Process Safety
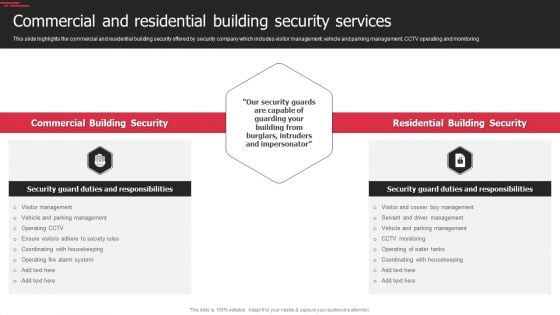
Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Security Agency Business Profile Commercial And Residential Building Security Services Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Presenting Manpower Corporate Security Business Profile Commercial And Residential Building Security Services Clipart PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Commercial Building Security, Residential Building Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IoT Security Best Practices In Banking Sector IoT In Banking For Digital Future IoT SS V
Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable IoT Security Best Practices In Banking Sector IoT In Banking For Digital Future IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc.

Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides
Incorporate this Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides to make your business idea and proposal stand out. This will also ensure that your proposal,in seventeen slides of this complete deck,is well organized and professional. You can also add variables like market opportunity,value proposition,innovative solutions,and more for any business concern or issue that you might be facing. Download this design now. The 100 percent customizable nature of the template adds to the beauty of the entire concept of the off the shelf presentation concept that we have mastered. Our Cyber Security Response Management Ppt Powerpoint Presentation Complete Deck With Slides are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
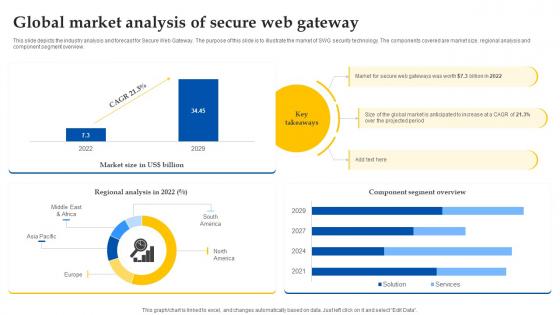
Web Access Control Solution Global Market Analysis Of Secure Web Gateway
This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview. This Web Access Control Solution Global Market Analysis Of Secure Web Gateway is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Web Access Control Solution Global Market Analysis Of Secure Web Gateway features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today This slide depicts the industry analysis and forecast for Secure Web Gateway. The purpose of this slide is to illustrate the market of SWG security technology. The components covered are market size, regional analysis and component segment overview.

Team And Success Key Business PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Team and Success Key Business PowerPoint Templates PPT Backgrounds for Slides 1112.Use our Success PowerPoint Templates because, many a core idea has various enveloping layers. Use our Security PowerPoint Templates because, Business 3D Circular Puzzle: - Your business and plans for its growth consist of processes that are highly co-related. Use our Business PowerPoint Templates because, we provide the means to project your views. Use our Finance PowerPoint Templates because, Spread the light of knowledge around you, clear the doubts and enlighten the questioning minds with your brilliance and ability. Use our Teamwork PowerPoint Templates because, It You intend to deliver. Make it happen with our Team And Success Key Business PowerPoint Templates Ppt Backgrounds For Slides 1112. Make sure your presentation gets the attention it deserves.

Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Do you know about Slidesgeeks Measures To Maintain Data Security In Datafication Ethical Dimensions Of Datafication Infographics Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls.
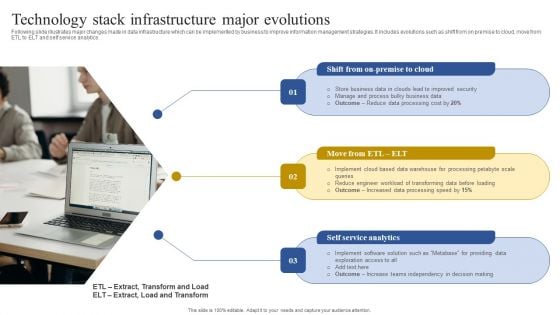
Technology Stack Infrastructure Major Evolutions Download PDF
Following slide illustrates major changes made in data infrastructure which can be implemented by business to improve information management strategies. It includes evolutions such as shift from on premise to cloud, move from ETL to ELT and self service analytics. Persuade your audience using this Technology Stack Infrastructure Major Evolutions Download PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Business Data, Improved Security, Processing Cost. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. The Cryptographic Cloud Security Solution Cloud Data Security Using Cryptography Inspiration Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.
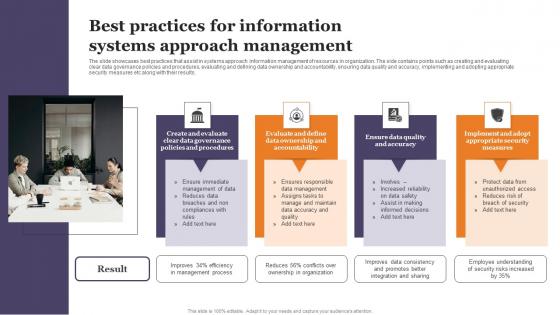
Best Practices For Information Systems Approach Management Professional Pdf
The slide showcases best practices that assist in systems approach information management of resources in organization. The side contains points such as creating and evaluating clear data governance policies and procedures, evaluating and defining data ownership and accountability, ensuring data quality and accuracy, implementing and adopting appropriate security measures etc along with their results. Showcasing this set of slides titled Best Practices For Information Systems Approach Management Professional Pdf The topics addressed in these templates are Policies And Procedures, Ownership And Accountability, Security Measures All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. The slide showcases best practices that assist in systems approach information management of resources in organization. The side contains points such as creating and evaluating clear data governance policies and procedures, evaluating and defining data ownership and accountability, ensuring data quality and accuracy, implementing and adopting appropriate security measures etc along with their results.
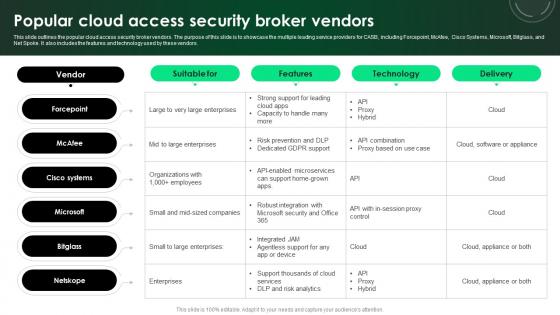
CASB 2 0 IT Popular Cloud Access Security Broker Vendors
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. CASB 2 0 IT Popular Cloud Access Security Broker Vendors will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today. This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors.
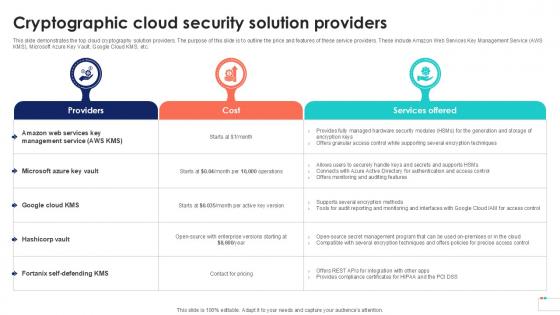
Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template
This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cryptographic Cloud Security Solution Data Security In Cloud Computing Ppt Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide demonstrates the top cloud cryptography solution providers. The purpose of this slide is to outline the price and features of these service providers. These include Amazon Web Services Key Management Service AWS KMS, Microsoft Azure Key Vault, Google Cloud KMS, etc.
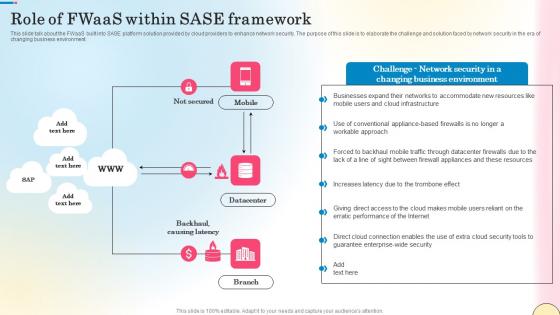
Role Of Fwaas Within Sase Framework Network Security Elements Pdf
This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment. Want to ace your presentation in front of a live audience Our Role Of Fwaas Within Sase Framework Network Security Elements Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide talk about the FWaaS built into SASE platform solution provided by cloud providers to enhance network security. The purpose of this slide is to elaborate the challenge and solution faced by network security in the era of changing business environment.

Security Camera Services Proposal Template Table Of Contents One Pager Sample Example Document
Presenting you an exemplary Security Camera Services Proposal Template Table Of Contents One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Security Camera Services Proposal Template Table Of Contents One Pager Sample Example Document brilliant piece now.
Table Of Contents Security Camera Services Proposal Template One Pager Sample Example Document
Presenting you an exemplary Table Of Contents Security Camera Services Proposal Template One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents Security Camera Services Proposal Template One Pager Sample Example Document brilliant piece now.

Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template
This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Devsecops Adoption Integration Security Into Ci Cd Pipeline Role Of Devsecops Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, codecommit, build test, deploy, and monitor.
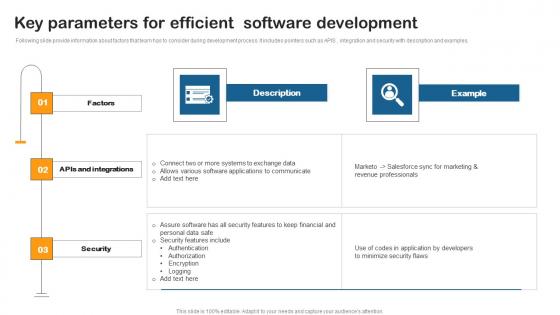
Key Parameters Efficient Software Building Utility Billing Invoicing Management System Mockup Pdf
Following slide provide information about factors that team has to consider during development process. It includes pointers such as APIS , integration and security with description and examples. This modern and well arranged Key Parameters Efficient Software Building Utility Billing Invoicing Management System Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. Following slide provide information about factors that team has to consider during development process. It includes pointers such as APIS , integration and security with description and examples.
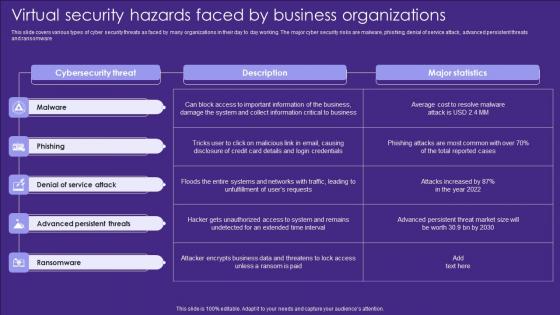
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout. This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware
Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf
The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer. This Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Esteemed Clientele Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today The slide outlines clients served by an IT company that offers open source technologies to build platforms for voice powered applications. It highlights clients photo and the name of customer.

3d Man With Locked Jigsaw Puzzle Security PowerPoint Templates And PowerPoint Themes 1112
We present our 3d Man With Locked Jigsaw Puzzle Security PowerPoint Templates And PowerPoint Themes 1112.Use our Business PowerPoint Templates because,Sales & Marketing funnel:- You have the product you need. Use our People PowerPoint Templates because, This template with an image of helps you chart the course of your presentation. Use our Security PowerPoint Templates because, Use our templates to emphasise your views. Use our Success PowerPoint Templates because, Corporate Ladder:- The graphic is a symbol of growth and sucess. Use our Puzzles or Jigsaws PowerPoint Templates because, Business 3D Circular Puzzle:- Your business and plans for its growth consist of processes that are highly co-related.Use these PowerPoint slides for presentations relating to Man with puzzle, business, people, security, success, puzzles or jigsaws, shapes. The prominent colors used in the PowerPoint template are Green, Black, White Our 3d Man With Locked Jigsaw Puzzle Security PowerPoint Templates And PowerPoint Themes 1112 have an enduring feature. They constantly remind people of your views.

Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document
This slide illustrates the cover letter for the business proposal providing a brief overview of the clients wants and a brief introduction to the project. Presenting you an exemplary Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Security Camera Services Proposal Template One Pager Sample Example Document brilliant piece now.
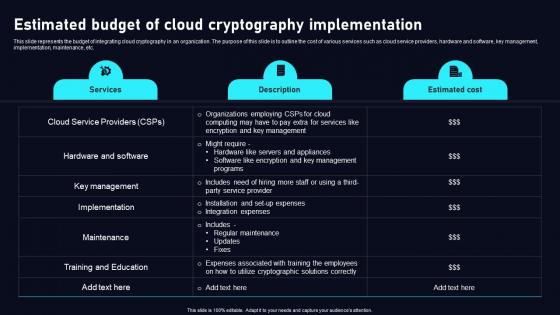
Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. This Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc.
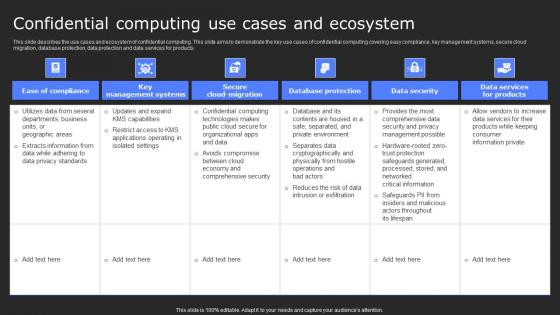
Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. The Confidential Computing Use Cases And Ecosystem Secure Computing Framework Guidelines Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
Key In The Labyrinth Complex Structure Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Key In The Labyrinth Complex Structure Security PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Money PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Download and present our Finance PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit. Use our Security PowerPoint Templates because You can Hit the nail on the head with our PowerPoint Templates and Slides. Embed your ideas in the minds of your audience. Download our Services PowerPoint Templates because You should Press the right buttons with our PowerPoint Templates and Slides. They will take your ideas down the perfect channel. Use our Business PowerPoint Templates because You can Create a matrix with our PowerPoint Templates and Slides. Feel the strength of your ideas click into place.Use these PowerPoint slides for presentations relating to Key in the labyrinth with complex security, security, services, business, shapes, success. The prominent colors used in the PowerPoint template are Orange, Black, White. Estabish the key factors of your scheme. Explain the crucial elements with our Key In The Labyrinth Complex Structure Security PowerPoint Templates Ppt Backgrounds For Slides 0213.

Piggy Bank Secured With Padlock Business PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Piggy Bank Secured With Padlock Business PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Download our Chains PowerPoint Templates because Our PowerPoint Templates and Slides are a sure bet. Gauranteed to win against all odds. Use our Business PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Present our Services PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Present our Success PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake.Use these PowerPoint slides for presentations relating to Piggy bank secured with padlock and chain, security, chains, business, services, success. The prominent colors used in the PowerPoint template are Yellow, Green lime , Black. Our Piggy Bank Secured With Padlock Business PowerPoint Templates Ppt Backgrounds For Slides 0213 will follow your bent of mind. They adapt to the contours of your thought process.
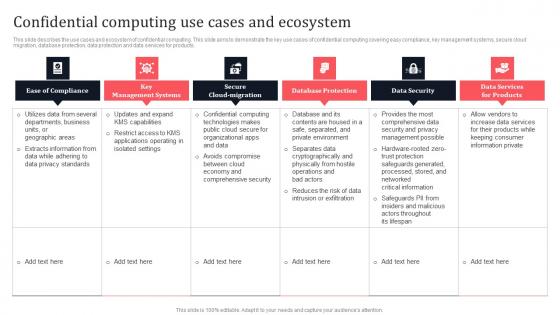
Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf
This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products. Explore a selection of the finest Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Confidential Computing Use Cases And Ecosystem Secure Multi Party Mockup Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks. This slide describes the use cases and ecosystem of confidential computing. This slide aims to demonstrate the key use cases of confidential computing covering easy compliance, key management systems, secure cloud migration, database protection, data protection and data services for products.
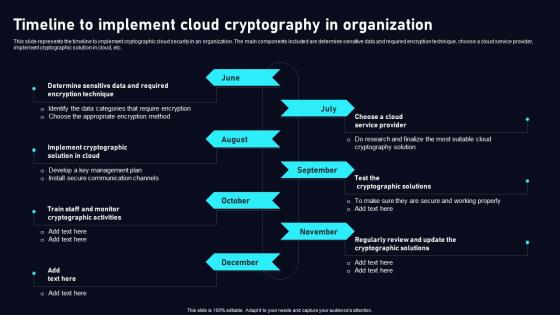
Timeline To Implement Cloud Data Security Using Cryptography Download Pdf
This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Timeline To Implement Cloud Data Security Using Cryptography Download Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
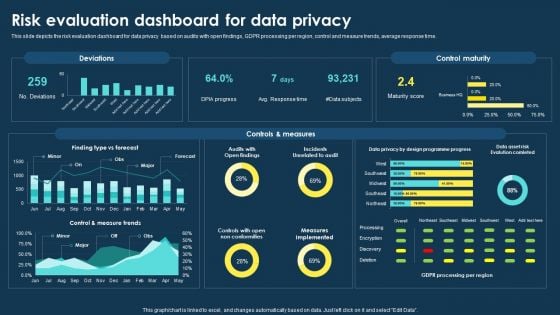
Integrating Data Privacy System Roadmap For Data Privacy Implementation Ppt Ideas Graphic Images
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Explore a selection of the finest Integrating Data Privacy System Risk Evaluation Dashboard For Data Privacy Ppt File Slides PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Integrating Data Privacy System Risk Evaluation Dashboard For Data Privacy Ppt File Slides PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Products And Services Offered Manufacturing Control Software Company Investor PPT Template
This slide caters to details related to a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Manufacturing Control Software Company Investor PPT Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide caters to details related to a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights.

Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable. This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc.
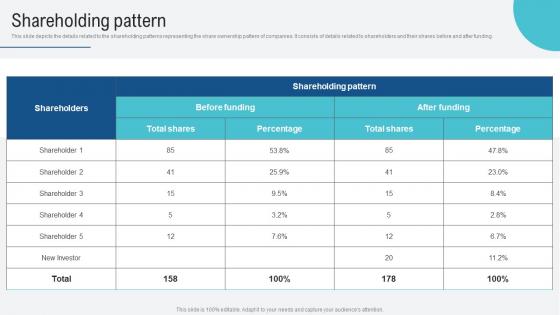
Shareholding Pattern Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide showcases revenue model of business which generates income which are enterprise partnerships, value added services, hardware integrations and developer ecosystem. Boost your pitch with our creative Shareholding Pattern Voice Assistance Security Platform Investor Funding Presentation Professional Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide showcases revenue model of business which generates income which are enterprise partnerships, value added services, hardware integrations and developer ecosystem.
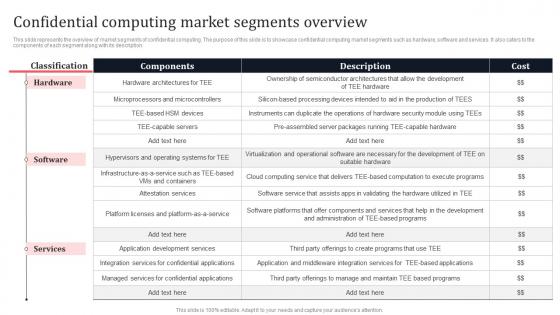
Confidential Computing Market Segments Overview Secure Multi Party Background Pdf
This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Confidential Computing Market Segments Overview Secure Multi Party Background Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Confidential Computing Market Segments Overview Secure Multi Party Background Pdf This slide represents the overview of market segments of confidential computing. The purpose of this slide is to showcase confidential computing market segments such as hardware, software and services. It also caters to the components of each segment along with its description.

Key Secure Web Gateway Solution Providers Web Threat Protection System
This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Key Secure Web Gateway Solution Providers Web Threat Protection System from Slidegeeks and deliver a wonderful presentation. This slide outlines the popular service providers of Secure Wen Gateway. The purpose of this slide is to demonstrate the services provided by various SWG solutions such as Cisco, Symantec, McAfee, Zscaler, Barracuda Networks, Fortinet, etc.
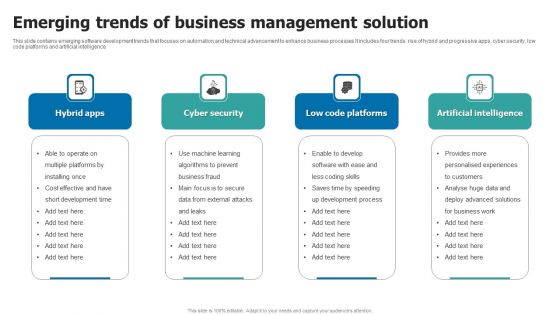
Emerging Trends Of Business Management Solution Template PDF
This slide contains emerging software development trends that focuses on automation and technical advancement to enhance business processes It includes four trends rise of hybrid and progressive apps, cyber security, low code platforms and artificial intelligence. Persuade your audience using this Emerging Trends Of Business Management Solution Template PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Hybrid Apps, Cyber Security, Low Code Platforms. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
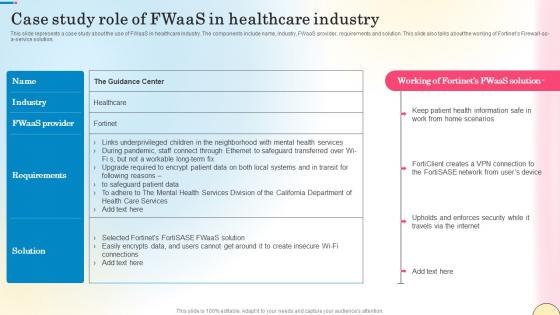
Case Study Role Of Fwaas In Healthcare Industry Network Security Slides Pdf
This slide represents a case study about the use of FWaaS in healthcare industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the working of Fortinets Firewall-as-a-service solution. Slidegeeks is here to make your presentations a breeze with Case Study Role Of Fwaas In Healthcare Industry Network Security Slides Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first This slide represents a case study about the use of FWaaS in healthcare industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the working of Fortinets Firewall-as-a-service solution.
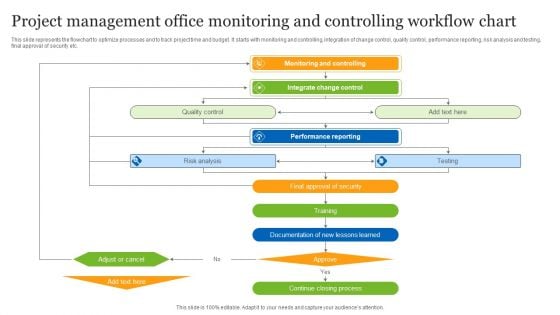
Project Management Office Monitoring And Controlling Workflow Chart Ppt Slides Mockup PDF
This slide represents the flowchart to optimize processes and to track project time and budget. It starts with monitoring and controlling, integration of change control, quality control, performance reporting, risk analysis and testing, final approval of security etc. Presenting Project Management Office Monitoring And Controlling Workflow Chart Ppt Slides Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Monitoring And Controlling, Integrate Change Control, Performance Reporting. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
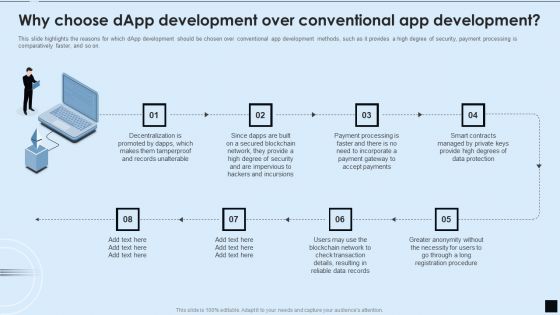
Decentralized Applications IT Why Choose Dapp Development Over Conventional App Development Brochure PDF
This slide highlights the reasons for which dApp development should be chosen over conventional app development methods, such as it provides a high degree of security, payment processing is comparatively faster, and so on. This is a Decentralized Applications IT Why Choose Dapp Development Over Conventional App Development Brochure PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Decentralization, Security, Payments. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Data Security Industry Report Major Market Trends Impacting Cybersecurity Industry IR SS V
The slide highlights the market trends in the global cybersecurity industry. These trends are having a significant impact on the way the industry operates, and they are likely to continue in the coming years. It cover trends such as artificial intelligence, real-time data monitoring, managed services, users as an attack surface, and quantum cryptography. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Global Data Security Industry Report Major Market Trends Impacting Cybersecurity Industry IR SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. The slide highlights the market trends in the global cybersecurity industry. These trends are having a significant impact on the way the industry operates, and they are likely to continue in the coming years. It cover trends such as artificial intelligence, real-time data monitoring, managed services, users as an attack surface, and quantum cryptography.

Overall Costs For Handling Comprehensive Guide For Building Management Template Pdf
The following slide showcases budget analysis which can help facility managers in deploying their services effectively. It provides information about building maintenance, equipment, machinery, security, pest control, sanitation, etc. Are you searching for a Overall Costs For Handling Comprehensive Guide For Building Management Template Pdf that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overall Costs For Handling Comprehensive Guide For Building Management Template Pdf from Slidegeeks today. The following slide showcases budget analysis which can help facility managers in deploying their services effectively. It provides information about building maintenance, equipment, machinery, security, pest control, sanitation, etc.
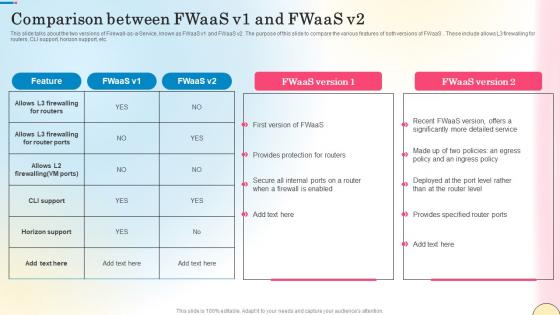
Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf
This slide talks about the two versions of Firewall-as-a-Service, known as FWaaS v1 and FWaaS v2. The purpose of this slide to compare the various features of both versions of FWaaS . These include allows L3 firewalling for routers, CLI support, horizon support, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparison Between Fwaas V1 And Fwaas V2 Network Security Brochure Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide talks about the two versions of Firewall-as-a-Service, known as FWaaS v1 and FWaaS v2. The purpose of this slide to compare the various features of both versions of FWaaS . These include allows L3 firewalling for routers, CLI support, horizon support, etc.
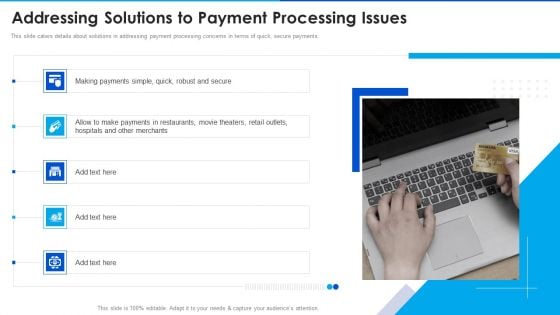
Digital Payment Solution Company Stakeholder Addressing Solutions To Payment Summary PDF
This slide caters details about solutions in addressing payment processing concerns in terms of quick, secure payments. Presenting digital payment solution company stakeholder addressing solutions to payment summary pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like making payments simple, hospitals and other merchants, payments in restaurants In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
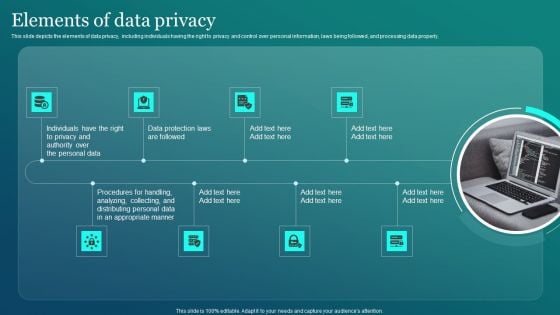
Information Security Elements Of Data Privacy Ppt PowerPoint Presentation File Deck PDF
This slide depicts the elements of data privacy, including individuals having the right to privacy and control over personal information, laws being followed, and processing data properly. Present like a pro with Information Security Elements Of Data Privacy Ppt PowerPoint Presentation File Deck PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
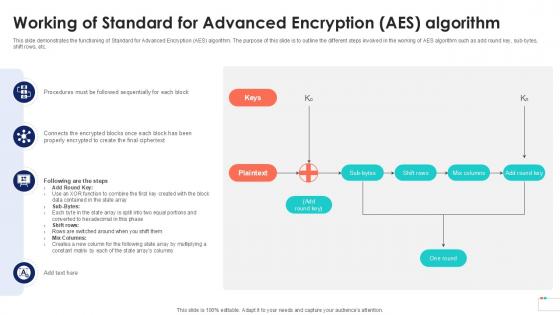
Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc.
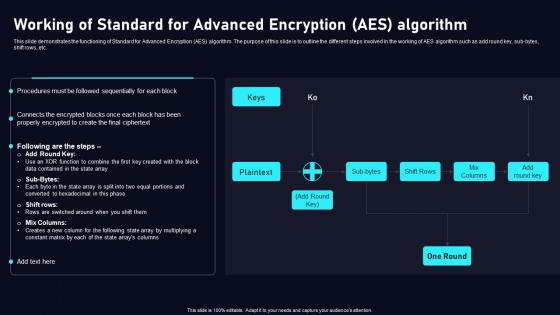
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay. This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc.
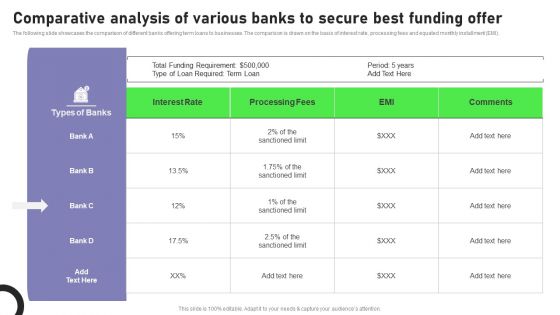
Comparative Analysis Of Various Banks To Secure Best Funding Offer Designs PDF
The following slide showcases the comparison of different banks offering term loans to businesses. The comparison is drawn on the basis of interest rate, processing fees and equated monthly installment EMI. Presenting this PowerPoint presentation, titled Comparative Analysis Of Various Banks To Secure Best Funding Offer Designs PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Comparative Analysis Of Various Banks To Secure Best Funding Offer Designs PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Comparative Analysis Of Various Banks To Secure Best Funding Offer Designs PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
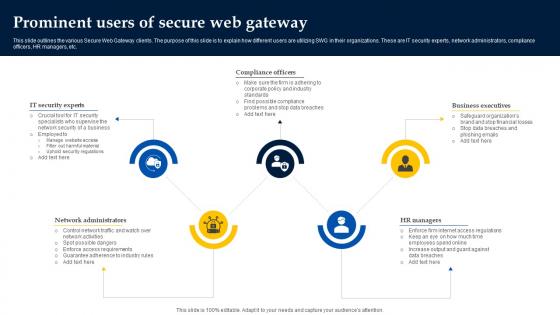
Web Access Control Solution Prominent Users Of Secure Web Gateway
Do you know about Slidesgeeks Web Access Control Solution Prominent Users Of Secure Web Gateway These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes. This slide outlines the various Secure Web Gateway clients. The purpose of this slide is to explain how different users are utilizing SWG in their organizations. These are IT security experts, network administrators, compliance officers, HR managers, etc.

Types Of Access Control In Application Security Testing Ppt Powerpoint Topics
This slide outlines the different types of access control safeguards in application security which include Role-based Access Control RBAC, Access Control Lists, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Types Of Access Control In Application Security Testing Ppt Powerpoint Topics to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Types Of Access Control In Application Security Testing Ppt Powerpoint Topics. This slide outlines the different types of access control safeguards in application security which include Role-based Access Control RBAC, Access Control Lists, etc.
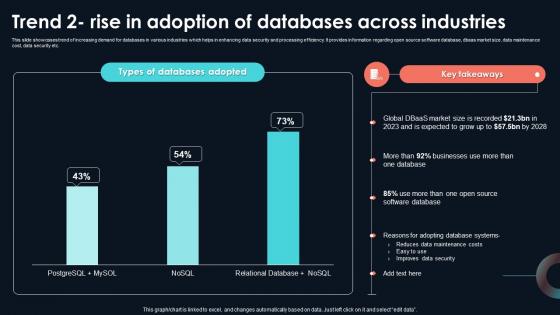
Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc. This Trend 2 Rise In Adoption Of Databases Across Developing Strategic Insights Using Big Data Analytics SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide showcases trend of increasing demand for databases in various industries which helps in enhancing data security and processing efficiency. It provides information regarding open source software database, dbaas market size, data maintenance cost, data security etc.

Critical Principles Of Zero Trust Network Access Security Formats Pdf
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Critical Principles Of Zero Trust Network Access Security Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Critical Principles Of Zero Trust Network Access Security Formats Pdf today and make your presentation stand out from the rest This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything.
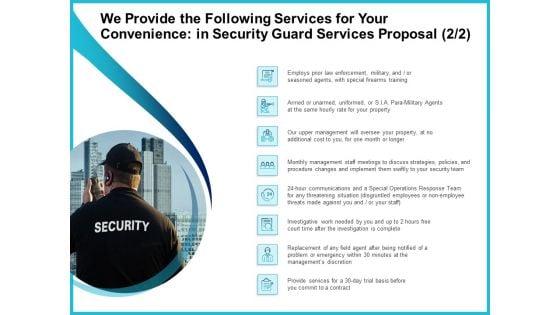
Uniformed Security We Provide The Following Services For Your Convenience In Security Guard Services Proposal Formats PDF
Deliver an awe inspiring pitch with this creative uniformed security we provide the following services for your convenience in security guard services proposal formats pdf bundle. Topics like training, strategies, policies, management, investigative can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
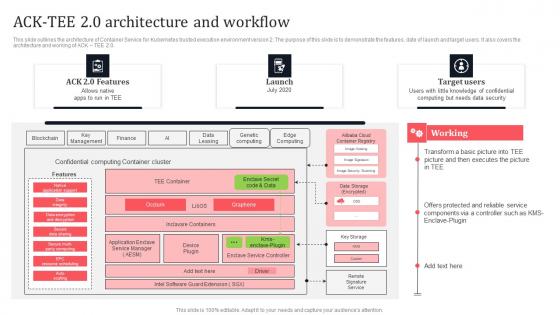
Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf
This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Ack Tee 2 0 Architecture And Workflow Secure Multi Party Mockup Pdf This slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0.

Cyber Network Code Security PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with cyber security network data monitor as abstract Factor it all in with our Cyber Network Code Security PowerPoint Templates And PowerPoint Backgrounds 0511. They account for every element.
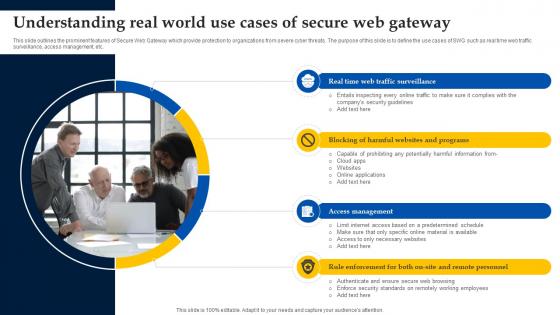
Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway
This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Understanding Real World Use Cases Of Secure Web Gateway and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide outlines the prominent features of Secure Web Gateway which provide protection to organizations from severe cyber threats. The purpose of this slide is to define the use cases of SWG such as real time web traffic surveillance, access management, etc.

Cybersecurity Operations Cybersecops Steps To Build Security Operations Center Structure PDF
This slide represents the main steps to developing a security operations center. The purpose of this slide is to highlight the main building steps involved in a SecOps creation. These steps include selecting a service model, location, technology, people and processes. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Cybersecurity Operations Cybersecops Steps To Build Security Operations Center Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Us Dollars Locked And Chained Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our US Dollars Locked And Chained Security PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Money PowerPoint Templates because You can Hit the nail on the head with our PowerPoint Templates and Slides. Embed your ideas in the minds of your audience. Download and present our Security PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Download our Business PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download and present our Services PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines.Use these PowerPoint slides for presentations relating to Dismiss the blues with our Us Dollars Locked And Chained Security PowerPoint Templates Ppt Backgrounds For Slides 0113. Your thoughts will dispel all despondency.

Technical Criteria Billing Building Utility Billing And Invoicing Management System Structure Pdf
Following slide represents technological factor to consider while selecting billing system. It includes pointers such as security, deployment options and developer experience. Find a pre designed and impeccable Technical Criteria Billing Building Utility Billing And Invoicing Management System Structure Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. Following slide represents technological factor to consider while selecting billing system. It includes pointers such as security, deployment options and developer experience.

Web Access Control Solution Reasons Behind Need For Secure Web Gateway
Find a pre-designed and impeccable Web Access Control Solution Reasons Behind Need For Secure Web Gateway. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide discusses the requirement of Secure Web Gateway in protecting organizations from various cyber crimes. The reasons behind need of Secure Web Gateway are protection against web-based threats, enforce security policies, controlled access, etc.
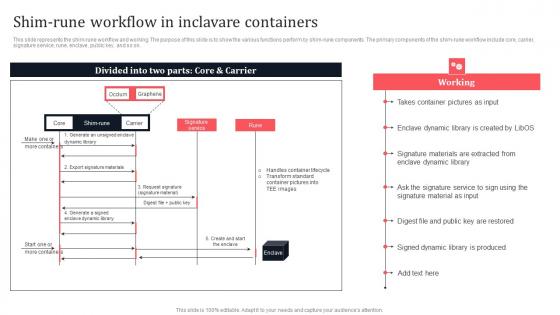
Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf
This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf can be your best option for delivering a presentation. Represent everything in detail using Shim Rune Workflow In Inclavare Containers Secure Multi Party Ideas Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the shim-rune workflow and working. The purpose of this slide is to show the various functions perform by shim-rune components. The primary components of the shim-rune workflow include core, carrier, signature service, rune, enclave, public key, and so on.
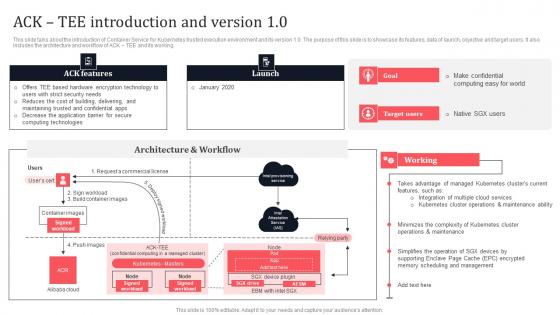
Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working.

Web Access Control Solution Secure Web Gateway For Remote And Onsite Workers
This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. There are so many reasons you need a Web Access Control Solution Secure Web Gateway For Remote And Onsite Workers. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily. This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees.


 Continue with Email
Continue with Email

 Home
Home


































