Process Safety

Comprehensive Guide For Website Website Security Management Action Plan
Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc. Welcome to our selection of the Comprehensive Guide For Website Website Security Management Action Plan. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. Mentioned slide provides insights into site security management tips which can be implemented by businesses to prevent hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, etc.
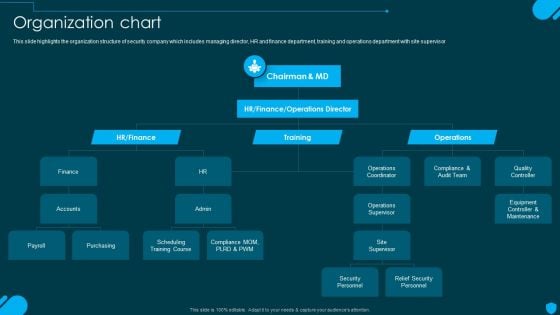
Security And Human Resource Services Business Profile Organization Chart Elements PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security And Human Resource Services Business Profile Organization Chart Elements PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
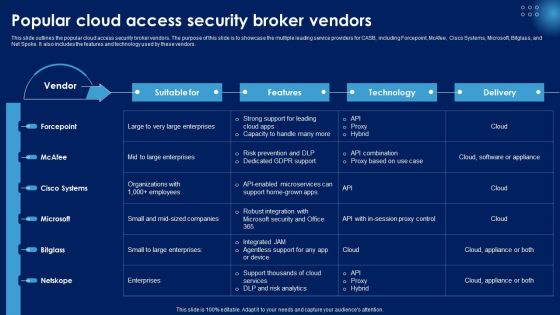
Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF today and make your presentation stand out from the rest.

Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF from Slidegeeks today. This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
Business Diagram Five Staged Colorful Key Diagram Text Boxes Presentation Template
This business diagram has been designed with graphic of five staged keys and text boxes. Download this diagram to analyze the key points. This diagram offers a way for your audience to visually conceptualize the process.

Features Of Zero Trust Network Access Security Model Background Pdf
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Background Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Background Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
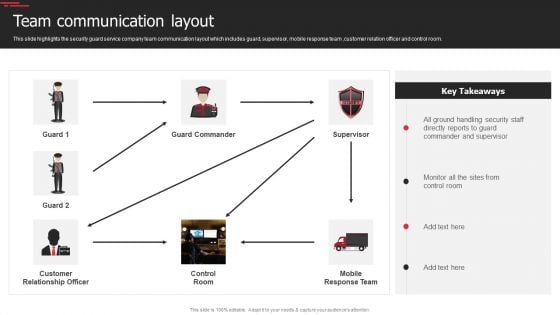
Security Agency Business Profile Team Communication Layout Topics PDF
This slide highlights the security guard service company team communication layout which includes guard, supervisor, mobile response team ,customer relation officer and control room. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Team Communication Layout Topics PDF. Use them to share invaluable insights on Customer Relationship Officer, Mobile Response Team, Supervisor and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Manpower Corporate Security Business Profile Team Communication Layout Icons PDF
This slide highlights the security guard service company team communication layout which includes guard, supervisor, mobile response team , customer relation officer and control room. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Team Communication Layout Icons PDF bundle. Topics like Customer Relationship Officer, Supervisor, Mobile Response Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
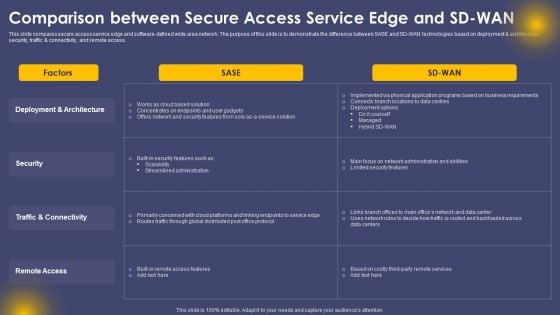
Comparison Between Secure Access Service Edge And Sd Wan Ppt Outline Guide PDF
This slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Find a pre designed and impeccable Comparison Between Secure Access Service Edge And Sd Wan Ppt Outline Guide PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Benefits Of Zero Trust Network Security Portrait Pdf
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Zero Trust Network Security Portrait Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control AND visibility, invisible infrastructure, and simple app segmentation.
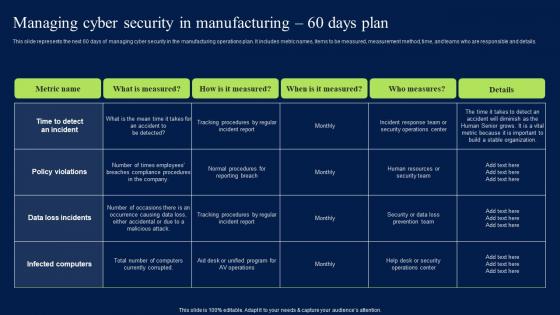
Managing Cyber Security In Manufacturing 60 Days Plan Mockup PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Retrieve professionally designed Managing Cyber Security In Manufacturing 60 Days Plan Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere. This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.
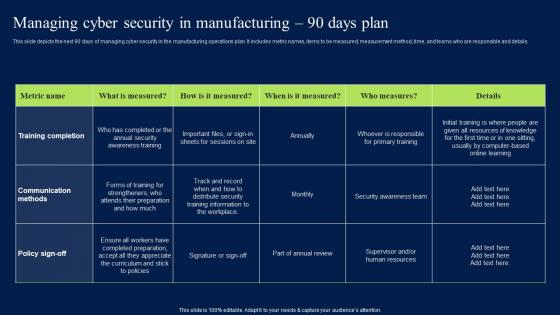
Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, andteams who are responsible and details. Slidegeeks has constructed Managing Cyber Security In Manufacturing 90 Days Plan Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates. This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details.

Our Services For Security Services Proposal One Pager Sample Example Document
Presenting you an exemplary Our Services For Security Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Services For Security Services Proposal One Pager Sample Example Document brilliant piece now.
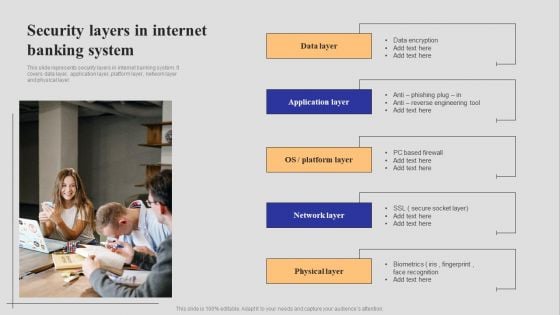
Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF
This slide represents security layers in internet banking system. It covers data layer, application layer, platform layer, network layer and physical layer. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
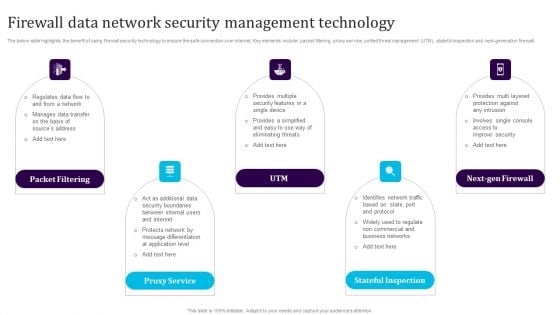
Firewall Data Network Security Management Technology Template PDF
The below slide highlights the benefit of using firewall security technology to ensure the safe connection over internet. Key elements include packet filtering, proxy service, unified threat management UTM, stateful inspection and next-generation firewall. Persuade your audience using this Firewall Data Network Security Management Technology Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Packet Filtering, Proxy Service, Utm, Next Gen Firewall, Stateful Inspection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Computing Application Security Architecture Framework Elements PDF
The slide shows a framework describing security architecture to meet organizational unique requirements. It includes setting goals, determining process, constructing architecture and reviewing and revising security model. Showcasing this set of slides titled Cloud Computing Application Security Architecture Framework Elements PDF. The topics addressed in these templates are Set Goals, Determine Process, Construct Architecture. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
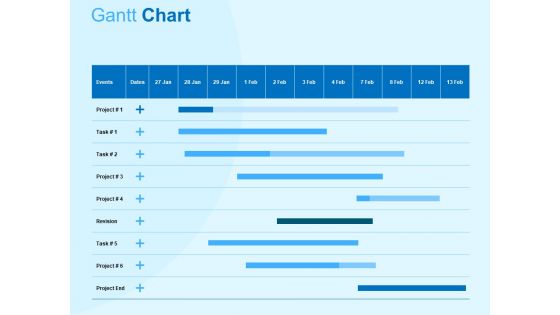
Damage Security Insurance Proposal Gantt Chart Ppt Gallery Graphic Tips PDF
Your complex projects can be managed and organized simultaneously using this detailed damage security insurance proposal gantt chart ppt gallery graphic tips pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.
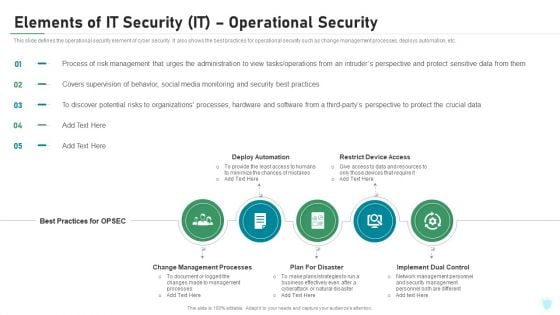
Elements Of IT Security IT Operational Security Ppt Outline Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting elements of it security it operational security ppt outline ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like change management processes, deploy automation, restrict device access, plan for disaster, implement dual control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
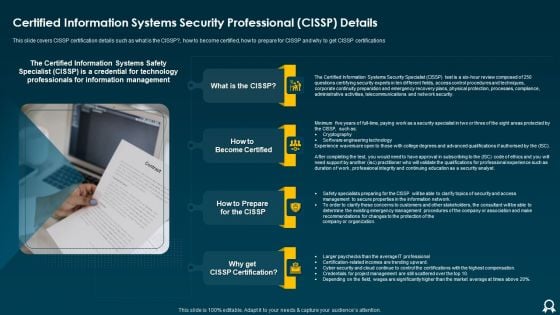
IT Data Services Certification Programs Certified Information Systems Security Professional CISSP Details Brochure PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Presenting IT Data Services Certification Programs Certified Information Systems Security Professional CISSP Details Brochure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Software Engineering Technology, Network Security, Telecommunications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Benefits Of Using Secure Web Gateway Web Threat Protection System
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Welcome to our selection of the Key Benefits Of Using Secure Web Gateway Web Threat Protection System. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc.
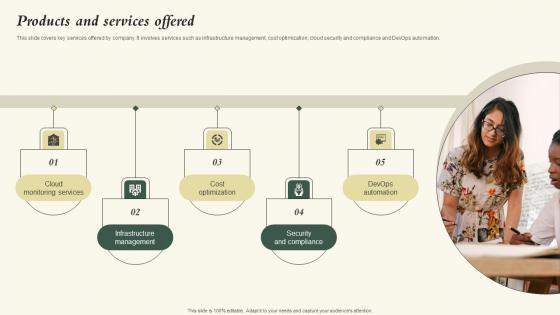
Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf
This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Nubity Capital Funding Pitch Deck Guidelines Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide covers key services offered by company. It involves services such as infrastructure management, cost optimization, cloud security and compliance and DevOps automation.
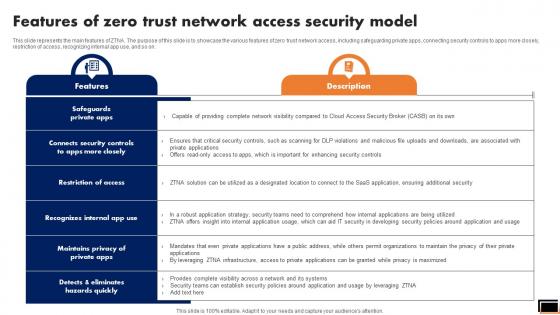
Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Features Of Zero Trust Network Access Security Model Software Defined Perimeter SDP that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.
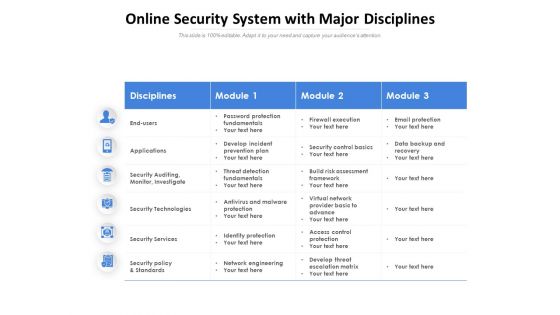
Online Security System With Major Disciplines Ppt PowerPoint Presentation Ideas Inspiration PDF
Presenting this set of slides with name online security system with major disciplines ppt powerpoint presentation ideas inspiration pdf. The topics discussed in these slides are disciplines, module, applications, security auditing, monitor, investigate, security technologies, security services, security policy and standards. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF
The following slide exhibits the advantages and disadvantages of red ocean strategy. The advantages mentioned in the slide are no need to create new marketplace, high demand of products and services etc. The disadvantages are difficult to survive in the existing market, no extraordinary profits etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF today and make your presentation stand out from the rest.

Zero Trust Model Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. This modern and well-arranged Zero Trust Model Features Of Zero Trust Network Access Security Model provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on.

Develop Corporate Cyber Security Risk Mitigation Plan Cover Letter For Organization Cyber Protection Services Inspiration PDF
Presenting develop corporate cyber security risk mitigation plan cover letter for organization cyber protection services inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like systems and servers, achieve goals, secure organization information, network security monitoring. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
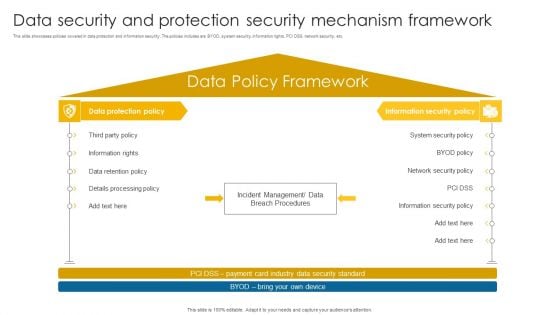
Data Security And Protection Security Mechanism Framework Background PDF
This slide showcases policies covered in data protection and information security. The policies includes are BYOD, system security, information rights, PCI DSS, network security, etc.Pitch your topic with ease and precision using this Data Security And Protection Security Mechanism Framework Background PDF. This layout presents information on Information Rights, Retention Policy, Details Processing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
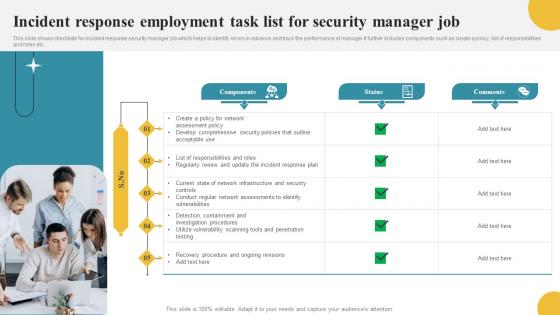
Incident Response Employment Task List For Security Manager Job Themes Pdf
This slide shows checklists for incident response security manager job which helps to identify errors in advance and track the performance of manager It further includes components such as create a policy, list of responsibilities and roles etc. Showcasing this set of slides titled Incident Response Employment Task List For Security Manager Job Themes Pdf The topics addressed in these templates are Components, Responsibilities And Roles, Response Plan All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide shows checklists for incident response security manager job which helps to identify errors in advance and track the performance of manager It further includes components such as create a policy, list of responsibilities and roles etc.

IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. There are so many reasons you need a IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Additional Service Offerings For Security Camera Services Proposal One Pager Sample Example Document
The slide presents the additional services offered by the bidding company in context with the project proposal. Presenting you an exemplary Additional Service Offerings For Security Camera Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Additional Service Offerings For Security Camera Services Proposal One Pager Sample Example Document brilliant piece now.

Exploring Investment Opportunities With Security Token Offerings Complete Deck
This seventy nine slide Exploring Investment Opportunities With Security Token Offerings Complete Deck is your content ready tool to impress the stakeholders with your business planning and its manner of execution. Showcase your ideas and how you plan to make them real in detail with this PPT Template Bundle. The slides have the conceptual bandwidth to present the crucial aspects of your plan, such as funding, marketing, resource allocation, timeline, roadmap, and more. When you present your plans with this PPT Layout, the stakeholders are sure to come on board because you will be able to present a succinct, thought-out, winning project. Download this Complete Deck now to take control into your hands. The 100 percent customizable offer is just too good to be resisted. Our Exploring Investment Opportunities With Security Token Offerings Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Cyber Security Risk Assessment And Management Ppt Powerpoint Presentation File Example File Pdf
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the Cyber Security Risk Assessment And Management Ppt Powerpoint Presentation File Example File Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.

Google Cloud Service Models Identity And Security Services On Google Cloud Platform Clipart PDF
This slide depicts the security services on the google cloud platform. The purpose of this slide is to show the various security services available on the google cloud platform. The main components include a cloud resource manager, cloud identity and access management, cloud security scanner, and cloud platform security. Welcome to our selection of the Google Cloud Service Models Identity And Security Services On Google Cloud Platform Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
Home Security Network Icon Ppt PowerPoint Presentation Portfolio Ideas
Presenting this set of slides with name home security network icon ppt powerpoint presentation portfolio ideas. The topics discussed in these slides are communication, teamwork, build network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain
This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain can be your best option for delivering a presentation. Represent everything in detail using Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.

Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Incident Response Preparation Ppt Powerpoint Presentation Diagram Templates Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation. This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to activities such as document incident response plan with policies and procedures etc.
PowerPoint Design Slides Executive Strategy Targets Umbrella Chart Ppt Templates
PowerPoint Design Slides Executive Strategy Targets Umbrella Chart PPT Templates-These high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT! Resolve the feud with our PowerPoint Design Slides Executive Strategy Targets Umbrella Chart Ppt Templates. Take all different approaches into consideration.
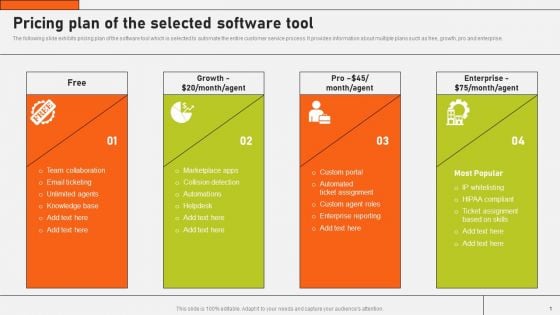
Securing Market Leadership Through Competitive Excellence Pricing Plan Of The Selected Software Tool Themes PDF
The following slide exhibits pricing plan of the software tool which is selected to automate the entire customer service process. It provides information about multiple plans such as free, growth, pro and enterprise. Slidegeeks is here to make your presentations a breeze with Securing Market Leadership Through Competitive Excellence Pricing Plan Of The Selected Software Tool Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Solution Offered Delivery Service Provider Business Model BMC SS V
This slide showcases solutions such as a delivery management system, live tracking, security and reliability, and responsive customer support. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Solution Offered Delivery Service Provider Business Model BMC SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates This slide showcases solutions such as a delivery management system, live tracking, security and reliability, and responsive customer support.
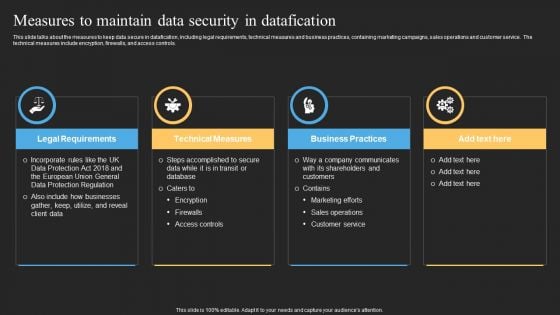
Datafy Measures To Maintain Data Security In Datafication Diagrams PDF
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Welcome to our selection of the Datafy Measures To Maintain Data Security In Datafication Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Comprehensive Guide To Blockchain Digital Security Risk Management Complete Deck
This Comprehensive Guide To Blockchain Digital Security Risk Management Complete Deck will give you an idea about business planning and how it helps in achievement of objectives and goals. With seventy seven slides,this complete deck aims to ensure that business planning is internalized in the audience. The 100 percent customisable template is also colour coded in a way that visually the message has a very clear impact. The presenter might not be a business expert,but the high quality PPT forces him her to rise to the ocassion. Download now to wow a roomful of people. Our Comprehensive Guide To Blockchain Digital Security Risk Management Complete Deck are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

Checklist To Implement Secure Access Service Edge Ppt Portfolio Outline PDF
Slidegeeks is here to make your presentations a breeze with Checklist To Implement Secure Access Service Edge Ppt Portfolio Outline PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
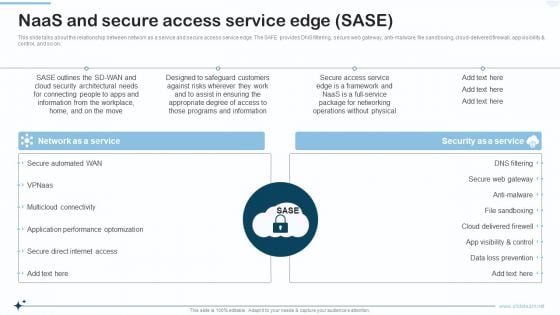
Naas Integrated Solution IT Naas And Secure Access Service Edge SASE Designs PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti malware, file sandboxing, cloud delivered firewall, app visibility and control, and so on. Presenting Naas Integrated Solution IT Naas And Secure Access Service Edge SASE Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Network As A Service, Security As A Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

CASB 2 0 IT Emerging Cloud Security Risks And Threats
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Boost your pitch with our creative CASB 2 0 IT Emerging Cloud Security Risks And Threats. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on.

Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf
This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc. This Iot Device Monitoring Dashboard To Analyse Security Issues Iot Device Management Template Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance. This slide includes a device monitoring dashboard to analyse network devices performance in various sites. It includes elements such as total sites, offline sites, sites with security issues, sites with major offline devices, site location, etc.
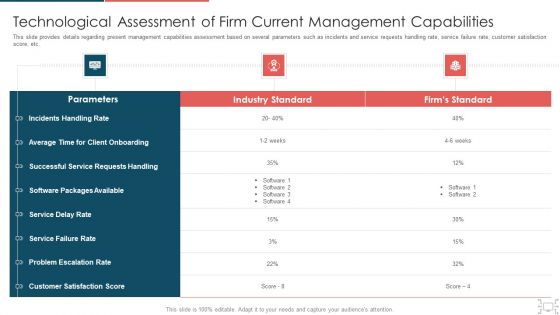
Cyber Security Administration In Organization Technological Assessment Of Firm Current Management Elements PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization technological assessment of firm current management elements pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Virtual Identify Biometric Access Control With Finger Print Scanner Themes PDF
Presenting virtual identify biometric access control with finger print scanner themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including virtual identify biometric access control with finger print scanner. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security And Human Resource Services Business Profile Employees Rules And Regulations Clipart PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. If you are looking for a format to display your unique thoughts, then the professionally designed Security And Human Resource Services Business Profile Employees Rules And Regulations Clipart PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security And Human Resource Services Business Profile Employees Rules And Regulations Clipart PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF
This slide outlines the business plan for managed security service which includes services such as antivirus, anti-malware, anti-spam etc. it also provides information about the total cost of services, status of purchase, security goal, etc. Pitch your topic with ease and precision using this Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF. This layout presents information on Revenue, Security Goal, IT Security Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF.

Civil Infrastructure Designing Services Management It Infrastructure Optimization Pictures PDF
Deliver an awe inspiring pitch with this creative civil infrastructure designing services management it infrastructure optimization pictures pdf bundle. Topics like management, security, process, service, customer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
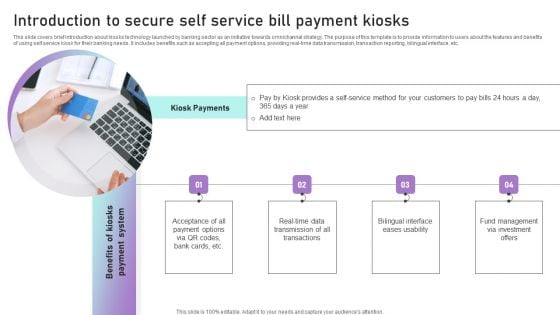
Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF
This slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real-time data transmission, transaction reporting, bilingual interface, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Introduction To Secure Self Service Bill Payment Kiosks Ppt Outline Grid PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
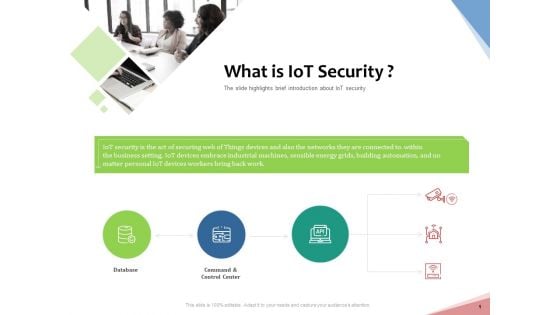
Machine To Machine Communication Outline What Is Iot Security Ppt PowerPoint Presentation Show PDF
The slide highlights brief introduction about IoT security. Presenting machine to machine communication outline what is iot security ppt powerpoint presentation show pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like database, command and control center, building automation, business. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

International Organization Standardization 270001 Performance Indicators To Measure Information Security Controls Clipart PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this international organization standardization 270001 performance indicators to measure information security controls clipart pdf. Use them to share invaluable insights on information security policy, information security training, incident response and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
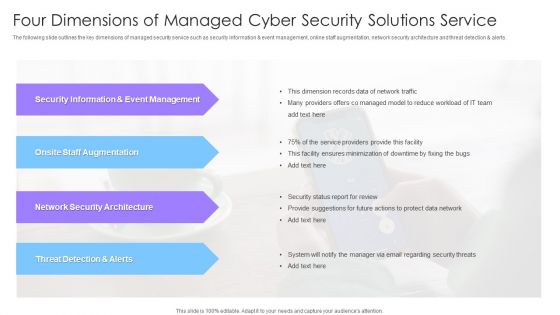
Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF
The following slide outlines the key dimensions of managed security service such as security information and event management, online staff augmentation, network security architecture and threat detection and alerts. Pitch your topic with ease and precision using this Four Dimensions Of Managed Cyber Security Solutions Service Ppt Pictures Model PDF. This layout presents information on Security Information, Event Management, Staff Augmentation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
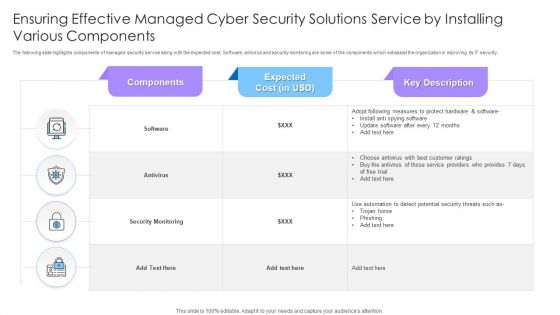
Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF
The following slide highlights components of managed security service along with the expected cost. Software, antivirus and security monitoring are some of the components which will assist the organization in improving its IT security. Showcasing this set of slides titled Ensuring Effective Managed Cyber Security Solutions Service By Installing Various Components Ppt Styles Example PDF. The topics addressed in these templates are Security Monitoring, Antivirus, Components. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
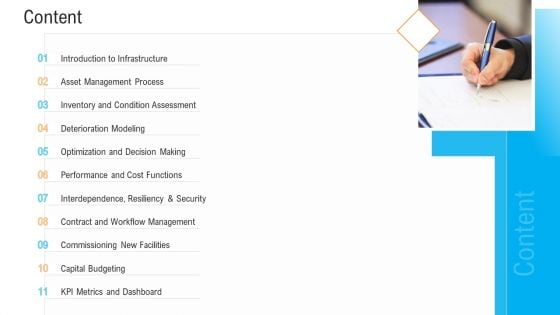
Civil Infrastructure Designing Services Management Content Information PDF
Presenting civil infrastructure designing services management content information pdf to provide visual cues and insights. Share and navigate important information on eleven stages that need your due attention. This template can be used to pitch topics like inventory, management process, cost, security, capital budgeting. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Training Program For Zero Trust Network Access Model Security Inspiration Pdf
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Find a pre-designed and impeccable Training Program For Zero Trust Network Access Model Security Inspiration Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation. This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training.

Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample
This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc. Boost your pitch with our creative Roadmap To Implement Tokenization For Data Security Securing Your Data Ppt Sample Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them. This slide outlines the deployment for tokenization. The purpose of this slide is to highlight the steps that an organization should take while implementing tokenization including, generating tokens, identifying sensitive data, etc.
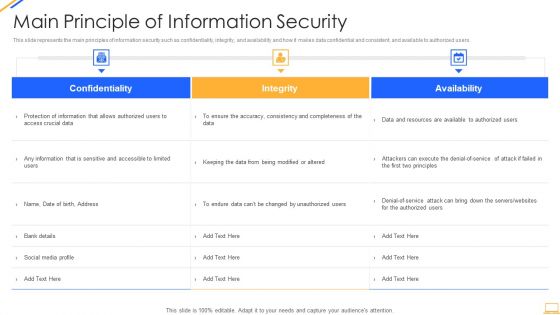
Desktop Security Management Main Principle Of Information Security Introduction PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver and pitch your topic in the best possible manner with this desktop security management main principle of information security introduction pdf. Use them to share invaluable insights on availability, integrity, confidentiality and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


 Continue with Email
Continue with Email

 Home
Home


































