Process Safety
Icon Showing Data Security Through Blockchain Technology In Supply Chain Rules PDF
Persuade your audience using this Icon Showing Data Security Through Blockchain Technology In Supply Chain Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Icon Showing Data Security, Blockchain Technology Supply Chain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
The following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
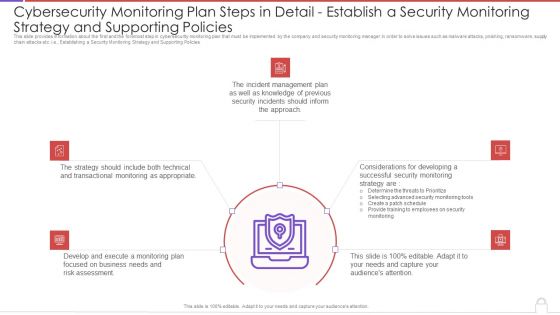
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Online Settlement Revolution Payment Security And Fraud Management Solutions Analysis Ppt Slides File Formats PDF
From prevention to detection and resolution, Data Fraud Management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions analysis ppt slides file formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like before the payment, on the payment page, after the payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
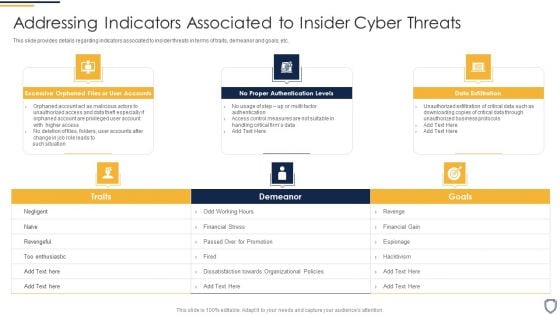
Corporate Security And Risk Management Addressing Indicators Associated To Insider Cyber Threats Topics PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. This is a corporate security and risk management addressing indicators associated to insider cyber threats topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like excessive orphaned files or user accounts, no proper authentication levels, data exfiltration . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
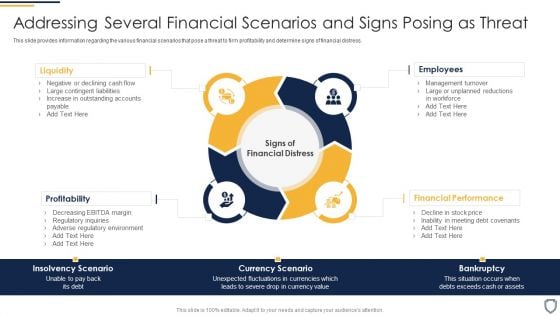
Corporate Security And Risk Management Addressing Several Financial Scenarios And Signs Posing As Threat Pictures PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting corporate security and risk management addressing several financial scenarios and signs posing as threat pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like profitability, liquidity, employees, financial performance . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
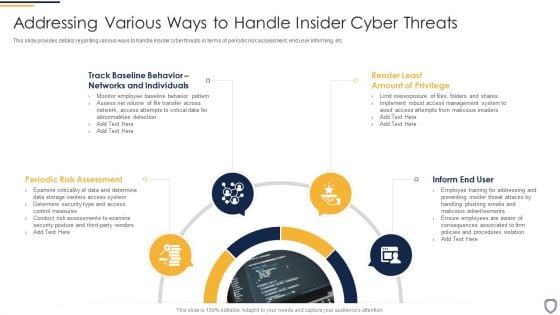
Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Infographics PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a corporate security and risk management addressing various ways to handle insider cyber threats infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, inform end user, render least amount of privilege, track baseline behavior networks and individuals . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Various Types Of Workplace Violence And Threats Designs PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Presenting corporate security and risk management various types of workplace violence and threats designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like threats or threatening behavior, physical assault, property damage, stalking, harassment or intimidation . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
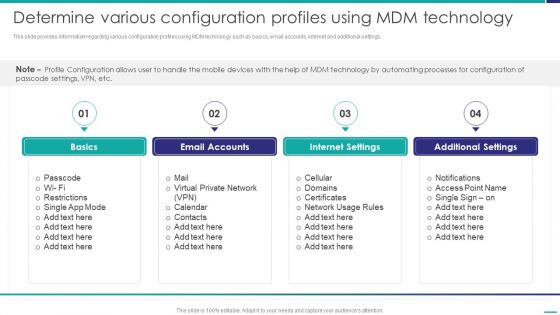
Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF
This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Presenting Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Restrictions, Internet Settings, Additional Settings. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Monitoring Plan Professional PDF
Presenting way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan professional pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like monitoring all systems, monitoring network traffic, monitoring user activity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
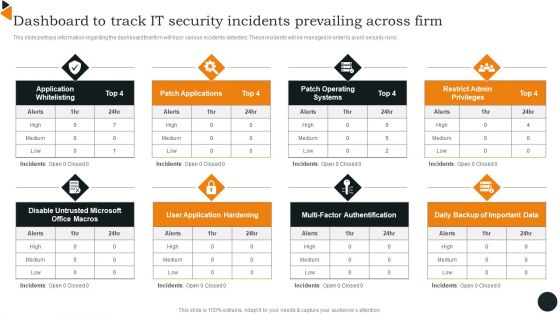
Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
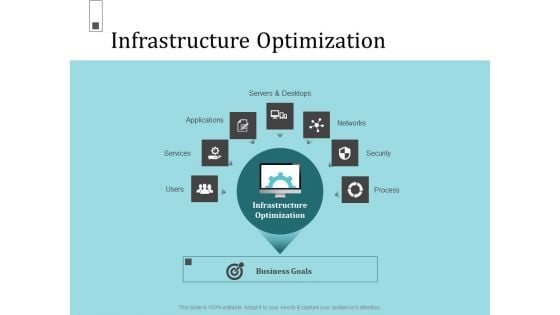
Infrastructure Project Management In Construction Infrastructure Optimization Professional PDF
This is a infrastructure project management in construction infrastructure optimization professional pdf. template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like services, networks, security, process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
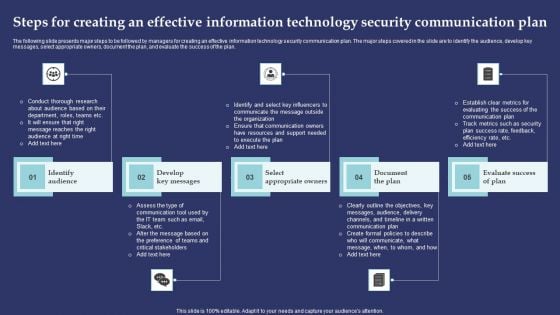
Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF
The following slide presents major steps to be followed by managers for creating an effective information technology security communication plan. The major steps covered in the slide are to identify the audience, develop key messages, select appropriate owners, document the plan, and evaluate the success of the plan. Presenting Steps For Creating An Effective Information Technology Security Communication Plan Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Identify Audience, Develop Key Messages, Select Appropriate Owners. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.m
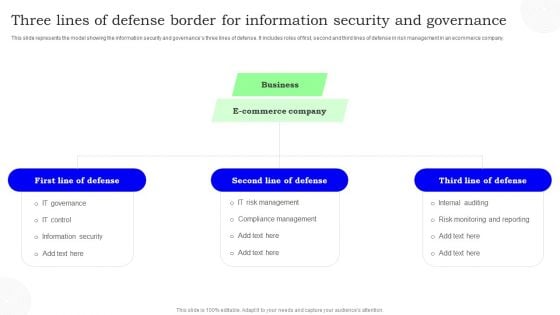
Three Lines Of Defense Border For Information Security And Governance Information PDF
This slide represents the model showing the information security and governances three lines of defense. It includes roles of first, second and third lines of defense in risk management in an ecommerce company. Persuade your audience using this Three Lines Of Defense Border For Information Security And Governance Information PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Defense, Commerce Company, Business. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
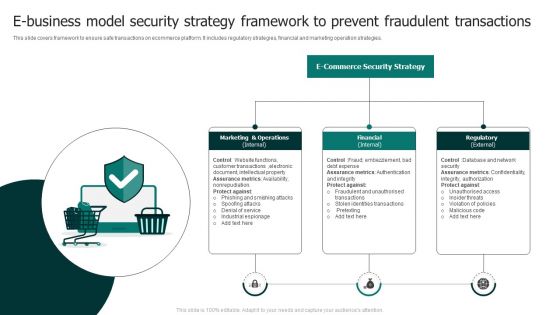
E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF
This slide covers framework to ensure safe transactions on ecommerce platform. It includes regulatory strategies, financial and marketing operation strategies. Persuade your audience using this E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Transactions, Assurance Metrics, Document Intellectual. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
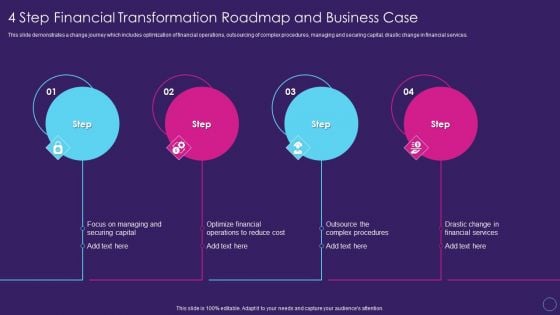
Digital Transformation Toolkit Accounting Finance 4 Step Financial Transformation Roadmap Mockup PDF
This slide demonstrates a change journey which includes optimization of financial operations, outsourcing of complex procedures, managing and securing capital, drastic change in financial services. This is a digital transformation toolkit accounting finance 4 step financial transformation roadmap mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like managing, securing, operations, financial, procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
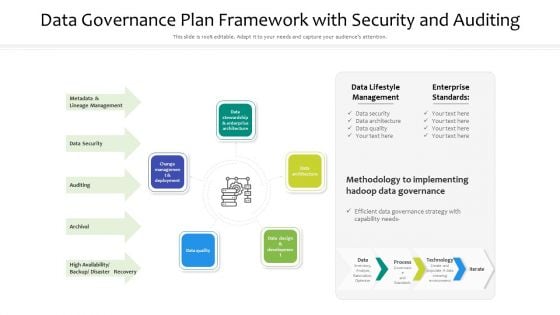
Data Governance Plan Framework With Security And Auditing Ppt PowerPoint Presentation File Template PDF
Presenting data governance plan framework with security and auditing ppt powerpoint presentation file template pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including data architecture, data quality, change management and deployment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
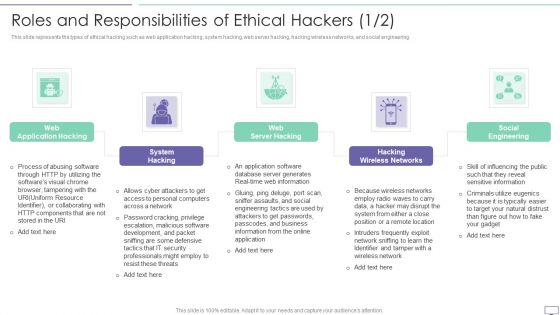
IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF
This slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering.Presenting IT Security Hacker Roles And Responsibilities Of Ethical Hackers Pictures PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Application Hacking, System Hacking, Wireless Networks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
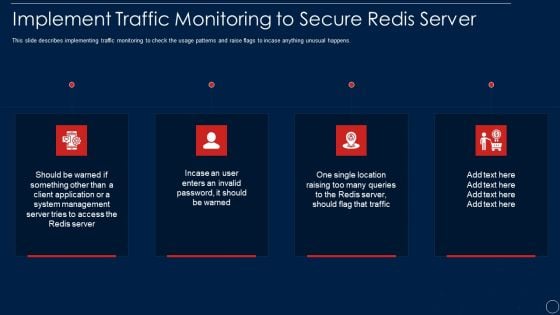
Redis Cache Data Structure IT Implement Traffic Monitoring To Secure Redis Server Ideas PDF
This slide describes implementing traffic monitoring to check the usage patterns and raise flags to incase anything unusual happens. Presenting redis cache data structure it implement traffic monitoring to secure redis server ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management, system, location. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. The Global Cyber Security Trend Analysis Ppt PowerPoint Presentation File Styles PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
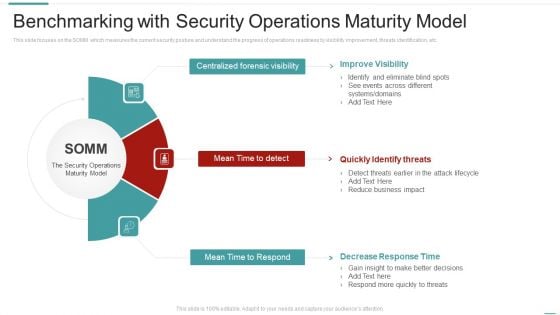
Risk Recognition Automation Benchmarking With Security Operations Maturity Model Ppt Pictures Infographic Template PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting risk recognition automation benchmarking with security operations maturity model ppt pictures infographic template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improve visibility, quickly identify threats, decrease response time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
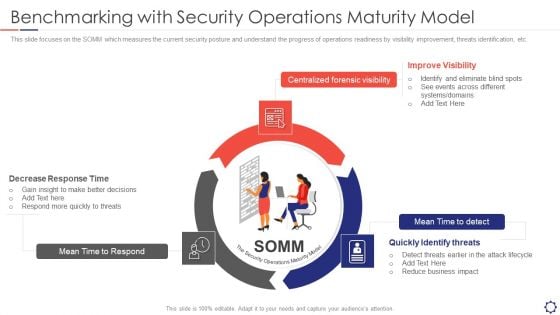
SIEM Benchmarking With Security Operations Maturity Model Ppt Layouts Templates PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. This is a siem benchmarking with security operations maturity model ppt layouts templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like mean time to respond, centralized forensic visibility, mean time to detect. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
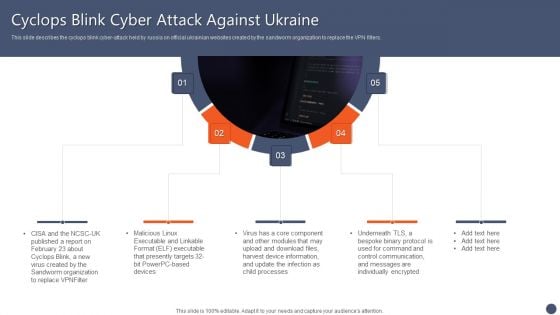
Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF
This slide describes the cyclops blink cyber attack held by russia on official ukrainian websites created by the sandworm organization to replace the VPN filters. Get a simple yet stunning designed Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 Cyclops Blink Cyber Attack Against Ukraine Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
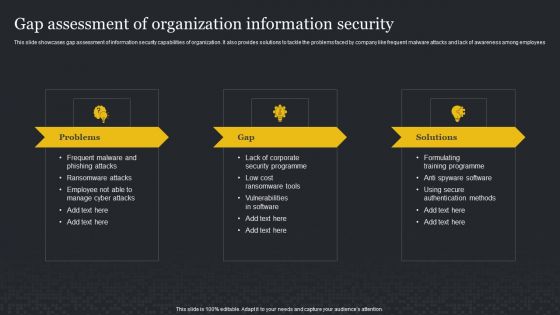
Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employees. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF.
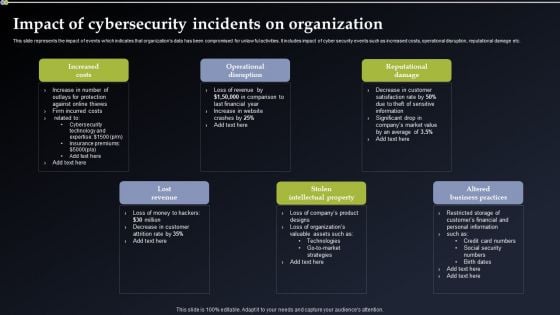
Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Impact Of Cybersecurity Incidents On Organization Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Recent Technologies In IT Industry Need For Cyber Security Technology Brochure PDF
This slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Retrieve professionally designed Recent Technologies In IT Industry Need For Cyber Security Technology Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
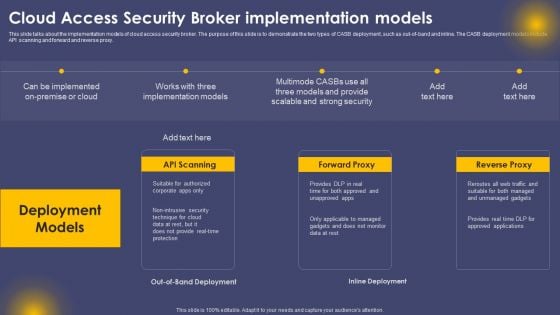
Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF
This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
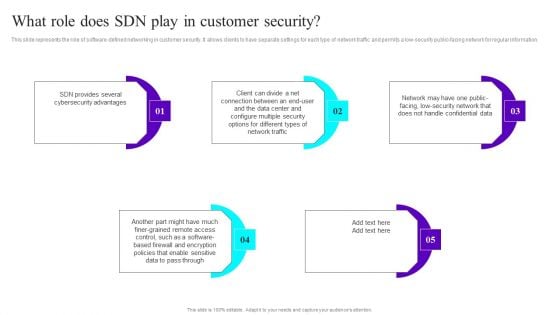
What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information. Do you know about Slidesgeeks What Role Does SDN Play In Customer Security Ppt Infographic Template Slides PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
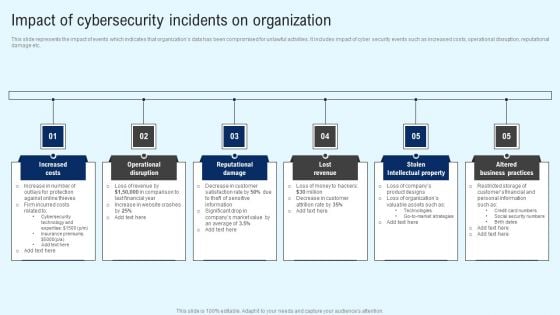
Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Get a simple yet stunning designed Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
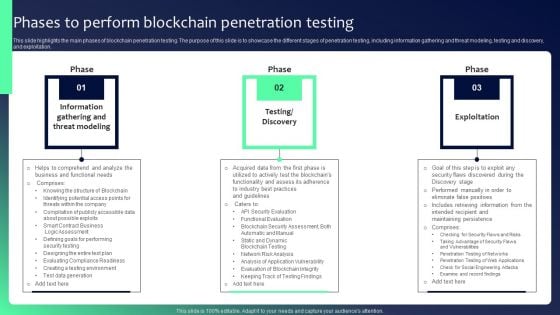
Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF
This slide highlights the main phases of blockchain penetration testing. The purpose of this slide is to showcase the different stages of penetration testing, including information gathering and threat modeling, testing and discovery, and exploitation. Find highly impressive Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
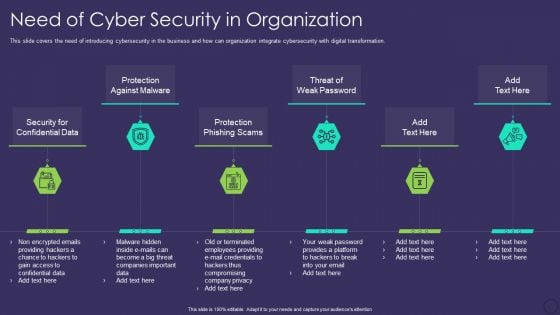
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
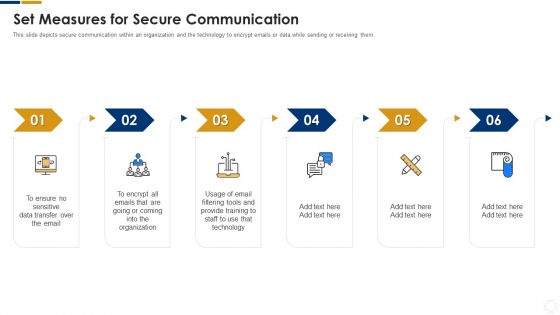
Cybersecurity Set Measures For Secure Communication Ppt Visual Aids Show PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Presenting cybersecurity set measures for secure communication ppt visual aids show pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like organization, technology, email. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
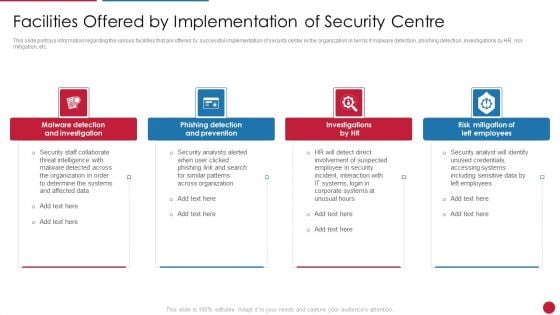
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Campaign Roadmap With Goal And Target Audience Mockup PDF
This slide shows timeline for campaign to raise security awareness . It covers target audience, goal, phase 1 and 2. Persuade your audience using this Security Awareness Campaign Roadmap With Goal And Target Audience Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Target Audience, Goal, awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF
This slide depicts the hermetic wiper attack on ukrainian corporations, detected by a threat intelligence agency on february 23rd, and it damaged the master boot record through eases partition master. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Non Governmental Organization Action Plan To Secure Human Rights And Dignity Mockup PDF
This slide covers the strategic plan adopted by NGO non governmental organization to secure rights and dignity for all. The purpose of this template is to depict the NGO strategic plan. It also includes details related to vision, mission, goals, etc.Persuade your audience using this Non Governmental Organization Action Plan To Secure Human Rights And Dignity Mockup PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Crowdfunding Through, Social Responsibility, Collecting Recycling. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
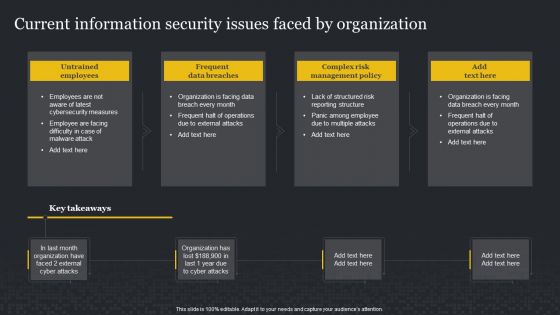
Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF
This Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF
Are you searching for a Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF from Slidegeeks today.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF
This slide signifies the strategic plan timeline to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor Persuade your audience using this Strategic Plan Roadmap To Develop Effective Cyber Security Strategy Icons PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Analyse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
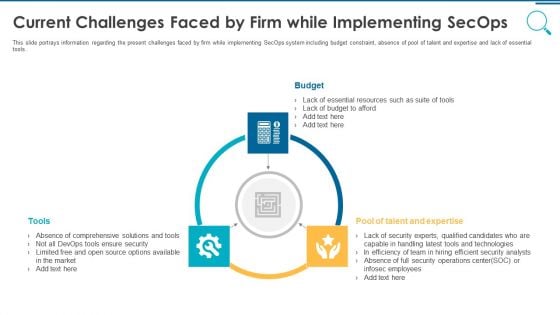
Information And Technology Security Operations Current Challenges Faced By Firm While Implementing Secops Slides PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting information and technology security operations current challenges faced by firm while implementing secops slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Security Solutions Current Challenges Faced By Firm While Implementing Secops Topics PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting organizational security solutions current challenges faced by firm while implementing secops topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget tools, pool of talent and expertise. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
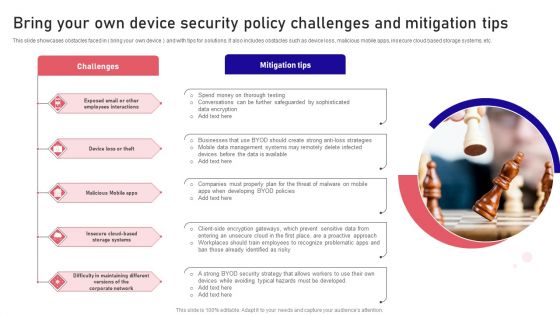
Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF
This slide showcases obstacles faced in bring your own device and with tips for solutions. It also includes obstacles such as device loss, malicious mobile apps, insecure cloud based storage systems, etc. Presenting Bring Your Own Device Security Policy Challenges And Mitigation Tips Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Challenges, Mitigation Tips, Malicious Mobile. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
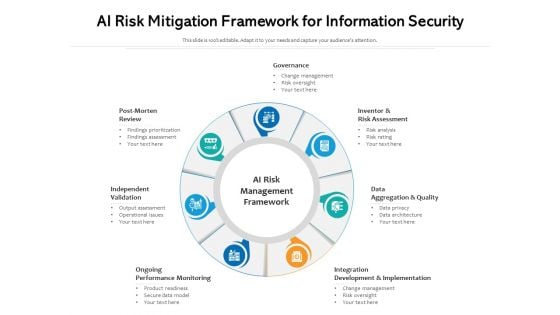
AI Risk Mitigation Framework For Information Security Ppt PowerPoint Presentation Gallery Slides PDF
Presenting ai risk mitigation framework for information security ppt powerpoint presentation gallery slides pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including governance, independent validation, ongoing performance monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Incidents Functions Report With Icons Ppt PowerPoint Presentation Gallery Influencers PDF
Presenting security incidents functions report with icons ppt powerpoint presentation gallery influencers pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including priority resolving, priority critical, priority moderate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Three Area Ppt Visual For Static Application Security Testing Sast Ppt PowerPoint Presentation File Show PDF
Presenting three area ppt visual for static application security testing sast ppt powerpoint presentation file show pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Agency Business Profile Mission Vision And Core Values Microsoft PDF
Presenting Security Agency Business Profile Mission Vision And Core Values Microsoft PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Mission Vision, Core Values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
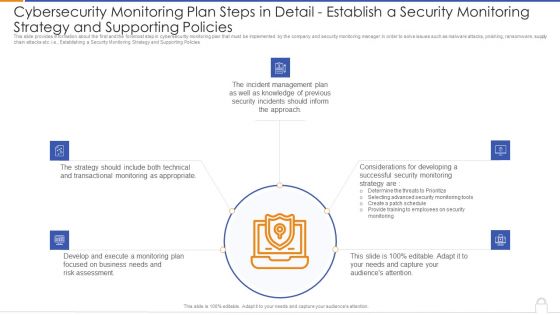
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Supporting Policies Microsoft PDF
Presenting cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like transactional monitoring, develop and execute, incident management plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
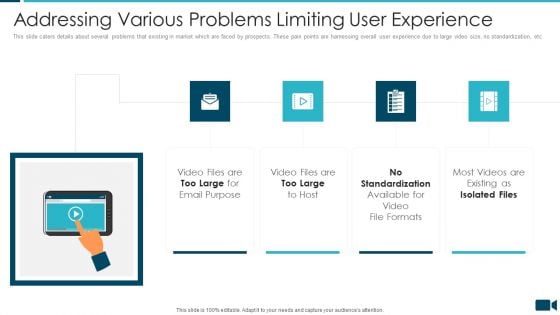
Secured Video Hosting Platform Investor Capital Funding Addressing Various Problems Limiting User Experience Topics PDF
This slide caters details about several problems that existing in market which are faced by prospects. These pain points are harnessing overall user experience due to large video size, no standardization, etc. This is a secured video hosting platform investor capital funding addressing various problems limiting user experience topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like addressing various problems limiting user experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
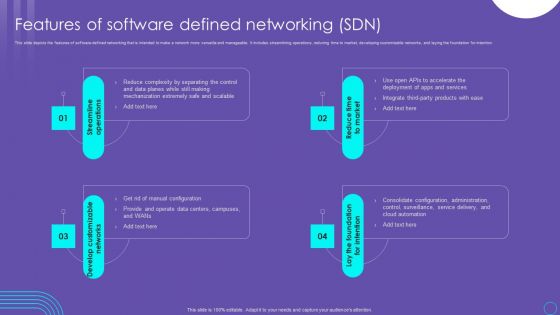
SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF
This slide depicts the features of software defined networking that is intended to make a network more versatile and manageable. It includes streamlining operations, reducing time to market, developing customizable networks, and laying the foundation for intention. This SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
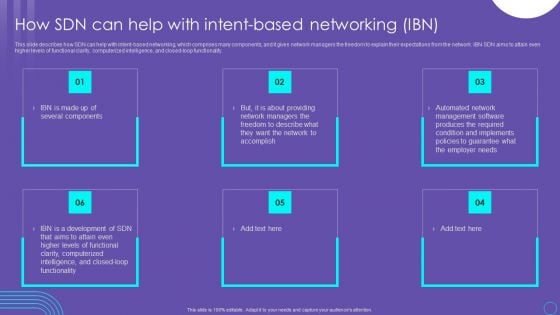
SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF
This slide describes how SDN can help with intent based networking, which comprises many components, and it gives network managers the freedom to explain their expectations from the network. IBN SDN aims to attain even higher levels of functional clarity, computerized intelligence, and closed loop functionality. Explore a selection of the finest SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
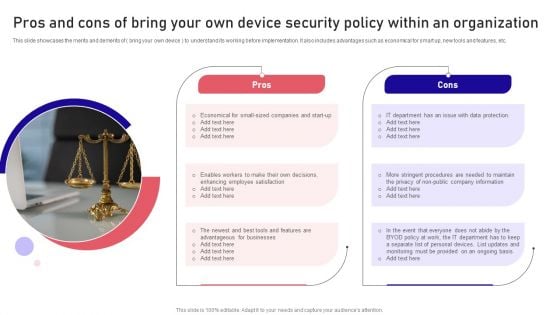
Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF
This slide showcases the merits and demerits of bring your own device to understand its working before implementation. It also includes advantages such as economical for smart up, new tools and features, etc. Presenting Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Data Protection, Organization, Company Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
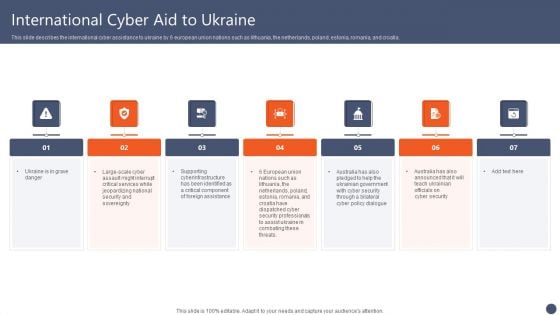
Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF
This slide describes the international cyber assistance to ukraine by 6 european union nations such as lithuania, the netherlands, poland, estonia, romania, and croatia. Get a simple yet stunning designed Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF
This slide shows that information privacy laws are beneficial for both social media platforms and their users, as it protects companies from any unnecessary penalties while providing users the required data protection. Get a simple yet stunning designed Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Information Security Data Privacy In Social Media Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well arranged Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
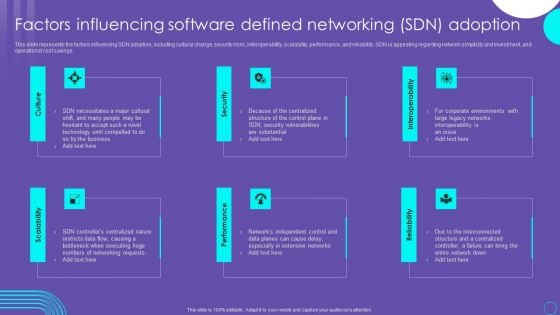
SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.


 Continue with Email
Continue with Email

 Home
Home


































