Product Business Case

Steps To Integrate Secure Web Gateway Into Organization Web Threat Protection System
This slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc. Present like a pro with Steps To Integrate Secure Web Gateway Into Organization Web Threat Protection System. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today. This slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc.
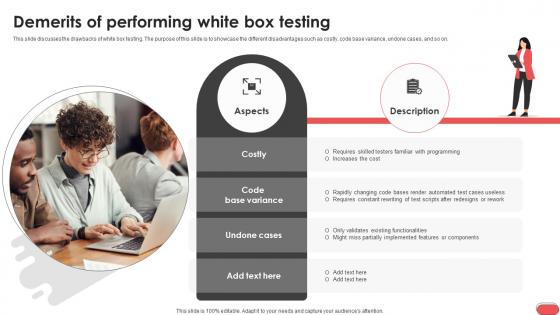
Demerits Of Performing White Box Testing Gray Box Testing Best Practices
This slide discusses the drawbacks of white box testing. The purpose of this slide is to showcase the different disadvantages such as costly, code base variance, undone cases, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Demerits Of Performing White Box Testing Gray Box Testing Best Practices can be your best option for delivering a presentation. Represent everything in detail using Demerits Of Performing White Box Testing Gray Box Testing Best Practices and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide discusses the drawbacks of white box testing. The purpose of this slide is to showcase the different disadvantages such as costly, code base variance, undone cases, and so on.
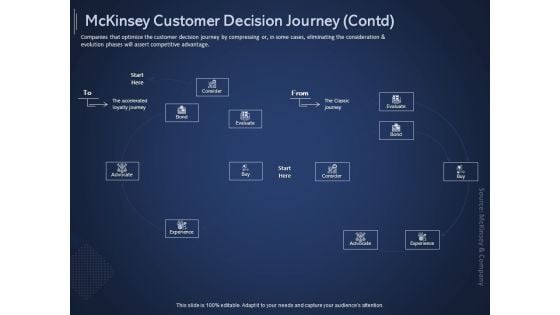
Online Promotional Marketing Frameworks Mckinsey Customer Decision Journey Contd Bond Download PDF
Companies that optimize the customer decision journey by compressing or, in some cases, eliminating the consideration and evolution phases will assert competitive advantage. Deliver an awe-inspiring pitch with this creative online promotional marketing frameworks mckinsey customer decision journey contd bond download pdf bundle. Topics like experience, consider, advocate, bond, evaluate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
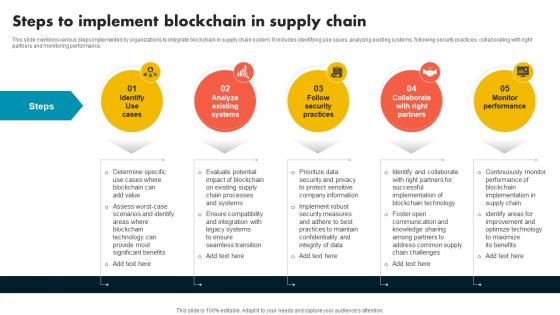
Steps To Implement Blockchain In Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V
This slide mentions various steps implemented by organizations to integrate blockchain in supply chain system. It includes identifying use cases, analyzing existing systems, following security practices, collaborating with right partners and monitoring performance. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Steps To Implement Blockchain In Supply Chain Supply Chain Evolution Harnessing The Power BCT SS V from Slidegeeks and deliver a wonderful presentation. This slide mentions various steps implemented by organizations to integrate blockchain in supply chain system. It includes identifying use cases, analyzing existing systems, following security practices, collaborating with right partners and monitoring performance.

Roadmap To Integrate Serverless Role Serverless Computing Modern Technology Slides Pdf
This slide represents the roadmap for integrating serverless computing. The main components included are identify the use case, choose a serverless provider, develop and deploy functions, configure trigger and events, test and monitor, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roadmap To Integrate Serverless Role Serverless Computing Modern Technology Slides Pdf can be your best option for delivering a presentation. Represent everything in detail using Roadmap To Integrate Serverless Role Serverless Computing Modern Technology Slides Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide represents the roadmap for integrating serverless computing. The main components included are identify the use case, choose a serverless provider, develop and deploy functions, configure trigger and events, test and monitor, etc.
Common Challenges Of Hyper Automation Implementation Ppt Ideas Icons Pdf
This slide depicts the common challenges of hyper automation implementation, including lack of process knowledge, specific customer demands, organizational challenges, and edge cases. It also caters to the solutions for these challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Common Challenges Of Hyper Automation Implementation Ppt Ideas Icons Pdf can be your best option for delivering a presentation. Represent everything in detail using Common Challenges Of Hyper Automation Implementation Ppt Ideas Icons Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide depicts the common challenges of hyper automation implementation, including lack of process knowledge, specific customer demands, organizational challenges, and edge cases. It also caters to the solutions for these challenges.
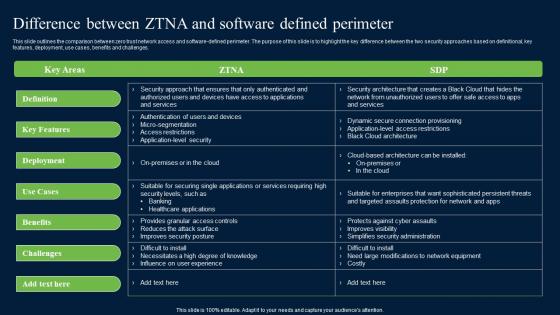
Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf can be your best option for delivering a presentation. Represent everything in detail using Difference Between ZTNA And Software Defined Zero Trust Network Security Brochure Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.
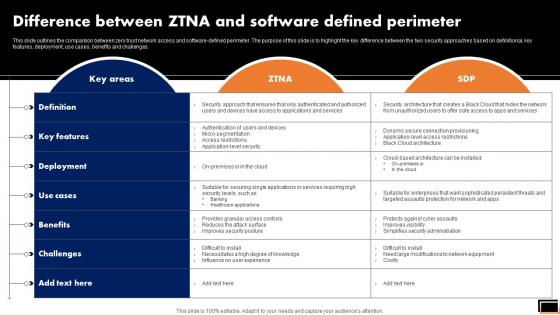
Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP
This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP can be your best option for delivering a presentation. Represent everything in detail using Difference Between Ztna And Software Defined Perimeter Software Defined Perimeter SDP and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results. This slide outlines the comparison between zero trust network access and software-defined perimeter. The purpose of this slide is to highlight the key difference between the two security approaches based on definitional, key features, deployment, use cases, benefits and challenges.

Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. Find highly impressive Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Outliers Model For Predictive Analytics Predictive Analytics For Improved Professional Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now. This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes.
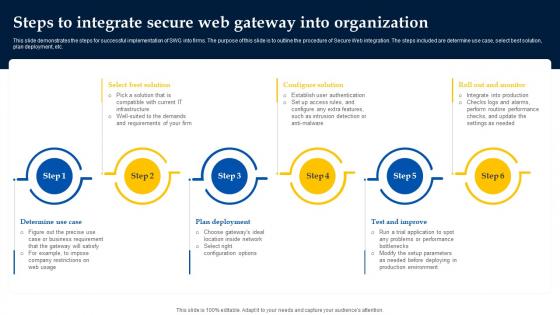
Web Access Control Solution Steps To Integrate Secure Web Gateway Into Organization
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Web Access Control Solution Steps To Integrate Secure Web Gateway Into Organization. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Web Access Control Solution Steps To Integrate Secure Web Gateway Into Organization today and make your presentation stand out from the rest This slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc.


 Continue with Email
Continue with Email

 Home
Home


































