled Conceptual Structure For Organizational Compliance Risk Information PDF. The topics addressed in these templates are Determine Potential Threats, Evaluate Threats, Develop Prevention Safety Plans. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Awareness Areas For Effective Planning And Communication Demonstration Pdf
This slide showcases process of initiating cybersecurity communication plan. This template focuses on protecting information to ensure that it is not corrupted. It includes information related to network security,malware protection, etc.Showcasing this set of slides titled Cybersecurity Awareness Areas For Effective Planning And Communication Demonstration Pdf The topics addressed in these templates are Network Safety, Awareness Education, Secure Construction All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcases process of initiating cybersecurity communication plan. This template focuses on protecting information to ensure that it is not corrupted. It includes information related to network security,malware protection, etc.

Building Trust With IoT Security Understanding Software Security Attacks In IoT Landscape IoT SS V
This slide presents an overview and types of software security threats, helpful in identifying potential areas of vulnerabilities. It includes types such as denial of service attacks, phishing attacks, malicious scripts, and worms and spyware. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Understanding Software Security Attacks In IoT Landscape IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide presents an overview and types of software security threats, helpful in identifying potential areas of vulnerabilities. It includes types such as denial of service attacks, phishing attacks, malicious scripts, and worms and spyware.
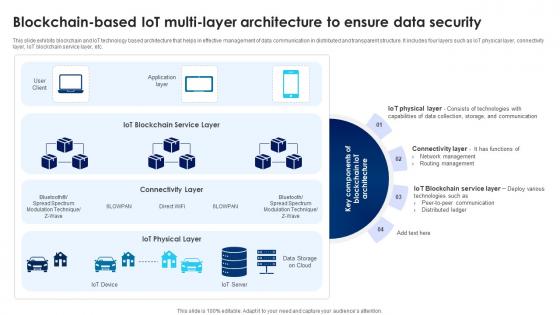
Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V
This slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc. Get a simple yet stunning designed Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Building Trust With IoT Security Blockchain Based IoT Multi Layer Architecture To Ensure Data IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide exhibits blockchain and IoT technology based architecture that helps in effective management of data communication in distributed and transparent structure. It includes four layers such as IoT physical layer, connectivity layer, IoT blockchain service layer, etc.

Key Partnerships Security Service Provider Business Model BMC SS V
This slide showcases the essential relationship that the firm builds to enhance functioning. It includes technology partners, service providers and independent software sellers. Present like a pro with Key Partnerships Security Service Provider Business Model BMC SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases the essential relationship that the firm builds to enhance functioning. It includes technology partners, service providers and independent software sellers.

Building Trust With IoT Security Automated Patch Management To Increase Overall Productivity IoT SS V
This slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies. It includes steps such as scan for missing patches, collect patches from vendors, deploy patches, and report results. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Automated Patch Management To Increase Overall Productivity IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide includes an automated patch management process that ensures patch availability on devices in accordance with deployment policies. It includes steps such as scan for missing patches, collect patches from vendors, deploy patches, and report results.
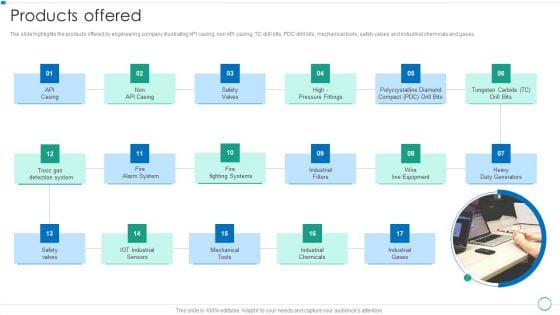
Real Estate Construction And Engineering Company Profile Products Offered Demonstration PDF
The slide highlights the products offered by engineering company illustrating API casing, non API casing, TC drill bits, PDC drill bits, mechanical tools, safety valves and industrial chemicals and gases.This is a Real Estate Construction And Engineering Company Profile Products Offered Demonstration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Bridges Development, Processing Factory, Refinery Improvement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V
This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Building Trust With IoT Security IoT Data Security Vulnerabilities And Privacy Concerns IoT SS V from Slidegeeks and deliver a wonderful presentation. This slide includes common IoT security vulnerabilities and risk that helps organization implement security measures. It includes vulnerabilities such as lack of privacy protection, improper device management approach, default settings, weak credentials, etc.

Building Trust With IoT Security Case Study 2 Improving Connected Home Security With Aws IoT SS V
This slide exhibits case study showcasing how AWS solutions helps consumer product company in enhancing connected home products security. It includes elements such as business goals, challenges, IoT solutions, and results. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Building Trust With IoT Security Case Study 2 Improving Connected Home Security With Aws IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Building Trust With IoT Security Case Study 2 Improving Connected Home Security With Aws IoT SS V today and make your presentation stand out from the rest This slide exhibits case study showcasing how AWS solutions helps consumer product company in enhancing connected home products security. It includes elements such as business goals, challenges, IoT solutions, and results.

Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V
This slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation. It includes malicious code injection, malicious node injection, node tampering, and RF interference on radio frequency identification. Find highly impressive Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Building Trust With IoT Security Understanding Physical Security Attacks In IoT Landscape IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide presents an overview and types of physical security threats, helpful in identifying areas for strict regulation. It includes malicious code injection, malicious node injection, node tampering, and RF interference on radio frequency identification.
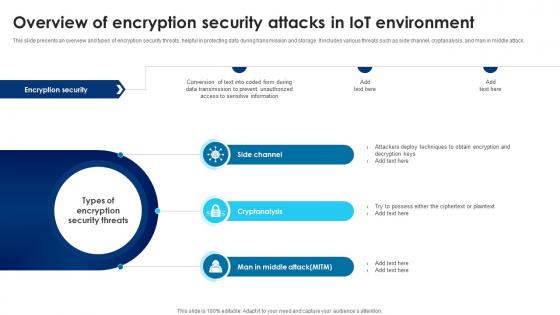
Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack.
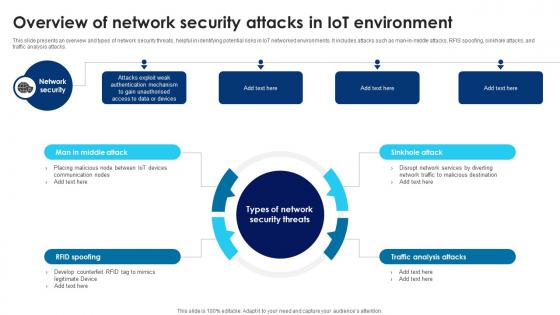
Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks. There are so many reasons you need a Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks.
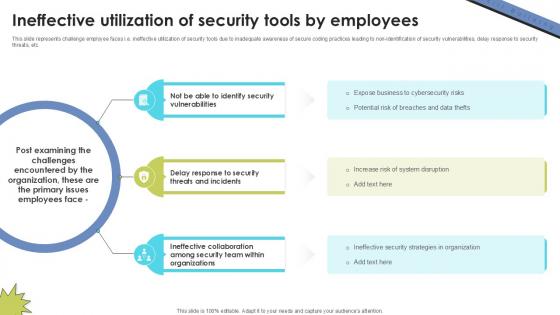
Ineffective Utilization Of Security Skill Building Plan For Application PPT Presentation DTE SS V
This slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non-identification of security vulnerabilities, delay response to security threats, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Ineffective Utilization Of Security Skill Building Plan For Application PPT Presentation DTE SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents challenge employee faces i.e. ineffective utilization of security tools due to inadequate awareness of secure coding practices leading to non-identification of security vulnerabilities, delay response to security threats, etc.
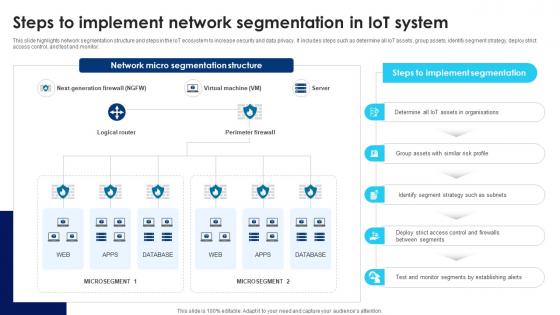
Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V
This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Slidegeeks is here to make your presentations a breeze with Building Trust With IoT Security Steps To Implement Network Segmentation In IoT System IoT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor.
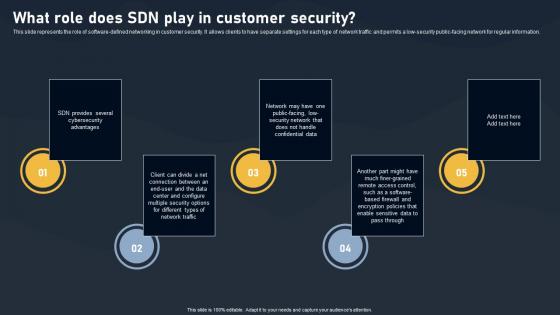
What Role Does SDN Play In Customer Security SDN Building Blocks Topics Pdf
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information.This modern and well-arranged What Role Does SDN Play In Customer Security SDN Building Blocks Topics Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the role of software defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low security public facing network for regular information.
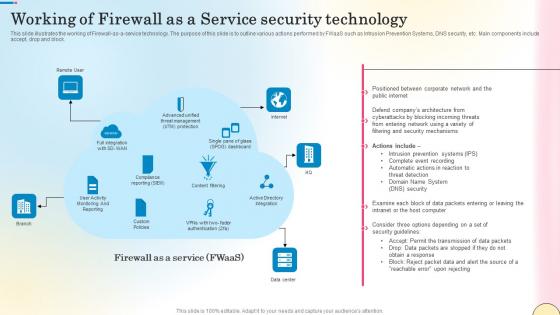
Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf
This slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block. Find highly impressive Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Working Of Firewall As A Service Security Technology Network Security Guidelines Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block.
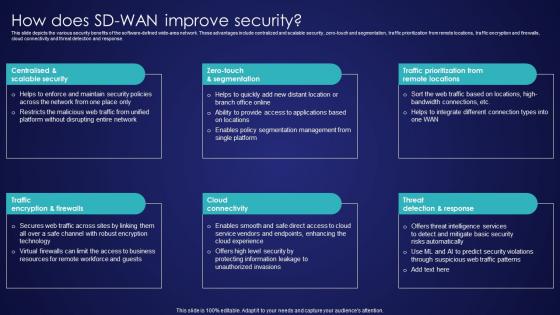
How Does SD Wan Improve Security Wide Area Network Services Structure Pdf
This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than How Does SD Wan Improve Security Wide Area Network Services Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab How Does SD Wan Improve Security Wide Area Network Services Structure Pdf today and make your presentation stand out from the rest. This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response.
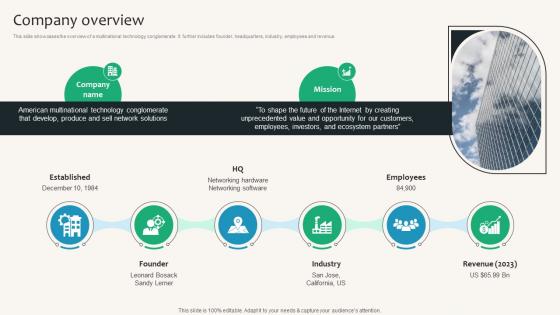
Company Overview Security Service Provider Business Model BMC SS V
This slide showcases the overview of a multinational technology conglomerate. It further includes founder, headquarters, industry, employees and revenue. Create an editable Company Overview Security Service Provider Business Model BMC SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Company Overview Security Service Provider Business Model BMC SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide showcases the overview of a multinational technology conglomerate. It further includes founder, headquarters, industry, employees and revenue.
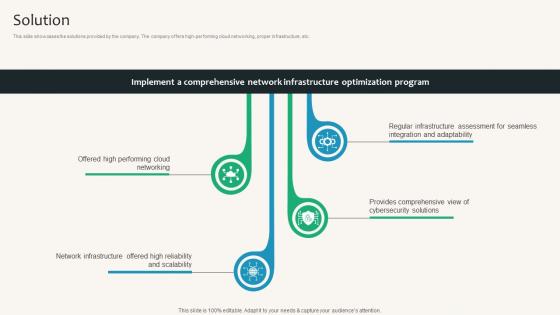
Solution Security Service Provider Business Model BMC SS V
This slide showcases the solutions provided by the company. The company offers high-performing cloud networking, proper infrastructure, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Security Service Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases the solutions provided by the company. The company offers high-performing cloud networking, proper infrastructure, etc.
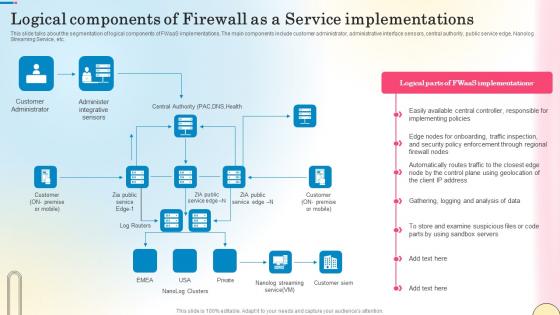
Logical Components Of Firewall As A Service Network Security Designs Pdf
This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Logical Components Of Firewall As A Service Network Security Designs Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Logical Components Of Firewall As A Service Network Security Designs Pdf. This slide talks about the segmentation of logical components of FWaaS implementations. The main components include customer administrator, administrative interface sensors, central authority, public service edge, Nanolog Streaming Service, etc.

IoT Solutions For Oil IoT Technology Adoption Benefits In Oil And Gas Industry IoT SS V
This slide highlights benefits of IoT technology in oil and gas industry that helps to predict equipment failure and improve safety measurers. It includes benefits such as improved operational efficiency, reduced maintenance costs, hazard management, and process automation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download IoT Solutions For Oil IoT Technology Adoption Benefits In Oil And Gas Industry IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the IoT Solutions For Oil IoT Technology Adoption Benefits In Oil And Gas Industry IoT SS V. This slide highlights benefits of IoT technology in oil and gas industry that helps to predict equipment failure and improve safety measurers. It includes benefits such as improved operational efficiency, reduced maintenance costs, hazard management, and process automation.
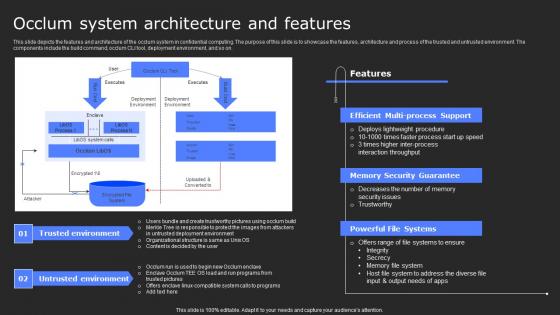
Occlum System Architecture And Features Secure Computing Framework Clipart Pdf
This slide depicts the features and architecture of the occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, occlum CLI tool, deployment environment, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Occlum System Architecture And Features Secure Computing Framework Clipart Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Occlum System Architecture And Features Secure Computing Framework Clipart Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide depicts the features and architecture of the occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, occlum CLI tool, deployment environment, and so on.
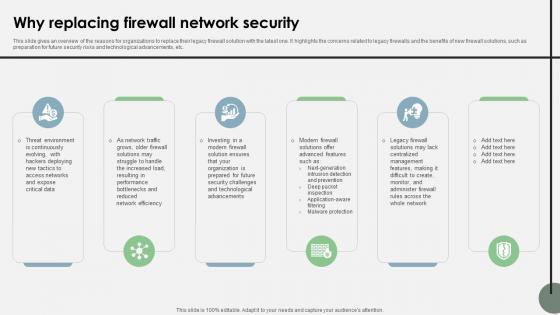
Why Replacing Firewall Network Security Cloud Security Firewall Proposal
This slide gives an overview of the reasons for organizations to replace their legacy firewall solution with the latest one. It highlights the concerns related to legacy firewalls and the benefits of new firewall solutions, such as preparation for future security risks and technological advancements, etc.Stand out from the crowd with our dynamic Why Replacing Firewall Network Security Cloud Security Firewall Proposal template. Designed to help you make a statement, this single-slide PPT template is fully customizable to suit your unique needs. With eye-catching visuals and seamless editing options, you can create impactful presentations in minutes. Say goodbye to boring slides and unlock your presentation potential with our top-notch template. This slide gives an overview of the reasons for organizations to replace their legacy firewall solution with the latest one. It highlights the concerns related to legacy firewalls and the benefits of new firewall solutions, such as preparation for future security risks and technological advancements, etc.
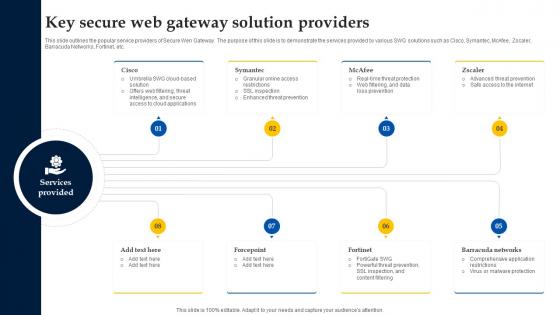
Web Access Control Solution Key Secure Web Gateway Solution Providers
This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Web Access Control Solution Key Secure Web Gateway Solution Providers to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Web Access Control Solution Key Secure Web Gateway Solution Providers. This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc.
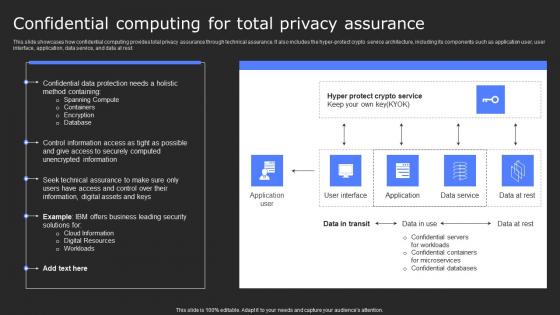
Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest.
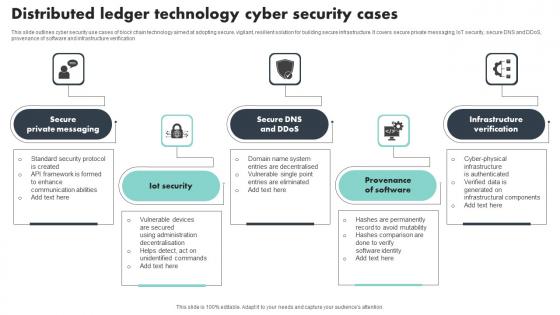
Distributed Ledger Technology Cyber Security Cases Brochure Pdf
This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification Showcasing this set of slides titled Distributed Ledger Technology Cyber Security Cases Brochure Pdf The topics addressed in these templates are Private Messaging, Provenance Of Software, Infrastructure Verification All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification
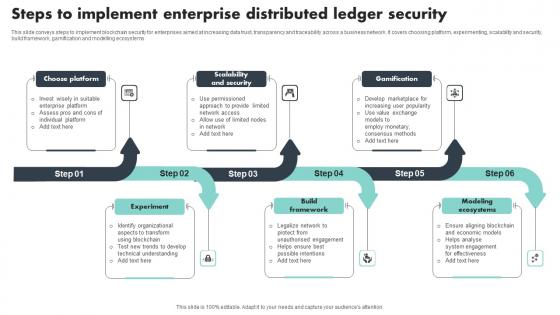
Steps To Implement Enterprise Distributed Ledger Security Download Pdf
This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems Pitch your topic with ease and precision using this Steps To Implement Enterprise Distributed Ledger Security Download Pdf This layout presents information on Choose Platform, Scalability And Security, Gamification It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems

IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V
Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc.
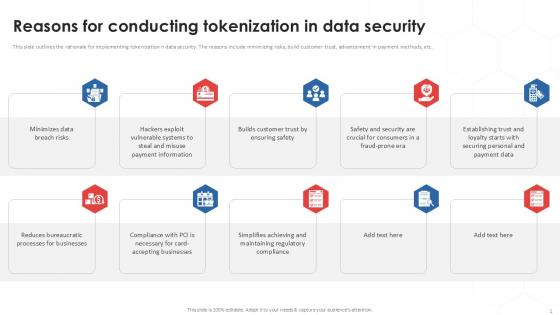
Reasons For Conducting Tokenization In Data Security PPT Template
This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc. Boost your pitch with our creative Reasons For Conducting Tokenization In Data Security PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the rationale for implementing tokenization n data security. The reasons include minimizing risks, build customer trust, advancement in payment methods, etc.

About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc.
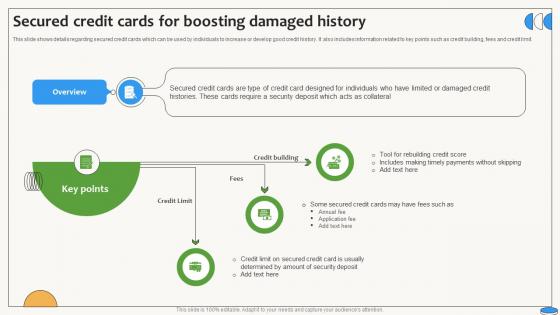
Secured Credit Cards For Boosting Damaged History Swipe Smartly A Practical Guide Fin SS V
This slide shows details regarding secured credit cards which can be used by individuals to increase or develop good credit history. It also includes information related to key points such as credit building, fees and credit limit. There are so many reasons you need a Secured Credit Cards For Boosting Damaged History Swipe Smartly A Practical Guide Fin SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide shows details regarding secured credit cards which can be used by individuals to increase or develop good credit history. It also includes information related to key points such as credit building, fees and credit limit.

Smart Home System Security Threats Utilizing Smart Appliances IoT SS V
This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft. Take your projects to the next level with our ultimate collection of Smart Home System Security Threats Utilizing Smart Appliances IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft.
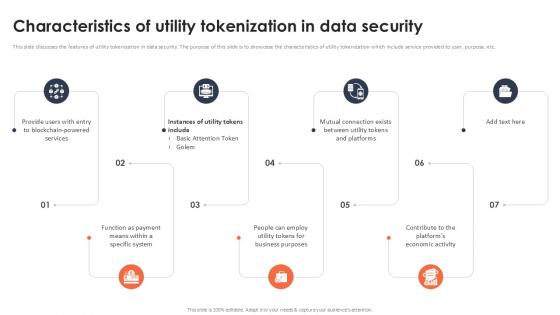
Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Characteristics Of Utility Tokenization In Data Security Securing Your Data Ppt Slide will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc.

Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. The Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc.

Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc. Take your projects to the next level with our ultimate collection of Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc.
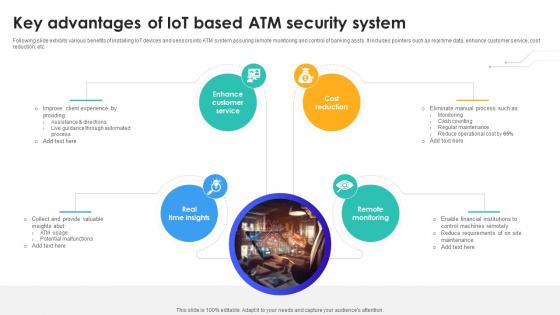
Key Advantages Of IoT Based Atm Security System IoT In Banking For Digital Future IoT SS V
Following slide exhibits various benefits of installing IoT devices and sensors into ATM system assuring remote monitoring and control of banking assts. It includes pointers such as real time data, enhance customer service, cost reduction, etc. This modern and well-arranged Key Advantages Of IoT Based Atm Security System IoT In Banking For Digital Future IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide exhibits various benefits of installing IoT devices and sensors into ATM system assuring remote monitoring and control of banking assts. It includes pointers such as real time data, enhance customer service, cost reduction, etc.
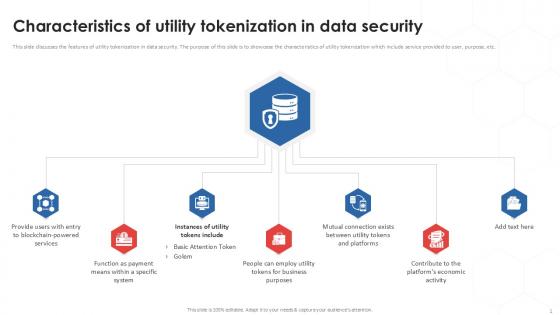
Characteristics Of Utility Tokenization In Data Security PPT Sample
This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc. Find a pre-designed and impeccable Characteristics Of Utility Tokenization In Data Security PPT Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the features of utility tokenization in data security. The purpose of this slide is to showcase the characteristics of utility tokenization which include service provided to user, purpose, etc.
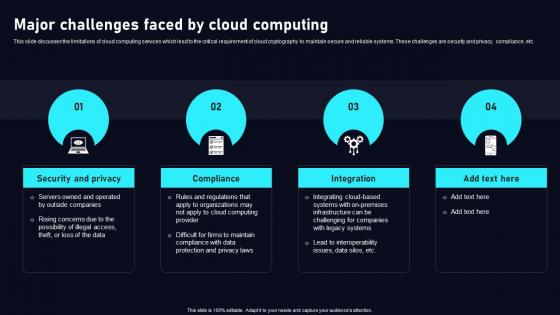
Major Challenges Faced By Cloud Data Security Using Cryptography Inspiration Pdf
This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc. QThere are so many reasons you need a Major Challenges Faced By Cloud Data Security Using Cryptography Inspiration Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc.
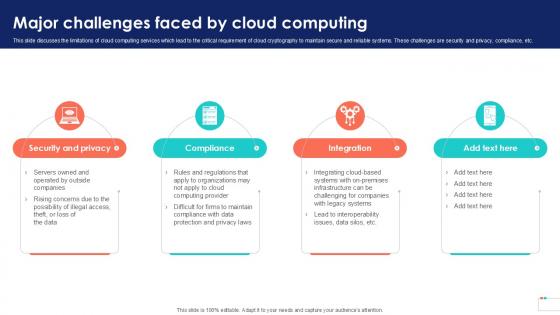
Major Challenges Faced By Data Security In Cloud Computing Ppt Sample
This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc. Do you know about Slidesgeeks Major Challenges Faced By Data Security In Cloud Computing Ppt Sample These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide discusses the limitations of cloud computing services which lead to the critical requirement of cloud cryptography to maintain secure and reliable systems. These challenges are security and privacy, compliance, etc.
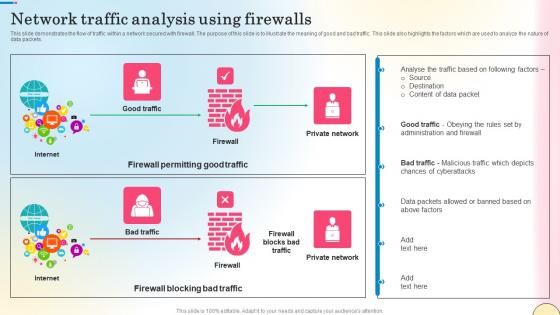
Network Traffic Analysis Using Firewalls Network Security Themes Pdf
This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc. Take your projects to the next level with our ultimate collection of Network Traffic Analysis Using Firewalls Network Security Themes Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide represents the architecture of Next generation Firewall as a Service technology. The purpose of this slide is to explain the working of next-generation FWaaS. The main components are branch, data center, internet, client, cloud, firewall, etc.
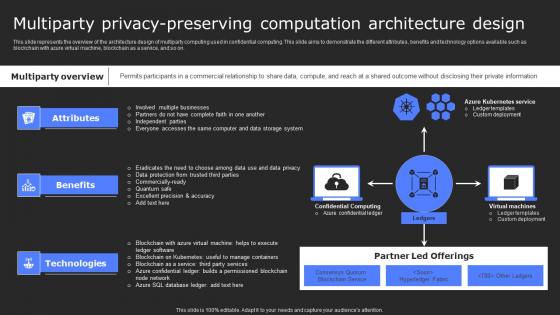
Multiparty Privacy Preserving Computation Secure Computing Framework Topics Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with azure virtual machine, blockchain as a service, and so on. Want to ace your presentation in front of a live audience Our Multiparty Privacy Preserving Computation Secure Computing Framework Topics Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with azure virtual machine, blockchain as a service, and so on.


 Continue with Email
Continue with Email

 Home
Home


































