Process Safety
Addressing Overarching Principles Digital Approaches To Increase Business Growth Topics Pdf
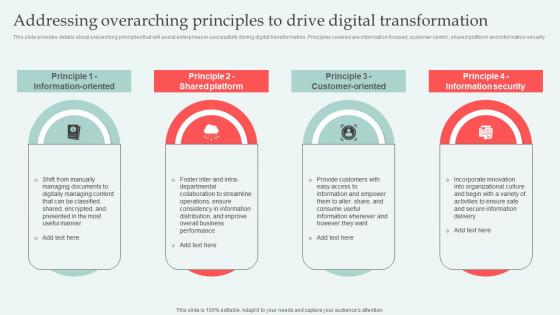
This slide provides details about overarching principles that will assist enterprises in successfully driving digital transformation. Principles covered are information focused, customer centric, shared platform and information security. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Addressing Overarching Principles Digital Approaches To Increase Business Growth Topics Pdf from Slidegeeks and deliver a wonderful presentation. This slide provides details about overarching principles that will assist enterprises in successfully driving digital transformation. Principles covered are information focused, customer centric, shared platform and information security.
Steps For Controlling Smart Home Through Phones Utilizing Smart Appliances IoT SS V
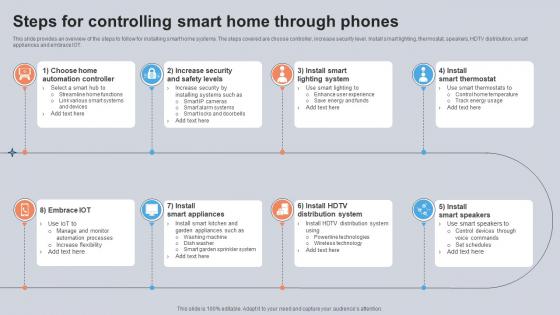
This slide provides an overview of the steps to follow for installing smart home systems. The steps covered are choose controller, increase security level. Install smart lighting, thermostat, speakers, HDTV distribution, smart appliances and embrace IOT. Boost your pitch with our creative Steps For Controlling Smart Home Through Phones Utilizing Smart Appliances IoT SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide provides an overview of the steps to follow for installing smart home systems. The steps covered are choose controller, increase security level. Install smart lighting, thermostat, speakers, HDTV distribution, smart appliances and embrace IOT.
Key Benefits Of Using Implementing Scale AI PPT Presentation AI SS V
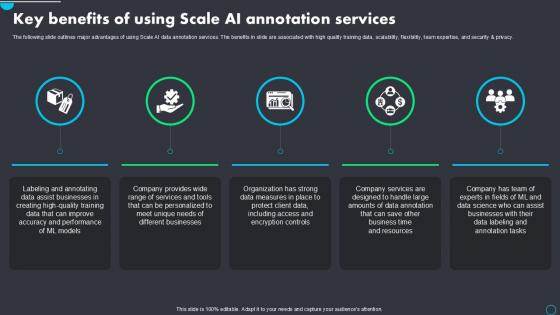
The following slide outlines major advantages of using Scale AI data annotation services. The benefits in slide are associated with high quality training data, scalability, flexibility, team expertise, and security and privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Key Benefits Of Using Implementing Scale AI PPT Presentation AI SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Benefits Of Using Implementing Scale AI PPT Presentation AI SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The following slide outlines major advantages of using Scale AI data annotation services. The benefits in slide are associated with high quality training data, scalability, flexibility, team expertise, and security and privacy.
Our Solution Value Based Investor Financing Pitch Deck Demonstration Pdf
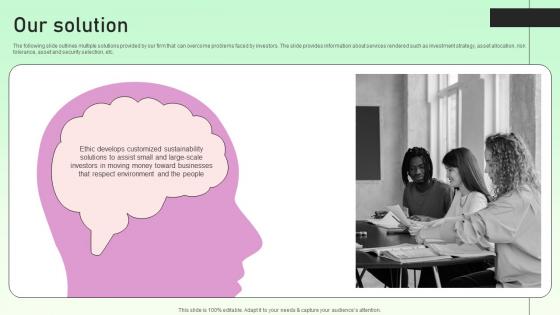
The following slide outlines multiple solutions provided by our firm that can overcome problems faced by investors. The slide provides information about services rendered such as investment strategy, asset allocation, risk tolerance, asset and security selection, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Our Solution Value Based Investor Financing Pitch Deck Demonstration Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The following slide outlines multiple solutions provided by our firm that can overcome problems faced by investors. The slide provides information about services rendered such as investment strategy, asset allocation, risk tolerance, asset and security selection, etc.
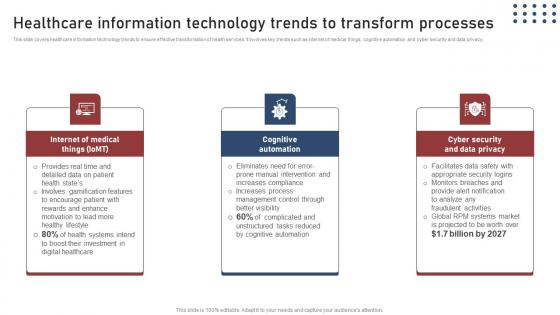
Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf
This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy. If you are looking for a format to display your unique thoughts, then the professionally designed Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Healthcare Information Transforming Medical Workflows Via His Integration Designs Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide covers healthcare information technology trends to ensure effective transformation of health services. It involves key trends such as internet of medical things, cognitive automation and cyber security and data privacy.
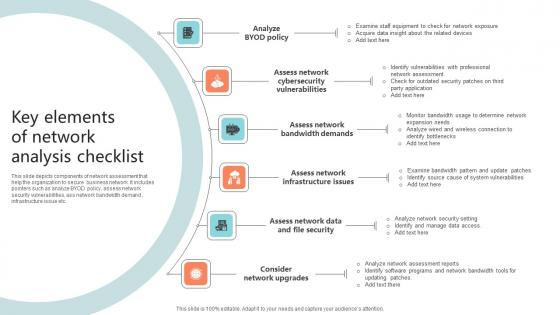
Key Elements Of Network Analysis Checklist Microsoft Pdf
This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.Pitch your topic with ease and precision using this Key Elements Of Network Analysis Checklist Microsoft Pdf This layout presents information on Cybersecurity Vulnerabilities, Bandwidth Demands, Assess Network It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide depicts components of network assessment that help the organization to secure business network. It includes pointers such as analyze BYOD policy, assess network security vulnerabilities, ass network bandwidth demand , infrastructure issue etc.
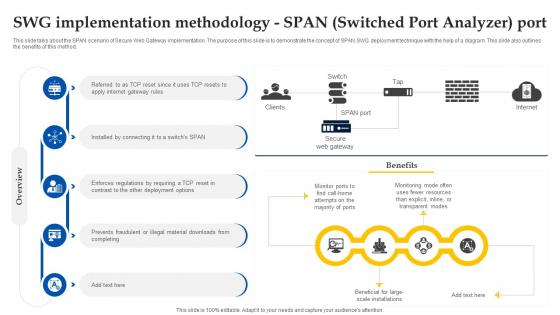
Web Access Control Solution Swg Implementation Methodology Span Switched Port Analyzer Port
This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Find highly impressive Web Access Control Solution Swg Implementation Methodology Span Switched Port Analyzer Port on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Web Access Control Solution Swg Implementation Methodology Span Switched Port Analyzer Port for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method.
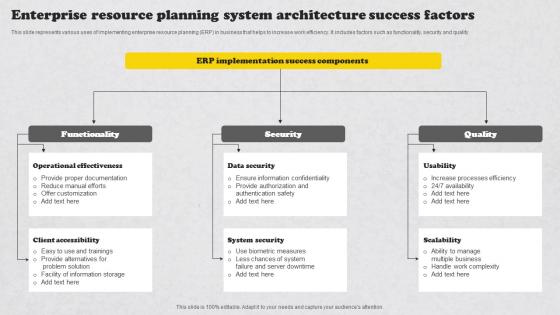
Enterprise Resource Planning System Architecture Success Factors Background Pdf
This slide represents various uses of implementing enterprise resource planning ERP in business that helps to increase work efficiency. It includes factors such as functionality, security and quality Showcasing this set of slides titled Enterprise Resource Planning System Architecture Success Factors Background Pdf. The topics addressed in these templates are Quality, Security, Functionality. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide represents various uses of implementing enterprise resource planning ERP in business that helps to increase work efficiency. It includes factors such as functionality, security and quality
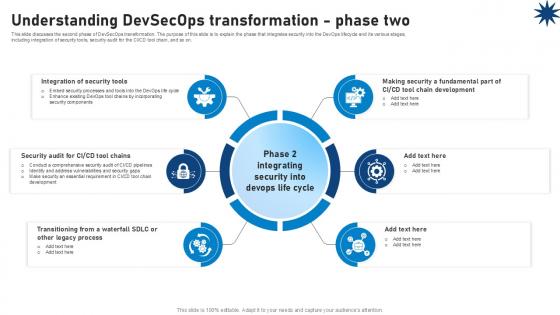
Understanding Devsecops Transformation Phase Two Role Of Devsecops Ppt Powerpoint
This slide discusses the second phase of DevSecOps transformation. The purpose of this slide is to explain the phase that integrates security into the DevOps lifecycle and its various stages, including integration of security tools, security audit for the CICD tool chain, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Understanding Devsecops Transformation Phase Two Role Of Devsecops Ppt Powerpoint and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide discusses the second phase of DevSecOps transformation. The purpose of this slide is to explain the phase that integrates security into the DevOps lifecycle and its various stages, including integration of security tools, security audit for the CICD tool chain, and so on.

IAC Governance Policy Principle IAC Tools For Performance Analysis PPT Sample
This slide discusses the governance policies principle framework of infrastructure as code. The purpose of this slide is to outline the principles such as security and compliance management, financial management, operational management, etc. Are you searching for a IAC Governance Policy Principle IAC Tools For Performance Analysis PPT Sample that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IAC Governance Policy Principle IAC Tools For Performance Analysis PPT Sample from Slidegeeks today. This slide discusses the governance policies principle framework of infrastructure as code. The purpose of this slide is to outline the principles such as security and compliance management, financial management, operational management, etc.

Main Advantages Of Software Harnessing The World Of Ethical Ppt Slide
This slide showcases the advantages of software security testing such as identifying weaknesses, enhancing security, ensuring compliance, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Main Advantages Of Software Harnessing The World Of Ethical Ppt Slide These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide showcases the advantages of software security testing such as identifying weaknesses, enhancing security, ensuring compliance, etc.
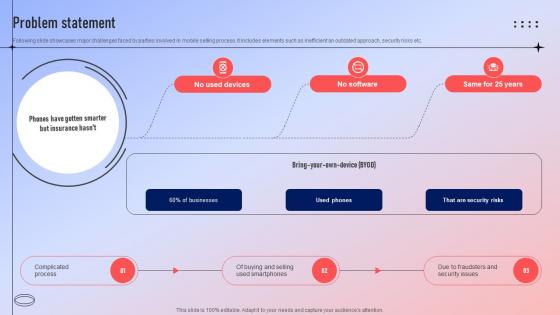
Problem Statement Fundraising Pitch Deck For Ecommerce Platform
Following slide showcases major challenges faced by parties involved in mobile selling process. It includes elements such as inefficient an outdated approach, security risks etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Problem Statement Fundraising Pitch Deck For Ecommerce Platform. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. Following slide showcases major challenges faced by parties involved in mobile selling process. It includes elements such as inefficient an outdated approach, security risks etc.
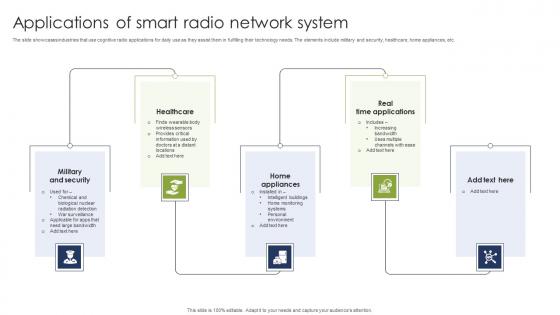
Applications Of Smart Radio Network System Summary Pdf
The slide showcases industries that use cognitive radio applications for daily use as they assist them in fulfilling their technology needs. The elements include military and security, healthcare, home appliances, etc. Showcasing this set of slides titled Applications Of Smart Radio Network System Summary Pdf. The topics addressed in these templates are Military Security, Healthcare, Home Appliances. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases industries that use cognitive radio applications for daily use as they assist them in fulfilling their technology needs. The elements include military and security, healthcare, home appliances, etc.

Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf
The purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers The purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties.

Types Of Employee Incentives Offered By Company Elements Pdf
This slide showcase employee benefits provided by industry to motivate workers and provide job satisfaction to achieve work life goals. It include perks such as work, healthcare, financial security and lifestyle benefits. Showcasing this set of slides titled Types Of Employee Incentives Offered By Company Elements Pdf The topics addressed in these templates are Work Benefits, Healthcare Benefits, Lifestyle Benefits All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide showcase employee benefits provided by industry to motivate workers and provide job satisfaction to achieve work life goals. It include perks such as work, healthcare, financial security and lifestyle benefits.
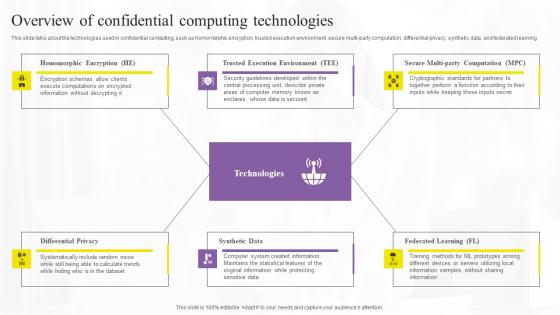
Overview Of Confidential Computing Technologies Elements Pdf
This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. The Overview Of Confidential Computing Technologies Elements Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning.
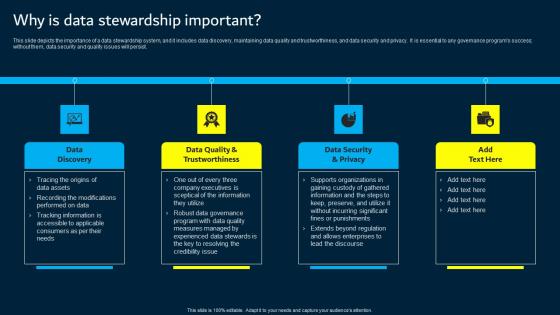
Why Is Data Stewardship Important Data Custodianship Formats Pdf
This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance program s success without them, data security and quality issues will persist. Boost your pitch with our creative Why Is Data Stewardship Important Data Custodianship Formats Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide depicts the importance of a data stewardship system, and it includes data discovery, maintaining data quality and trustworthiness, and data security and privacy. It is essential to any governance program s success without them, data security and quality issues will persist.
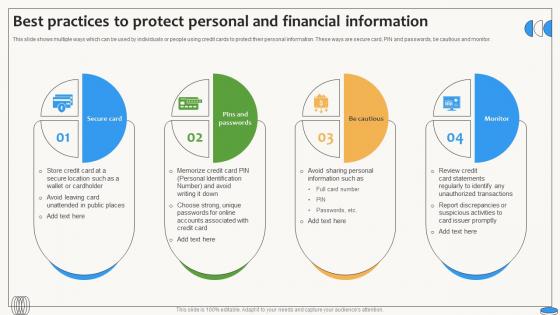
Best Practices To Protect Personal And Financial Swipe Smartly A Practical Guide Fin SS V
This slide shows multiple ways which can be used by individuals or people using credit cards to protect their personal information. These ways are secure card, PIN and passwords, be cautious and monitor. Want to ace your presentation in front of a live audience Our Best Practices To Protect Personal And Financial Swipe Smartly A Practical Guide Fin SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide shows multiple ways which can be used by individuals or people using credit cards to protect their personal information. These ways are secure card, PIN and passwords, be cautious and monitor.
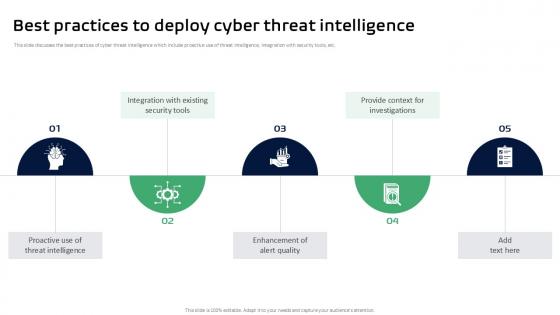
Best Practices To Deploy Cyber Threat Intelligence Ppt Slides
This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices To Deploy Cyber Threat Intelligence Ppt Slides for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide discusses the best practices of cyber threat intelligence which include proactive use of threat intelligence, integration with security tools, etc.
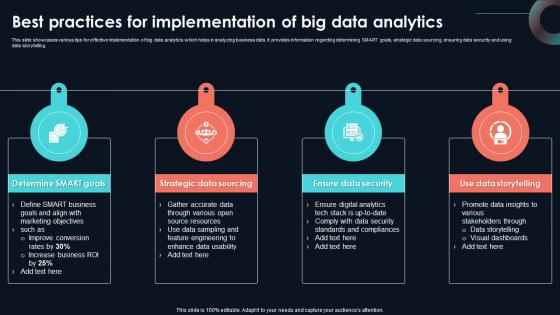
Best Practices For Implementation Of Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases various tips for effective implementation of big data analytics which helps in analyzing business data. It provides information regarding determining SMART goals, strategic data sourcing, ensuring data security and using data storytelling. Present like a pro with Best Practices For Implementation Of Developing Strategic Insights Using Big Data Analytics SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide showcases various tips for effective implementation of big data analytics which helps in analyzing business data. It provides information regarding determining SMART goals, strategic data sourcing, ensuring data security and using data storytelling.
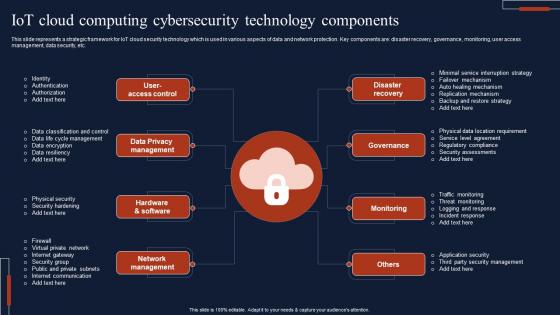
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc.
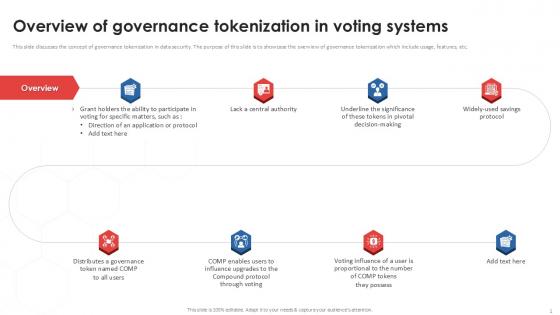
Overview Of Governance Tokenization In Voting Systems PPT Sample
This slide discusses the concept of governance tokenization in data security. The purpose of this slide is to showcase the overview of governance tokenization which include usage, features, etc. Boost your pitch with our creative Overview Of Governance Tokenization In Voting Systems PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide discusses the concept of governance tokenization in data security. The purpose of this slide is to showcase the overview of governance tokenization which include usage, features, etc.
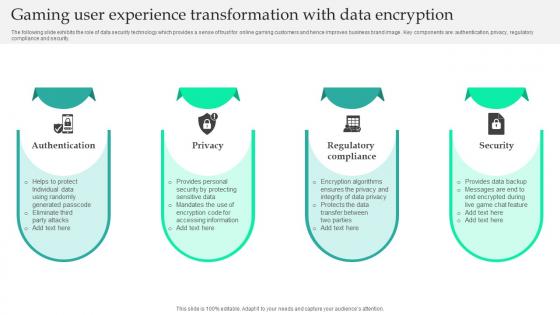
Gaming User Experience Transformation With Data Encryption Portrait Pdf
The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security. Pitch your topic with ease and precision using this Gaming User Experience Transformation With Data Encryption Portrait Pdf. This layout presents information on Authentication, Privacy, Regulatory Compliance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide exhibits the role of data security technology which provides a sense of trust for online gaming customers and hence improves business brand image . Key components are authentication, privacy, regulatory compliance and security.
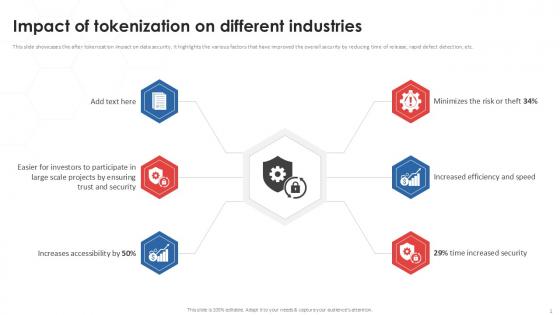
Impact Of Tokenization On Different Industries PPT Template
This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc. Find a pre-designed and impeccable Impact Of Tokenization On Different Industries PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide showcases the after tokenization impact on data security. It highlights the various factors that have improved the overall security by reducing time of release, rapid defect detection, etc.

Zero Trust Model Case Study Intellectual Property Protection
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Zero Trust Model Case Study Intellectual Property Protection will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business.
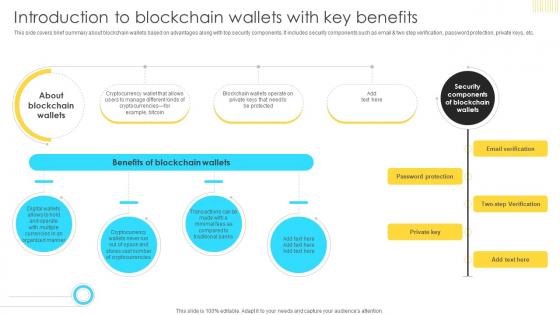
Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V
This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc Do you know about Slidesgeeks Mastering Blockchain Wallets Introduction To Blockchain Wallets With Key BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This side covers brief summary about blockchain wallets based on advantages along with top security components. It includes security components such as email and two step verification, password protection, private keys, etc

Content Protection Mechanisms In Mobile Application Areas Of Mobile Cloud Computing
The purpose of the mentioned slide is to showcase the content protection techniques to secure mobile cloud media streaming. It includes encryption, secure authentication and authorization, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Content Protection Mechanisms In Mobile Application Areas Of Mobile Cloud Computing will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. The purpose of the mentioned slide is to showcase the content protection techniques to secure mobile cloud media streaming. It includes encryption, secure authentication and authorization, etc.

Advantages Of Mobile Cloud Computing In Application Areas Of Mobile Cloud Computing
The given slide outlines the potential benefits of using mobile cloud computing in healthcare to streamline concurrent processes. It includes collaboration, security, cost-effectiveness, speed, and scalability. Boost your pitch with our creative Advantages Of Mobile Cloud Computing In Application Areas Of Mobile Cloud Computing. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. The given slide outlines the potential benefits of using mobile cloud computing in healthcare to streamline concurrent processes. It includes collaboration, security, cost-effectiveness, speed, and scalability

Benefits Of Using Smart Attendance Systems Impact Of IoT Technology On Education IoT SS V
Following slide represents key advantage of using automation based attendance systems in education sector. It includes pointers such as fewer errors, cost effective, security, scalability, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Benefits Of Using Smart Attendance Systems Impact Of IoT Technology On Education IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Benefits Of Using Smart Attendance Systems Impact Of IoT Technology On Education IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today Following slide represents key advantage of using automation based attendance systems in education sector. It includes pointers such as fewer errors, cost effective, security, scalability, etc.
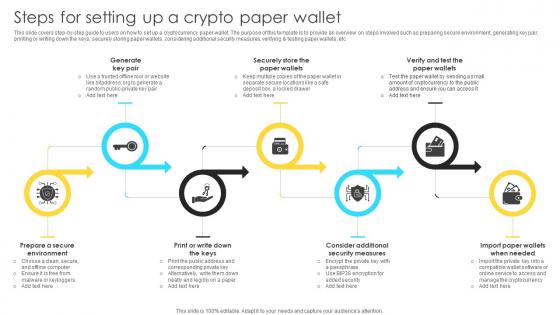
Mastering Blockchain Wallets Steps For Setting Up A Crypto Paper Wallet BCT SS V
This slide covers step-by-step guide to users on how to set up a cryptocurrency paper wallet. The purpose of this template is to provide an overview on steps involved such as preparing secure environment, generating key pair, printing or writing down the keys, securely storing paper wallets, considering additional security measures, verifying and testing paper wallets, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Mastering Blockchain Wallets Steps For Setting Up A Crypto Paper Wallet BCT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Mastering Blockchain Wallets Steps For Setting Up A Crypto Paper Wallet BCT SS V. This slide covers step-by-step guide to users on how to set up a cryptocurrency paper wallet. The purpose of this template is to provide an overview on steps involved such as preparing secure environment, generating key pair, printing or writing down the keys, securely storing paper wallets, considering additional security measures, verifying and testing paper wallets, etc.

Problem Statement Customer Engagement Platform Business Model BMC SS V
This slide showcases the major problems addressed by company such as poor security and confidentiality, limited team collaboration, ineffective sales process, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Problem Statement Customer Engagement Platform Business Model BMC SS V can be your best option for delivering a presentation. Represent everything in detail using Problem Statement Customer Engagement Platform Business Model BMC SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide showcases the major problems addressed by company such as poor security and confidentiality, limited team collaboration, ineffective sales process, etc.
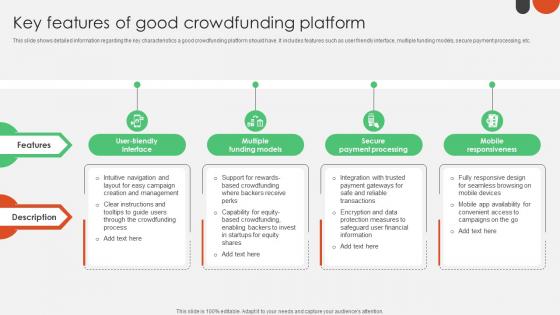
Key Features Of Good Crowdfunding Platform Crowdfunding For Nonprofits To Support Fin SS V
This slide shows detailed information regarding the key characteristics a good crowdfunding platform should have. It includes features such as user friendly interface, multiple funding models, secure payment processing, etc. Are you searching for a Key Features Of Good Crowdfunding Platform Crowdfunding For Nonprofits To Support Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Features Of Good Crowdfunding Platform Crowdfunding For Nonprofits To Support Fin SS V from Slidegeeks today. This slide shows detailed information regarding the key characteristics a good crowdfunding platform should have. It includes features such as user friendly interface, multiple funding models, secure payment processing, etc.

Operational Challeneges Of Outsourced Call Center Sample Pdf
The following slide highlights lack of knowledge, lack of control, hidden costs, security concern and language barrier to show challenges of offshore call center outsourcing to show challenges of offshore call center. It helps organizations to identify and mitigate potential challenges. Showcasing this set of slides titled Operational Challeneges Of Outsourced Call Center Sample Pdf. The topics addressed in these templates are Lack Of Company Knowledge, Lack Of Control, Security Concerns, Language Barrier. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The following slide highlights lack of knowledge, lack of control, hidden costs, security concern and language barrier to show challenges of offshore call center outsourcing to show challenges of offshore call center. It helps organizations to identify and mitigate potential challenges.
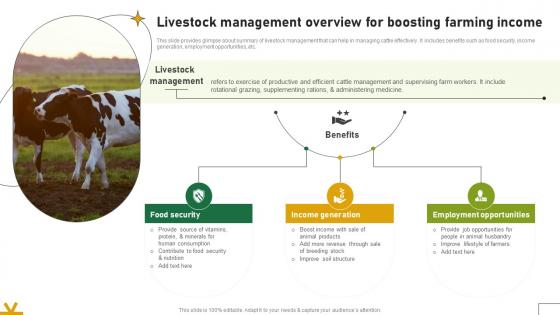
Livestock Management Overview For Boosting Farming Income Adopting Sustainable Farming Techniques
This slide provides glimpse about summary of livestock management that can help in managing cattle effectively. It includes benefits such as food security, income generation, employment opportunities, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Livestock Management Overview For Boosting Farming Income Adopting Sustainable Farming Techniques. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Livestock Management Overview For Boosting Farming Income Adopting Sustainable Farming Techniques today and make your presentation stand out from the rest This slide provides glimpse about summary of livestock management that can help in managing cattle effectively. It includes benefits such as food security, income generation, employment opportunities, etc.

Major Focus Of White Box Testing Gray Box Testing Best Practices
This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Major Focus Of White Box Testing Gray Box Testing Best Practices and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the area of focus for white box testing in software development. The purpose of this slide is to highlight the primary emphasis of white box testing which include path checking, output validation, security testing, and so on.
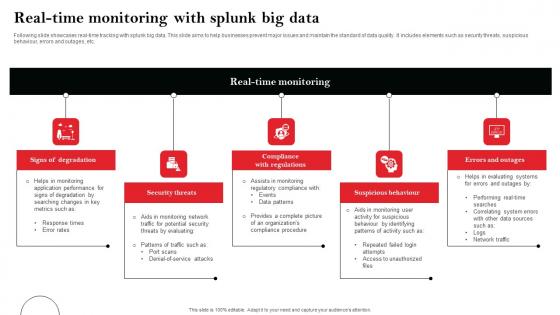
Real Time Monitoring With Splunk Big Data Diagrams Pdf
Following slide showcases real-time tracking with splunk big data. This slide aims to help businesses prevent major issues and maintain the standard of data quality. It includes elements such as security threats, suspicious behaviour, errors and outages, etc. Pitch your topic with ease and precision using this Real Time Monitoring With Splunk Big Data Diagrams Pdf This layout presents information on Signs Of Degradation, Security Threats, Errors And Outages It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. Following slide showcases real-time tracking with splunk big data. This slide aims to help businesses prevent major issues and maintain the standard of data quality. It includes elements such as security threats, suspicious behaviour, errors and outages, etc.
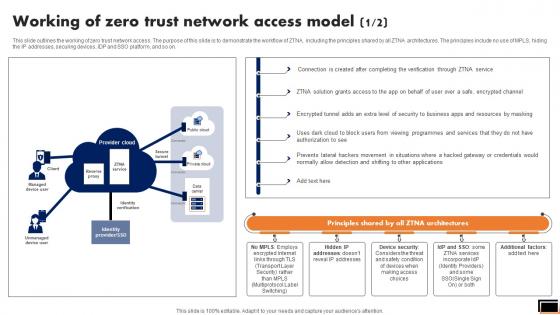
Working Of Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Zero Trust Network Access Model Software Defined Perimeter SDP to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on.

Best Practices For Implementing Marketing Resource Effective Strategies To Enhance Summary Pdf
This slide covers best practices for integrating marketing resources management and its optimum utilization. It involves key strategies such as create implementation team, secure IT support and regular review. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Best Practices For Implementing Marketing Resource Effective Strategies To Enhance Summary Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Best Practices For Implementing Marketing Resource Effective Strategies To Enhance Summary Pdf This slide covers best practices for integrating marketing resources management and its optimum utilization. It involves key strategies such as create implementation team, secure IT support and regular review.

Benefits Of AML In Cryptocurrency Transactions Mapping Out The Anti Money Fin SS V
This slide represents the advantages of anti-money laundering in cryptocurrency along with benefit description. The various benefits are improved security, legal compliance, prevention of illicit activities. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Benefits Of AML In Cryptocurrency Transactions Mapping Out The Anti Money Fin SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Benefits Of AML In Cryptocurrency Transactions Mapping Out The Anti Money Fin SS V today and make your presentation stand out from the rest This slide represents the advantages of anti-money laundering in cryptocurrency along with benefit description. The various benefits are improved security, legal compliance, prevention of illicit activities.
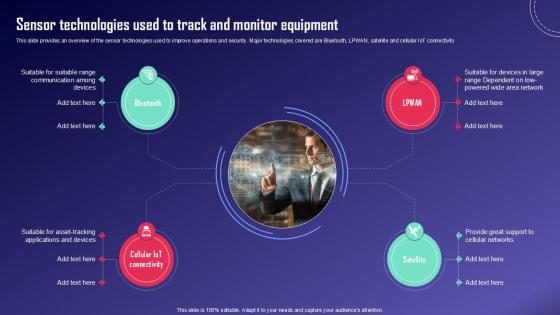
Sensor Technologies Used To IoT Fleet Monitoring Ppt Slide IoT SS V
This slide provides an overview of the sensor technologies used to improve operations and security. Major technologies covered are Bluetooth, LPWAN, satellite and cellular IoT connectivity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Sensor Technologies Used To IoT Fleet Monitoring Ppt Slide IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Sensor Technologies Used To IoT Fleet Monitoring Ppt Slide IoT SS V today and make your presentation stand out from the rest This slide provides an overview of the sensor technologies used to improve operations and security. Major technologies covered are Bluetooth, LPWAN, satellite and cellular IoT connectivity
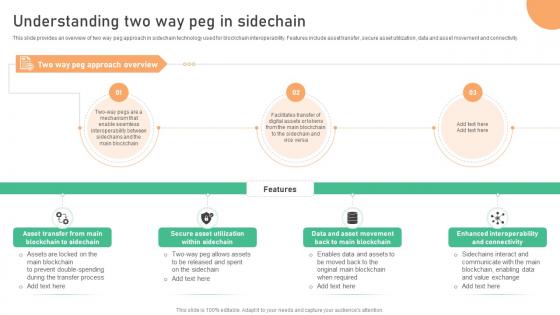
Seamless Integration The Power Understanding Two Way Peg In Sidechain BCT SS V
This slide provides an overview of two way peg approach in sidechain technology used for blockchain interoperability. Features include asset transfer, secure asset utilization, data and asset movement and connectivity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Seamless Integration The Power Understanding Two Way Peg In Sidechain BCT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Seamless Integration The Power Understanding Two Way Peg In Sidechain BCT SS V today and make your presentation stand out from the rest This slide provides an overview of two way peg approach in sidechain technology used for blockchain interoperability. Features include asset transfer, secure asset utilization, data and asset movement and connectivity.

Our Solution Open Source Solution Investor Funding Elevator Pitch Deck
The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform. Make sure to capture your audiences attention in your business displays with our gratis customizable Our Solution Open Source Solution Investor Funding Elevator Pitch Deck. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. The following slide showcases solution offered by company for its customers by incorporating privacy and data security system in its open source virtual assistant platform.

Zero Trust Network Access System Use Cases Software Defined Perimeter SDP
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Network Access System Use Cases Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access System Use Cases Software Defined Perimeter SDP from Slidegeeks today. This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on.
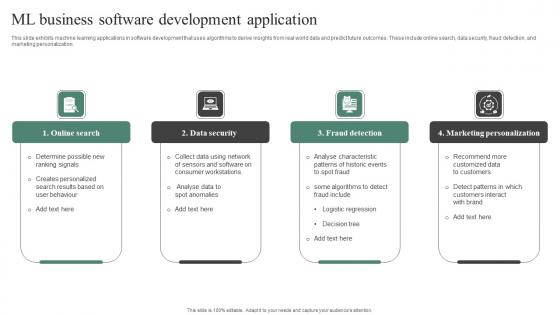
ML Business Software Development Application Guidelines Pdf
This slide exhibits machine learning applications in software development that uses algorithms to derive insights from real world data and predict future outcomes. These include online search, data security, fraud detection, and marketing personalization. Showcasing this set of slides titled ML Business Software Development Application Guidelines Pdf. The topics addressed in these templates are Online Search, Data Security, Fraud Detection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide exhibits machine learning applications in software development that uses algorithms to derive insights from real world data and predict future outcomes. These include online search, data security, fraud detection, and marketing personalization.

Key Benefits Of Non FHA Home Loan Themes Pdf
The following slide enlists major benefits of conventional loans with transparency, flexibility in regulations and variety specifics to appeal customers. It covers faster underwriting, optional escrow accounts, security and flexibility. Pitch your topic with ease and precision using this Key Benefits Of Non FHA Home Loan Themes Pdf. This layout presents information on Escrow Accounts, Security, Flexibility. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. The following slide enlists major benefits of conventional loans with transparency, flexibility in regulations and variety specifics to appeal customers. It covers faster underwriting, optional escrow accounts, security and flexibility.
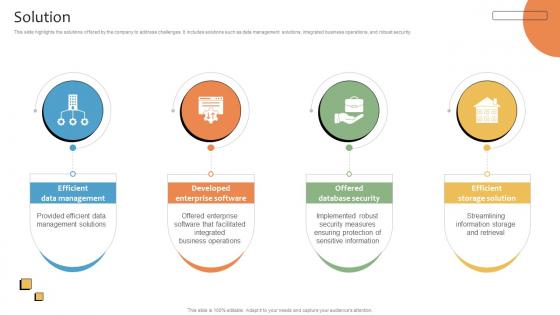
Solution CRMS Platform Business Model BMC SS V
This slide highlights the solutions offered by the company to address challenges. It includes solutions such as data management solutions, integrated business operations, and robust security. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution CRMS Platform Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide highlights the solutions offered by the company to address challenges. It includes solutions such as data management solutions, integrated business operations, and robust security.

Introduction To Smart Home Alarm System Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart alarm system installed in homes to increase security. It further includes challenges faced and advantages that are easy installation, cost-effective, send real-time alerts, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Introduction To Smart Home Alarm System Utilizing Smart Appliances IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Introduction To Smart Home Alarm System Utilizing Smart Appliances IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today This slide provides an overview of the smart alarm system installed in homes to increase security. It further includes challenges faced and advantages that are easy installation, cost-effective, send real-time alerts, etc.
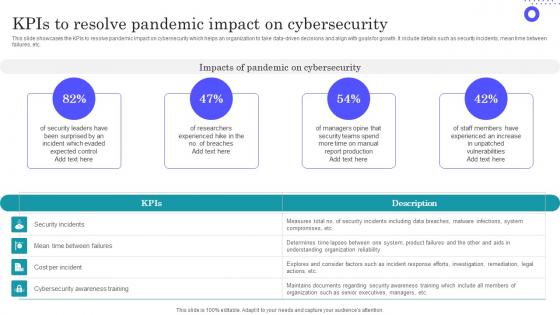
KPIs To Resolve Pandemic Impact On Cybersecurity Microsoft Pdf
Pitch your topic with ease and precision using this KPIs To Resolve Pandemic Impact On Cybersecurity Microsoft Pdf This layout presents information on Understanding Organization, Security Incidents, Malware Infections It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide showcases the KPIs to resolve pandemic impact on cybersecurity which helps an organization to take data driven decisions and align with goals for growth. It include details such as security incidents, mean time between failures, etc.
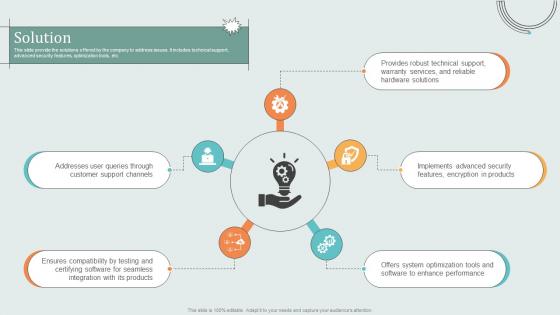
Solution Hardware Technology Provider Business Model BMC SS V
This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Hardware Technology Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc.
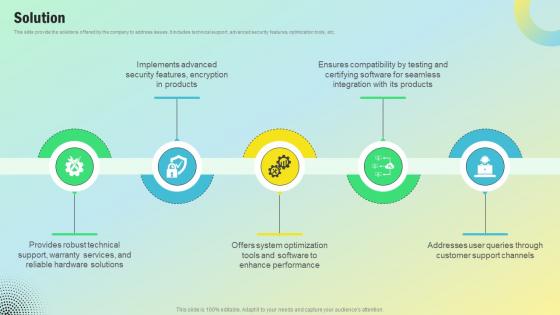
Solution Personal Computing Company Revenue Model BMC SS V
This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Personal Computing Company Revenue Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide provide the solutions offered by the company to address issues. It includes technical support, advanced security features, optimization tools, etc.

Digital Project Management Strategies Significance Of Digital Tools In Project Management
The purpose of the mentioned slide is to illustrate the importance of incorporating digital solutions in project management. It includes advantages such as efficiency and automation, centralized information, task monitoring, and security and access control. Find a pre-designed and impeccable Digital Project Management Strategies Significance Of Digital Tools In Project Management. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. The purpose of the mentioned slide is to illustrate the importance of incorporating digital solutions in project management. It includes advantages such as efficiency and automation, centralized information, task monitoring, and security and access control.
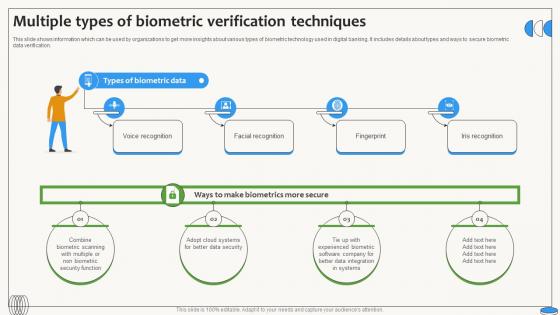
Multiple Types Of Biometric Verification Techniques Swipe Smartly A Practical Guide Fin SS V
This slide shows information which can be used by organizations to get more insights about various types of biometric technology used in digital banking. It includes details about types and ways to secure biometric data verification. Create an editable Multiple Types Of Biometric Verification Techniques Swipe Smartly A Practical Guide Fin SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Multiple Types Of Biometric Verification Techniques Swipe Smartly A Practical Guide Fin SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide shows information which can be used by organizations to get more insights about various types of biometric technology used in digital banking. It includes details about types and ways to secure biometric data verification.
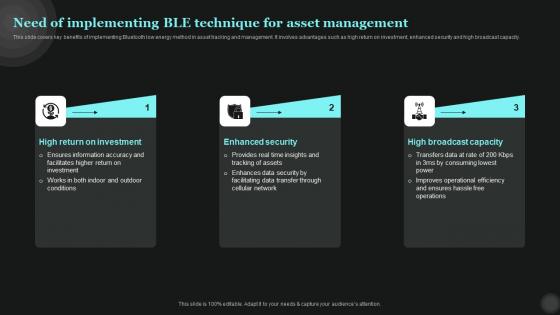
Need Of Implementing BLE Technique For Asset Tech Asset Management Elements Pdf
This slide covers key benefits of implementing Bluetooth low energy method in asset tracking and management. It involves advantages such as high return on investment, enhanced security and high broadcast capacity.Make sure to capture your audiences attention in your business displays with our gratis customizable Need Of Implementing BLE Technique For Asset Tech Asset Management Elements Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide covers key benefits of implementing Bluetooth low energy method in asset tracking and management. It involves advantages such as high return on investment, enhanced security and high broadcast capacity.
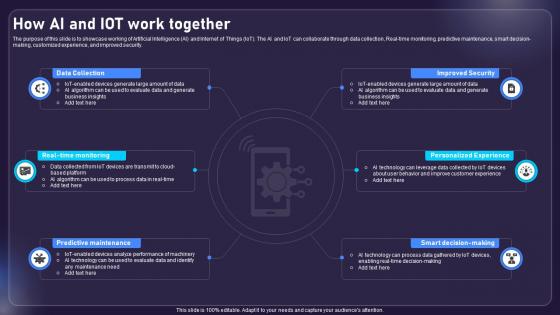
How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security. This How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Ai And Iot Work Together AIOT Applications For Various Industries IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security.
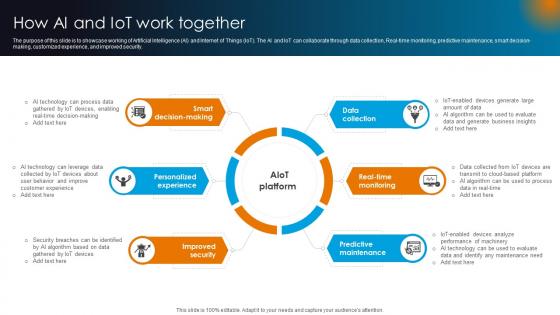
Integrating AI With IoT How Ai And IoT Work Together IoT SS V
The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security. This modern and well-arranged Integrating AI With IoT How Ai And IoT Work Together IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. The purpose of this slide is to showcase working of Artificial Intelligence AI and Internet of Things IoT. The AI and IoT can collaborate through data collection, Real-time monitoring, predictive maintenance, smart decision-making, customized experience, and improved security.

Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck
This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Problem Statement ICT Solutions Provider Investor Funding Elevator Pitch Deck This slide caters to details about several problems in the market faced by prospects. These pain points are 5G technology issues, security issues, smart devices are expensive and cloud computing security breaches.
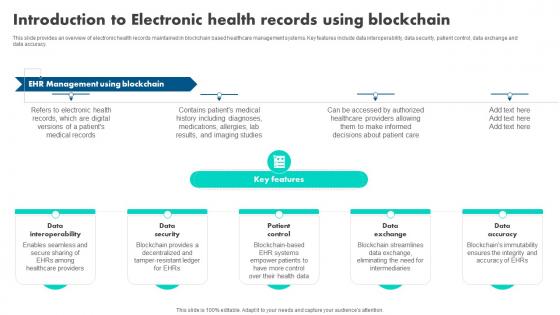
How Blockchain Is Reshaping Introduction To Electronic Health Records BCT SS V
This slide provides an overview of electronic health records maintained in blockchain based healthcare management systems. Key features include data interoperability, data security, patient control, data exchange and data accuracy. Find a pre-designed and impeccable How Blockchain Is Reshaping Introduction To Electronic Health Records BCT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide provides an overview of electronic health records maintained in blockchain based healthcare management systems. Key features include data interoperability, data security, patient control, data exchange and data accuracy.

Zero Trust Network Access User Flow Overview Ppt File Deck
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. The Zero Trust Network Access User Flow Overview Ppt File Deck is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office.

IoT Supply Chain Management Best IoT Fleet Monitoring Ppt PowerPoint IoT SS V
This slide provides an overview of the best practices to be followed in the IoT supply chain. Major practices covered are maintaining data security, ensuring scalability and leveraging the cloud platform. Take your projects to the next level with our ultimate collection of IoT Supply Chain Management Best IoT Fleet Monitoring Ppt PowerPoint IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide provides an overview of the best practices to be followed in the IoT supply chain. Major practices covered are maintaining data security, ensuring scalability and leveraging the cloud platform

Impact Of Blockchain Technology On Commercial Complete Guide On Managing Banking Fin SS V
This slide shows details which can be used by individuals or banks to understand the advantages of using blockchain technology in banking. It includes benefits such as more efficient KYC process, trade finance and better data security. Retrieve professionally designed Impact Of Blockchain Technology On Commercial Complete Guide On Managing Banking Fin SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide shows details which can be used by individuals or banks to understand the advantages of using blockchain technology in banking. It includes benefits such as more efficient KYC process, trade finance and better data security.


 Continue with Email
Continue with Email

 Home
Home


































