Process Safety

Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V
The slide covers the cybersecurity industrys strengths, weaknesses, opportunities, and threats. The slide aims to identify internal and external factors impacting the industrys functioning. It will help stakeholders to develop strategies to achieve their objectives and improve efficiency. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today The slide covers the cybersecurity industrys strengths, weaknesses, opportunities, and threats. The slide aims to identify internal and external factors impacting the industrys functioning. It will help stakeholders to develop strategies to achieve their objectives and improve efficiency.
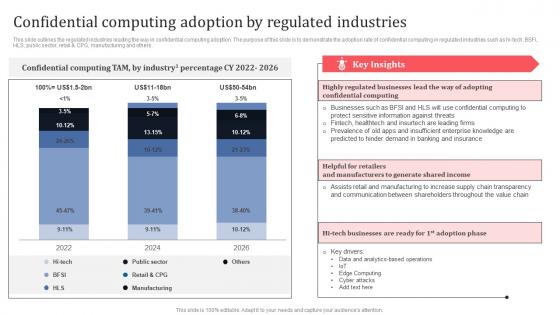
Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Get a simple yet stunning designed Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today. This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others.

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
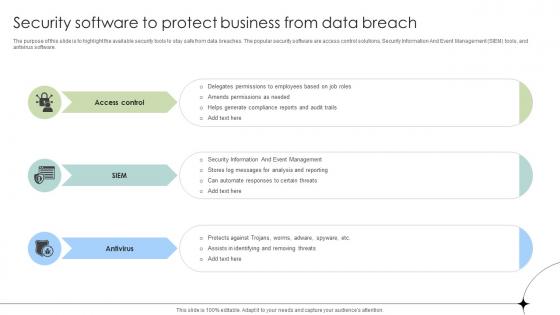
Security Software To Protect Business From Data Breach Data Fortification Strengthening Defenses
The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software To Protect Business From Data Breach Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software.

Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Are you searching for a Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF from Slidegeeks today.
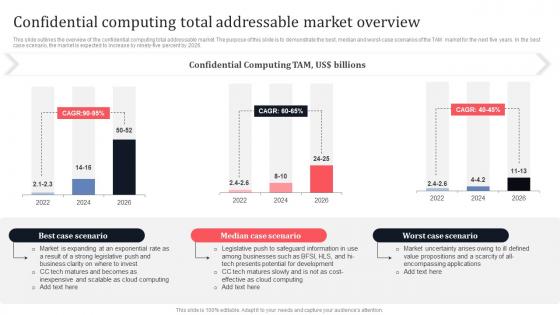
Confidential Computing Total Addressable Market Overview Secure Multi Party Download Pdf
This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Welcome to our selection of the Confidential Computing Total Addressable Market Overview Secure Multi Party Download Pdf These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today. This slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026.
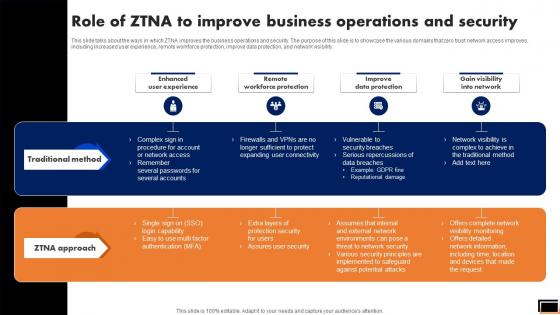
Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility.
Security Testing Tracking And Monitoring Harnessing The World Of Ethical Ppt Slide
This slide showcases the security testing tracking and monitoring dashboard components such as planning, design, development, testing, project budget, etc. The Security Testing Tracking And Monitoring Harnessing The World Of Ethical Ppt Slide is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. This slide showcases the security testing tracking and monitoring dashboard components such as planning, design, development, testing, project budget, etc.

Secured Internet Connection PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Secured Internet Connection PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Security PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Present our Technology PowerPoint Templates because you can Break through with our PowerPoint Templates and Slides. Bring down the mental barriers of your audience. Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Download and present our Shapes PowerPoint Templates because You will get more than you ever bargained for. Use our Signs PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience.Use these PowerPoint slides for presentations relating to Browser window with a Key, security, business, technology, signs, shapes. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Advertise your expertise with our Secured Internet Connection PowerPoint Templates Ppt Backgrounds For Slides 0313. Establish your undeniable command over the subject.
IT Security System Installation With Gear Wheel Vector Icon Ppt PowerPoint Presentation File Skills PDF
Presenting it security system installation with gear wheel vector icon ppt powerpoint presentation file skills pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including it security system installation with gear wheel vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
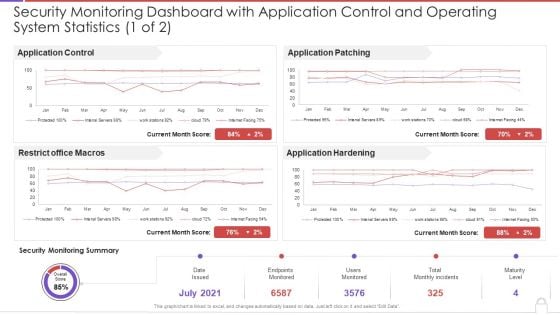
Security Monitoring Dashboard With Application Control And Operating System Statistics Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this security monitoring dashboard with application control and operating system statistics template pdf. Use them to share invaluable insights on application control, restrict office macros, application patching, application hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Dollars Chained And Locked Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Dollars Chained And Locked Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Money PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation. Download and present our Security PowerPoint Templates because You are working at that stage with an air of royalty. Let our PowerPoint Templates and Slides be the jewels in your crown. Use our Finance PowerPoint Templates because You should Bet on your luck with our PowerPoint Templates and Slides. Be assured that you will hit the jackpot. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Download our Chains PowerPoint Templates because Our PowerPoint Templates and Slides are like the strings of a tennis racquet. Well strung to help you serve aces.Use these PowerPoint slides for presentations relating to Safe secure chain locked dollar bills, money, security, finance, marketing, chains. The prominent colors used in the PowerPoint template are Black, Green, Gray. Conserve your energy with our Dollars Chained And Locked Security PowerPoint Templates Ppt Backgrounds For Slides 0213. Download without worries with our money back guaranteee.
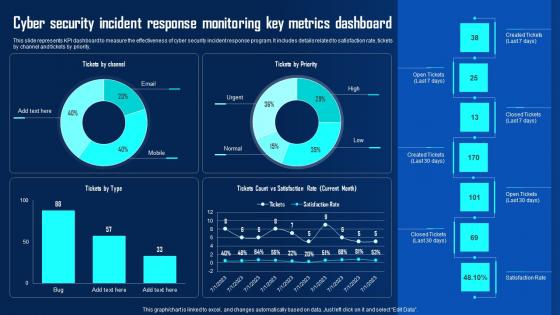
Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority.
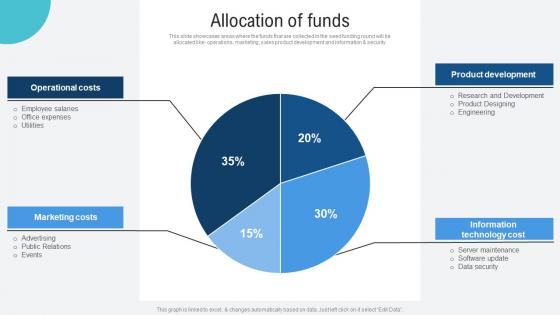
Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security. If you are looking for a format to display your unique thoughts, then the professionally designed Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Allocation Of Funds Voice Assistance Security Platform Investor Funding Presentation Professional Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. This slide showcases areas where the funds that are collected in the seed funding round will be allocated like operations, marketing, sales product development and information and security.

Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V. This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.
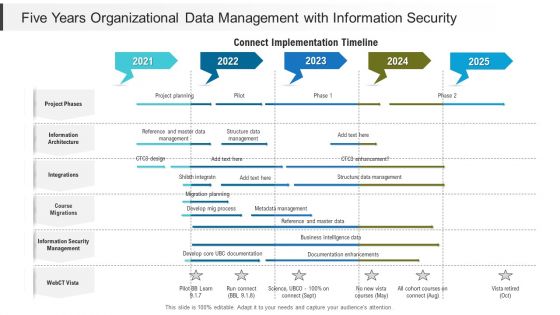
Five Years Organizational Data Management With Information Security Information
Presenting our jaw dropping five years organizational data management with information security information. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
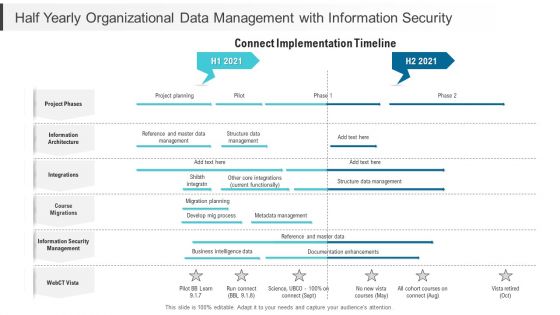
Half Yearly Organizational Data Management With Information Security Designs
Presenting our jaw dropping half yearly organizational data management with information security designs. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
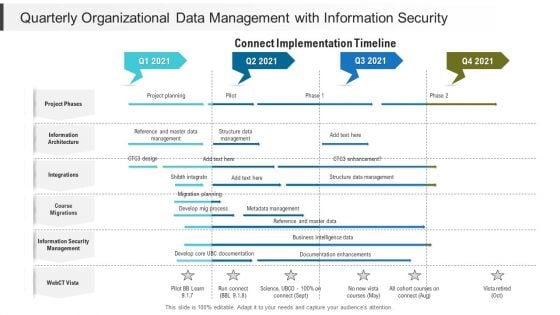
Quarterly Organizational Data Management With Information Security Ideas
Presenting our jaw dropping quarterly organizational data management with information security ideas. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
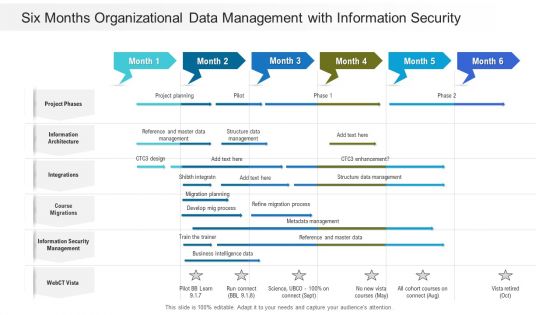
Six Months Organizational Data Management With Information Security Sample
Presenting our jaw dropping six months organizational data management with information security sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Three Months Organizational Data Management With Information Security Information
Presenting our jaw dropping three months organizational data management with information security information. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf
This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc. Showcasing this set of slides titled Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf. The topics addressed in these templates are Analysis Progress, Resolution Progress, Threshold Limit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting. This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc.
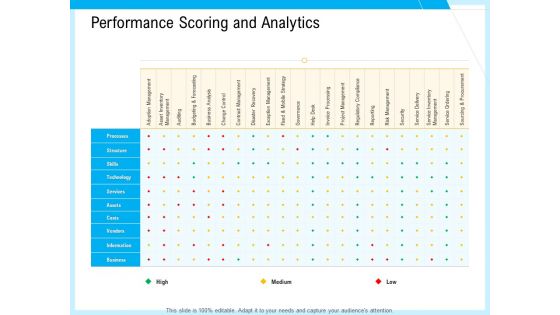
IT And Cloud Facilities Management Performance Scoring And Analytics Ppt Inspiration Design Ideas PDF
Deliver an awe-inspiring pitch with this creative it and cloud facilities management performance scoring and analytics ppt inspiration design ideas pdf bundle. Topics like processes, structure, technology, vendors, adoption management, security, project management, service delivery can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
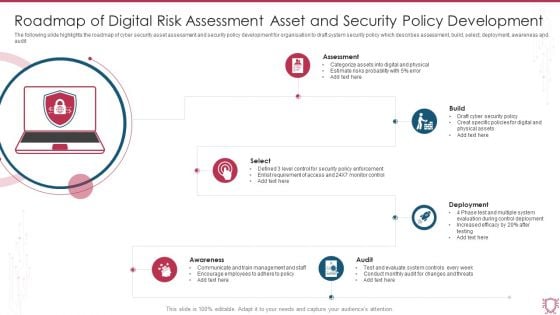
Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF
The following slide highlights the roadmap of cyber security asset assessment and security policy development for organisation to draft system security policy which describes assessment, build, select, deployment, awareness and audit. Persuade your audience using this Roadmap Of Digital Risk Assessment Asset And Security Policy Development Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Assessment, Build, Deployment, Select, Audit, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For Smart Home Security Solutions Company Profile Structure PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Smart Home Security Solutions Company Profile Structure PDF. Use them to share invaluable insights on Key Solutions Services, Intelligent Smart Devices, Operating System Integration, Service Delivery Model and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
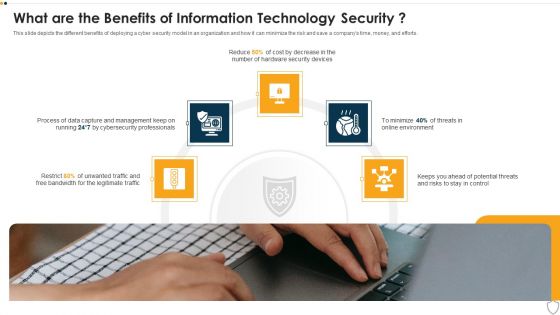
IT Security What Are The Benefits Of Information Technology Security Ppt Layouts Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a it security what are the benefits of information technology security ppt layouts ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, process, potential threats, security devices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF
The following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Create an editable Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V
The slide provides a comprehensive overview of the rules and regulations governing the cybersecurity industry. The slide aims to inform stakeholders regarding the laws in different countries such as USA, Europe, China And UK. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Global Data Security Industry Report Law And Regulations Governing Cybersecurity Industry IR SS V The slide provides a comprehensive overview of the rules and regulations governing the cybersecurity industry. The slide aims to inform stakeholders regarding the laws in different countries such as USA, Europe, China And UK.
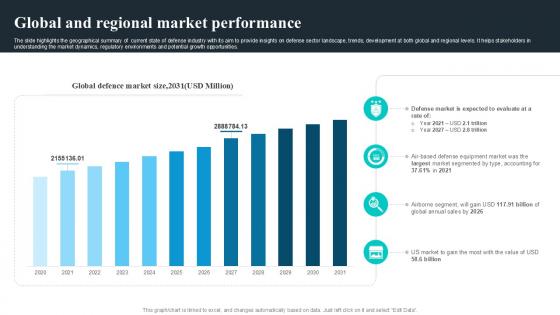
Global And Regional Market Performance Global Security Industry PPT Slide IR SS V
The slide highlights the geographical summary of current state of defense industry with its aim to provide insights on defense sector landscape, trends, development at both global and regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If you are looking for a format to display your unique thoughts, then the professionally designed Global And Regional Market Performance Global Security Industry PPT Slide IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global And Regional Market Performance Global Security Industry PPT Slide IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable. The slide highlights the geographical summary of current state of defense industry with its aim to provide insights on defense sector landscape, trends, development at both global and regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities.
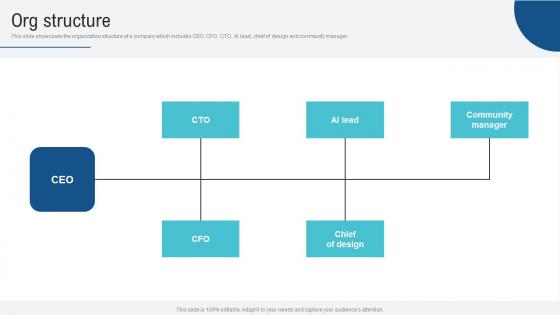
Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf
This slide showcases the organization structure of a company which includes CEO, CFO, CTO, AI lead, chief of design and community manager. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Org Structure Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf. This slide showcases the organization structure of a company which includes CEO, CFO, CTO, AI lead, chief of design and community manager.

Developing Firm Security Strategy Plan Budget Analysis For Effective Security Management At Workplace Designs PDF
Firm has prepared a budget for managing security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan budget analysis for effective security management at workplace designs pdf. Use them to share invaluable insights on incident management, risk management, client onboarding process, document management, information management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Strategies To Mitigate Cyber Security Risks Optimizing Cybersecurity Framework Roadmap Ppt File Icon PDF
Presenting this set of slides with name strategies to mitigate cyber security risks optimizing cybersecurity framework roadmap ppt file icon pdf. The topics discussed in these slides are implement enterprise, security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V
The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as. The Global Data Security Industry Report Strategies And Recommendations For Cybersecurity Industry IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression. The purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as.
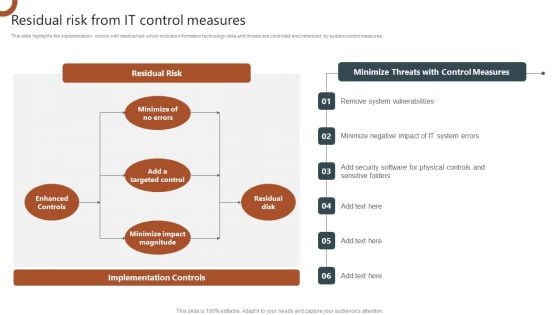
Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF
This slide highlights the implementation control with residual risk which includes information technology risks and threats are controlled and minimized by system control measures. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF today and make your presentation stand out from the rest.
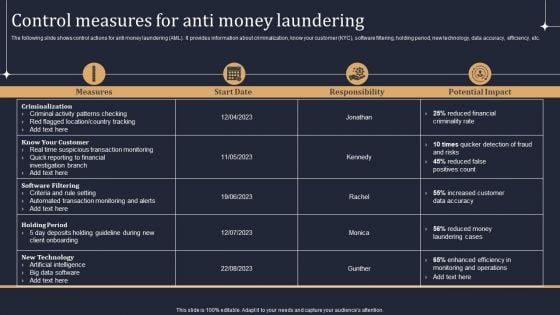
KYC Transaction Monitoring System Business Security Control Measures For Anti Money Laundering Ideas PDF
The following slide shows control actions for anti money laundering AML. It provides information about criminalization, know your customer KYC, software filtering, holding period, new technology, data accuracy, efficiency, etc. The following slide shows control actions for anti money laundering AML. It provides information about criminalization, know your customer KYC, software filtering, holding period, new technology, data accuracy, efficiency, etc. This modern and well arranged KYC Transaction Monitoring System Business Security Control Measures For Anti Money Laundering Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
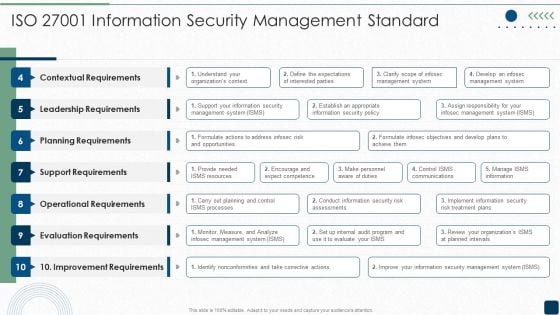
ISO 27001 Information Security Management Standard Microsoft PDF
Deliver and pitch your topic in the best possible manner with this ISO 27001 Information Security Management Standard Microsoft PDF. Use them to share invaluable insights on Contextual Requirements, Leadership Requirements, Planning Requirements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Employee Awareness Training Budget For FY2022 Ppt PowerPoint Presentation File Graphics Download PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative info security employee awareness training budget for fy2022 ppt powerpoint presentation file graphics download pdf bundle. Topics like build and maintain, secure network and system, protect cardholder data, maintain a vulnerability, management program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Architecture Of Citrix Secure Web Gateway Proxy Solution Web Threat Protection System
This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Architecture Of Citrix Secure Web Gateway Proxy Solution Web Threat Protection System for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes. This slide represents the Secure Web Gateway solution provided by Citrix. The purpose of this slide is to demonstrate the architecture of Citrixs SWG solution. The key components included are users, firewall, internet, logstream, SWG appliance, etc.

Before Vs After Implementing Secure Web Gateway Web Threat Protection System
This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Want to ace your presentation in front of a live audience Our Before Vs After Implementing Secure Web Gateway Web Threat Protection System can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use. This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc.

Importance Of Secure Web Gateway For Businesses Web Threat Protection System
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Secure Web Gateway For Businesses Web Threat Protection System. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides. This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc.

Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System
This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment. Present like a pro with Comparison Between Secure Web Gateway And Firewalls Web Threat Protection System. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide demonstrates the concept of two security technologies named firewalls and Secure Web Gateways. The purpose of this slide is to compare firewalls and SWGs on the basis of various factors such as function, scope, granularity, features and deployment.

Introduction To Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. This modern and well-arranged Introduction To Next Generation Secure Web Gateway Web Threat Protection System provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included. This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications.

Golden Key On Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Golden Key On Keyboard Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Computer PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Present our Technology PowerPoint Templates because Your audience will believe you are the cats whiskers. Download and present our Security PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Use our Business PowerPoint Templates because You have a driving passion to excel in your field. Our PowerPoint Templates and Slides will prove ideal vehicles for your ideas.Use these PowerPoint slides for presentations relating to Golden key on keyboard, technology, computer, security, success, business. The prominent colors used in the PowerPoint template are Yellow, Black, White. Achieve any feat you desire to. Our Golden Key On Keyboard Security PowerPoint Templates Ppt Backgrounds For Slides 0213 are extremely facilitating.
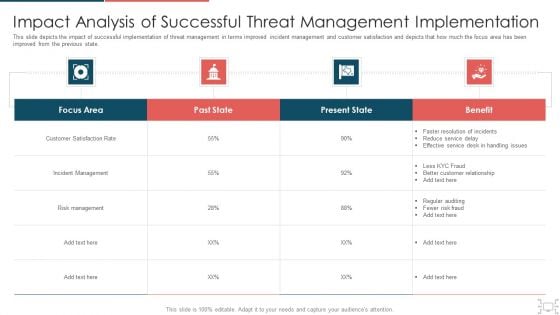
Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
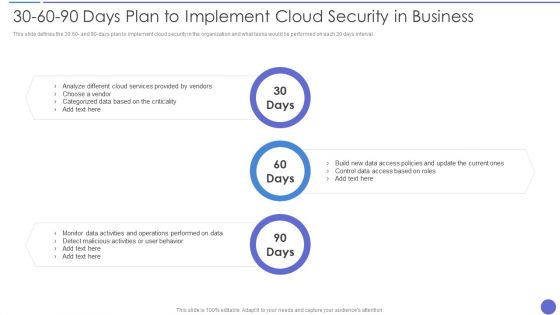
30 60 90 Days Plan To Implement Cloud Security In Business Information PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. This is a 30 60 90 Days Plan To Implement Cloud Security In Business Information PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyze, Cloud Services Provided , Control Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
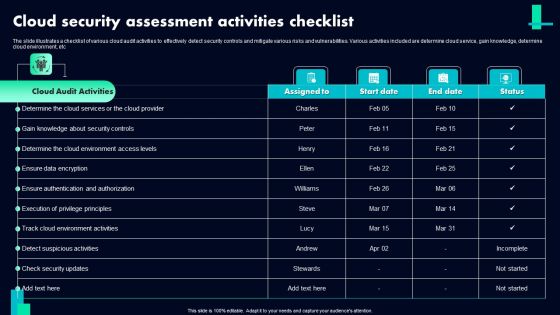
Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF
The slide illustrates a checklist of various cloud audit activities to effectively detect security controls and mitigate various risks and vulnerabilities. Various activities included are determine cloud service, gain knowledge, determine cloud environment, etc. Showcasing this set of slides titled Cloud Security Assessment Activities Checklist Ppt PowerPoint Presentation Gallery Model PDF. The topics addressed in these templates are Cloud Audit Activities, Ensure Data Encryption, Detect Suspicious Activities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
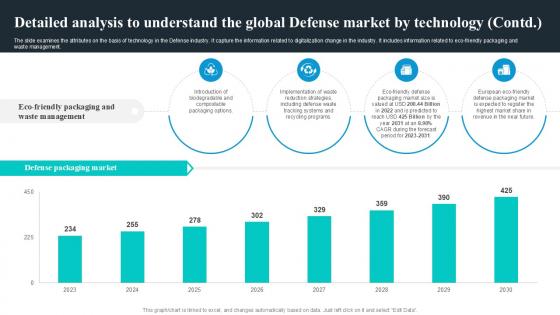
Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V
The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management. Present like a pro with Detailed Analysis To Understand Global Security Industry PPT PowerPoint IR SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. The slide examines the attributes on the basis of technology in the Defense industry. It capture the information related to digitalization change in the industry. It includes information related to eco-friendly packaging and waste management.
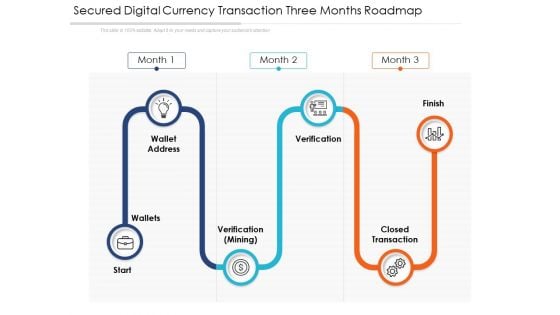
Secured Digital Currency Transaction Three Months Roadmap Graphics
Presenting our jaw dropping secured digital currency transaction three months roadmap graphics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
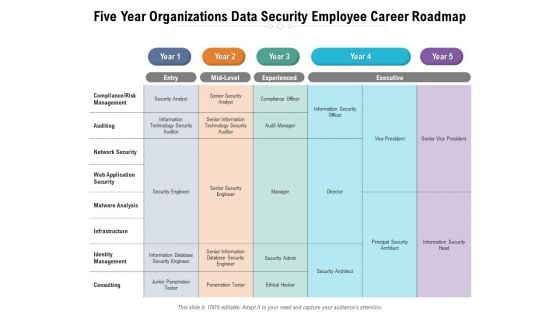
Five Year Organizations Data Security Employee Career Roadmap Inspiration
Presenting our jaw-dropping five year organizations data security employee career roadmap inspiration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Half Yearly Data Encryption For Security Career Roadmap Structure
Presenting our jaw-dropping half yearly data encryption for security career roadmap structure. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
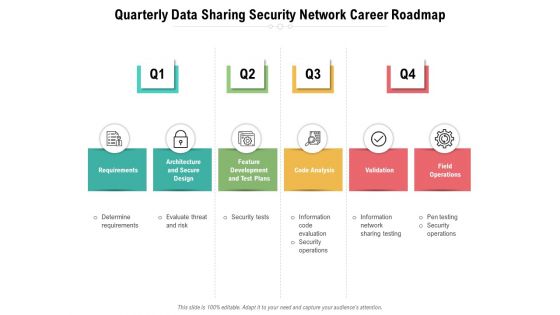
Quarterly Data Sharing Security Network Career Roadmap Guidelines
Presenting our jaw-dropping quarterly data sharing security network career roadmap guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
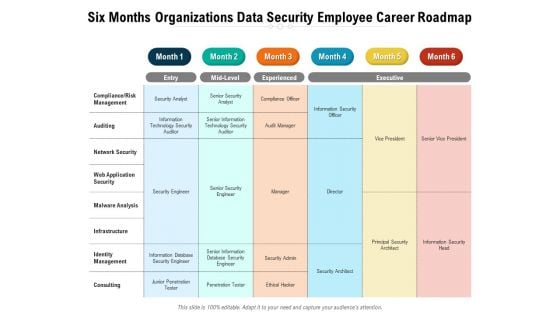
Six Months Organizations Data Security Employee Career Roadmap Ideas
Presenting our jaw-dropping six months organizations data security employee career roadmap ideas. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
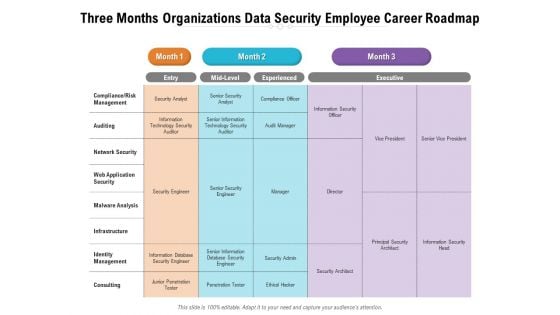
Three Months Organizations Data Security Employee Career Roadmap Background
Presenting our jaw-dropping three months organizations data security employee career roadmap background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
Five Years Security Business Growth Assessment Roadmap Icons
Presenting our jaw-dropping five years security business growth assessment roadmap icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
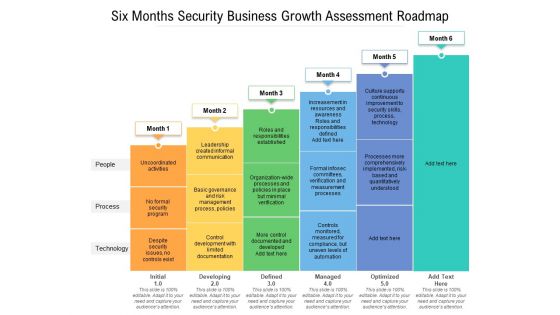
Six Months Security Business Growth Assessment Roadmap Topics
Presenting our jaw-dropping six months security business growth assessment roadmap topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
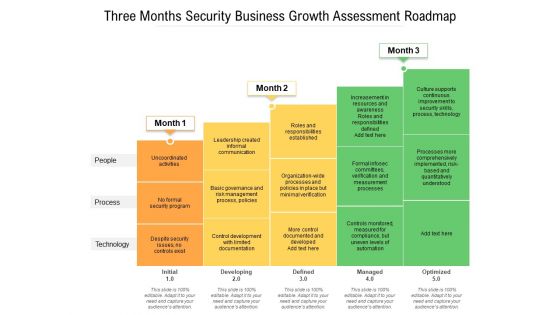
Three Months Security Business Growth Assessment Roadmap Formats
Presenting our jaw-dropping three months security business growth assessment roadmap formats. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
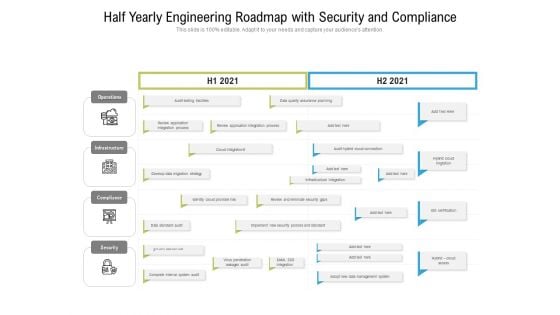
Half Yearly Engineering Roadmap With Security And Compliance Topics
Presenting our jaw-dropping half yearly engineering roadmap with security and compliance topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
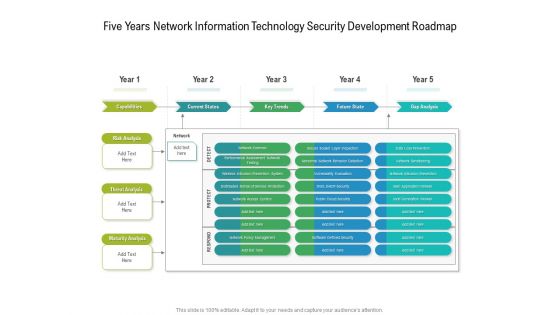
Five Years Network Information Technology Security Development Roadmap Mockup
Presenting our jaw dropping five years network information technology security development roadmap mockup. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Half Yearly Network Information Technology Security Development Roadmap Rules
Presenting our jaw dropping half yearly network information technology security development roadmap rules. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Quarterly Network Information Technology Security Development Roadmap Diagrams
Presenting our jaw dropping quarterly network information technology security development roadmap diagrams. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Six Months Network Information Technology Security Development Roadmap Slides
Presenting our jaw dropping six months network information technology security development roadmap slides. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.


 Continue with Email
Continue with Email

 Home
Home


































